CS 261: Research Topics in Operating Systems (2021)
Some links to papers are links to the ACM’s site. You may need to use the Harvard VPN to get access to the papers via those links. Alternate links will be provided.

Meeting 1 (1/26): Overview
Operating system architectures, meeting 2 (1/28): multics and unix.
“Multics—The first seven years” , Corbató FJ, Saltzer JH, and Clingen CT (1972)
“Protection in an information processing utility” , Graham RM (1968)
“The evolution of the Unix time-sharing system” , Ritchie DM (1984)
Additional resources
The Multicians web site for additional information on Multics, including extensive stories and Multics source code.
Technical: The Multics input/output system , Feiertag RJ and Organick EI, for a description of Multics I/O to contrast with Unix I/O.
Unix and Multics , Tom Van Vleck.
… I remarked to Dennis that easily half the code I was writing in Multics was error recovery code. He said, "We left all that stuff out. If there's an error, we have this routine called panic() , and when it is called, the machine crashes, and you holler down the hall, 'Hey, reboot it.'"
The Louisiana State Trooper Story
The IBM 7094 and CTSS
This describes the history of the system that preceded Multics, CTSS (the Compatible Time Sharing System). It also contains one of my favorite stories about the early computing days: “IBM had been very generous to MIT in the fifties and sixties, donating or discounting its biggest scientific computers. When a new top of the line 36-bit scientific machine came out, MIT expected to get one. In the early sixties, the deal was that MIT got one 8-hour shift, all the other New England colleges and universities got a shift, and the third shift was available to IBM for its own use. One use IBM made of its share was yacht handicapping: the President of IBM raced big yachts on Long Island Sound, and these boats were assigned handicap points by a complicated formula. There was a special job deck kept at the MIT Computation Center, and if a request came in to run it, operators were to stop whatever was running on the machine and do the yacht handicapping job immediately.”
Using Ring 5 , Randy Saunders.
"All Multics User functions work in Ring 5." I have that EMail (from Dave Bergum) framed on my wall to this date. … All the documentation clearly states that system software has ring brackets of [1,5,5] so that it runs equally in both rings 4 and 5. However, the PL/I compiler creates segments with ring brackets of [4,4,4] by default. … I found each and every place CNO had fixed a program without resetting the ring brackets correctly. It started out 5 a day, and in 3 months it was down to one a week.”
Bell Systems Technical Journal 57(6) Part 2: Unix Time-sharing System (July–August 1978)
This volume contains some of the first broadly-accessible descriptions of Unix. Individual articles are available on archive.org . As of late January 2021, you can buy a physical copy on Amazon for $2,996. Interesting articles include Thompson on Unix implementation, Ritchie’s retrospective, and several articles on actual applications, especially document preparation.
Meeting 3 (2/2): Microkernels
“The nucleus of a multiprogramming system” , Brinch Hansen P (1970).
“Toward real microkernels” , Liedtke J (1996).
“Are virtual machine monitors microkernels done right?” , Hand S, Warfield A, Fraser K, Kotsovinos E, Magenheimer DJ (2005).
Supplemental reading
“Improving IPC by kernel design” , Liedtke J (1993). Article introducing the first microbenchmark-performant microkernel.
“Are virtual machine monitors microkernels done right?” , Heiser G, Uhlig V, LeVasseur J (2006).
“From L3 to seL4: What have we learnt in 20 years of L4 microkernels?” , Elphinstone K, Heiser G (2013).
Retained: Minimality as key design principle. Replaced: Synchronous IPC augmented with (seL4, NOVA, Fiasco.OC) or replaced by (OKL4) asynchronous notification. Replaced: Physical by virtual message registers. Abandoned: Long IPC. Replaced: Thread IDs by port-like IPC endpoints as message destinations. Abandoned: IPC timeouts in seL4, OKL4. Abandoned: Clans and chiefs. Retained: User-level drivers as a core feature. Abandoned: Hierarchical process management. Multiple approaches: Some L4 kernels retain the model of recursive address-space construc- tion, while seL4 and OKL4 originate mappings from frames. Added: User-level control over kernel memory in seL4, kernel memory quota in Fiasco.OC. Unresolved: Principled, policy-free control of CPU time. Unresolved: Handling of multicore processors in the age of verification. Replaced: Process kernel by event kernel in seL4, OKL4 and NOVA. Abandoned: Virtual TCB addressing. … Abandoned: C++ for seL4 and OKL4.
Meeting 4 (2/4): Exokernels
“Exterminate all operating systems abstractions” , Engler DE, Kaashoek MF (1995).
“Exokernel: an operating system architecture for application-level resource management” , Engler DE, Kaashoek MF, O’Toole J (1995).
“The nonkernel: a kernel designed for the cloud” , Ben-Yehuda M, Peleg O, Ben-Yehuda OA, Smolyar I, Tsafrir D (2013).
“Application performance and flexibility on exokernel systems” , Kaashoek MF, Engler DR, Ganger GR, Briceño HM, Hunt R, Mazières D, Pinckney T, Grimm R, Jannotti J, Mackenzie K (1997).
Particularly worth reading is section 4, Multiplexing Stable Storage, which contains one of the most overcomplicated designs for stable storage imaginable. It’s instructive: if your principles end up here, might there be something wrong with your principles?
“Fast and flexible application-level networking on exokernel systems” , Ganger GR, Engler DE, Kaashoek MF, Briceño HM, Hunt R, Pinckney T (2002).
Particularly worth reading is section 8, Discussion: “The construction and revision of the Xok/ExOS networking support came with several lessons and controversial design decisions.”
Meeting 5 (2/9): Security
“EROS: A fast capability system” , Shapiro JS, Smith JM, Farber DJ (1999).
“Labels and event processes in the Asbestos operating system” , Vandebogart S, Efstathopoulos P, Kohler E, Krohn M, Frey C, Ziegler D, Kaashoek MF, Morris R, Mazières D (2007).
This paper covers too much ground. On the first read, skip sections 4–6.
Meeting 6 (2/11): I/O
“Arrakis: The operating system is the control plane” (PDF) , Peter S, Li J, Zhang I, Ports DRK, Woos D, Krishnamurthy A, Anderson T, Roscoe T (2014)
“The IX Operating System: Combining Low Latency, High Throughput, and Efficiency in a Protected Dataplane” , Belay A, Prekas G, Primorac M, Klimovic A, Grossman S, Kozyrakis C, Bugnion E (2016) — read Sections 1–4 first (return to the rest if you have time)
“I'm Not Dead Yet!: The Role of the Operating System in a Kernel-Bypass Era” , Zhang I, Liu J, Austin A, Roberts ML, Badam A (2019)
- “The multikernel: A new OS architecture for scalable multicore systems” , Baumann A, Barham P, Dagand PE, Harris T, Isaacs R, Peter S, Roscoe T, Schüpach A, Singhana A (2009); this describes the Barrelfish system on which Arrakis is based
Meeting 7 (2/16): Speculative designs
From least to most speculative:
“Unified high-performance I/O: One Stack to Rule Them All” (PDF) , Trivedi A, Stuedi P, Metzler B, Pletka R, Fitch BG, Gross TR (2013)
“The Case for Less Predictable Operating System Behavior” (PDF) , Sun R, Porter DE, Oliveira D, Bishop M (2015)
“Quantum operating systems” , Corrigan-Gibbs H, Wu DJ, Boneh D (2017)
“Pursue robust indefinite scalability” , Ackley DH, Cannon DC (2013)
Meeting 8 (2/18): Log-structured file system
“The Design and Implementation of a Log-Structured File System” , Rosenblum M, Ousterhout J (1992)
“Logging versus Clustering: A Performance Evaluation”
- Read the abstract of the paper ; scan further if you’d like
- Then poke around the linked critiques
Meeting 9 (2/23): Consistency
“Generalized file system dependencies” , Frost C, Mammarella M, Kohler E, de los Reyes A, Hovsepian S, Matsuoka A, Zhang L (2007)
“Application crash consistency and performance with CCFS” , Sankaranarayana Pillai T, Alagappan R, Lu L, Chidambaram V, Arpaci-Dusseau AC, Arpaci-Dusseau RH (2017)
Meeting 10 (2/25): Transactions and speculation
“Rethink the sync” , Nightingale EB, Veeraraghavzn K, Chen PM, Flinn J (2006)
“Operating system transactions” , Porter DE, Hofmann OS, Rossbach CJ, Benn E, Witchel E (2009)
Meeting 11 (3/2): Speculative designs
“Can We Store the Whole World's Data in DNA Storage?”
“A tale of two abstractions: The case for object space”
“File systems as processes”
“Preserving hidden data with an ever-changing disk”
More, if you’re hungry for it
- “Breaking Apart the VFS for Managing File Systems”
Virtualization
Meeting 14 (3/11): virtual machines and containers.
“Xen and the Art of Virtualization” , Barham P, Dragovic B, Fraser K, Hand S, Harris T, Ho A, Neugebauer R, Pratt I, Warfield A (2003)
“Blending containers and virtual machines: A study of Firecracker and gVisor” , Anjali, Caraz-Harter T, Swift MM (2020)
Meeting 15 (3/18): Virtual memory and virtual devices
“Memory resource management in VMware ESX Server” , Waldspurger CA (2002)
“Opportunistic flooding to improve TCP transmit performance in virtualized clouds” , Gamage S, Kangarlou A, Kompella RR, Xu D (2011)
Meeting 16 (3/23): Speculative designs
“The Best of Both Worlds with On-Demand Virtualization” , Kooburat T, Swift M (2011)
“The NIC is the Hypervisor: Bare-Metal Guests in IaaS Clouds” , Mogul JC, Mudigonda J, Santos JR, Turner Y (2013)
“vPipe: One Pipe to Connect Them All!” , Gamage S, Kompella R, Xu D (2013)
“Scalable Cloud Security via Asynchronous Virtual Machine Introspection” , Rajasekaran S, Ni Z, Chawla HS, Shah N, Wood T (2016)
Distributed systems
Meeting 17 (3/25): distributed systems history.
“Grapevine: an exercise in distributed computing” , Birrell AD, Levin R, Schroeder MD, Needham RM (1982)
“Implementing remote procedure calls” , Birrell AD, Nelson BJ (1984)
Skim : “Time, clocks, and the ordering of events in a distributed system” , Lamport L (1978)
Meeting 18 (3/30): Paxos
“Paxos made simple” , Lamport L (2001)
“Paxos made live: an engineering perspective” , Chanra T, Griesemer R, Redston J (2007)
“In search of an understandable consensus algorithm” , Ongaro D, Ousterhout J (2014)
- Adrian Colyer’s consensus series links to ten papers, especially:
- “Raft Refloated: Do we have consensus?” , Howard H, Schwarzkopf M, Madhavapeddy A, Crowcroft J (2015)
- A later update from overlapping authors: “Paxos vs. Raft: Have we reached consensus on distributed consensus?” , Howard H, Mortier R (2020)
- “Understanding Paxos” , notes by Paul Krzyzanowski (2018); includes some failure examples
- One-slide Paxos pseudocode , Robert Morris (2014)
Meeting 19 (4/1): Review of replication results
Meeting 20 (4/6): project discussion, meeting 21 (4/8): industrial consistency.
“Scaling Memcache at Facebook” , Nishtala R, Fugal H, Grimm S, Kwiatkowski M, Lee H, Li HC, McElroy R, Paleczny M, Peek D, Saab P, Stafford D, Tung T, Venkataramani V (2013)
“Millions of Tiny Databases” , Brooker M, Chen T, Ping F (2020)
Meeting 22 (4/13): Short papers and speculative designs
“Scalability! But at what COST?” , McSherry F, Isard M, Murray DG (2015)
“What bugs cause production cloud incidents?” , Liu H, Lu S, Musuvathi M, Nath S (2019)
“Escape Capsule: Explicit State Is Robust and Scalable” , Rajagopalan S, Williams D, Jamjoom H, Warfield A (2013)
“Music-defined networking” , Hogan M, Esposito F (2018)
- Too networking-centric for us, but fun: “Delay is Not an Option: Low Latency Routing in Space” , Handley M (2018)
- A useful taxonomy: “When Should The Network Be The Computer?” , Ports DRK, Nelson J (2019)
Meeting 23 (4/20): The M Group
“All File Systems Are Not Created Equal: On the Complexity of Crafting Crash-Consistent Applications” , Pillai TS, Chidambaram V, Alagappan R, Al-Kiswany S, Arpaci-Dusseau AC, Arpaci-Dusseau RH (2014)
“Crash Consistency Validation Made Easy” , Jiang Y, Chen H, Qin F, Xu C, Ma X, Lu J (2016)
Meeting 24 (4/22): NVM and Juice
“Persistent Memcached: Bringing Legacy Code to Byte-Addressable Persistent Memory” , Marathe VJ, Seltzer M, Byan S, Harris T
“NVMcached: An NVM-based Key-Value Cache” , Wu X, Ni F, Zhang L, Wang Y, Ren Y, Hack M, Shao Z, Jiang S (2016)
“Cloudburst: stateful functions-as-a-service” , Sreekanti V, Wu C, Lin XC, Schleier-Smith J, Gonzalez JE, Hellerstein JM, Tumanov A (2020)
- Adrian Colyer’s take
Meeting 25 (4/27): Scheduling
- “The Linux Scheduler: A Decade of Wasted Cores” , Lozi JP, Lepers B, Funston J, Gaud F, Quéma V, Fedorova A (2016)
Study at Cambridge
About the university, research at cambridge.
- Events and open days
- Fees and finance
- Student blogs and videos
- Why Cambridge
- Course directory
- How to apply
- Fees and funding
- Frequently asked questions
- International students
- Continuing education
- Executive and professional education
- Courses in education
- How the University and Colleges work
- Visiting the University
- Term dates and calendars
- Video and audio
- Find an expert
- Publications
- Global Cambridge
- Public engagement
- Give to Cambridge
- For current students
- For business
- Colleges & departments
- Libraries & facilities
- Museums & collections
- Email & phone search
- Computer Laboratory
- Past exam papers
Operating Systems
Department of Computer Science and Technology
- Academic staff
- Support staff
- Contract researchers
- Fellows & affiliates
- PhD students
- Wednesday Seminar Series
- Wheeler Lectures
- women@cl 10th Anniversary
- Computer Laboratory 75th Anniversary
- Shopping and leisure
- Library induction
- Electronic resources
- Virtual journals shelf
- Local services
- Lab technical reports
- External technical reports
- Resource lists
- Reading lists
- Maps and directions
- Contact information
- Group Meetings
- Project ideas for current students
- Projects and research topics
- [no title found]
- Selected Publications
- Open source components
- Contact Details
- Digital Technology
- Applying to do a PhD
- Project suggestions
- Other information
- Reading Club
- Postgraduate opportunities
- Programming, Logic, Semantics
- Projects and topics
- Security Seminar Series
- Mailing lists
- Research Projects
- Student Projects
- Research Admin
- PhD applications
- Graduate Admissions Prospectus
- Funding deadlines
- MPhil in Advanced Computer Science
- Premium Research Studentship
- Student Administration
- Induction for M.Phil and Part III students
- Part III and ACS projects
- Part IA CST
- Part IB CST
- Part II CST
- Lecturer index
- Instructions for lecturers
- Examination dates
- Examination results
- Examiners' reports
- Plagiarism and collusion
- Purchase of calculators
- Data Retention Policy
- Guidance on deadlines
- Part III Assessment
- MPhil Assessment
- Student Complaint Procedure
- Short form timetable
- Part II supervisions overview
- Part II sign-up dates
- Notes on supervising
- Supervisor support
- Advice for students visiting Cambridge
- UROP internships
- Previous years
- Briefing document (Pink Book)
- Important dates
- Phase 1 report
- Back-up advice
- Resources Declaration
- Studies Involving Human Participants
- Failure to submit proposal
- Selection Tips
- Declaration of originality
- Submission of dissertation
- IP ownership
- Diploma model projects
- Older project suggestions
- Supervising Notes
- Overseer Briefing Notes
- Directors of Studies
- Managed Cluster Service
- Part III and MPhil machines
- Online services
- Installing Linux
- Microsoft Azure for Education Membership
- Neil Wiseman, 1934–1995
- Roger Needham, 1935–2003
- David Wheeler, 1927–2004
- Karen Spärck Jones, 1935–2007
- Judith Ann Bailey, 1934–2008
- Robin Milner, 1934–2010
- Sir Maurice Wilkes, 1913–2010
- Michael JC Gordon, 1948–2017
- Richard Gibbens, 1962–2018
- An introduction to our computing facilities
- Information for new PhD students
- Information for new staff
- Information for visitors
- Information for hosts of visitors
- General information
- Induction Guidelines
- Specialist resources
- Printing and scanning
- The CL network
- SSH access to the CL systems
- Supported platforms
- Generic Unix/Linux information
- Web servers and sites
- The RT ticketing system
- Lecture theatre AV
- Departmental policies
- Meeting rooms
- Personnel information
- Staff training
- Wiseman prize
- General health and safety
- Environment
- H&S policies & committees
- Risk assessment
- Laser safety
- Useful links
- Index of Health & Safety pages
- PhD supervisors
- Graduate Advisers
- First Year Report: PhD Proposal
- Second Year Report: Dissertation Schedule
- Third Year Report: Progress Statement
- Fourth Year Report: the last year
- Papers and conferences
- Thesis formatting
- Submitting your dissertation
- Exemption from University Composition Fees
- Leave to work away, holidays and intermission
- Researcher Development
- Application deadlines
- List of PhD thesis
- Graduate Students' Forum
- PAT, recycling and Building Services
- Preparing Tripos exam questions in LaTeX
- Information for CST examiners
- Information for Directors of Studies
- ACS module definition
- Providing advice to incoming ACS students
- ACS interviewing and admissions
- Outreach material
- Faculty Board
- Degree Committee
- Graduate Education
- Tripos Management
- Health & Safety
- IT Strategy
- Equality and Diversity
- Research Staff
- Staff–Student
- Graduate Students
- Buildings and Environment
- Discontinued committees
- Building Services
- Access and security
- Care of the WGB
- Facilities in offices
- Energy & Environment
- West Cambridge Site
- Leaving the department
Past exam papers: Operating Systems
Solution notes are available for many past questions to local users. They were produced by question setters, primarily for the benefit of the examiners. These are not model answers : there may be many other good ways of answering a given exam question!
The solution notes for the most recent two year’s worth of examinations (with exceptions for 2020 and 2021) are held back by the department and only made available to supervisors and other teaching staff (marked with 🔒). Supervisors are instructed not to release hardcopy or electronic versions of these notes to students, although they may be shown to students during supervisions when helpful. Access to any solution notes here requires a Raven login, i.e. they are not public.
Making corrections: Question setters who want to amend solution notes can find the source files under /anfs/www/tripospapers/ and may email updated files to pagemaster.
- 2023 Paper 2 Question 3 – 🔒solution notes
- 2023 Paper 2 Question 4 – 🔒solution notes
- 2022 Paper 2 Question 3 – 🔒solution notes
- 2022 Paper 2 Question 4 – 🔒solution notes
- 2021 Paper 2 Question 3 – solution notes
- 2021 Paper 2 Question 4 – solution notes
- 2020 Paper 2 Question 3 – solution notes
- 2020 Paper 2 Question 4 – solution notes
- 2019 Paper 2 Question 3 – solution notes
- 2019 Paper 2 Question 4 – solution notes
- 2018 Paper 2 Question 3 – solution notes
- 2018 Paper 2 Question 4 – solution notes
- 2017 Paper 2 Question 3 – solution notes
- 2017 Paper 2 Question 4 – solution notes
- 2016 Paper 2 Question 3 – solution notes
- 2016 Paper 2 Question 4 – solution notes
- 2015 Paper 2 Question 3 – solution notes
- 2015 Paper 2 Question 4 – solution notes
- 2014 Paper 2 Question 3 – solution notes
- 2014 Paper 2 Question 4 – solution notes
- 2013 Paper 2 Question 3 – solution notes
- 2013 Paper 2 Question 4 – solution notes
- 2012 Paper 2 Question 3 – solution notes
- 2012 Paper 2 Question 4 – solution notes
- 2011 Paper 2 Question 3 – solution notes
- 2011 Paper 2 Question 4 – solution notes
- 2010 Paper 2 Question 3 – solution notes
- 2010 Paper 2 Question 4 – solution notes
- 2009 Paper 2 Question 3 – solution notes
- 2009 Paper 2 Question 4 – solution notes
- 2008 Paper 1 Question 2 – solution notes
- 2008 Paper 1 Question 7 – solution notes
- 2008 Paper 1 Question 8 – solution notes
- 2007 Paper 1 Question 2 – solution notes
- 2007 Paper 1 Question 7 – solution notes
- 2007 Paper 1 Question 8 – solution notes
- 2006 Paper 1 Question 2 – solution notes
- 2006 Paper 1 Question 7 – solution notes
- 2006 Paper 1 Question 8 – solution notes
- 2005 Paper 1 Question 4
- 2005 Paper 1 Question 11
- 2005 Paper 1 Question 12
- 2004 Paper 1 Question 4
- 2004 Paper 1 Question 11
- 2004 Paper 1 Question 12
- 2003 Paper 1 Question 4
- 2003 Paper 1 Question 11
- 2003 Paper 1 Question 12
- 2002 Paper 1 Question 4
- 2002 Paper 1 Question 11
- 2002 Paper 1 Question 12
- 2001 Paper 1 Question 4
- 2001 Paper 1 Question 11
- 2001 Paper 1 Question 12
- 2000 Paper 1 Question 3
- 2000 Paper 1 Question 11
- 2000 Paper 1 Question 12
- 1999 Paper 1 Question 4
- 1999 Paper 1 Question 11
- 1999 Paper 1 Question 12
- 1998 Paper 1 Question 4
- 1998 Paper 1 Question 11
- 1998 Paper 1 Question 12
- 1997 Paper 1 Question 4
- 1997 Paper 1 Question 11
- 1997 Paper 1 Question 12
- 1994 Paper 10 Question 6
- 1993 Paper 10 Question 5
🔒 = access to solution notes is restricted to cl-supervisors, teaching, wednesday, undergrad-directors-of-studies .
- University A-Z
- Contact the University
- Accessibility
- Freedom of information
- Terms and conditions
- Undergraduate
- Spotlight on...
- About research at Cambridge
bestessayhelp.com
Operating Systems – Essay Sample
An operating system, or OS, is a common computer piece in the world today. An OS is an intricate set of software programs that helps organize information within a computer’s hardware. It can store information and retrieve it from memory systems or the hard drive. It can also direct applications and programs within the computer or from portable sources. In essence, an operating system communicates between the hardware and the programs as an organizational tool. For example, when you click on a program file to retrieve stored information, it is the operating system that communicates the command to the hardware, which pulls up the desired information. This means the only way that programs and hardware can interact is through the operating system, which determines the set of procedures and regulations they must follow to maintain order in the computer system.
There are many common operating systems used in the world today. They are used in many electronic devices, including computers, phones, videogames, tablets, portable music devices and websites. The Macintosh company is currently known for producing several operating systems, including Mac OS and Mac OS X (there are several versions of the Mac OS X, including the Lion and the Snow Leopard). The search engine Google recently developed the Google Chrome operating system, thought it was created from the foundations of an older system know as Linux kernel, one of the first that applied to many different devices. Linux, in turn, was derived from UNIX, the original (and largest) group of operating systems, which included a successful subgroup known as BSD. Microsoft Windows is another popular operating system with many versions (Windows 95, Windows 7, etc.).
There are also many different types of operating systems. Some are more commonly used than others, but all have benefits. Some, base their functions on timelines and real-time events. These programs are found in scheduled updates, reservation programs and other time-related tasks; they are known as real-time operating systems. A distributed operating system, on the other hand, links many computers together to create a cohesive network of information and rules; power and electricity-governing computers are a typical example.
Multi-user and single-user operating systems either allow multiple access to computer information (multi) or only allow the access of one persona at a time (single). Home computers typically allow only one user access at a time to the system on that computer. An embedded operating system are typically found on devices other than computers – usually phones and other small devices – and have much more strict, regulated, efficient operating styles than others. Without the invention of the operating system, computers would not have nearly the amount of power, diversity and applicability they do today.
The road to success is easy with a little help. Let's get your assignment out of the way.
Home — Essay Samples — Information Science and Technology — Operating System — Operating System & Its Examples
Operating System & Its Examples
- Categories: Computer Computer Software Operating System
About this sample

Words: 401 |
Published: Mar 19, 2020
Words: 401 | Page: 1 | 3 min read
Table of contents

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
1 pages / 594 words
3 pages / 1146 words
2 pages / 707 words
3 pages / 1370 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Operating System
The market for operating systems is an oligopoly, characterized by a few dominant firms controlling the majority of the market. Microsoft is a significant player in this market due to its historical dominance and market control. [...]
Operation management can be defined as “a configuration of resources combined for the provision of goods or services” (Morris, 1978). It involves planning, organizing, and supervising processes, and make necessary improvements [...]
Android operating system started its journey with the public release of android beta in November, 2007. But its first commercial version android 1. 0 is introduced in September, 2008. Android is a mobile operating system [...]
The International Federation of Red Cross (IFRC) is an organization which operating activities are filled with unpredictability and urgency, that many of the fundamentals that apply to normal business supply chains do not fit as [...]
Android is a Linux kernel based operating system and currently developed by Google. The Android operating system is one of the most widely used operating systems. Android Operating System has a middleware and other key [...]
Jawa- It is a programming language and used for developing Mobile, Desktop, web, server-side and web applications. It is also used in the development of the Android application. It is fast, safe, and very reliable.and grounded [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!

Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

- Get started with computers
- Learn Microsoft Office
- Apply for a job
- Improve my work skills
- Design nice-looking docs
- Getting Started
- Smartphones & Tablets
- Typing Tutorial
- Online Learning
- Basic Internet Skills
- Online Safety
- Social Media
- Zoom Basics
- Google Docs
- Google Sheets
- Career Planning
- Resume Writing
- Cover Letters
- Job Search and Networking
- Business Communication
- Entrepreneurship 101
- Careers without College
- Job Hunt for Today
- 3D Printing
- Freelancing 101
- Personal Finance
- Sharing Economy
- Decision-Making
- Graphic Design
- Photography
- Image Editing
- Learning WordPress
- Language Learning
- Critical Thinking
- For Educators
- Translations
- Staff Picks
- English expand_more expand_less
Computer Basics - Understanding Operating Systems
Computer basics -, understanding operating systems, computer basics understanding operating systems.

Computer Basics: Understanding Operating Systems
Lesson 8: understanding operating systems.
/en/computerbasics/mobile-devices/content/
What is an operating system?
An operating system is the most important software that runs on a computer. It manages the computer's memory and processes , as well as all of its software and hardware . It also allows you to communicate with the computer without knowing how to speak the computer's language. Without an operating system, a computer is useless .
Watch the video below to learn more about operating systems.
Looking for the old version of this video? You can still view it here .
The operating system's job
Your computer's operating system ( OS ) manages all of the software and hardware on the computer. Most of the time, there are several different computer programs running at the same time, and they all need to access your computer's central processing unit (CPU) , memory , and storage . The operating system coordinates all of this to make sure each program gets what it needs.
Types of operating systems
Operating systems usually come pre-loaded on any computer you buy. Most people use the operating system that comes with their computer, but it's possible to upgrade or even change operating systems. The three most common operating systems for personal computers are Microsoft Windows , macOS , and Linux .
Modern operating systems use a graphical user interface , or GUI (pronounced gooey ). A GUI lets you use your mouse to click icons , buttons , and menus , and everything is clearly displayed on the screen using a combination of graphics and text .

Each operating system's GUI has a different look and feel, so if you switch to a different operating system it may seem unfamiliar at first. However, modern operating systems are designed to be easy to use , and most of the basic principles are the same.
Microsoft Windows
Microsoft created the Windows operating system in the mid-1980s. There have been many different versions of Windows, but the most recent ones are Windows 10 (released in 2015), Windows 8 (2012), Windows 7 (2009), and Windows Vista (2007). Windows comes pre-loaded on most new PCs, which helps to make it the most popular operating system in the world.

Check out our tutorials on Windows Basics and specific Windows versions for more information.
macOS (previously called OS X ) is a line of operating systems created by Apple. It comes preloaded on all Macintosh computers, or Macs. Some of the specific versions include Mojave (released in 2018), High Sierra (2017), and Sierra (2016).
According to StatCounter Global Stats , macOS users account for less than 10% of global operating systems—much lower than the percentage of Windows users (more than 80% ). One reason for this is that Apple computers tend to be more expensive. However, many people do prefer the look and feel of macOS over Windows.
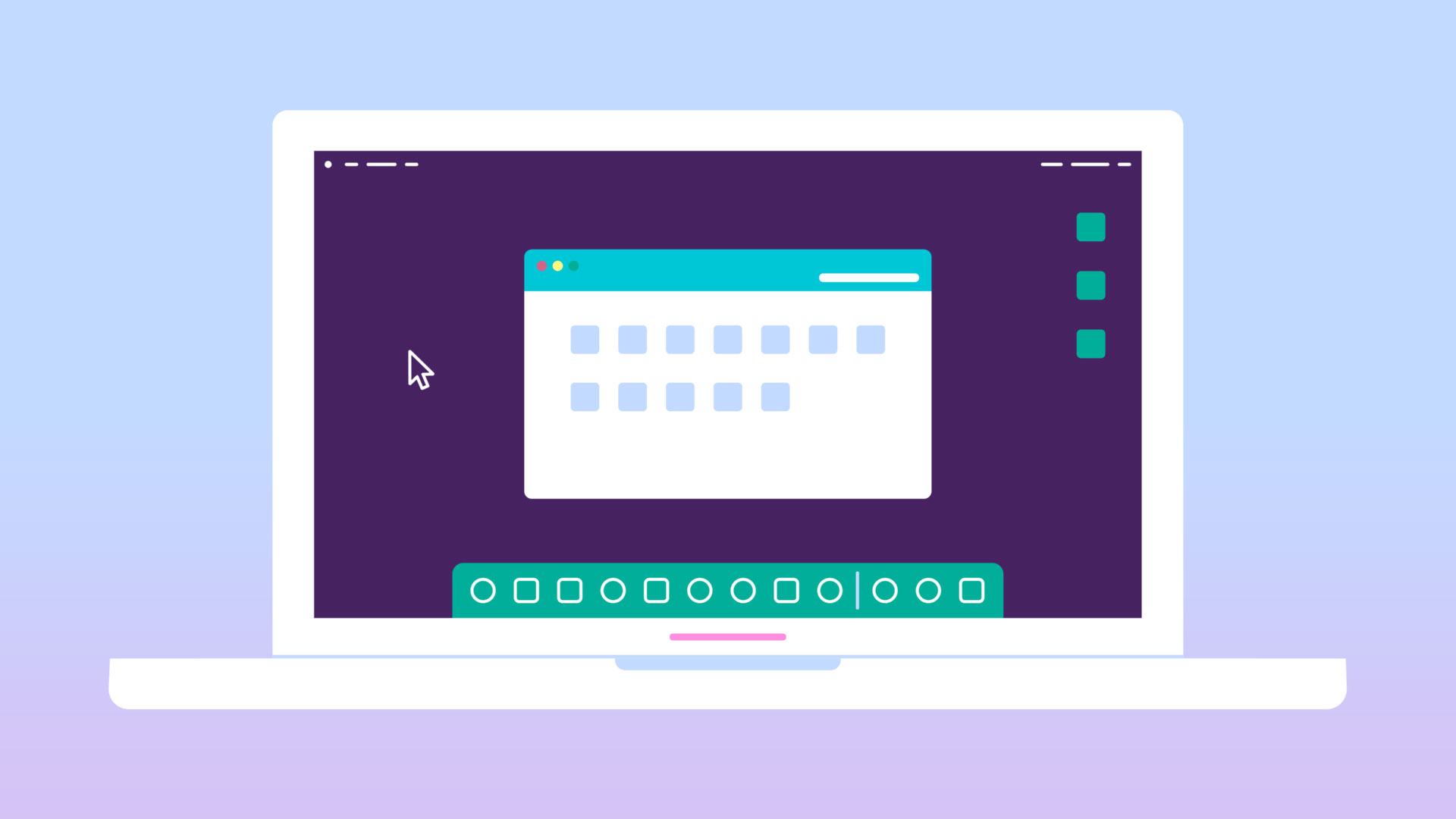
Check out our macOS Basics tutorial for more information.
Linux (pronounced LINN-ux ) is a family of open-source operating systems, which means they can be modified and distributed by anyone around the world. This is different from proprietary software like Windows, which can only be modified by the company that owns it. The advantages of Linux are that it is free , and there are many different distributions —or versions—you can choose from.
According to StatCounter Global Stats , Linux users account for less than 2% of global operating systems. However, most servers run Linux because it's relatively easy to customize.
To learn more about different distributions of Linux, visit the Ubuntu , Linux Mint , and Fedora websites, or refer to our Linux Resources . For a more comprehensive list, you can visit MakeUseOf's list of The Best Linux Distributions .
Operating systems for mobile devices
The operating systems we've been talking about so far were designed to run on desktop and laptop computers. Mobile devices such as phones , tablet computers , and MP3 players are different from desktop and laptop computers, so they run operating systems that are designed specifically for mobile devices. Examples of mobile operating systems include Apple iOS and Google Android . In the screenshot below, you can see iOS running on an iPad.
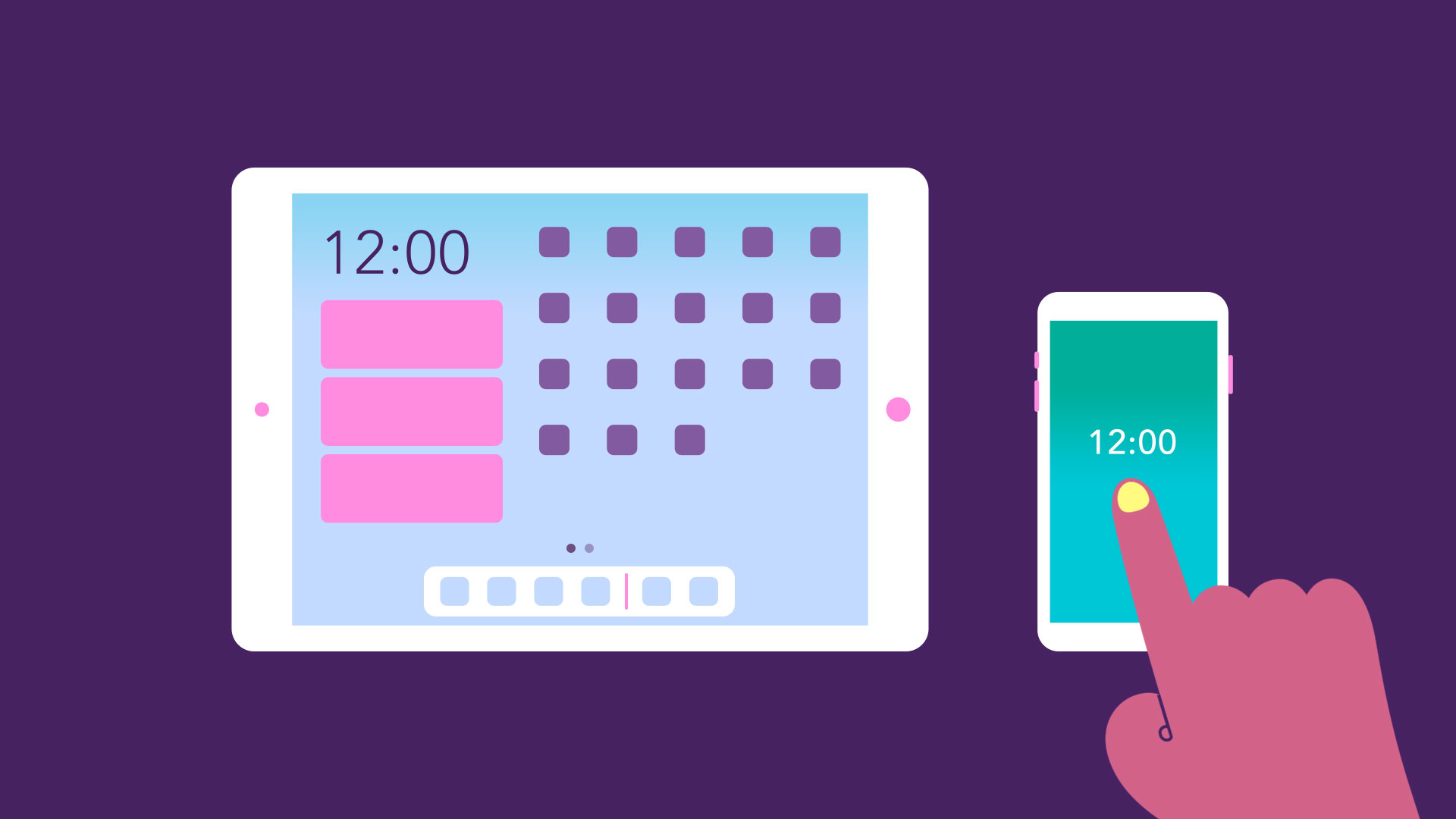
Operating systems for mobile devices generally aren't as fully featured as those made for desktop and laptop computers, and they aren't able to run all of the same software. However, you can still do a lot of things with them, like watch movies, browse the Web, manage your calendar, and play games.
To learn more about mobile operating systems, check out our Mobile Devices tutorials.
/en/computerbasics/understanding-applications/content/
> cs > cs.OS
Help | Advanced Search
Operating Systems
Authors and titles for recent submissions.
- Tue, 16 Apr 2024
- Fri, 5 Apr 2024
- Wed, 3 Apr 2024
- Tue, 2 Apr 2024
- Tue, 26 Mar 2024
Links to: arXiv , form interface , find , cs , new , 2404 , contact , h elp ( Access key information)

ESSAY SAUCE
FOR STUDENTS : ALL THE INGREDIENTS OF A GOOD ESSAY
Essay: Operating systems
Essay details and download:.
- Subject area(s): Information technology essays
- Reading time: 18 minutes
- Price: Free download
- Published: 18 March 2018*
- File format: Text
- Words: 5,351 (approx)
- Number of pages: 22 (approx)
Text preview of this essay:
This page of the essay has 5,351 words. Download the full version above.
At the most fundamental level, an operating system serves as an intermediary—that is, a middleman—between a computer user and computer hardware (Bower, 2015). It is an extensive and complicated group of system programs that oversees the many operations of a computer and handles the management of computer resources (Garrido, Schlesinger, & Hoganson, 2013). Furthermore, it is arguably the most important component of system software, because without an operating system, a computer is rendered inoperable (Goodwill Community Foundation, Inc., 2017).
An operating system plays a significant role in facilitating communication between humans and computers because it allows one to indirectly “speak” to them, despite not being fluent in machine language. This is made possible with the use of a user interface, such as a command line or a graphical user interface (GUI) that enables users to interact with a computer by clicking on an array of graphic objects that appear on the screen, such as icons, buttons, and menus (Goodwill Community Foundation, Inc., 2017). These interfaces allow the operating system to abstract out the smaller, more unnecessary details related to the computer’s underlying hardware. If operating systems did not exist, then one would need to know all of these details in order to make anything run (Wienand, 2016).
Aside from acting as a communication interface, operating systems also perform crucial functions such as ensuring system security. The operating system is in charge of controlling access to system resources, such as the central processing unit (CPU), memory, file storage, external devices, and network connections (Hemmendinger, 2017). In other words, it checks that only those with proper permissions can use system resources. For instance, if one file is owned by User 1, User 2 should not be permitted to open the file, read the file, or make changes to the file [4] .
Figure 1. The operating system acts as an intermediary between users and computer hardware (Bower, 2015)
The three most commonly used operating systems are Linux, Unix, and Windows [2]. This paper will concentrate its attention on the Mac operating system, macOS, a Unix-based operating system developed by Apple Inc. Before turning our focus to the technicalities of macOS, we will describe a timeline that charts the inception, growth, and development of the Mac operating system and outline its transformation over the years. Following this, we will present an overview of the architecture that makes up macOS and explore each of its components in detail. After, we will consider the advantages that macOS provides over other operating systems, as well as the tradeoffs that come with it. Finally, we will analyze the current direction of macOS and theorize about its future possible trajectories.
Early Beginnings
macOS has come quite a long way from where it began in 1984 when Steve Jobs released the first Macintosh computer on stage at a community college in Cupertino, California. Weighing in at 22 pounds and costing a whopping $2,500 (or $6,000 when adjusted for inflation), it was promised to be “the computer you know how to use.” At that time, the computer was unlike any other. Its pleasing GUI and ground-breaking design caused it to receive high praise from big names, such as Consumer Reports, despite the fact that it only had 128 kilobytes of memory (enough for just under nine pages) once the operating system was installed (Pierce, 2014).
Just one year after the first computer was released, Steve Jobs was forced to leave Apple and set out to create “the next big thing.” Job’s idea was to design what he called “the perfect research computer” (Singh, 2003). Jobs, joined by five previous Apple employees, spent the next three years bringing the idea to life. What resulted was named the NeXT Computer workstation, the first computer to include a digital signal processor. Its accompanying operating system was called NeXTSTEP.
NeXTSTEP went through a number of iterations over the next two years and was transformed into a powerful Objective-C operating system with a highly praised, postscript-based GUI. NeXTSTEP boasted many achievements, such as being the first platform on which a web browser was designed. Further down the road, NeXTSTEP evolved into OPENSTEP, a platform that would allow users to design their own versions of the operating system. The NeXT computer was eventually discontinued, but OPENSTEP would become the foundation for what is known today as macOS.
Around the height of NeXT’s success, Apple was furiously trying to compete with Microsoft Windows. They were in an all-out race to release something big before Windows 95 was made available to the public (Dormehl, 2015). They ultimately lost that race when Pink OS, Apple’s failed venture with IBM, was ended. In response to the loss, Apple went on a full-fledged advertising campaign mocking Windows 95. Apple employees would drive around with bumper stickers comparing the new release to a four-year-old Mac operating system. They even posted a massive ad in the Wall Street Journal mocking the new system.
Unfortunately, Apple’s campaign did not go quite as they had planned. Consumers were lined up around the block on the Windows 95 release day, a feat very uncommon to see in those days. Users loved the start menu and seemed to enjoy the bold, bright colors that Apple had made it a point to avoid in their interface. A then Apple employee, David Curbow, was quoted as saying, “We had this big crash course to make everything look sexier, to make it more colorful. I think it was the first realization that we were not just building computers for people. We were building things that would look good enough that you wanted to buy them” (Dormehl, 2015). To make matters worse, Internet Explorer, which would soon become the first web browser for many, was released afterwards. It was clear that something had to be done to regain a competitive edge. In 1997, NeXT was purchased by Apple and development on Mac OS X began (Patton, 1993).
In September of 2000, Apple released an official preview version of OS X for $30 with the intention of getting opinions from the public. This release greatly improved on the classic Mac OS and had many updated features, including the famous Aqua user interface and the Darwin core, meeting long standing user demand for “preemptive multitasking” and “protected memory.” New native applications were also included. Features that are well known today, such as TextEdit, Preview, QuickTime, and even a pre-iTunes MP3 player, all began there (Siracusa, 2004).
The first full version of Mac OS X, 10.0, called Cheetah, was made available in March of 2001, just two months before the beta trial ended. Despite such a positive beta test, OS X 10.0 received plenty of user criticism. Much of this criticism was focused on three main areas: (1) compatibility, (2) responsiveness, and (3) stability. With this first release, users were not able to burn CDs or play DVDs. Although the Aqua GUI was called beautiful, it lagged terribly and resulted in response times plummeting (McElhearn, Timeline of Key Features Added to Every Mac OS X Release to Date, 2016). Users were fast to point out all of the issues that they ran into, such as kernel panic, which caused computers to continually restart for no apparent reason (Kuziv, 2017). These complaints ultimately convinced Apple to give its users a free upgrade to the next version, 10.01, of Mac OS X (Orlowski, 2001).
Moving forward in time, Mac OS X Jaguar 10.2 was released in August of 2002. This would be the world’s first look at many of the Mac features that are seen today. Things like QuickTime, Contacts, and the native mail client were all rolled out during this time. This would a lso be the start of using Quartz Extre me for smooth graphics rendering and image processing (Apple Inc., 2002). Users embraced this iteration and seemed to be much happier with the improvements included.
Moving down the line, Apple continued with its trend of announcing yearly to bi-yearly operating systems releases, each named after a large cat. Panther, Tiger, Leopard, Snow Leopard, Lion, and Mountain Lion made up the full lineup until the release of OS X Mavericks 10.9, in June of 2013. Mavericks was the tenth significant release from the OS X line and introduced many features. Apple promised its users that there would be more than 200 changes. The front-runner was major improvements to system efficiency, which included the batch processing of more low-level functions. This change allowed the CPU to remain in power-saving mode for longer stretches of time, ultimately reducing CPU utilization by 72% and showing a massive gain in battery life (MacRumors.com, LLC, 2017).
Moving ahead in time, Apple adopted a new naming convention, using names of mountain ranges located in California. The introduction of OS X Yosemite 10.10, in June of 2014, completely overhauled the UI. Flat-like elements completely replaced the more 3D icons. The overall theme became much more resemblant of the current iOS look and feel. Moving down the line there is El Capitan and Sierra. Starting with Sierra 10.12 Apple made the bold decision to rename Mac OS X to macOS. Today we have High Sierra and a much more feature-rich interface. Sierra and High Sierra offer a much more mobile-like experience and huge new feature set. Siri can now be accessed and the computers can be unlocked instantly. with TouchID. Picture in picture videos have and integrated apple pay have both also become user favorites.( https://www.imore.com/macos-sierra) Insert closing sentence here
Architecture
The architecture of macOS consists of several layers: (1) the interface layer, (2) the applications layer, (3) the graphics layer, and (4) the core OS layer. An overview of these layers is given in Figure 3. Layers toward the top provide services that are “closer” to the user, whereas layers toward the bottom provide services that are “farther” from the user (Miser, 2004).
Figure 3. macOS architectural overview (Miser, 2004)
The Interface Layer
The interface layer, Aqua, is one of the first things that comes to mind for many Mac owners when they think of the “Mac Experience.” The UI, menus, Finder, Dock, as well as other key features are what primarily give the user the unique feeling of using a Mac. In most cases, this layer is all the user will ever really directly interact with (Landau, 2003). Aqua was originally designed to resemble a water-like theme; it incorporated a raindrop style with reflective and transparent components. Steve Jobs was quoted as saying that “one of the design goals was when you saw it you wanted to lick it” (Jobs, 2000).
Figure 4. The first version of the Aqua GUI
The Applications Layer
Below the interface layer is the application layer. This layer is comprised of four main environments: (1) the Classic Mac environment, (2) the Carbon environment, (3) the Cocoa environment, and (4) the Java 2 environment. The diversity of this layer greatly contributes to the robustness of macOS because it allows the operating system to be compatible with a wide variety of applications (Miser, 2004).
The primary purpose of the Mac Classic environment is to provide the operating system with a means to run legacy applications and programs that were written for previous versions of macOS. Because of this, literally thousands of applications that would otherwise be obsolete are still able to be utilized, and potentially improved, by making use of the configurable virtual memory of macOS. However, this feature is still not a perfect fix—running these legacy applications can cause graphic issues as well as reference errors due to the previous confusing files systems (Ray & Ray, 2003).
The Carbon environment is responsible for handling all OS X 8 and OS X 9 programs that have had their code optimized for current macOS compatibility (Sellers, 2001). By a process known as Carbonizing, it allows users to port older programs to make use of the Carbon application programming interface (API). Applications being run in this environment can take advantage of the benefits provided by Darwin, including “protected memory” and “preemptive multitasking.” One of the greatest things about Carbon is the amount of time that users save when they choose to Carbonize an application, rather than freshly rebuilding an updated version (Apple Inc., 2017).
Generally, when applications are designed for the current version of macOS, they are designed in the Cocoa environment. Cocoa makes use of object-oriented programming principles and is currently Apple’s native API (Gallagher, 2010). Many components of the applications built in this environment are highly automated in order to remain compliant with Apple’s “Human Interface Guidelines,” allowing them to make full use of the newest macOS features while simultaneously giving them a unique feel. Cocoa applications are rapidly becoming more and more predominant in the macOS world (Miller, 2017).
The final environment in the applications layer is the Java 2 environment. One of the primary draws of the Java 2 environment is that it gives users the ability to build entirely pure Java applications and applets using the Java development environment. Applications written in Java are some of the most common applications found on the web today. Because Java applications are so widespread, programming in the Java 2 environment provides a huge advantage over other alternatives because the resulting products will be cross-platform compatible (Zobkiw, 2003).
The Graphics Layer
The Mac operating system includes an advanced graphics layer, which has three main components: (1) Quartz Extreme, (2) OpenGL, and (3) QuickTime.
The first part of the graphics layer is known as Quartz Extreme. Quartz Extreme is responsible for handling the system’s 2D elements, such as interface graphics, fonts, and the rendering and antialiasing of images. If available, Quartz Extreme processes images using the system’s graphics card instead of using the machine’s CPU. This reduces the CPU load, effectively making the machine more responsive because it frees up the CPU to handle other processes. The engine driving Quartz Extreme is designed on top of the Acrobat Portable Format (PDF), a file format designed by Adobe Systems Incorporated. The text and graphics rendered in Quartz Extreme are crisp, clean, easily resized, and easily transferred between computers. Quartz Extreme allows the Mac operating system to display PDF files without using Adobe Acrobat Reader in Mac’s native Preview application (Chambers, 2012). The use of Quartz Extreme also eliminates the need for non-native font smoothing when working with PostScript fonts (Miser, 2004).
The second component of the graphics layer is OpenGL, an API that facilitates the use of 3D graphics. OpenGL is arguably the heart of the graphics system in macOS. Being an industry standard, OpenGL can take applications that were built to run on other operating systems, such as Windows and Unix, and more easily convert them to native macOS applications (Apple Inc., 2017). The Mac version of OpenGL gives users access to a wide variety of 3D graphics functions, such as texture mapping, transparency, antialiasing, atmospheric effects, and other special effects (Miser, 2004).
The final part of the graphics layer is QuickTime, a multimedia framework that handles a wide array of media formats on macOS, such as video, sound, animation, graphics, text, interactivity, and mus ic (Apple Inc., 2017).
The Core OS Laye r
One of the most distinctive characteristics of macOS is the core on which it is built upon. The operating system is structured around a Unix core named Darwin, which was modeled after the Berkeley Software Distribution (BSD) Unix version. Darwin is the primary facilitator of all I/O services for macOS allowing modern features like “plug and play” and “hot swapping.” Surprisingly, the code for Darwin is free to use for anyone without any special permissions.
At the heart of Darwin is a component called Mach. Mach is responsible for performing critical system operations. Mach that a unique space in memory is allocated each application. As a result, unexpected application freezes or shut-downs will not affect other running applications. Mach is in-charge of managing random access memory. This takes the burden of having to worry about memory usage off of the user, a welcomed change from Mac OS 9 and earlier. A third primary function of Mach is managing the CPU processes making sure that each application has the needed resources as well as the CPU running efficiently overall. (http://www.informit.com/articles/article.aspx?p=1552774).
Advantages, Disadvantages, and Future Possibilities
Apple supporters might claim that their MacBook laptops or Mac desktop computers eclipse other operating systems due to the logical synthesis of macOS and state-of-the-art hardware specifications. Meanwhile, Apple cynics may contend that the Mac operating system is markedly limited when compared to others, such as Windows, or that it is too costly a product (Bonheur, 2016). In truth, all operating systems come with their share of advantages and disadvantages, and macOS is no exception. macOS has numerous benefits that make it more attractive than other operating systems, in addition to shortcomings that may make other operating systems appear to be better options.
One of the strongest advantages of macOS lies in its advanced security technology. Part of the reason why macOS is so secure is because it is built on a Unix core—antivirus software is largely unnecessary on macOS devices because destructive software cannot be installed unless the user explicitly gives root access, that is, administrative privileges, to the harmful programs (Carson, 2011). macOS also offers many security features that keep its users and their data safe (McElhearn, OS X Security: Under the Hood Features That Protect Your Mac, 2016). For instance, Gatekeeper, a feature introduced in Mountain Lion and OS X Lion v10.7.5, makes it safer to download applications by putting additional checks in place to guard against malicious software, or malware, that users may unintentionally stumble upon (Apple Inc., 2017). It uses a process called code signing to verify the authenticity of an application’s publisher (McElhearn, OS X Security: Under the Hood Features That Protect Your Mac, 2016). iCloud Keychain, another helpful security feature, makes it easier for users to visit websites that require login credentials because it safely stores and encrypts account names, usernames, passwords, or credit card information that the user saves. This information is kept up-to-date and is synced across all of the user’s Apple devices (Apple Inc., 2017).
Ease-of-use is another trait that makes macOS advantageous. The Mac operating system offers an appealing and intuitive GUI that is somewhat similar to the GUI found in other Apple products, such as the iPhone and the iPad. Those who are familiar with iOS devices will find that navigating the user workflow of macOS in a desktop environment to be quite simple and straightforward (Bonheur, 2016). The logical organization of macOS makes for a very user-friendly interface. Even those unfamiliar with iOS devices will find that such a process is clear-cut, due to things being where one expects them to be (Miser, 2004).
An extension of macOS’ ease-of-use is the fact that it comes pre-stocked with useful applications, such as Pages, Numbers, and Keynote, the web browser Safari, the email client Mail, and communication apps such as Messages and FaceTime. For creative-minded professionals, Apple includes the photo-editing app iPhoto, the video-editing app iMovie, and the music-production app GarageBand (Bonheur, 2016). Figure 5 shows Launchpad, the application launcher in macOS Sierra, where all of these applications can be started (Apple Inc., 2017).
Perhaps one of the most compelling advantages of macOS in relation to other operating systems is its seamless integration with other Apple products (Bonheur, 2016). macOS will automatically recognize other Apple devices (Carson, 2011). Only individuals with several Apple devices can enjoy the benefit of painless data and information synchronization across multiple devices, without the need to use cloud-based drives such as OneDrive or Google Drive (Bonheur, 2016).
Figure 5. macOS Sierra application launcher (Apple Inc., 2017)
Although macOS may provide many enticing advantages over other operating systems, it is not without its drawbacks. Perhaps one of the most frequently cited reasons to use an operating system other than macOS is the steep price tag placed on Apple products. The only way to legally obtain legitimate macOS software is to purchase a Mac computer (Bonheur, 2016). Macs are expensive computers, with the latest iMacs, MacBooks, and MacBook Pros costing upwards of $1,300. A 15-inch MacBook Pro with 512 gigabytes (GB) of storage will set one back $2,799, for instance (Apple Inc., 2017).
Another significant disadvantage to macOS is its inflexibility with regards to hardware upgrades. With Windows computers, users can design and tailor their builds to their preferences and upgrade specific hardware parts whenever desired. However, most Mac computers cannot be upgraded effortlessly due to the integration of the Mac’s hardware components at the design and engineering levels (Bonheur, 2016). For those who enjoy tinkering with computers as a hobby, or for those who wish to lengthen the lifespan of their PC, this is somewhat disheartening and oftentimes a deal breaker when it comes to selecting an operating system. It is the same scenario for those who enjoy playing video games: gamers generally want the ability to easily upgrade hardware components so that they can keep up with and adapt to ever-changing game requirements.
Some users may also feel rather constrained by the fact that there are fewer software options available for macOS than there are for other operating systems, such as Windows (Carson, 2011). That is, macOS has a smaller application ecosystem, even though the gap is beginning to close. Many software developers may opt to develop for Windows before macOS in order to reach a larger audience (Bonheur, 2016). This is especially true when it comes to the highly specialized, harder-to-source software that is often found in industry-specific applications or at small and/or independent companies (Carson, 2011). For instance, there are fewer video game titles available for macOS than there are for Windows, although there has been a push more recently for greater support for gaming on macOS and Linux.
Despite Windows’ position as the most prominent and accessible desktop operating system in the world, Apple’s macOS has gained a significant following in recent years. Figure 6 and Figure 7 illustrate the results of an annual survey conducted by Stack Overflow about developers’ desktop operating system preferences. In 2016, although Windows operating systems as a whole prevailed with 52.2 percent of developers’ votes, macOS rose to 26.2 percent from its previous 18.7 percent in 2013, illustrating its progressively rising influence among web developers (Stack Exchange, Inc., 2017). It would not be surprising if this trend continued.
Figure 6. Stack Overflow’ s Web Developer Survey Results (2016) – Desktop Operating System preferences (Stack Exchange, Inc., 2017)
Figure 7. Stack Overflow’s Web Developer Survey Results (2013) – Desktop Operating System preferences (Stack Exchange, Inc., 2017)
Beyond developer preferences, what does the future hold in store for macOS? Some believe that Apple’s iOS will ultimately replace macOS. Others, like programmer Steven Troughton-Smith, wouldn’t’ be surprised if Apple were to consolidate iOS and macOS into something new: “We’re far enough into the age of mobile that the big players are designing the OSes that’ll follow it—surprised if Apple isn’t doing the same. It’s not so crazy to think that Apple would want to replace both iOS and macOS with something new and more unified” (Snell, 2017).
[CONTENT here.]
Apple Inc. (2002, July 17). Apple Introduces “Jaguar,” the Next Major Release of Mac OS X. (Apple Inc.) Retrieved November 18, 2017, from https://www.apple.com/newsroom/2002/07/17Apple-Introduces-Jaguar-the-Next-Major-Release-of-Mac-OS-X/
Apple Inc. (2017). Carbon Accessibility. (Apple Inc.) Retrieved November 18, 2017, from https://developer.apple.com/documentation/applicationservices/carbon_accessibility
Apple Inc. (2017, November 17). Frequently Asked Questions About iCloud Keychain. (Apple Inc.) Retrieved November 18, 2017, from https://support.apple.com/en-us/HT204085
Apple Inc. (2017). MacBook Pro. (Apple Inc.) Retrieved November 19, 2017, from https://www.apple.com/shop/buy-mac/macbook-pro/15-inch
Apple Inc. (2017, March 29). macOS Sierra: Use Launchpad to View and Open Apps. (Apple Inc.) Retrieved November 18, 2017, from https://support.apple.com/kb/PH25704?viewlocale=en_OM&locale=en_OM
Apple Inc. (2017). OpenGL for macOS. (Apple Inc.) Retrieved November 18, 2017, from https://developer.apple.com/opengl/
Apple Inc. (2017). OS X: About Gatekeeper. (Apple Inc.) Retrieved November 18, 2017, from https://support.apple.com/en-us/HT202491
Apple Inc. (2017). What Is QuickTime? (Apple Inc.) Retrieved November 18, 2017, from https://documentation.apple.com/en/finalcutpro/usermanual/index.html#chapter=103%26section=1%26tasks=true
Bonheur, K. (2016, October 22). Advantages and Disadvantages of macOS. (Version Daily) Retrieved November 17, 2017, from http://www.versiondaily.com/advantages-disadvantages-mac-os-x/
Bower, T. (2015). Operating Systems Study Guide. Retrieved November 19, 2017, from http://faculty.salina.k-state.edu/tim/ossg/index.html
Carson, A. (2011, May 24). What Are the Advantages and Disadvantages of Mac OS? (Bright Hub) Retrieved November 18, 2017, from http://www.brighthub.com/computing/mac-platform/articles/73326.aspx
Chambers, M. L. (2012). OS X Mountain Lion All-in-One For Dummies. Hoboken: John Wiley & Sons, Inc.
Dormehl, L. (2015, August 24). How Apple Responded to the Release of Windows 95, 20 years Ago Today. (Cult of Mac) Retrieved November 19, 2017, from https://www.cultofmac.com/386189/how-apple-responded-to-the-release-of-windows-95-twenty-years-ago-today/
Gallagher, M. (2010, June 22). The Design of Every Mac Application. Retrieved November 18, 2017, from https://www.cocoawithlove.com/2010/06/design-of-every-mac-application.html
Garrido, J., Schlesinger, R., & Hoganson, K. (2013). Principles of Modern Operating Systems. Burlington: Jones & Bartlett Learning, LLC.
Goodwill Community Foundation, Inc. (2017). Computer Basics: Understanding Operating Systems. (Goodwill Community Foundation, Inc.) Retrieved November 15, 2017, from https://www.gcflearnfree.org/computerbasics/understanding-operating-systems/1/
Hemmendinger, D. (2017, August 28). Operating system (OS). (Encyclopædia Britannica, Inc.) Retrieved November 15, 2017, from https://www.britannica.com/technology/operating-system
Jobs, S. (2000). Macworld San Francisco 2000 – The Mac OS X Introduction (Pt.1).
Kuziv, I. (2017, July 28). What is a Kernel Panic on Mac and How to Fix it? (MacPaw Inc.) Retrieved November 19, 2017, from https://macpaw.com/how-to/fix-kernel-panic-on-macos
Landau, T. (2003, May 9). Understanding Mac OS X: In Depth. (Pearson Education, Peachpit) Retrieved November 18, 2017, from http://www.peachpit.com/articles/article.aspx?p=31702
MacRumors.com, LLC. (2017). Mavericks. (MacRumors.com, LLC) Retrieved November 19, 2017, from https://www.macrumors.com/roundup/os-x-mavericks/
McElhearn, K. (2016, February 22). OS X Security: Under the Hood Features That Protect Your Mac. (Intego) Retrieved November 18, 2017, from https://www.intego.com/mac-security-blog/os-x-security-under-the-hood-features-that-protect-your-mac/
McElhearn, K. (2016, February 18). Timeline of Key Features Added to Every Mac OS X Release to Date. (Intego) Retrieved November 18, 2017, from https://www.intego.com/mac-security-blog/timeline-of-key-features-added-to-every-mac-os-x-release-to-date/
Miller, C. (2017, August 29). Apple Shares Detailed Human Interface Guidelines for Developers Building ARKit Apps. (9to5Mac) Retrieved November 18, 2017, from https://9to5mac.com/2017/08/29/arkit-human-interface-guidelines/
Miser, B. (2004). Special Edition Using Mac OS X, v10.3 Panther. Que. Retrieved November 18, 2017, from http://etutorials.org/Mac+OS/using+mac+os+x+v10.3+panther/Part+I+Mac+OS+X+Exploring+the+Core/Chapter+1.+Mac+OS+X+Foundations/Mac+OS+X+Benefits/
Orlowski, A. (2001, September 26). Mac Loyalists Get Free OS X 10.1 Upgrade. (The Register) Retrieved November 17, 2017, from https://www.theregister.co.uk/2001/09/26/mac_loyalists_get_free_os/
Patton, P. (1993, June 1). Steve Jobs and the Next Big Thing. (Wired) Retrieved November 18, 2017, from https://www.wired.com/1993/06/steve-jobs-and-the-next-big-thing/
Pierce, D. (2014, January 24). The Mac Turns 30: A Visual History. (The Verge) Retrieved November 18, 2017, from https://www.theverge.com/2014/1/24/5340320/the-mac-turns-30-a-visual-history
Ray, J., & Ray, W. C. (2003, January 10). Running Classic Mac OS Applications. (Pearson Education, Informit) Retrieved November 18, 2017, from http://www.informit.com/articles/article.aspx?p=30485
Sellers, D. (2001, January 4). Road to Mac OS X: Carbon versus Cocoa. (IDG Communications, Inc.) Retrieved November 18, 2017, from https://www.macworld.com/article/1021535/macosx.html
Singh, A. (2003, December). What is Mac OS X? Retrieved November 19, 2017, from http://osxbook.com/book/bonus/ancient/whatismacosx/history.html
Siracusa, J. (2004). Mac OS X Public Beta. (Ars Technica, LLC) Retrieved November 18, 2017, from http://archive.arstechnica.com/reviews/4q00/macosx-pb1/macos-x-beta-1.html
Snell, J. (2017, August 25). iOS and macOS: What Does the Future Hold? (IDG Communications, Inc.) Retrieved November 18, 2017, from https://www.macworld.com/article/3219695/ios/future-of-ios-and-macos.html
Stack Exchange, Inc. (2017). Stack Overflow Developer Survey 2016 Results. (Stack Exchange, Inc.) Retrieved November 17, 2017, from https://insights.stackoverflow.com/survey/2016#technology-desktop-operating-system
Wienand, I. (2016). Computer Science from the Bottom Up. Retrieved November 14, 2017, from https://www.bottomupcs.com/chapter03.xhtml
Zobkiw, J. (2003). Mac OS X: Advanced Development Techniques. Indianapolis: Sams Publishing.
API: a set of commands, functions, protocols, and objects that programmers can use to create software; it provides developers wi th standard commands for performing common operations so that they do not have to write code from scra tch
Application programming interface (API): a set of commands, functions, protocols, and objects that programmers can use to create software; provides developers with standard commands for performing common operations so that they do not have to write code from scratch
Central processing unit (CPU): the primary component of a computer that processes instructions; it runs the operating system and applications, constantly receiving input from the user or active software programs; it processes the data and produces output, which may be stored by an application or displayed on the screen
Code signing: the method of using a certificate-based digital signature to sign executables and scripts in order to verify an author’s identity and ensure that code has not been changed or corrupted since it was signed by the author; helps users and other software determine whether the software can be trusted
CPU: the primary component of a computer that processes instructions; it runs the operating system and applications, constantly receiving input from the user or active software programs; it processes the data and produces output, which may be stored by an application or displayed on the screen
Gatekeeper: a security feature of the macOS operating system by Apple that enforces code signing and verifies downloaded applications before allowing them to run, thereby reducing the likelihood of inadvertently executing malware
Graphical user interface (GUI): a type of user interface that allows users to interact with electronic devices through graphic icons and visual indicators, instead of text-based user interfaces, typed command labels, or text navigation
GUI: a type of user interface that allows users to interact with electronic devices through graphic icons and visual indicators, instead of text-based user interfaces, typed command labels, or text navigation
iCloud Keychain: a security feature of the macOS operating system that keeps a user’s Safari website usernames and passwords, credit card information, and Wi-Fi network information up to date across all approved devices
Kernel panic: a safety measure taken by an operating system’s kernel upon detecting an internal fatal error from which it cannot safely recover from, or where the system cannot continue to run without risking major data loss
Machine language:
Malicious software (“malware”): an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs
Malware: an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs
Operating system:
Root: refers to the top-level directory of a file system; the username or account that, by default, has access to all commands and files on a Linux or other Unix-like operating system
Unix: a popular multi-user, multitasking operating system developed at Bell Labs in the early 1970s; it was designed for flexibility and adaptability; it has become a leading operating system for workstations, but historically has been less popular in the personal computer market
Biographies
Ali Amin is a senior pursuing a degree in Information Systems at the University of North Florida. He is expected to graduate in Fall 2018. Ali is currently living in Jacksonville, Florida.
Katie Grubbs is a senior pursuing a degree in Information Science at the University of North Florida. She is expected to graduate in Summer or Fall 2018. Katie currently lives in St. Johns, Florida, but has lived in quite a few other places (including Japan) due to her family’s military background. In Summer 2017, she interned at APPX Software, Inc. as a business application developer. She is currently in the midst of senior project and hopes to obtain a position with a software development company upon graduation.
Daniel Lee is a junior pursuing a degree in Information Systems at the University of North Florida. He is expected to graduate in Summer or Fall 2019. Daniel currently lives in Middleburg, Florida.
Matthew Ramsay is a senior at the University of North Florida. Upon graduating, he will have earned a Bachelor’s of Business Administration with a concentration in Accounting, as well as a Bachelor’s of Science with a concentration in Computer and Information Science. Matthew is an active member of his community and takes the time to help others whenever possible. In his free moments, Matthew enjoys spending time in nature and striving to maintain a healthy lifestyle. Aside from school, Matthew is a candidate engineer at feature[23], a local consulting/software-engineering firm that focuses on innovation in the software industry. Matthew plans to graduate in Summer 2018.
• check for consistent use of abbreviations vs full words, such as:
...(download the rest of the essay above)
About this essay:
If you use part of this page in your own work, you need to provide a citation, as follows:
Essay Sauce, Operating systems . Available from:<https://www.essaysauce.com/information-technology-essays/operating-systems/> [Accessed 12-04-24].
These Information technology essays have been submitted to us by students in order to help you with your studies.
* This essay may have been previously published on Essay.uk.com at an earlier date.
Essay Categories:
- Accounting essays
- Architecture essays
- Business essays
- Computer science essays
- Criminology essays
- Economics essays
- Education essays
- Engineering essays
- English language essays
- Environmental studies essays
- Essay examples
- Finance essays
- Geography essays
- Health essays
- History essays
- Hospitality and tourism essays
- Human rights essays
- Information technology essays
- International relations
- Leadership essays
- Linguistics essays
- Literature essays
- Management essays
- Marketing essays
- Mathematics essays
- Media essays
- Medicine essays
- Military essays
- Miscellaneous essays
- Music Essays
- Nursing essays
- Philosophy essays
- Photography and arts essays
- Politics essays
- Project management essays
- Psychology essays
- Religious studies and theology essays
- Sample essays
- Science essays
- Social work essays
- Sociology essays
- Sports essays
- Types of essay
- Zoology essays
- / Technology
Computer Operating System
By: Jack • Essay • 961 Words • December 13, 2008 • 2,119 Views
Essay title: Computer Operating System
Introduction
An operating system (OS) is a program that acts an intermediary between a user of a computer and the computer hardware. The purpose of an operating system is to provide an environment in which a user can execute programs. The main purpose of an operating is to make the computer system convenient to use and user can the computer hardware in an efficient manner. An operating system is similar to a government. The components of a computer system are its hardware, software, and data. The operating system provides the means for the proper use of these resources in the operating system. Like a government, the operating system performs no useful function by itself. It simply provides an environment within which other programs can do useful work.
The Operating System With Advantages and Disadvantages
Nowadays, most of the computers are using the Windows OS as their operating system. Microsoft-designed computer operating system, a program that controls the basic functions of personal computers.
Windows started life as Microsoft's take on a graphical user interface (GUI). Windows 3.0, Windows 3.1, and Windows 3.11 were the three earliest versions of Microsoft's Windows operating system. Windows 95 is a major upgrade to Windows 3.1. This operating system is a true operating system and not an operating environment as were the 3.x version of Windows. Windows 95 does not require a separate version of DOS, although some DOS features are included for compatibility. One advantage of Windows 95 is its improved graphical user interface, which makes working with files and programs easier than earlier versions. Another advantage of Windows 95 is most programs run faster under it because it is written to take advantage of newer 32-bit processors and supports cooperative multitasking. Window 95 includes support for peer-to-peer networking and e-mail. Windows 95 does not include the tools for developing Internet Web pages and operating Web page server.
After some time, Microsoft came out with another operating system to upgrade Windows 95 - which named as Windows 98. Windows 98 is able to provide faster system startup and shutdown, better file management, support for few multimedia technologies such as digital video disk (DVD) and Web TV. Windows 98's Internet integration allows for automatic delivery of Web pages to your computer and an optional Web page-like user interface. Like Windows 95, Windows 98 can run 16 and 32 bit software, which means it can run software designed for DOS and other versions of Windows. Windows 98 comes with excellent online help specifically designed to troubleshoot gaffe with your hardware, operating system, and applications. It's called the Windows 98 Resource Kit Plus Tools Ampler. There are some disadvantages for Windows 98, it is easier for trashing or what we call hang compare to Windows 95.
Microsoft's Windows NT (for new technology), also referred to as NT, is a sophisticated graphical user interface operating system designed for client-server networks. Windows NT is a complete operating system but not an operating
- MLA 7
- CHICAGO
(2008, 12). Computer Operating System. EssaysForStudent.com . Retrieved 12, 2008, from https://www.essaysforstudent.com/essays/Computer-Operating-System/154.html
"Computer Operating System" EssaysForStudent.com . 12 2008. 2008. 12 2008 <https://www.essaysforstudent.com/essays/Computer-Operating-System/154.html>.
"Computer Operating System." EssaysForStudent.com . EssaysForStudent.com, 12 2008. Web. 12 2008. <https://www.essaysforstudent.com/essays/Computer-Operating-System/154.html>.
"Computer Operating System." EssaysForStudent.com. 12, 2008. Accessed 12, 2008. https://www.essaysforstudent.com/essays/Computer-Operating-System/154.html.
Essay on Computer and its Uses for School Students and Children
500+ words essay on computer.
In this essay on computer, we are going to discuss some useful things about computers. The modern-day computer has become an important part of our daily life. Also, their usage has increased much fold during the last decade. Nowadays, they use the computer in every office whether private or government. Mankind is using computers for over many decades now. Also, they are used in many fields like agriculture, designing, machinery making, defense and many more. Above all, they have revolutionized the whole world.

History of Computers
It is very difficult to find the exact origin of computers. But according to some experts computer exists at the time of world war-II. Also, at that time they were used for keeping data. But, it was for only government use and not for public use. Above all, in the beginning, the computer was a very large and heavy machine.
Working of a Computer
The computer runs on a three-step cycle namely input, process, and output. Also, the computer follows this cycle in every process it was asked to do. In simple words, the process can be explained in this way. The data which we feed into the computer is input, the work CPU do is process and the result which the computer give is output.
Components and Types of Computer
The simple computer basically consists of CPU, monitor, mouse, and keyboard . Also, there are hundreds of other computer parts that can be attached to it. These other parts include a printer, laser pen, scanner , etc.
The computer is categorized into many different types like supercomputers, mainframes, personal computers (desktop), PDAs, laptop, etc. The mobile phone is also a type of computer because it fulfills all the criteria of being a computer.
Get the huge list of more than 500 Essay Topics and Ideas
Uses of Computer in Various Fields
As the usage of computer increased it became a necessity for almost every field to use computers for their operations. Also, they have made working and sorting things easier. Below we are mentioning some of the important fields that use a computer in their daily operation.
Medical Field
They use computers to diagnose diseases, run tests and for finding the cure for deadly diseases . Also, they are able to find a cure for many diseases because of computers.
Whether it’s scientific research, space research or any social research computers help in all of them. Also, due to them, we are able to keep a check on the environment , space, and society. Space research helped us to explore the galaxies. While scientific research has helped us to locate resources and various other useful resources from the earth.
For any country, his defence is most important for the safety and security of its people. Also, computer in this field helps the country’s security agencies to detect a threat which can be harmful in the future. Above all the defense industry use them to keep surveillance on our enemy.
Threats from a Computer
Computers have become a necessity also, they have become a threat too. This is due to hackers who steal your private data and leak them on internet. Also, anyone can access this data. Apart from that, there are other threats like viruses, spams, bug and many other problems.

The computer is a very important machine that has become a useful part of our life. Also, the computers have twin-faces on one side it’s a boon and on the other side, it’s a bane. Its uses completely depend upon you. Apart from that, a day in the future will come when human civilization won’t be able to survive without computers as we depend on them too much. Till now it is a great discovery of mankind that has helped in saving thousands and millions of lives.
Frequently Asked Questions on Computer
Q.1 What is a computer?
A.1 A computer is an electronic device or machine that makes our work easier. Also, they help us in many ways.
Q.2 Mention various fields where computers are used?
A.2 Computers are majorly used in defense, medicine, and for research purposes.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

- MyU : For Students, Faculty, and Staff
Fall 2024 CSCI Special Topics Courses
Cloud computing.
Meeting Time: 09:45 AM‑11:00 AM TTh Instructor: Ali Anwar Course Description: Cloud computing serves many large-scale applications ranging from search engines like Google to social networking websites like Facebook to online stores like Amazon. More recently, cloud computing has emerged as an essential technology to enable emerging fields such as Artificial Intelligence (AI), the Internet of Things (IoT), and Machine Learning. The exponential growth of data availability and demands for security and speed has made the cloud computing paradigm necessary for reliable, financially economical, and scalable computation. The dynamicity and flexibility of Cloud computing have opened up many new forms of deploying applications on infrastructure that cloud service providers offer, such as renting of computation resources and serverless computing. This course will cover the fundamentals of cloud services management and cloud software development, including but not limited to design patterns, application programming interfaces, and underlying middleware technologies. More specifically, we will cover the topics of cloud computing service models, data centers resource management, task scheduling, resource virtualization, SLAs, cloud security, software defined networks and storage, cloud storage, and programming models. We will also discuss data center design and management strategies, which enable the economic and technological benefits of cloud computing. Lastly, we will study cloud storage concepts like data distribution, durability, consistency, and redundancy. Registration Prerequisites: CS upper div, CompE upper div., EE upper div., EE grad, ITI upper div., Univ. honors student, or dept. permission; no cr for grads in CSci. Complete the following Google form to request a permission number from the instructor ( https://forms.gle/6BvbUwEkBK41tPJ17 ).
CSCI 5980/8980
Machine learning for healthcare: concepts and applications.
Meeting Time: 11:15 AM‑12:30 PM TTh Instructor: Yogatheesan Varatharajah Course Description: Machine Learning is transforming healthcare. This course will introduce students to a range of healthcare problems that can be tackled using machine learning, different health data modalities, relevant machine learning paradigms, and the unique challenges presented by healthcare applications. Applications we will cover include risk stratification, disease progression modeling, precision medicine, diagnosis, prognosis, subtype discovery, and improving clinical workflows. We will also cover research topics such as explainability, causality, trust, robustness, and fairness.
Registration Prerequisites: CSCI 5521 or equivalent. Complete the following Google form to request a permission number from the instructor ( https://forms.gle/z8X9pVZfCWMpQQ6o6 ).
Visualization with AI
Meeting Time: 04:00 PM‑05:15 PM TTh Instructor: Qianwen Wang Course Description: This course aims to investigate how visualization techniques and AI technologies work together to enhance understanding, insights, or outcomes.
This is a seminar style course consisting of lectures, paper presentation, and interactive discussion of the selected papers. Students will also work on a group project where they propose a research idea, survey related studies, and present initial results.
This course will cover the application of visualization to better understand AI models and data, and the use of AI to improve visualization processes. Readings for the course cover papers from the top venues of AI, Visualization, and HCI, topics including AI explainability, reliability, and Human-AI collaboration. This course is designed for PhD students, Masters students, and advanced undergraduates who want to dig into research.
Registration Prerequisites: Complete the following Google form to request a permission number from the instructor ( https://forms.gle/YTF5EZFUbQRJhHBYA ). Although the class is primarily intended for PhD students, motivated juniors/seniors and MS students who are interested in this topic are welcome to apply, ensuring they detail their qualifications for the course.
Visualizations for Intelligent AR Systems
Meeting Time: 04:00 PM‑05:15 PM MW Instructor: Zhu-Tian Chen Course Description: This course aims to explore the role of Data Visualization as a pivotal interface for enhancing human-data and human-AI interactions within Augmented Reality (AR) systems, thereby transforming a broad spectrum of activities in both professional and daily contexts. Structured as a seminar, the course consists of two main components: the theoretical and conceptual foundations delivered through lectures, paper readings, and discussions; and the hands-on experience gained through small assignments and group projects. This class is designed to be highly interactive, and AR devices will be provided to facilitate hands-on learning. Participants will have the opportunity to experience AR systems, develop cutting-edge AR interfaces, explore AI integration, and apply human-centric design principles. The course is designed to advance students' technical skills in AR and AI, as well as their understanding of how these technologies can be leveraged to enrich human experiences across various domains. Students will be encouraged to create innovative projects with the potential for submission to research conferences.
Registration Prerequisites: Complete the following Google form to request a permission number from the instructor ( https://forms.gle/Y81FGaJivoqMQYtq5 ). Students are expected to have a solid foundation in either data visualization, computer graphics, computer vision, or HCI. Having expertise in all would be perfect! However, a robust interest and eagerness to delve into these subjects can be equally valuable, even though it means you need to learn some basic concepts independently.
Sustainable Computing: A Systems View
Meeting Time: 09:45 AM‑11:00 AM Instructor: Abhishek Chandra Course Description: In recent years, there has been a dramatic increase in the pervasiveness, scale, and distribution of computing infrastructure: ranging from cloud, HPC systems, and data centers to edge computing and pervasive computing in the form of micro-data centers, mobile phones, sensors, and IoT devices embedded in the environment around us. The growing amount of computing, storage, and networking demand leads to increased energy usage, carbon emissions, and natural resource consumption. To reduce their environmental impact, there is a growing need to make computing systems sustainable. In this course, we will examine sustainable computing from a systems perspective. We will examine a number of questions: • How can we design and build sustainable computing systems? • How can we manage resources efficiently? • What system software and algorithms can reduce computational needs? Topics of interest would include: • Sustainable system design and architectures • Sustainability-aware systems software and management • Sustainability in large-scale distributed computing (clouds, data centers, HPC) • Sustainability in dispersed computing (edge, mobile computing, sensors/IoT)
Registration Prerequisites: This course is targeted towards students with a strong interest in computer systems (Operating Systems, Distributed Systems, Networking, Databases, etc.). Background in Operating Systems (Equivalent of CSCI 5103) and basic understanding of Computer Networking (Equivalent of CSCI 4211) is required.
- Future undergraduate students
- Future transfer students
- Future graduate students
- Future international students
- Diversity and Inclusion Opportunities
- Learn abroad
- Living Learning Communities
- Mentor programs
- Programs for women
- Student groups
- Visit, Apply & Next Steps
- Information for current students
- Departments and majors overview
- Departments
- Undergraduate majors
- Graduate programs
- Integrated Degree Programs
- Additional degree-granting programs
- Online learning
- Academic Advising overview
- Academic Advising FAQ
- Academic Advising Blog
- Appointments and drop-ins
- Academic support
- Commencement
- Four-year plans
- Honors advising
- Policies, procedures, and forms
- Career Services overview
- Resumes and cover letters
- Jobs and internships
- Interviews and job offers
- CSE Career Fair
- Major and career exploration
- Graduate school
- Collegiate Life overview
- Scholarships
- Diversity & Inclusivity Alliance
- Anderson Student Innovation Labs
- Information for alumni
- Get engaged with CSE
- Upcoming events
- CSE Alumni Society Board
- Alumni volunteer interest form
- Golden Medallion Society Reunion
- 50-Year Reunion
- Alumni honors and awards
- Outstanding Achievement
- Alumni Service
- Distinguished Leadership
- Honorary Doctorate Degrees
- Nobel Laureates
- Alumni resources
- Alumni career resources
- Alumni news outlets
- CSE branded clothing
- International alumni resources
- Inventing Tomorrow magazine
- Update your info
- CSE giving overview
- Why give to CSE?
- College priorities
- Give online now
- External relations
- Giving priorities
- Donor stories
- Impact of giving
- Ways to give to CSE
- Matching gifts
- CSE directories
- Invest in your company and the future
- Recruit our students
- Connect with researchers
- K-12 initiatives
- Diversity initiatives
- Research news
- Give to CSE
- CSE priorities
- Corporate relations
- Information for faculty and staff
- Administrative offices overview
- Office of the Dean
- Academic affairs
- Finance and Operations
- Communications
- Human resources
- Undergraduate programs and student services
- CSE Committees
- CSE policies overview
- Academic policies
- Faculty hiring and tenure policies
- Finance policies and information
- Graduate education policies
- Human resources policies
- Research policies
- Research overview
- Research centers and facilities
- Research proposal submission process
- Research safety
- Award-winning CSE faculty
- National academies
- University awards
- Honorary professorships
- Collegiate awards
- Other CSE honors and awards
- Staff awards
- Performance Management Process
- Work. With Flexibility in CSE
- K-12 outreach overview
- Summer camps
- Outreach events
- Enrichment programs
- Field trips and tours
- CSE K-12 Virtual Classroom Resources
- Educator development
- Sponsor an event

COMMENTS
Unresolved: Principled, policy-free control of CPU time. Unresolved: Handling of multicore processors in the age of verification. Replaced: Process kernel by event kernel in seL4, OKL4 and NOVA. Abandoned: Virtual TCB addressing. …. Abandoned: C++ for seL4 and OKL4.
Past exam papers: Operating Systems. Solution notes are available for many past questions to local users. They were produced by question setters, primarily for the benefit of the examiners. These are not model answers: there may be many other good ways of answering a given exam question! The solution notes for the most recent two year's worth ...
Operating Systems - Essay Sample. An operating system, or OS, is a common computer piece in the world today. An OS is an intricate set of software programs that helps organize information within a computer's hardware. It can store information and retrieve it from memory systems or the hard drive. It can also direct applications and programs ...
An operating system is a form of "low level" software that supports a computer's basic functions such as scheduling tasks and controlling peripherals. We can simply the operating system into three main functions which are: Manage computer resources. This will be things such as the central processing unit, memory, disk drives, and printers.
Essay about Operating Systems. An operating system is the program that manages all the application programs in a computer system. This also includes managing the input and output devices, and assigning system resources. Operating systems evolved as the solution to the problems that were evident in early computer systems, and coincide with the ...
An operating system is the most important software that runs on a computer. It manages the computer's memory and processes, as well as all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer's language. Without an operating system, a computer is useless.
Operating systems provide the user to interact with the software and the hardware by using two types of user interface called. Command-line Interface (CLI) with this the user types commands in to the command prompt as shown in Fig 3.0. Graphical user interface with this the user interacts with menus, icons and applications as shown in Fig 3.1.
Essay On Computer Operating System. 1237 Words5 Pages. A computer was born at the intersection of science and human intelligence. The computer is the greatest invention in the history of human civilization. With the advent of the computer, how to use a computer is a problem, the first way is using DOS to send instructions to the computer.
2. Single-user, single task - As the name implies, this operating system is designed to manage the computer so that one user can effectively do one thing at a time. The Palm OS for Palm handheld computers is a good example of a modern single-user, single-task operating system. 3. Single-user, multi-tasking - This is the type of operating ...
The evolution of operating systems. Published 1 November 2001. Computer Science. TLDR. The author looks back on the first half century of operating systems and selects his favorite papers on classic operating systems, which conclude that operating systems are based on a surprisingly small number of ideas of permanent interest. Expand.
Operating Systems Authors and titles for recent submissions. Tue, 26 Mar 2024; Tue, 19 Mar 2024; Thu, 14 Mar 2024; Tue, 12 Mar 2024; Fri, 8 Mar 2024 [ total of 8 entries: 1-8] ... Comments: Computer Science, Computer Engineering, and Applied Computing (CSCE) Conference 2022
Operating Systems And Software Systems. An operating system is a system software that manages and control all interaction between a computer hardware and software. There are several types of operating systems, for example, multi-user, multitasking, single user and more. The first ever created OS date back in the 50's.
The operating system acts as an intermediary between users and computer hardware (Bower, 2015) The three most commonly used operating systems are Linux, Unix, and Windows [2]. This paper will concentrate its attention on the Mac operating system, macOS, a Unix-based operating system developed by Apple Inc.
An operating system (OS) is a program that acts as an interface between the system hardware and the user. Moreover, it handles all the interactions between the software and the hardware. All the working of a computer system depends on the OS at the base level. Further, it performs all the functions like handling memory, processes, the ...
Computer operating systems have come from a past of no User interface and being a command line base to the modern day Windows 8 and Mac OS's of application based. If operating systems focus on Applications, cloud and digital downloads for software, this approach will take the computer operating systems into the next twenty years of computing.
computer, device for processing, storing, and displaying information.. Computer once meant a person who did computations, but now the term almost universally refers to automated electronic machinery.The first section of this article focuses on modern digital electronic computers and their design, constituent parts, and applications. The second section covers the history of computing.
Essay Writing Service. The operating system has many goals. The main goal is efficient use. The operating system ensures efficient use of memory, CPU and input output devices. Operating system can consume CPU and memory resources that can consume overhead. Besides, operating system monitors use of resources to make certain of efficiency.
Read this Technology Essay and over 89,000 other research documents. Computer Operating System. Introduction An operating system (OS) is a program that acts an intermediary between a user of a computer and the...
heyyyyy operating systems essay learning how to use an operating system is an important skill for anyone who plans to use computers. operating systems are
The operating system is an extremely crucial type of system software. It is the backbone of a computer. Without an operating system, our computers will not function properly. Operating systems are highly skilled software that includes programs with an ample amount of information.
An operating system (OS) is a collection of software that manages computer hardware resources and provides common services for computer programs. It is a program designed to run other programs on a computer. The operating system is an essential component of the system software in a computer system. Application programs usually require an ...
Frequently Asked Questions on Computer. Q.1 What is a computer? A.1 A computer is an electronic device or machine that makes our work easier. Also, they help us in many ways. Q.2 Mention various fields where computers are used? A.2 Computers are majorly used in defense, medicine, and for research purposes.
Readings for the course cover papers from the top venues of AI, Visualization, and HCI, topics including AI explainability, reliability, and Human-AI collaboration. ... This course is targeted towards students with a strong interest in computer systems (Operating Systems, Distributed Systems, Networking, Databases, etc.). Background in ...