Enterprise Risk Management Case Studies: Heroes and Zeros
By Andy Marker | April 7, 2021
- Share on Facebook
- Share on LinkedIn
Link copied
We’ve compiled more than 20 case studies of enterprise risk management programs that illustrate how companies can prevent significant losses yet take risks with more confidence.
Included on this page, you’ll find case studies and examples by industry , case studies of major risk scenarios (and company responses), and examples of ERM successes and failures .

Enterprise Risk Management Examples and Case Studies
With enterprise risk management (ERM) , companies assess potential risks that could derail strategic objectives and implement measures to minimize or avoid those risks. You can analyze examples (or case studies) of enterprise risk management to better understand the concept and how to properly execute it.
The collection of examples and case studies on this page illustrates common risk management scenarios by industry, principle, and degree of success. For a basic overview of enterprise risk management, including major types of risks, how to develop policies, and how to identify key risk indicators (KRIs), read “ Enterprise Risk Management 101: Programs, Frameworks, and Advice from Experts .”
Enterprise Risk Management Framework Examples
An enterprise risk management framework is a system by which you assess and mitigate potential risks. The framework varies by industry, but most include roles and responsibilities, a methodology for risk identification, a risk appetite statement, risk prioritization, mitigation strategies, and monitoring and reporting.
To learn more about enterprise risk management and find examples of different frameworks, read our “ Ultimate Guide to Enterprise Risk Management .”
Enterprise Risk Management Examples and Case Studies by Industry
Though every firm faces unique risks, those in the same industry often share similar risks. By understanding industry-wide common risks, you can create and implement response plans that offer your firm a competitive advantage.
Enterprise Risk Management Example in Banking
Toronto-headquartered TD Bank organizes its risk management around two pillars: a risk management framework and risk appetite statement. The enterprise risk framework defines the risks the bank faces and lays out risk management practices to identify, assess, and control risk. The risk appetite statement outlines the bank’s willingness to take on risk to achieve its growth objectives. Both pillars are overseen by the risk committee of the company’s board of directors.
Risk management frameworks were an important part of the International Organization for Standardization’s 31000 standard when it was first written in 2009 and have been updated since then. The standards provide universal guidelines for risk management programs.
Risk management frameworks also resulted from the efforts of the Committee of Sponsoring Organizations of the Treadway Commission (COSO). The group was formed to fight corporate fraud and included risk management as a dimension.
Once TD completes the ERM framework, the bank moves onto the risk appetite statement.
The bank, which built a large U.S. presence through major acquisitions, determined that it will only take on risks that meet the following three criteria:
- The risk fits the company’s strategy, and TD can understand and manage those risks.
- The risk does not render the bank vulnerable to significant loss from a single risk.
- The risk does not expose the company to potential harm to its brand and reputation.
Some of the major risks the bank faces include strategic risk, credit risk, market risk, liquidity risk, operational risk, insurance risk, capital adequacy risk, regulator risk, and reputation risk. Managers detail these categories in a risk inventory.
The risk framework and appetite statement, which are tracked on a dashboard against metrics such as capital adequacy and credit risk, are reviewed annually.
TD uses a three lines of defense (3LOD) strategy, an approach widely favored by ERM experts, to guard against risk. The three lines are as follows:
- A business unit and corporate policies that create controls, as well as manage and monitor risk
- Standards and governance that provide oversight and review of risks and compliance with the risk appetite and framework
- Internal audits that provide independent checks and verification that risk-management procedures are effective
Enterprise Risk Management Example in Pharmaceuticals
Drug companies’ risks include threats around product quality and safety, regulatory action, and consumer trust. To avoid these risks, ERM experts emphasize the importance of making sure that strategic goals do not conflict.
For Britain’s GlaxoSmithKline, such a conflict led to a breakdown in risk management, among other issues. In the early 2000s, the company was striving to increase sales and profitability while also ensuring safe and effective medicines. One risk the company faced was a failure to meet current good manufacturing practices (CGMP) at its plant in Cidra, Puerto Rico.
CGMP includes implementing oversight and controls of manufacturing, as well as managing the risk and confirming the safety of raw materials and finished drug products. Noncompliance with CGMP can result in escalating consequences, ranging from warnings to recalls to criminal prosecution.
GSK’s unit pleaded guilty and paid $750 million in 2010 to resolve U.S. charges related to drugs made at the Cidra plant, which the company later closed. A fired GSK quality manager alerted regulators and filed a whistleblower lawsuit in 2004. In announcing the consent decree, the U.S. Department of Justice said the plant had a history of bacterial contamination and multiple drugs created there in the early 2000s violated safety standards.
According to the whistleblower, GSK’s ERM process failed in several respects to act on signs of non-compliance with CGMP. The company received warning letters from the U.S. Food and Drug Administration in 2001 about the plant’s practices, but did not resolve the issues.
Additionally, the company didn’t act on the quality manager’s compliance report, which advised GSK to close the plant for two weeks to fix the problems and notify the FDA. According to court filings, plant staff merely skimmed rejected products and sold them on the black market. They also scraped by hand the inside of an antibiotic tank to get more product and, in so doing, introduced bacteria into the product.
Enterprise Risk Management Example in Consumer Packaged Goods
Mars Inc., an international candy and food company, developed an ERM process. The company piloted and deployed the initiative through workshops with geographic, product, and functional teams from 2003 to 2012.
Driven by a desire to frame risk as an opportunity and to work within the company’s decentralized structure, Mars created a process that asked participants to identify potential risks and vote on which had the highest probability. The teams listed risk mitigation steps, then ranked and color-coded them according to probability of success.
Larry Warner, a Mars risk officer at the time, illustrated this process in a case study . An initiative to increase direct-to-consumer shipments by 12 percent was colored green, indicating a 75 percent or greater probability of achievement. The initiative to bring a new plant online by the end of Q3 was coded red, meaning less than a 50 percent probability of success.
The company’s results were hurt by a surprise at an operating unit that resulted from a so-coded red risk identified in a unit workshop. Executives had agreed that some red risk profile was to be expected, but they decided that when a unit encountered a red issue, it must be communicated upward when first identified. This became a rule.
This process led to the creation of an ERM dashboard that listed initiatives in priority order, with the profile of each risk faced in the quarter, the risk profile trend, and a comment column for a year-end view.
According to Warner, the key factors of success for ERM at Mars are as follows:
- The initiative focused on achieving operational and strategic objectives rather than compliance, which refers to adhering to established rules and regulations.
- The program evolved, often based on requests from business units, and incorporated continuous improvement.
- The ERM team did not overpromise. It set realistic objectives.
- The ERM team periodically surveyed business units, management teams, and board advisers.
Enterprise Risk Management Example in Retail
Walmart is the world’s biggest retailer. As such, the company understands that its risk makeup is complex, given the geographic spread of its operations and its large number of stores, vast supply chain, and high profile as an employer and buyer of goods.
In the 1990s, the company sought a simplified strategy for assessing risk and created an enterprise risk management plan with five steps founded on these four questions:
- What are the risks?
- What are we going to do about them?
- How will we know if we are raising or decreasing risk?
- How will we show shareholder value?
The process follows these five steps:
- Risk Identification: Senior Walmart leaders meet in workshops to identify risks, which are then plotted on a graph of probability vs. impact. Doing so helps to prioritize the biggest risks. The executives then look at seven risk categories (both internal and external): legal/regulatory, political, business environment, strategic, operational, financial, and integrity. Many ERM pros use risk registers to evaluate and determine the priority of risks. You can download templates that help correlate risk probability and potential impact in “ Free Risk Register Templates .”
- Risk Mitigation: Teams that include operational staff in the relevant area meet. They use existing inventory procedures to address the risks and determine if the procedures are effective.
- Action Planning: A project team identifies and implements next steps over the several months to follow.
- Performance Metrics: The group develops metrics to measure the impact of the changes. They also look at trends of actual performance compared to goal over time.
- Return on Investment and Shareholder Value: In this step, the group assesses the changes’ impact on sales and expenses to determine if the moves improved shareholder value and ROI.
To develop your own risk management planning, you can download a customizable template in “ Risk Management Plan Templates .”
Enterprise Risk Management Example in Agriculture
United Grain Growers (UGG), a Canadian grain distributor that now is part of Glencore Ltd., was hailed as an ERM innovator and became the subject of business school case studies for its enterprise risk management program. This initiative addressed the risks associated with weather for its business. Crop volume drove UGG’s revenue and profits.
In the late 1990s, UGG identified its major unaddressed risks. Using almost a century of data, risk analysts found that extreme weather events occurred 10 times as frequently as previously believed. The company worked with its insurance broker and the Swiss Re Group on a solution that added grain-volume risk (resulting from weather fluctuations) to its other insured risks, such as property and liability, in an integrated program.
The result was insurance that protected grain-handling earnings, which comprised half of UGG’s gross profits. The greater financial stability significantly enhanced the firm’s ability to achieve its strategic objectives.
Since then, the number and types of instruments to manage weather-related risks has multiplied rapidly. For example, over-the-counter derivatives, such as futures and options, began trading in 1997. The Chicago Mercantile Exchange now offers weather futures contracts on 12 U.S. and international cities.
Weather derivatives are linked to climate factors such as rainfall or temperature, and they hedge different kinds of risks than do insurance. These risks are much more common (e.g., a cooler-than-normal summer) than the earthquakes and floods that insurance typically covers. And the holders of derivatives do not have to incur any damage to collect on them.
These weather-linked instruments have found a wider audience than anticipated, including retailers that worry about freak storms decimating Christmas sales, amusement park operators fearing rainy summers will keep crowds away, and energy companies needing to hedge demand for heating and cooling.
This area of ERM continues to evolve because weather and crop insurance are not enough to address all the risks that agriculture faces. Arbol, Inc. estimates that more than $1 trillion of agricultural risk is uninsured. As such, it is launching a blockchain-based platform that offers contracts (customized by location and risk parameters) with payouts based on weather data. These contracts can cover risks associated with niche crops and small growing areas.
Enterprise Risk Management Example in Insurance
Switzerland’s Zurich Insurance Group understands that risk is inherent for insurers and seeks to practice disciplined risk-taking, within a predetermined risk tolerance.
The global insurer’s enterprise risk management framework aims to protect capital, liquidity, earnings, and reputation. Governance serves as the basis for risk management, and the framework lays out responsibilities for taking, managing, monitoring, and reporting risks.
The company uses a proprietary process called Total Risk Profiling (TRP) to monitor internal and external risks to its strategy and financial plan. TRP assesses risk on the basis of severity and probability, and helps define and implement mitigating moves.
Zurich’s risk appetite sets parameters for its tolerance within the goal of maintaining enough capital to achieve an AA rating from rating agencies. For this, the company uses its own Zurich economic capital model, referred to as Z-ECM. The model quantifies risk tolerance with a metric that assesses risk profile vs. risk tolerance.
To maintain the AA rating, the company aims to hold capital between 100 and 120 percent of capital at risk. Above 140 percent is considered overcapitalized (therefore at risk of throttling growth), and under 90 percent is below risk tolerance (meaning the risk is too high). On either side of 100 to 120 percent (90 to 100 percent and 120 to 140 percent), the insurer considers taking mitigating action.
Zurich’s assessment of risk and the nature of those risks play a major role in determining how much capital regulators require the business to hold. A popular tool to assess risk is the risk matrix, and you can find a variety of templates in “ Free, Customizable Risk Matrix Templates .”
In 2020, Zurich found that its biggest exposures were market risk, such as falling asset valuations and interest-rate risk; insurance risk, such as big payouts for covered customer losses, which it hedges through diversification and reinsurance; credit risk in assets it holds and receivables; and operational risks, such as internal process failures and external fraud.
Enterprise Risk Management Example in Technology
Financial software maker Intuit has strengthened its enterprise risk management through evolution, according to a case study by former Chief Risk Officer Janet Nasburg.
The program is founded on the following five core principles:
- Use a common risk framework across the enterprise.
- Assess risks on an ongoing basis.
- Focus on the most important risks.
- Clearly define accountability for risk management.
- Commit to continuous improvement of performance measurement and monitoring.
ERM programs grow according to a maturity model, and as capability rises, the shareholder value from risk management becomes more visible and important.
The maturity phases include the following:
- Ad hoc risk management addresses a specific problem when it arises.
- Targeted or initial risk management approaches risks with multiple understandings of what constitutes risk and management occurs in silos.
- Integrated or repeatable risk management puts in place an organization-wide framework for risk assessment and response.
- Intelligent or managed risk management coordinates risk management across the business, using common tools.
- Risk leadership incorporates risk management into strategic decision-making.
Intuit emphasizes using key risk indicators (KRIs) to understand risks, along with key performance indicators (KPIs) to gauge the effectiveness of risk management.
Early in its ERM journey, Intuit measured performance on risk management process participation and risk assessment impact. For participation, the targeted rate was 80 percent of executive management and business-line leaders. This helped benchmark risk awareness and current risk management, at a time when ERM at the company was not mature.
Conduct an annual risk assessment at corporate and business-line levels to plot risks, so the most likely and most impactful risks are graphed in the upper-right quadrant. Doing so focuses attention on these risks and helps business leaders understand the risk’s impact on performance toward strategic objectives.
In the company’s second phase of ERM, Intuit turned its attention to building risk management capacity and sought to ensure that risk management activities addressed the most important risks. The company evaluated performance using color-coded status symbols (red, yellow, green) to indicate risk trend and progress on risk mitigation measures.
In its third phase, Intuit moved to actively monitoring the most important risks and ensuring that leaders modified their strategies to manage risks and take advantage of opportunities. An executive dashboard uses KRIs, KPIs, an overall risk rating, and red-yellow-green coding. The board of directors regularly reviews this dashboard.
Over this evolution, the company has moved from narrow, tactical risk management to holistic, strategic, and long-term ERM.
Enterprise Risk Management Case Studies by Principle
ERM veterans agree that in addition to KPIs and KRIs, other principles are equally important to follow. Below, you’ll find examples of enterprise risk management programs by principles.
ERM Principle #1: Make Sure Your Program Aligns with Your Values
Raytheon Case Study U.S. defense contractor Raytheon states that its highest priority is delivering on its commitment to provide ethical business practices and abide by anti-corruption laws.
Raytheon backs up this statement through its ERM program. Among other measures, the company performs an annual risk assessment for each function, including the anti-corruption group under the Chief Ethics and Compliance Officer. In addition, Raytheon asks 70 of its sites to perform an anti-corruption self-assessment each year to identify gaps and risks. From there, a compliance team tracks improvement actions.
Every quarter, the company surveys 600 staff members who may face higher anti-corruption risks, such as the potential for bribes. The survey asks them to report any potential issues in the past quarter.
Also on a quarterly basis, the finance and internal controls teams review higher-risk profile payments, such as donations and gratuities to confirm accuracy and compliance. Oversight and compliance teams add other checks, and they update a risk-based audit plan continuously.
ERM Principle #2: Embrace Diversity to Reduce Risk
State Street Global Advisors Case Study In 2016, the asset management firm State Street Global Advisors introduced measures to increase gender diversity in its leadership as a way of reducing portfolio risk, among other goals.
The company relied on research that showed that companies with more women senior managers had a better return on equity, reduced volatility, and fewer governance problems such as corruption and fraud.
Among the initiatives was a campaign to influence companies where State Street had invested, in order to increase female membership on their boards. State Street also developed an investment product that tracks the performance of companies with the highest level of senior female leadership relative to peers in their sector.
In 2020, the company announced some of the results of its effort. Among the 1,384 companies targeted by the firm, 681 added at least one female director.
ERM Principle #3: Do Not Overlook Resource Risks
Infosys Case Study India-based technology consulting company Infosys, which employees more than 240,000 people, has long recognized the risk of water shortages to its operations.
India’s rapidly growing population and development has increased the risk of water scarcity. A 2020 report by the World Wide Fund for Nature said 30 cities in India faced the risk of severe water scarcity over the next three decades.
Infosys has dozens of facilities in India and considers water to be a significant short-term risk. At its campuses, the company uses the water for cooking, drinking, cleaning, restrooms, landscaping, and cooling. Water shortages could halt Infosys operations and prevent it from completing customer projects and reaching its performance objectives.
In an enterprise risk assessment example, Infosys’ ERM team conducts corporate water-risk assessments while sustainability teams produce detailed water-risk assessments for individual locations, according to a report by the World Business Council for Sustainable Development .
The company uses the COSO ERM framework to respond to the risks and decide whether to accept, avoid, reduce, or share these risks. The company uses root-cause analysis (which focuses on identifying underlying causes rather than symptoms) and the site assessments to plan steps to reduce risks.
Infosys has implemented various water conservation measures, such as water-efficient fixtures and water recycling, rainwater collection and use, recharging aquifers, underground reservoirs to hold five days of water supply at locations, and smart-meter usage monitoring. Infosys’ ERM team tracks metrics for per-capita water consumption, along with rainfall data, availability and cost of water by tanker trucks, and water usage from external suppliers.
In the 2020 fiscal year, the company reported a nearly 64 percent drop in per-capita water consumption by its workforce from the 2008 fiscal year.
The business advantages of this risk management include an ability to open locations where water shortages may preclude competitors, and being able to maintain operations during water scarcity, protecting profitability.
ERM Principle #4: Fight Silos for Stronger Enterprise Risk Management
U.S. Government Case Study The terrorist attacks of September 11, 2001, revealed that the U.S. government’s then-current approach to managing intelligence was not adequate to address the threats — and, by extension, so was the government’s risk management procedure. Since the Cold War, sensitive information had been managed on a “need to know” basis that resulted in data silos.
In the case of 9/11, this meant that different parts of the government knew some relevant intelligence that could have helped prevent the attacks. But no one had the opportunity to put the information together and see the whole picture. A congressional commission determined there were 10 lost operational opportunities to derail the plot. Silos existed between law enforcement and intelligence, as well as between and within agencies.
After the attacks, the government moved toward greater information sharing and collaboration. Based on a task force’s recommendations, data moved from a centralized network to a distributed model, and social networking tools now allow colleagues throughout the government to connect. Staff began working across agency lines more often.
Enterprise Risk Management Examples by Scenario
While some scenarios are too unlikely to receive high-priority status, low-probability risks are still worth running through the ERM process. Robust risk management creates a culture and response capacity that better positions a company to deal with a crisis.
In the following enterprise risk examples, you will find scenarios and details of how organizations manage the risks they face.
Scenario: ERM and the Global Pandemic While most businesses do not have the resources to do in-depth ERM planning for the rare occurrence of a global pandemic, companies with a risk-aware culture will be at an advantage if a pandemic does hit.
These businesses already have processes in place to escalate trouble signs for immediate attention and an ERM team or leader monitoring the threat environment. A strong ERM function gives clear and effective guidance that helps the company respond.
A report by Vodafone found that companies identified as “future ready” fared better in the COVID-19 pandemic. The attributes of future-ready businesses have a lot in common with those of companies that excel at ERM. These include viewing change as an opportunity; having detailed business strategies that are documented, funded, and measured; working to understand the forces that shape their environments; having roadmaps in place for technological transformation; and being able to react more quickly than competitors.
Only about 20 percent of companies in the Vodafone study met the definition of “future ready.” But 54 percent of these firms had a fully developed and tested business continuity plan, compared to 30 percent of all businesses. And 82 percent felt their continuity plans worked well during the COVID-19 crisis. Nearly 50 percent of all businesses reported decreased profits, while 30 percent of future-ready organizations saw profits rise.
Scenario: ERM and the Economic Crisis The 2008 economic crisis in the United States resulted from the domino effect of rising interest rates, a collapse in housing prices, and a dramatic increase in foreclosures among mortgage borrowers with poor creditworthiness. This led to bank failures, a credit crunch, and layoffs, and the U.S. government had to rescue banks and other financial institutions to stabilize the financial system.
Some commentators said these events revealed the shortcomings of ERM because it did not prevent the banks’ mistakes or collapse. But Sim Segal, an ERM consultant and director of Columbia University’s ERM master’s degree program, analyzed how banks performed on 10 key ERM criteria.
Segal says a risk-management program that incorporates all 10 criteria has these characteristics:
- Risk management has an enterprise-wide scope.
- The program includes all risk categories: financial, operational, and strategic.
- The focus is on the most important risks, not all possible risks.
- Risk management is integrated across risk types.
- Aggregated metrics show risk exposure and appetite across the enterprise.
- Risk management incorporates decision-making, not just reporting.
- The effort balances risk and return management.
- There is a process for disclosure of risk.
- The program measures risk in terms of potential impact on company value.
- The focus of risk management is on the primary stakeholder, such as shareholders, rather than regulators or rating agencies.
In his book Corporate Value of Enterprise Risk Management , Segal concluded that most banks did not actually use ERM practices, which contributed to the financial crisis. He scored banks as failing on nine of the 10 criteria, only giving them a passing grade for focusing on the most important risks.
Scenario: ERM and Technology Risk The story of retailer Target’s failed expansion to Canada, where it shut down 133 loss-making stores in 2015, has been well documented. But one dimension that analysts have sometimes overlooked was Target’s handling of technology risk.
A case study by Canadian Business magazine traced some of the biggest issues to software and data-quality problems that dramatically undermined the Canadian launch.
As with other forms of ERM, technology risk management requires companies to ask what could go wrong, what the consequences would be, how they might prevent the risks, and how they should deal with the consequences.
But with its technology plan for Canada, Target did not heed risk warning signs.
In the United States, Target had custom systems for ordering products from vendors, processing items at warehouses, and distributing merchandise to stores quickly. But that software would need customization to work with the Canadian dollar, metric system, and French-language characters.
Target decided to go with new ERP software on an aggressive two-year timeline. As Target began ordering products for the Canadian stores in 2012, problems arose. Some items did not fit into shipping containers or on store shelves, and information needed for customs agents to clear imported items was not correct in Target's system.
Target found that its supply chain software data was full of errors. Product dimensions were in inches, not centimeters; height and width measurements were mixed up. An internal investigation showed that only about 30 percent of the data was accurate.
In an attempt to fix these errors, Target merchandisers spent a week double-checking with vendors up to 80 data points for each of the retailer’s 75,000 products. They discovered that the dummy data entered into the software during setup had not been altered. To make any corrections, employees had to send the new information to an office in India where staff would enter it into the system.
As the launch approached, the technology errors left the company vulnerable to stockouts, few people understood how the system worked, and the point-of-sale checkout system did not function correctly. Soon after stores opened in 2013, consumers began complaining about empty shelves. Meanwhile, Target Canada distribution centers overflowed due to excess ordering based on poor data fed into forecasting software.
The rushed launch compounded problems because it did not allow the company enough time to find solutions or alternative technology. While the retailer fixed some issues by the end of 2014, it was too late. Target Canada filed for bankruptcy protection in early 2015.
Scenario: ERM and Cybersecurity System hacks and data theft are major worries for companies. But as a relatively new field, cyber-risk management faces unique hurdles.
For example, risk managers and information security officers have difficulty quantifying the likelihood and business impact of a cybersecurity attack. The rise of cloud-based software exposes companies to third-party risks that make these projections even more difficult to calculate.
As the field evolves, risk managers say it’s important for IT security officers to look beyond technical issues, such as the need to patch a vulnerability, and instead look more broadly at business impacts to make a cost benefit analysis of risk mitigation. Frameworks such as the Risk Management Framework for Information Systems and Organizations by the National Institute of Standards and Technology can help.
Health insurer Aetna considers cybersecurity threats as a part of operational risk within its ERM framework and calculates a daily risk score, adjusted with changes in the cyberthreat landscape.
Aetna studies threats from external actors by working through information sharing and analysis centers for the financial services and health industries. Aetna staff reverse-engineers malware to determine controls. The company says this type of activity helps ensure the resiliency of its business processes and greatly improves its ability to help protect member information.
For internal threats, Aetna uses models that compare current user behavior to past behavior and identify anomalies. (The company says it was the first organization to do this at scale across the enterprise.) Aetna gives staff permissions to networks and data based on what they need to perform their job. This segmentation restricts access to raw data and strengthens governance.
Another risk initiative scans outgoing employee emails for code patterns, such as credit card or Social Security numbers. The system flags the email, and a security officer assesses it before the email is released.
Examples of Poor Enterprise Risk Management
Case studies of failed enterprise risk management often highlight mistakes that managers could and should have spotted — and corrected — before a full-blown crisis erupted. The focus of these examples is often on determining why that did not happen.
ERM Case Study: General Motors
In 2014, General Motors recalled the first of what would become 29 million cars due to faulty ignition switches and paid compensation for 124 related deaths. GM knew of the problem for at least 10 years but did not act, the automaker later acknowledged. The company entered a deferred prosecution agreement and paid a $900 million penalty.
Pointing to the length of time the company failed to disclose the safety problem, ERM specialists say it shows the problem did not reside with a single department. “Rather, it reflects a failure to properly manage risk,” wrote Steve Minsky, a writer on ERM and CEO of an ERM software company, in Risk Management magazine.
“ERM is designed to keep all parties across the organization, from the front lines to the board to regulators, apprised of these kinds of problems as they become evident. Unfortunately, GM failed to implement such a program, ultimately leading to a tragic and costly scandal,” Minsky said.
Also in the auto sector, an enterprise risk management case study of Toyota looked at its problems with unintended acceleration of vehicles from 2002 to 2009. Several studies, including a case study by Carnegie Mellon University Professor Phil Koopman , blamed poor software design and company culture. A whistleblower later revealed a coverup by Toyota. The company paid more than $2.5 billion in fines and settlements.
ERM Case Study: Lululemon
In 2013, following customer complaints that its black yoga pants were too sheer, the athletic apparel maker recalled 17 percent of its inventory at a cost of $67 million. The company had previously identified risks related to fabric supply and quality. The CEO said the issue was inadequate testing.
Analysts raised concerns about the company’s controls, including oversight of factories and product quality. A case study by Stanford University professors noted that Lululemon’s episode illustrated a common disconnect between identifying risks and being prepared to manage them when they materialize. Lululemon’s reporting and analysis of risks was also inadequate, especially as related to social media. In addition, the case study highlighted the need for a system to escalate risk-related issues to the board.
ERM Case Study: Kodak
Once an iconic brand, the photo film company failed for decades to act on the threat that digital photography posed to its business and eventually filed for bankruptcy in 2012. The company’s own research in 1981 found that digital photos could ultimately replace Kodak’s film technology and estimated it had 10 years to prepare.
Unfortunately, Kodak did not prepare and stayed locked into the film paradigm. The board reinforced this course when in 1989 it chose as CEO a candidate who came from the film business over an executive interested in digital technology.
Had the company acknowledged the risks and employed ERM strategies, it might have pursued a variety of strategies to remain successful. The company’s rival, Fuji Film, took the money it made from film and invested in new initiatives, some of which paid off. Kodak, on the other hand, kept investing in the old core business.
Case Studies of Successful Enterprise Risk Management
Successful enterprise risk management usually requires strong performance in multiple dimensions, and is therefore more likely to occur in organizations where ERM has matured. The following examples of enterprise risk management can be considered success stories.
ERM Case Study: Statoil
A major global oil producer, Statoil of Norway stands out for the way it practices ERM by looking at both downside risk and upside potential. Taking risks is vital in a business that depends on finding new oil reserves.
According to a case study, the company developed its own framework founded on two basic goals: creating value and avoiding accidents.
The company aims to understand risks thoroughly, and unlike many ERM programs, Statoil maps risks on both the downside and upside. It graphs risk on probability vs. impact on pre-tax earnings, and it examines each risk from both positive and negative perspectives.
For example, the case study cites a risk that the company assessed as having a 5 percent probability of a somewhat better-than-expected outcome but a 10 percent probability of a significant loss relative to forecast. In this case, the downside risk was greater than the upside potential.
ERM Case Study: Lego
The Danish toy maker’s ERM evolved over the following four phases, according to a case study by one of the chief architects of its program:
- Traditional management of financial, operational, and other risks. Strategic risk management joined the ERM program in 2006.
- The company added Monte Carlo simulations in 2008 to model financial performance volatility so that budgeting and financial processes could incorporate risk management. The technique is used in budget simulations, to assess risk in its credit portfolio, and to consolidate risk exposure.
- Active risk and opportunity planning is part of making a business case for new projects before final decisions.
- The company prepares for uncertainty so that long-term strategies remain relevant and resilient under different scenarios.
As part of its scenario modeling, Lego developed its PAPA (park, adapt, prepare, act) model.
- Park: The company parks risks that occur slowly and have a low probability of happening, meaning it does not forget nor actively deal with them.
- Adapt: This response is for risks that evolve slowly and are certain or highly probable to occur. For example, a risk in this category is the changing nature of play and the evolution of buying power in different parts of the world. In this phase, the company adjusts, monitors the trend, and follows developments.
- Prepare: This category includes risks that have a low probability of occurring — but when they do, they emerge rapidly. These risks go into the ERM risk database with contingency plans, early warning indicators, and mitigation measures in place.
- Act: These are high-probability, fast-moving risks that must be acted upon to maintain strategy. For example, developments around connectivity, mobile devices, and online activity are in this category because of the rapid pace of change and the influence on the way children play.
Lego views risk management as a way to better equip itself to take risks than its competitors. In the case study, the writer likens this approach to the need for the fastest race cars to have the best brakes and steering to achieve top speeds.
ERM Case Study: University of California
The University of California, one of the biggest U.S. public university systems, introduced a new view of risk to its workforce when it implemented enterprise risk management in 2005. Previously, the function was merely seen as a compliance requirement.
ERM became a way to support the university’s mission of education and research, drawing on collaboration of the system’s employees across departments. “Our philosophy is, ‘Everyone is a risk manager,’” Erike Young, deputy director of ERM told Treasury and Risk magazine. “Anyone who’s in a management position technically manages some type of risk.”
The university faces a diverse set of risks, including cybersecurity, hospital liability, reduced government financial support, and earthquakes.
The ERM department had to overhaul systems to create a unified view of risk because its information and processes were not linked. Software enabled both an organizational picture of risk and highly detailed drilldowns on individual risks. Risk managers also developed tools for risk assessment, risk ranking, and risk modeling.
Better risk management has provided more than $100 million in annual cost savings and nearly $500 million in cost avoidance, according to UC officials.
UC drives ERM with risk management departments at each of its 10 locations and leverages university subject matter experts to form multidisciplinary workgroups that develop process improvements.
APQC, a standards quality organization, recognized UC as a top global ERM practice organization, and the university system has won other awards. The university says in 2010 it was the first nonfinancial organization to win credit-rating agency recognition of its ERM program.
Examples of How Technology Is Transforming Enterprise Risk Management
Business intelligence software has propelled major progress in enterprise risk management because the technology enables risk managers to bring their information together, analyze it, and forecast how risk scenarios would impact their business.
ERM organizations are using computing and data-handling advancements such as blockchain for new innovations in strengthening risk management. Following are case studies of a few examples.
ERM Case Study: Bank of New York Mellon
In 2021, the bank joined with Google Cloud to use machine learning and artificial intelligence to predict and reduce the risk that transactions in the $22 trillion U.S. Treasury market will fail to settle. Settlement failure means a buyer and seller do not exchange cash and securities by the close of business on the scheduled date.
The party that fails to settle is assessed a daily financial penalty, and a high level of settlement failures can indicate market liquidity problems and rising risk. BNY says that, on average, about 2 percent of transactions fail to settle.
The bank trained models with millions of trades to consider every factor that could result in settlement failure. The service uses market-wide intraday trading metrics, trading velocity, scarcity indicators, volume, the number of trades settled per hour, seasonality, issuance patterns, and other signals.
The bank said it predicts about 40 percent of settlement failures with 90 percent accuracy. But it also cautioned against overconfidence in the technology as the model continues to improve.
AI-driven forecasting reduces risk for BNY clients in the Treasury market and saves costs. For example, a predictive view of settlement risks helps bond dealers more accurately manage their liquidity buffers, avoid penalties, optimize their funding sources, and offset the risks of failed settlements. In the long run, such forecasting tools could improve the health of the financial market.
ERM Case Study: PwC
Consulting company PwC has leveraged a vast information storehouse known as a data lake to help its customers manage risk from suppliers.
A data lake stores both structured or unstructured information, meaning data in highly organized, standardized formats as well as unstandardized data. This means that everything from raw audio to credit card numbers can live in a data lake.
Using techniques pioneered in national security, PwC built a risk data lake that integrates information from client companies, public databases, user devices, and industry sources. Algorithms find patterns that can signify unidentified risks.
One of PwC’s first uses of this data lake was a program to help companies uncover risks from their vendors and suppliers. Companies can violate laws, harm their reputations, suffer fraud, and risk their proprietary information by doing business with the wrong vendor.
Today’s complex global supply chains mean companies may be several degrees removed from the source of this risk, which makes it hard to spot and mitigate. For example, a product made with outlawed child labor could be traded through several intermediaries before it reaches a retailer.
PwC’s service helps companies recognize risk beyond their primary vendors and continue to monitor that risk over time as more information enters the data lake.
ERM Case Study: Financial Services
As analytics have become a pillar of forecasting and risk management for banks and other financial institutions, a new risk has emerged: model risk . This refers to the risk that machine-learning models will lead users to an unreliable understanding of risk or have unintended consequences.
For example, a 6 percent drop in the value of the British pound over the course of a few minutes in 2016 stemmed from currency trading algorithms that spiralled into a negative loop. A Twitter-reading program began an automated selling of the pound after comments by a French official, and other selling algorithms kicked in once the currency dropped below a certain level.
U.S. banking regulators are so concerned about model risk that the Federal Reserve set up a model validation council in 2012 to assess the models that banks use in running risk simulations for capital adequacy requirements. Regulators in Europe and elsewhere also require model validation.
A form of managing risk from a risk-management tool, model validation is an effort to reduce risk from machine learning. The technology-driven rise in modeling capacity has caused such models to proliferate, and banks can use hundreds of models to assess different risks.
Model risk management can reduce rising costs for modeling by an estimated 20 to 30 percent by building a validation workflow, prioritizing models that are most important to business decisions, and implementing automation for testing and other tasks, according to McKinsey.
Streamline Your Enterprise Risk Management Efforts with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Discover why over 90% of Fortune 100 companies trust Smartsheet to get work done.
- Browse All Articles
- Newsletter Sign-Up
RiskandUncertainty →
No results found in working knowledge.
- Were any results found in one of the other content buckets on the left?
- Try removing some search filters.
- Use different search filters.
- Harvard Business School →
- Faculty & Research →
- July 2008 (Revised January 2012)
- HBS Case Collection
Enterprise Risk Management at Hydro One (A)
- Format: Print
- | Pages: 22
More from the Author
- Winter 2015
- Journal of Applied Corporate Finance
When One Size Doesn't Fit All: Evolving Directions in the Research and Practice of Enterprise Risk Management
- August 2014
- Faculty Research
Enterprise Risk Management at Hydro One (B): How Risky are Smart Meters?
Learning from the kursk submarine rescue failure: the case for pluralistic risk management.
- When One Size Doesn't Fit All: Evolving Directions in the Research and Practice of Enterprise Risk Management By: Anette Mikes and Robert S. Kaplan
- Enterprise Risk Management at Hydro One (B): How Risky are Smart Meters? By: Anette Mikes and Amram Migdal
- Learning from the Kursk Submarine Rescue Failure: the Case for Pluralistic Risk Management By: Anette Mikes and Amram Migdal

- Predict! Software Suite
- Training and Coaching
- Predict! Risk Controller
- Rapid Deployment
- Predict! Risk Analyser
- Predict! Risk Reporter
- Predict! Risk Visualiser
- Predict! Cloud Hosting
- BOOK A DEMO
- Risk Vision
- Win Proposals with Risk Analysis
- Case Studies
- Video Gallery
- White Papers
- Upcoming Events
- Past Events

Fehmarnbelt case study
. . . . . learn more

Lend Lease case study

ASC case study

Tornado IPT case study

LLW Repository case study

OHL case study

Babcock case study

HUMS case study

UK Chinook case study
- EMEA: +44 (0) 1865 987 466
- Americas: +1 (0) 437 269 0697
- APAC: +61 499 520 456

Subscribe for Updates
Copyright © 2024 risk decisions. All rights reserved.
- Privacy Policy
- Cookie Policy
- Terms and Conditions
- Company Registration No: 01878114
Powered by The Communications Group
- How it works
- Case studies
13 case studies on how risk managers are assessing their risk culture
Continuing on from last week's post, There’s no such thing as risk culture, or is there? , this is the third in a series of blogs in which we are summarising key insights gained from about 50 risk managers and CROs interviewed between December 2019 and May 2020.
There are various techniques and different mindsets on how to assess and measure risk culture. We round-up the very best case studies, tools and templates used by risk managers around the world.
To survey or not to survey?
If you start from a base of assuming you need a survey (or perhaps you have an executive or board who want one), then you are faced with two main choices:
- Include a number of questions in a larger employee engagement/culture survey, probably being run by HR (as one of our Member organisations did, only to discover the results didn’t align with their anecdotal feedback and experiences)
- Conduct a dedicated risk culture survey, which might later be re-run as a benchmark (as one former CRO at an international airline did upon joining the organisation).
However, not everyone believes a survey is the way to go. Or at least, not a survey in isolation.
It’s a self-assessment tool, for one thing, as former Bank of Queensland CRO Peter Deans pointed out in a recent Intelligence contribution (Members: access this here ). You may not get the true risk picture you need, if you are only asking people if they believe they are making risk-aware decisions and are satisfied with the culture.
UK risk consultant Roger Noon shared with us a variety of tools risk managers can use in-house to help understand behaviours and diagnose culture (Members: access these tools here) . Of quantitative risk culture surveys, he says: “Survey instruments can also be used so long as you and your sponsors recognise that they are typically very blunt tools, often with poor validity. They're very ‘point in time and context’ driven, and they don't really provide you with objective observable output.
“However, they can be used to generate interesting data that creates helpful dialogue at the senior management table. They’re also useful to build engagement with the people that are part of the culture, and as part of a wider, triangulated set of data.”
In other instances, risk managers found it was not employees they initially needed to survey, but their board. Across different industries, different understandings of risk culture exist. If your board is asking about risk culture, it can be a good idea to check in that you (and they, among themselves) are all on the same page before beginning any broader projects. (Members: take a look at some sample questions about risk culture for the board here .)
So overt it’s covert
When it comes to an organisation’s overall approach to assessing and changing risk culture, there are also a few fundamentally different mindsets.
For some companies, the ‘culture overhaul’ needs to be a large project with lots of publicity and a big push from the top. In such cases, when it comes to driving change, extensive engagement and communications programs are planned, potentially including video.
We collected one case study, however, that stood out for its far more subtle and positive approach. In it, the head of risk at a large organisation with a few thousand staff spread across nine departments said there were a lot of preconceptions and quite a bit of nervousness around the idea of ‘working on risk culture’. This risk manager had therefore developed a different kind of self-assessment tool, which helped participants map their own risk culture using evidence-based attributes.
At the end of the initial meeting (which took no more than an hour and a half), participants had identified their own areas for improvement and incorporated culture elements into their future risk planning. (Members: access this case study here .)
Sometimes risk managers reach a point where they simply have to be realistic about their resources and prospects for implementing large scale change.
In another example from the Middle East, an expat risk manager found it was a case of trying to move his company’s risk culture at different ‘clock speeds’ across the organisation’s verticals, catering to different levels of appetite, awareness and need for change between delivery teams and the C-Suite. (Members: access this case study here .)
And, finally, sometimes risk managers reach a point where they simply have to be realistic about their resources and prospects for implementing large scale change. If there’s no appetite from the top for a risk culture shift, the risk manager will have an uphill battle. We’ve collected ideas from the former risk leader at a government utility, who devised tactics for embedding changes into existing systems and processes to deliver better risk outcomes for the business. (Members: access these ideas here .)
Measuring, reporting and dashboards
We found that the facet of culture where everybody most wanted to know what everybody else was measuring and what they were doing in terms of reporting and dashboards.
Again, there were a number of different methods shared by our Members and contributors, as well as contrasting views on what actually should be measured.
For example, is it redundant to actually measure ‘risk culture’? After all, isn’t the entire point of improving risk culture to improve risk outcomes? Why not just focus on measuring the risk outcomes, with culture change happening in the background to facilitate?
Certainly, this was the view of the former risk manager at a prominent United States government organisation, who spoke to us about building up their organisation’s risk capability over several years. (Members: read more on this here .)
Is it redundant to actually measure ‘risk culture’? After all, isn’t the entire point of improving risk culture to improve risk outcomes?
However, others saw value in tracking specific culture metrics, even if these goals were a means to an end. A scorecard or dashboard became a talking point to launch difficult conversations with different managers or executives, and the ability to show progress over time helped maintain momentum and commitment.
Over time, Peter Deans at BOQ developed and refined a ‘basket of risk culture measures’ along the same lines as the consumer price index, which he regularly updated and used to give leadership a ‘big picture view’ of how risk culture was doing.
Other contributing risk managers shared their scorecards and dashboards with us as templates, such as a scorecard example using a traffic light system across nine key risk indicators. We also collected ideas for dashboard metrics and a spreadsheet-based sunburst tool, alongside risk culture pillars.
On a final note, UK risk advisor Danny Wong shared a detailed case study on how to use data to drive an impactful risk narrative. For any risk managers who are striving to bring risk into line with many other functions in contemporary business – such as product development, sales, operations, and others that regularly use data strategically to inform decision making and best practice – this piece is essential reading. (Members: access this piece here .)
Risk Leadership Network’s Intelligence platform – our searchable database of peer-contributed case-studies, tools and templates – delves deeper into risk culture with more on diagnosing culture , addressing culture and ethics , and building a risk culture survey of boards . (Members only)
Are you an in-house risk manager who could benefit from collaborating with a global network of senior risk professionals talk to us about becoming a member today ., related posts you may be interested in.

5 ways to become a better leader in risk culture

There’s no such thing as risk culture, or is there?

Three useful tools to optimise a risk culture review
Get new posts by email.
Case Study: Companies Excelling in Risk Management

In this article
In the modern business landscape, navigating uncertainties and pitfalls is essential for sustainable growth and longevity. Effective risk management emerges as a shield against potential threats – and it also unlocks opportunities for innovation and advancement. In this article, we will explore risk management and its significance and criteria for excellence. We will also examine case studies of two companies that have excelled in this domain. Through these insights, we aim to glean valuable lessons and best practices. As such, businesses across diverse industries can fortify their risk management frameworks.
The Significance of Risk Management
Risk management is vital for the sustenance and prosperity of companies, regardless of their size or industry. At its core, it is the identification, assessment and mitigation of potential risks that may impede organisational objectives or lead to adverse outcomes. Having a robust risk management approach means businesses can safeguard their assets, reputation and bottom line.
The statistics are somewhat alarming. According to research , 69% of executives are not confident with their current risk management policies and practices. What’s more, only 36% of organisations have a formal enterprise risk management (ERM) programme.
Proactive risk management isn’t just a defensive measure; rather, it is necessary for sustainability and growth. With 62% of organisations experiencing a critical risk event in the last three years, it is important to be proactive. By identifying and addressing potential risks, organisations can become more resilient to external shocks and internal disruptions. This means they’re better able to survive through difficult times and maintain operational continuity. Moreover, a proactive stance enables companies to seize strategic advantages. It allows them to innovate, expand into new markets and capitalise on emerging trends with confidence.

Criteria for Excellence in Risk Management
Achieving excellence in risk management means adhering to several key criteria:
- Ability to Identify Risks: Exceptional risk management begins with identifying potential risks comprehensively. This involves a thorough understanding of both internal and external factors that could impact the organisation. It includes market volatility, regulatory changes, cybersecurity threats and operational vulnerabilities.
- Assessment of Risks: Once identified, risks must be assessed to gauge their potential impact and likelihood of occurrence. This involves using risk assessment methodologies like quantitative analysis, scenario planning and risk heat mapping, to prioritise risks based on their severity and urgency.
- Mitigation Strategies and Control Measures: Effective risk management relies on proactive mitigation strategies to minimise the likelihood of risk occurrence and mitigate its potential impact. This may involve implementing control measures, diversifying risk exposure, investing in risk transfer mechanisms such as insurance and enhancing resilience through business continuity planning.
- Adaptability to Change: Organisations need to be ready to adapt to emerging risks and changing circumstances. This requires a culture of continuous learning and improvement. This means lessons are learned from past experiences to enhance risk management practices and anticipate future challenges.
- Leadership Commitment: Effective leaders demonstrate a clear understanding of the importance of risk management. They know how to allocate adequate resources, support and incentives to prioritise risk management initiatives.
- Strong Risk Culture: A strong risk culture permeates every level of the organisation. This involves a mindset where risk management is viewed as everyone’s responsibility.
- Robust Risk Management Frameworks: Finally, excellence in risk management requires robust frameworks and processes to guide risk identification, assessment and mitigation efforts. This includes defining clear roles and responsibilities, implementing effective governance structures and leveraging technology and data analytics to enhance risk visibility and decision-making.
Company A: Case Study in Risk Management Excellence
Now, let’s take a look at a case study that highlights risk management excellence in practice.
ApexTech Solutions is a company known for its exemplary risk management practices. Founded in 2005 by visionary entrepreneur Sarah Lawson, ApexTech began as a small start-up in the tech industry. It specialises in software development and IT consulting services.
Over the years, under Lawson’s leadership, the company expanded its offerings and diversified into various sectors, including cybersecurity solutions, cloud computing and artificial intelligence. Today, ApexTech is a prominent player in the global technology market, serving clients ranging from small businesses to Fortune 500 companies.
Risk management strategies and successes
ApexTech’s journey to risk management excellence can be attributed to several key strategies and initiatives:
- Comprehensive Risk Assessment: ApexTech conducts regular and thorough risk assessments to identify potential threats and vulnerabilities across its operations.
- Investment in Technology and Innovation: ApexTech prioritises investments in cutting-edge technologies such as AI-driven analytics, predictive modelling and threat intelligence solutions.
- Customer-Centric Approach: ApexTech tailors its risk management solutions to meet specific needs and preferences. This fosters trust and long-term partnerships.
- Cybersecurity Measures: ApexTech has made cybersecurity a top priority. The company employs a multi-layered approach to cybersecurity to mitigate the risk of cyberattacks.
- Continual Improvement and Adaptation: ApexTech fosters a culture of continual improvement and adaptation. The company encourages feedback and collaboration among employees at all levels so they can identify areas for improvement and implement solutions to mitigate risks effectively.
By proactively identifying and addressing operational risks, such as supply chain disruptions and regulatory compliance challenges, ApexTech has maintained operational continuity and minimised potential disruptions to its business operations.
ApexTech Solutions serves as a compelling example of a company that has excelled in risk management excellence by embracing proactive strategies, leveraging advanced technologies and fostering a culture of innovation and adaptation.
Company B: Case Study in Risk Management Excellence
TerraSafe Pharmaceuticals is a renowned company in the pharmaceutical industry, dedicated to developing and manufacturing innovative medications to improve global health outcomes. Established in 1998 by Dr Elena Chen, TerraSafe initially focused on the production of generic drugs to address critical healthcare needs.
Over the years, the company has expanded its portfolio to include novel biopharmaceuticals and speciality medications.
TerraSafe Pharmaceuticals has a holistic approach to identifying, assessing and mitigating risks across its operations:
- Rigorous Quality Assurance Standards: TerraSafe prioritises stringent quality assurance measures throughout the drug development and manufacturing process. This ensures product safety, efficacy and compliance with regulatory requirements.
- Investment in Research and Development (R&D): TerraSafe allocates significant resources to research and development initiatives. These are aimed at advancing scientific knowledge and discovering breakthrough therapies. With its culture of innovation and collaboration, the company mitigates the risk of product obsolescence.
- Regulatory Compliance and Risk Monitoring: TerraSafe maintains a dedicated regulatory affairs department. This team stays abreast of evolving regulatory requirements and industry standards. They monitor regulatory changes proactively and engage with regulatory authorities to ensure timely compliance with applicable laws and standards. This reduces the risk of non-compliance penalties and legal disputes.
- Supply Chain Resilience: TerraSafe works closely with its suppliers and logistics partners to assess and mitigate supply chain risks like raw material shortages, transportation disruptions and geopolitical instability. It implements contingency planning and diversification of sourcing strategies.
- Focus on Patient Safety and Ethical Practices: The company adheres to stringent ethical guidelines and clinical trial protocols to protect patient welfare and maintain public trust in its products and services.
By investing in R&D and adhering to rigorous quality assurance standards, TerraSafe has successfully developed and commercialised several breakthrough medications that address unmet medical needs and improve patient outcomes. What’s more, the company’s proactive approach to regulatory compliance has facilitated the timely approval and market authorisation of its products in key global markets. This has enabled the company to expand its geographic footprint and reach new patient populations.
Key Takeaways and Best Practices
Despite being in different industries, both companies share similarities. Both ApexTech and TerraSafe Pharmaceuticals know the importance of proactive risk management. They have procedures in place that work to identify, assess and mitigate risks before they escalate. What’s more, both companies are led by visionary leaders who set the tone for decision-making. They prioritise building a strong risk culture with all employees knowing their role in risk management.

Best practices and strategies employed
- Conducting Regular Risk Assessments: Both companies conduct regular and comprehensive risk assessments to identify potential threats and vulnerabilities across their operations.
- Investing in Training and Education: Both invest in training and education programmes so that employees are equipped with the knowledge and skills necessary to identify and manage risks effectively. Employees at all levels contribute to risk management efforts.
- Collaboration and Communication: Both companies know the importance of collaboration and communication in risk management. They create channels for open dialogue and information sharing. Stakeholders collaborate on risk identification, assessment and mitigation efforts.
- Continual Improvement: Both companies have a culture of continual improvement. They encourage feedback and innovation to adapt to changing circumstances and emerging risks.
- Tailored Risk Management Approaches: Both companies develop customised risk management frameworks and strategies that align with their objectives and priorities.
Emerging Trends in Risk Management
One of the most prominent trends in risk management is the increasing integration of technology into risk management processes. Advanced technologies such as artificial intelligence (AI), machine learning and automation are revolutionising risk assessment, prediction and mitigation. These technologies mean companies can analyse vast amounts of data in real time. This allows them to identify patterns and trends and predict potential risks more accurately.
Data analytics is another key trend reshaping risk management practices. Companies are leveraging big data analytics tools and techniques to gain deeper insights. By analysing historical data and real-time information, they can identify emerging risks, detect anomalies and make more informed risk management decisions.
Cybersecurity risks have become a major concern. Threats such as data breaches, ransomware attacks and phishing scams pose significant risks to companies’ data, operation and reputation. Companies are investing heavily in cybersecurity measures and adopting proactive approaches to protect their digital assets and mitigate cyber risks.
Companies are integrating global risk management into their overall risk management strategy too. They are monitoring global developments, assessing the impact of global risks on their business operations and developing contingency plans.
The Role of Leadership
Leadership plays a pivotal role in shaping organisational culture and driving initiatives that promote risk management excellence. Effective leaders recognise the importance of risk management but also actively champion its integration into the fabric of the organisation. Effective leaders:
- Set the Tone: Leaders set the tone by articulating a clear vision and commitment to risk management from the top down.
- Lead by Example: Leaders demonstrate their own commitment to risk management through their actions and decisions.
- Empower Employees: Leaders empower employees at all levels to actively participate in risk management efforts. They encourage employees to voice their concerns and contribute.
- Provide Resources and Support: Effective leaders invest in training and development programmes to enhance employees’ risk management skills and knowledge.
- Encourage Innovation: Leaders encourage employees to think creatively and experiment with new approaches to risk management.
- Promote Continuous Improvement: Leaders create opportunities for reflection and evaluation to identify areas for improvement and drive learning.
Encouraging a Risk-Aware Culture
For organisations to identify, assess and mitigate risks at all levels effectively, they need to encourage a risk-aware culture. Here are some tips for encouraging a risk-aware culture:
Communication and transparency:
- Encourage open communication channels where employees feel comfortable discussing risks and raising concerns.
- Provide regular updates on the organisation’s risk landscape, including emerging risks and mitigation strategies.
- Foster transparency in decision-making processes, particularly regarding risk-related decisions.
Education and training:
- Provide comprehensive training programmes on risk management principles, processes and tools for employees at all levels.
- Offer specialised training sessions on specific risk areas relevant to employees’ roles and responsibilities.
- Incorporate real-life case studies and examples to illustrate the importance of risk awareness and effective risk management.
Empowerment and ownership:
- Empower employees to take ownership of risk management within their respective areas of expertise.
- Encourage employees to identify and assess risks in their day-to-day activities and propose mitigation strategies.
- Recognise and reward employees who demonstrate proactive risk awareness and contribute to effective risk management practices.
Integration into performance management:
- Include risk management objectives and key performance indicators (KPIs) in employee performance evaluations.
- Link performance bonuses or incentives to successful risk management outcomes and adherence to risk management protocols.
- Provide feedback and coaching to employees on their risk management performance, highlighting areas for improvement and best practices.

Challenges in Risk Management
Challenges in risk management are inevitable, even for companies excelling in this domain. Despite their proactive efforts, all organisations encounter obstacles that can impede their risk management practices. Here are some common challenges and strategies for addressing them:
Complexity and interconnectedness:
- Challenge: The modern business environment is increasingly complex and interconnected, making it challenging for organisations to anticipate and mitigate all potential risks comprehensively.
- Strategy: Implement a holistic risk management approach that considers both internal and external factors impacting the organisation. Create cross-functional collaboration and information sharing to gain a comprehensive understanding of risks across departments and business units.
Rapidly evolving risks:
- Challenge: Risks are constantly evolving due to technological advancements, regulatory changes and global events such as pandemics or geopolitical shifts. Organisations may struggle to keep pace with emerging risks and adapt their risk management strategies accordingly.
- Strategy: Stay informed about emerging trends and developments that may impact the organisation’s risk landscape. Maintain flexibility and agility in risk management processes to respond promptly to new challenges.
Resource constraints:
- Challenge: Limited resources, including budgetary constraints and staffing limitations, can hinder organisations’ ability to invest adequately in risk management initiatives and tools.
- Strategy: Prioritise risk management activities based on their potential impact on organisational objectives and allocate resources accordingly. Leverage technology and automation to streamline risk management processes and maximise efficiency.
Compliance and regulatory burden:
- Challenge: Meeting regulatory requirements and compliance standards can be burdensome and complex.
- Strategy: Stay abreast of regulatory developments and ensure compliance with applicable laws and regulations. Implement robust governance frameworks and internal controls to demonstrate regulatory compliance and mitigate legal and reputational risks. Invest in compliance training and education for employees.
Human factors and behavioural biases:
- Challenge: Human factors such as cognitive biases, organisational politics and resistance to change can undermine effective risk management practices, leading to decision-making errors and oversight of critical risks.
- Strategy: Raise awareness about common cognitive biases and behavioural tendencies that may influence risk perception and decision-making. Create a culture of psychological safety where employees feel comfortable challenging assumptions and raising concerns about potential risks.
Conclusion: Striving for Excellence
In this article, we have explored the importance of effective risk management for businesses. We have delved into the criteria for excellence in risk management, showcasing companies such as ApexTech Solutions and TerraSafe Pharmaceuticals that exemplify these principles through their proactive strategies and robust frameworks.
From embracing technology and fostering a culture of innovation to prioritising regulatory compliance and empowering employees, these companies have demonstrated remarkable achievements in navigating complex risk landscapes and achieving sustainable success.
However, it’s essential to recognise that even companies excelling in risk management face challenges. By acknowledging these and implementing strategies to address them, organisations can enhance their resilience and effectiveness in managing risks over the long term.

Assessing Risk
Study online and gain a full CPD certificate posted out to you the very next working day.
Take a look at this course
About the author

Louise Woffindin
Louise is a writer and translator from Sheffield. Before turning to writing, she worked as a secondary school language teacher. Outside of work, she is a keen runner and also enjoys reading and walking her dog Chaos.
Similar posts

Top Risk Factors for Cardiovascular Diseases and How to Mitigate Them

The Role of Therapy and Counselling in Anger Management

Case Study: Inspirational Stories of Individuals Regaining Confidence

How Play Enhances Cognitive, Social and Physical Development
Celebrating our clients and partners.

An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- HHS Author Manuscripts

A case study exploring field-level risk assessments as a leading safety indicator
Lead research behavioral scientist and research behavioral scientist, respectively, National Institute for Occupational Safety and Health, Pittsburgh, PA, USA
B.P. Connor
J. vendetti.
Manager, mining operations, Solvay Soda Ash & Derivatives North America, Green River, WY, USA
CSP, Mine production superintendent, Solvay Chemicals Inc., Green River, WY, USA
Health and safety indicators help mine sites predict the likelihood of an event, advance initiatives to control risks, and track progress. Although useful to encourage individuals within the mining companies to work together to identify such indicators, executing risk assessments comes with challenges. Specifically, varying or inaccurate perceptions of risk, in addition to trust and buy-in of a risk management system, contribute to inconsistent levels of participation in risk programs. This paper focuses on one trona mine’s experience in the development and implementation of a field-level risk assessment program to help its organization understand and manage risk to an acceptable level. Through a transformational process of ongoing leadership development, support and communication, Solvay Green River fostered a culture grounded in risk assessment, safety interactions and hazard correction. The application of consistent risk assessment tools was critical to create a participatory workforce that not only talks about safety but actively identifies factors that contribute to hazards and potential incidents. In this paper, reflecting on the mine’s previous process of risk-assessment implementation provides examples of likely barriers that sites may encounter when trying to document and manage risks, as well as a variety of mini case examples that showcase how the organization worked through these barriers to facilitate the identification of leading indicators to ultimately reduce incidents.
Introduction
Work-related health and safety incidents often account for lost days on the job, contributing to organizational/financial and personal/social burdens ( Blumenstein et al., 2011 ; Pinto, Nunes and Ribeiro, 2011 ). Accompanying research demonstrates that risk and ambiguity around risk contribute to almost every decision that individuals make throughout the day ( Golub, 1997 ; Suijs, 1999 ). In response, understanding individual attitudes toward risk has been linked to predicting health and safety behavior ( Dohmen et al., 2011 ). Although an obvious need exists to identify more comprehensive methods to assess and mitigate potential hazards, some argue that risk management is not given adequate attention in occupational health and safety ( Haslam et al., 2016 ). Additionally, research suggests that a current lack of knowledge, skills and motivation are primary barriers to worker participation in mitigating workplace risks ( Dohmen et al., 2011 ; Golub, 1997 ; Haslam et al., 2016 ; Suijs, 1999 ). Therefore, enhancing knowledge and awareness around risk-based decisions, including individuals’ abilities to understand, measure and assign levels of risk to determine an appropriate response, is increasingly important in hazardous environments to predict and prevent incidents.
This paper focuses on one field-level risk assessment (FLRA) program, including a matrix that anyone can use to assess site-wide risks and common barriers to participating in such activities. We use a trona mine in Green River, WY, to illustrate that a variety of methods may be needed to successfully implement a proactive risk management program. By discussing the mine’s tailored FLRA program, this paper contributes to the literature by providing (1) common barriers that may prevent proactive risk assessment programs in the workplace and (2) case examples in the areas of teamwork, front-line leadership development, and tangible and intangible communication efforts to foster a higher level of trust and empowerment among the workforce.
Risk assessment practices to reveal leading indicators
Risk assessment is a process used to gather knowledge and information around a specific health threat or safety hazard ( Smith and Harrison, 2005 ). Based on the probability of a negative incident, risk assessment also includes determining whether or not the level of risk is acceptable ( Lindhe et al., 2010 ; International Electrotechnical Commission, 1995 ; Pinto, Nunes and Ribeiro, 2011 ). Risk assessments can occur quantitatively or qualitatively. Research values both types in high-risk occupations to ensure that all possible hazards and outcomes have been identified, considered and reduced, if needed ( Boyle, 2012 ; Haas and Yorio, 2016 ; Hallenbeck, 1993 ; International Council on Mining & Metals (ICMM), 2012 ; World Health Organization (WHO), 2008 ). Quantitative methods are commonly found where the site is trying to reduce a specific health or environmental exposure, such as respirable dust or another toxic substance ( Van Ryzin, 1980 ). These methods focus on a specific part of an operation or task within a system, rather than the system as a whole ( Lindhe et al., 2010 ). Conversely, a qualitative approach is useful for potential or recently identified risks to decide where more detailed assessments may be needed and prioritize actions ( Boyle, 2012 ; ICMM, 2012 ; WHO, 2008 ).
Although mine management can use risk assessments to inform procedural decisions and policy changes, they are more often used by workers to identify, assess and respond to worksite risks. A common risk assessment practice is to formulate a matrix that prompts workers to identify and consider the likelihood of a hazardous event and the severity of the outcome to yield a risk ranking ( Pinto, Nunes and Ribeiro, 2011 ). After completing such a matrix and referring to the discretized scales, any organizational member should be able to determine and anticipate the risk of a hazard, action or situation, from low to high ( Bartram, 2009 ; Hokstad et al., 2010 ; Rosén et al., 2006 ). The combination of these two “scores” is used to determine whether the risk is acceptable, and subsequently, to identify an appropriate response. For example, a list of hazards may be developed and evaluated for future interventions, depending upon the severity and probability of the hazards. Additionally, risk assessments often reveal a prioritization of identified risks that inform where risk-reduction actions are more critical ( Lindhe et al., 2010 ), which may result in changes to a policy or protocol ( Boyle, 2012 ).
If initiated and completed consistently, risk assessments allow root causes of accidents and patterns of risky behavior to emerge — in other words, leading indicators ( Markowski, Mannan and Bigoszewska, 2009 ). Leading indicators demonstrate pre-incident trends rather than direct measures of performance, unlike lagging indicators such as incident rates, and as a result, are useful for worker knowledge and motivation ( Juglaret et al., 2011 ). Recently, high-risk industries have allocated more resources to preventative activities — not only to prevent injuries but also to avoid the financial costs associated with incidents — which has produced encouraging results ( Maniati, 2014 ; Robson et al., 2007 ). However, research has pointed to workers’ general confusion about the interpretation of hazards and assignment of probabilities as a hindrance to appropriate risk identification and response ( Apeland, Aven and Nilsen, 2002 ; Reason, 2013 ). In response, better foresight into the barriers of risk management is needed to (1) engage workers in risk identification and assessment, and (2) develop pragmatic solutions to prevent incidents.
Methods and materials
In December 2015, Haas and Connor, two U.S. National Institute for Occupational Safety and Health (NIOSH) researchers, traveled to Solvay Green River’s mine in southwest Wyoming. This trona mine produces close to 3 Mt/a of soda ash using a combination of longwall and solution mining and borer miners ( Fiscor, 2015 ). A health, safety and risk management framework had been introduced in phases during 2009 and 2010 to the mine’s workforce of more than 450 to help reduce risks to an acceptable level, and NIOSH wanted to understand all aspects of this FLRA program and how it became integrated into everyday work processes. We collected an extensive amount of qualitative data, analyzed the material and triangulated the results to inform a case study in health and safety system implementation ( Denzin and Lincoln, 2000 ; Pattson, 2002 ; Yin, 2014 ). The combination of expert interviews, existing documentary materials, and observation of onsite activities provided a holistic view of both post-hoc and current data points, allowing for various contexts to be compared and contrasted to determine consistency and saturation of the data ( Wrede, 2013 ).
Participants
We collected several qualitative data points, including all-day expert interviews and discussions with mine-site senior-level management such as the mine manager, health and safety manager, and mine foremen/supervisors, some of whom were hourly workers at the time of the risk assessment program implementation ( Flick, 2009 ). Additionally, we heard presentations from the mine managers and site supervisors, received archived risk assessment documents and were able to engage in observations on the surface and in the underground mine operation during the visit, where several mineworkers engaged in conversations about the FLRA, hazard interactions, and general safety culture on site.
Retrospective data analysis of risk assessment in action
Typically, qualitative analysis and triangulation of case study data use constant comparison techniques, sometimes within a grounded theory framework ( Corbin and Strauss, 2008 ; Glaser and Strauss, 1967 ). We employed the constant comparison method within a series of iterative coding steps. First, we typed the field notes and interview notes, and scanned the various risk assessment example documents received during the visit. Each piece of data was coded for keywords and themes through an initial, focused and then constant comparison approach ( Boyatzis, 1998 ; Fram, 2013 ).
Throughout the paper, quotes and examples from employees who participated in the visit are shared to better demonstrate their process to establish the FLRA program. To address the reliability and validity of our interpretation of the data, the two primary, expert information providers during the field visit, Vendetti and Heiser, became coauthors and served as member checkers of the data to ensure all information was described in a way that is accurate and appropriate for research translation to other mine sites ( Kitchener, 2002 ).
It is important to know that in 2009 Solvay experienced a sharp increase in incidents in its more-than-450-employee operation. Although no fatalities occurred, there were three major amputations and injury frequencies that were increasing steadily. The root causes of these incidents — torn ligaments/tendons/muscles requiring surgical repair or restricted duty; lacerations requiring sutures; and fractures ( Mine Safety and Health Administration, 2017 ) — showed that inconsistent perceptions of risk and mitigation efforts were occurring on site among all types of work positions, from bolters to maintenance workers. These incidents caused frustration and disappointment among the workforce.
Intervention implementation, pre- and post-FLRA program
Faced with inconsistencies in worker knowledge of risks and varying levels of risk tolerance, management could have taken a punitive, “set an example” response, based on an accountability framework. Instead, they began a process in 2009 to bring new tools, methods and mindset to safety performance at the site. Specifically, based on previous research and experience, such as from 1998, they saw the advantages of creating a common, site-wide set of tools and metrics to guide workers in a consistent approach to risk assessment in the field. This involvement trickled down to hourly workers in the form of a typical risk assessment matrix ( Table 1 ) described earlier to identify, assess and evaluate risks. Management indicated that if everyone had tools, then “It doesn’t matter what you knew or what you didn’t, you had tools to assess and manage a situation.” They hypothesized that matrices populated by workers would reveal leading indicators to proactively identify and prevent incidents that had been occurring on site. Workers were expected to utilize this matrix daily to help identify and evaluate risks.
Risk assessment matrix used by Solvay ( Heiser and Vendetti, 2015 ).
To complete the matrix, workers rate consequences of a risk using the scales/key depicted in Table 2 . As shown in the color-coded matrix, multiplying the scores for these two areas yields a risk ranking of low, moderate, high or critical, thereby providing guidance on what energies or hazards to mitigate immediately. Although the matrix approach, specifically, may not be new to the industry, the implementation and evaluation of such efforts offer value in the form of heightened engagement, leadership and eventually behavior change.
Evaluation matrix key ( Heiser and Vendetti, 2015 ).
Observing incidents post-implementation of the FLRA intervention during 2009 and front-line leadership efforts during 2010, much can be learned to understand where and how impact occurred on site. Figure 1 shows Green River’s 2009 spike in non-fatal days lost (NFDL) incidents with a consistent drop thereafter, providing cursory support of the program.

Solvay non-fatal days lost operator injuries, 2006–2016 ( MSHA, 2017 ).
Seeing a drop in incidents provides initial support for the FLRA program that Solvay introduced. Knowing that many covariates may account for a drop in incidents, however, additional data were garnered from MSHA’s website to account for hours worked. Still, the incident rate declined consistently, as shown in Fig. 2 .

Non-fatal days lost operator injury incidence rate (injuries by hours worked), 2006–2016 ( MSHA, 2017 ).
From a quantitative tracking effort of these lagging indicators, it can be gleaned that the implemented program was successful. However, it is important to understand what, how and why incidents decreased over time to maintain consistency in implementation and evaluation efforts. In response, this paper focuses on the qualitative data that NIOSH collected in hopes of sharing how common barriers to risk assessment can be addressed to identify leading indicators on site.
During the iterative analysis of the data, researchers sorted the initial and ongoing barriers to continuous risk assessment. The results provide insight into promising ways to measure and document as well as support and manage a risk-based program over several years. After common barriers to risk assessment implementation are discussed, mini case examples to illustrate how the organization improved and used their FLRA process to identify leading indicators follow. Ultimately, these barriers and organizational responses show that an FLRA program can help (1) measure direct/indirect precursors to harm and provide opportunities for preventative action, (2) allow the discovery of proactive leadership risk reduction strategies, and (3) provide warning before an undesired event occurs and develop a database of response strategies ( Blumenstein et al., 2011 ; ICMM, 2012 ).
Barrier to risk assessment intervention: Varying levels of risk tolerance and documentation
An initial challenge, not uncommon in occupational health and safety, was the varying levels of risk tolerance possessed by the workforce. Research shows that individuals have varying levels of knowledge, awareness and tolerance in their abilities to recognize and perceive risks as unacceptable ( Brun, 1992 ; Reason, 2013 ; Ruan, Liu and Carchon, 2003 ). Managers and workers reflected that assessments of a risk were quite broad, having an impact on the organization’s ability to consistently identify and categorize hazards. One employee who was an hourly worker at the time of the FLRA implementation said, “It took time to establish a sensitivity to potential hazards.” This is not particularly surprising; as individuals gain experience, they can become complacent with health and safety risks and, eventually, have a lower sense of perceived susceptibility and severity of a negative outcome ( Zohar and Erev, 2006 ). As a result, abilities to consistently notice and believe that a hazard poses threat to their personal health and safety decreases. The health and safety manager said, “It took a long time to get through to people that this isn’t the same as what they do every day. To really assess a risk you have to mentally stop what you’re doing and consider something.”
Eventually, management developed an understanding that risk tolerance differed individually and generationally onsite, acknowledging that sources of risk are always changing in some regard and tend to be more complicated for some employees to see than others. In response, discussions about the importance of encouraging conscious efforts of risk management became ongoing to support a new level of awareness on site. Additionally, the value of documenting risk assessment efforts on an individual and group level became more apparent. One area emphasized was encouraging team communication around risk assessment if it was warranted. An example of this process and outcome is detailed below to help elucidate how Solvay overcame disparate perceptions of risk through teamwork.
Case example: FLRA discussion and documentation in action
An example of the FLRA in action as a leading indicator was provided by the maintenance supervisor during the visit. This example included an installation of a horizontal support beam. Workers collectively completed an FLRA to determine if they could simply remove the gantry system without compromising the integrity of the headframe. As part of their FLRA process, workers were expected to identify energies/hazards that could exist during this job task. Hazards that they recorded for this process for consideration within the matrix as possible indicators included:
- Working from heights/falling.
- Striking against/being struck by objects.
- Pinch points.
- Traction and balance.
- Hand placement.
- Caught in/on/between objects.
An initial risk rank was provided for each of the identified hazards, based on the matrix ( Tables 1 and and2). 2 ). Based on the initial risk rank, workers decided which controls to implement to minimize the risk to an acceptable level. Examples of controls implemented included:
- Review the critical lift plan.
- Conduct a pre-job safety and risk assessment meeting.
- Inspect all personal protective equipment (PPE) fitting and harnesses.
- Understand structural removal sequence.
- Communicate between crane operator and riggers.
- Assure 100 percent of tie-off protocol is followed.
- Watch out for coworkers.
- Participate in housekeeping activities.
Upon determining and implementing controls, a final risk rank was rendered to make a decision for the job task: whether or not the headframe could be removed in one section. Ultimately, workers decided it could safely be done. However, management emphasized the importance of staying true to their FLRA. They said that 50 percent of their hoisting capabilities are based on wind and that if the wind is too high, they shut down the task, which happened one day during this process. So, although an FLRA was completed and provided a documented measurement and direction about what decisions to carry out, the idea of staying true to a minute-by-minute risk assessment was important and adhered to for this task.
In this sense, the FLRAs served as a communication platform to share a common language and ultimately, common proactive behavior. In general, vagueness of data on health and safety risks can prevent hazard recognition, impair decision-making, and disrupt risk-based decisions among workers ( Ruan, Liu and Carchon, 2003 ). This example showed that the more workers understood what constitutes an acceptable level of risk, the greater sense of shared responsibility they had to prevent hazards and make protective decisions on the job ( Reason, 1998 ) such as shutting down a procedure due to potential problems. Now, workers have the ability to implement their own check-and-balance system to determine if a response is needed and their decision is supported. Treating the FLRA as a check-and-balance system allowed workers to improve their own risk assessment knowledge, skills and motivation, a common barrier to hazard identification ( Haslam et al., 2016 ). In theory, as FLRAs are increasingly used to predetermine possible incidents and response strategies are developed and referenced, the occurrence of lagging indicators should decrease, as has been the case at Solvay in recent years.
Barrier to risk assessment intervention: Resisting formal risk assessment methods
Worksites often face challenges of determining the best ways to measure and develop suitable tools to facilitate consistent risk measurement ( Boyle, 2012 ; Haas and Yorio, 2016 ; Haas, Willmer and Cecala, 2016 ). For example, research shows that assessing site risks using a series of checklists or general observations during site walkthroughs is more common ( Navon and Kolten, 2006 ). Although practical, checklists and observations require little cognitive investment and have more often been insufficient in revealing potential safety problems ( Jou et al., 2009 ). Due to familiarity with “the way things were,” implementing the system of risk assessments at Solvay came with challenges. Workers experienced initial resistance to moving toward something more formal.
For example, at the outset, hourly workers said they felt, “I do this in my head all the time. I just don’t write it down.” Particularly, individuals who were hourly workers at the time of the FLRA program implementation felt that they already did some form of risk identification and that they did not need to go into more detail to assess the risk. Just as some workers did not see a difference with what they did implicitly, and so discounted the value of conducting an FLRA, others did not think they needed to take action based on their matrix risk ranking. As one worker reflected on the previous mindset, he said, “It would be okay to be in the red, so long as you knew you were in the red.” Because of the varying levels of initial acceptance, there were inconsistencies in the quality of the completed risk assessment matrices. Management noted, “Initially, people were doing them, but not to the quality they could have been.” In response, Solvay management focused on strengthening their frontline leadership skills to help facilitate hourly buy-in, as described in the following case example.
Case example: Starting with frontline leadership to facilitate buy-in, “The Club”
To facilitate wider commitment and buy-in, senior-level management took additional steps with their frontline supervisors. To train frontline leaders on how to understand rather than punish worker actions, Solvay management started a working group in 2010 called “The Club.” This group consisted of supervisory personnel within various levels of the organization. The purpose of The Club was to develop leaders and a different sort of accountability with respect to safety. One of its first actions was to, as a group, agree on qualities of a safety leader. From there, they eventually executed a quality leadership program that embraced the use of the risk assessment tools and their outcomes ( Fiscor, 2015 ; Heiser and Vendetti, 2015 ).
After receiving this leadership training and engaging in discussions about FLRA, the execution of model leadership from The Club started. Specifically, the frontline foremen that the researchers talked with indicated that they were better able to communicate about and manage safety across the site. Prior to The Club and adapting to the FLRA, one of these supervisors reflected, “No one wanted to make a safety decision.” Senior management acknowledged with their frontline leadership that the FLRA identifies steps that anyone might miss because they are interlocked components of a system. Because of the complex risks present on site, they discussed the importance of sitting down and reviewing with hourly workers if something happened or went wrong. They shared the importance of supportive language: “We say ‘let’s not do this again,’ but they don’t get in trouble.”
To further illustrate the leadership style and communicative focus, one manager shared a conversation conducted with a worker after an incident. Rather than reprimanding the worker’s error in judgement, the manager asked: “What was going through your mind before, during this task? I just want to understand you, your choices, your thought process, so we can prevent someone else from doing the same thing, making those same choices.” After the worker acknowledged he did not have the right tools but tried to improvise, the manager asked him what other risky choices he had made that turned out okay. This process engaged the worker, and he “really opened up” about his perceptions and behaviors on site. This incident is an example of site leaders establishing accountability for action but ensuring that adequate resources and site support were available to facilitate safer practice in the future ( Yorio and Willmer, 2015 ; Zohar and Luria, 2005 ). In other words, management used these conversations not only to educate the workers about hazards involved in complex systems, but also to enact their positive safety culture.
Importantly, this communication and documentation among The Club allowed insight into how employees think, serving as a leading indicator for health and safety management. The stack of FLRAs that were pulled out — completed between 2009 and 2015 — were filled out with greater detail as the years progressed. It was apparent that the hourly workforce continually adapted, resulting in an improved sense of organizational motivation, culture and trust. Management indicated to NIOSH that workers now have an increased sense of empowerment to identify and mitigate risks. Contrary to how workers used to document their risk assessments, a management member said: “You pull one out today, and even if it isn’t perfect, the fundamentals are all there, even if it isn’t exactly how we would do it. And more likely than not, you’d pull out one and find it to be terrific.”
Barrier to risk assessment intervention: Communicate and show tangible support for risk assessment methods
A lack of management commitment, poor communication and poor worker involvement have all been identified as features of a safety climate that inhibit workers’ willingness to proactively identify risks ( Rundmo, 2000 ; Zohar and Luria, 2005 ). Therefore, promoting these organizational factors was needed to encourage workers to identify hazards and prevent incidents ( Pinto et al., 2011 ). When first rolling out their FLRA process, Solvay management knew that if they were going to transform safety practices at the mine, there had to be open communication between hourly and salary workers about site conditions and practices ( Fiscor, 2015 ; Heiser and Vendetti, 2015 ; Neal and Griffin, 2006 ; Reason, 1998 ; Rundmo, 2000 ; Wold and Laumann, 2015 ; Zohar and Luria, 2005 ). They discussed preparing themselves to be “exposed” to such information and commit as a group to react in a way that would maintain buy-in, use and behavior.
Creating a process of open sharing meant that, especially at the outset, management was likely to hear things that they didn’t necessarily want to hear. Despite perhaps not wanting to hear feedback against a policy in place or attitude of risk acceptance, all levels of management wanted to communicate their understanding for changing risks and hazards, and the need to sometimes adapt policies in place based on changing energies in the environment, as revealed by the FLRAs that the workers were taking time to complete. The following case example showcases the value of ongoing communication to maintain a risk assessment program and buy-in from workers.
Case example: Illustrating flexibility with site procedures
During the visit, managers and workers both discussed the conscious efforts made during group meetings and one-on-one interactions to improve their organizational leadership and communication, noting the difficulty of incorporating the FLRA as a complement to existing rules and regulations on site: “We needed to continually stress the importance of utilizing the risk assessment tool, and if something were to occur, to evaluate the level of controls implemented during a reassessment of the task.” To encourage worker accountability, the managers wanted to show their commitment to the FLRA process and that they could be flexible in changing a rule or policy if the risk assessment showed a need. As an example, they showed NIOSH a “general isolation” procedure about lock-out/tag-out that was distributed at their preshift safety meeting that morning. They handed out a piece of paper saying that, “While a visual disconnect secured with individual locks is always the preferred method of isolation, there are specific isolation procedures for tasks unique to underground operations.” The handout went on to state: “In rare circumstances, when a visual disconnect with lock is not used and circumstances other than those specifically identified are encountered, a formal documented risk assessment will be performed. All potential energies will be identified and understood, every practical barrier at the appropriate level will be identified and implemented, and the foreman in charge of the task will approve with his/her signature prior to performing the work. All personnel involved in the job or task must review and understand the energies and barriers implemented prior to any work being performed…”
This example shows the site’s commitment to risk assessment while also showing that, if leading indicators are identified, a policy can be changed to avoid a potential incident. Noting that they would change a procedure if workers identified something, the document illustrated management’s confidence and value in the FLRA process. Workers indicated that these behaviors are a support mechanism for them and their hazard identification efforts. Along the same lines, the managers we talked with noted the importance of not just training to procedure but also to emphasize: “High-level policies complement but don’t drive safety.” This example showcases their leadership and communicative commitment.
The lock-out/tag-out example is just one safety share that occurred at a preshift meeting. These shares “might be no more than five minutes, they might go a half-hour, but they’re allowed to take as long as they need,” one manager said. This continued commitment to foster the use of leading indicators to support a health and safety management program has shown that the metrics used to assess risks are only as good as the response to those metrics to support and encourage health and safety as well as afforded workers an opportunity to engage in improving the policies and rules on site. This continued consistency in communication helped to create a sense of ownership among workers, which led them to recognize the need for a minute-to-minute thought process that helped them foresee consequences, probabilities, and deliberate different response options. As one manager said, “You can have a defined plan but an actual risk assessment shows the dynamics of a situation and allows different plans to emerge.”
Limitations and conclusions
The purpose of this paper was to illustrate an example in which everyone could participate to identify leading safety indicators. In everyone’s judgment, it took about four to five years until Solvay actually saw the change in action, meaning that the process was sustained by workers and they were using the risk assessment terminology in their everyday discussions. In addition to providing how leading indicators can be developed or look “in action,” this paper advanced the discussion to provide insight into common barriers to risk assessment, and potential responses to these barriers. As Figs. 1 and and2 2 show, incidents had been down at Solvay since the implementation of the FLRA program and enhanced leadership training of frontline supervisors, showing the impact of the FLRAs as a strong leading indicator for health and safety. Additionally, hourly workers discussed how much better the culture is on site now than it was several years ago, noting their appreciation for having a common language on site to communicate about risks. It is rare that both sides — hourly and salary — see benefits in a written tool from an operational and behavioral standpoint. The cooperation on site speaks to the positive attributes discussed within this case study and mini examples provided that cannot be shown in a graph.
Although the results of this study are only part of a small case study and cannot be generalized across the industry, data support the argument that poor leadership and an overall lack of trust on site can inhibit workers’ willingness to participate in risk measurement, documentation and decision-making. Obviously, the researchers could not talk with every worker and manager present on site, so not all opinions are reflected in this paper. However, the consistency in messages from both levels of the organization showed saturation of insights that reflect the impact of the FLRAs. It is acknowledged that some of this information may already be known and utilized by mine site leadership. However, because the focus of the study was not only on the development and use of specific risk measurement tools, but the organizational practices that are needed to foster such proactive behavior, the results provide several potential areas of improvement for the industry in terms of formal risk assessment over a period of time.
In lieu of these limitations, mine operators should consider this information when interpreting the results in terms of (1) how to establish formal risk assessment on site, especially when trying to identify and mitigate hazards, (2) what the current mindset of frontline leadership may be and how they could support (or hinder) such an risk assessment program and (3) methods to consistently support a participatory risk assessment program. Gaining an in-depth view of Solvay’s own health and safety journey provides expectations and a possible roadmap for encouraging worker participation in risk management at other mine sites to proactively prevent health and safety incidents.
Acknowledgments
The authors wish to thank the Solvay Green River operation for its participation and cooperation in this case study and for openly sharing their experiences.
The findings and conclusions in this paper are those of the authors and do not necessarily represent the views of NIOSH. Reference to specific brand names does not imply endorsement by NIOSH.
Contributor Information
E.J. Haas, Lead research behavioral scientist and research behavioral scientist, respectively, National Institute for Occupational Safety and Health, Pittsburgh, PA, USA.
B.P. Connor, Lead research behavioral scientist and research behavioral scientist, respectively, National Institute for Occupational Safety and Health, Pittsburgh, PA, USA.
J. Vendetti, Manager, mining operations, Solvay Soda Ash & Derivatives North America, Green River, WY, USA.
R. Heiser, CSP, Mine production superintendent, Solvay Chemicals Inc., Green River, WY, USA.
- Apeland S, Aven T, Nilsen T. Quantifying uncertainty under a predictive epistemic approach to risk analysis. Reliability Engineering and System Safety. 2002; 75 :93–102. https://doi.org/10.1016/s0951-8320(01)00122-3 . [ Google Scholar ]
- Bartram J. Water safety plan manual: step-by-step risk management for drinking-water suppliers. World Health Organization; Geneva: 2009. [ Google Scholar ]
- Blumenstein D, Ferriter R, Powers J, Reiher M. Accidents – The Total Cost: A Guide for Estimating The Total Cost of Accidents. Western Mining Safety and Health Training and Translation Center, Colorado School of Mines, Mine Safety and Health Program technical staff. 2011 http://inside.mines.edu/UserFiles/File/MSHP/GuideforEstimatingtheTotalCostofAccidentspercent20FINAL(8-10-11).pdf .
- Boyatzis RE. Transforming Qualitative Information: Thematic Analysis and Code Development. Sage; Thousand Oaks, CA: 1998. [ Google Scholar ]
- Boyle T. Health And Safety: Risk Management. Routledge; New York, NY: 2012. [ Google Scholar ]
- Brun W. Cognitive components in risk perception: Natural versus manmade risks. Journal of Behavioral Decision Making. 1992; 5 :117–132. https://doi.org/10.1002/bdm.3960050204 . [ Google Scholar ]
- Corbin J, Strauss A. Basics of Qualitative Research. 3. Sage; Thousand Oaks, CA: 2008. [ Google Scholar ]
- Denzin NK, Lincoln YS. The discipline and practice of qualitative research. In: Denzin NK, Lincoln YS, editors. Handbook of Qualitative Research. 2. Sage; Thousand Oaks, CA: 2000. pp. 1–28. [ Google Scholar ]
- Dohmen T, Falk A, Huffman D, Sunde U, Schupp J, Wagner GG. Individual risk attitudes: measurement, determinants, and behavioral consequences. Journal of the European Economic Association. 2011; 9 (3):522–550. https://doi.org/10.1111/j.1542-4774.2011.01015.x . [ Google Scholar ]
- Fiscor S. Solvay implements field level risk assessment program. Engineering and Mining Journal. 2015; 216 (9):38–42. [ Google Scholar ]
- Flick U. An Introduction to Qualitative Research. Sage; Thousand Oaks, CA: 2009. [ Google Scholar ]
- Fram SM. The constant comparative method outside of grounded theory. The Qualitative Report. 2013; 18 (1):1–25. [ Google Scholar ]
- Glaser B, Strauss A. The Discovery of Grounded Theory. Adeline; Chicago, IL: 1967. [ Google Scholar ]
- Golub A. Decision Analysis: An Integrated Approach. Wiley; New York, NY: 1997. [ Google Scholar ]
- Haas EJ, Yorio P. Exploring the state of health and safety management system performance measurement in mining organizations. Safety Science. 2016; 83 :48–58. https://doi.org/10.1016/j.ssci.2015.11.009 . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Haas EJ, Willmer DR, Cecala AB. Formative research to reduce mine worker respirable silica dust exposure: a feasibility study to integrate technology into behavioral interventions. Pilot and Feasibility Studies. 2016; 2 (6) https://doi.org/10.1186/s40814-016-0047-1 . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Hallenbeck WH. Quantitative Risk Assessment for Environmental and Occupational Health. 2. Lewis Publishers; Boca Raton, NY: 1993. [ Google Scholar ]
- Haslam C, O’Hara J, Kazi A, Twumasi R, Haslam R. Proactive occupational safety and health management: Promoting good health and good business. Safety Science. 2016; 81 :99–108. https://doi.org/10.1016/j.ssci.2015.06.010 . [ Google Scholar ]
- Heiser R, Vendetti JA. Field Level Risk Assessment - A Safety Culture. Longwall USA Exhibition and Convention; June 16, 2016; Pittsburgh, PA. 2015. [ Google Scholar ]
- Hokstad P, Røstum J, Sklet S, Rosén L, Lindhe A, Pettersson T, Sturm S, Beuken R, Kirchner D, Niewersch C. Deliverable No. D 4.2.4. Techneau; 2010. Methods for Analysing Risks of Drinking Water Systems from Source to Tap. [ Google Scholar ]
- International Council on Mining & Metals. Overview of Leading Indicators For Occupational Health And Safety In Mining. 2012 Nov; https://www.icmm.com/en-gb/publications/health-and-safety/overview-of-leading-indicators-for-occupational-health-and-safety-in-mining .
- International Electrotechnical Commission. IEC 300-3-9. Geneva: 1995. Dependability Management – Risk Analysis of Technological Systems. [ Google Scholar ]
- Jou Y, Lin C, Yenn T, Yang C, Yang L, Tsai R. The implementation of a human factors engineering checklist for human–system interfaces upgrade in nuclear power plants. Safety Science. 2009; 47 :1016–1025. https://doi.org/10.1016/j.ssci.2008.11.004 . [ Google Scholar ]
- Juglaret F, Rallo JM, Textoris R, Guarnieri F, Garbolino E. New balanced scorecard leading indicators to monitor performance variability in OHS management systems. In: Hollnagel E, Rigaud E, Besnard D, editors. Proceedings of the fourth Resilience Engineering Symposium; June 8–10, 2011; Sophia-Antipolis, France, Presses des Mines, Paris. 2011. pp. 121–127. https://doi.org/10.4000/books.pressesmines.1015 . [ Google Scholar ]
- Kitchener M. Mobilizing the logic of managerialism in professional fields: The case of academic health centre mergers. Organization Studies. 2002; 23 (3):391–420. https://doi.org/10.1177/0170840602233004 . [ Google Scholar ]
- Lindhe A, Sturm S, Røstum J, Kožíšek F, Gari DW, Beuken R, Swartz C. Deliverable No. D4.1.5g. Techneau; 2010. Risk Assessment Case Studies: Summary Report. https://www.techneau.org/fileadmin/files/Publications/Publications/Deliverables/D4.1.5g.pdf . [ Google Scholar ]
- Markowski A, Mannan S, Bigoszewska A. Fuzzy logic for process safety analysis. Journal of Loss Prevention in the Process Industries. 2009; 22 :695–702. https://doi.org/10.1016/j.jlp.2008.11.011 . [ Google Scholar ]
- Maniati M. The Business Benefits of Health and Safety: A Literature Review. British Safety Council; 2014. https://www.britsafe.org/media/1569/the-business-benefits-health-and-safety-literature-review.pdf . [ Google Scholar ]
- Mine Safety and Health Administration (MSHA) Data & Reports. U.S. Department of Labor; 2017. https://www.msha.gov/data-reports . [ Google Scholar ]
- Navon R, Kolton O. Model for automated monitoring of fall hazards in building construction. Journal of Construction Engineering and Management. 2006; 132 (7):733–740. https://doi.org/10.1061/(asce)0733-9364(2006)132:7(733) [ Google Scholar ]
- Neal A, Griffin MA. A study of the lagged relationships among safety climate, safety motivation, safety behavior, and accidents at the individual and group levels. Journal of Applied Psychology. 2006; 91 (4):946–953. https://doi.org/10.1037/0021-9010.91.4.946 . [ PubMed ] [ Google Scholar ]
- Pattson MQ. Qualitative Research and Evaluation Methods. 3. Sage; Thousand Oaks, CA: 2002. [ Google Scholar ]
- Pinto A, Nunes IL, Ribeiro RA. Occupational risk assessment in construction industry – Overview and reflection. Safety Science. 2011; 49 :616–624. https://doi.org/10.1016/j.ssci.2011.01.003 . [ Google Scholar ]
- Reason J. Achieving a safe culture: Theory and practice. Work & Stress. 1998; 12 (3):293–306. https://doi.org/10.1080/02678379808256868 . [ Google Scholar ]
- Reason J. A Life in Error: From Little Slips to Big Disasters. Ashgate Publishing; Burlington, VT: 2013. [ Google Scholar ]
- Robson LS, Clarke JA, Cullen K, Bielecky A, Severin C, Bigelow PL, Mahood Q. The effectiveness of occupational health and safety management system interventions: a systematic review. Safety Science. 2007; 45 (3):329–353. https://doi.org/10.1016/j.ssci.2006.07.003 . [ Google Scholar ]
- Rosén L, Hokstad P, Lindhe A, Sklet S, Røstum J. Generic Framework and Methods for Integrated. Water Science and Technology. 2006; 43 :31–38. [ Google Scholar ]
- Ruan D, Liu J, Carchon R. Linguistic assessment approach for managing nuclear safeguards indicators information. Logistics Information Management. 2003; 16 (6):401–419. https://doi.org/10.1108/09576050310503385 . [ Google Scholar ]
- Rundmo T. Safety climate, attitudes and risk perception in Norsk Hydro. Safety Science. 2000; 34 (1):47–59. https://doi.org/10.1016/s0925-7535(00)00006-0 . [ Google Scholar ]
- Smith SP, Harrison MD. Measuring reuse in hazard analysis. Reliability Engineering & System Safety. 2005; 89 (1):93–104. https://doi.org/10.1016/j.ress.2004.08.010 . [ Google Scholar ]
- Suijs J. Cooperative Decision-Making Under Risk. Kluwer Academic Publishers, Springer Science+Business Media New York; NY: 1999. [ Google Scholar ]
- Van Ryzin J. Quantitative risk assessment. Journal of Occupational and Environmental Medicine. 1980; 22 (5):321–326. https://doi.org/10.1097/00043764-198005000-00004 . [ PubMed ] [ Google Scholar ]
- Wold T, Laumann K. Safety management systems as communication in an oil and gas producing company. Safety Science. 2015; 72 :23–30. https://doi.org/10.1016/j.ssci.2014.08.004 . [ Google Scholar ]
- World Health Organization. Recommendations. 3. Vol. 1. World Health Organization; Geneva: 2008. Guidelines for Drinking-Water Quality [Electronic Resource]: Incorporating First and Second Addenda. [ Google Scholar ]
- Wrede S. How country matters: Studying health policy in a comparative perspective. In: Bourgeault I, Dingwall R, de Vries R, editors. The SAGE Handbook of Qualitative Methods in Health Research. Sage; Thousand Oaks, CA: 2013. [ Google Scholar ]
- Yin RK. Case Study Research: Design and Methods. 5. Sage; Thousand Oaks, CA: 2014. [ Google Scholar ]
- Yorio PaL, Willmer DR. Explorations in Pursuit of Risk-Based Health and Safety Management Systems. SME Annual Conference & Expo; Feb. 15–18, 2015; Denver, CO: Society for Mining, Metallurgy & Exploration; 2015. [ Google Scholar ]
- Zohar D, Erev I. On the difficulty of promoting workers’ safety behaviour: Overcoming the underweighting of routine risks. International Journal of Risk Assessment and Management. 2006; 7 (2):122–136. https://doi.org/10.1504/ijram.2007.011726 . [ Google Scholar ]
- Zohar D, Luria G. A multilevel model of safety climate: cross-level relationships between organization and group-level climates. Journal of Applied Psychology. 2005; 90 (4):616–628. https://doi.org/10.1037/0021-9010.90.4.616 . [ PubMed ] [ Google Scholar ]

Chipotle Case Study: Either Manage Risk or Disclose Lack of Risk Management
Steven Minsky | Feb. 9, 2016
Back in 2009, we blogged about the SEC’s decision to require board-level accountability for ERM . This decision was based on the conclusion that inadequate risk management allowed the regulatory failures that ultimately led to the financial crisis. As we wrote in that post, “boards are now required by the SEC to report in-depth on how their organizations identify risk, set risk tolerances, and manage risk/reward trade-offs throughout the enterprise.”
That blog detailed an important ruling: it refers not only to integrated risk management competency at the executive level, but at all employee levels that have an impact on company performance. This perfectly mirrors a risk management mantra – risk should make up a part of everyone’s – not just risk managers’ – job description.
In 2007 , regulators released Sarbanes-Oxley Audit Standard 5 (SOX AS5), which holds management accountable for the risk of misstated company financials. The SEC disclosure rule is similar in the sense that it uses materiality, not specific risks, as a measure of what needs to be mitigated. It differs, however, in the sense that it applies to all risks, not only financial concerns, and does not take into account an organization’s size. In other words, everyone should be concerned with ERM compliance.
This leads to a fork in the road; organizations need to either adopt an effective risk management program or bite the bullet and disclose their ineffectiveness. There is no third option – maintaining ineffective risk management tools without disclosure is considered negligence, and is easier to prove than fraud is.
Chipotle’s recent fiasco demonstrates the results of poor risk management
According to Business Insurance , Chipotle’s problems don’t end with a host of recent salmonella outbreaks, which have been linked to food sold in numerous branches. The company also “failed to disclose that its ‘quality controls were inadequate to safeguard consumer and employee health,’ according to a civil lawsuit.”
The company is now suffering a major reduction in share prices (“35% since the end of October”), reduced sales (December sales were down 30% in some locations), and a marred reputation that relies upon the appeal of safe, sustainably grown food. The manner in which the company misled shareholders is almost entirely responsible for the civil suit.
Chipotle introduced a great innovation in the food industry: fresh, healthy, locally sourced fast food. However, the company failed to implement the risk management necessary to support that innovation. Enterprise risk management is as much about enabling innovation as it is about facilitating compliance, health, and safety. The check-the-box approach of disclosing the “usual risks” was made unacceptable back in 2010, if ever it was acceptable. Every business innovates, and every business therefore needs to find the unique risks it introduces, get them covered, and disclose them to shareholders.
Had Chipotle’s management implemented an enterprise risk management solution, either of two outcomes would have occurred:
- Food might never have been contaminated, since ERM extends to a robust vendor risk management methodology that helps identify risks associated with a company’s supply chain.
- Even if the outbreaks had still happened, Chipotle would have been able to use enterprise risk management reporting capabilities to evidence its risk program. This would have avoided regulatory penalties, provided evidence of control activities, and guided risk disclosure, all of which would have eliminated liability for non-disclosure of risk.
These outcomes aren’t just possible, they’ve happened before . In 2009, a Morgan Stanley executive was found to have evaded internal controls. The company itself avoided prosecution thanks to the robustness of its internal policies and procedures. Unlike Chipotle, Morgan Stanley “maintained a system of internal controls meant to ensure accountability,” and pointed to these systems when asked about the adequacy of its risk management program.
There is never a 100-percent guarantee that surprises won’t happen. Sometimes, human error and external threats can’t be predicted. What’s important is minimizing the likelihood of those surprises, and ERM software accomplishes just that. At the very least, a robust, well-documented solution provides an easy way for organizations to maintain full disclosure and avoid regulatory action.
Adopt Risk-Based Vendor Management
We look at actions you can take that will help streamline your vendor management process in this webinar!
My Favorites List
Submit your Favorites List and our experts will reach out to you with more information. You will also receive this list as an e-mail which you can share with others. Here are the solutions you've added to your list so far:
- Skip to Content

Advertisement: Certified CEO Program
- Business Basics
- Business IT
- Finance And Risk
- Growing Your Business
- Managing People
- Personal Success
- Meet Some Of Our Contributors
- Business Books
- Purchase Audio Seminar Series
- Certified Manager Program
- Certified CEO Program
- Top CEO Issues
- Business Book Summaries
- Audio Seminar Library
- Business Book Extracts
- Learning Modules
- Video Seminars
- How IIDM CPD Works
- IIDM Knowledge Units
- Certification - CEOs, Senior Executives & Managers
- Approved Certification Courses
- Certified CPD Reporting
Advertisement: Join IIDM
Advertisement: register for newsletter, advertisement: cpd small top, risk management case studies.

Mitigating Risk
As John Curnow inherited $7million of debt when he became CEO of three advertising agencies during the global financial crisis, he has given a lot of thought to risk mitigation. Now, as Founder and Managing Director of Virtual Ad Agency (VAA), his entire business model is based on risk mitigation.
Creative Recovery
Imagine landing a multi-million dollar contract to conduct business in Dubai - then not getting paid for the work you've done. Discover how one entrepreneur is using the lessons learnt from this experience to rebuild his company bigger, better and stronger after a complete collapse.
Under Pressure
What would you do if your bank cancelled your short-term finance facility just as you had landed three new contracts? Now imagine that happening between Christmas and New Year. Welcome to Paul Newbound’s nightmare.
Medals Of Honour
Two Defence Force Academy graduates have been successfully applying their military training to a corporate assault on the project management sector.
Startup Decompression
An innovative R&D start-up is fighting a classic battle that faces most brilliant youngsters: turning intellectual property into a cash-flowing business.
Sweet Harvest
Setting out to challenge a dominant market player became a whole lot harder when a new fruit-processing business ran into cashflow problems.
Armor-Plated Business
A Sydney inventor uses technology to strengthen his glass and mentors to reinforce his management weaknesses.
The Case For Safety
The cost of not maintaining a safe workplace can be injured workers and criminal action against directors.
How To Make Good Ideas Pay
A New Zealand research commercialiser says the new-idea business is all about experience, contacts and patent defence.
Keeping The Thief From Your Door
Police can no longer cope with theft from workplaces. Two experts tell how to avoid the problem in the first place.
Work Safety Begins Before The Work Starts
When Des Walters won a contract to provide dive services for a major construction project, he knew his company's reputation would depend on keeping workers safe.

Featured Article 1
A fresh approach to leading today's sales teams.

7 Types Of Self-care That Every Business Leader Should Be Mindful Of

Featured Articles

Why Tapping Into The Power Of A Growth Mindset Boosts Performance

Six Steps To Less Stress And More Balance

- Terms of Use
- Advertise With Us
- Testimonials
Copyright © 2024 International Institute of Directors and Managers ABN 26 112 140 299. All rights reserved.
A Case Study of Introducing Security Risk Assessment in Requirements Engineering in a Large Organization
- Original Research
- Open access
- Published: 27 June 2023
- Volume 4 , article number 488 , ( 2023 )
Cite this article
You have full access to this open access article

- Shanai Ardi 1 ,
- Kristian Sandahl ORCID: orcid.org/0000-0002-3052-5604 2 &
- Mats Gustafsson 1
3069 Accesses
Explore all metrics
Software products are increasingly used in critical infrastructures, and verifying the security of these products has become a necessary part of every software development project. Effective and practical methods and processes are needed by software vendors and infrastructure operators to meet the existing extensive demand for security. This article describes a lightweight security risk assessment method that flags security issues as early as possible in the software project, namely during requirements analysis. The method requires minimal training effort, adds low overhead, and makes it possible to show immediate results to affected stakeholders. We present a longitudinal case study of how a large enterprise developing complex telecom products adopted this method all the way from pilot studies to full-scale regular use. Lessons learned from the case study provide knowledge about the impact that upskilling and training of requirements engineers have on reducing the risk of malfunctions or security vulnerabilities in situations where it is not possible to have security experts go through all requirements. The case study highlights the challenges of process changes in large organizations as well as the pros and cons of having centralized, distributed, or semi-distributed workforce for security assurance in requirements engineering.
Similar content being viewed by others

A Security Requirement Engineering Case Study: Challenges and Lessons Learned

Identifying Security Requirements Body of Knowledge for the Security Systems Engineer

Risk-Based Elicitation of Security Requirements According to the ISO 27005 Standard
Avoid common mistakes on your manuscript.
Introduction
Many software products are used in sensitive infrastructures where software malfunctions or security vulnerabilities can have significant consequences. Various factors like increased digitalization and geopolitical tensions contribute to the challenges faced by software vendors and result in a significant increase of exposure of software products and an increased risk that an adversary can take advantage of the situation. The increase in exposure and attack surface means that individuals and organizations need to deal with a higher risk to any asset they value in the cyber world.
To mitigate such risks, governments and legislators place ever-increasing demands for security assurance on infrastructure operators and equipment and system vendors, which requires these actors to review and strengthen their processes and methods extensively.
Requirements engineering is one of the earliest phases in the software development life cycle in which software vulnerabilities can be introduced into software products if requirements specifications are inadequate. In recent years, efforts have been made to integrate security risk assessment into requirements engineering activities [ 1 , 2 , 3 , 4 , 5 , 6 , 7 ]. The expected benefit from this is that exposing potential risks early in the requirement engineering phase allows more time for finding solutions to manage the risk. Failure to identify risk in this phase will decrease the overall probability of detecting and preventing vulnerabilities in the product with acceptable costs.
Defining the security objectives of a software product, identifying threats to system assets, estimating the risk level caused by identified threats, and coming up with countermeasures are crucial steps in the process of correctly defining the requirements that will ensure the security of a software product.
Security risk assessment is one of the well-known security activities that is recommended by several software security approaches [ 8 , 9 , 10 , 11 , 12 , 13 , 14 , 15 ] and is a common denominator of several security standards [ 16 , 17 , 18 ]. Getting an understanding of the involved risks by understanding the involved threat models [ 14 ] and problems related to the use cases and misuse cases [ 5 ] enables early detection of potential issues. This understanding also provides a rationale for security-related decisions and for security activities designed and introduced to address security issues.
One common characteristic of most existing approaches is that the assessment activities are performed through heavyweight activities that in many cases are validated in theoretical case studies [ 11 , 19 ]. However, such approaches often turn into key challenges for software vendors that operate using a development context characterized by:
Many small feature-oriented teams;
Teams of developers working according to agile methods and with only basic security knowledge;
Frequent iterations, each comprising a limited number of requirements at a low level of abstraction.
To reconcile the apparent conflict between lean and agile development practices on one side, and traditional heavyweight risk assessment practices on the other, we need to seek out, introduce, and evaluate new practices. Introducing a new method often involves adoption of new technology, changes in work practices, and an additional workload [ 20 ]. This can lead to an acceptance issue for the proposed changes. This issue is especially magnified when competing goals and quality factors must be considered when specifying, designing, and implementing new software solutions. Since these requirements often do not add to functionality, development teams tend to lower their priority to meet deadlines [ 21 ].
Another aspect we have focused on is the challenge of ensuring access to adequate security expertise and security competence. It is widely understood in security community that the basis for security assurance is security awareness among all members of a development organization [ 1 , 2 ]. Considering the increased need for security in software products, the demand for competent expert support and building strong cybersecurity teams in organizations is increasing globally. This has resulted in a security skills gap that is getting bigger every year, according to the International Information System Security Certification Consortium (ISC)2. For these reasons, it is crucial for software and information system vendors to utilize existing cybersecurity expertise to meet cybersecurity requirements.
Forming a central security team to ensure that security activities are handled well has been recommended by several researchers [ 2 , 5 ], but this can introduce bottlenecks, especially in large organizations developing complex products. At the same time, security awareness among developers of a product is the basis for ensuring the security assurance of that product. This poses a knowledge management challenge in the sense that security experts, generally a scarce resource, need to support an often large community of requirements engineers, who are the specialists in the details of the different layers of abstraction in the product. It is usually the case that knowledge about the lowest level of detail is found in development teams. They, not the security experts, are also responsible for implementing and keeping track of the fulfillment of the requirements. The remaining challenge is to find a proper distribution of responsibility between security experts and developers for performing security-related activities.
Another perspective we have included in our approach is to consider security risks associated with requirements in general. This breaks with the traditional mindset in the software development community of considering security separately in requirements engineering and of classifying security requirements as a subgroup of software requirements. Most software requirements are developed in terms of what must happen, but security requirements are driven by a need to mitigate risks and threats to system assets and must be specified in terms of what must not be allowed to happen [ 22 ]. Various methods for eliciting, analyzing, and specifying security requirements have been proposed by researchers [ 22 , 23 , 24 ]. However, identifying concrete advice for immediate deployment of such methods by software vendors is still challenging, especially in the complex context of large-scale software engineering [ 25 , 26 ].
Most contemporary methods use risk assessment for security requirements engineering by focusing primarily on the risks involved with stakeholder goals and/or system-level risks introduced by functional requirements and identifying non-functional security requirements [ 8 , 9 , 10 , 11 , 12 ]. This is vital, but we believe that security cuts across abstraction levels and is also a concern at lower levels of detail in the design of a product. We have seen examples wherein vulnerabilities are introduced into a design at the lowest abstraction levels, as shown in the example presented in in this article.
Based on all above-mentioned considerations this article aims at supporting software vendors by proposing a lightweight security risk assessment method to be applied during requirements engineering phase. The technical contribution presented in this article is consisting of getting high-level product requirements, breaking them down to lower abstraction levels (functionalities) during requirement engineering phase and performing a lightweight security risk assessment to fine-tune the functional requirements to address possible security risks. The security fine-tuned requirements then are used in design and implementation (iteratively or depending on the software development process) reducing the probability of introducing associated risks into the end product. In this contribution, we also experiment the pros and cons of performing these activities by security experts in one end vs requirement engineers in the other end (see Fig. 1 ).
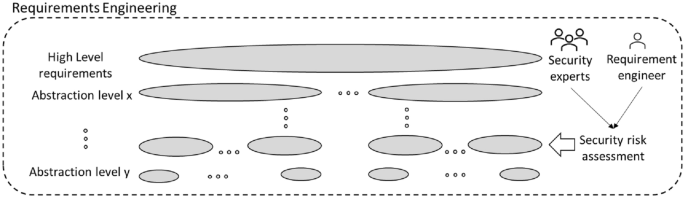
High-level view of the technical approach
We focus on the challenges with the utilization of security competence and through a longitudinal case study evaluate the introduction of our security risk assessment method in a large-scale industrial setting to answer the following research questions:
What are the difficulties of introducing a security risk assessment method in a big organization that is developing complex systems?
When performing security risk assessment, can we bridge the gap between security experts and requirement engineers who are not specialized in security? In that case, what is an efficient distribution of tasks between security experts and requirement engineers?
What are the considerations (introduction or training) needed for engineers to achieve acceptable results?
The remainder of the article is as follows: in section “ Security Risk Assessment ” we provide a thorough description of our lightweight risk assessment method, security risk assessment (SRA). Section “ Case Study ” contains a description of the case study of the introduction of SRA in a large infrastructure development organization is presented in Section “ Case Study ”. A discussion around findings from the case study and a survey of related work are provided in section “ Discussion ” and section “ Related work ”, respectively.
Security Risk Assessment
In this section, we present the SRA method and how it is applied during requirements engineering. The SRA method is designed considering the complexity of the product to be developed and aims at providing a simple method for requirement engineers who are not specialized in security to get better understanding of security risks.
The inputs to the SRA method are requirements that emanate directly from customer requests for added functionality and/or from updates and improvements proposed by developers working on the product. Product managers receive customer requirements that are usually goal-like at a product strategy level. Requirement engineers study these requirements, check their feasibility, priority, and the cost of implementation, break them down to requirements in lower abstraction, and define well-defined and testable requirements that initiate the development project and lead to implementation of the required functionality in the final product.
We use the requirement abstraction model (RAM) by Gorschek et al. [ 27 ] and define four abstraction levels for requirements: product level, feature level, function level, and component level. Product level is the most abstract level and is comparable directly to the product strategies and indirectly to the organizational strategies. An example of a product-level requirement could be “the system shall provide intrusion detection support”. Feature-level requirements are features that the product should support and are an abstract description of the feature itself. An example requirement at this level is “the system shall provide the possibility to log and report security-related events”. The function level is, as the name suggests, a repository for functional requirements and describes what a user should be able to perform/do, for example, “users shall be able to subscribe remotely to receive logs of security-related events”. The component level is of a detailed nature containing information that is closer to how something should be solved, i.e., on the boundary of design information [ 27 ], e.g., “the feature state is enabled/disabled by changing the featureState parameter”.
Method Overview
The SRA method is designed, inspired by the definition of risk by Kaplan and Garrick [ 28 ] where the risk is defined by the answers to three questions:
What can go wrong?
How likely is it to go wrong?
If it does go wrong, what are the consequences?
To answer these questions, we need to understand the scenario or undesirable event that may occur during a product’s runtime. As shown in Fig. 2 , the SRA method consists of three main steps: risk assessment content establishment, risk identification and estimation, and requirements analysis and specification. The preliminary assumption is that there is a feature-level requirement as a starting point to use SRA.

Risk assessment content establishment starts with requirements engineering team getting a feature-level requirement and determining if it is possible to be implemented, what the different implementation alternatives are, and what these alternatives would cost. One of these alternative solutions is then chosen after discussion with the product manager and the function-level/detailed requirements are identified and documented. Such requirements are of a detailed nature representing information that is closer to a description of how something will be implemented. At this step, it is crucial to ensure the following factors while establishing the risk assessment content:
Security objectives of the software project are known for the requirements engineering team.
Assumptions in terms of the users of the functionality and the environment in which the feature will function are defined.
Initial security status of the underlying system is known (in the case of incremental development) based on the security risk assessment of the legacy system (performed in previous releases).
Use cases of the feature have been identified.
Requirements engineers are familiar with basic security concepts, such as the three key security requirements for any asset, namely, the CIA criteria: Confidentiality, Integrity and Availability in the context of the system they are working with [ 29 ].
Risk identification and estimation is done by going through every detailed requirement, documented during risk assessment content establishment, and identifying assets involved in the required functionality, system entry points. Additionaly, attention is given to attacker’s capabilities in terms of misusing the functionality, likelihood and impact of functionality misuse, and possible misuse cases involving harm to the identified assets. This is done by answering the following questions:
What is the asset (to be protected) in the detailed requirement? An asset is something that is valuable for the feature, for example, the functionality provided by the feature, any new data introduced, variables, control parameters, interfaces, protocols, and/or anything that is included in the use case of the feature.
Who has access to the asset and how? The goal is to identify the actors that have access to the asset identified in question 1, for example, end users, developers, and any outsider who might have access to certain variables/parameters through system entry points are considered to be actors.
Can the actor/user identified in question 2 misuse the asset? Considering system and environmental assumptions as well as confidentiality, integrity, and availability criteria, can anyone harm the asset (any scenario)?
How difficult is it to harm the asset? What is the probability over a certain period (e.g., 1 year) and what is the impact of harm?
The answers to the above-mentioned questions are used to define the risk level using the matrix in Fig. 3 . The flowchart in Fig. 4 shows the overview of the SRA process including the above-mentioned steps. In the following section, we illustrate the use of SRA in an example..
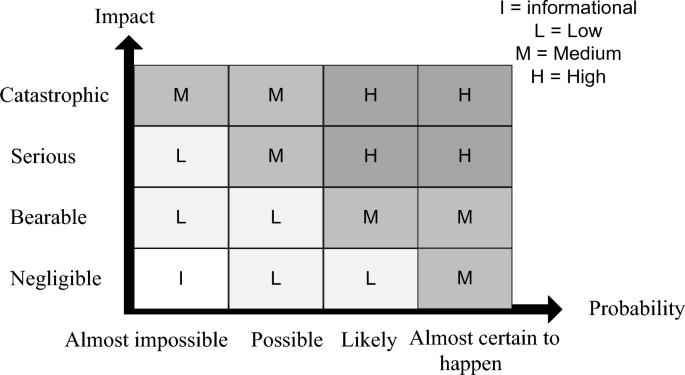
Risk-level matrix
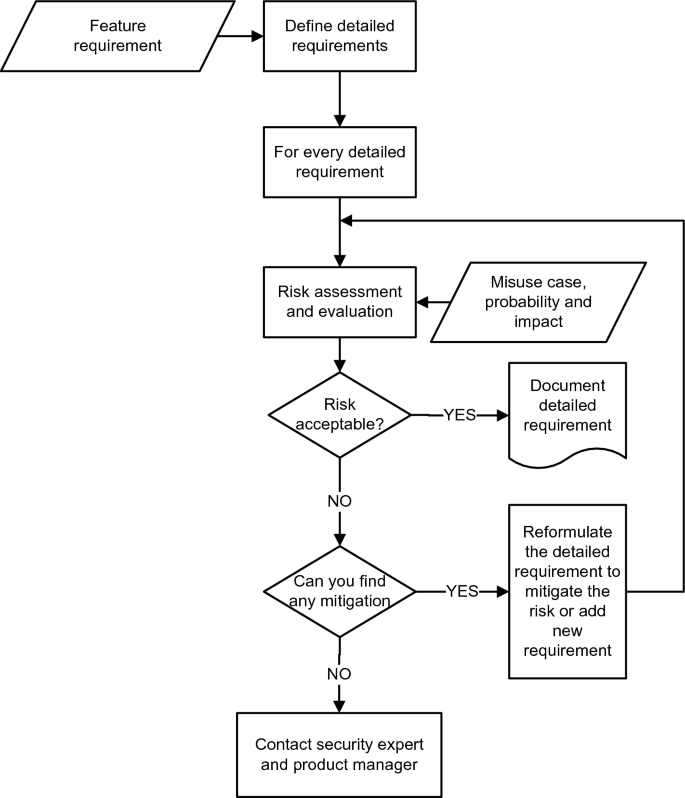
SRA process
Requirement analysis and specification is the last step, where the requirements engineering team uses information of the risks identified for every detailed requirement to fine-tune the use cases covered by the requirement so that the risk would be addressed/prevented. This is done either by reformulating the requirement so that the risk is mitigated, or by defining the corresponding component-level requirements to enforce the risk mitigation.
The flowchart in Fig. 4 shows the overview of the SRA process including the above-mentioned steps. In the following section, we illustrate the use of SRA in an example.
Risk assessment content establishment: Telecom networks consist of several subsystems interacting with each other. These subsystems (nodes) are used by operators to serve their customers (subscribers) with fixed and/or mobile services. The overall system is large and is commercially active over several releases. Consequently, including security in such a system and sustaining security throughout the whole life cycle could be a challenging issue requiring continuous improvements. One example set of features requested by operators is features for self-organizing networks (SON), including self-configuration and self-optimization of the nodes in a telecom network. The self-configuration function enables the network to automatically perform installation procedures (plug and play) on the nodes, and self-optimization enables the network to auto-tune its operational parameters using performance measurements that are either performed by the node itself or received from user equipment (UE) [ 30 ].
One type of functionality that is provided as a part of self-configuration is the automatic neighbor relations (ANR) feature. ANR is a known feature in the telecom industry [ 31 ] for automating operation and maintenance of a specific function (handover functionality) when neighbor nodes provide a telecom service to subscribers jointly. The feature-level requirement in this case is the node shall support ANR functionality .
To initiate the development of this feature, we need to define the detailed requirements at the function level. Some examples of these requirements are presented in Table 1 .
Risk identification and estimation: We start from the first detailed requirement and perform the risk assessment by answering the questions mentioned above.
Detailed Requirement 1
What is the asset? What shall be protected?
Asset: disable/enable functionality of the ANR function on one or multiple nodes.
Who has access to the asset and how?
Operators (who configure the features), using a configuration GUI.
Can the actor/user, identified in the previous question, misuse the asset?
This is not likely since the assumption is that operators will not harm their own products/network.
How difficult is it to harm the asset? What is the probability over a certain time period (e.g., 1 year) and what is the impact of harm?
The probability is “almost impossible”, but the impact is “serious” because the ANR functionality would not be available. According to the matrix in Fig. 3 , this will be a low risk.
Detailed Requirement 2
Asset: ANR measurement results from the selected UE.
End user (using UE).
It is possible that a malicious actor could modify measurement reports.
The probability is “possible” and the impact is “serious”, since the measurement reports are used for certain network planning decisions. This is a medium risk and the requirements engineering team shall revisit the requirement. Depending on the system architecture, there could be different alternatives: for example, if it is possible to get required ANR measurements from a source other than UE the initial design can be modified. If getting measurements via UE is the only way (e.g., as a standard method for all telecom vendors), then an additional requirement shall be defined to validate the received values and minimize the impact of malicious reports.
Detailed Requirement 3
Asset 1: collecting reports functionality.
Asset 2: maximum number of relations (variable).
Developer has access to both assets through the code that implements the functionality and defines the maximum number value.
Only if the implementation is modified, the asset can be misused.
Developer has access to both assets through the code that implements the functionality and defines the maximum number value. The probability is “almost impossible” because the functionality will be tested to ensure that the requirement is fulfilled, and the impact is “serious” since the functionality will not be available and the feature-level requirement will not be fulfilled. This is a low risk according to the risk-level matrix.
Requirement analysis and specification: The results of the risk assessment are shown in Table 2 . This table can be used for residual risk management, helping product managers to decide if the cost of mitigating the risks is acceptable or if the risk is relatively low compared to the mitigation cost and the feature can be delivered as it is. For example, if product management decides to address only the medium risk, it can be addressed in different ways. Example alternatives could be to:
Define a criterion to accept measurement reports from approved UEs and add this as a new detailed requirement. Also adjust detailed requirement 2 to cover the criteria.
Accept the risk of getting untrusted data from some UEs, and to minimize the risk get the reports from more than one UE and compare the values before using them. This will lead to several other detailed requirements.
Note that the table can also be used to track the identified risks during the whole development process. This table is reported as a part of the documentation of the requirement engineering phase.
We introduced the SRA method in a software development process in a telecom company that is developing complex products using agile practices (e.g., Scrum or a combination of other agile flavors). To evaluate the application of SRA and find answers to our research questions, we performed a case study. One reason for choosing a case study as the evaluation method was to study the problem in its context and evaluate how our proposed method was used in this context. Another reason was to develop an understanding on how a process improvement attempt through introduction of SRA was received in real-life industrial setup. The case study context was as follows: the target organization is a large enterprise offering telecom and multimedia solutions in a highly competitive market. The setup of the team is a mix of both co-located and remote workers, distributed in different locations. The company has around a hundred thousand employees and the unit supporting the case study consists of around 150 engineers. The development model is a combination of customer and market-driven processes in the sense that requirements are collected from both existing and potential customers. The market demands highly customized solutions with requirements that are compliant with domain-specific standards. There are dozens of development teams working on the subject project. The project time may vary between 6 and 12 months and the requirements engineering activity may take up to 4 weeks. The projects are integrated with the previous baseline of the system and only one product exists at the time.
The target organization has a security framework that includes security design rules and generic security requirements to be followed and fulfilled during the software development life cycle. Security risk assessment as part of the organizational security framework is performed for all the products in the company portfolio. A central security team consisting of security experts performs security risk assessments on all feature requirements and feeds the findings back to the development process.
We defined the following variables to be studied to answer the research questions:
Deployment of the method in the requirement analysis (during requirements engineering):
Comprehensibility of the documentation introducing the method.
The overhead of applying the method.
Applicability of the method in an industrial setup as explained above in the case study context:
Acceptance by requirements engineers.
Shortcomings and improvement possibilities.
Effects/benefits of applying the method:
Number of identified vs missed risks.
We used a single case study design as defined in [ 32 ], with the telecom company being the overall context and performed the case study in three iterations followed by a final root cause analysis on the findings of the third iteration to identify the way forward, as shown in Fig. 5 and over a period of 4 years. We used the process as described by Runeson et al. to design the case study with a flexible design, based on qualitative data [ 33 ]. The first case started with applying the SRA in a certain context by pilot subjects and the contexts of succeeding cases were adjusted after analyzing the results of the previous cases. The initial state of the iterations was a team of security experts performing the SRA activity. We then examined the consequences of fully distributing this task to non-security-expert requirements engineers, and finally a semi-distributed setup where an SRA forum would perform further analysis of results by requirements engineers if needed.
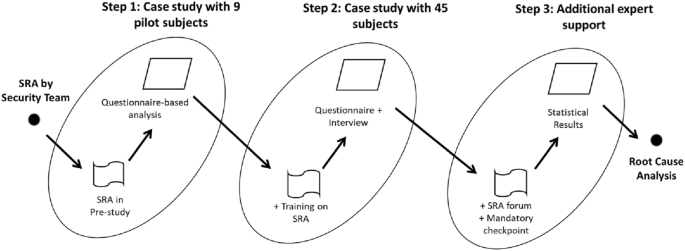
Case study process
For the first iteration, nine pilot subjects were identified using a focus group [ 34 ] of five technical team leaders, who received a presentation of the goal of the case study and, in an open discussion session moderated by the researcher, nominated candidates to be pilot subjects. The selected subjects had deep knowledge of the software product’s architecture and its value to the customers. The subjects worked either alone or in a team of two or more engineers. The subjects applied SRA during requirements engineering activity and answered a questionnaire about method conformance, domain conformance, and general feedback.
Process conformance questions focused on characterization of the method and an assessment of how it is performed. Domain conformance questions focus on learning about subjects’ knowledge concerning security and requirements engineering, and finally to get general feedback for improving the method.
We analyzed the final feedback from pilot subjects, based on the variables we had defined.

Deployment of the Method
An average of 6 h was spent on performing the risk assessment and documenting the requirements and risks. According to six of the participants, analysis time overhead was considered acceptable with respect to the planned time. One of the participants mentioned that it took a long time to perform the analysis and one of the participants answered that the time could vary based on complexity of the feature. Seven participants saw no specific hindrance to deploying the method, and one of the subjects felt that the study team’s lack of security knowledge could be a major hurdle.
Applicability of the Method
All participants found the method beneficial in finding the risks and that it should be used for all requirements. According to all participants, the introduction presentation was enough to start using the method. In the general feedback, one subject was interested in getting a presentation of the existing security capabilities of the system, as this would help system engineers reuse the already existing mechanisms as risk mitigations. Another suggestion was to provide a list of security best practices to be considered by system engineers when, for example, new attributes and new interfaces are introduced by a feature. The example-driven nature of the method was important for understanding the usability of the method, according to one of the participants.
Effects/Benefits of Applying the Method
One of the participants mentioned that even if there might be no or low security risk, the assessment helped in reaching that conclusion. Only one of the participants was already familiar with security topics and for the rest of them it was their first time thinking about security issues. One of the participants found no risk, four of them identified two medium-level risks each, and the rest identified only low-level risks. Based on the results we concluded that the method could help system engineers to consider the security aspects of technical solutions using the proposed method with minimum overhead. All medium-level risks were reported to product managers to discuss a cost-effective mitigation or to be considered in negotiations with customers if required. Two of the risks resulted in new feature-level requirements from product managers and the rest of them were not prioritized in the upcoming release from a business point of view.
Iteration 2: Case Study with 45 Subjects
After the first iteration was completed, the decision was to extend the scope and apply the method to an entire release project, wherein all of the system engineers on that project would apply the method to all of its features in that project.
Subject and Case Selection
The target release project consisted of 45 features to be implemented and integrated into a legacy telecom product. In this iteration, we provided a 1-h training for all system engineers studying these 45 feature requirements to present the security risk assessment method. We also modified the security impact chapter in the mandatory document that was to be written in the pre-study phase. This document describes the systemization of the feature and includes the list of detailed requirements. The security chapter was updated to require that the results of the security risk assessment be documented and reported in the chapter.
Data Collection
We had three sources for data collection. We used a two-step qualitative data collection method in this iteration, which took the form of a questionnaire to be answered by the subjects, followed by individual interviews to get a more in-depth view of the subjects’ opinions. In parallel, all the reports were systematically reviewed by the central security team and the data provided in the security impact chapter were reviewed. The goal was to analyze the outcome of the modifications to the pre-study process and compare the results of the security risk assessments done by the subjects with the results of the same analysis as performed by the central security team. This approach helped to determine whether all the risks had been identified by the subjects. To ensure ethical considerations, all subjects were informed about the purpose of the activity and asked to give consent on the use of their contributions in this research approach. This included the information they provided about their own technical background and experience.
As with the first iteration, the questionnaire included questions about process conformance (PC), domain conformance (DC), and general feedback (GF).
Process conformance (PC) and general feedback (GF)
The questions on PC and GF, which placed more focus on gathering statistical data about the application of the method, were as follows:
(PC) Did you attend training on the method and the new document template?
(PC) Did you use the proposed method?
Yes: describe the differences you see between this template and the old one.
No: why not?
(PC) How long did it take for you to perform the risk analysis on the detailed requirements and document it? How long was the whole study?
(GF) What are the pros and cons you see in this method, as mentioned in the security impact chapter?
(GF) Talk about your opinion regarding any significant problems that might hinder the deployment and use of the method.
(PC) How much training do you think is needed to be able to use the method?
(PC) Did you identify any risk for your feature and what was the level of the risk?
Yes: what did you do with the risks you identified?
No: why do you think you did not identify any risk?
(GF) What are your suggestions to improve the risk analysis method and instruction document?
(GF) Is there anything more you would like to add?
Questions about the subjects’ pre-knowledge in security and their depth of knowledge about the product were handed out in a separate set.
We organized training sessions and presented the SRA method and examples of how to apply it to all subjects. During the roadshow, we also went through the changes applied to the “security impact” chapter in the pre-study report document template.
After the project was closed, the subjects were asked to answer the questionnaire and then invited to a 30 min interview (for each functional requirement). A total of 41 subjects responded to the questionnaire and participated in interviews. The interview sessions were semi-structured [ 34 ] with a mix of open and closed questions. The interview agenda is:
Meeting starts with a presentation of the interviewer.
The interviewer explains the goal of the interview.
The subject is asked to sign the statement of consent to use the data in the research project.
The subject is asked to present information about their own background.
The subject provides information on what the study is about.
The interviewer walks through the answers provided by the subject and takes notes of the reasons for the answers.
The interviewer provides information on how the data will be analyzed.
The notes from each interview were sent to the subject after the interview for a second review.
The questionnaires were printed, and the answers provided by the respondents were independently analyzed and categorized by the three authors. The independent analyses were subsequently compared and reconciled with only minor inconsistencies noted that could all be resolved through a joint review of the interpretation of the answers and clarifications given in the interviews. There were four categories of subjects as shown in Table 3 .
The studies in which the method was applied were of varying complexity and length. One subject reported having spent 5 min out of 3 months, and another reported having spent half a day out of 2 weeks. A majority (18 out of 26) of the subjects that used the method report having spent 2 h or less on applying the method. Four subjects reported having spent more than 2 h. Four subjects did not answer the question about how much time was spent applying the method. The subject spending half a day out of 2 weeks had not attended the roadshow and reported having to overcome a threshold for using the method for the first time.
In the questionnaire, most respondents provided feedback and suggestions for improvements. The most frequent feedback (from more than half of all subjects) contained a suggestion to introduce a concept of “No impact” to be used when a simple review makes it obvious that the change being studied will not introduce new risks. Other common items of feedback were each expressed by about a quarter of the subjects: suggestions to provide more examples of risks as it might occur in different types of system features, a concern over slip-through or that risks might be introduced in later stages of the process, that the context in which risk was to be assessed needed to be better defined, and mention of the use or need for a subject matter expert to complete the assessment.
In the context of knowledge supply, approximately, one-third of the subjects expressed a need for getting expert support when needed and one-third expected improved/additional training.
Other feedback included suggestions for using structured queries, the need for continuous training, and the need to also consider risks holistically at the system level and not just at the feature level.
Among subjects in categories A and C (see Table 3 ) that have applied the method ( n = 26), our analysis shows a generally positive or neutral attitude toward the setup. 14 subjects categorized their impression of the method as ‘worked well’ or ‘worthwhile’, while 5 subjects expressed an opinion of ‘not worthwhile’. The remaining seven subjects that used the method did not state any valuation. See Fig. 6 .
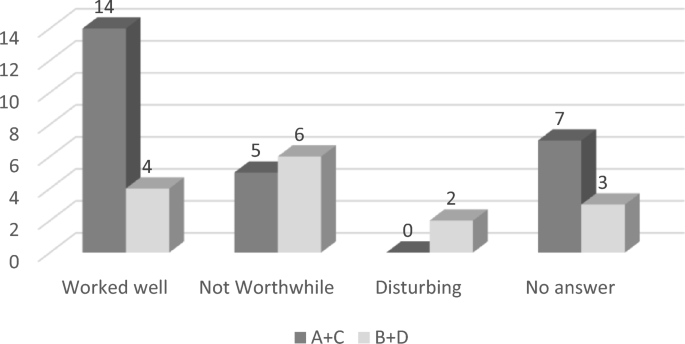
Applicability of the method according to subject categories
Of the 15 subjects in categories B and D who did not apply the method, six found the method ‘not worthwhile’ and two found it somehow disturbing. Four subjects had applied parts of the method and thought it ‘worked well’. The remaining three did not express an opinion about the method.
We analyzed the results to list the risks identified by the subjects. The pre-studies were then reviewed by security experts and the cases where additional risks were listed by security experts were identified. Figure 7 shows the number of risks identified by subjects vs. security experts based on subject categories.
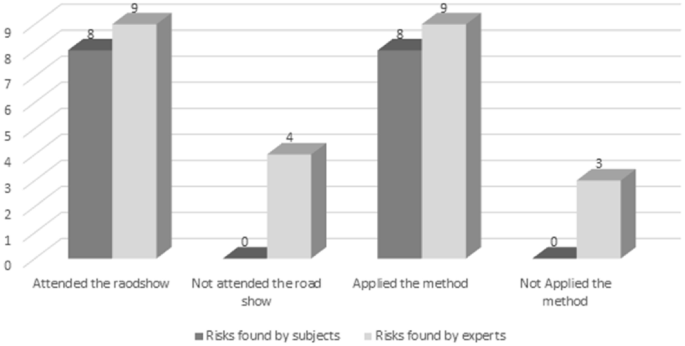
Risks found by subject categories vs. security experts
We also went through the collected data to identify the possible benefits of applying this method regarding increasing security awareness among requirements engineers. We were able to categorize the answers into three main categories as in Fig. 8 :
22 subjects who clearly stated that they had no security background and became aware of security and security issues during this case study.
13 subjects who had at least basic security knowledge prior to the case study, but who also found it useful to be given instructions on how to perform security assessments.
Six subjects who did not have basic security knowledge and it was not evident that the proposed approach and case study affected their security awareness.
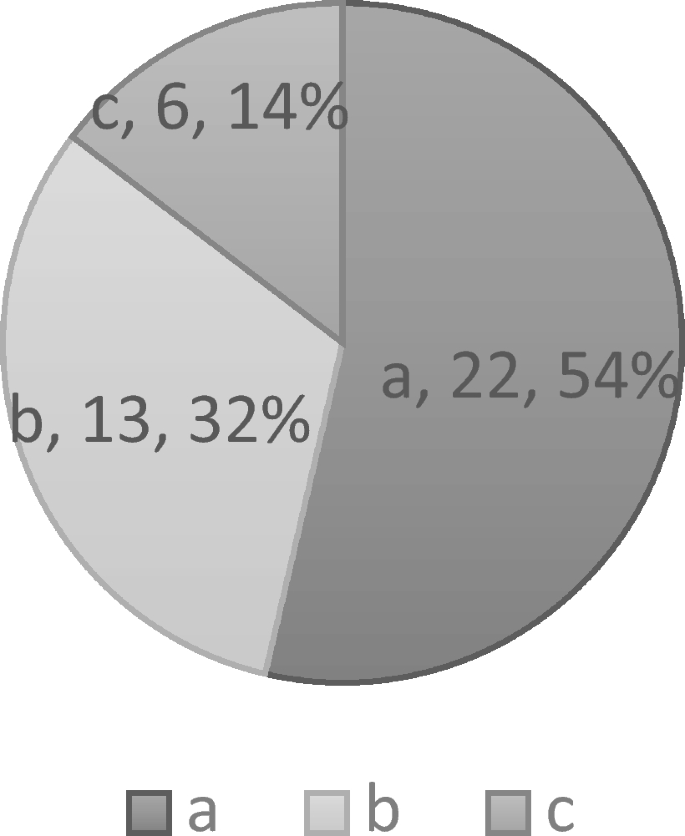
Security awareness categories
Concluding Remarks: Iteration 2
In this study, we observed that those who have participated in the training and tried to use the method found almost the same number of risks as the security experts. The cost of applying the method was acceptable. When the results were presented to the company, two things were concluded:
The value of making early security risk analysis on a detailed level of requirements is high and should be continued.
However, as many subjects indicated, more training and support from security experts were necessary.
Iteration 3: Additional Expert Support
As mentioned earlier, the initial state for starting the process of proposing our approach was risk assessments of implemented features conducted by a central security team consisting of security experts. We then studied the impact of decentralizing this activity to system engineers with no specialization in security. This way of working continued in the same way as in iteration 2 above with more training and dialog with security experts. Feedback was continually collected. As the final step in the third iteration, we modified the proposal to provide security expert support to system engineers performing the risk assessment when needed.
In this iteration, the risk assessment activity was included as a mandatory checkpoint in the pre-study process during requirement analysis and it was defined as a part of the definition of “done” for the pre-studies. This strengthens the requirements on using the method compared to iteration 2. The security expert team was renamed to security risk assessment (SRA) forum and an improved workflow was defined as shown in Fig. 9 .
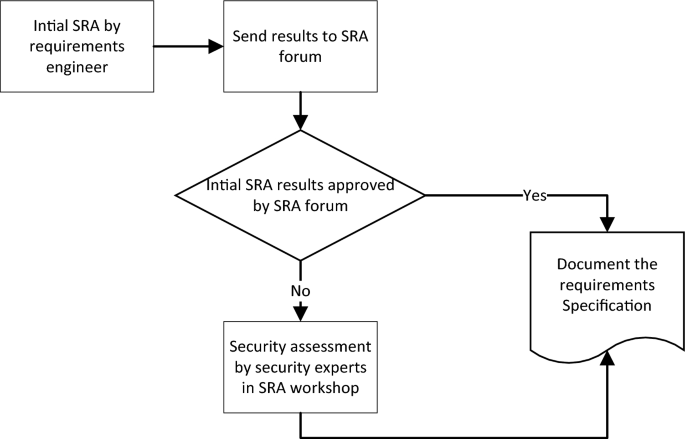
SRA workflow
In this workflow, requirement engineers perform a risk assessment according to the method in section “ Security Risk Assessment ” and sends the results to the SRA forum. A security expert then goes through the results and either approves them or identifies the need for expert involvement and in-depth analysis. If necessary, the in-depth analysis is then done in an SRA workshop and the security expert team assists the requirements engineers with in-depth analysis. In this way, there is already a quality control process being performed on the assessments done by the requirements engineers. We applied this process in eight releases projects in the subject organization.
To evaluate the outcome of these changes, we used the statistical data collected by the organization for follow-up purposes. The organization uses this data to go through the pre-study documentations and review the security risk assessment results. As a result of this review, all studies must have a proper security risk assessment documentation, approved by the SRA forum. By analyzing this statistic, we identified three categories of studies:
Studies with missing security risk assessment documentation (no assessment reported in pre-study documentation).
Studies with incomplete security risk assessment data provided in the pre-study documentation and no communication with the SRA forum.
Studies with proper security risk assessment provided in the pre-study document, which had passed through the SRA forum (with the results of the analysis performed by the requirement engineers either being approved directly or after expert involvement through an SRA workshop).
Table 4 shows the statistics for these categories. The requirements engineers responsible for the studies in categories 1 and 2 were invited to a root cause analysis workshop and their input on the causes of identified issues was discussed with them. All the participants were encouraged to share their ideas and give feedback about the method, and a recorder took notes on the board to capture all of the input.
The five whys method [ 36 ] was then used to identify the root causes of the identified issues. The following root causes were identified:
Security awareness/competence: Due to reorganizations, and responsibility relocations, new teams started on the project without getting the planned training on applying the method. The statistics in different releases have a correlation with changes in the organization.
The training material is old and needs to be refreshed and adjusted to the agile teams’ way of working which changes regularly.
The old template for the pre-study document (without the security chapter) was used for documenting the pre-study in some of the studies.
There was a lack of communication to pre-study drivers that it is mandatory to complete the security chapter.
The SRA forum was not sufficiently introduced to the new pre-study drivers.
The pre-study documentation including the security chapter (to include security risk assessment) exists, but is not linked into project management tools, which led to missing documentation when working on the statistics above.
The method is focused on the new (delta) functionality in the product, since the new requirements are used as an input to the security risk assessment. However, the study driver must have access to the security risks that were identified for the legacy system when the new feature is an incremental change in functionality.
Based on these findings several corrective actions were identified: security guardian(s) were appointed in each project to ensure that the security risk assessment would be in place before respective project milestones/checkpoints. The guardian also supports the function of the security risk assessment forum representing the respective project. Security guardians are project managers that ensure mandatory project activities are performed, including security.
It was ensured that the release project checklist is updated and includes security risk assessment as a mandatory checkpoint to pass. It was also ensured that the SRA forum representative is invited to the final review of the pre-study documentation. Training material was updated and the training program was improved to include SRA forum information to cover all new engineers. It was ensured that the documentation template would be updated as required.
We also analyzed the email throughput in the SRA forum mailbox and listed the statistics about the emails sent to the SRA forum by unique individual senders (requests for SRA forum support) as shown in Fig. 10 . The increasing trend in the number of emails can be interpreted as a sign of increased security awareness among pre-study drivers and the increasing number of security risk assessments performed for studies that require approval from the SRA forum.
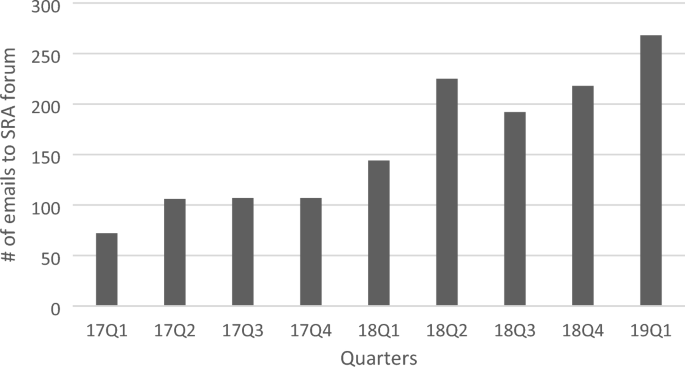
Statistics on number of emails sent to SRA forum by unique individual senders
We proposed the application of a method in a telecom company and studied different aspects of introducing such a method in the context of the target company. This approach examined the target company's journey through several steps of changes, based on a continuous improvement mindset.
The journey started from an initial status of security risk assessments being performed by a centralized team of security experts who did not have deep technical knowledge of the lower abstraction level of the respective functionality of the system under assessment. This assessment was performed in requirement verification. During our research journey, we examined introducing security risk assessment activity to be performed during requirements engineering and through a completely distributed approach, by letting requirements engineers with deep technical knowledge, but no specialization in security, perform the assessment. One of the goals was to ensure that introduction of security considerations into the product’s functionality as early as possible, and the other goal was to eliminate the bottleneck of a central team conducting the security assessment activity for all features of the project. In the third round, the approach was modified to examine a cooperative setup involving both individual requirements engineers as well as the central security team. The first iteration of our case study can be defined as exploratory [ 33 ], which helped us to find out how the requirements engineering was performed and if SRA could be applied by pilot subjects. The output from this study led us to the idea of training subjects on how to apply SRA and study the outcome in the second iteration. The second iteration could be defined as explanatory [ 33 ], as it was used to seek an explanation of the outcome of iteration 1 (subjects performing SRA without receiving any training) with the case where subjects did get a training on the method. The output from this study helped us to define the type of support needed by security experts. The third iteration focused on a descriptive study of the organization in the last 2 years with requirements engineers using the SRA method and improved the application of the method by involving security experts to triage when needed.
The results of our extensive case study allowed us to answer the research questions we had defined:
What are the difficulties of introducing such a method in a big organization that is developing complex systems? We realized in each case study iteration that by adding SRA to the existing way of working and to the development artifacts in the company, the application of the method is impacted by the efficiency/deficiency of the original artifacts. Changes in the organization must also be monitored to adjust the proposed method.
When performing security risk assessment, can we bridge the gap between security experts and requirement engineers who are not specialized in security? In that case, what is an efficient distribution of tasks between security experts and requirement engineers? The case study showed that expert involvement could not be eliminated to ensure that the quality of the risk assessment is acceptable and that all risks are identified. Based on this finding, we also learned that changes of this type must be managed over time to achieve the desired results. It was also observed that the bottleneck issue could be solved in a cooperative approach and, as we see in the results of iteration 2, most subjects reported manageable overhead with respect to total time of the pre-study. Considering the increasing number of features to be implemented (see Table 4 ) in a project, the overhead factor became important.
What considerations (introduction or training) are needed for engineers to achieve acceptable results? During all iterations of the case study, one of the main elements of feedbacks we received was related to training and providing examples and background material for requirement engineers as well as the possibility of supervision/consulting supported by security experts. The results clearly showed that having basic security knowledge, as well as understanding the purpose and expected outcome of the security risk assessment is a crucial prerequisite to achieving the desired results. It is also important to ensure that training is refreshed continuously and is adapted to the changes in the organization, development processes, and daily way of working. Note that the emphasis in our case study has always been on basic security knowledge and understanding what security principles are in terms of confidentiality, integrity, and availability rather than knowledge of sophisticated attack patterns, threat models, etc.
In summary, despite all obstacles, comparing the initial state with the existing state, we see an obvious increase in security awareness in the company and among developers, since everyone is expected to see security considerations as a part of the functional requirements to be developed in the final product. We have effectively shifted security risk assessment that had previously been done in later stages of the development to the earliest stage where the requirements are elicited to implement the functionality. Through the continuous improvement process, we managed to reform the central team of subject matter experts, who were serving the development activities in a support function to the SRA forum that acts in a corrective function.
As stated by Runeson et al. [ 33 ], about the nature of the case studies, the case study methodology can primarily be used for exploratory purposes, but it can be used for explanatory and descriptive purposes if the generalizability of the situation or phenomenon is of secondary importance. During design and implementation of the case studies, our assumption was that the results could be transferable, and we believe the results provided a deeper understanding of the phenomena under study. We also believe that providing the details of factors defining the context of cases study (the size of the company, complexity of the product, the type of development process, the size of the project, and the abstraction level of requirements) supports transferability goals. It allows the readers of our results to make inferences about how our findings match their context and which part of our solution can be transferred to their respective settings [ 35 ]. Any software or system which has interfaces and/or is communicating with its surrounding is subject to risks and needs a security risk assessment to be prepared for being resilient. SRA can be performed on any system and in any abstraction level, on a whole system within its boundaries or on the components of any system and is not limited to telecom products.
We analyzed the validity threats of our results based on Runeson et al.’s checklist [ 33 ]. For construct validity and to ensure that researcher and subjects have the same interpretation of the operational measures, we used both questionnaire and interview sessions to go through the answers to the questionnaire. The case study design and three different iterations of the case study contribute to the internal validity and help to ensure that various factors are considered in the findings. This includes the factors of the technical background and security competence of the subjects, as well as the organizational way of working and processes that are already in place, but which may differ from project to project. The same characteristics of our approach help with analysis of the external validity, since it is performed by different subjects in different projects over an extended period of time. To support the reliability of the findings, all steps of the case study activities were designed and reviewed by three researchers, and to reduce bias by individual researchers, we conducted data analysis after the third iteration by three researchers independently.
Related Work
To identify related work in risk-based requirements engineering, we performed a literature review and went through the publications on research approaches to security risk assessments applied in requirements engineering as well as similar empirical studies. During this literature study, we compared the novelty of our contribution with existing research contributions, considering that:
We use security risk assessment in requirement analysis of all functional requirements, not just security requirements.
Our focus is on assets at a lower abstraction level than similar approaches, which start mostly from strategic interests of stakeholders or objectives. Going from system-level to subsystem-level analysis highlights the functional aspects of the solution to be developed that might be missed in higher-level analysis [ 37 ]. Identifying risks at this level helps us to refine the solution to counter the risk by choosing a security-tuned solution.
We emphasize the technical knowledge of requirements engineers supported with security training and security expert consulting (when needed), to distribute the overhead of security activities instead of using the limited resource of security experts.
We have empirically verified the proposed approach in an industrial setup, over the course of several years and in large-scale software development projects using agile methods. This has provided a good understanding and lessons learned about the realities of introducing such approaches in a real-life setup.
Identifying system assets, formulating significant threats to the software system, and associating the probability and impacts of risks with the system requirements have been presented in several articles and in various dimensions [ 8 , 9 , 10 , 11 , 12 , 38 ]. Franqueira et al. introduce an agile security risk management approach that addresses the topic of performing risk assessments in development process iterations. This approach focuses on supporting decision making on mitigations to be incorporated into the next iteration of development [ 8 ]. Asnar et al. propose a goal-oriented approach for analyzing risks along with stakeholder interests and identify countermeasures as a part of system requirements [ 13 ]. In a similar approach, Mayer et al. [ 9 ] propose using risk analysis in security requirements engineering of information systems that focus on business assets. Firesmith [ 22 ] presents different types of security requirements and provides guidelines for system engineers to specify security requirements. These guidelines are used to ensure that security requirements are not confused with architectural security mechanisms. Our approach is similar to these works in that it focuses on the knowledge of system engineers rather than security engineers. Laoufi [ 10 ] also aims at identification of security requirements for information systems from risk analysis and uses ontologies to do so. He also focuses only on security requirements and no empirical evaluation of his approach is presented. All the approaches mentioned aim at identifying security requirements using security risk assessment, compared to our approach that applies risk assessment to all requirements, resulting in requirements that have been fine-tuned for security. In this way, we ensure that the security considerations are built into the requirements and consequently into design of the system under development.
Note that there are various definitions for security requirements in the requirements engineering and security engineering communities. Within requirements engineering, security is often classified as a non-functional requirement [ 39 , 40 ]. An example from the security engineering community, common criteria (CC) [ 41 ] distinguishes between two types of security requirements: functional and assurance. Security functional requirements describe security properties that users can detect by direct interaction with the system or by the systems’ response to stimulus. Security assurance requirements are process requirements that require active investigation and evaluation by the IT system to determine their security properties [ 42 ].
We agree with the statement that “no common agreement exists on what a security requirement is” [ 23 ] and various approaches [ 22 , 24 ], [ 43 , 44 , 45 , 46 , 47 ] define different extents for security considerations covered by security requirements and different levels of details on how to cope with security requirements. In our approach, we do not separate security and non-security requirements; instead, we propose to define and “security-tune” function-level requirements after considering the relevant security risks. Considering security, as a part of designing the solution will ensure that security aspects are not ignored. Haley et al . [ 43 ] recommend security requirements “… to express what is to happen in the given situation, as opposed to what is not ever to happen in any situation.” In our approach, we use the same mindset and propose risk analysis for every detailed requirement, considering the context in which the requirement is to be implemented.
Focusing on the assets, in a similar approach to ours, Vasilevskaya et al. use risk assessment (consequence assessment) to decide which asset to prioritize for protection, and this is used as an input to selection of security mechanism to protect the asset in embedded systems [ 48 ]. This approach also combines security expertise with embedded system engineering knowledge, although the approach does not target requirements engineering.
We reuse the concept of misuse cases [ 49 ] to detect the possibilities to abuse the functionality and identify the risks. Misuse cases are introduced by Sindre et al. [ 50 ] and extend traditional use cases by specifying behavior not wanted in the proposed system. Mwambe and Echizen [ 51 ] focus on supporting information systems security during the design phase. As an extension of unified modeling language (UML) activity diagrams, mal-activity diagrams (MAD) have also been used to model malicious and risk mitigation processes.
In our literature review and going through the relevant survey studies on information security risk analysis and security requirements engineering such as [ 52 , 53 ], we found some similar empirical studies with industrial setups. Oyetoyan et al. [ 11 ] presented an empirical study with an extensive presentation of the case study and its results with partially overlapping research question. Challenges of applying threat modeling in agile development are presented by Cruzes et al . [ 54 ]. This approach uses a similar research method to ours and presents challenges to adoption of threat modeling as a security practice in a smaller development organization. The challenges identified by this contribution are mapped to our findings in some of the cases such as challenges with having distributed teams or the importance of providing security expert support in certain discussions.
Morrison et al. [ 55 ] surveyed several security-focused open source projects to collect evidences on adherence to the number of software development security practices. According to their findings, training is positively correlated with the use of these practices and we see a similar finding in our work as well: training system engineers improves the use of security risk assessment as a security best practice. In a similar way, we also observed that the use of a simplified security risk assessment method that is designed with ease of use in mind is impacted by various factors.
Security has become a critical part of nearly every software engineering project and identifying and performing proper activities to ensure security is one of the challenges of software vendors. The work presented in this article proposes the introduction of a risk assessment method in requirement engineering and studies the realities and challenges of applying this method in a real-life industrial setup. The goal of this validation step was to see if it is possible with a small effort to introduce such a risk assessment approach. In this approach, requirements engineers who are not specialized in security attempt to efficiently find security risks early in the development process as well as to gather information on the outcome. Lessons learned from this validation activity showing the need of systematic interaction between security experts and requirements engineers may provide a basis for being prepared and facilitating similar approaches.
The risk-based requirements engineering method provides incentives in the sense that system engineers find the risks involved with their proposed solutions immediately. When developing solutions, they can react accordingly by fine-tuning the solution or by adding new requirements. This is an immediate perceived benefit and is one of the factors that increases the acceptance of the method. In our industrial case study, we examined the applicability and usability of the method when used by distributed teams, developing complex products in agile ways. We started on a small scale, iteratively improved the application of the method, and increased the scale.
For future work, we are focusing on applying the method in a different organization to measure the correlation in findings. The next step of our research is to analyze the quality and quantity of risks identified by the subjects and compare them to similar case studies with security experts as the subjects. This could be performed in a quantitative approach to identify the risk coverage of the method. Another area to be considered as future work is to create a database of different types of known security risks which can be used as a reference during the assessment performed by requirement engineers. Such a database would of course need to be supported by known security modeling methods such as various threat models, attack trees [ 5 ], etc. to ease the navigation and usage. SRA is not limited to identify a specific type of risks and answering the mentioned three questions and the type of risk to the identified assets can result in any type of risks. By providing a starting point for requirement engineers through a list of example risks for similar systems, there is a possibility to minimize the probability of missing a risk type.
Data Availability
No raw data is available.
Code Availability
Not applicable.
McGraw G. Software security. IEEE Secur Priv. 2004;2(2):80–3.
Article Google Scholar
Howard M. Building more secure software. IEEE Secur Priv. 2004;2(6):63–5.
Ardi S, Byers D and Shahmehri N Towards a structured unified process for software security, Proc. Int. Workshop on Software Engineering for Secure Systems (SESS), Shanghai, China, pp. 3–10. (2006)
Lipner S. B The trustworthy computing security development lifecycle, Proc. ACSAC 04, 20 th Annual Computer Security Applications Conference, Tucson, USA, pp. 2–13. (2004)
McGraw G. Software Security: Building Security In. Boston: Addison-Wesley; 2006.
Viega J, McGraw G (2011) Building Secure Software: How to Avoid Security Problems the Right Way. Boston: Addison-Wesley; 2011.
McGraw G, Migues S, West J, (2018) Building Security In Maturity Model (BSIMM 8), https://www.bsimm.com/ . Accessed 2020–02–10
Franqueira V.N.L, Bakalova Z, Than Tun T, Daneva Towards agile security risk management in RE and beyond, Proc. 1st Int. Workshop on Empirical Requirements (EMPIRE), Trento, Italy, pp. 33–36. (2011)
Mayer N, Rifaut A, Dubois E Towards a risk-based security requirement engineering framework, Proc. 11th Int. Workshop on Requirements Engineering: Foundation for Software Quality (REFSQ'05), Los Alamitos, USA, pp 83–97. (2005)
Laoufi N, From risk analysis to the expression of security requirements for systems information, Proc. Fourth International conference on Cyber security, cyber warefare and digital forensics, Jakarta, Indonesia, pp 84–89. (2015)
Oyetoyan T. D, Soares Cruzes D, Gilje Jaatun M, An empirical study on relationship between software security skills, usage and training needs in agile settings, International Conference on Availability, Reliability and Security, Salzburg, Austria, pp 548–555. (2016)
Savola R. M, Väisänen T, Evesti A, Savolainen P, Kemppainen J, Kokemäki M. Towards risk-driven security measurement for android smartphone platform, International Information Security South Africa conference, Johannesburg, South Africa, pp. 1–8. (2013)
Asnar Y, Giorgini P, Mylopoulos J. Goal-driven risk assessment in requirements engineering. Requir Eng. 2011;16(2):101–16.
Howard M, Lipner S. The security development lifecycle. Redmond, Washington: Microsoft Press; 2006.
Google Scholar
The CLASP application security process. Secure Software Inc. 2005. https://cwe.mitre.org/documents/sources/TheCLASPApplicationSecurityProcess.pdf . Accessed 23 Jun 2023.
Guide for conducting risk assessment, NIST Special Publication 800–30, https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf . Accessed 23 Jun 2023.
ISO/IEC 27000: https://www.iso.org/standard/73906.html . Accessed 23 Jun 2023.
ISC2 Cybersecurity workforce study (2019), https://www.isc2.org/Research/Workforce-Study . Accessed 23 Jun 2023.
Herrmann A, Morali A RiskREP: Risk-Based Security Requirements Elicitation and Prioritization, Proc. Perspectives in Business Informatics Research, Riga, Latvia, pp. 155–162. (2011)
Umarji M, Seaman C. Predicting acceptance of software process improvement. SIGSOFT Softw Eng Notes. 2005;30(4):1–6.
Borg A, Yong A, Carlshamre P, Sandahl K The bad conscience of requirements engineering: an investigation in real-world treatment of non-functional requirements, Proc. 3rd International Conference on Software Engineering Research and Practice in Sweden (SERPS'03), pp. 1–8. (2003)
Firesmith DG. Engineering security requirements. J Object Technol. 2003;2(1):53–68.
Tondel A, Gilje Jaatun M, Meland PH. Security requirements for the rest of us: a survey. IEEE Softw. 2008;25(1):20–7.
Mead N.R, Houg E.D, Stehny T.R, Security quality requirements engineering (SQUARE) methodology, Software Eng. Inst. Carnegie Mellon University, Techncial Report CMU/SEI-2005-TR-009. (2005)
Luburic N, Sladic G, Milosaljevic B Applicability issues in security requirements engineering for agile development, Proc. International Conference on Applied Internet and Information Technologies, Bitola, Macedonia, DOI: https://doi.org/10.20544/AIIT2018.I02. (2018)
Poller A, Kocksch L, Turpe S, EPP F. A, Kinder-Kurlansa K. Can security become a routine?: A study of organizational changes in an agile software development group, Cumputer Supported Cooperative Work (CSCW), Portland, Oregon, USA, pp 2849-2503
Gorschek T, Wohlin C. Requirements abstraction model. Requirements Eng. 2007;11(1):79–101.
Kaplan S, Garrik BJ. On the quantitate definition of risk. Risk Anal. 1981;1(1):11–27.
Stalling W, Brown L. Computer security, principles and practice. Hoboken: Prentice hall; 2007.
http://www.3gpp.org/SON , Accessed 2021–03–09
http://www.3gpp.org/ftp/Specs/html-info/25484.htm , Accessed 2021–03–09
Yin R. K Case study research: Design and Methods, Fourth Edition, Applied Social Research Methods Series. (2009)
Runeson P, Höst M. Guidelines for conducting and reporting case study research in software engineering. J Empirical Softw Eng Springer. 2009;14(2):131–64.
Kitzinger J. Qualitative research: introducing focusgroups. BMJ. 1995. https://doi.org/10.1136/bmj.311.7000.299 .
Polit DF, Tatano Beck C. Generalization in quantitative and qualitative research: myths and strategies. Int J Nurs Stud. 2010;47(11):1451–8.
Samuel JB, Marathamuthu MS, Murugaiah U. The use of 5-WHYs technique to eliminate OEE’s speed loss in a manufacturing firm. J Qual Maint Eng. 2015;21(4):419–43.
Alexander I. Misuse cases: use cases with hostile intent. IEEE Softw. 2003;20(1):58–66.
Salehie M, Pasquale L, Omoronyia I, Ali R, and Nuseibeh B Requirements-driven adaptive security: Protecting variable assets at runtime, 20th IEEE International Requirements Engineering Conference (RE), Chicago, IL, USA, pp. 111-120. (2012)
Chung L, Nixon BA, Yu E, Mylopoulos J. Non-functional requirements in software engineering. Dordrecht: Kluwer Academic Publishers; 2000.
Book MATH Google Scholar
Burge J, Brown D (2002) NFRs: fact or fiction? Worcester Polytechnic Institute, Technical Report, WPI-CS-TR-02–01.
http://commoncriteriaportal.org . Accessed 2019–03–30
Wilander J, Gustavsson J Security requirements - a field study of current practices, E-Proc. The Symposium on Requirements Engineering for Information Security (SREIS), Paris, France. (2005)
Haley CB, Laney R, Moffett J, Nuseibeh B. Security requirements engineering: a framework for representation and analysis. IEEE Trans Softw Eng. 2008;34(1):133–53.
Apvrille A, Pourzandi M. Security software development by example. IEEE Secur Priv. 2005;3(4):10–7.
Boström B, Wäyrynen J, Boden M (2006) Extending XP practices to support security requirements engineering International Workshop on Software Engineering for Secure Systems (SESS). Shanghai, pp. 11–18
Souag A, Mazo R, Salinesi C, Comyn-Wattiau I. Using the AMAN-DA method to generate security requirements: a case study in the maritime domain. Requirements Eng. 2018;23(1):557–80.
Villamizar H, Kalinowski M, Garcia A, Mendez D. An efficient approach for reviewing security-related aspects in agile requirements specifications of web applications. Requirements Eng. 2020;25:439–68.
Vasilevskaya M, Nadjm-Tehrani S Model-based Security Risk Analysis for Networked Embedded Systems, Proc. The 9th International Conference on Critical Information Infrastructures Security (CRITIS) Limassol, Cyprus, pp. 381–386. (2014)
Hope P, McGraw G, Anton AI. Misuse and abuse cases: getting past the positive. IEEE Secur Priv. 2004;2(3):90–2.
Sindre G, Opdahl A.L Eliciting security requirements with misuse cases, Proc. 37th International Conference on Technology of Object Oriented Languages and Systems (TOOLS-37’00) Sydney, Australia, pp. 120–131. (2000)
Mwambe O, Echisen I Security oriented malicious activity diagrams to support information systems security, International conference on advanced information networking and applications workshop Taipei, Taiwan, pp. 74–81. (2017)
Behnia A, Abd Rashid R, Chaudhry JA. A survey of information security risk analysis methods. Smart Comput Rev. 2012;2(1):79–64.
Souag A, Mazo A, Salinesi C, Comyn-Wattiau I. Reusable knowledge in security requirements engineering: a systematic mapping study. Requirement Eng. 2016;21:251–83.
Cruzes D, Gilje Jaatun M, Bernsmed K, Tondel I.A Challenges and experinces with applying Microsoft Threat Modeling in Agile Development Projects, 25 th Australasian Software Engineering Conference, Adelaide, Australia, pp. 111–120. (2018)
Morrison P, Smith B.H, Williams L Surveying security practice adherence in software development, Proc. of the Hot Topics in Science of Security: Symposium and Bootcamp, ACM International Conference Proceeding Series Part F127186, New York, USA, pp. 85–94. (2017)
Download references
Acknowledgements
Funding for this work was provided from Ericsson AB and Linköping University. Proofreading of a late draft of the article was done by Brittany Shahmehri and David Partain.
Open access funding provided by Linköping University. This research was funded by Ericsson AB and Linköping University.
Author information
Authors and affiliations.
Ericsson AB, Linköping, Sweden
Shanai Ardi & Mats Gustafsson
Department of Computer and Information Science, Linköping University, Linköping, Sweden
Kristian Sandahl
You can also search for this author in PubMed Google Scholar
Contributions
A comprehensive description of the security risk assessment (SRA) method; a longitudinal case study of introducing SRA in a large organization; a survey of related work.
Corresponding author
Correspondence to Kristian Sandahl .
Ethics declarations
Conflict of interest.
Ardi and Gustafsson are both employed at Ericsson AB, full time. Sandahl is employed full time at Linköping University and is a senior member of IEEE.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Ardi, S., Sandahl, K. & Gustafsson, M. A Case Study of Introducing Security Risk Assessment in Requirements Engineering in a Large Organization. SN COMPUT. SCI. 4 , 488 (2023). https://doi.org/10.1007/s42979-023-01968-x
Download citation
Received : 28 June 2021
Accepted : 27 May 2023
Published : 27 June 2023
DOI : https://doi.org/10.1007/s42979-023-01968-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Requirements analysis
- Risk assessment
- Process improvement
- Find a journal
- Publish with us
- Track your research
- Discover our global expertise Project services PMO & Project Delivery Project Dashboards Project Management as a Service (PMaaS) Project Portfolio Execution Strategy execution & Business Improvements Project Management Improvement Agility at scale Change Management Lean Innovation Project Portfolio Management & Optimisation Digital Solutions Digital PMO Deployment of PM Solutions Intelligent Project Prediction (IPP) Clayverest: the PMO's Copilot Case studies Discover how our expertise supports our clients
- Join our team Our company culture Empower your project experience Empower your professional experience Empower your CSR experience Empower your social experience Our job families Project Management Consultant Delivery Manager Business Manager Your profile Early Professional Experienced Professional Our job offers Discover our local and international opportunities
- The Project Management Blog PM Guides Agile Change Management Cost Management Crisis Management Digital PMO Industry Insights Lean Innovation PMaaS PMO Portfolio Management Project Management Delivery Project Managements Roles Risk Management Schedule Management Latest articles Newsroom Case studies Discover how our expertise supports our clients
- Europe France Germany Italy Portugal Romania Spain Switzerland United Kingdom North America Canada Mexico United States Asia South East Asia Oceania Australia Contact Us
Case Study: Improving Risk Culture
- 28 May 2020
- Financial Services , Change Management
Risk management is a key component of every organization’s strategy and operations. Companies make important risk-based decisions every day. At the forefront of such risk decisions are financial institutions. Improving risk culture allows a company to both raise awareness on how to better manage risk, and also to bridge the gap between management operations and organizational values.
In brief: 5 steps to create a sustainable risk culture
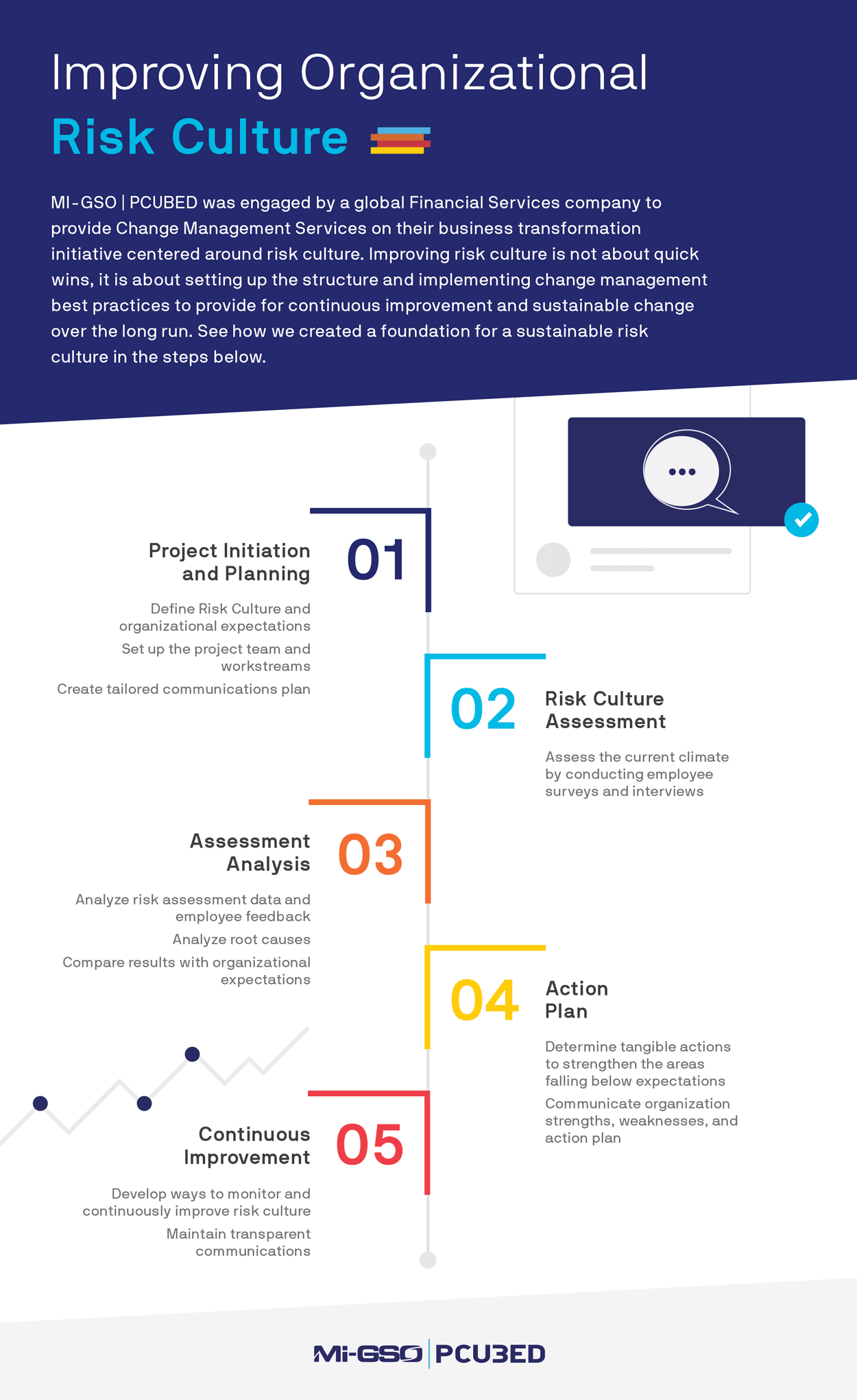
The Challenge
MIGSO-PCUBED was engaged by a federally regulated Financial Services company to provide Change Management Services in support of a company-wide business transformation program.
The program began as a response to recommendations and mandates from regulators. However, risk management had become largely control-driven and lacked consistent awareness among the employee base. Compliance with aggressive regulatory timeframes, competing project scopes, and changes in leadership each contributed to poor risk management.
The change management initiative, therefore, focused on improving the understanding of risk culture across the organization and creating a foundation for a more sustainable culture going forward.
The Solution
For a transformation initiative centered around risk culture improvement, it is important to set up an effective structure – one that successfully nurtures, builds, and supports an environment for change, which, in turn, allows the organization to see and experience long-term benefits and continuous improvement.
Working directly with the Senior Management Committee and key stakeholders, the team quickly structured the business transformation program into six corporate workstreams that would each simultaneously deliver results. Each workstream’s output provided an understanding of current capability, an assessment of gaps against benchmarks, and a clear roadmap for change.
With a structure in place, the team next set out to determine what aspects of their risk culture the client needed to specifically address. With that, we will take a quick detour on risk culture and risk culture measurement.
What is a Risk Culture?
“ Risk culture is the values, beliefs, knowledge, and understanding about risk, shared by a group of people with a common purpose.” – PMI, The ABC of Risk Culture . And, having a robust risk culture is important in more effectively managing risk.
"Risk culture is the values, beliefs, knowledge and understanding about risk, shared by a group of people with a common purpose." PMI - The ABC of Risk Culture
Enterprise risk management includes identifying, assessing, and mitigating risks depending on both the risk tolerance and the risk appetite of the firm. Whereas risk appetite is the amount of total risk an organization is willing to accept, risk tolerance is the day to day or transactional limit.
Want to know more about
By raising risk awareness and understanding, a healthy risk culture aligns a company’s attitudes and behaviors with their business strategy. This ensures that the values and ethics of employees – around risk strategy, appetite, and tolerance – are aligned with those of the organization.
Key elements of a healthy risk culture include Knowledge and Understanding as well as Leadership, Respect, and Accountability. To cultivate those values, you must also be able to observe the behaviors of Transparency, Communication, Awareness, and Motivation.
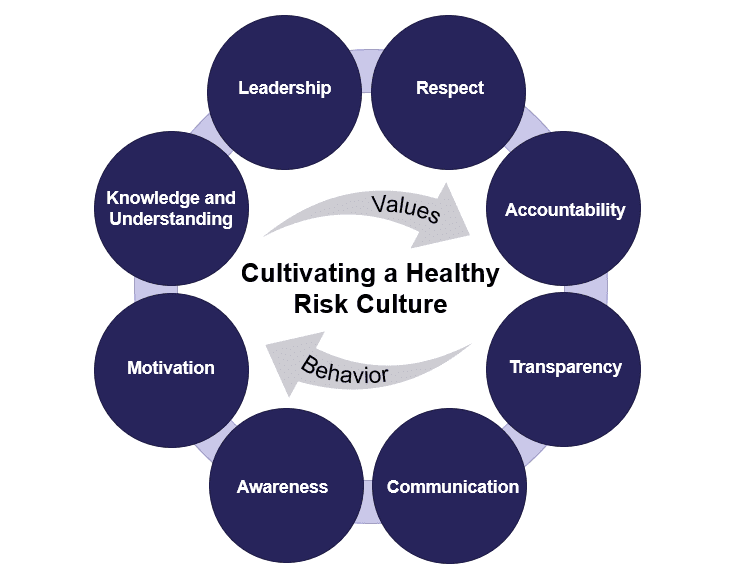
Bringing Risk Management into Focus
Bringing us to perhaps the most interesting aspect of this project – the focus on risk management and its integration to change management. You may wonder how an organization quantifies their risk management capabilities and overall risk awareness – basically how they conduct a risk culture assessment.
“There is no one good or model culture against which others can be measured and ranked, and no single template or checklist for firms to adopt.” - Banking Standards Board
Within the Financial Services industry, the Banking Standards Board conducts an annual assessment with its member firms. While it does not rank their culture directly, it does provide its member firms with feedback against key elements to help them manage their culture more effectively (image below).
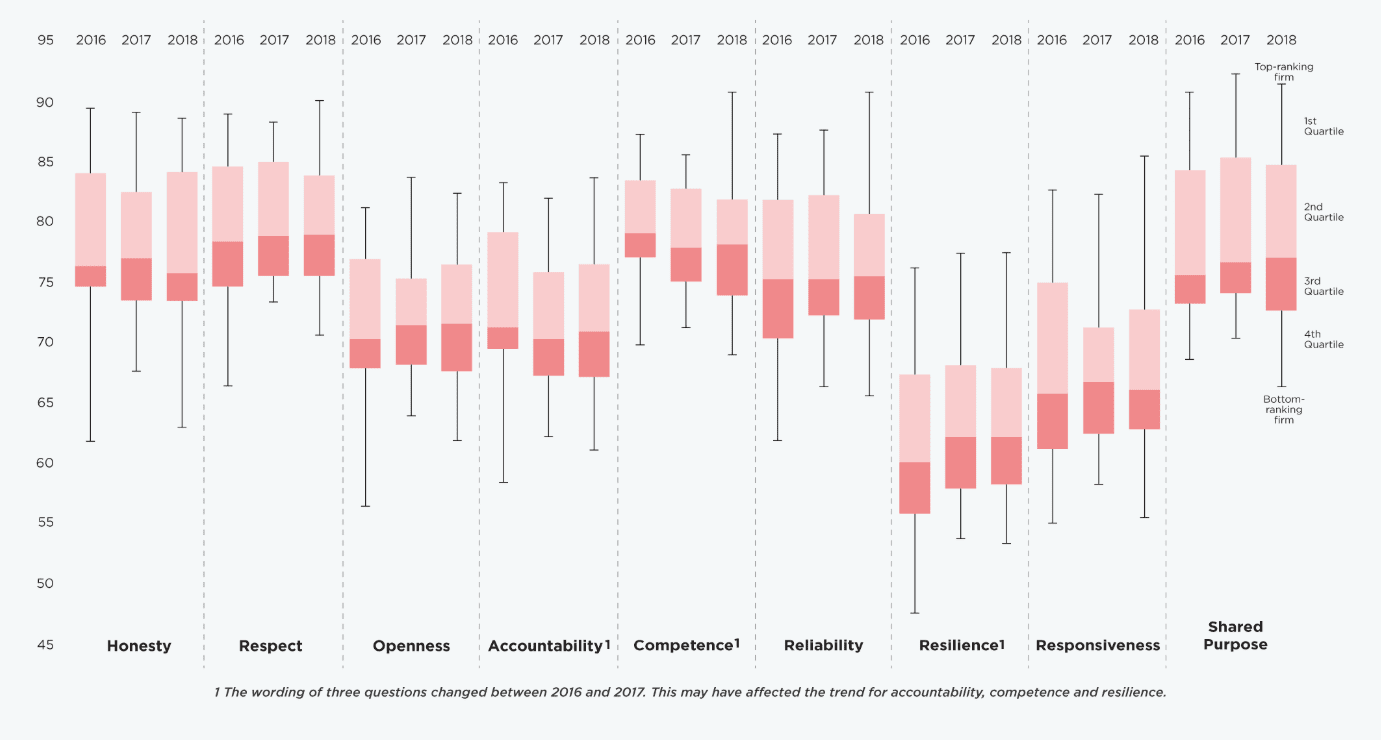
In the same way, risk culture itself cannot be measured. However, an organization can measure its ability to demonstrate risk-related values and meet company objectives. That means an organization must first determine what outcomes are driven by values and behaviors, and then begin to measure them.
What values and behaviors contribute to effective risk management? How can these be measured or evaluated? What actions can an organization take thereafter to establish risk awareness?
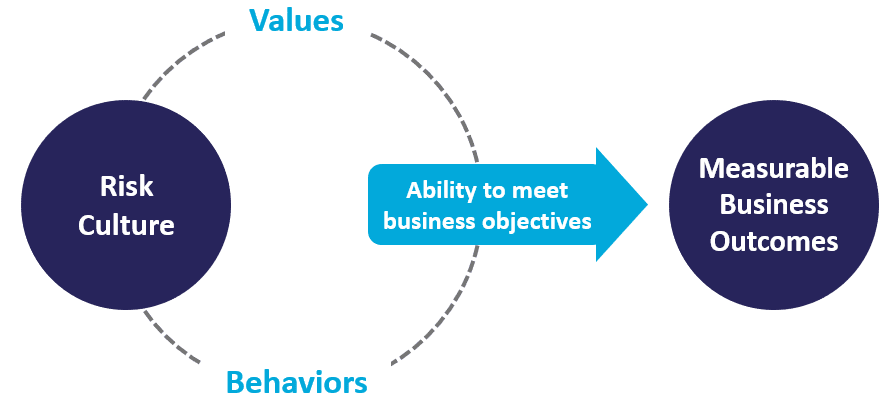
To give you an example, with a strong risk culture, employees feel more empowered to speak up and escalate issues. In turn, an organization that encourages employees to raise concerns and issues might observe a decrease in their employee turnover rate. They may also see an increase in the number of reported issues or a decrease in the number of integrity-related risks.
Using an anonymous forum, a company may identify sensitive issues or gauge the number and severity of integrity risks. Using this data, the company can then organize its risk indicators into a dashboard to consistently appropriate and evaluate risk culture.
Implementing a Risk Culture Approach
Adopting this approach, the MIGSO-PCUBED change management team led the client through each of the 4 steps in the graphic below. The team leveraged core Change Management tools and techniques beginning with assessing the current climate and analyzing in comparison to organizational expectations. The team then defined a set of tangible actions mapped to a change roadmap of short, medium, and long term actions to strengthen areas falling below expectations.
Additionally, they established a robust governance and planning structure, and tailored communications to facilitate a more sustainable business transformation initiative.
The Benefits
In the short term, the MIGSO-PCUBED team has supported the client in building a company-wide and unified understanding of their corporate risk culture. Roles and responsibilities are better understood. Moreover, the client is observing greater risk awareness and more effective risk management practices.
The client also has the means to assess and monitor their risk culture going forward in the short, medium, and long term. This allows them to identify gaps and take action more proactively in driving risk culture. This highlights the longevity of the business transformation initiative long after its closure, as its outputs are fully integrated into the organization.
This article was written by Elaina Wheeler and Victoria Emslie .
You might also like:

Mondelēz’s Digital Transformation Journey

Using PMO KPIs to Measure Performance

Global Supply Chain Schedule Integration
Loved what you just read? Let's stay in touch.
No spam, only great things to read in our newsletter.
We combine our expertise with a fine knowledge of the industry to deliver high-value project management services.
MIGSO-PCUBED is part of the ALTEN group.
Find us around the world
Australia – Canada – France – Germany – Italy – Mexico – Portugal – Romania – South East Asia – Spain – Switzerland – United Kingdom – United States
Follow us here
© 2024 MIGSO-PCUBED. All rights reserved | Legal information | Privacy Policy | Cookie Settings | Intranet
Perfect jobs also result from great environments : the team, its culture and energy. So tell us more about you : who you are, your project, your ambitions, and let’s find your next step together.
- Netherlands
South East Asia
Switzerland
United Kingdom
United States
In accordance with the General Data Protection Regulations (GDPR), the data entered is processed for the management of recruitment and its improvement. To find out more, visit our privacy policy .
Dear candidates, please note that you will only be contacted via email from the following domain: migso-pcubed.com . Please remain vigilant and ensure that you interact exclusively with our official websites. The MIGSO-PCUBED Team
Discover our global expertise →
Project Services →
Strategy Execution & Business Improvements →
Digital Solutions →
Our case studies →
Join our team →
Company Culture →
Job Families →
Choose your language

Subscribe to our Newsletter
A monthly digest of our best articles on all things Project Management.
Subscribe to our newsletter!
Our website is not supported on this browser
The browser you are using (Internet Explorer) cannot display our content. Please come back on a more recent browser to have the best experience possible


IT Assessment Risk Mitigation
In only 2 weeks of working with a university, a set of recommendations minimizing data center risk by protecting the current infrastructure and architecting for improved cooling was developed., project background.
A major renovation of the campus center (housing the data center) was beginning. As a part of the renovation, an elevator was being added to the building, and the elevator shaft needed to go through the university’s data center. The CIO wanted to understand the risk to the school’s computing infrastructure.
The Strategy
We met with members of the IT department to understand the current data center layout and inventory. Meeting with the facilities team (including architect and construction vendor), we were able to identify areas of data center risk and make recommendations for avoiding risk. Our recommendations were scaled appropriately for the size and criticality of the university’s data center.
We also provided detailed documentation of the data center layout, including equipment placement and cable paths. During our assessment, we identified opportunities for data center expansion, improved cooling, and new cable layouts.
Proven Results
- Steps were taken to reduce dust and vibration during construction and install devices to reduce EMI during the elevator’s operation.
- Plans were made to migrate racks 90 degrees, allowing for hot aisle/cold aisle operation.
- Cabinet doors were changed to grills to improve airflow and cooling.
More Successful Projects

Business Resiliency Assessment and Planning

Business Continuance Recovery Planning

IT Assessment - Full Evaluation
Uncover opportunities for it excellence.
Terra Gaines, Senior Account Manager for Harvard Partners has been in the Staffing Industry for 17 years, supporting multiple industry verticals and market segments including: IT, Cybersecurity, Semi-Conductor, Tech Integrators, Finance & Medical to name a few. Her personal and professional passions have always been people centric and she’s extremely proud of providing white glove service to each client and manager that she serves.
Jill Gearhart, Director Client Services, has over 20 years of Account Management experience in technology service areas across IT Consulting & Staffing, Cloud, Datacenter, Networking & Communications. Jill’s focus is in Client Engagement, proposing and ensuring the successful delivery of services from the Harvard Partners Portfolio tailored to attain each Client’s desired business outcomes, including the Staffing of essential resources.
Prior to joining Harvard Partners in 2014, she held a high-level Account Management position at a global technology company now known as Lumen (formerly CenturyLink), where she was appointed to multiple Excellence Advisory boards in several Enterprise product areas, domestic and abroad, over the span of 11 years. Notably, after the Qwest-CenturyLink Merger in 2010, and the acquisition of Savvis thereafter, she was instrumental in the integration between organizations in the effort to build a seamless customer experience. Through continual engagement with Enterprise client organizations throughout her tenure, she has had the privilege of collaborating on solutions and individual resources needed to answer numerous business objectives, whether expanding into new markets or advancing operational efficiency and resiliency.
Education: Bachelor’s of Science, Business Administration, Bryant University, Cum Laude
Chris Callaghan is the Director of Architecture Services and is responsible for overseeing the architectural services arm of Harvard Partners. This includes everything from to architecture approach strategy, to candidate selection & vetting, to engagement leadership. Chris has years of technology architecture consulting experience ranging from boutique architectural services companies to larger, established consulting companies. He’s played multiple roles, from individual contribution to client and consultant management.
Prior to joining Harvard Partners, he was the Engagement Lead and Consultant Manager at Systems Flow, Inc. where he was responsible for client engagement management, consultant management, architectural services, SOW negotiation/creation/signing, training, etc. Prior to that, he worked as an Enterprise Solutions Architect for a large reinsurance firm under Fairfax Holdings.
Gary Gardner is the Managing Director of Harvard Partners and an Information Technology executive with over 30 years of global Investment Management experience. He has a broad range of knowledge of Investment Management systems including investment research, portfolio management, trading, compliance, back office, CRM, and client reporting. Gary has expertise with technical infrastructure, operational risk, business continuity, SOX compliance, SSAE16 certification, vendor management, and cloud services.
Prior to joining Harvard Partners, he was the Chief Technology Officer at Batterymarch Financial Management, Inc. and GMO LLC where he was responsible for IT leadership and technical strategy for high computational and data-intensive quantitative asset management environments. Gary also held senior technology positions at Santander Global Advisors and Baring Asset Management.
Education: Gary studied Management Information Systems at Northeastern University.
Steve Walsh is a Managing Partner at Harvard Partners. Steve has been a career business leader for companies such as Hewlett Packard, EMC, Centerstone Manhattan Software, ClearEdge Partners, and Alliance Consulting.
Prior to joining Harvard Partners Steve was the worldwide leader for the Storage Consulting practice at Hewlett Packard. In this role, Steve was responsible for more than 500 employees encompassing sales, pursuit, portfolio, and delivery. Under Steve’s stewardship Storage Consulting built offerings to help clients assess and design complex storage infrastructures and develop state-of-the-art backup, recovery, and business continuance strategies. Steve grew the Storage Consulting Practice at HP by over 200% and introduced 20 new value-added offerings.
In addition to Hewlett Packard Steve has worked for companies both large and small. At ClearEdge Partners Steve advised C-level Fortune 500eExecutives on their IT purchasing and supply chain strategies, saving his clients millions over his tenure. Steve also has been a business leader at Alliance Consulting, where he built a practice to more than 200 consultants and 10 strategic offerings. Steve started his career at EMC Corporation from 1986 to 1998.
Education: Boston College School of Management, Computer Science
Matt Ferm is a F ounder and Managing Partner of Harvard Partners. Matt’s focus is on IT Assessments, IT Governance, and Program Management. Prior to Harvard Partners, Matt spent 17 years with Wellington Management Company, LLP. As an Associate Partner and Director of Enterprise Technologies, Matt was responsible for managing the global physical computing infrastructure of this financial services firm. This includes data centers, servers, voice and data networks, desktops, laptops, audio/video hardware, messaging (email, IM, etc.), security administration, disaster recovery, production control, monitoring, market data services, storage systems, and capacity planning.
During his career at Wellington, Matt managed the Operational Resilience, Resource Management, Systems Engineering, IT Client Services, and IT Strategic Development groups, chaired the firm’s Year 2000 efforts and was a member of the firms IS Priorities Committee, Project Review Committee (Chair), Systems Architecture Committee (Chair), Year 2000 Committee (Chair), Operational Resilience Committee, Incident Review Committee and Web Oversight Committee.
Prior to joining Wellington Management in 1992, Matt served as Director of Financial Services Markets for Apollo Computer, Hewlett-Packard, and Oki Electric where he managed the marketing of Unix workstations to the Financial Services industry. In 1985, Matt was Manager, New Business Development for Gregg Corporation (now IDD/Dow Jones/SunGard), a small investment database software company. Matt got his start in 1981 on Wall Street, working in the Custody Department of Bankers Trust and the MIS department of E.F. Hutton. Matt received his BA in Economics from Queens College, the City University of New York in 1982, and is a member of the Society for Information Management.
Education: Queens College, City University of New York – BA in Economics
Jason Young is a Senior Technical Recruiter at Harvard Partners and has more than 13 years of experience in recruiting and talent acquisition. Jason’s focus is on leading recruiting efforts and ensuring expectations are met or exceeded between our client’s needs and our candidate’s experience to deliver. Throughout his career, he’s filled immediate needs with high-level IT and business professionals. He also developed sourcing strategies and built strong relationships with IT specialists, leaders, and executives in a variety of industries.
Prior to joining Harvard Partners in 2018, Jason had a successful career with Advantage Technical Resourcing, (formerly TAC Worldwide Companies). He began his career in IT Staffing with Advantage as a Sourcing Recruiter, finding top-tier candidates for the Sr. Recruiters. He quickly advanced to be the sole recruiter of a national high-volume staffing program. His accomplishments with this program led to him being an MSA recruiter for a large global enterprise client. He provided them with a wide range of talent for more than five years.
Education: Bachelor’s of Arts, Psychology, Framingham State University
Lisa Brody is the Talent Operations Manager at Harvard Partners and her focus is on managing the recruiting practice. Lisa has over 30 years of experience in recruiting and talent acquisition. She has successfully brought top-tier Information Technology and Business Professionals to our clients, with a purpose, to fill immediate needs as well as, create an ongoing strategy to find IT specialists, leaders, and executives in a variety of industries.
Prior to joining Harvard Partners in 2016, Lisa reveled in an accomplished career with Advantage Technical Resourcing, (formerly TAC Worldwide Companies) from the rise of the organization, serving in several specialized recruiting and talent management roles. She was a lead MSA recruiter for large global enterprise clients for over a decade, providing a wide range of talent. Throughout her advancement, she has consistently, cultivated a strong reputation among candidates and clients for competency, professionalism, and results.
Education: Massachusetts Bay Community College, Wellesley, MA Associate of Science, Retail Management
- Discounts and promotions
- Delivery and payment
Cart is empty!
Case study definition

Case study, a term which some of you may know from the "Case Study of Vanitas" anime and manga, is a thorough examination of a particular subject, such as a person, group, location, occasion, establishment, phenomena, etc. They are most frequently utilized in research of business, medicine, education and social behaviour. There are a different types of case studies that researchers might use:
• Collective case studies
• Descriptive case studies
• Explanatory case studies
• Exploratory case studies
• Instrumental case studies
• Intrinsic case studies
Case studies are usually much more sophisticated and professional than regular essays and courseworks, as they require a lot of verified data, are research-oriented and not necessarily designed to be read by the general public.
How to write a case study?
It very much depends on the topic of your case study, as a medical case study and a coffee business case study have completely different sources, outlines, target demographics, etc. But just for this example, let's outline a coffee roaster case study. Firstly, it's likely going to be a problem-solving case study, like most in the business and economics field are. Here are some tips for these types of case studies:
• Your case scenario should be precisely defined in terms of your unique assessment criteria.
• Determine the primary issues by analyzing the scenario. Think about how they connect to the main ideas and theories in your piece.
• Find and investigate any theories or methods that might be relevant to your case.
• Keep your audience in mind. Exactly who are your stakeholder(s)? If writing a case study on coffee roasters, it's probably gonna be suppliers, landlords, investors, customers, etc.
• Indicate the best solution(s) and how they should be implemented. Make sure your suggestions are grounded in pertinent theories and useful resources, as well as being realistic, practical, and attainable.
• Carefully proofread your case study. Keep in mind these four principles when editing: clarity, honesty, reality and relevance.
Are there any online services that could write a case study for me?
Luckily, there are!
We completely understand and have been ourselves in a position, where we couldn't wrap our head around how to write an effective and useful case study, but don't fear - our service is here.
We are a group that specializes in writing all kinds of case studies and other projects for academic customers and business clients who require assistance with its creation. We require our writers to have a degree in your topic and carefully interview them before they can join our team, as we try to ensure quality above all. We cover a great range of topics, offer perfect quality work, always deliver on time and aim to leave our customers completely satisfied with what they ordered.
The ordering process is fully online, and it goes as follows:
• Select the topic and the deadline of your case study.
• Provide us with any details, requirements, statements that should be emphasized or particular parts of the writing process you struggle with.
• Leave the email address, where your completed order will be sent to.
• Select your payment type, sit back and relax!
With lots of experience on the market, professionally degreed writers, online 24/7 customer support and incredibly low prices, you won't find a service offering a better deal than ours.
- Open access
- Published: 26 April 2024
Clinician and staff experiences with frustrated patients during an electronic health record transition: a qualitative case study
- Sherry L. Ball 1 ,
- Bo Kim 2 , 3 ,
- Sarah L. Cutrona 4 , 5 ,
- Brianne K. Molloy-Paolillo 4 ,
- Ellen Ahlness 6 ,
- Megan Moldestad 6 ,
- George Sayre 6 , 7 &
- Seppo T. Rinne 2 , 8
BMC Health Services Research volume 24 , Article number: 535 ( 2024 ) Cite this article
Metrics details
Electronic health record (EHR) transitions are known to be highly disruptive, can drastically impact clinician and staff experiences, and may influence patients’ experiences using the electronic patient portal. Clinicians and staff can gain insights into patient experiences and be influenced by what they see and hear from patients. Through the lens of an emergency preparedness framework, we examined clinician and staff reactions to and perceptions of their patients’ experiences with the portal during an EHR transition at the Department of Veterans Affairs (VA).
This qualitative case study was situated within a larger multi-methods evaluation of the EHR transition. We conducted a total of 122 interviews with 30 clinicians and staff across disciplines at the initial VA EHR transition site before, immediately after, and up to 12 months after go-live (September 2020-November 2021). Interview transcripts were coded using a priori and emergent codes. The coded text segments relevant to patient experience and clinician interactions with patients were extracted and analyzed to identify themes. For each theme, recommendations were defined based on each stage of an emergency preparedness framework (mitigate, prepare, respond, recover).
In post-go-live interviews participants expressed concerns about the reliability of communicating with their patients via secure messaging within the new EHR portal. Participants felt ill-equipped to field patients’ questions and frustrations navigating the new portal. Participants learned that patients experienced difficulties learning to use and accessing the portal; when unsuccessful, some had difficulties obtaining medication refills via the portal and used the call center as an alternative. However, long telephone wait times provoked patients to walk into the clinic for care, often frustrated and without an appointment. Patients needing increased in-person attention heightened participants’ daily workload and their concern for patients’ well-being. Recommendations for each theme fit within a stage of the emergency preparedness framework.
Conclusions
Application of an emergency preparedness framework to EHR transitions could help address the concerns raised by the participants, (1) mitigating disruptions by identifying at-risk patients before the transition, (2) preparing end-users by disseminating patient-centered informational resources, (3) responding by building capacity for disrupted services, and (4) recovering by monitoring integrity of the new portal function.
Peer Review reports
Electronic health record (EHR) transitions present significant challenges for healthcare clinicians and staff. These transitions require adjustments in care delivery and may threaten care quality and value. It is critical that healthcare organizations undergoing these changes learn from others who have undergone similar transitions [ 1 , 2 ]. However, the current literature lacks adequate guidance on navigating EHR transitions, especially as they relate to how clinicians and staff interact with patients [ 3 ].
Embedded within EHRs, patient portals facilitate complete, accurate, timely, and unambiguous exchange of information between patients and healthcare workers [ 4 , 5 ]. These portals have become indispensable for completing routine out-of-office-visit tasks, such as medication refills, communicating laboratory results, and addressing patient questions [ 6 ]. In 2003, the VA launched their version of a patient portal, myHealtheVet [ 7 ] and by 2017 69% of Veterans enrolled in healthcare at the VA had registered to access the patient portal [ 8 ]. Similar to other electronic portals, this system allows Veterans to review test results, see upcoming appointments, and communicate privately and securely with their healthcare providers.
EHR transitions can introduce disruptions to patient portal communication that may compromise portal reliability, impacting patient and clinician satisfaction, patients’ active involvement in self-management, and ultimately health outcomes [ 9 ]. During an EHR transition, patients can expect reductions in access to care even when clinician capacity and IT support are increased. Patients will likely need for more assistance navigating the patient portal including and using the portal to communicate with their providers [ 10 ]. Staff must be prepared and understand how the changes in the EHR will affect patients and safeguards must be in place to monitor systems for potential risks to patient safety. Building the capacity to respond to emerging system glitches and identified changes must be included in any transition plan. Although portal disruptions are likely to occur when a new EHR is implemented, we know little about how these disruptions impact healthcare workers’ interactions and care delivery to patients [ 11 , 12 ].
Due to an urgency to raise awareness and promote resolution of these patient portal issues,, we utilized existing data from the first EHR transition site for the Department of Veterans Affairs (VA)’s enterprise-wide transition. We focused on end users’ responses to the question “How Veterans were affected by the transition?”. We used qualitative methods to begin to understand how provider and patient interactions were affected during and by the EHR transition. We explored the impact of the EHR transition on patients through healthcare workers’ vicarious and direct experiences with patients. Due to the high level of disruption in care delivery we draw on insights from an emergency preparedness framework [ 13 ] to generate a set of recommendations to improve healthcare workers’ experiences during EHR transitions. The emergency preparedness framework includes 4 phases of an iterative cycle that include: (1) building capacity to mitigate issues, (2) preparing for the inevitable onset of issues, (3) responding to issues as they emerge, and (4) strategies to recover from any damage incurred.
In early 2020, the VA embarked on an EHR transition from a homegrown, legacy EHR system, developed by VA clinicians and used since the 1990s, to a new commercial system by the Oracle-Cerner Corporation. The primary objectives of this transition were to standardize care and improve interoperability between VA Medical Centers nationwide and the Department of Defense (DoD). Spanning over a decade, this transition plan is scheduled to roll out to all VA medical centers and outpatient clinics.
In this manuscript, we present data from the Mann-Grandstaff VA Medical Center in Spokane, WA, VA’s first EHR transition site. The study uses qualitative methods with clinician and staff interviews as part of a larger multi-method evaluation of the EHR transition. Our overarching goal is to identify and share recommendations to improve VA’s EHR transition efforts; rather than be guided by a theoretical framework our study design including the interview guides [ 14 , 15 ] were based primarily on what was being experienced. An experienced team of ten qualitative methodologists and analysts conducted the study.
This evaluation was designated as non-research/quality improvement work by the VA Bedford Healthcare System Institutional Review Board deeming it exempt from needing an informed consent. Study materials, including interview guides with verbal consent procedures, were reviewed and approved by labor unions and by the VA Bedford Healthcare System Institutional Review Board; all methods were carried out in accordance with local and national VA guidelines and regulations.
Interview guides and an outline of the data collection plans were reviewed and approved by relevant national unions before beginning recruitment.
Recruitment
Recruitment began in July 2020, before the first site implemented the new EHR. Prior to collecting data, we met with site leadership to get buy-in and support for the study, understand local context, determine how the site was approaching the transition, and to obtain the names of clinicians and staff for potential interviews. All potential participants were invited by email to participate in a one-hour voluntary interview conducted on Microsoft Teams® about their experiences with this transition; we used snowball sampling during interviews to expand the pool of interviewees. Verbal permission for audio recording of interviews was obtained immediately prior to the interview. Interview participants were informed that they could skip any questions, pause or stop the recording, and stop the interview at any time and were invited to ask questions before beginning the interview.
Most participants were interviewed at multiple timepoints; these included pre-implementation interviews, brief check-ins, and post-implementation interviews (Table 1 ). At the end of the pre-implementation interview, participants were invited to participate in 3–4 additional, shorter (15–20 min), check-in interviews where information about any changes in the transition process, context, or experience could be discussed. Most initial interviewees, in addition to three new participants, participated in post-implementation interviews (35–60 min; approximately 2–3 months and 10–12 months after the implementation) to reflect on the entire transition process.
Data collection
Experienced qualitative interviewers included PhD trained qualitative methodologist and masters level qualitative analysts (JB, SB, AC, EK, MM, GS) conducted individual interviews with clinicians and staff, aligning to a semi-structured interview guide with follow-up probes using the participant’s words to elicit rich responses grounded in the data [ 16 ]. The guide was designed to inform ongoing efforts to improve the rollout of the new EHR. Six main categories were covered in our interview guides, including (1) attitudes toward the new software, (2) information communicated about the transition, (3) training and education, (4) resources, (5) prior experience with EHRs, and (6) prior experiences with EHR transitions. After piloting the interview guide with a clinician, initial interviews were completed between September and October 2020 and averaged ∼ 45 min in duration. Two-month and one-year post-implementation interview guides included an additional question, “Has the Cerner transition affected Vets?”; data presented here largely draw from responses to this question. Check-ins (October 2020– December 2020) took ∼ 15 min; two-month post-implementation interviews (December 2020– January 2021) and one-year post-implementation interviews (October 2020 - November 2021) took ∼ 45 min. Audio recordings of all interviews were professionally transcribed. To ensure consistency and relationship building, participants were scheduled with the same interviewer for the initial and subsequent interviews whenever feasible (i.e., check-ins and post-implementation interviews). Immediately following each interview, interviewers completed a debrief form where highlights and general reflections were noted.
Throughout the data collection process, interviewers met weekly with the entire qualitative team and the project principal investigators to discuss the recruitment process, interview guide development, and reflections on data collection. To provide timely feedback to leadership within the VA, a matrix analysis [ 17 ] was conducted concurrently with data collection using the following domains: training, roles, barriers, and facilitators. Based on these domains, the team developed categories and subcategories, which formed the foundation of an extensive codebook.
Data analysis
All interviewers also coded the data. We used inductive and deductive content analysis [ 18 ]. Interview transcripts were coded in ATLAS.ti qualitative data analysis software (version 9). A priori codes and categories (based on the overall larger project aims and interview guide questions) and emergent codes and categories were developed to capture concepts that did not fit existing codes or categories [ 18 ]. Codes related to patient experience and clinician interactions with patients were extracted and analyzed using qualitative content analysis to identify themes [ 18 ]. Themes were organized according to their fit within the discrete stages of an emergency preparedness framework to generate recommendations for future rollout. In total, we examined data from 111 interviews with 24 VA clinicians and staff (excluding the initial 11 stakeholder meetings (from the 122 total interviews) that were primarily for stakeholder engagement). We focused on participants’ responses related to their experiences interacting with patients during the EHR transition.
Exemplar quotes primarily came from participants’ responses to the question, “Has the Cerner transition affected Vets?” and addressed issues stemming from use of the patient portal. This included both clinicians’ direct experiences with the portal and indirect experiences when they heard from patients about disruptions when using the portal. We identified four themes related to clinicians’ and staff members’ reported experiences: (1) stress associated with the unreliability of routine portal functions and inaccurate migrated information; (2) concern about patients’ ability to learn to use a new portal (especially older patients and special populations); (3) frustration with apparent inadequate dissemination of patient informational materials along with their own lack of time and resources to educate patients on use of the new portal; and (4) burden of additional tasks on top of their daily workload when patients needed increased in-person attention due to issues with the portal.
Stress associated with the unreliability of routine portal functions and inaccurate migrated information
One participant described the portal changes as, “It’s our biggest stress, it’s the patients’ biggest stress… the vets are definitely frustrated; the clinicians are; so I would hope that would mean that behind the scenes somebody is working on it” (P5, check-in).
Participants expressed significant frustration when they encountered veterans who were suddenly unable to communicate with them using routine secure messaging. These experiences left them wondering whether messages sent to patients were received.
Those that use our secure messaging, which has now changed to My VA Health, or whatever it’s called, [have] difficulty navigating that. Some are able to get in and send the message. When we reply to them, they may or may not get the reply. Which I’ve actually asked one of our patients, ‘Did you get the reply that we took care of this?’ And he was like, ‘No, I did not (P11, 2-months post)
Participants learned that some patients were unable to send secure messages to their care team because the portal contained inaccurate or outdated appointment and primary site information.
I’ve heard people say that the appointments aren’t accurate in there… veterans who have said, ‘yeah, it shows I’m registered,’ and when they go into the new messaging system, it says they are part of a VA that they haven’t gone to in years, and that’s the only area they can message to, they can’t message to the [site] VA, even though that’s where they’ve actively being seen for a while now. (P20, 2-months post)
After the EHR transition, participants noted that obtaining medications through the portal, which was once a routine task, became unreliable. They expressed concern around patients’ ability to obtain their medications through the portal, primarily due to challenges with portal usability and incomplete migration of medication lists from the former to the new EHR.
I think it’s been negative, unfortunately. I try to stay optimistic when I talk to [patients], but they all seem to be all having continued difficulty with their medications, trying to properly reorder and get medications seems to still be a real hassle for them. (P17, one-year post) …the medications, their med list just didn’t transfer over into that list [preventing their ability to refill their medications]. (P13, 2-months post)
Concern about patients’ ability to learn to use a new portal
Clinicians and staff expressed concerns around veterans’ ability to access, learn, and navigate a new portal system. Clinicians noted that even veterans who were adept at using the prior electronic portal or other technologies also faced difficulties using the new portal.
They can’t figure out [the new portal], 99% of them that used to use our [old] portal, the electronic secure messaging or emailing between the team, they just can’t use [the new one]. It’s not functioning. (P13, one-year post) Apparently, there’s a link they have to click on to make the new format work for them, and that’s been confusing for them. But I still am having a lot of them tell me, I had somebody recently, who’s very tech savvy, and he couldn’t figure it out, just how to message us. I know they’re still really struggling with that. (P5, 2-months post) And it does seem like the My Vet [my VA Health, new portal], that used to be MyHealtheVet [prior portal], logging on and getting onto that still remains really challenging for a large number of veterans. Like they’re still just unable to do it. So, I do think that, I mean I want to say that there’s positive things, but really, I struggle (P17, one-year post)
Participants recognized difficulties with the new system and expressed empathy for the veterans struggling to access the portal.
I think that a lot of us, individually, that work here, I think we have more compassion for our veterans, because they’re coming in and they can’t even get onto their portal website. (P24, one-year post)
Participants acknowledged that learning a new system may be especially difficult for older veterans or those with less technology experience.
But, you know, veterans, the general population of them are older, in general. So, their technologic skills are limited, and they got used to a system and now they have to change to a new one. (P13, 2-months post) So, for our more elderly veterans who barely turn on the computer, they’re not getting to this new portal. (P8, check in) And you know, I do keep in mind that this is a group of people who aren’t always technologically advanced, so small things, when it’s not normal to them, stymie them.(P13, one-year post)
Concerns were heightened for veterans who were more dependent on the portal as a key element in their care due to specific challenges. One participant pointed out that there may be populations of patients with special circumstances who depend more heavily on the prior portal, MyHealtheVet.
I have veterans from [specific region], that’s the way they communicate. Hearing impaired people can’t hear on the phone, the robocall thing, it doesn’t work, so they use MyHealtheVet. Well, if that goes away, how is that being communicated to the veteran? Ok? (P18, Check-in)
Frustration with inadequate dissemination of information to veterans about EHR transition and use of new portal
Participants were concerned about poor information dissemination to patients about how to access the new portal. During medical encounters, participants often heard from patients about their frustrations accessing the new portal. Participants noted that they could only give their patients a phone number to call for help using the new system but otherwise lacked the knowledge and the time to help them resolve new portal issues. Some clinicians specifically mentioned feeling ill-equipped to handle their patients’ needs for assistance with the new portal. These experiences exacerbated clinician stress during the transition.
Our veterans were using the MyHealtheVet messaging portal, and when our new system went up, it transitioned to My VA Health, but that wasn’t really communicated to the veterans very well. So, what happened was they would go into their MyHealtheVet like they had been doing for all of these years, to go in and request their medications, and when they pulled it up it’d show that they were assigned to a clinician in [a different state], that they have no active medications. Everything was just messed up. And they didn’t know why because there was no alert or notification that things would be changing. (P8, check in) I field all-day frustration from the veterans. And I love my job, I’m not leaving here even as frustrated as I am, because I’m here for them, not to, I’m here to serve the veterans and I have to advocate for them, and I know it will get better, it can’t stay like this. But I constantly field their frustrations.… So, I give them the 1-800 number to a Cerner help desk that helps with that, and I’ve had multiple [instances of] feedback that it didn’t help. (P13, one-year post) And [the patients are] frequently asking me things about their medication [within the portal], when, you know, I can’t help them with that. So, I have to send them back up to the front desk to try to figure out their medications. (P17, one-year post)
Veteran frustration and the burden of additional tasks due to issues with the portal
Clinicians reported that veterans expressed frustration with alternatives to the portal, including long call center wait times. Some veterans chose to walk into the clinic without an appointment rather than wait on the phone. Clinicians noted an increase in walk-ins by frustrated veterans, which placed added workload on clinics that were not staffed to handle the increase in walk-ins.
It’s been kind of clunky also with trying to get that [new portal] transitioned. And then that’s created more walk-ins here, because one, the vets get frustrated with the phone part of it, and then MyHealtheVet (prior portal) not [working], so they end up walking [into the clinic without an appointment]. (P19, check-in) In terms of messages, they can’t necessarily find the clinician they want to message. We had a veteran who came in recently who wanted to talk to their Rheumatologist, and it’s like, yeah, I typed in their name, and nothing came up. So, they have to try calling or coming in. (P20, 2-months post)
In summary, participants described the new patient portal as a source of stress for both themselves and their patients.
In addition to their own direct experience using a new EHR to communicate with their patients, clinicians and staff can be affected by perceptions of their patients’ experiences during an EHR transition [ 19 ]. At this first VA site to transition to the new EHR, clinicians and staff shared their concerns about their patients’ experiences using the portal. They were particularly troubled by unreliability of the secure messaging system and challenges patients faced learning to use the new system without proper instruction. Moreover, clinicians were alarmed to hear about patients having to make in-person visits– especially unplanned (i.e., walk in) ones– due to challenges with the new portal. Each of these issues needs to be addressed to ensure veteran satisfaction. However, the only solution participants could offer to frustrated patients was the telephone number to the help desk, leaving them with no clear knowledge of a solution strategy or a timeline for resolution of the issues.
We propose applying emergency preparedness actions to future EHR rollouts: mitigate, prepare, respond, and recover (Fig. 1 ) [ 13 ]. By applying these actions, patient portal disruptions may be alleviated and patients’ communication with their clinicians and access to care can be maintained. For example, issues stemming from a disruption in the portal may be mitigated by first identifying and understanding which patients typically use the portal and how they use it. Sites can use this information to prepare for the transition by disseminating instructional materials to staff and patients on how to access the new portal, targeting the most common and critical portal uses. Sites can respond to any expected and emerging portal disruptions by increasing access to alternative mechanisms for tasks disrupted by and typically completed within the portal. After the transition, recovery can begin by testing and demonstrating the accuracy and reliability of functions in the new portal. These actions directly address reported clinician concerns and can help maintain patient-clinician communication, and access to care.
The emergency preparedness framework was applied. This framework includes 4 actions: (1) mitigate, (2) prepare, (3) respond, and (4) recover. These actions can be repeated. Recommendations for how each action (1–4) can be applied to a portal transition are included in each blue quadrant of the circle
Sites could mitigate issues by first understanding which patients will be most affected by the transition, such as those who rely heavily on secure messaging. Reliable use of secure messaging within the VA facilitates positive patient-clinician relationships by providing a mechanism for efficient between-visit communication [ 20 , 21 , 22 , 23 ]. During the EHR transition, clinicians and staff became concerned about the well-being of patients from whom they weren’t receiving messages and those who depended on the portal to complete certain tasks. Since secure messaging is often initiated by patients to clinicians [ 23 ], clinicians will likely be unaware that messages are being missed. Understanding how and which patients currently use the portal and anticipating potential portal needs is a first step toward mitigating potential issues.
Despite efforts to inform Veterans of the EHR transition and patient portal [ 24 ] including information sent to a Veteran by email, direct mail, postings on VA websites, and a town hall, our findings agree with those of Fix and colleagues [ 10 ] and suggest that many Veterans were unprepared for the transition. Our findings suggest that end users heard that more is needed to improve the dissemination of knowledge about the transition and how to navigate the new patient portal to both VA employees and the patients they serve.
Preparations for the transition should prioritize providing VA clinicians and staff with updated information and resources on how to access and use the new portal [ 25 ]. VA clinicians deliver quality care to veterans and many VA employees are proud to serve the nation’s veterans and willing to go the extra mile to support their patients’ needs [ 26 ]. In this study, participants expressed feeling unprepared to assist or even respond to their patients’ questions and concerns about using the new portal. This unpreparedness contributed to increased clinician and staff stress, as they felt ill-equipped to help their patients with portal issues. Such experiences can negatively affect the patient-clinician relationship. Preparing clinicians and patients about an upcoming transition, including technical support for clinicians and patients, may help minimize these potential issues [ 10 , 27 ]. Specialized training about an impending transition, along with detailed instructions on how to gain access to the new system, and a dedicated portal helpline may be necessary to help patients better navigate the transition [ 23 , 28 ].
In addition to a dedicated helpline, our recommendations include responding to potential changes in needed veteran services during the transition. In our study, participants observed more veteran walk-ins due to challenges with the patient portal. Health systems need to anticipate and address this demand by expanding access to in-person services and fortifying other communication channels. For example, sites could use nurses to staff a walk-in clinic to handle increases in walk-in traffic and increase call center capacity to handle increases in telephone calls [ 29 ]. Increased use of walk-in clinics have received heightened attention as a promising strategy for meeting healthcare demands during the COVID-19 pandemic [ 30 ] and can potentially be adapted for meeting care-related needs during an EHR transition. These strategies can fill a gap in communication between clinicians and their patients while patients are learning to access and navigate a new electronic portal.
Finally, there is a need for a recovery mechanism to restore confidence in the reliability of the EHR and the well-being of clinicians and staff. Healthcare workers are experiencing unprecedented levels of stress [ 31 ]. A plan must be in place to improve and monitor the accuracy of data migrated, populated, and processed within the new system [ 2 ]. Knowing that portal function is monitored could help ease clinician and staff concerns and mitigate stress related to the transition.
Limitations
This study has several limitations. First, data collection relied on voluntary participation, which may introduce self-selection response bias. Second, this work was completed at one VA medical center that was the first site in the larger enterprise-wide transition, and experiences at other VAs or healthcare systems might differ substantially. Third, we did not interview veterans and relied entirely on secondhand accounts of patient experiences with the patient portal. Future research should include interviews with veterans during the transition and compare veteran and VA employee experiences.
Despite a current delay in the deployment of the new EHR at additional VA medical centers, findings from this study offer timely lessons that can ensure clinicians and staff are equipped to navigate challenges during the transition. The strategies presented in this paper could help maintain patient-clinician communication and improve veteran experience. Guided by the emergency preparedness framework, recommended strategies to address issues presented here include alerting those patients most affected by the EHR transition, being prepared to address patients’ concerns, increasing staffing for the help desk and walk-in care clinics, and monitoring the accuracy and reliability of the portal to provide assurance to healthcare workers that patients’ needs are being met. These strategies can inform change management at other VA medical centers that will soon undergo EHR transition and may have implications for other healthcare systems undergoing patient portal changes. Further work is needed to directly examine the perspectives of veterans using the portals, as well as the perspectives of both staff and patients in the growing number of healthcare systems beyond VA that are preparing for an EHR-to-EHR transition.
Data availability
Deidentified data analyzed for this study are available from the corresponding author on reasonable request.
Abbreviations
Electronic health record
Department of Veterans Affairs
VA Medical Centers
Department of Defense
Huang C, Koppel R, McGreevey JD 3rd, Craven CK, Schreiber R. Transitions from one Electronic Health record to another: challenges, pitfalls, and recommendations. Appl Clin Inf. 2020;11(5):742–54.
Article Google Scholar
Penrod LE. Electronic Health Record Transition considerations. PM R. 2017;9(5S):S13–8.
Article PubMed Google Scholar
Cogan AM, Haltom TM, Shimada SL, Davila JA, McGinn BP, Fix GM. Understanding patients’ experiences during transitions from one electronic health record to another: a scoping review. PEC Innov. 2024;4:100258. https://doi.org/10.1016/j.pecinn.2024.100258 . PMID: 38327990; PMCID: PMC10847675.
Article PubMed PubMed Central Google Scholar
Powell KR. Patient-perceived facilitators of and barriers to Electronic Portal Use: a systematic review. Comput Inf Nurs. 2017;35(11):565–73.
Google Scholar
Wilson-Stronks A, Lee KK, Cordero CL, et al. One size does not fit all: meeting the Health Care needs of diverse populations. Oakbrook Terrace, IL: The Joint Commission; 2008.
Carini E, Villani L, Pezzullo AM, Gentili A, Barbara A, Ricciardi W, Boccia S. The Impact of Digital Patient Portals on Health outcomes, System Efficiency, and patient attitudes: updated systematic literature review. J Med Internet Res. 2021;23(9):e26189.
Home -. My HealtheVet - My HealtheVet (va.gov).
Nazi KM, Turvey CL, Klein DM, Hogan TP. A decade of veteran voices: examining patient Portal Enhancements through the Lens of user-centered design. J Med Internet Res. 2018;20(7):e10413. https://doi.org/10.2196/10413 .
Tapuria A, Porat T, Kalra D, Dsouza G, Xiaohui S, Curcin V. Impact of patient access to their electronic health record: systematic review. Inf Health Soc Care. 2021;46:2.
Fix GM, Haltom TM, Cogan AM, et al. Understanding patients’ preferences and experiences during an Electronic Health Record Transition. J GEN INTERN MED. 2023. https://doi.org/10.1007/s11606-023-08338-6 .
Monturo C, Brockway C, Ginev A. Electronic Health Record Transition: the patient experience. CIN: Computers Inf Nurs. 2022;40:1.
Tian D, Hoehner CM, Woeltje KF, Luong L, Lane MA. Disrupted and restored patient experience with transition to New Electronic Health Record System. J Patient Exp. 2021;18:8.
Emergency management programs for healthcare facilities. the four phases of emergency management. US Department of Homeland Security website: https://www.hsdl.org/?view&did=765520 . Accessed 28 Aug 2023.
Ahlness EA, Orlander J, Brunner J, Cutrona SL, Kim B, Molloy-Paolillo BK, Rinne ST, Rucci J, Sayre G, Anderson E. Everything’s so Role-Specific: VA Employee Perspectives’ on Electronic Health Record (EHR) transition implications for roles and responsibilities. J Gen Intern Med. 2023;38(Suppl 4):991–8. Epub 2023 Oct 5. PMID: 37798577; PMCID: PMC10593626.
Rucci JM, Ball S, Brunner J, Moldestad M, Cutrona SL, Sayre G, Rinne S. Like one long battle: employee perspectives of the simultaneous impact of COVID-19 and an Electronic Health Record Transition. J Gen Intern Med. 2023;38(Suppl 4):1040–8. https://doi.org/10.1007/s11606-023-08284-3 . Epub 2023 Oct 5. PMID: 37798583; PMCID: PMC10593661.
Sayre G, Young J. Beyond open-ended questions: purposeful interview guide development to elicit rich, trustworthy data [videorecording]. Seattle (WA): VA Health Services Research & Development HSR&D Cyberseminars; 2018.
Averill JB. Matrix analysis as a complementary analytic strategy in qualitative inquiry. Qual Health Res. 2002;12:6855–66.
Elo S, Kyngäs H. The qualitative content analysis process. J Adv Nurs. 2008;62:1107–15.
Haun JN, Lind JD, Shimada SL, Simon SR. Evaluating Secure Messaging from the veteran perspective: informing the adoption and sustained use of a patient-driven communication platform. Ann Anthropol Pract. 2013;372:57–74.
Kittler AF, Carlson GL, Harris C, Lippincott M, Pizziferri L, Volk LA, et al. Primary care physician attitudes toward using a secure web-based portal designed to facilitate electronic communication with patients. Inf Prim Care. 2004;123:129–38.
Shimada SL, Petrakis BA, Rothendler JA, Zirkle M, Zhao S, Feng H, Fix GM, Ozkaynak M, Martin T, Johnson SA, Tulu B, Gordon HS, Simon SR, Woods SS. An analysis of patient-provider secure messaging at two Veterans Health Administration medical centers: message content and resolution through secure messaging. J Am Med Inf Assoc. 2017;24:5.
Jha AK, Perlin JB, Kizer KW, Dudley RA. Effect of the transformation of the Veterans Affairs Health Care System on the quality of care. N Engl J Med. 2003;348:22.
McAlearney AS, Walker DM, Gaughan A, Moffatt-Bruce S, Huerta TR. Helping patients be better patients: a qualitative study of perceptions about Inpatient Portal Use. Telemed J E Health. 2020;26:9.
https://www.myhealth.va.gov/mhv-portal-web/transitioning-to-my-va-health-learn-more .
Beagley L. Educating patients: understanding barriers, learning styles, and teaching techniques. J Perianesth Nurs. 2011;26:5.
Moldestad M, Stryczek KC, Haverhals L, Kenney R, Lee M, Ball S, et al. Competing demands: Scheduling challenges in being veteran-centric in the setting of Health System initiatives to Improve Access. Mil Med. 2021;186:11–2.
Adusumalli J, Bhagra A, Vitek S, Clark SD, Chon TY. Stress management in staff supporting electronic health record transitions: a novel approach. Explore (NY). 2021;17:6.
Heponiemi T, Gluschkoff K, Vehko T, Kaihlanen AM, Saranto K, Nissinen S, et al. Electronic Health Record implementations and Insufficient Training Endanger nurses’ Well-being: cross-sectional survey study. J Med Internet Res. 2021;23:12e27096.
Laurant M, van der Biezen M, Wijers N, Watananirun K, Kontopantelis E, van Vught AJ. Nurses as substitutes for doctors in primary care. Cochrane Database Syst Rev. 201;7(7):CD001271.
Elnahal S, Kadakia KT, Gondi S, How, U.S. Health systems Can Build Capacity to Handle Demand Surges. Harvard Business Review. 2021. https://hbr.org/2021/10/how-u-s-health-systems-can-build-capacity-to-handle-demand-surges/ Accessed 25 Nov 2022.
George RE, Lowe WA. Well-being and uncertainty in health care practice. Clin Teach. 2019;16:4.
Download references
Acknowledgments
We acknowledge and thank members of the EMPIRIC Evaluation qualitative and supporting team for their contributions to this work including Ellen Ahlness, PhD, Julian Brunner, PhD, Adena Cohen-Bearak, MPH, M.Ed, Leah Cubanski, BA, Christine Firestone, Bo Kim, PhD, Megan Moldestad, MS, and Rachel Smith. We greatly appreciate the staff at the Mann-Grandstaff VA Medical Center and associated community-based outpatient clinics for generously sharing of their time and experiences participating in this study during this challenging time.
The “EHRM Partnership Integrating Rapid Cycle Evaluation to Improve Cerner Implementation (EMPIRIC)” (PEC 20–168) work was supported by funding from the US Department of Veterans Affairs, Veterans Health Administration, Health Services Research & Development Quality Enhancement Research Initiative (QUERI) (PEC 20–168). The findings and conclusions in this article are those of the authors and do not necessarily reflect the views of the Veterans Health Administration, Veterans Affairs, or any participating health agency or funder.
Author information
Authors and affiliations.
VA Northeast Ohio Healthcare System, 10701 East Blvd., Research Service 151, 44106, Cleveland, OH, USA
Sherry L. Ball
Center for Healthcare Organization and Implementation Research, VA Boston Healthcare System, Boston, MA, USA
Bo Kim & Seppo T. Rinne
Department of Psychiatry, Harvard Medical School, Boston, MA, USA
Center for Healthcare Organization and Implementation Research, VA Bedford Healthcare System, Bedford, MA, USA
Sarah L. Cutrona & Brianne K. Molloy-Paolillo
Division of Health Informatics & Implementation Science, Department of Population and Quantitative Health Sciences, University of Massachusetts Chan Medical School, Worcester, MA, USA
Sarah L. Cutrona
Seattle-Denver Center of Innovation for Veteran-Centered and Value-Driven Care, VHA Puget Sound Health Care System, Seattle, WA, USA
Ellen Ahlness, Megan Moldestad & George Sayre
University of Washington School of Public Health, Seattle, WA, USA
George Sayre
Geisel School of Medicine at Dartmouth, Hannover, NH, USA
Seppo T. Rinne
You can also search for this author in PubMed Google Scholar
Contributions
S.R. designed the larger study. G.S. was the qualitative methodologist who led the qualitative team. S.B., E.A., and M.M. created the interview guides and completed the interviews; Data analysis, data interpretation, and the initial manuscript draft were completed by S.B. and B.K. S.C. and B.M. worked with the qualitative team to finalize the analysis and edit and finalize the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Sherry L. Ball .
Ethics declarations
Ethics approval and consent to participate.
This evaluation was designated as non-research/quality improvement by the VA Bedford Healthcare System Institutional Review Board. All methods were carried out in accordance with local and national VA guidelines and regulations for quality improvement activities. This study included virtual interviews with participants via MS Teams. Employees volunteered to participate in interviews and verbal consent was obtained to record interviews. Study materials, including interview guides with verbal consent procedures, were reviewed and approved by labor unions and determined as non-research by the VA Bedford Healthcare System Institutional Review Board.
Consent for publication
Not applicable.
The findings and conclusions in this paper are those of the authors and do not necessarily represent the official position of the Department of Veterans Affairs.
Prior presentations
Ball S, Kim B, Moldestad M, Molloy-Paolillo B, Cubanski L, Cutrona S, Sayre G, and Rinne S. (2022, June). Electronic Health Record Transition: Providers’ Experiences with Frustrated Patients. Poster presentation at the 2022 AcademyHealth Annual Research Meeting. June 2022.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Ball, S.L., Kim, B., Cutrona, S.L. et al. Clinician and staff experiences with frustrated patients during an electronic health record transition: a qualitative case study. BMC Health Serv Res 24 , 535 (2024). https://doi.org/10.1186/s12913-024-10974-5
Download citation
Received : 29 August 2023
Accepted : 09 April 2024
Published : 26 April 2024
DOI : https://doi.org/10.1186/s12913-024-10974-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- EHR transition
- Patient experience
- Clinician experience
- Qualitative analysis
BMC Health Services Research
ISSN: 1472-6963
- General enquiries: [email protected]
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 25 April 2024
Association between Baltic sea diet and healthy Nordic diet index with risk of non-alcoholic fatty liver disease: a case–control study
- Zahra Rasoulizadeh 1 ,
- Abolfazl Namazi 2 ,
- Mohammad Hassan Sohouli 3 , 4 ,
- Pejman Rohani 4 ,
- Azita Hekmatdoost 5 &
- Mahdieh Hosseinzadeh 6
Scientific Reports volume 14 , Article number: 9537 ( 2024 ) Cite this article
14 Accesses
1 Altmetric
Metrics details
- Endocrinology
- Gastroenterology
- Risk factors
Recent evidence shows the beneficial effects of Baltic Sea diet score (BSDS) and healthy Nordic diet index (HNDI) on chronic diseases, however, there is no evidence to investigate them on the risk of non-alcoholic fatty liver disease (NAFLD). The purpose of this study was to investigate the associations between BSDS and HNDI with the risk of NAFLD. In this case–control study, 552 people in good health and 340 people with NAFLD over the age of 18 took part. The evaluation of BSDS and HNDI employed a validated 168-item semi-quantitative food frequency questionnaire (FFQ). Binary logistic regression was used to determine how OBS and NAFLD are related. The mean BSDS and HNDI were 16.00 ± 2.49 and 11.99 ± 2.61, respectively. The final model's confounder adjustment revealed that greater HNDI adherence scores gave protection against the occurrence of NAFLD (odds ratio [OR]: 0.42; 95% confidence interval [CI] 0.18–0.98; P for trend = 0.043). In addition, those with the highest BSDS scores had significantly lower risks of developing NAFLD compared to subjects with the lowest scores (OR = 0.48, 95% CI 0.32–0.89; p for trend = 0.003). Our findings showed that following a healthy Nordic diet can significantly prevent the risk of developing NAFLD, and suggest that the highly nutritious components of the Nordic diet are beneficial for the prevention of NAFLD.
Similar content being viewed by others

Favorable association between Mediterranean diet (MeD) and DASH with NAFLD among Iranian adults of the Amol Cohort Study (AmolCS)
Association between healthy beverage index and nonalcoholic fatty liver disease in the Ravansar noncommunicable disease cohort study
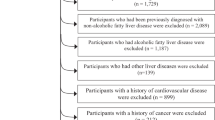
Higher plain water intake is related to lower newly diagnosed nonalcoholic fatty liver disease risk: a population-based study
Introduction.
The most prevalent kind of chronic liver disease is non-alcoholic fatty liver disease (NAFLD), which is characterized by a variety of fat liver conditions that can lead to cirrhosis and severe liver disease 1 . Adult NAFLD prevalence is estimated to be 20–25 percent worldwide, as well as 5–18 and 25–31% among populations in Iran and Asian nations, respectively 2 , 3 , 4 . Finding practical methods to prevent and cure NAFLD is essential because it places a heavy financial strain on the healthcare system and lowers quality of life as the illness worsens 5 . It is believed that poor dietary practices, particularly the intake of a high-calorie diet heavy in saturated fatty acids or simple carbohydrates, are mostly to blame for this high prevalence of NAFLD 6 . There is not yet agreement on the pharmacological treatments for NAFLD. The cornerstone of NAFLD therapy is still thought to be lifestyle therapies that emphasize physical exercise and a balanced diet in terms of both quality and quantity 1 .
This treatment's cornerstone is a change in lifestyle that starts with a decrease in the intake of foods that are rich in red meat, trans and saturate fatty acids, processed carbohydrates, and high-fructose corn syrup; low in fiber; and high in energy density 7 . The two well-researched healthy eating patterns (rich in vegetables, fruits, types of antioxidant micronutrients, high fiber, and whole grains) are the Mediterranean and Dietary Approaches to Stop Hypertension (DASH) diets 8 , the effect of which on the reduction in NAFLD odds has been demonstrated 9 , 10 . A healthy Nordic diet (HND), also known as the Baltic Sea diet, is an additional plant-based dietary pattern that refers to a nutritional profile that is prevalent in the Nordic regions 11 . The HND is rich in high consumption of fruits and vegetables such as cabbage, barriers, legumes and root vegetables, fresh herb, plants and mushrooms, potatoes and nuts, whole grains from oat, repressed oil, and also emphasize the importance on consumption of white and low-fat meat, lower amount of sugar-sweetened products 12 . The composition of food differs between communities, making it difficult to assess connections between specific dietary components such as micronutrients and macronutrients with health outcomes. Dietary scores were developed to include the synergistic effects and combinations of various meals and minerals. They act as a gauge of dietary adherence and indicate a summary value of consumed foods and nutrients 13 . The Baltic Sea Diet Score (BSDS) was developed to quantify a HND based on traditional Nordic foods eaten in Finland. The idea behind the HND prioritize the healthy foods which locally produced, easily accessible, and culturally acceptable. The diet is rich in fruits, barriers, vegetables, low- or non-fat dietary, repressed oil and fish, and low intake of processed meat and alcohol 14 .
The diet is high in fruits consumption, nuts, vegetables, low- or non-fat dietary, repressed oil and fish, and low in processed meats and alcohol 14 .
Previous research has demonstrated that a higher BSDS is connected with a lower risk of abdominal obesity, improved physical ability in old age, and a lower risk of increased C-reactive protein levels which are also known as risk factors of NAFLD disease 15 , 16 , 17 . Other comparable diet scores that have been devised to characterize a HND have also been associated with a reduction in disease risk factors. Despite the fact the relationship with risk of illnesses or death are inconsistent 18 .
Therefore, due to rising frequency of NAFLD in communities and limited data about adherence to HND and the risk of NAFLD, we aimed to examine whether following HND, based on BSDS and Healthy Nordic Diet Index (HNDI) was related with risk of NAFLD among Iranian adults.
Study design and population
This study encompassed a case–control design conducted from 2020 to 2022, involving individuals aged 18 and above who were recently diagnosed with NAFLD. The healthy control group consisted of individuals admitted to Taleghani Hospital in Tehran, Iran, and the academic liver disease clinics of Shahid Sadoughi University of Medical Sciences in Yazd, Iran. The case group included 552 consecutive patients diagnosed with NAFLD by a gastroenterologist. The control group consisted of 340 people without a previous history of NAFLD, who were recruited from the same hospital. The patient sampling technique was validated by two dietitians. The following criteria were used in the diagnosis of NAFLD 19 , 20 , 21 : Chronic elevation of liver enzymes, defined as liver enzymes exceeding 19 U/L for women and 30 U/L for men, along with abstention from alcohol consumption, ultrasonography (US) results indicating NAFLD, liver biopsy findings consistent with NAFLD (Grades II and III), and the exclusion of alternative causes of liver disease. Furthermore, the individuals comprising the case group were directed to our medical facilities for assessment using Fibroscan 19 . The confirmation of non-alcoholic steatohepatitis diagnosis was conducted by a gastroenterologist upon observing Fibroscan results indicating a controlled attenuation parameter score exceeding 237 and a fibrosis score surpassing 7. Additionally, the control group, consisting of individuals without a history of NAFLD, was recruited from several outpatient clinics within the same hospital, including dermatology, ophthalmology, and otorhinolaryngology. The healthy control group consisted of individuals who adhered to a regular dietary regimen for a duration of six months before to the study. Additionally, these individuals had no prior medical records indicating the presence of chronic or inflammatory conditions, including but not limited to diabetes, gastrointestinal disorders, cardiovascular disorders, and cancer. The control group's inclusion criteria were determined by laboratory tests and liver ultrasonography to confirm the absence of hepatic steatosis at any stage. Patients that were excluded from the study met the following criteria: Long-term dietary modifications, weight loss, and specific medical conditions, including hepatic or renal diseases (such as nonalcoholic steatohepatitis (NASH), alcoholic fatty liver disease, Wilson's disease, cirrhosis, autoimmune liver disease, hemochromatosis, and viral infections), diabetes, cancer, thyroid disorder, and autoimmune disease, are factors that may require consideration. Demographic, economic, and social questionnaires were used to gather data pertaining to age, degree of education, work status, medical history, smoking status, usage of particular pharmaceuticals (excluding routine NAFLD medications), and dietary history during the preceding six months. The researchers used General Practice Physical Activity Questionnaires (GPPAQs) to assess the participants' levels of physical activity. GPPAQ is a straightforward assessment tool used to evaluate an individual's present level of physical activity 21 . Nutritionists were utilized as interviewers in this research. As a result, all patients completed the survey questions completely.
The present study received approval from Shahid Beheshti University of Medical Sciences in Tehran, Iran, as well as Shahid Sadoughi University of Medical Sciences in Yazd, Iran. We confirm that all methods were performed in accordance with relevant guidelines and regulations and we also confirm that informed consent was obtained from all individuals and/or their guardians or legal guardians.
The minimum required sample size for this study was determined by considering the hypothesis of a 1.5-fold reduction in the odds of NAFLD associated with the intervention of interest. Hence, taking into account a type I error rate of 5%, a study power of 90%, and an approximate ratio of controls to cases of 1.5, the minimum required sample size was calculated to be 450 people in the case group and 300 people in the control group.
Dietary assessment
Data on dietary consumption during the preceding year were collected using a semi-quantitative validated food-frequency questionnaire (FFQ) consisting of 168 food items 22 . The FFQ included a comprehensive list of typical Iranian foods and their corresponding serving sizes. Participants provided self-reports on the FFQ, indicating the average portion size and frequency of consumption for each food item. The frequency of consumption options ranged from never to daily, with specific categories such as 2–3 times per month, once per week, 2–4 times per week, 5–6 times per week, and daily. Serving quantities were measured in grams using standard Iranian household measurements 23 . Daily nutrient consumptions for each individual were calculated by utilizing the United States Department of Agriculture's (USDA) national nutritional databank 24 . The nutritional and calorie content of the foods were analyzed using a customized version of Nutritionist 4, specifically designed for Iranian meals, developed by First Databank Inc., Hearst Corp., San Bruno, CA, USA.
Dietary indices
The BSDS has a total of nine parts, as enumerated below. It was developed using the methodologies described in Kanerva et al. 14 : 1 1) Various categories of fruits and berries, vegetables encompassing roots, pulses, and other varieties, cereals excluding rice and pasta, fish, both processed and unprocessed meat, low-fat or fat-free milk, 7) the ratio of polyunsaturated fatty acids (PUFAs) to saturated fatty acids (SFAs) and trans fatty acids, 8) Alcohol has been excluded from the BSDS due to its prohibition in Iran, 9) Additionally, the BSDS considers total fat and its proportion as a percentage of total energy intake, as indicated in point eight. The intake of participants was used to classify each component of the BSDS into tertiles (Q1-Q3). In the case of healthy items, scores of 1, 2, and 3 were assigned to tertiles Q1 to Q3, respectively. However, for harmful items, namely meat and total fat, the scoring system was reversed. The Baltic Sea Diet adherence is indicated by a higher BSDS score, which spans from 0 to 24 points.
The first estimation of the Healthy Nordic Diet Index (HNDI) was conducted by Olsen et al. 25 using a set of six items. These items were fish, cabbage, vegetables, whole grains, oats, apples, pears, fruits with high antioxidant activity, and root vegetables. In this index, the six components are categorized into tertiles (Q1-Q3) according to the individuals' intake levels. Subsequently, the tertiles ranging from Q1 to Q3 are assigned scores of 1, 2, and 3, respectively. The level of adherence exhibited a range of values between 0 and 18, with higher values of HNDI indicating more adherence.
Anthropometric measurement
The researchers conducted an anthropometric study. The weight measurements were obtained by using an SECA 700 Digital Scale (SECA, Hamburg, Germany), which is a standard instrument often used for this purpose. The measurements were rounded to the nearest 100 g. Participants were instructed to wear minimal clothes and remove their shoes before to being weighed. The height of the patient were assessed using a Seca portable height gauge that had an accuracy of 0.1 cm. Furthermore, the researchers used a Seca waist measuring instrument to determine the waist circumference (WC) across the central region spanning from the iliac crest to the last rib. Furthermore, the measurement of hip circumference was obtained in cm by positioning a measuring tape parallel to the floor at the point of maximum fullness of the buttocks. The calculation of body mass index (BMI) included dividing the weight (in kilograms) by the square of the height (in meters), as per the previously described procedure. The researcher performed anthropometric assessments in order to minimize observational variation.
Biochemical measurement
The laboratory technician collected 10 ml of venous blood from the participants at the commencement and conclusion of the study, after a fasting period of 10–12 h. Following the occurrence of clotting in the surrounding environment, the serum was expeditiously isolated using the process of centrifugation and then preserved at a temperature of − 70 °C till its transportation to the laboratory for the purpose of conducting tests. The concentrations of triglycerides (TG), high-density lipoprotein cholesterol (HDL-C), and fasting blood glucose (FBG) were measured using an enzymatic colorimetric approach using a kit provided by Pars Azmon Company, located in Tehran, Iran. The total cholesterol content was determined by enzyme photometry using the Pars test kit (Parsazmun, Tehran, Iran). The concentration of low-density lipoprotein cholesterol (LDL-C) was measured using the Friedewald formula 26 . LDL-C concentration was also calculated using Friedewald formula: LDL-C (mg/dL) = TC (mg/dL) − HDL-C (mg/dL) − TG (mg/dL)/5. Based on an automated analysis conducted using the BT-3000 system. The measurement of alanine aminotransferase (ALT) and aspartate aminotransferase (AST) enzymes was conducted using enzymatic reagents that were commercially available from Pars Azmoon in Tehran, Iran.
Statistical analysis
The statistical analysis was performed using the Statistical Package Software for Social Science v.21 (SPSS Inc., Chicago, IL, USA). The normality of the data was assessed by the use of the Kolmogorov–Smirnov's test and the examination of histogram charts. The study collected data on baseline and dietary intakes, representing quantitative variables as mean standard deviation (SD) and qualitative variables as number and percentages. The independent sample t-tests and chi-squared tests were used to compare data between two groups for continuous and categorical variables, respectively. Logistic regression was used to investigate the association between HNDI and BSDS scores and the risk of NAFLD. The analyses were adjusted for possible confounders, including gender, BMI, WC, hip circumference, physical activity, smoking status, education level, drug usage, history of illness, caloric intake, FBG, ALT, AST, lipid profiles, and dietary fiber. The odds ratio (OR) of NAFLD was computed across quartiles of scores, with a 95% confidence interval (CI). We deemed P-values less than 0.05 to be statistically significant.
Ethics approval and consent to participate
This study was approved by the research council and ethics committee Shahid Beheshti University of Medical Sciences, Tehran, Iran.
The average age of the study population was 39.53 ± 9.79 years, as shown by the mean (± standard deviation). The average BMI was 27.10 ± 4.45 kg/m2, with the standard deviation (SD) indicating the variability of the data. The average values for BSDS and HNDI were found to be 16.00 ± 2.49 and 11.99 ± 2.61, respectively.
Table 1 presents an overview of the participants' basic characteristics and biochemical data, categorized according to the quartiles of BSDS and HNDI. There was a substantial rise in the age of individuals belonging to the highest quartiles of BSDS and HNDI in comparison to those in the lowest quartiles. Furthermore, a notable disparity was seen in the educational attainment levels across the quartiles of the examined indices. No statistically significant variations were seen between the quartiles of indices and other factors.
Dietary intake of subjects across the quartiles of BSDS and HNDI are presented in Table 2 . Compared with those in the lowest quartile of HNDI, subjects in the highest quartile had higher energy, carbohydrate, protein, fat, SFA, MUFA, PUFA, cholesterol, fiber, potassium, iron, calcium, magnesium, zinc, vitamin C, E, D, B9, caffeine and all of food groups. No significant difference was found for sodium across quartiles of HNDI. Also, individuals in the highest quartiles of BSDS had higher intake of energy, carbohydrate, protein, PUFA, fiber, potassium, iron, calcium, magnesium, zinc, vitamin C, E, D, B9, caffeine, total dairy, legume, nut, fish, whole grains, fruits, and vegetables as well as a lower intake of red and processed meat.
The odds ratios (ORs) and 95% confidence intervals (CIs) for individuals with NAFLD are shown in Table 3 , categorized according to quartiles of BSDS and HNDI.
In the crude and initial adjusted model, which accounted for age and sex, no statistically significant association was found for HNDI in the highest quartile compared to the lowest quartile (odds ratio [OR] = 0.99, 95% confidence interval [CI] 0.67–1.47; p for trend = 0.870; OR = 0.95, 95% CI 0.64–1.41; p for trend = 0.957, respectively). Nevertheless, when controlling for confounding variables using the final model, it was seen that increased adherence to the HNDI was associated with a reduced likelihood of NAFLD (odds ratio [OR]: 0.42; 95% confidence interval [CI]: 0.18–0.98; p for trend = 0.043). A notable association was observed between a decrease in the likelihood of NAFLD among individuals with the highest score of BSDS, in comparison to those with the lowest score. This association was evident in both the unadjusted model (odds ratio [OR] = 0.49, 95% confidence interval [CI] 0.31–0.77; p-value for trend = 0.001) and the model adjusted for confounding factors (OR = 0.48, 95% CI 0.32–0.89; p-value for trend = 0.003).
The association between HND and the risk of NAFLD was investigated in this research. After adjusting for age, sex, BMI, WC, hip circumference, physical activity, smoking, education, drug use, illness history, FBS, ALT, AST, Lipid profiles, fiber, and calorie consumption, it is noteworthy that individuals with higher BSDS and HNDI scores had decreased probabilities of developing NAFLD. To the best of our knowledge, no prior research have indicated a relationship between HND and NAFLD chances.
Indeed, dietary patterns such as excessive calorie intake, high fructose consumption, and insufficient physical exercise are the most important risk factors for NAFLD. Previous studies demonstrated that the Mediterranean diet have positive benefits on reducing the NAFLD odds 9 . Despite the fact that the items in Mediterranean diet and HND belong to distinct varieties, there are commonalities between them, such as the fact that all of them are rich in fruits, vegetables, whole grains, fish, and low-fat dairy products. Furthermore, both of these diets have been linked to a decreased risk of various disorders, including diabetes and cardiovascular disease, as well as alterations in body homeostasis, such as insulin resistance and inflammation 27 . Because of this, we consider that feasible explanation for the observed relationships between the healthy diet and NAFLD are multifactorial, such as the favorable effects of diet on risk factors for chronic illnesses.
Inflammation and oxidative stress are the primary contributors to the pathophysiology of NAFLD 1 . Hence, the other important risk factors are being overweight or obese, having diabetes, having hyperlipidemia, not getting enough exercise, and eating an unhealthy diet 28 , 29 , 30 . Multiple pathways may have mediated the effective benefits of a HND with NAFLD risk factors.
Several processes, including alterations in cytokines, inflammatory factors, insulin resistance, and dyslipidemia, have been reported to explain the link between obesity and fatty liver 31 , and also up-regulating the expression of some of the genes in the liver of obsess patients diagnosed with NAFLD were founded 32 . For instance, the HND has been demonstrated to reduce the probability of obesity 15 . Besides, Kolehmainen et al. declared that a HND decreases inflammatory gene expression in SAT when compared to a control diet, regardless of changes in body weight in the patients with a metabolic syndrome 33 . A recent meta-analysis also illustrated that adherence to HND meaningfully reduce body weight 34 .
Moreover, a large Danish cohort research revealed an adverse relationship between adherence to HND and low risk of T2D 35 . Interestingly, in patients with hypercholesterolemia, a HND improves blood lipid profile and insulin sensitivity while also lowering blood pressure to clinically meaningful levels 36 In the randomized dietary study, participations with metabolic syndrome had significant changes in non-HDL-C , LDL-C to HDL-C ratio, and Apo B to Apo A1 ratio, which has been reported adherence to HND improved lipid profile 37 . By contrast, we demonstrated that changing in lipid profile were not significantly different between the groups.
The favorable benefits of the HND on NAFLD may be attributed to several reasons. The Nordic dietary pattern emphasizes eating foods with high content of fiber and are linked to a greater sense of fullness 38 . A high concentration of soluble and insoluble fibers is related to a reduction in serum TAG and blood glucose 39 .Indeed, this diet may be beneficial for NAFLD patients.
It is noteworthy to notice that the two scores to represent a HND, HNDI and BSDS, which were formed fairly differently from one another, provided consistent relationships with the risk of developing NAFLD. The HNDI was based on intakes of fish, apples and pears, and root vegetables, cabbage, oatmeal, rye bread, however, it did not include some of the factors that were used in the BSDS. These factors included dietary fat quality as well as dairy and meat intakes 40 .
The strengths of the present study include a large study population consisting of both men and women, comprehensive data about potential cofounding factors and also no loss in follow-up. A trained interviewer was filled out the questionnaires in order to minimizing the random errors in recording. Our study had some potential limitations, there is a risk of recall bias in the present study due to the retrospective way of the data collection. Hence, to reduce the bias, a valid and trustworthy FFQ was utilized. It also seems that the level of adherence to this type of dietary index in countries and regions (Baltic countries) is different compared to the region where the study was conducted (Iran) and this itself can be a limitation.
In conclusion, our findings revealed that adherence to a healthy Nordic diet remarkably reduces the risk of developing NAFLD, demonstrating that the highly nutritious components of the Nordic diet are beneficial for reducing the risk of NAFLD. Therefore, a high adherence to healthy Nordic dietary pattern may be effective also in reducing the possibility of developing the NAFLD risk factors. Further longitudinal studies in diverse population are warranted to confirm our results.
Data availability
Data are available upon request from the corresponding author (Mohammad Hassan Sohouli) due to privacy/ethical restrictions.
Anania, C., Perla, F. M., Olivero, F., Pacifico, L. & Chiesa, C. Mediterranean diet and nonalcoholic fatty liver disease. World J. Gastroenterol. 24 (19), 2083–94 (2018).
Article CAS PubMed PubMed Central Google Scholar
Williams, C. D. et al. Prevalence of nonalcoholic fatty liver disease and nonalcoholic steatohepatitis among a largely middle-aged population utilizing ultrasound and liver biopsy: a prospective study. Gastroenterology. 140 (1), 124–31 (2011).
Article PubMed Google Scholar
Lankarani, K. B. et al. Non alcoholic fatty liver disease in southern Iran: a population based study. Hepat. Mon. 13 (5), e9248 (2013).
PubMed PubMed Central Google Scholar
Browning, J. D. et al. Prevalence of hepatic steatosis in an urban population in the United States: impact of ethnicity. Hepatology. 40 (6), 1387–95 (2004).
Younossi, Z. M. et al. The economic and clinical burden of nonalcoholic fatty liver disease in the United States and Europe. Hepatology. 64 (5), 1577–86 (2016).
Giraldi, L. et al. Mediterranean diet and the prevention of non-alcoholic fatty liver disease: results from a case-control study. Eur. Rev. Med. Pharmacol. Sci. 24 (13), 7391–8 (2020).
CAS PubMed Google Scholar
Mundi, M. S. et al. Evolution of NAFLD and its management. Nutr. Clin. Pract. 35 (1), 72–84 (2020).
Sacks, F. M. et al. A dietary approach to prevent hypertension: a review of the Dietary Approaches to Stop Hypertension (DASH) Study. Clin. Cardiol. 22 (7 Suppl), ii6–ii10 (1999).
Article Google Scholar
Entezari, M. R. et al. Mediterranean dietary pattern and non-alcoholic fatty liver diseases: a case-control study. J. Nutr. Sci. 10 , e55 (2021).
Katsiki, N., Stoian, A. P. & Rizzo, M. Dietary patterns in non-alcoholic fatty liver disease (NAFLD): Stay on the straight and narrow path!. Clin. Investig. Arterioscler. 34 (Suppl 1), s24–s31 (2022).
PubMed Google Scholar
Poulsen, S. K. et al. Health effect of the new nordic diet in adults with increased waist circumference: a 6-mo randomized controlled trial. Am. J. Clin. Nutr. 99 (1), 35–45 (2014).
Article CAS PubMed Google Scholar
Salomo, L. et al. The new Nordic diet: phosphorus content and absorption. Eur. J. Nutr. 55 (3), 991–6 (2016).
Waijers, P. M., Feskens, E. J. & Ocké, M. C. A critical review of predefined diet quality scores. Br. J. Nutr. 97 (2), 219–31 (2007).
Kanerva, N., Kaartinen, N. E., Schwab, U., Lahti-Koski, M. & Männistö, S. The Baltic Sea Diet Score: a tool for assessing healthy eating in Nordic countries. Public Health Nutr. 17 (8), 1697–705 (2014).
Kanerva, N., Kaartinen, N. E., Schwab, U., Lahti-Koski, M. & Männistö, S. Adherence to the Baltic Sea diet consumed in the Nordic countries is associated with lower abdominal obesity. Br. J. Nutr. 109 (3), 520–8 (2013).
Perälä, M. M. et al. A healthy Nordic diet and physical performance in old age: findings from the longitudinal Helsinki Birth Cohort Study. Br. J. Nutr. 115 (5), 878–86 (2016).
Kanerva, N. et al. Associations of the Baltic Sea diet with obesity-related markers of inflammation. Ann. Med. 46 (2), 90–6 (2014).
Tertsunen, H. M., Hantunen, S., Tuomainen, T. P. & Virtanen, J. K. Healthy Nordic diet and risk of disease death among men: the Kuopio Ischaemic Heart Disease Risk Factor Study. Eur. J. Nutr. 59 (8), 3545–53 (2020).
Article PubMed PubMed Central Google Scholar
Yamamura, S. et al. MAFLD identifies patients with significant hepatic fibrosis better than NAFLD. Liver Int. 40 (12), 3018–30 (2020).
Piazzolla, V.A., Mangia, A. Noninvasive diagnosis of NAFLD and NASH. Cells. 2020;9(4). PubMed PMID: 32316690. Pubmed Central PMCID: PMC7226476. Epub 20200417. eng.
Semmler, G. et al. Novel reliability criteria for controlled attenuation parameter assessments for non-invasive evaluation of hepatic steatosis. Unit. Eur. Gastroenterol. J. 8 (3), 321–31 (2020).
Article CAS Google Scholar
Mirmiran, P., Esfahani, F. H., Mehrabi, Y., Hedayati, M. & Azizi, F. Reliability and relative validity of an FFQ for nutrients in the Tehran lipid and glucose study. Public Health Nutr. 13 (5), 654–62 (2010).
Ghafarpour, M., Houshiar-Rad, A., Kianfar, H. & Ghaffarpour, M. The manual for household measures, cooking yields factors and edible portion of food (Keshavarzi Press, 1999).
Google Scholar
Bowman, S.A., Friday, J.E., Moshfegh, A.J. MyPyramid equivalents database, 2.0 for USDA survey foods, 2003–2004: documentation and user guide. US Department of Agriculture. 2008.
Olsen, A. et al. Healthy aspects of the Nordic diet are related to lower total mortality. J. Nutr. 141 (4), 639–644 (2011).
Friedewald, W. T., Levy, R. I. & Fredrickson, D. S. Estimation of the concentration of low-density lipoprotein cholesterol in plasma, without use of the preparative ultracentrifuge. Clin. Chem. 18 (6), 499–502 (1972).
Perälä, M. M. et al. The healthy Nordic diet and Mediterranean diet and incidence of disability 10 years later in home-dwelling old adults. J. Am. Med. Dir. Assoc. 20 (5), 511–516 (2019).
Trenell, M. I. Sedentary behaviour, physical activity, and NAFLD: Curse of the chair. J. Hepatol. 63 (5), 1064–5 (2015).
Ortiz-Lopez, C. et al. Prevalence of prediabetes and diabetes and metabolic profile of patients with nonalcoholic fatty liver disease (NAFLD). Diabetes Care. 35 (4), 873–8 (2012).
Hamaguchi, M. et al. The metabolic syndrome as a predictor of nonalcoholic fatty liver disease. Ann. Intern Med. 143 (10), 722–8 (2005).
Jung, U. J. & Choi, M. S. Obesity and its metabolic complications: the role of adipokines and the relationship between obesity, inflammation, insulin resistance, dyslipidemia and nonalcoholic fatty liver disease. Int. J. Mol. Sci. 15 (4), 6184–223 (2014).
Article MathSciNet PubMed PubMed Central Google Scholar
Pettinelli, P. & Videla, L. A. Up-regulation of PPAR-gamma mRNA expression in the liver of obese patients: an additional reinforcing lipogenic mechanism to SREBP-1c induction. J. Clin. Endocrinol. Metab. 96 (5), 1424–30 (2011).
Kolehmainen, M. et al. Healthy Nordic diet downregulates the expression of genes involved in inflammation in subcutaneous adipose tissue in individuals with features of the metabolic syndrome. Am. J. Clin. Nutr. 101 (1), 228–39 (2015).
Ramezani-Jolfaie, N., Mohammadi, M. & Salehi-Abargouei, A. Effects of a healthy Nordic diet on weight loss in adults: A systematic review and meta-analysis of randomized controlled clinical trials. Eat. Weight Disord. 25 (5), 1141–50 (2020).
Lacoppidan, S. A. et al. Adherence to a healthy Nordic food index is associated with a lower risk of type-2 diabetes–the Danish diet, cancer and health cohort study. Nutrients. 7 (10), 8633–44 (2015).
Adamsson, V. et al. Effects of a healthy Nordic diet on cardiovascular risk factors in hypercholesterolaemic subjects: a randomized controlled trial (NORDIET). J. Int. Med. 269 (2), 150–9 (2011).
Uusitupa, M. et al. Effects of an isocaloric healthy Nordic diet on insulin sensitivity, lipid profile and inflammation markers in metabolic syndrome – a randomized study (SYSDIET). J Int Med. 274 (1), 52–66 (2013).
Mithril, C. et al. Dietary composition and nutrient content of the New Nordic Diet. Public Health Nutr. 16 (5), 777–85 (2013).
Garcia, M. et al. The effect of the traditional mediterranean-style diet on metabolic risk factors: A meta-analysis. Nutrients. 8 (3), 168 (2016).
Tertsunen, H. M., Hantunen, S., Tuomainen, T. P. & Virtanen, J. K. Adherence to a healthy Nordic diet and risk of type 2 diabetes among men: the Kuopio Ischaemic Heart Disease Risk Factor Study. Eur J Nutr. 60 (7), 3927–34 (2021).
Download references
Acknowledgements
We thank the Student Research Committee and the Research & Technology Chancellor of Shahid Beheshti University of Medical Sciences.
Author information
Authors and affiliations.
School of Medicine, Shahid Sadoughi University of Medical Sciences, Yazd, Iran
Zahra Rasoulizadeh
Department of Internal Medicine, Hazrat-E Rasool General Hospital, Iran University Of Medical Sciences, Tehran, Iran
Abolfazl Namazi
Student Research Committee, Department of Clinical Nutrition and Dietetics, Faculty of Nutrition and Food Technology, National Nutrition and Food Technology Research Institute, Shahid Beheshti University of Medical Sciences, No 7, West Arghavan St, Farahzadi Blvd, PO Box 19395-4741, Tehran, 1981619573, Iran
Mohammad Hassan Sohouli
Pediatric Gastroenterology and Hepatology Research Center, Pediatrics Centre of Excellence, Children′s Medical Center, Tehran University of Medical Sciences, Tehran, Iran
Mohammad Hassan Sohouli & Pejman Rohani
Department of Clinical Nutrition and Dietetics, Faculty of Nutrition and Food Technology, Shahid Beheshti University of Medical Sciences, Tehran, Iran
Azita Hekmatdoost
Department of Nutrition, School of Public Health, Shahid Sadoughi University of Medical Sciences, Yazd, Iran
Mahdieh Hosseinzadeh
You can also search for this author in PubMed Google Scholar
Contributions
M.H, and Mh.S contributed in conception, design, and statistical analysis. Mh.S, Z.R., M.H., P.R, A.N., and A.H contributed in data collection and manuscript drafting. Mh.S and M.H supervised the study. All authors approved the final version of the manuscript.
Corresponding authors
Correspondence to Mohammad Hassan Sohouli or Mahdieh Hosseinzadeh .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rasoulizadeh, Z., Namazi, A., Sohouli, M.H. et al. Association between Baltic sea diet and healthy Nordic diet index with risk of non-alcoholic fatty liver disease: a case–control study. Sci Rep 14 , 9537 (2024). https://doi.org/10.1038/s41598-024-60400-3
Download citation
Received : 08 September 2023
Accepted : 23 April 2024
Published : 25 April 2024
DOI : https://doi.org/10.1038/s41598-024-60400-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Nordic diet
- Baltic sea diet
- Chronic diseases
- Case–control
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Impact Accounting: Raising ESG Reporting Standards
Sponsor content from Pure Storage.

by Charles Giancarlo
Environmental, social, and governance (ESG) frameworks began in 2004 as a concept from the United Nations to help investors assess a company’s global impact and drive corporate responsibility. In the 20 years since its introduction as a broad concept without strict guidelines, ESG has become politicized. Detractors argue that it introduces divisive social causes into corporate decision making.
Certainly, there are many areas for serious debate within the topics of social responsibility and corporate governance. However, anything done with greater efficiency is a general good. Reducing waste and pollution is positive for all concerned, and the reduction of uncontrolled costs to society is to be applauded.
Still, the ESG measurement landscape has become highly fragmented, marked by inconsistent standards and , making environmental reporting unreliable , often misleading, and difficult to interpret. Today, 75% of companies say they are unprepared for upcoming ESG audits, according to Reuters .
Confusing Calculations
Companies reporting ESG metrics must sift through many layers of supply and distribution chains over which they have little oversight and must deal with diverse methodologies, agencies, and reports. They must estimate the environmental impact of partners far out in their supply chains with which they have no direct business, leading to both scalability and accuracy issues, and to potential manipulation, as SEC settlements show. If unchecked, ESG compliance costs will rise sharply, risking report reliability, according to CNN .
The confusing comparisons of various ESG measurements’ environmental performance exemplify the challenge businesses and consumers face in evaluating products’ and companies’ environmental claims. “Greenwashing”—companies’ dishonest efforts to embellish their environmental credentials, engage in selective reporting, or use carbon credits with dubious effectiveness—has become a common problem.
No reasonable person would argue about whether companies should do better in addressing sustainability issues. Proponents say ESG has proved to be a compass for identifying companies that excel financially, demonstrating that prioritizing environmental sustainability, social responsibility, and governance is both good economics and good ethics.
However, disentangling ESG’s components into separate priorities would simplify and reduce needless complexity and disagreement. With the advancement of artificial intelligence, new energy and environmental challenges will also necessitate new dialogue among all stakeholders.
The Impact of Impact Accounting
So the question remains: How can organizations most efficiently and effectively reduce their corporate environmental impact with integrity and clarity?
Historically, market-based mechanisms and transparent corporate practices have driven global economic growth, expanding the middle class and enhancing living standards worldwide. Today’s environmental sustainability challenges stem from the absence of these market-based mechanisms in managing critical resources, pollution, and waste.
The good news is that the practices and tools exist to address this measurement gap through impact accounting . By using impact accounting standards, companies can:
• Use their existing cost accounting capabilities for externalities—the indirect costs (such as carbon dioxide or other pollution) that companies impose on society but that do not show up in their financial statements or products’ specifications;
• Use universal standardized measures for these indirect costs; and
• Employ standard audit practices and auditors to ensure fair, common, and supportable numbers and reports across companies and industries.
Impact accounting is transparent and scalable because it allows each organization to use the metrics its direct suppliers provide to its own accounts, and then to transform these inputs into metrics for their customers.
This is a far more efficient process than having every company analyze the many layers in its supply chain. It uses standardized metrics for each critical resource and integrates them into its financial reporting. And it allows companies to incorporate these costs into their product pricing and features. In so doing, impact accounting also creates a competitive market based on products’ environmental qualities, while fostering transparency through standard auditing oversight.
For public companies, impact accounting transforms the environmental landscape. It introduces a market-based mechanism that quantifies the environmental impact of production, packaging, and usage of products and services in monetary terms, creating a competitive market for the reduction of externalities, which in time will lead to a significant reduction of external costs to society.
Through impact accounting, each supplier can disclose to customers the true resource costs to manufacture and use their product, in addition to the product’s price. The practice expands traditional cost accounting to incorporate societal costs—addressing the gap where companies cover direct costs, like consumption of energy and materials, but not the environmental costs of emissions or waste disposal.
Integrating these costs into both product sales and corporate financial reporting allows companies to report profits alongside resource usage such as energy, water, precious metals, and even plastics, providing a true total cost of production and a true audited view of the environmental footprint to ensure fairness and comparability. Importantly, impact accounting is a scalable and efficient practice for businesses that aligns with increasing consumer demand for sustainable practices, marrying profitability with sustainability.
Leading Sustainable Change
Modern efficiency relies on accurate pricing and audited statements, fostering business trust. Impact accounting extends this trust by quantifying indirect costs, promoting efficiency, and allowing choices based on resource efficiency and product value. This approach is gaining traction among institutions like Pure Storage.
Adopting impact accounting and innovating to reduce the energy and carbon footprint of business takes society steps closer to a transparent, accountable, and sustainable future, which is beneficial for our collective well-being. Pure Storage is replacing outdated, energy-intensive hard disk drives with efficient flash storage, cutting energy use and power-related emissions by up to 85%, and setting the standard in environmental reporting in the data storage industry through impact accounting.
We call on technology leaders to help reduce the energy demands of data centers, which are projected to double to 4% of global electricity use in the next two years. Impact accounting will reduce the cost of and confusion in ESG reporting and benefit all customers, significantly strengthen our communities, and allow businesses to play a sizable role in leading us toward a more sustainable future.
Learn more about Pure Storage’s sustainable tech infrastructure and its impact on reducing energy consumption and minimizing e-waste.
Charles Giancarlo is the CEO of Pure Storage
- Open access
- Published: 22 April 2024
The influence of maternal prepregnancy weight and gestational weight gain on the umbilical cord blood metabolome: a case–control study
- Xianxian Yuan ORCID: orcid.org/0000-0001-8762-8471 1 ,
- Yuru Ma 1 ,
- Jia Wang 2 ,
- Yan Zhao 1 ,
- Wei Zheng 1 ,
- Ruihua Yang 1 ,
- Lirui Zhang 1 ,
- Xin Yan 1 &
- Guanghui Li ORCID: orcid.org/0000-0003-2290-1515 1
BMC Pregnancy and Childbirth volume 24 , Article number: 297 ( 2024 ) Cite this article
107 Accesses
Metrics details
Maternal overweight/obesity and excessive gestational weight gain (GWG) are frequently reported to be risk factors for obesity and other metabolic disorders in offspring. Cord blood metabolites provide information on fetal nutritional and metabolic health and could provide an early window of detection of potential health issues among newborns. The aim of the study was to explore the impact of maternal prepregnancy overweight/obesity and excessive GWG on cord blood metabolic profiles.
A case control study including 33 pairs of mothers with prepregnancy overweight/obesity and their neonates, 30 pairs of mothers with excessive GWG and their neonates, and 32 control mother-neonate pairs. Untargeted metabolomic profiling of umbilical cord blood samples were performed using UHPLC‒MS/MS.
Forty-six metabolites exhibited a significant increase and 60 metabolites exhibited a significant reduction in umbilical cord blood from overweight and obese mothers compared with mothers with normal body weight. Steroid hormone biosynthesis and neuroactive ligand‒receptor interactions were the two top-ranking pathways enriched with these metabolites ( P = 0.01 and 0.03, respectively). Compared with mothers with normal GWG, in mothers with excessive GWG, the levels of 63 metabolites were increased and those of 46 metabolites were decreased in umbilical cord blood. Biosynthesis of unsaturated fatty acids was the most altered pathway enriched with these metabolites ( P < 0.01).
Conclusions
Prepregnancy overweight and obesity affected the fetal steroid hormone biosynthesis pathway, while excessive GWG affected fetal fatty acid metabolism. This emphasizes the importance of preconception weight loss and maintaining an appropriate GWG, which are beneficial for the long-term metabolic health of offspring.
Peer Review reports
The obesity epidemic is an important public health problem in developed and developing countries [ 1 ] and is associated with the emergence of chronic noncommunicable diseases, including type 2 diabetes mellitus (T2DM), hypertension, cardiovascular disease, nonalcoholic fatty liver disease (NAFLD), and cancer [ 2 , 3 , 4 ]. Maternal obesity is the most common metabolic disturbance in pregnancy, and the prevalence of obesity among women of childbearing age is 7.1% ~ 31.9% in some countries [ 5 ]. In China, the prevalence of overweight and obesity has also increased rapidly in the past four decades. Based on Chinese criteria, the latest national prevalence estimates for 2015–2019 were 34.3% for overweight and 16.4% for obesity in adults (≥ 18 years of age) [ 6 ].
Increasing evidence implicates overnutrition in utero as a major determinant of the health of offspring during childhood and adulthood, which is compatible with the developmental origins of health and disease (DOHaD) framework [ 7 ]. Maternal obesity and excessive gestational weight gain (GWG) are important risk factors for several adverse maternal outcomes, including gestational diabetes and hypertensive disorders, fetal death, and preterm birth [ 8 , 9 , 10 ]. More importantly, they have negative implications for offspring, both perinatally and later in life. Evidence from cohort studies focusing on offspring development confirms the relationship between maternal obesity/excessive GWG and offspring obesity programming [ 11 , 12 , 13 ]. Currently, there is no unified mechanism to explain the adverse outcomes associated with maternal obesity and excessive GWG, which may be the independent and interactive effects of the obese maternal phenotype itself and the diet associated with this phenotype. In addition to genetic and environmental factors, metabolic programming may also lead to the intergenerational transmission of obesity through epigenetic mechanisms.
Metabolomics, which reflects the metabolic phenotype of human subjects and animals, is the profiling of metabolites in biofluids, cells and tissues using high-throughput platforms, such as mass spectrometry. It has unique potential in identifying biomarkers for predicting occurrence, severity, and progression of diseases, as well as exploring underlying mechanistic abnormalities [ 14 , 15 ]. Umbilical cord metabolites can provide information about fetal nutritional and metabolic health, and may provide an early window for detection of potential health issues in newborns [ 16 ]. Previous studies have reported differences in umbilical cord metabolite profiles associated with maternal obesity [ 17 , 18 ]. However, the results were inconsistent due to differences in sample sizes, ethnicity and region, and mass spectrometry. In addition, most studies have not considered the difference in the effects of prepregnancy body mass index (BMI) and GWG on cord blood metabolites.
To investigate the relationship between early metabolic programming and the increased incidence of metabolic diseases in offspring, we studied the associations between elevated prepregnancy BMI/excessive GWG and umbilical cord metabolic profiles. Another purpose of this study was to explore whether there were differences in the effects of prepregnancy overweight/obesity and excessive GWG on cord blood metabolites.
Study population
This was a hospital-based, case control study that included singleton pregnant women who received prenatal care and delivered vaginally at Beijing Obstetrics and Gynecology Hospital, Capital Medical University, from January 2022 to March 2022. We selected 33 pregnant women with a prepregnancy BMI ≥ 24.0 kg/m 2 regardless of their gestational weight gain as the overweight/obese group, 30 pregnant women with a prepregnancy BMI of 18.5–23.9 kg/m 2 and a GWG > 14.0 kg as the excessive GWG group, and 32 pregnant women with a BMI of 18.5–23.9 kg/m 2 and a GWG of 8.0–14.0 kg as the control group. The ages of the three groups were matched (± 1.0 years), and the prepregnancy BMIs of the excessive GWG and control groups were matched (± 1.0 kg/m 2 ).
The inclusion criteria were women with singleton pregnancies, those aged between 20 and 45 years, those with full-term delivery (gestational age ≥ 37 weeks), those with a prepregnancy BMI ≥ 18.5 kg/m 2 , those without prepregnancy diabetes mellitus (DM) or hypertension, and those without gestational diabetes mellitus (GDM). The exclusion criteria were women with multiple pregnancies, those less than 20 years or more than 45 years old, those with a prepregnancy BMI < 18.5 kg/m 2 , those with prepregnancy DM, hypertension or GDM, and those without cord blood samples.
We classified pregnant women into BMI categories based on Chinese guidelines [ 19 ]: normal weight (prepregnancy BMI 18.5–23.9 kg/m 2 ), overweight (prepregnancy BMI 24.0–27.9 kg/m 2 ), and obese (prepregnancy BMI ≥ 28.0 kg/m 2 ). GWG guideline concordance was defined by the 2021 Chinese Nutrition Society recommendations according to prepregnancy BMI. The upper limits of GWG for normal weight, overweight, and obesity were 14.0 kg, 11.0 kg, and 9.0 kg, respectively.
Ethical approval and written informed consent were obtained from all participants. The study has been performed according to the Declaration of Helsinki, and the procedures have been approved by the ethics committees of Beijing Obstetrics and Gynecology Hospital, Capital Medical University (2021-KY-037).
Sample and data collection
Maternal and neonatal clinical data were collected from the electronic medical records system of Beijing Obstetrics and Gynecology Hospital. Maternal clinical characteristics included age, height, prepregnancy and predelivery weight, education level, smoking and drinking status during pregnancy, parity, conception method, comorbidities and complications of pregnancy, family history of DM and hypertension, gestational age, mode of delivery, and biochemical results during pregnancy. Prepregnancy BMI was calculated as prepregnancy weight in kilograms divided by the square of height in meters. GWG was determined by subtracting the prepregnancy weight in kilograms from the predelivery weight in kilograms. GDM was defined using the IAPDSG’s diagnostic criteria at 24 to 28 +6 weeks gestation and the fasting glucose and 1- and 2-h glucose concentrations at the time of the oral glucose tolerance test (OGTT). Neonatal clinical characteristics included sex, birth weight and length. Macrosomia was defined as a birth weight of 4,000 g or more [ 20 ]. Low birth weight (LBW) was defined as a birth weight less than 2,500 g [ 21 ].
Umbilical cord blood samples were obtained by trained midwives after clamping the cord at delivery. Whole blood samples were collected in EDTA tubes, refrigerated for < 24 h, and centrifuged at 2,000 r.p.m. at 4 ℃ for 10 min. Plasma aliquots were stored at -80 ℃ until shipment on dry ice to Novogene, Inc. (Beijing, China) for untargeted metabolomic analysis.
Untargeted metabolomic analyses
Ultrahigh-performance liquid chromatography tandem mass spectrometry (UHPLC‒MS/MS) analyses were performed using a Vanquish UHPLC system (Thermo Fisher, Germany) coupled with an Orbitrap Q Exactive™ HF mass spectrometer (Thermo Fisher, Germany) at Novogene Co., Ltd. (Beijing, China). Detailed descriptions of the sample preparation, mass spectrometry and automated metabolite identification procedures are described in the Supplementary materials .
Statistical analysis
Clinical data statistical analysis.
Quantitative data are shown as the mean ± standard deviation (SD) or median (interquartile range), and categorical data are presented as percentages. The Mann‒Whitney U test, chi-square test, and general linear repeated-measures model were used to assess the differences between the control and study groups when appropriate. A P value < 0.05 was considered statistically significant. All analyses were performed using Statistical Package of Social Sciences version 25.0 (SPSS 25.0) for Windows (SPSS Inc).
Umbilical cord metabolome statistical analysis
These metabolites were annotated using the Human Metabolome Database (HMDB) ( https://hmdb.ca/metabolites ), LIPIDMaps database ( http://www.lipidmaps.org/ ), and Kyoto Encylopaedia of Genes and Genomes (KEGG) database ( https://www.genome.jp/kegg/pathway.html ). Principal component analysis (PCA) and partial least-squares discriminant analysis (PLS-DA) were performed at metaX. We applied univariate analysis ( T test) to calculate the statistical significance ( P value). Metabolites with a variable importance for the projection (VIP) > 1, a P value < 0.05 and a fold change (FC) ≥ 2 or FC ≤ 0.5 were considered to be differential metabolites. A false discovery rate (FDR) control was implemented to correct for multiple comparisons. The q -value in the FDR control was defined as the FDR analog of the P -value. In this study, the q -value was set at 0.2. For clustering heatmaps, the data were normalized using z scores of the intensity areas of differential metabolites and were plotted by the Pheatmap package in R language.
The correlations among differential metabolites were analyzed by cor () in R language (method = Pearson). Statistically significant correlations among differential metabolites were calculated by cor.mtest () in R language. A P value < 0.05 was considered statistically significant, and correlation plots were plotted by the corrplot package in R language. The functions of these metabolites and metabolic pathways were studied using the KEGG database. The metabolic pathway enrichment analysis of differential metabolites was performed when the ratio was satisfied by x/n > y/N, and the metabolic pathway was considered significantly enriched when P < 0.05.
Demographic characteristics of study participants
The demographic and clinical characteristics of the three population groups enrolled in the study are summarized in Table 1 . Mothers had no significant difference regarding their ages or gestational ages. Compared to the mothers in the excessive GWG and control groups, those in the prepregnancy overweight/obesity group had a significantly higher prepregnancy BMI (25.6 (24.5, 27.2) kg/m 2 ). However, there was no significant difference in prepregnancy BMI between mothers in the excessive GWG group (20.3 ± 1.2 kg/m 2 ) and mothers in the control group (20.6 ± 1.5 kg/m 2 ). Mothers in the excessive GWG group had the highest GWG (17.0 (15.5, 19.1) kg) among the three groups. The mean GWG of the mothers in the prepregnancy overweight/obesity group was 12.9 ± 3.8 kg, which was similar to that of the control group (11.8 ± 1.5 kg). It was noteworthy that among the 33 prepregnancy overweight/obese pregnant women, 20 of them had appropriate GWG, 1 had insufficient GWG, and 12 had excessive GWG. The proportion of mothers who underwent invitro fertilization and embryo transfer (IVF-ET) in the prepregnancy overweight/obesity group (15.2%) was significantly higher than that in the excessive GWG and control groups. There were no statistically significant differences in the proportions of pregnancy outcomes among the three groups, including preeclampsia, premature rupture of membranes, postpartum hemorrhage, macrosomia, and LBW. The babies in the three groups showed no significant difference regarding their birth weights or lengths.
The biochemical parameters of the mothers during pregnancy are shown in Table 2 . The levels of triglyceride (TG) and uric acid (UA) of mothers in the prepregnancy overweight/obesity group were significantly higher than those of the mothers in the excessive GWG and control groups in the first trimester. However, there was no significant difference in the blood glucose and lipid levels in the second and third trimesters of pregnancy among the three groups.
PCA and PLS-DA analysis of cord blood metabolites
Functional and taxonomic annotations of the identified metabolites included the HMDB classification annotations, LIPID MAPS classification annotations, and KEGG pathway annotations. Those cord blood metabolites included lipids and lipid-like molecules, organic acids and their derivatives, and organoheterocyclic compounds, which were mainly involved in metabolism. To better understand the structure of the cord blood metabolome in cases versus controls, we used unsupervised PCA to identify metabolites contributing the most to observed differences in the dataset. PCA did not clearly separate the three groups. We next used PLS-DA to identify metabolites that were predictive of case versus control status. PLS-DA clearly distinguished the cases from the controls (Fig. 1 ), the prepregnancy overweight/obesity group vs. the control group (R2Y = 0.82, Q2Y = 0.37; R2Y = 0.77, Q2Y = 0.13, respectively) (Fig. 1 A), and the excessive GWG group vs. the control group (R2Y = 0.76, Q2Y = 0.16; R2Y = 0.81, Q2Y = 0.41) (Fig. 1 B).
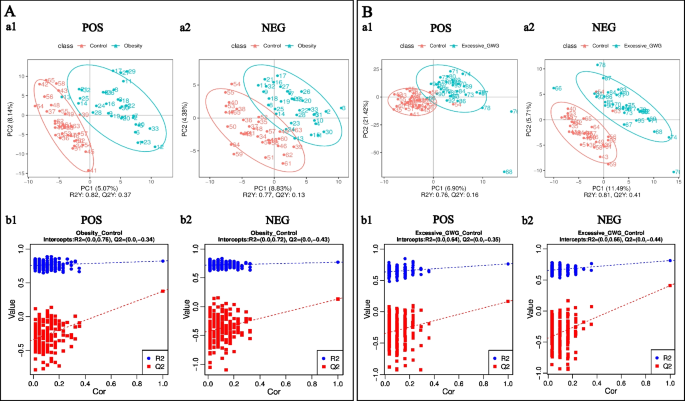
PLS-DA of identified cord blood metabolites. A the prepregnancy overweight/obesity group vs. the control group; B the excessive GWG group vs. the control group. (a) PLS-DA score. The horizontal coordinates are the score of the sample on the first principal component; the longitudinal coordinates are the score of the sample on the second principal component; R2Y represents the interpretation rate of the model, and Q2Y is used to evaluate the predictive ability of the PLS-DA model, and when R2Y is greater than Q2Y, it means that the model is well established. (b) PLS-DA valid. Horizontal coordinates represent the correlation between randomly grouped Y and the original group Y, and vertical coordinates represent the scores of R2 and Q2. (1) POS, positive metabolites; (2) NEG, negative metabolites
Maternal prepregnancy overweight/obesity
Screening differential metabolites according to a PLS-DA VIP > 1.0, a FC > 1.2 or < 0.833 and a P value < 0.05, a total of 106 cord blood metabolites (77 positive metabolites and 29 negative metabolites) differed between the prepregnancy overweight/obesity group and the control group. Compared with those in the control group, the levels of 46 metabolites (19 positive metabolites and 27 negative metabolites) were increased in the prepregnancy overweight/obesity group, among which octopamine was the metabolite with the largest increase, followed by (2S)-4-Oxo-2-phenyl-3,4-dihydro-2H-chromen-7-yl beta-D-glucopyranoside, N-tetradecanamide, stearamide, and methanandamide (Fig. 2 A). Compared with the control group, in the prepregnancy overweight/obesity group, there were 60 metabolites (58 positive metabolites and 2 negative metabolites) with reduced concentrations, among which senecionine was the metabolite with the largest decrease, followed by 3-(methylsulfonyl)-2H-chromen-2-one, methyl EudesMate, cuminaldehyde, and 2-(tert-butyl)-1,3-thiazolane-4-carboxylic acid (Fig. 2 A).
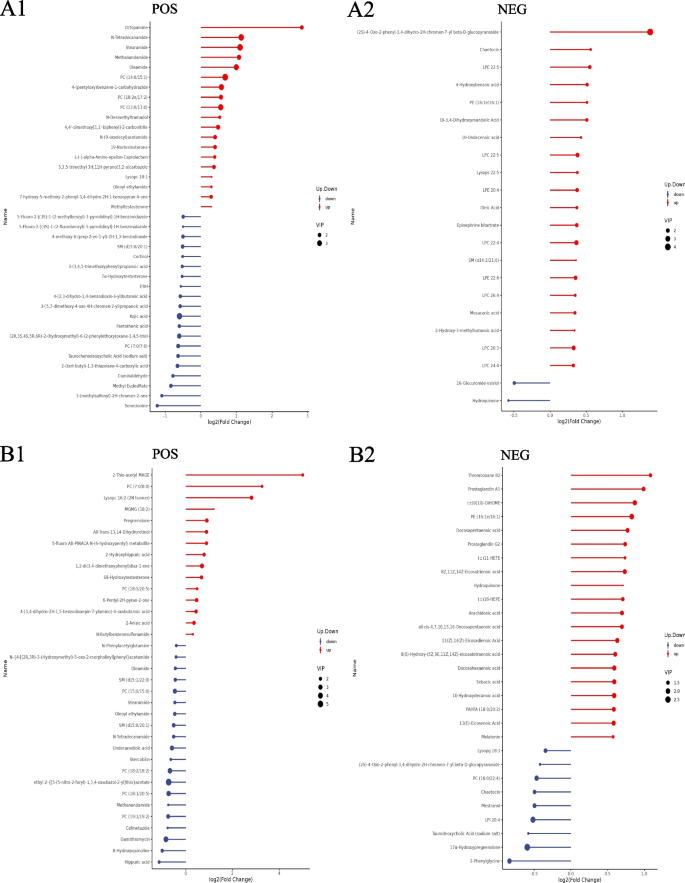
Stem plots of differential cord blood metabolites. A the prepregnancy overweight/obesity group vs. the control group; B the excessive GWG group vs. the control group. (1) positive metabolites; (2) negative metabolites. Notes: The color of the dot in the stem plots represents the upward and lower adjustment, the blue represents downward, and the red represents upward. The length of the rod represents the size of log2 (FC), and the size of the dot represents the size of the VIP value
A hierarchical analysis of the two groups of differential metabolites obtained was carried out, and the difference in metabolic expression patterns between the two groups and within the same comparison was obtained, which is shown in Fig. 3 . KEGG pathway analysis of differential cord blood metabolites associated with the prepregnancy overweight/obesity group versus the control group is shown in Table 3 and Fig. 4 A. The metabolite enrichment analysis revealed that steroid hormone biosynthesis ( P value = 0.01) and neuroactive ligand‒receptor interactions ( P value = 0.03) were the two pathways that were most altered between the prepregnancy overweight/obesity group and the control group. 19 metabolites were distributed in the pathway of steroid hormone biosynthesis, and 4 metabolites were distributed in the pathway of neuroactive ligand‒receptor interactions. In the steroid hormone biosynthesis pathway, the levels of corticosterone, 11-deoxycortisol, cortisol, testosterone, and 7α-hydroxytestosterone were decreased in the prepregnancy overweight/obesity group relative to those in the control group. In the neuroactive ligand‒receptor interaction pathway, the level of cortisol was decreased and the levels of trace amines were increased in the prepregnancy overweight/obesity group relative to the control group.
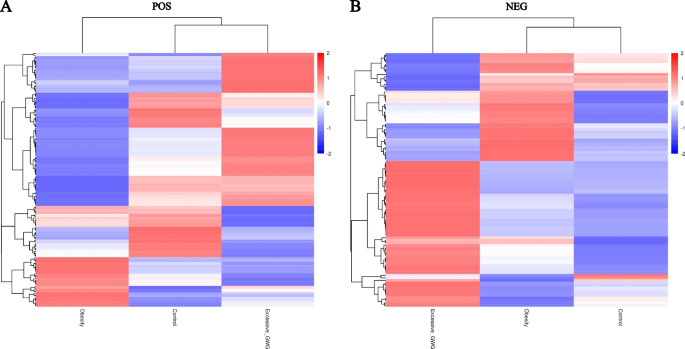
Clustering heat maps of differential cord blood metabolites of the three groups. A positive metabolites; B negative metabolites. Notes: Longitudinal clustering of samples and trans-verse clustering of metabolites. The shorter the clustering branches, the higher the similarity. Through horizontal comparison, we can see the relationship between groups of metabolite content clustering
KEGG enrichment scatterplots (a) and net (b) of differential cord blood metabolites. A the prepregnancy overweight/obesity group vs. the control group; B the excessive GWG group vs. the control group. (1) positive metabolites; (2) negative metabolites. Notes: (a) The horizontal co-ordinates in the figure are x/y (the number of differential metabolites in the corresponding metabolic pathway/the total number of total metabolites identified in this pathway). The value represents the enrichment degree of differential metabolites in the pathway. The color of the point rep-resents the P -value of the hypergeometric test, and the size of the point represents the number of differential metabolites in the corresponding pathway. (b) The red dot represents a metabolic pathway, the yellow dot represents a substance-related regulatory enzyme information, the green dot represents the background substance of a metabolic pathway, the purple dot represents the molecular module information of a class of substances, the blue dot represents a substance chemical reaction, and the green square represents the differential substance obtained by this comparison
Maternal excessive GWG
A total of 109 cord blood metabolites (52 positive metabolites and 57 negative metabolites) differed between the excessive GWG group and the control group. Compared with the control group, in the excessive GWG group, there were 63 metabolites (15 positive metabolites and 48 negative metabolites) with increased concentrations, among which 2-thio-acetyl MAGE was the metabolite with the largest increase, followed by PC (7:0/8:0), lysopc 16:2 (2 N isomer), MGMG (18:2), and thromboxane B2 (Fig. 2 B). Compared with the levels in the control group, the levels of 46 metabolites (37 positive metabolites and 9 negative metabolites) in the excessive GWG group were reduced, among which hippuric acid had the largest decrease, followed by 8-hydroxyquinoline, gamithromycin, 2-phenylglycine, and cefmetazole (Fig. 2 B).
A hierarchical analysis of differential metabolites obtained in the two groups was carried out, and the difference in metabolic expression patterns between the two groups and within the same comparison was obtained, which is shown in Fig. 3 . KEGG pathway analysis of the cord blood metabolites associated with the excessive GWG group versus the control group is shown in Table 4 and Fig. 4 B. The metabolite enrichment analysis revealed that biosynthesis of unsaturated fatty acids was the most altered pathway between the excessive GWG and control groups ( P value < 0.01). There were 13 metabolites distributed in the enriched pathway. The levels of docosapentaenoic acid (DPA), docosahexaenoic acid (DHA), arachidonic acid, adrenic acid, palmitic acid, stearic acid, behenic acid, lignoceric acid, and erucic acid were increased in the excessive GWG group relative to those in the control group.
Our present study found that both maternal prepregnancy overweight/obesity and excessive GWG could affect umbilical cord blood metabolites, and they had different effects on these metabolites. Regardless of their gestational weight gain, the umbilical cord blood of prepregnancy overweight and obese mothers had 46 metabolites increased and 60 metabolites decreased compared with the umbilical cord blood of mothers with normal body weight and appropriate GWG. Steroid hormone biosynthesis and neuroactive ligand‒receptor interactions were the two top-ranking pathways enriched with these metabolites. Compared with mothers with normal prepregnancy BMI and appropriate GWG, in mothers with normal prepregnancy BMI but excessive GWG, the levels of 63 metabolites were increased and those of 46 metabolites were decreased in umbilical cord blood. Biosynthesis of unsaturated fatty acids was the most altered pathway enriched with these metabolites.
There were many differential metabolites in the cord blood between the prepregnancy overweight/obesity group and the control group and between the excessive GWG group and the control group. However, the roles of most of these differential metabolites are unknown. The levels of stearamide and methanandamide were increased in the prepregnancy overweight/obesity group. Stearamide, also known as octadecanamide or kemamide S, belongs to the class of organic compounds known as carboximidic acids. Stearamide, which is increased in the serum of patients with hepatic cirrhosis and sepsis, may be associated with the systemic inflammatory state [ 22 , 23 ]. Methanandamide is a stable analog of anandamide that participates in energy balance mainly by activating cannabinoid receptors. Methanandamide dose-dependently inhibits and excites tension-sensitive gastric vagal afferents (GVAs), which play a role in appetite regulation [ 24 ]. In mice fed a high-fat diet, only an inhibitory effect of methanandamide was observed, and GVA responses to tension were dampened [ 24 , 25 ]. These changes may contribute to the development and/or maintenance of obesity. Moreover, methanandamide can produce dose-related hypothermia and attenuate cocaine-induced hyperthermia by a cannabinoid 1-dopamine D2 receptor mechanism [ 26 ].
Metabolomic pathway analysis of the cord blood metabolite features in the prepregnancy overweight and obesity group identified two filtered significant pathways: steroid hormone biosynthesis and neuroactive ligand‒receptor interaction pathways. In the steroid hormone biosynthesis pathway, the levels of several glucocorticoids (including corticosterone, 11-deoxycortisol, cortisol, testosterone, and 7α-hydroxytestosterone) were decreased in the prepregnancy overweight/obesity group. In addition to the physiological role of glucocorticoids in the healthy neuroendocrine development and maturation of fetuses and babies, glucocorticoids are essential to human health by regulating different physiological events in mature organs and tissues, such as glucose metabolism, lipid biosynthesis and distribution, food intake, thermogenesis, and mood and learning patterns [ 27 ]. Glucocorticoids have been considered as a link between adverse early-life conditions and the development of metabolic disorders in later life [ 28 , 29 , 30 ]. However, there is still much controversy regarding the role of maternal obesity in the fetal–steroid hormone biosynthesis pathway. Studies of maternal obesity animal models showed that corticosterone and cortisol levels were increased in the offspring of obese mothers [ 31 , 32 ]. A study reported by Satu M Kumpulainen et al. showed that young adults born to mothers with higher early pregnancy BMIs show lower average levels of diurnal cortisol, especially in the morning [ 33 ]. Laura I. Stirrat et al. found that increased maternal BMI was associated with lower maternal cortisol, corticosterone, and 11-dehydrocorticosterone levels. However, there were no associations between maternal BMI and glucocorticoid levels in the cord blood [ 34 ]. The differences in the study protocols of these previous studies may explain the mixed findings, such as cortisol measured from peripheral blood, cord blood or saliva; variation in measurement time points; the number of samples. Although the effect of maternal obesity on fetal steroid hormone levels is controversial, dysregulation of glucocorticoids may be a plausible mechanism by which maternal obesity can increase the risk of metabolic disorders and mental health disorders in offspring.
The effect of excessive GWG on umbilical cord blood metabolites is different from that of maternal overweight and obesity. Compared with the control group, in the excessive GWG group, the level of thromboxane B2 was increased and the level of hippuric acid was decreased. Thromboxane B2, which is important in the platelet release reaction, is a stable, physiologically active compound formed in vivo from prostaglandin endoperoxides. Hippuric acid is an acyl glycine formed from the conjugation of benzoic acid with glycine. Several studies have confirmed that both thromboxane B2 and hippuric acid levels are associated with diet. Dietary fatty acids affect platelet thromboxane production [ 35 , 36 , 37 ]. In our study, several fatty acids (e.g., palmitic acid, stearic acid, behenic acid, and lignoceric acid) in the excessive GWG group were also increased, which may have led to the increase in thromboxane B2 levels. Hippuric acid can be detected after the consumption of whole grains and anthocyanin-rich bilberries [ 38 , 39 ]. A healthy diet intervention increased the signals for hippuric acid to incorporate polyunsaturated fatty acids [ 38 ], and the low level of hippuric acid was associated with lower fruit-vegetable intakes [ 39 ]. Maternal overnutrition and unhealthy dietary patterns are the main reasons for excessive GWG [ 40 , 41 ]. Therefore, we speculated that the differences in thromboxane B2 and hippuric acid between the excessive GWG and control groups were associated with maternal diet during pregnancy. The effect of these differential metabolites on the long-term metabolic health of offspring after birth needs further study.
Metabolomic pathway analysis of the cord blood metabolite features in the excessive GWG group identified that biosynthesis of unsaturated fatty acids was the filtered significant pathway. The levels of several fatty acids in this pathway were increased in the excessive GWG group, including long-chain saturated fatty acids (e.g., palmitic acid (C 16:0), stearic acid (C 18:0), behenic acid (C 22:0), and lignoceric acid (C 23:0)), monounsaturated fatty acids (erucic acid), and polyunsaturated fatty acids (e.g., DPA, DHA, arachidonic acid, and adrenic acid). Because perinatal fatty acid status can be influenced by maternal dietary modifications or supplementation [ 42 ], we speculated that maternal diet during pregnancy caused the difference in umbilical cord blood fatty acids between the excessive GWG and control groups. A large body of evidence from mechanistic studies supports the potential of fatty acids to influence later obesity. However, the possible mechanisms and observed relationships are complex and related to the types and patterns of fatty acids [ 43 , 44 ]. Maternal dietary fatty acids have been found to induce hypothalamic inflammation, cause epigenetic changes, and alter the mechanisms of energy control in offspring [ 43 ]. Evidence from cell culture and rodent studies showed that polyunsaturated fatty acids might serve several complex roles in fetuses, including the stimulation and/or inhibition regulation of adipocyte differentiation [ 44 ]. The questions of whether lower n-6 long-chain polyunsaturated fatty acid levels or higher n-3 long-chain polyunsaturated fatty acid levels are of more relevance and whether the long-term effects differ with different offspring ages remain [ 44 ]. Although there is a biologically plausible case for the relevance of perinatal fatty acid status in later obesity risk, available data in humans suggest that the influence of achievable modification of perinatal n-3/n-6 status is not sufficient to influence offspring obesity risk in the general population [ 45 ]. Further studies seem justified to clarify the reasons.
The advantage of our present study is that we simultaneously analyzed the effects of prepregnancy overweight/obesity and excessive GWG on cord blood metabolites and explored their differences. In addition, to exclude the effect of hyperglycemia on cord blood metabolites, both women with prepregnancy diabetes mellitus and gestational diabetes mellitus were excluded from our study. The limitation of our study is that it was a single-center study with a small sample, especially in the prepregnancy overweight/obesity group. In the future, we can expand the sample size and conduct a subgroup analysis of the prepregnancy overweight/obesity group and analyze the differences in the effects of different degrees of obesity on cord blood metabolites. The prepregnancy overweight/obesity group can be further divided into an appropriate GWG group and an excessive GWG group, and the differences in the effects of these two groups on umbilical cord blood metabolites can be analyzed. Moreover, the dietary pattern of the pregnant woman could affect the production of cord blood metabolites. We did not investigate the dietary patterns of the mothers in this study, which is another limitation of this study. In future studies, we should investigate maternal dietary patterns as a very important confounding variable.
In conclusion, our present study confirmed that both prepregnancy overweight/obesity and excessive GWG could affect umbilical cord blood metabolites, and they had different effects on these metabolites. Prepregnancy overweight and obesity affected the fetal steroid hormone biosynthesis pathway, while normal prepregnancy body weight but excessive GWG affected fetal fatty acid metabolism. This emphasizes the importance of preconception weight loss and maintaining an appropriate GWG, which are beneficial for the long-term metabolic health of offspring.
Availability of data and materials
Data sets generated during the current study are not publicly available but will be available from the corresponding author at a reasonable request. Responses to the request for the raw data will be judged by a committee including XXY and GHL.
Abbreviations
Excessive gestational weight gain
Ultrahigh-performance liquid chromatography tandem mass spectrometry
Type 2 diabetes mellitus
Nonalcoholic fatty liver disease
The developmental origins of health and disease
Body mass index
Diabetes mellitus
Gestational diabetes mellitus
Oral glucose tolerance test
Low birth weight
Standard deviation
The Human Metabolome Database
Kyoto Encylopaedia of Genes and Genomes
Principal component analysis
Partial least-squares discriminant analysis
Importance for the projection
Fold change
Invitro fertilization and embryo transfer
Triglyceride
Docosapentaenoic acid
Docosahexaenoic acid
Gastric vagal afferents
Collaborators GBDO, Afshin A, Forouzanfar MH, Reitsma MB, Sur P, Estep K, Lee A, Marczak L, Mokdad AH, Moradi-Lakeh M, et al. Health effects of overweight and obesity in 195 countries over 25 years. N Engl J Med. 2017;377(1):13–27.
Article Google Scholar
Bjerregaard LG, Jensen BW, Angquist L, Osler M, Sorensen TIA, Baker JL. Change in overweight from childhood to early adulthood and risk of type 2 diabetes. N Engl J Med. 2018;378(14):1302–12.
Article PubMed Google Scholar
Sharma V, Coleman S, Nixon J, Sharples L, Hamilton-Shield J, Rutter H, Bryant M. A systematic review and meta-analysis estimating the population prevalence of comorbidities in children and adolescents aged 5 to 18 years. Obes Rev. 2019;20(10):1341–9.
Article PubMed PubMed Central Google Scholar
Llewellyn A, Simmonds M, Owen CG, Woolacott N. Childhood obesity as a predictor of morbidity in adulthood: a systematic review and meta-analysis. Obes Rev. 2016;17(1):56–67.
Article CAS PubMed Google Scholar
Poston L, Caleyachetty R, Cnattingius S, Corvalan C, Uauy R, Herring S, Gillman MW. Preconceptional and maternal obesity: epidemiology and health consequences. Lancet Diabetes Endocrinol. 2016;4(12):1025–36.
Pan XF, Wang L, Pan A. Epidemiology and determinants of obesity in China. Lancet Diabetes Endocrinol. 2021;9(6):373–92.
Barker DJ. The developmental origins of adult disease. J Am Coll Nutr. 2004;23(6 Suppl):588S-595S.
LifeCycle Project-Maternal O, Childhood Outcomes Study G, Voerman E, Santos S, Inskip H, Amiano P, Barros H, Charles MA, Chatzi L, Chrousos GP, et al. Association of gestational weight gain with adverse maternal and infant outcomes. JAMA. 2019;321(17):1702–15.
Aune D, Saugstad OD, Henriksen T, Tonstad S. Maternal body mass index and the risk of fetal death, stillbirth, and infant death: a systematic review and meta-analysis. JAMA. 2014;311(15):1536–46.
Ukah UV, Bayrampour H, Sabr Y, Razaz N, Chan WS, Lim KI, Lisonkova S. Association between gestational weight gain and severe adverse birth outcomes in Washington State, US: a population-based retrospective cohort study, 2004–2013. PLoS Med. 2019;16(12):e1003009.
Starling AP, Brinton JT, Glueck DH, Shapiro AL, Harrod CS, Lynch AM, Siega-Riz AM, Dabelea D. Associations of maternal BMI and gestational weight gain with neonatal adiposity in the Healthy Start study. Am J Clin Nutr. 2015;101(2):302–9.
Voerman E, Santos S, Patro Golab B, Amiano P, Ballester F, Barros H, Bergstrom A, Charles MA, Chatzi L, Chevrier C, et al. Maternal body mass index, gestational weight gain, and the risk of overweight and obesity across childhood: an individual participant data meta-analysis. PLoS Med. 2019;16(2):e1002744.
Heslehurst N, Vieira R, Akhter Z, Bailey H, Slack E, Ngongalah L, Pemu A, Rankin J. The association between maternal body mass index and child obesity: a systematic review and meta-analysis. PLoS Med. 2019;16(6):e1002817.
Newgard CB. Metabolomics and metabolic diseases: where do we stand? Cell Metab. 2017;25(1):43–56.
Johnson CH, Ivanisevic J, Siuzdak G. Metabolomics: beyond biomarkers and towards mechanisms. Nat Rev Mol Cell Biol. 2016;17(7):451–9.
Article CAS PubMed PubMed Central Google Scholar
Hivert MF, Perng W, Watkins SM, Newgard CS, Kenny LC, Kristal BS, Patti ME, Isganaitis E, DeMeo DL, Oken E, et al. Metabolomics in the developmental origins of obesity and its cardiometabolic consequences. J Dev Orig Health Dis. 2015;6(2):65–78.
Schlueter RJ, Al-Akwaa FM, Benny PA, Gurary A, Xie G, Jia W, Chun SJ, Chern I, Garmire LX. Prepregnant obesity of mothers in a multiethnic cohort is associated with cord blood metabolomic changes in offspring. J Proteome Res. 2020;19(4):1361–74.
Shokry E, Marchioro L, Uhl O, Bermudez MG, Garcia-Santos JA, Segura MT, Campoy C, Koletzko B. Impact of maternal BMI and gestational diabetes mellitus on maternal and cord blood metabolome: results from the PREOBE cohort study. Acta Diabetol. 2019;56(4):421–30.
Chen C, Lu FC, Department of Disease Control Ministry of Health PRC. The guidelines for prevention and control of overweight and obesity in Chinese adults. Biomed Environ Sci. 2004;17(Suppl):1–36.
PubMed Google Scholar
The American College of Obstetricians and Gynecologists. Macrosomia: ACOG practice bulletin, number 216. Obstet Gynecol. 2020;135(1):e18–e35.
Goldenberg RL, Culhane JF. Low birth weight in the United States. Am J Clin Nutr. 2007;85(2):584S-590S.
Lian JS, Liu W, Hao SR, Guo YZ, Huang HJ, Chen DY, Xie Q, Pan XP, Xu W, Yuan WX, et al. A serum metabonomic study on the difference between alcohol- and HBV-induced liver cirrhosis by ultraperformance liquid chromatography coupled to mass spectrometry plus quadrupole time-of-flight mass spectrometry. Chin Med J (Engl). 2011;124(9):1367–73.
CAS PubMed Google Scholar
Ding W, Xu S, Zhou B, Zhou R, Liu P, Hui X, Long Y, Su L. Dynamic plasma lipidomic analysis revealed cholesterol ester and amides associated with sepsis development in critically Ill patients after cardiovascular surgery with cardiopulmonary bypass. J Pers Med. 2022;12(11):1838.
Christie S, O’Rielly R, Li H, Nunez-Salces M, Wittert GA, Page AJ. Modulatory effect of methanandamide on gastric vagal afferent satiety signals depends on nutritional status. J Physiol. 2020;598(11):2169–82.
Christie S, O’Rielly R, Li H, Wittert GA, Page AJ. High fat diet induced obesity alters endocannabinoid and ghrelin mediated regulation of components of the endocannabinoid system in nodose ganglia. Peptides. 2020;131:170371.
Rasmussen BA, Kim E, Unterwald EM, Rawls SM. Methanandamide attenuates cocaine-induced hyperthermia in rats by a cannabinoid CB1-dopamine D2 receptor mechanism. Brain Res. 2009;1260:7–14.
Facchi JC, Lima TAL, Oliveira LR, Costermani HO, Miranda GDS, de Oliveira JC. Perinatal programming of metabolic diseases: the role of glucocorticoids. Metabolism. 2020;104:154047.
Reynolds RM, Walker BR, Syddall HE, Andrew R, Wood PJ, Whorwood CB, Phillips DI. Altered control of cortisol secretion in adult men with low birth weight and cardiovascular risk factors. J Clin Endocrinol Metab. 2001;86(1):245–50.
Valtat B, Dupuis C, Zenaty D, Singh-Estivalet A, Tronche F, Breant B, Blondeau B. Genetic evidence of the programming of beta cell mass and function by glucocorticoids in mice. Diabetologia. 2011;54(2):350–9.
Jia Y, Li R, Cong R, Yang X, Sun Q, Parvizi N, Zhao R. Maternal low-protein diet affects epigenetic regulation of hepatic mitochondrial DNA transcription in a sex-specific manner in newborn piglets associated with GR binding to its promoter. PLoS ONE. 2013;8(5):e63855.
Rodriguez JS, Rodriguez-Gonzalez GL, Reyes-Castro LA, Ibanez C, Ramirez A, Chavira R, Larrea F, Nathanielsz PW, Zambrano E. Maternal obesity in the rat programs male offspring exploratory, learning and motivation behavior: prevention by dietary intervention pre-gestation or in gestation. Int J Dev Neurosci. 2012;30(2):75–81.
Tuersunjiang N, Odhiambo JF, Long NM, Shasa DR, Nathanielsz PW, Ford SP. Diet reduction to requirements in obese/overfed ewes from early gestation prevents glucose/insulin dysregulation and returns fetal adiposity and organ development to control levels. Am J Physiol Endocrinol Metab. 2013;305(7):E868-878.
Kumpulainen SM, Heinonen K, Kaseva N, Andersson S, Lano A, Reynolds RM, Wolke D, Kajantie E, Eriksson JG, Raikkonen K. Maternal early pregnancy body mass index and diurnal salivary cortisol in young adult offspring. Psychoneuroendocrinology. 2019;104:89–99.
Stirrat LI, Just G, Homer NZM, Andrew R, Norman JE, Reynolds RM. Glucocorticoids are lower at delivery in maternal, but not cord blood of obese pregnancies. Sci Rep. 2017;7(1):10263.
Prisco D, Filippini M, Francalanci I, Paniccia R, Gensini GF, Serneri GG. Effect of n-3 fatty acid ethyl ester supplementation on fatty acid composition of the single platelet phospholipids and on platelet functions. Metabolism. 1995;44(5):562–9.
Kaapa P, Uhari M, Nikkari T, Viinikka L, Ylikorkala O. Dietary fatty acids and platelet thromboxane production in puerperal women and their offspring. Am J Obstet Gynecol. 1986;155(1):146–9.
Teng KT, Chang CY, Kanthimathi MS, Tan AT, Nesaretnam K. Effects of amount and type of dietary fats on postprandial lipemia and thrombogenic markers in individuals with metabolic syndrome. Atherosclerosis. 2015;242(1):281–7.
Hanhineva K, Lankinen MA, Pedret A, Schwab U, Kolehmainen M, Paananen J, de Mello V, Sola R, Lehtonen M, Poutanen K, et al. Nontargeted metabolite profiling discriminates diet-specific biomarkers for consumption of whole grains, fatty fish, and bilberries in a randomized controlled trial. J Nutr. 2015;145(1):7–17.
Brunelli L, Davin A, Sestito G, Mimmi MC, De Simone G, Balducci C, Pansarasa O, Forloni G, Cereda C, Pastorelli R, et al. Plasmatic hippuric acid as a hallmark of frailty in an Italian cohort: the mediation effect of fruit-vegetable intake. J Gerontol A Biol Sci Med Sci. 2021;76(12):2081–9.
Ferreira LB, Lobo CV, Miranda A, Carvalho BDC, Santos LCD. Dietary patterns during pregnancy and gestational weight gain: a systematic review. Rev Bras Ginecol Obstet. 2022;44(5):540–7.
Tielemans MJ, Garcia AH, Peralta Santos A, Bramer WM, Luksa N, Luvizotto MJ, Moreira E, Topi G, de Jonge EA, Visser TL, et al. Macronutrient composition and gestational weight gain: a systematic review. Am J Clin Nutr. 2016;103(1):83–99.
Lewis RM, Wadsack C, Desoye G. Placental fatty acid transfer. Curr Opin Clin Nutr Metab Care. 2018;21(2):78–82.
Cesar HC, Pisani LP. Fatty-acid-mediated hypothalamic inflammation and epigenetic programming. J Nutr Biochem. 2017;42:1–6.
Demmelmair H, Koletzko B. Perinatal polyunsaturated fatty acid status and obesity risk. Nutrients. 2021;13(11):3882.
Hauner H, Brunner S. Early fatty acid exposure and later obesity risk. Curr Opin Clin Nutr Metab Care. 2015;18(2):113–7.
Download references
Acknowledgements
The authors thank the study participants for their involvement and research assistants for their help conducting the study.
This research was funded by the Beijing Natural Science Foundation, grant number 7214231.
Author information
Authors and affiliations.
Division of Endocrinology and Metabolism, Department of Obstetrics, Beijing Obstetrics and Gynecology Hospital, Capital Medical University, Beijing Maternal and Child Health Care Hospital, No. 251, Yaojiayuan Road, Chaoyang District, Beijing, 100026, China
Xianxian Yuan, Yuru Ma, Yan Zhao, Wei Zheng, Ruihua Yang, Lirui Zhang, Xin Yan & Guanghui Li
Department of Obstetrics and Gynecology, The Second Hospital of Jilin University, Changchun, 130041, Jilin, China
You can also search for this author in PubMed Google Scholar
Contributions
XXY designed the study. XXY, WZ, LRZ and XY analyzed the data. YRM, JW, YZ and RHY took part in data collection and management. XXY wrote the manuscript. XXY and GHL reviewed the manuscript and contributed to manuscript revision. All authors contributed to the article and approved the submitted version. All authors reviewed the manuscript.
Corresponding author
Correspondence to Guanghui Li .
Ethics declarations
Ethics approval and consent to participate.
This study has been performed in accordance with the Declaration of Helsinki and has been approved by the ethics committee of Beijing Obstetrics and Gynecology Hospital, Capital Medical University (2021-KY-037). Informed consent was obtained from all subjects involved in the study to publish this paper. All methods were carried out in accordance with relevant guidelines and regulations in the declaration.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary material 1., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Yuan, X., Ma, Y., Wang, J. et al. The influence of maternal prepregnancy weight and gestational weight gain on the umbilical cord blood metabolome: a case–control study. BMC Pregnancy Childbirth 24 , 297 (2024). https://doi.org/10.1186/s12884-024-06507-x
Download citation
Received : 30 September 2023
Accepted : 11 April 2024
Published : 22 April 2024
DOI : https://doi.org/10.1186/s12884-024-06507-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Maternal obesity
- Gestational weight gain
- Offspring health
- Metabolites
- Umbilical cord blood
BMC Pregnancy and Childbirth
ISSN: 1471-2393
- Submission enquiries: [email protected]
- General enquiries: [email protected]

IMAGES
VIDEO
COMMENTS
This study of financial risk-taking among politicians shows risk preferences to be an important antecedent of misconduct. Risk preferences as measured by portfolio choices between risky and safe investments were found to strongly predict political scandals. ... In the new case study "Honeywell and the Great Recession," Sandra Sucher and ...
we draw lessons from seven case studies about the multiple and contingent ways that a corporate risk function can foster highly interactive and intrusive dialogues tosurface and prioritize risks, help to allocate resources to mitigate them, and bring clarity to the value trade-offs and moral dilemmas that lurk in those decisions.
For example, the case study cites a risk that the company assessed as having a 5 percent probability of a somewhat better-than-expected outcome but a 10 percent probability of a significant loss relative to forecast. In this case, the downside risk was greater than the upside potential.
Risk management Magazine Article. Nassim N. Taleb, Daniel G. Goldstein, and Mark W. Spitznagel. Black Swan events are almost impossible to predict. Instead of perpetuating the illusion that we can ...
by Carolin E. Pflueger, Emil Siriwardane, and Adi Sunderam. This paper sheds new light on connections between financial markets and the macroeconomy. It shows that investors' appetite for risk—revealed by common movements in the pricing of volatile securities—helps determine economic outcomes and real interest rates.
Risk culture: defining the weak end of the continuum 6 Diagnosing organizational risk culture 7 The risk assessment journey: benefits for managers 8 Selected pilot findings and interventions 9 Case study 1 - global investment bank 10 Case study 2 - global professional services firm 10
The case challenges students to define the problems and risks that the company faces, given its strategic objectives, its evolving risk profile, and the changing environment. The case also offers a discussion ground for defining the role of the chief risk officer and the relationship between risk management, strategic planning and capital ...
How do different organisations use Predict! to manage their risks and opportunities? Read our risk management case studies to learn from their experiences and insights. Find out how Predict! helps them to achieve their strategic objectives, deliver projects on time and budget, and improve their risk culture.
Newsroom. In this article, industry experts who have gone through the journey of establishing and executing a mature actuarial model risk management function share their tips and tricks through three case studies that convey commonly faced issues.
Establishing an enterprise risk management (ERM) system is widely viewed as providing firms with the tools and processes needed to build resilience and expertise, enabling them to manage the consequences of crises that have led to the collapse of major firms across different industries globally. Intended for use in advanced accounting, auditing, and finance courses, this case study (of a true ...
This Summary of Findings and Recommendations summarizes the Case Studies in Cyber Supply Chain Risk Management series' major findings and recommendations based on expert interviews. The Case Studies in Cyber Supply Chain Risk Management series engaged information security, supply chain, and risk leaders across a diverse set of organizations.
In our case study, the most important risk is 2.1, which represents the risk of "Poor quality of the final product". Then we have 5.2, which represents the risk of "poor staff training," and third we have the risk of "poor customer service." The following Fig. 1 shows a 3D bar graph that allows us to observe it visually.
(Members: access this case study here.) Sometimes risk managers reach a point where they simply have to be realistic about their resources and prospects for implementing large scale change. In another example from the Middle East, an expat risk manager found it was a case of trying to move his company's risk culture at different 'clock ...
Now, let's take a look at a case study that highlights risk management excellence in practice. ApexTech Solutions is a company known for its exemplary risk management practices. Founded in 2005 by visionary entrepreneur Sarah Lawson, ApexTech began as a small start-up in the tech industry.
Risk assessment practices to reveal leading indicators. Risk assessment is a process used to gather knowledge and information around a specific health threat or safety hazard (Smith and Harrison, 2005).Based on the probability of a negative incident, risk assessment also includes determining whether or not the level of risk is acceptable (Lindhe et al., 2010; International Electrotechnical ...
Chipotle Case Study: Either Manage Risk or Disclose Lack of Risk Management. Back in 2009, we blogged about the SEC's decision to require board-level accountability for ERM. This decision was based on the conclusion that inadequate risk management allowed the regulatory failures that ultimately led to the financial crisis.
To evaluate our cyber defense against risk tolerance criteria, a good starting point would be the plant's process hazard analysis (PHA) documentation, for example the LOPA (Layer of Protection Analysis) sheet. If that's not available, then the HAZOP (Hazard and Operability Study) sheet would be the next go-to document.
Business case studies for success that look at threats to the business - intellectual property (IP) protection, individual and organisation stress, workplace fraud and securing business knowledge. Mitigating Risk
HypoCom case study design. Working in small teams, students are given an extensive profile about the company with data and information to assess, including corporate structure, operations, competitive environment, and risk management options. Students must address four specific risks facing HypoCom: warehouse fire risk, fluctuations in the ...
The case study showed that expert involvement could not be eliminated to ensure that the quality of the risk assessment is acceptable and that all risks are identified. Based on this finding, we also learned that changes of this type must be managed over time to achieve the desired results.
Case Study: Improving Risk Culture. Risk management is a key component of every organization's strategy and operations. Companies make important risk-based decisions every day. At the forefront of such risk decisions are financial institutions. Improving risk culture allows a company to both raise awareness on how to better manage risk, and ...
Case Study Following successful cranial surgery, a 54-year-old man experienced back and lower extremity pain which was ultimately diagnosed as being related to an intrathecal lumbar catheter left behind at the time of surgery eight months earlier.
Read our IT assessment case study that lends insight into a risk mitigation analysis we completed. Learn more about the IT risk assessment services Harvard Partners offers by visiting our website. ... Case Studies Open Positions Connect. Location. 75 Arlington Street, Suite 500 Boston, Massachusetts 02116
The ordering process is fully online, and it goes as follows: • Select the topic and the deadline of your case study. • Provide us with any details, requirements, statements that should be emphasized or particular parts of the writing process you struggle with. • Leave the email address, where your completed order will be sent to.
While the risk and regulatory protection agenda remains a major focus, banks must also address financial performance and heightened customer and investor expectations, as they reshape and optimize operational and business models to deliver sustainable returns. ... Case study: how one regional bank used core platform modernization to build a ...
This qualitative case study was situated within a larger multi-methods evaluation of the EHR transition. We conducted a total of 122 interviews with 30 clinicians and staff across disciplines at the initial VA EHR transition site before, immediately after, and up to 12 months after go-live (September 2020-November 2021).
In Ecuador, the regulatory framework for the remediation of petroleum-contaminated soils is based on predefined concentration endpoints for a selected range of petroleum hydrocarbon compounds. However, such approach may lead to over- or under- estimation of the environmental risk posed by contaminated soils. In this study, the end-point remediation criteria according to Ecuadorian ...
The purpose of this study was to investigate the associations between BSDS and HNDI with the risk of NAFLD. In this case-control study, 552 people in good health and 340 people with NAFLD over ...
Environmental, social, and governance (ESG) frameworks began in 2004 as a concept from the United Nations to help investors assess a company's global impact and drive corporate responsibility ...
The aim of the study was to explore the impact of maternal prepregnancy overweight/obesity and excessive GWG on cord blood metabolic profiles. A case control study including 33 pairs of mothers with prepregnancy overweight/obesity and their neonates, 30 pairs of mothers with excessive GWG and their neonates, and 32 control mother-neonate pairs.