BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings

Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
What caused the medibank data breach.

Edward Kost
The Medibank hack began with the theft of credentials belonging to a n individual with privileged access to Medibank’s internal systems. These credentials were sold and purchased on the dark web by an unconfirmed buyer who used them to gain access to Medibank’s internal system.
Once inside, the threat actor identified the location of a customer database and then used the stolen privileged credentials to write a script to automate the customer data exfiltration process - a similar data theft mechanism was used in the Optus data breach .
This stolen data was placed into a zip file and extracted through two established backdoors. Medibank’s security team allegedly detected suspicious activity at this point and shut down both back doors, but not before 200GB worth of customer data was stolen,
9.7 million Medibank customers were impacted by the breach. Compromised records include:
- Birth dates
- Passport numbers
- Information on medicare claims
News of the successful attack was published on the dark web blog associated with a ransomware gang tracked as BlogXX (a cybercriminal group believed to be a reformation of the notorious ransomware gange REVil). The hackers posted a sample of the stolen data to prove the legitimacy of their claims and demanded Medibank pay a US$10m ransom to prevent the entire database from being freely published on the dark web.
To force Medibank to pay the ransom, the cybercriminal group will continue posting segments of the stolen database until the ransom is paid completely.

Medibank CEO, David Koczkar, announced that the company has refused to pay the ransom since cybercriminals can never be trusted to follow through with their promises.
“...paying could have the opposite effect and encourage the criminal to directly extort our customers and there is a strong chance that paying puts more people in harm’s way by making Australia a bigger target.” - Medibank CEO David Koczkar
For a more technical explanation of the Medibank hack, see this post .

Corporate Credential Theft: The Reason the Medibank Breach was Possible
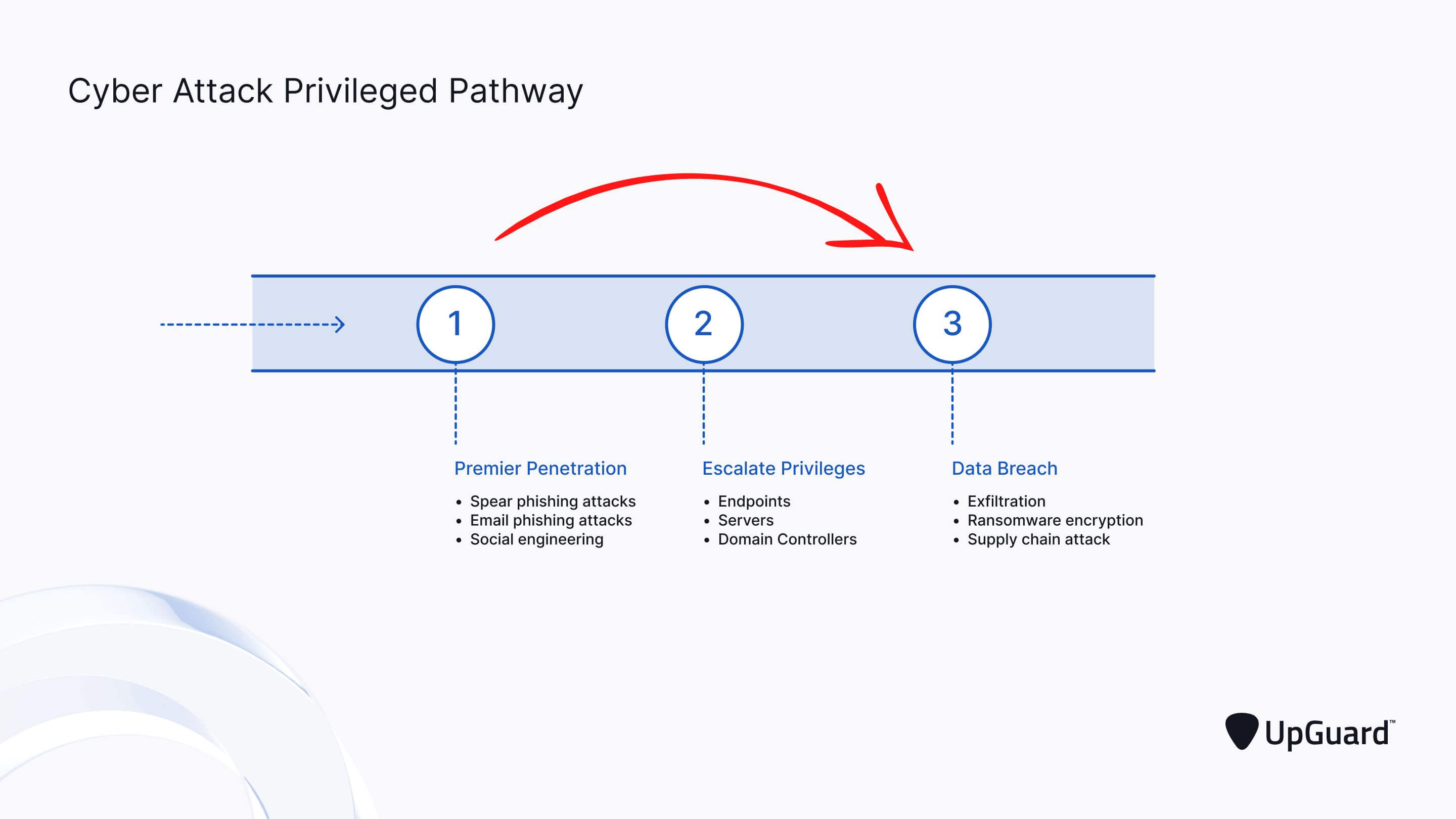
The Medibank data breach was made possible by the theft of internal credentials believed to belong to an individual with privileged system access. Internal credential theft is one of the first objectives of almost every cyberattack. It hasn’t yet been confirmed how the Medibank credentials were stolen, but the most common method of stealing account information is through a tactic known as Phishing - a style of cyberattack where hackers send fraudulent emails with malicious links leading to credential-stealing websites.
When hackers steal “disappointing” account credentials with limited user permissions, they use them to get inside a network and then clandestinely examine every region of it, searching for higher privilege credentials to steal - a process known as ‘lateral movement.’
By instantly getting their hands on privileged account details, the Medibank hackers bypassed the arduous lateral movement stage of the attack and skipped straight to the final data breach stage. This compressed the cyberattack pathway, allowing the breach to be completed much faster.
See how your organization's security posture compares to Medibank's.
View Medibank's security report.
How Could the Medibank Data Breach Have Been Prevented?
Mapping all of the exploits leading to the Medibank bank breach to their corresponding security controls reveals four initiatives that could have prevented the incident from happening.
1. Cyber Threat Awareness Training
Cyber threat awareness training teaches employees how to recognize and correctly respond to corporate credential theft attempts from phishing and social engineering attacks.
We don’t yet know how the Medicare credentials that facilitated the breach were stolen, but by teaching your employees how to recognize a phishing attack, you’ll protect your business from the most common method of credential theft.
Learn more about phishing attacks >
2. Implement the Principle of Least Privilege (POLP)
The principle of least privilege is an account security policy that limits each employee’s account access to the minimum level required to perform daily tasks. This should be a standard security policy for all Australian businesses since excessive privileges present a significant security risk.
By reducing the chances of hackers bypassing the privilege escalation phase of an attack, a POLP policy forces the entire attack to take longer, which increases the chances of vigilant security teams detecting and intercepting the breach attempt. The Medibank event proved that it’s possible to disrupt a cyberattack while it's still unfolding, reducing its potential damages.
According to Medibank, its systems were not encrypted during the attack, which is odd considering the attackers were likely a ransomware gang. A possible reason for this is that by promptly shutting down the backdoors established by the cyber criminals to facilitate the breach, Medibank disrupted the attack before it reached its final encryption phase .
Learn more about the Principle of Least Privilege >
3. Segment your Network
A network segmentation strategy separates a network into different segments or “zones” to make sensitive data more difficult to locate and access. In case a sensitive zone is located, connection requests to this region should be passed through a jump server (a hardened system used to manage connection requests to sensitive zones) to further reduce the potential for compromise.
Learn more about network segmentation best practices >
4. Use Multi-Factor Authentication (MFA)
It hasn’t yet been confirmed whether multi-factor authentication was bypassed during the Medibank hack. MFA is one of the most effective measures against account compromise attempts.
According to Microsoft , Multi-Factor Authentication could prevent up to 99.9% of account compromise attacks.
All employee accounts, including privileged access accounts, should be protected with MFA - ideally, adaptive MFA since it’s the hardest to bypass
When a cybercriminal attempts to connect to a network with an account protected with MFA, they’ll be unable to complete the login process unless they also pass a series of user identity verification steps. These additional verification requirements are difficult to bypass and could be enough to stop an attack from progressing.
Note: Even though bypassing MFA is difficult, it’s still possible. If you’re implementing MFA, make sure you’re aware of these common bypass methods.

How UpGuard can Help
Every organisation is at risk of corporate credential compromise, but not every organisation will suffer the same devastating outcome as Medicare when these events occur. UpGuard has developed a data leak detection solution to help organisations rapidly detect sensitive credential dumps on popular dark ransomware blogs. Rapid detection means that compromised accounts can be secured much faster, decreasing the chances of follow-up cyberattacks targeting impacted businesses.

Each detected leak is manually reviewed by cybersecurity experts to eliminate false positives and support the efficiency of data leak remediation efforts.
Reviewed by

Kaushik Sen
Ready to see upguard in action, join 27,000+ cybersecurity newsletter subscribers, a complete guide to data breaches.

Related posts
How to prevent data breaches in 2024 (highly effective strategy), the 72 biggest data breaches of all time [updated 2024].

9 Ways to Prevent Third-Party Data Breaches in 2024
What are cloud leaks, what is a supply chain attack examples & prevention strategies, zero trust as a defence against supply chain attacks.
- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity

Note: this article was updated on November 11, 2022 to reflect a development in the Australian Federal Police's investigation
The hacker responsible for a data breach of Australian health insurance provider Medibank which affected 9.7 million people has released private medical information on the dark web .
The hacker posted a file labelled “abortions” to dark web hacking site BreachForums on November 10, 2022. It apparently contains information on procedures that policyholders have claimed on, including miscarriages, terminations and ectopic pregnancies.
The hackers also released files containing customer data called "good-list" and "naughty-list" on November 9, 2022. The so-called “naughty-list” reportedly includes details on those who had sought medical treatment for HIV, drug addiction or alcohol abuse or for mental health issues like eating disorders.
The hacker added to the November 10 data leak post, saying: "Society ask us about ransom, it's a 10 millions (sic) usd. We can make discount 9.7m 1$=1 customer."
During question time in Australian parliament on November 10, Minister of Home Affairs Clare O’Neil hit back at the hackers, saying: “I want the scumbags behind this attack to know that the smartest and toughest people in this country are coming [at] you.
“I want to say, particularly to the women whose private health information has been compromised overnight, as the minister for cyber-security but more importantly, as a woman, this should not have happened, and I know this is a really difficult time.”
David Koczkar, CEO of Medibank, called the release of the data “disgraceful” and a “weaponization of people’s private information”. He also called those involved in the cyber-attack and data leak “deplorable”.
In an attempt to protect those affected by the cyber security incident and the subsequent data leaks , Medibank urged members of the public and the media to not “unnecessarily download sensitive personal data from the dark web” and to “refrain from contacting customers directly”.
How did the breach happen?
The initial cyber security incident occurred on October 13, 2022, when Medibank detected some “unusual activity” on its internal systems. After dealing with the cyber-attack, Medibank said in a statement that there was “no evidence that customer data has been accessed” during the breach.
Medibank was then contacted on October 17 by the malicious party , who aimed to “negotiate with the [healthcare] company regarding their alleged removal of customer data”.
The malicious party attempted to weaponize Medibank’s customers’ private medical data to extort the medical insurer, saying that they would release the data of the“1k most [prominent] media persons” that include “[those with the] most [social media] followers, politicians, actors, bloggers, [LGBTQ+] activists [and] drug-addicted people” as well as people with “very interesting diagnoses”.
It was confirmed on October 20 that the hacker’s claims were legitimate. Medibank, however, publicly refused to bend to the hacker’s demands and said it would not pay a ransom over concerns it would “encourage the criminal to directly extort [its] customers”.
The company also said that it had received council from cyber security experts who had said there was only a “limited chance” that paying the ransom would result in the return of the stolen data.
How we got here with @medibank . It initially said compromised login credentials were used (that may have involved VPN access). The attackers claim they accessed Redshift - an Amazon data warehousing product - via jump servers. #auspol #infosec (1/4) — Jeremy Kirk (@Jeremy_Kirk) November 10, 2022
In a tweet on November 10, journalist Jeremy Kirk suggested that the hack took place as a result of hackers gaining access to Medibank’s internal systems via compromized login credentials, a tactic that “may have involved VPN access”.
According to Kirk, the hackers claim they used jump servers to access Amazon data warehouse Redshift. The hackers also claim that they had access to Medibank’s internal systems for a month before they were discovered.
What data was stolen in the hack?
On November 7, Medibank revealed the true extent of the hack . The malicious actor gained unauthorized access to and stole the data for 9.7 million past and present customers.
The information included email addresses, phone numbers, addresses, Medicare numbers, names, dates of birth, passport numbers and visa details. It also encompassed the health claims data for 192,000 customers which contained private medical information including where customers were admitted for procedures, service provider names and locations and codes associated with diagnosis and procedures given.
Medibank urged all those affected to “stay vigilant” against cyber attacks that may be levelled against them because of the leak.
A full timeline of the data breach
- 13 October – Medibank notices some unusual activity on its networks. The affected networks are shut down.
- 14 October – the affected networks are restarted. Medibank releases a statement saying that there is “no evidence” that any customer data was accessed during the breach.
- 17 October – Medibank releases an update on the cyber security incident, describing the ongoing investigation into the unusual activity and recognizing that while it was “consistent with the precursors to a ransomware event”, there was still no evidence customer data had been compromised.
- 19 October – Medibank are contacted directly by the hacker, who claims to have stolen 200GB worth of customer data. The hacker attempts to negotiate the release of the information.
- 20 October – Medibank confirms that the hacker’s claims are legitimate. The Australian Federal Police starts investigating the cyber-attack.
- 7 November – the scope of the data breach is revealed, with Medibank confirming that the data of 9.7 million past and present customers was stolen in the breach. Medibank makes a public statement refusing to pay any ransom to the hacker.
- 8 November – the hacker threatens to release files on the dark web and encourages Medibank shareholders to sell their shares.
- 9 November – the hacker releases the “good-list” and “naughty-list” customer data files on the dark web. The Australian Federal Police partners with Commonwealth agencies and the Five Eyes Law Enforcement partners to investigate the cyber crime. Operation Guardian, which was previously introduced to help the victims of the Optus data breach, is extended to those affected by the Medibank data breach.
- 10 November – the hacker releases the “abortions” customer data files on the dark web and demands US$10mn to stop releasing data.
- 11 November - The AFP, in collaboration with Interpol, linked the gang to a Russian hacking group
More From Incident of the Week
Iotw: victoria court recordings exposed in suspected ransomware attack.
Unauthorized access disrupted audio visual in-court technology network impacting video recordings, a...

IOTW: Xfinity data breach impacts 35 million customers
Exposed data includes usernames, hashed passwords and social security numbers

IOTW: Russia-linked cyber attack targets Ukraine’s biggest phone operator
Powerful attack knocked out internet access and mobile communications, damaging IT infrastructure

IOTW: HTC confirms cyber attack as BlackCat ransomware gang teases stolen data
BlackCat/ALPHV ransomware group leaked photos of what appears to be stolen passports, contact lists,...

IOTW: Okta data breach affects all customer support users
Hackers stole information on all users of Okta’s customer support system

RECOMMENDED

FIND CONTENT BY TYPE
- Case Studies
- White Papers
Cyber Security Hub COMMUNITY
- Advertise with us
- Cookie Policy
- User Agreement
- Become a Contributor
- All Access from CS Hub
- Become a Member Today
- Media Partners
ADVERTISE WITH US
Reach Cyber Security professionals through cost-effective marketing opportunities to deliver your message, position yourself as a thought leader, and introduce new products, techniques and strategies to the market.
JOIN THE Cyber Security Hub COMMUNITY
Join CSHUB today and interact with a vibrant network of professionals, keeping up to date with the industry by accessing our wealth of articles, videos, live conferences and more.

Cyber Security Hub, a division of IQPC
Careers With IQPC | Contact Us | About Us | Cookie Policy
Become a Member today!
PLEASE ENTER YOUR EMAIL TO JOIN FOR FREE
Already an IQPC Community Member? Sign in Here or Forgot Password Sign up now and get FREE access to our extensive library of reports, infographics, whitepapers, webinars and online events from the world’s foremost thought leaders.
We respect your privacy, by clicking 'Subscribe' you will receive our e-newsletter, including information on Podcasts, Webinars, event discounts, online learning opportunities and agree to our User Agreement. You have the right to object. For further information on how we process and monitor your personal data click here . You can unsubscribe at any time.
- International edition
- Australia edition
- Europe edition

Medibank confirms hacker had access to data of all 3.9 million customers
Data breach, which exposed all Medibank, ahm and international student data, could cost health insurer $35m
- Follow the latest news updates with our live blog
- Get our morning and afternoon news emails, free app or daily news podcast
Medibank has revealed all of its 3.9 million customers have had their data exposed to a hacker, in a significant escalation of the cyber-attack on the Australian health insurer.
In an update to the Australian Stock Exchange on Wednesday, the company said that since Tuesday’s announcement that all customer data may have been exposed , the investigation into the breach has now established the hacker had access to all Medibank, ahm and international student customers’ personal data, and significant amounts of health claims data.
The personal information includes name, address, date of birth, some Medicare card numbers and gender. The health information includes the claim codes made by customers.
Medibank still cannot say definitively how many or which customers are affected beyond the 1,000 records provided to the insurer by the hacker in the past two weeks. It is through this communication with the hacker that Medibank has been able to determine the extent of the breach so far.
Sign up for our free morning newsletter and afternoon email to get your daily news roundup
The breach will also affect former customers, with Medibank confirming yesterday that state and territory health record laws require the company to keep data for seven years.
Customers will be provided a hardship financial support package if they are in a “uniquely vulnerable position” as a result of the hack, and Medibank says it will reimburse customers for costs associated with the reissuing of ID documents for those that were compromised in the hack.
The hack is likely to cost the company a minimum between $25m and $35m, Medibank said. This is due to Medibank not having cyber-attack insurance, and this estimated cost does not include customer compensation or regulatory or legal costs that may be brought against the company.
Medibank is in communication with the hacker – who obtained stolen Medibank credentials from another hacker on a Russian cybercriminal forum – but the company has declined to say whether it would pay any ransom demands made.
In a call with investors on Wednesday, Medibank’s head of technology and operations, John Goodall, said that the company had deployed monitoring tools on its network and those tools suggest that the hacker is no longer in the company’s systems.
Medibank’s chief executive, David Koczkar, said there was no evidence that credit card information had been compromised but he would not rule it out.
“We have no evidence that credit card data has been removed,” he said. “But I will be very clear to say we are continuing to investigate. And as soon as it becomes clear to us if that changes, we will make it clear.”
after newsletter promotion
He said the information the company has been able to obtain about the attack has been through communications with the hacker, who showed evidence of records obtained.
In a statement to the stock exchange, Koczkar apologised unreservedly to customers.
“This is a terrible crime – this is a crime designed to cause maximum harm to the most vulnerable members of our community.”
Medibank announced on Tuesday it would delay premium increases for all customers until the end of January 2023. On Wednesday, the company said this would cost around $62m, which would be offset by savings the company has made during the Covid-19 pandemic.
The hack is under investigation by the Australian federal police.
- Australian politics
Most viewed

I agree to receive Information Age.
I declare that I have read, understood and agree to the ACS Privacy Policy and consent to my personal information being collected, held and processed for the purposes outlined in that policy.
Thanks for signing up!
Sorry there was an error with your request.

Medibank finally reveals ‘rookie mistake’ in breach
Hacker got credentials from third-party it provider..
By Casey Tonkin on Mar 02 2023 06:47 AM
Print article

Australian health insurer Medibank made a “rookie mistake” that led to one of the largest data breaches in our country’s history, a cyber security expert has claimed in the wake of new details about the breach.
In its half-yearly report, Medibank shared a brief outline of how the Russian-based attackers got access to personal details of all 9.7 million of its customers .
The health insurer said its systems were accessed “using a stolen Medibank username and password used by a third party IT service provider”.
“The criminal used the stolen credentials to access Medibank’s network through a misconfigured firewall which did not require an additional digital security certificate,” the health insurer said.
“The criminal was able to obtain further usernames and passwords to gain access to a number of Medibank’s systems and their access was not contained.
Once inside, the attackers gained a trove of customer information which they used to try and extort Medibank, demanding a ransom which the company refused to pay.
The saga ended with the hackers dumping the full 5GB dataset online .
Louay Ghashash, chair of the Australian Computer Society’s (ACS) Cyber Security Committee, said it was a “rookie mistake” for Medibank to give a third party uncontrolled access to its systems.
“The fact they left this service provider running freely without checking its security practices and conducting user access reviews is a failure on Medibank’s part,” Ghashash told Information Age .
“Service providers needs to have security standards that are better than or equal to the customer’s standard but it’s up to the customers to make certain of that.”
Ghashash said it's not uncommon for companies to share admin accounts with third party providers who may need high level access to their environment.
But this makes it near-impossible to enforce multi-factor authentication (MFA), creating a serious weakness in that company’s security.
“Service providers are often necessary but they can add elevated risk to a business, so you need to ensure you trust them,” he said.
"In some cases you need to audit the firm, send someone to validate their claims that they regularly patch their infrastructure, and see evidence that they are following the Essential Eight at a minimum.
For Medibank, the cost of failing to mitigate against the risk of a third party handing over high-level credentials to an attacker has already reached $26 million, though it expects that figure could be as high as $45 million by the end of the financial year.
And that’s excluding the potential “remediation, regulatory or litigation related costs” which might come from a class action lawsuit that has been launched against the insurer, or fines from the Office of the Australian Information Commission (OAIC) which is investigating the breach.
Aaron Bugal, regional CTO with cyber security company Sophos, said “negligence has proven to be a complicit element” in cyber attacks
“Multifactor authentication could have negated the impact of stolen credentials, and while not impervious to a determined cyber criminal, it would have limited the ease with which they gained initial access,” he said.
On Wednesday, the OAIC published its latest notifiable data breaches report covering the July to December 2023.
In that period, the commissioner was notified of 497 breaches, most of which affected fewer than 100 people.
Of those breaches, 70 per cent were attributed to criminal or malicious attackes, with 25 per cent being caused by human error – such as personal information being emailed to the wrong recipient – and the remaining five per cent a result of system faults.


Related Articles

Australians losing 'significantly more' to fake invoice scams

X threatens to sue Australian govt over removal notice

US joins UK-led global AI safety initiative

OpenAI debuts voice cloning
Medibank hackers declare ‘case closed’ as trove of stolen data is released

The cybercriminals behind the Medibank ransomware attack have published what appears to be the rest of the data stolen from the Australian health insurance giant.
The attackers, believed to be linked to the Russian-backed REvil ransomware gang , posted an update to its dark web blog in the early hours of Thursday morning, saying: “Happy Cyber Security Day!!! Added folder full. Case closed.”
The dark web blog was unavailable at the time of writing, but according to Medibank , the “full” folder contained six zipped files of raw data. At more than six gigabytes in size, the cache is much larger than any of the attackers’ previous Medibank leaks. Medibank confirmed in November that the attackers took 9.7 million customers’ personal details and health claims data for almost 500,000 customers.
The Medibank cybercriminals previously published data including customers’ names, birth dates, passport numbers, information on medical claims and sensitive files related to abortions and alcohol-related illnesses. Portions of the data seen by TechCrunch also appear to include correspondence between the cybercriminals and Medibank CEO David Koczkar, including a message in which the hackers threaten to leak “keys for decrypting credit cards,” despite Medibank’s assertion that no banking or credit card details were accessed.
The cybercriminals claimed they published the data after Medibank refused to pay their $10 million ransom demand, which was later reduced to $9.7 million, or $1 per affected customer.
Medibank said on Thursday that it is in the process of analyzing the latest leaked data but said it “appears to be the data we believed the criminal stole.”
“While our investigation continues there are currently no signs that financial or banking data has been taken,” Medibank said. “And the personal data stolen, in itself, is not sufficient to enable identity and financial fraud. The raw data we have analyzed today so far is incomplete and hard to understand.”
Although it’s believed the hackers have released all of the data stolen from Medibank, the company added that it expects “the criminal to continue to release files on the dark web.”
The Australian health insurance giant is urging customers to be vigilant with all online communications and transactions and to be alert for phishing scams related to the breach. Medibank added that to strengthen its security, it has this week added two-factor authentication in its contact centers to verify the identity of customers.
While Medibank is taking steps to shore up its cybersecurity, the company could face major financial penalties after the Australian parliament this week passed legislation that paves the way for businesses to be fined up to $50 million for repeated or serious data breaches.
Australia’s data and privacy watchdog, the Office of the Australian Information Commissioner (OAIC) on Thursday announced that it had begun an investigation into the personal information handling practices of Medibank. The OAIC — also investigating the recent Optus breach — said its investigation will focus on whether Medibank took reasonable steps to protect the personal information they held from misuse, interference, loss, unauthorized access, modification or disclosure.
“If the investigation finds serious and/or repeated interferences with privacy in contravention of Australian privacy law, then the Commissioner has the power to seek civil penalties through the Federal Court of up to $2.2 million for each contravention,” the OAIC said.
News of the investigation comes after the Australian Federal Police (AFP) said in November that it knows the identity of the individuals responsible for the attack on Medibank. The agency declined to name the individuals but said the police believe that those responsible for the breach are based in Russia, though some affiliates may be in other countries. The Russian Embassy in Canberra rebuffed the allegations.
Though their identities remain unknown, the attackers responsible already appear to be moving on from the Medibank hack. In recent days the group has posted new victims to its dark web blog, including New York-based medical group Sunknowledge Services and the Kenosha Unified School District.
Ransomware is a global problem that needs a global solution
OAIC opens investigation into Medibank over data breach
1 December 2022
The Office of the Australian Information Commissioner (OAIC) today commenced an investigation into the personal information handling practices of Medibank in relation to its notifiable data breach.
This decision follows the OAIC’s preliminary inquiries commenced into the matter in October.
The OAIC’s investigation will focus on whether Medibank took reasonable steps to protect the personal information they held from misuse, interference, loss, unauthorised access, modification or disclosure.
The investigation will also consider whether Medibank took reasonable steps to implement practices, procedures and systems to ensure compliance with the Australian Privacy Principles (APPs).
If the OAIC’s investigation satisfies the Commissioner that an interference with the privacy of individuals has occurred, the Commissioner may make a determination that can include requiring Medibank to take steps to ensure the act or practice is not repeated or continued, and to redress any loss or damage. If the investigation finds serious and/or repeated interferences with privacy in contravention of Australian privacy law, then the Commissioner has the power to seek civil penalties through the Federal Court of up to $2.2 million for each contravention.
Given that the breach involves sensitive information, we remind any Medibank customers affected that they may seek assistance through Medibank’s helpline.
Australian Information Commissioner and Privacy Commissioner Angelene Falk also reminded organisations covered by the Privacy Act 1988 to ensure they take reasonable steps to protect the personal information they hold.
“All organisations should review their personal information handling practices to ensure reasonable security safeguards are in place,” she said.
In line with the OAIC’s Privacy regulatory action policy , the OAIC will await the conclusion of the investigation before commenting further.
About Commissioner-initiated investigations
The Commissioner is authorised to investigate an act or practice that may be an interference with the privacy of an individual or a breach of APP 1 under section 40(2) of the Privacy Act.
Preliminary inquiries will continue with Medibank regarding compliance with the Notifiable Data Breaches scheme.
Under the Notifiable Data Breaches scheme, organisations covered by the Privacy Act must notify affected individuals and the OAIC as quickly as possible if they experience a data breach that is likely to result in serious harm to individuals whose personal information is involved.
Further assistance
The Australian Government has released a factsheet to provide information on what to do if your data has been compromised in the recent Medibank and AHM cyber incident.
If you think you may be affected by the breach, contact Medibank Private on 13 23 31 or AHM on 13 42 46.
Medibank has an information page for enquiries and details of a customer support package on its newsroom page.
Customers can also seek advice or support around mental health or wellbeing by contacting 1800 644 325.
If you are concerned your identity has been compromised, contact your bank immediately and call IDCARE on 1800 595 160.
There are a number of resources that provide information on how individuals can take steps to mitigate the risk from data breaches. Information about responding to a data breach notification is available on our website. Resources are also available at cyber.gov.au .

- Terms and conditions
- Privacy policy
- Accessibility
Monday to Thursday 10 am to 4 pm (AEST/AEDT)
Acknowledgement of Country
The OAIC acknowledges Traditional Custodians of Country across Australia and their continuing connection to land, waters and communities. We pay our respect to First Nations people, cultures and Elders past and present.
© Commonwealth of Australia
The Biggest Data Breach of 2022: Medibank-How did it happen?

Taresh Pattanaik
The Medibank hack began with the theft of credentials belonging to a n individual with privileged access to Medibank’s internal systems. These credentials were sold and purchased on the dark web by an unconfirmed buyer who used them to gain access to Medibank’s internal system.
Once inside, the threat actor identified the location of a customer database and then used the stolen privileged credentials to write a script to automate the customer data exfiltration process - a similar data theft mechanism was used in the Optus data breach .
This stolen data was placed into a zip file and extracted through two established backdoors. Medibank’s security team allegedly detected suspicious activity at this point and shut down both back doors, but not before 200GB worth of customer data was stolen,
9.7 million Medibank customers were impacted by the breach. Compromised records include:
- Birth dates
- Passport numbers
- Information on medicare claims
News of the successful attack was published on the dark web blog associated with a ransomware gang tracked as BlogXX (a cybercriminal group believed to be a reformation of the notorious ransomware gange REVil). The hackers posted a sample of the stolen data to prove the legitimacy of their claims and demanded Medibank pay a US$10m ransom to prevent the entire database from being freely published on the dark web.
To force Medibank to pay the ransom, the cybercriminal group will continue posting segments of the stolen database until the ransom is paid completely.
Hacker annoucement published on the dark web
Medibank CEO, David Koczkar, announced that the company has refused to pay the ransom since cybercriminals can never be trusted to follow through with their promises.
“...paying could have the opposite effect and encourage the criminal to directly extort our customers and there is a strong chance that paying puts more people in harm’s way by making Australia a bigger target.”
- Medibank CEO David Koczkar
Corporate Credential Theft: The Reason the Medibank Breach was Possible
The Medibank data breach was made possible by the theft of internal credentials believed to belong to an individual with privileged system access. Internal credential theft is one of the first objectives of almost every cyberattack. It hasn’t yet been confirmed how the Medibank credentials were stolen, but the most common method of stealing account information is through a tactic known as Phishing - a style of cyberattack where hackers send fraudulent emails with malicious links leading to credential-stealing websites.
When hackers steal “disappointing” account credentials with limited user permissions, they use them to get inside a network and then clandestinely examine every region of it, searching for higher privilege credentials to steal - a process known as ‘lateral movement.’
By instantly getting their hands on privileged account details, the Medibank hackers bypassed the arduous lateral movement stage of the attack and skipped straight to the final data breach stage. This compressed the cyberattack pathway, allowing the breach to be completed much faster.
How Could the Medibank Data Breach Have Been Prevented?
Mapping all of the exploits leading to the Medibank bank breach to their corresponding security controls reveals four initiatives that could have prevented the incident from happening.
Cyber Threat Awareness Training
Cyber threat awareness training teaches employees how to recognize and correctly respond to corporate credential theft attempts from phishing and social engineering attacks.
We don’t yet know how the Medicare credentials that facilitated the breach were stolen, but by teaching your employees how to recognize a phishing attack, you’ll protect your business from the most common method of credential theft.
Law firm launches class action on behalf of millions of customers caught up in Medibank data hack
A class action has been launched on behalf of customers whose highly sensitive health data was stolen during last year's massive Medibank data breach.
Key points:
- More than 9 million current and former Medibank customers had their data stolen in the October 2022 hack
- Lawyers will seek compensation for financial losses as well as stress caused by the data theft
- Australia has an "opt-out" system for class actions so all affected customers are automatically part of the legal proceedings
Law firm Slater and Gordon has issued proceedings in the Federal Court seeking compensation for people caught up in the October 2022 breach.
Data from millions of current and former Medibank customers was hacked by a Russian ransomware group that released the information in stages onto the dark web.
The legal action also covers customers of Medibank's subsidiary Australian Health Management (ahm) as well as customers of Medibank's travel insurance products.
Separate legal action was launched by three other law firms in January .
The statement of claim alleges Medibank and ahm breached privacy and consumer laws as well as legislation that governs customer data retention and data protection in Australia.
It argues Medibank and ahm failed to take reasonable steps to protect customers' personal information from unauthorised access or disclosure, failed to destroy or de-identify former customers' information and failed to comply with legal obligations in collecting, using, storing and disclosing customer information.
Slater and Gordon will also allege in court that Medibank had assured its customers that it had "adequate and appropriate security controls in place" to protect their information.
"This breach was one of the most serious breaches in Australian history," Class Actions Practice Group leader Ben Hardwick said.
Mr Hardwick said the class action would seek compensation for the impact the breach had on affected customers, the time they spent applying for new identification and other documents, as well as the stress and frustration caused by the theft of their private, sometimes sensitive, information.
"We're talking about up to 9.7 million Australians who were affected and the nature of the information is what concern is concerning here," Mr Hardwick said.
"Health information is something most people keep incredibly private and want kept between them, their doctors or health providers, and their insurer," Mr Hardwick said.
He said some information included previous drug and alcohol addictions and HIV diagnoses.
The lead applicant has asked not to be identified to protect his privacy.
He said he had trusted ahm because it was owned by Medibank.
"I feel really exposed and unsettled knowing personal information of mine is out there and there's nothing I can do about it," he said.
Medibank has been contacted for comment.
The class action is just one of many lodged in Australia over recent data breaches.
Slater and Gordon is also leading legal action against Optus over its 2022 data breach in which up to 10 million customers and former customers' personal information was compromised.
Gordon Legal and Hayden Stephens and Associates are jointly investigating the possibility of a class action over the Latitude data hack .
- X (formerly Twitter)
- Business, Economics and Finance
- Courts and Trials
- Cyber Crime
- Health Insurance
- Law, Crime and Justice
- Study Guides
- Homework Questions
Medibank Data Breach Case Study 1
- Information Systems
Case Study: Medibank Data Breach

Industry : Health Insurance Provider
About Medibak:
Medibank is a dedicated health company committed to creating “Better Health for Better Lives.” With a legacy spanning 47 years as one of Australia’s leading health insurers, Medibank and its subsidiary brand, ahm, passionately support millions of customers across the nation on their journey to managing their health and wellbeing.
How did the data breach occur?
Even though the details of the hackers’ entry into the system have not yet been made public, we presume that the Medibank data breach have been made possible by hackers using phishing to acquire internal credentials from a worker who had the authority to get into the insurance provider’s system. Ransomware, too, is frequently the attack method used by hackers to execute a data breach. The bulk of cyberattacks that we have seen over the years have ransomware infection as one of their primary objectives.
What was the impact of the data breach as a whole?
The effects on Medibank were severe, ranging from the loss of customer data from the past and present to an 18% decline in stock prices. Although Medibank wasn’t the only victim of ransomware in recent times, the impact was significant as it also tarnished the company’s reputation.
Hacking confirmation breakthrough on the news
There was an unexplained behaviour on the company’s network on October 13, 2022, which was followed by a warning from Medibank indicating that they had been looking into the abnormal activity and determining the source. But despite their efforts, they were unable to discover any signs of a breach. On October 19, however, a group of hackers called the company, claiming to have stolen 200 GB of private customer information. They then started discussing the terms under which they would hand over the data to the dark web. The business admitted the very next day that the hacker’s shocking claim to have stolen 200 GB worth of client data was not a lie.
What data was compromised?
The data breach’s severity was revealed on November 7th, along with the acknowledgement that 9.7 million active and prior consumers’ confidential data had been exposed. Following that, news stations reported that Medibank would not be paying the ransom demanded by the hacker group REvil. This ransomware group is supported by a Russian website, and they posted a file on the dark web called “Abortion” that described miscarriages, abortions, and pregnancy difficulties. In addition, the cybercriminal group released two files titled “Good List” and “Naughty List.” Even though the event was made public, all that is known about it is what was on the “Naughty List,” which contained private information on things like drug use, mental illness, HIV treatment, and eating disorders.
Law-enforcement taking action
The hackers put Medibank under siege by posting a file called “Abortion” on the dark web and threatening to post more private data if they weren’t paid 10 million US dollars. The Australian Federal Police (AFP) relaunched Operation Guardian, which was first introduced in response to the Optus security breach event, to address this Medibank data leak. The Australian Federal Police (AFP) and Interpol soon identified a link between the operation and the hacking collective REvil as part of their criminal probe.
Stock price dropped
Apart from the negative impact on their financial and reputational status after the compromise of 9.7 million records, Medibank also saw a sharp decline in their stock prices as the news of the hack into the company’s network became public. The stock price fell from AUD 3.51 to AUD 2.87, representing a reduction of 18% since October 19th.
What is the usual pattern of incidents like the Medibank Data Breach?
Similar to Medibank, data breaches have been frequently covered in recent news headlines, and we are all aware of the implications of subpar cybersecurity strategies. However, neither the general public nor the workforce is taught how data breaches happen or the extent of the long-term harm they might do.
After data is stolen, a demand is made by the hackers to the victim company with the threat that, if the ransom money is not paid, the information will be made public on the dark web or other shady places where the data may be obtained and used inappropriately. Therefore, in light of this, it is essential to exercise prudence and inform the general public as soon as possible.
How to prevent data breaches?
There is always an answer to every issue. Most data breaches follow a similar pattern that begins with human error and a lack of awareness, where the hacker breaches in and mirrors the system to access the important files. However, if we take care of our security by putting some fundamental habits and awareness into practice, we may be able to reduce the risk of being breached or hacked. Let’s discuss some easy habits we can develop to protect our privacy.
Enable Two-factor authentication
Similar to how you apply sunscreen after moisturizer to protect your skin from UV rays before stepping outside your home, two-factor authentication is an additional layer of protection that comes after creating a strong, unique password to safeguard your account. Its primary function is to authorize access to the account following OTP validation sent to the associated email address or phone number.
Use strong and unique passwords and keep changing them routinely
Being cautious is a good thing, but having a password that is very strong and changes frequently creates a strong defence wall against cyber hackers, making it difficult to impossible for them to decipher the code.
Be vigilant at all times
Knowledge is essential because it helps individuals prepare for the unexpected. Otherwise, how would they handle the situation when it arises? Showcase actual incidents as a lesson and train your staff to recognize a phishing scam and take immediate action. Along with awareness, the right tools are necessary. For example, EmailRemediator helps spread awareness of potential scams by displaying suspicious emails in other employees’ mailboxes. If a particular email server has been reported in multiple accounts, EmailRemediator sends a red alert to the entire organization, and the server will be immediately blocked.
Use reliable antivirus software
Keeping reliable anti-virus software that can reduce malware risks on your system is crucial in addition to keeping your cybersecurity up to date. By comparing a specific code set in the database, it can quickly identify and eliminate any viruses that may already be present in the system. The codes contain specific information, and the anti-virus software will treat them as malware if they are discovered to be similar to the codes of malware.
Never share your PII online
Your Social Security number, address, financial and medical records, and other personally identifiable information are all examples of PII. These are private details, and only necessary disclosures should be made. Sharing this information on the internet can make you vulnerable to identity theft, fraud, and other malicious activities. Along with protecting PII, avoiding data breaches necessitates maintaining the privacy of your business and your employees’ credentials.
Regularly backup your data
Keeping a backup of your private information is essential for protection against hardware failure, malware infection, and even natural catastrophes. If you always have a backup of your confidential data on hand, the chances of losing it are reduced.
Provide security training to employees and have firm security measures
It is crucial to train your workforce to spot phishing attempts and take appropriate legal action. Strong security measures and regular checks to ensure the procedure is being followed are essential.
Every time a data breach occurs, the victims suffer a great deal, but gradually, cyber security is improving as well to counteract sophisticated social engineering such as phishing, data leaks, ransomware, malware attacks, etc. Law enforcement is increasingly stern towards online fraudsters, whether it be a minor phishing attack or a ransom demand. The only strategy we have to combat situations like the Medibank data breach is to have a thorough grasp of cybersecurity, undergo appropriate training of our workforce and clients, and position the appropriate protection tools.

IMAGES
COMMENTS
Corporate Credential Theft: The Reason the Medibank Breach was Possible. The Medibank data breach was made possible by the theft of internal credentials believed to belong to an individual with privileged system access. Internal credential theft is one of the first objectives of almost every cyberattack. It hasn't yet been confirmed how the ...
A full timeline of the data breach. 13 October - Medibank notices some unusual activity on its networks. The affected networks are shut down. 14 October - the affected networks are restarted. Medibank releases a statement saying that there is "no evidence" that any customer data was accessed during the breach.
This week, in response to the Optus and Medibank breaches, the parliament passed legislation that can result in businesses being fined $50m for repeated or serious data breaches.
Medibank was hit by a cyber attack last week but at the time the company said there was no evidence that sensitive data had been accessed. On Wednesday, it issued a statement saying it received a ...
Three law firms have joined forces to launch a data breach legal case against health insurance company Medibank. This comes after the personal data of about 9.7 million customers was leaked by ...
This is how the negotiations unfolded. At 1.20pm on October 12, Medibank Private received a call from Australia's top cyber spy agency. It came with a message no Australian business wants to ...
In the wake of the Medibank breach, the cybersecurity minister, Clare O'Neil, warned of a new world "under relentless cyber-attack", while Australia's security agencies scrambled to manage ...
First published on Tue 25 Oct 2022 20.38 EDT. Medibank has revealed all of its 3.9 million customers have had their data exposed to a hacker, in a significant escalation of the cyber-attack on the ...
The following day the company confirmed the hackers had sent a sample of 100 records believed to have been taken from Medibank's system. As a result of the breach, Medibank halted trading on the ...
A Medibank branch in Sydney, Australia, on Oct. 26, 2022. Cyber criminals in Russia are behind a ransomware attack on one of Australia's largest private health insurers that's seen sensitive ...
Image: Casey Tonkin. Australian health insurer Medibank made a "rookie mistake" that led to one of the largest data breaches in our country's history, a cyber security expert has claimed in the wake of new details about the breach. In its half-yearly report, Medibank shared a brief outline of how the Russian-based attackers got access to ...
The cybercriminals claimed they published the data after Medibank refused to pay their $10 million ransom demand, which was later reduced to $9.7 million, or $1 per affected customer. Medibank ...
The local post was published on November 30: "Happy Cyber Security Day!!! Added folder full. Case closed." In less than a month, Medibank is the second Australian business to experience a significant data breach after the telecommunications giant Optus. On October 12th, David Koczkar, the chief executive of Medibank, got an internal ...
1 December 2022. The Office of the Australian Information Commissioner (OAIC) today commenced an investigation into the personal information handling practices of Medibank in relation to its notifiable data breach. This decision follows the OAIC's preliminary inquiries commenced into the matter in October. The OAIC's investigation will ...
Stolen data of Medibank customers has been released on the dark web The breach is having hidden financial and emotional costs, customers have said Some are demanding more answers as to how it ...
The data breach claims. For some time now we have been expecting data breach class actions, and in the aftermath of the Optus data breach incident, we noted the risks had increased.. The Optus and Medibank data breaches are now the subject of four class actions: 6 February 2023: Baker & McKenzie filed a consumer class action against Medibank in the Federal Court.
Last week Medibank announced costs associated with its breach, including upgrading IT systems, would reach up to $45 million over the second half of the year, and gave details for the first time ...
Ionut Arghire. November 7, 2022. Australian health insurer Medibank today confirmed that the data of 9.7 million customers was compromised in a recent cyberattack. The incident was identified on October 12, before threat actors could deploy file-encrypting ransomware, but not before they stole data from the company's systems.
This stolen data was placed into a zip file and extracted through two established backdoors. Medibank's security team allegedly detected suspicious activity at this point and shut down both back doors, but not before 200GB worth of customer data was stolen, 9.7 million Medibank customers were impacted by the breach. Compromised records include:
Law firm Slater and Gordon launches legal proceedings on behalf of nearly 10 million current and former Medibank customers caught up in a data breach. ... in Australia over recent data breaches.
Medibank Data Breach Description of the Incident One of the biggest cybersecurity events in Australian history, the Medibank data breach occurred when a hacker used credentials, they had stolen to gain access to Medibank's systems and remove sensitive information. Approximately 9.7 million customers' sensitive medical records and personal ...
Case Study: Medibank Data Breach . Industry: Health Insurance Provider. About Medibak: Medibank is a dedicated health company committed to creating "Better Health for Better Lives." With a legacy spanning 47 years as one of Australia's leading health insurers, Medibank and its subsidiary brand, ahm, passionately support millions of ...