Bluetooth in Intelligent Transportation Systems: A Survey
- Open access
- Published: 29 May 2014
- Volume 13 , pages 143–153, ( 2015 )

Cite this article
You have full access to this open access article
- M. R. Friesen 1 &
- R. D. McLeod 2
15k Accesses
32 Citations
3 Altmetric
Explore all metrics
The rise of Bluetooth-equipped devices in personal consumer electronics and in in-car systems has revealed the potential to develop Bluetooth sensor systems for applications in intelligent transportation systems. These applications may include measurements of traffic presence, density, and flow, as well as longitudinal and comparative traffic analysis. A basic Bluetooth sensor system for traffic monitoring consists of a Bluetooth probe device (s) that scans for other Bluetooth-enabled device (s) within its radio proximity, and then stores the data for future analysis and use. The scanned devices are typically on-board vehicular electronics and consumer devices carried by the driver and/or passengers which use Bluetooth communications, and which then reasonably proxy for the vehicle itself. This paper surveys the scope and evolution of these systems, with system attributes and design decisions illustrated via a reference design. The work provides motivation for continued development of non-invasive systems that leverage the existing communication infrastructure and consumer devices that incorporate short range communication technology like Bluetooth.
Similar content being viewed by others

Design and Development of Bluetooth Based Vehicle Scanner for Real Time Traffic Control

Sensing Bluetooth Mobility Data: Potentials and Applications
Speed and density measurement for road traffic using mobile technology in cars.
Pedro García-Fernández, Pedro Á. Castillo, … Victor M. Rivas
Avoid common mistakes on your manuscript.
1 Introduction
Intelligent traffic systems (ITS) hold the promise to improve roadway congestion and transportation infrastructure management by capitalizing on information derived from traffic monitoring. The increasing requirement and public expectation for accurate vehicular traffic information to manage traffic flows has precipitated the deployment of large scale traffic monitoring infrastructures. Typically, this has included the use of inductive loop detectors, microwave sensors and relatively expensive video cameras.
On-board vehicular electronic devices as well as consumer electronic devices are emerging as an alternative traffic sensing modality to complement the existing traffic monitoring and management infrastructure. This evolving infrastructure provides has the benefit of providing cost-effective, real time traffic data by leveraging existing telecommunication infrastructure such as the cellular phone network.
This paper reviews the application of Bluetooth sensing in relation to ITS. It is a field that has seen very rapid evolution in the past 10 years, and will undoubtedly continue to evolve rapidly. A survey of the current state of the art can serve as a point of reference for both future and past works. In this paper, wireless sensor networks based on Bluetooth sensing are presented as a practical means of collecting a statistical representation of traffic density and flow. A basic system configuration consists of a Bluetooth probe device (s) that scans for other Bluetooth-enabled device (s) within its radio proximity, and then stores or forwards the data for future analysis and use. The scanned devices are typically on-board vehicular electronics and consumer devices carried by the driver and/or passengers which use Bluetooth communications, which reasonably proxy for the vehicle itself. Thus, the data provide the information needed to extract a reasonable approximation of traffic presence, density, and flows.
The work reported here is contextualized within many of the uses initially suggested under the IntelliDrive initiative [ 1 ] that are oriented towards improving mobility within surface transportation systems. However, advanced applications are not practical to deploy on scale without leveraging implementations based on networked and web services and evolving internet technologies. Currently, web service realization for ITS applications is promising, since a uniform middleware can be achieved while utilizing the underlying network infrastructure [ 2 ]. The applications reviewed in this paper demonstrate this integration.
Early vehicular telematic applications were user-centric, whereas innovative applications that are now within reach often combine crowdsourced information with the objective of data collection and analysis for statistical reliability and generalizability [ 3 ]. These newer class applications are cohort-centric rather than individual- or user-centric. An early reference to the use of crowdsourcing for ITS [ 4 ] pursued the idea via a Smartphone app than from a wireless sensor network. These applications often rely on inferencing from GPS-equipped probes or floating cars, with the intent to capture the behaviours of a statistically significant portion of vehicles, such that meaningful inferences can be made and potentially generalized to the entire population of vehicles [ 5 ], [ 6 ]. Being statistical in nature, in some cases, only a very small amount of floating car or probe data are required to infer significant events such as congestion build-up or dissolution [ 7 ]. In addition to the work relative to estimating traffic from GPS-enabled probe devices and map services, an alternative includes the possibility of using drivers’ cellphone trajectories as directly as proxies for vehicles, without an intermediary Smartphone app, as could be provided from a mobile cellular service provider [ 8 – 10 ]. Cellphone trajectories are typically coarser-grained in both space and time but can be overlaid on a traffic grid and allow for some degree of traffic flow inferencing [ 11 ].
This survey is directly related to the use of Bluetooth transceivers to crowdsource data from a statistically significant sample of vehicles, where the data can be analyzed for traffic reliable inferencing. Bluetooth is a short-range, wireless telecommunications standard that defines how mobile phones, computers, personal digital assistants, car radios, GPS units, and other digital devices can be easily interconnected. A prototypical example of the technology configuration is the interconnection of a driver’s or passengers’ mobile phone to a wireless earpiece of vehicle audio system for hands-free operation while driving.
The remainder of this paper is organized as follows. Section 2 provides a background of Bluetooth in Intelligent Transportation Systems (ITS) from some of the earliest academic references in the research area to the present. Section 3 discusses Bluetooth relative to the methods and data that can be readily obtained in a non-intrusive manner in an ITS context. Section 4 overviews the design considerations within a Bluetooth configuration for ITS applications, and Section 5 provides a provides a an illustrative reference design which encompasses many of the phenotypes of a typical Bluetooth sensor network for ITS and illustrates the ease with which data can be collected, stored and presented.
2 A Survey of Bluetooth in ITS
The earliest references to using Bluetooth for tracking purposes were typically unrelated to vehicular traffic and ITS. Within overall objectives of safety and flow monitoring, early examples included Bluetooth tracking systems to track of children at a zoo [ 12 ] and students at a University [ 13 ]. The realization that wireless sensor networks generally may play a significant role in traffic monitoring emerged in the literature in the mid-2000s [ 14 ] without explicitly mentioning Bluetooth.
Bluetooth may now appear to be an obvious methodology for non-intrusive traffic detection and estimation; however, industry reports and tests as late as 2010 evaluated various traffic sensors without considering Bluetooth as an option [ 15 ]. In a 2010 study, the authors almost apologetically implied that limiting their system to Bluetooth networks was a potential limitation, and indicated that their work could be applied to Wi-Fi devices as well [ 16 ]. The field since then has borne out that the Bluetooth devices serve as better proxies for vehicles than Wi-Fi devices would have been.
Another concurrent stream of research has been associated with the role of GPS in traffic monitoring relative to estimating travel times, vehicle density, and vehicle flows. In a more ambitious program where data was collected from GPS-enabled cellular devices, the work indicated that a 2-3 % penetration of GPS enabled cell phones in the driver population was sufficient to provide accurate measurement of the velocity of traffic flow [ 6 ]. Although the percentage of GPS enabled cell phones is clearly above the 2-3 % of the population, it is also a requirement that the GPS unit be physically on and driver data voluntarily be provided (either implicitly or explicitly). In comparison to Bluetooth, the only requirement is that the probed device has its Bluetooth enabled or discoverable, which is more often the case than having GPS enabled as well.
The potential of Bluetooth in traffic monitoring began to appear in the academic literature near 2010 [ 16 , 17 ] although a small number of early field trials by local government transportation departments and agencies date to as early as 2008 [ 18 ] and 2010 [ 19 ]. Another early reference to Bluetooth sensing in a 2009 academic thesis emphasized optimal sensor location as opposed to data collection [ 20 ]. These were some of the first publications to consider Bluetooth as a means of collecting data for traffic monitoring and ITS management. A potential exception may be a 2004 reference to Bluetooth for ITS where Bluetooth is considered as a means of inter-vehicle communication as opposed the use of Bluetooth as a traffic monitoring sensor [ 21 ].
The reliability of Bluetooth sensor systems for ITS depends on widespread Bluetooth-enabled device penetration. In a study of traffic through the Limfjord Tunnel, Bluetooth penetration was estimated at between 27 and 29 % [ 22 ]. This appears to be considerably higher than many other reports at or about the same time frame. In a longitudinal study, Bluetooth penetration was seen to increase dramatically with the number of unique MAC addresses seen increasing over a year by 26 % [ 22 ]. Rationale for the increased penetration was assumed to be the popularity of GPS units combined with an increasing number of vehicles with built-in Bluetooth. This reported level of Bluetooth penetration augers well for the continued investigation into these technologies and increased levels of statistical confidence as an increasing number of Bluetooth devices become discoverable.
Most often, one thinks of the Bluetooth-enabled cellular phone as a foundational component in a Bluetooth sensor system for ITS. This premise is supported by cellular penetration rates in Canada and the U.S as well as elsewhere. In the first quarter of 2012, Canada had 28 million cellular subscribers in total, which is a penetration rate of up to 80 % if no duplicate devices to a single subscriber are considered. While not all cellular phones are Bluetooth-capable, Nielson reports Smartphone penetration of up to 64 % of mobile phone owners in the U.S. by August 2013 [ 23 ].
In one of the earliest references, researchers in 2008 envisioned the basic system components of a Bluetooth sensor system for ITS that have since evolved, stating that “one could easily imagine a battery-powered, Bluetooth enabled, smart cell phone in a plastic case chained to the side of the road to collect much more substantive travel time estimates over 24 h or 7 d to much more precisely characterize operational characteristics of either a signalized corridor or a construction work zone. Those data might be logged for later download” [ 18 ].
In general, these early studies typically focused on applications to vehicle travel times estimates (including travel time delays due to roadway obstructions) and origin–destination estimates on urban arterials and freeways. Potential applications to network analysis (shortest path), congestion reporting, bicycle and pedestrian travel times, and before-after studies were also speculated [ 19 ]. Other research interests included the quality of data produced by the Bluetooth detection of mobile devices for applications to travel time forecasting and estimates of time-dependent origin–destination matrices within an Advanced Traffic Information System (ATIS) that supplies information to drivers [ 24 ]. More recent studies likewise investigate the role of Bluetooth sensors to estimate travel times [ 25 , 26 ] and vehicle velocities [ 27 ].
Privacy considerations were also foreseen early on, with the recommendation that organizations that implement Bluetooth-based tracking for ITS applications develop practices that encrypt and preclude storing MAC addresses for more than a few hours [ 18 ].
Early studies also observed asymmetry of traffic data collected in opposite directions (e.g. westbound vs. eastbound) and attributed this to antenna position. Others extended this line of investigation, characterizing antenna patterns and observing that an omnidirectional radiation pattern is most suitable for Bluetooth data collection [ 28 ]. This is not unexpected, as it reduces the complexity of antenna placement and analysis when implementing a larger system of Bluetooth sensors.
In one such study of antenna characterization relative to travel time data collection using Bluetooth, the proportion of unique Bluetooth MAC addresses read relative to the known total traffic flow was reported to be 10 % [ 28 ]. Although published in 2013, these data appear to have been collected in 2011 and as such, they represent a significant increase in the Bluetooth MAC address reads reported just three years earlier at 1 % [ 18 ]. This improvement is likely due to both higher gain antennas developed combined with the precipitous increase in the number of Bluetooth devices in vehicles over that same time period. Currently, the collecting of CoD information is largely absent in the available literature.
Furthermore, the role that Received Signal Strength Indicator (RSSI) may play in the Bluetooth data collection process in ITS arose as an explicit research question around 2011 [ 29 ], with little other apparent work on investigating RSSI as a Bluetooth data source specifically for vehicular traffic. One of the few studies available explores using RSSI as means of estimating distance from the scanning point and using Class of Device information as a potential means of differentiating pedestrians from vehicles [ 30 ].
System calibration and validation studies are becoming more rigorous as more Bluetooth sensor systems for ITS are deployed. Opportunities exist to calibrate the data with existing traffic measurement devices, including loop-detectors, mechanical counters, travel survey data of various forms, and increasingly, data inferred from cellphone trajectories. In one novel study, Bluetooth sensor data has been compared with automatic license plate recognition (ALPR) systems [ 17 ]. If available, ALPR provides as nice alternative for validation as both ALPR and Bluetooth sensors also label the data, in contrast to loop-detectors, counters, and survey data. Systems have been developed that employ a variety of sensors and their fusion in scaling up systems [ 31 ], such as the fusion of loop based detection with Bluetooth-enabled devices [ 32 ]. While Bluetooth devices appear to have been limited to defined probe vehicles resulting in a low quantity of Bluetooth data, the work demonstrated opportunities in multi-sensor data fusion using Bluetooth data in conjunction with auxiliary measurements. Another instructive example of multi-system calibration potential is with the Anonymous Wireless Address Matching (AWAM) proof of concept demonstration with the City of Houston on an urban arterial [ 33 ]. Travel times and speeds collected on identical roadway segments using a probe-based toll tag (AVI) system and the AWAM system were compared with excellent correlation.
While large-scale deployment of commercial Bluetooth traffic monitoring is still in its infancy, a number of pilot programs of various scales are being deployed. In Clark County, a pilot program costing $540,000 has approximately 20 Bluetooth probes installed collecting data along the Andresen corridor which experiences relatively high traffic, in an effort to determine whether the system can provide the information that traffic engineers need [ 34 ]. The study reports the system reading 3-5 % percent of vehicular traffic via Bluetooth MAC addresses, and they have recognized this to be sufficient to provide information on traffic flow. According to the authors, sufficient data and analysis is anticipated by early 2014 for agencies to use the outcomes to adjust traffic signal timing. Similar pilot programs are ongoing in many other countries [ 35 – 37 ]. While many pilot programs have focused on traffic flow on corridors and arterials, there are other Bluetooth scanning applications that are associated with work zone diversions [ 19 , 38 , 39 ]. At present, the majority of pilot programs are related to travel time informatics and Bluetooth data assessment towards building evidence-based cases for traffic signal retiming [ 40 ].
One of the earliest commercial system that used Bluetooth for vehicle identification for travel time estimation appears to be BLIDS [ 41 ] ( http://www.blids.cc/ ). BLIDS was introduced early 2008 with over 50 systems deployed primarily along corridors. Traffax Inc. ( http://www.traffaxinc.com/ ) is also one of the early commercial vendors of Bluetooth traffic monitoring systems, with the system known by the trade name BluFax and introduced in 2009. Traffax has a patent application pending (CA2711278 A1) which claims a priority date of January 2008, (provisional filing) but may come under some challenges as the system of [ 18 ] was already deployed at that time. Blipsystems ( http://www.blipsystems.com/home/ ) supplies a commercial solution to Bluetooth tracking and traffic monitoring, with their product is denoted BlipTrack. Another commercial system is TrafficCast ( http://trafficcast.com/ ) with a product denoted BlueTOAD. Iteris ( http://www.iteris.com/ ) also has similar product denoted Vantage Velocity for capturing Bluetooth MAC data but does not appear to have integrated cellular connectivity. In these commercial systems, most if not all of the components discussed in this survey are included as product offerings. Somewhere in-between commercial systems and academic prototypes, various transportation institutes and agencies are leveraging intellectual property developed at or in conjunction with universities. An excellent example is the Texas A&M Transportation Institute [ 37 , 42 ].
With the observed data gathering potential of Bluetooth for ITS applications combined with the emergence of a ‘big data’ culture, numerous references to systems and implementations have appeared from industry, governments, and academia. This diversity of approaches, motivations, and originators of the research lends credibility to the expanding role that Bluetooth sensing can play in ITS. In spite of this, there continues to be a need to explore system integration and validation for the various combinations of system configurations that can be envisioned.
3 Bluetooth Technology
Bluetooth is one of several available wireless technologies that may be employed to assist in resolving location extracted from a consumer electronic device (Table I ). This survey focuses on classical Bluetooth 2.0 with a range that is well-tailored for monitoring or detecting devices residing in or integrated into vehicles, such as Smartphones, Bluetooth earpieces and car audio. NFC and BLE 4.0 are more recent market entries with emphasis on low power and more personal communication or very body-centric networking. WiFi and cellular are intended for wider area networking.
In addition to Table I , there is a variety of wireless networking technologies developed over the IEEE 802.15.4 protocol such as ZigBee or XBee. These and similar are not considered here as they have not established a dominant presence in consumer devices such as smartphones. However, they are technologies to stay aware of as automobile manufacturers incorporate greater degrees of low cost wireless technologies into product lines. Relative to the basic functionality of inferencing vehicle presence by scavenging radio signals, ZigBee could provide an alternative to Bluetooth, although at this time is difficult to foresee ZigBee to be as pervasive as Bluetooth.
In general, Bluetooth scanning requires a device to probe the local wireless environment and detect the proximity of Bluetooth radios. In the ITS context, the proximate Bluetooth radios (typically, drivers’ or passengers’ Smartphones, earpieces, or on-board car audio) detected by the probe device serve as proxies for vehicles. The objective of the probe devices (aka probes) is to collect information on vehicle presence (detection by one probe) and vehicle trajectory information (detection by multiple probes in sequence) via Bluetooth device discovery, and then transmit this information via either an intermediate wireless tier or directly over a cellular network to a web service or backend server. The communication protocols between probes and backend servers are typically based on the TCP/IP protocol stack, leveraging not only the physical communication infrastructure but also the highly developed Internet IP infrastructure.
The data collected from a Bluetooth scan can be fairly detailed, including a detected Medium Access Control (MAC) address, Class of Device (CoD) information, as well as metadata from the manufacturer or as specified by the device owner (Fig. 1 ). While getting all of this information from a device and storing it could lead to security and privacy concerns, the MAC address, the primary method of identifying a Bluetooth device, can easily be anonymized in a fashion such that the device can be uniquely identifiable from other devices while preserving a user’s identity to a certain degree.
Simple Bluetooth Probe Scan Data
The Bluetooth address itself is a unique 48bit device identifier, where the first 3 bytes of the address are assigned to a specific device manufacturer by the IEEE ( www.ieee.org/ ), and the last 3 bytes are freely allocated by the manufacturer. Even if the manufacturer of a device is known, the number of possible Bluetooth addresses is immediately limited to 16,777,216. As well, since only devices that are in discoverable mode can be detected by the scan, a user can simply turn their device off (non-discoverable) to avoid being detected. There are software tools available which allow brute-force discovery of non-discoverable devices, an early example of which is RedFang, but this is usually too complex for a minimal hardware configuration and not necessary for data collection purposes associated with ITS. It is also possible to burrow deeper into Bluetooth connections to provide connection-based tracking for fine granular or building-wide device tracking [ 43 ].
It is desirable, but not necessary, to employ probes in such a way that the system is scalable. This is one of the most unique features of a Bluetooth data collection system. An organization can start with a very limited and even a portable system and easily scale it to meet increased sensing demands. In this regard, the backend data collection, storage and analysis hardware are conservative. Modern web servers and connectivity are more than sufficient to collect the volume of data that could be collected even from a large number of Bluetooth probes. The scalability issue has essentially been further resolved by existing cellular and internet infrastructure, web servers, and data services collectively being developed as a Service-Oriented Architecture (SOA) [ 44 , 45 ].
The primary equipment used as the Bluetooth probe device must have the ability to be set for device discovery. Several of the existing Bluetooth modules libraries are designed to detect eight devices per inquiry, which is insufficient for most vehicular traffic applications. The limitation of eight appears to be a consequence of the anticipated use cases of Bluetooth enabled consumer devices, where supporting eight connections is likely more than sufficient. In effect, many existing Bluetooth modules are designed for connecting with the Bluetooth devices it discovers, whereas for ITS Bluetooth data collection, the primary requirement is only for devices to be detected. During traffic congestion periods, it is desirable to discover as many surrounding devices as possible, but a connection to the surrounding devices is not required. The important aspect is to ensure that the selected Bluetooth probe modules can discover as many devices as possible. In the reference design (Section 5), up to 250 unique devices per inquiry were detectable and hence recordable. This detection capability is not a restriction of the standard but rather particular implementations. For example, a detailed description of the Bluetooth discovery protocol that simulates the detection of 15 devices within a few seconds is available in the literature [ 46 ].
4 Bluetooth Sensor System: Attributes & Design Decisions
When designing a Bluetooth sensor system for ITS applications, there are choices in system attributes that become design decisions unique to the context and objectives of the system in deployment (Fig. 2 ). The basic configuration requires the designer to decide what type of probe device (s) will be used, how many probe device (s) are required, and where and how they will be located and fixed in the environment.
Bluetooth traffic monitoring design decisions
Commercial/Prototype: In academia, a prototype system can often be easily assembled for several thousand dollars and provide entry-level data for exploring Bluetooth device detection. A commercial-grade installation of similar scope would likely be an order of magnitude greater in cost. Intermediate-grade systems are also available, for example [ 30 ].
Fixed/Portable: A fixed system implies a permanent or semi-permanent installation, whereas a portable system implies a system set-up or tear-down time of several hours maximum, and a deployment period measured in days, weeks, or months. In the case of a portable system, consideration has to be application domain, and a portable system offers the convenience of being more easily redeployed. A portable system typically implies a storage battery and possibly a battery charging system, such as solar. A fixed system is typically more robust but greater attention in sensor placement is required as the initial placement decisions may not be easily changeable. Fixed system may also rely on battery power, although a permanent power supply may be cost-effective as well. In both fixed and portable systems, GPS positioning is required. Both fixed and portable systems may be online or offline
Online/Offline: An on-line system has the potential for real-time data collection (and potentially, analysis), by data being stored in the probe for only very short periods of time and backhauled at regular intervals over a wireless connection to a dedicated server. In an offline system, a requirement exists for much more significant data storage and relatively simple retrieval. A minimum requirement would be for the probes to write data to an onboard SD card or similar, and the manual data retrieval protocol to be planned. On-board data storage is typically Flash-based and very robust.
Wireline power/battery/solar: The choice of power to the probe devices depends largely on the intended application. A portable application will most probably be battery powered, and depending on it intended duration and the environment, it may also be equipped with a solar charging system. Wireline power may be an economical alternative in a fixed system, although a fixed system may also run on battery power.
Networking: Networking considerations are typically limited to online systems, where the designer must consider means of data transport. Two of the more likely networking technologies are cellular (e.g. GSM), or WiFi. The consideration in selecting WiFi would be to ensure adequate coverage over a wide area.
Tiered wireless configuration: A tiered wireless sensor network is a very common architecture for sensor networks (e.g. [ 30 ] and the reference design in Section 5). In a system with multiple probe devices, a design decision must be made whether each probe will be equipped with its own WiFi or GSM/GPRS module, allowing direct communication from each probe to the back-end server. The alternate would be to implement a middle wireless tier, adding some complexity to the system. An example, of a multi- tiered wireless implementation is presented in Section 5. It is these authors opinion however, that a tired wireless system should be avoided and direct communication to the probes be supported.
RSSI capable: Only a very limited number of published works incorporated RSSI for traffic monitoring in an ITS context [ 29 , 30 , 47 ]. At time of writing, RSSI data does not play a significant role in Bluetooth systems for ITS applications, although the rapid evolution of this area in general may illuminate the potential and utility of RSSI data within a few years.
Bidirectional: A bidirectional system may be able to proactively communicate over Bluetooth to ‘subscribers’ or discovered devices, for example by providing traffic alerts. For example, a potential business model would allow users to purchase low-cost devices solely for the purpose of being tracked [ 18 ], with a subsequent feature of being able to backcast from the ITS to the device. This device may be as redundant as a Smartphone running a suitable app. The opportunity to also log a subscriber’s OBD-II data automatically would also require bidirectional communication via an established connection with a simple Bluetooth OBD-II dongle.
Remote monitoring and/or control: The Bluetooth probes should be chosen to be remotely monitored and preferably also configurable. The physical environment of installation sites (heavy traffic areas, exposure to all weather conditions) may make on-site monitoring and configuration both uncomfortable and potential dangerous. Remote monitoring allows for early detection of malfunctioning probes and other inconsistencies. Remote configuration can range from configuring the sampling rate and/or sleeping sensors when not required, which becomes critical for battery powered units. The implication of remote monitoring and configuration is that wireless access via WiFi or cellular is available to the probes. .
Cross validation/calibrating: As a Bluetooth sensor is sampling a proportion of the by-proxy vehicle population, by definition considerable emphasis has to be placed of validating and calibrating. A Bluetooth sensor network is relatively easy to install and provides considerable opportunity for sensor fusion. At minimum, designers must consider Bluetooth radio ranges of the probe (s) relative to the sampling area and clock synchronization between multiple probes. In data analysis, considerations include but are not limited to the ability to handle multiple MAC address reads from a given probe sensor that represent different vehicles as well as multiple reads of the same vehicle (e.g. a vehicle stopped at a traffic signal for several sampling periods), simultaneous MAC address reads from two or more probe sensors, one or more MAC address reads of a single MAC address by multiple sensors either simultaneously or in sequence, and MAC address reads of devices that are not necessarily sourced from a vehicle. The fact that the data is labeled can be used to provide some level of differentiation. There will always be some degree of uncertainty; for example, the data analysis is unlikely to be able to definitely differentiate a single vehicle from public transportation (e.g. a bus with 40 passengers and multiple Bluetooth reads). Managing uncertainty is one of the more academic aspects associated with Bluetooth traffic monitoring and promises to be a rich area of research [ 48 ].
Security: By virtue of the fact that all wireless communication devices need to signal to some degree in plain sight, security will always be an issue. It is not possible to alter this fact, as communicating devices need a standard means of identifying one another.
Bluetooth scanning for ITS applications such as simple traffic flow will become contextualized within big data concepts, in which the opportunities for exploring and exploiting the rich suite of data such systems are capable of generating is a significant research area in its own right. Examples include generating trajectories from uncertainties in measurement and detection [ 49 ] using techniques like Hidden Markov Models. Similar efforts will produce forecasting models that use massive amounts of real-time Bluetooth device data.
5 A Reference Design
This section presents a reference design as an example of one combination of many of the system attributes and design choices overviewed above. The system used multiple Bluetooth transceivers consisting of one master node or access point and multiple sensor probes around a major intersection in a Winnipeg, Canada, during winter 2013 (Fig. 3 ) [ 50 ]. The multiple probes collected vehicle presence information (detection by one probe) and vehicle trajectory information (detection by multiple probes in sequence) via Bluetooth device discovery, and then transmitted this information to the master node via the 802.15.4 protocol.
High level system overview
Architecture
The basic system architecture is that of a Bluetooth sensor network, interconnected with an XBee/802.15.4 middle tier to the master node, and then a GSM wireless backhaul tether to a web data collection and processing web portal. XBee Pro was selected as the middle tier wireless networking technology as it offers a low power solution with sufficient range for the interconnection between the master node and sensor probes. GSM was selected as the cellular tier as a means of aggregating and forwarding data collected to a web server for processing and display. The data sent to the central server displayed the current traffic density and average velocity of vehicles at the intersection on a web front end (including mobile website) at five-minute intervals.
Probe design
The probe design uses an Arduino Uno development board, which utilizes the ATMega328 microcontroller, an XBee module and a Bluetooth Pro module, both of which connect to the Arduino module (Fig. 4 ).
During the data collection process at each probe, the information was organized in a consistent manner. Each device frame is 8 bytes and included a marker byte, a 4 byte timestamp, and 3 bytes for the truncated MAC address. To increase privacy, only half of the MAC address is recorded which still provides 16 million unique combinations for one probe network. The first 3 bytes of the packet are reserved bytes; a control byte, a length byte, and a probe id byte. The maximum packet size that can be produced is 100 bytes, as this is the size of the receive buffer of the XBee module.
The XBee module on the master node was set as the network coordinator, and the XBee module on each probe was set to associate with the network coordinator. To save power, the XBee module on the probes were configured to hibernate when not in use. Due to changes in temperature and other internal and external factors on the probes and master node, the calculated time offset at various nodes slowly drifted over time, requiring scheduled clock resynchronization.
The function of the probe is illustrated in the main flow diagram of Fig. 5 , and the scan flow sub diagram is illustrated in Fig. 6 .
Probe flow diagram
Bluetooth scan diagram
Master node
The master node consisted of Arduino-based GBoard from iteadstudio.com. For the GSM module, a preexisting library was used, with modifications and additional functionality to meet system requirements.
The desired minimum run time of each probe was 24 h. A combination of battery-only and battery-plus-solar were used, demonstration the viability of a solar rechargeable source for the wireless sensor network. The rechargeable power sources were two 4,400 mA, 3.7 V lithium ion batteries hooked up in parallel to a step-up converter (to 7 V). Both batteries are connected to lithium-ion chargers powered by a 3.7 W, 6 V solar panel. A custom step-up converter was also designed to have lower current draw compared to the off the shelf step-up converter; thereby increasing the life expectancy of the supply.
Database and front-end
A MySQL database was used in order to store data, refreshed at five minute intervals, and display data to a user through a website or a smartphone app. Initial scripts were written where device MACs are compared to a table of existing MACs to find matching devices with a different probe location. When found, a probe-pair was created using the start probe, end probe and detection time difference; this was used to estimate the velocity of the device. Another PHP script was created that automatically runs every five minutes, refreshing the traffic data that is displayed on the websites. The data is stored as the total travel time for all vehicles and the total vehicle count through each probe-pair.
Implementation
A Bluetooth discovery test was conducted to ensure devices traveling in excess of 80 km/h could be detected. The XBee distance test consisted of testing the connectivity while increasing the separation between master and slave devices. Line of sight difficulties were encountered for distances exceeding 200 m. As a complete test of the system, four probes were placed along a major thoroughfare to capture the traffic over several 24 h timeframes for multiple iterations representative of different traffic and weather conditions. Probes and master nodes were mounted to light standards along the thoroughfare using steel strapping at an elevation of approximately 2.5 m. Several single-probe and multi-probe trials were carried out over winter, 2013. Data were cross-referenced to data obtained by mechanical traffic counters and to cellular service provider data that can serve as proxies for users’ movements between cell towers. Qualitatively similar trends in traffic density and flow were observed from the data sources. The reference design was found to capture an average of 4.5 % of real vehicle traffic (when compared to mechanical counters), which is above the 2-3 % conjectured as being required for statistically accurate traffic flower inferencing [ 6 ]. Initial findings lent credibility to the reference design as having the characteristics of a viable full-scale system. The cost of the reference design described above was approximately $1,500 in 2012 and 2013.
The reference system described above provides insights into the type of data that can be easily and cost effectively collected at a relatively inexpensive capital cost. The reference design, which was an academic prototype, is validated conceptually by others who report similar systems and investigations. In a study on traffic monitoring with Bluetooth sensors over ZigBee, an intervening multitier network is discussed [ 30 ]. Although a different protocol is deployed, the basic ideas and rationales are similar. Others similarly discuss the use of Bluetooth data to infer vehicle proximity as a means of estimating traffic characteristics, including the use of solar power to meet system energy requirements [ 51 , 52 ].
6 Additional Considerations
As of time of writing, the emerging wireless technology for inferring traffic is that based on Bluetooth 2.x. Bluetooth 2.x is the most widely deployed mid-range communication protocol has a range commensurate with distances typical of traffic and traffic control systems. The ubiquity of Bluetooth 2.x and its ready application to traffic-related contexts currently makes it a natural choice for ITS applications. In the future, communication alternatives and superior wireless versions - ostensibly developed for different user applications - will undoubtedly contribute to the data collected for ITS. For example, Bluetooth 4.0 is currently available for ‘coin-cell-powered’ devices and is currently not obviously applicable to common ITS applications; however, this applicability is likely to develop as new opportunities emerge. The same is true for other technologies, in the spirit that the most effective uses of a technology often emerge after its development rather than as a bounded or fixed a priori specification.
From our experience, one significant recommendation in this field of Bluetooth sensor systems for ITS would be to avoid ad hoc intermediate networks. The difficulties with installation and reliability make data collection networks that rely on lines of sight for communication too constraining. In addition, the XBee communications used in the reference design were power-intensive and not tuned for power conservation. As an alternative, each sensor should ideally be equipped with GSM/GPRS and have the backend service parse data from each probe directly. The additional costs of this approach are likely to be outweighed by the benefits accrued through much simpler deployment and lower maintenance. The intervening XBee, communication network also added complexity through the use of a less efficient protocol for data transmission than GSM directly. This follows the principle of “Lex Parsimonia” where the simplest system is most likely the best.
Future work should investigate the integration of mobile Bluetooth probes as well as stationary probes. This increases processing and analysis of the data collected, but would augment data collected by the stationary Bluetooth probes. An example of a vehicle trajectory while scanning, is in [ 53 ], while a patent application for a mobile probe can be found in [ 54 ]. Utilizing mobile probes would also allow for augmenting of the data with information such as acceleration at intersections, and would be a direct means of inferring environmental conditions such as ice and snow.
Finally, a decided advantage of a Bluetooth traffic monitoring system through a Services Oriented Architecture is that it can easily and inexpensively augment any existing traffic measurement system.
The real academic, engineering, and organizational challenges will lie in full-scale deployment of a Bluetooth sensor system at many intersections across a large urban centre. The probe sensor network may be augmented by a large number of probe vehicles that could also be configured to upload data from proximate devices detected while in transit. The only requirement for this additional data from probe vehicles is to augment the discovered Bluetooth MAC address and timestamp with GPS information. Once scaled to city-wide deployment, the data mining challenges will be considerable and will require a whole new big data approach, but will also become an invaluable input to an ITS.
Research and Innovative Technology Administration (2010). Achieving the Vision: From VII to Intellidrive. [Online]. Available: http://www.its.dot.gov/press/2010/vii2intellidrive.htm
R. Sengupta, C. Manasseh and S. Levenson,. “Service oriented architectures for VII – Extending web services to the roadway”. [Online]. Available: http://www.its.berkeley.edu/volvocenter/VREF/UCBSOA_VIIChristian.pdf
E. Hossain, G. Chow, V.C.M. Leung, R.D. McLeod, J. Mišić, V.W.S. Wong, and O. Yang, “Vehicular telematics over heterogeneous wireless networks: A survey”, Computer Communications, Volume 33 (Issue 7, 3), Pages 775–793 (May 2010)
J. Sorensen, “One in Evert Crowd”, Traffic Technology International, February-March, http://www.dagstuhl.de/Materials/Files/10/10121/10121.XuBo1.Paper.pdf (2010)
B.S. Kerner, C. Demir, R.G. Herrtwich, S.L. Klenov, H. Rehborn, M. Aleksic and A. Haug, “Traffic state detection with floating car data in road networks. Proceedings of the 8th International IEEE Conference on Intelligent Transportation Systems, 44–49 (2005)
Herrera, J.C., Work, D.B., Herring, R., Ban, X., Jacobson, Q., Bayen, A.M.: Evaluation of traffic data obtained via GPS-enabled mobile phones: The Mobile Century field experiment”. Transportation Research Part C: Emerging Technologies 18 (4), 568–583 (2010)
Article Google Scholar
G. Halbritter, T. Fleischer, C. Kupsch, J. Kloas and U. Voigt, “Nationale Innovationsstrategien für neue Techniken und Dienste zur Erreichung einer „nachhaltigen Entwicklung” im Verkehr (Report FZKA 7157). Karlsruhe, Germany: Forschungszentrum Karlsruhe GmbH, (2005)
Y. Yim and R. Cayford, “Investigation of vehicles as probes using global positioning system and cellular phone tracking: Field operational test”, Number UCB-ITS-PWP-2001-9, California PATH Program, Institute of Transportation Studies, University of California, Berkeley, CA, (2001)
J.L. Yagnace, C. Drane, Y.B. Yim, and R. de Lacvivier, “Travel time estimation on the San Francisco Bay area network using cellular phones as probes”. Number UCB-ITSPWP-2000-18, California PATH Program, Institute of Transportation Studies, University of California, Berkeley, CA, (2000)
A. Alessandri, R. Bolla, and M. Repetto, “Estimation of freeway traffic variables using information from mobile phones”, In Proc. American Control Conference the 2003, volume 5, pages 4089–4094, Denver, CO, (June 2003)
R. Neighbour, R.D. McLeod, M.R. Friesen, and S.N. Mukhi, “Vehicular Traffic Modeling Governed by Cellular Phone Trajectories”, VTC-Fall (2012)
BlueTags to install world’s first Bluetooth tracking system, 2003. http://www.geekzone.co.nz/content.asp?contentid=1070 .
M. Haase and M. Handy. BlueTrack – Imperceptible tracking of bluetooth devices. In Ubicomp Poster Proceedings, (2004)
Y. Wen, J.L. Pan and J.F.Le, “Survey On Application Of Wireless Sensor Networks For Traffic Monitoring”, International Conference on Transportation Engineering 2007 (ICTE 2007)
E. Minge, J. Kotzenmacher, and S. Peterson “Evaluation of Non- Intrusive Technologies for Traffic Detection”, Mn. DoT., Final Report #2010-36, http://www.miovision.com/wp-content/uploads/Evaluation_of_Non-Intrusive_Traffic_Detection_Technologies_pdf (September2010)
Barceló, J., Montero, L., Marqués, L., Carmona, C.: Travel Time Forecasting and Dynamic Origin–destination Estimation for Freeways Based on Bluetooth Traffic Monitoring”. J. Transp. Res. Board 2175 , 19–27 (2010)
Y. Wang, Y. Malinovskiy, Y-J. Wu and U-K. Lee, “Field Experiments with Bluetooth Sensors”, n.d., http://www.westernstatesforum.org/Documents/UW_FINAL_Bluetooth_WSRTF_6-17-10.pdf (2010)
Wasson, J.S., Sturdevant, J.R., Bullock, D.M.: Real-Time Travel Time Estimates Using MAC Address Matching. Institute of Transportation Engineers Journal, ITE 78 (6), 20–23 (2008)
Google Scholar
R. Haseman, J.S.Wasson and D.M. Bullock, D M., Real-Time Measurement of Travel Time Delay in Work Zones and Evaluation Metrics Using Bluetooth Probe Tracking. Transportation Research Record: Journal of the Transportation Research Board, pp. 40–53, (2010)
M. Asudeqi, “Optimal Number and Location of Bluetooth Sensors for Travel Time Data Collection in Networks”, M.Sc. Thesis, University of Maryland, http://hdl.handle.net/1903/9400
H. Sawant, J. Tan, Q. Yang, and Q. Wang, “Using Bluetooth and sensor networks for intelligent transportation systems,” Intelligent Transportation Systems, 2004. Proceedings. The 7th International IEEE Conference on, vol., no., pp.767,772, 3–6, doi: 10.1109/ITSC.2004.1398999 (Oct. 2004)
B. Araghi, K.S. Pederson, L.T. Christenson, R. Krishnan, and H. Lahrmann, “Accuracy of Travel Time Estimation using Bluetooth Technology: Case Study Limfjord Tunnel Aalborg”, ITS World Congress, (2012)
Nielson, “Smartphone Switch: Three Fourths of Recent Acquirers Chose Smartphones” Available: http://www.nielsen.com/us/en/newswire/2013/smartphone-switch--three-fourths-of-recent-acquirers-chose-smart.html
Barceló, J., Montero, L., Marqués, L., Carmon, C.: Travel Time Forecasting and Dynamic Origin–destination Estimation for Freeways Based on Bluetooth Traffic Monitoring”. J. Transp. Res. Board 2175 , 19–27 (2010)
J.D. Porter, D.S. Kim and M.E. Magana, “Wireless Data Collection System for Real-Time Arterial Travel Time Estimates”, OTREC 10–16, http://www.oregon.gov/ODOT/TD/TP_RES/docs/reports/2011/wirelessdata.pdf , (March 2011)
S.E. Young, “Bluetooth Traffic Detectors for Use as Permanently Installed Travel Time Instruments”, STMD -MDOT/SHA, http://roads.maryland.gov/OPR_Research/MD-12-SP909B4D-Bluetooth-Traffic-Detectors_Report.pdf , (Feb. 2012)
Anonymous Wireless Address Matching (AWAM) proof of concept demonstration, Texas Transportation Institute, http://ttihouston.tamu.edu/bluetooth/projects.aspx
Porter, J.D., Kim, D.S., Magaña, M.E., Poocharoen, P., Arriaga, C.A.G.: Antenna Characterization for Bluetooth-Based Travel Time Data Collection”. Journal of Intelligent Transportation Systems: Technology, Planning, and Operations 17 (2), 142–151 (2013). doi: 10.1080/15472450.2012.696452
J.D. Porter, D.S. Kim, M.E. Magaña, P. Poocharoen and C.A.G. Arriaga, “Antenna Characterization for Bluetooth-Based Travel Time Data Collection”, http://www.westernstatesforum.net/Documents/2011/presentations/OSU_KimEtAl_Final_AntennaCharacterization.pdf .
Vehicle Traffic Monitoring Platform with Bluetooth Sensors over ZigBee, [Online]. Available: http://sensor-networks.org/index.php?page=1129929946
G.A. Klunder, Y. S. Chen, K. Zantema, and K. Friso. “Consistent Traffic Modeling and Calibration at Different Resolution Levels Based on Various Sensor Data for Real-time Traffic Management”, 2nd International Conference on Models and Technologies for Intelligent Transportation Systems, 22–24, Leuven, Belgium (June, 2011)
Bachmann, C., Roorda, M.J., Abdulhai, B., Moshiri, B.: Fusing a Bluetooth Traffic Monitoring System With Loop Detector Data for Improved Freeway Traffic Speed Estimation. Journal of Intelligent Transportation Systems: Technology, Planning, and Operations 17 (2), 152–164 (2013). doi: 10.1080/15472450.2012.696449
http://ttihouston.tamu.edu/bluetooth/projects.aspx
E. Hidle, “Bluetooth can help local traffic flow”, http://www.columbian.com/news/2013/oct/21/bluetooth-traffic-flow-clark-county/
S. Yucel, H. Tuydes-Yaman, O. Altintasi, M. Ozen, “Determination of Vehicular Travel Patterns in an Urban Location using Bluetooth Technology”, https://itswc.confex.com/itswc/AM2013/webprogram/ExtendedAbstract/Paper11460/ITS_America_sule_yucel.pdf
M. Blogg, C. Semler, M. Hingorani, R. Troutbeck, “Travel Time And Origin–destination Data Collection Using Bluetooth MAC Address Readers”, Australasian Transport Research Forum 2010 Proceedings, p. 1–15 (2010)
D.D. Puckett and M.J. Vickich, “Bluetooth-Based Travel Time/Speed Measuring Systems Development”, Texas Transportation Institute, DTRT06-G-0044, http://utcm.tamu.edu/publications/final_reports/Puckett_09-00-17.pdf , (2010)
J. Effinger, A. J. Horowitz, Y. Liu, and J. Shaw, “Bluetooth Vehicle Reidentification for Analysis of Work Zone Diversion.” In Transportation Research Board 92nd Annual Meeting, no. 13–2159. (2013)
S. Zinner, “A methodology for using bluetooth to measure real-time work zone travel time.” PhD diss., Georgia Institute of Technology, 2012
C.M. Day, J. S. Wasson, T. M. Brennan, and D. M. Bullock. Application of Travel Time Information for Traffic Management. Publication FHWA/IN/JTRP-2012/06. Joint Transportation Research Program, Indiana Department of Transportation and Purdue University, Indiana, doi: 10.5703/1288284314666 (2012)
A. Steiner and B. Sick, “A new method for travel time estimation on long freeway sections”, Institute of Data Analysis and Process Design, Zurich University of Applied Sciences. European Journal of Transport and Infrastructure Research (ISSN 1567–7141), Vol.8, Issue 4, (2008)
http://tti.tamu.edu/03/01/now-taking-it-to-the-streets-collecting-travel-time-data-speed-with-bluetooth-technology/#applying (2010)
S. Hay and R. Harle, “Bluetooth tracking without discoverability,” Proc. of the 4th Int’l Symp. on Location and Context Awareness. Springer-Verlag, pp. 120–137 (2009)
H. Quintero, L. Felipe, F.M. Pérez, D.M. Jorquera, and Virgilio Gilart Iglesias. “SOA-based Model for the IT Integration into the Intelligent Transportation Systems.” IEEE ITSC2010 Workshop on Emergent Cooperative Technologies in Intelligent Transportation Systems, (2010)
X. Tao, C. Jiang, Y. Han, “Applying SOA to intelligent transportation system”, Proceedings of the IEEE International Conference on Services Computing (SCC’05), Vol.2, pp. 101–106 (2005)
G. Chakraborty, K. Naik, D. Chakraborty, N. Shiratori and D. Wei, “Analysis of the Bluetooth device discovery protocol. Wireless Networks”, Wireless Networks, vol.16, #2, http://dx.doi.org/ 10.1007/s11276-008-0142-1 (2010)
A. Saeedi, S. Park, D.S. Kim, J.D. Porter, “Improving Accuracy and Precision of Travel Time Samples Collected at Signalized Arterial Roads with Bluetooth Sensors ‘, Volume 2380, pp. 90–98, (2013)
F. Zheng, “Modelling Urban Travel Times”, Thesis Delft University of Technology, http://repository.tudelft654/Dissertation_Zheng.pdf (2011)
J.D. Lees-Miller, R.E. Wilson, and S. Box. “Hidden Markov Models for Vehicle Tracking with Bluetooth.” In Transportation Research Board 92nd Annual Meeting, no. 13–3032. (2013)
M. Friesen, R. Jacob, P. Grestoni, T. Mailey and R.D. McLeod, “Vehicular Traffic Monitoring using Bluetooth”, CCECE 2013
R. Cavaliere, P. Valleri, R. Kloibhofer, “The INTEGREEN approach for the assessment of environmental traffic management policies, 9th ITS European Congress, Dublin, Ireland, 4–7 June 2013
F. Biora, F. d’Aprile, and R. Marino, “A Large Scale Application for Bluetooth-based Travel Time Measurement in the Netherlands”, 19th ITS World Congress, Vienna, Austria, 22 to 26 October (2012)
J. Benavides, B.C.P. Demianyk, S.N. Mukhi, M. Laskowski, M.R. Friesen and R.D. McLeod, “Smartphone Technologies for Social Network Data Generation and Infectious Disease Modeling”, J. of Medical and Biological Engineering, 32(4): 235–244
L.M. Peterson, “Obtaining vehicle traffic information using mobile Bluetooth detectors”, https://www.google.com/patents/ US20120276847, Google Patents (2012)
Download references
Acknowledgments
The authors thank the City of Winnipeg Public Works Department for financial support, and in particular Mr. Doug Hurl and Mr. Luis Escobar. In addition, the financial support of NSERC and NSERC NCE Auto 21 is gratefully acknowledged.
Author information
Authors and affiliations.
Design Engineering, University of Manitoba, Winnipeg, MB, R3T 5V6, Canada
M. R. Friesen
Electrical and Computer Engineering, University of Manitoba, Winnipeg, MB, R3T 5V6, Canada
R. D. McLeod
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to R. D. McLeod .
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution License which permits any use, distribution, and reproduction in any medium, provided the original author(s) and the source are credited.
Reprints and permissions
About this article
Friesen, M.R., McLeod, R.D. Bluetooth in Intelligent Transportation Systems: A Survey. Int. J. ITS Res. 13 , 143–153 (2015). https://doi.org/10.1007/s13177-014-0092-1
Download citation
Received : 07 January 2014
Revised : 05 May 2014
Accepted : 19 May 2014
Published : 29 May 2014
Issue Date : September 2015
DOI : https://doi.org/10.1007/s13177-014-0092-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Bluetooth sensing
- Traffic monitoring
- Intelligent transportation systems
- Find a journal
- Publish with us
- Track your research
BLE Beacons in the Smart City: Applications, Challenges, and Research Opportunities
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Effect of Bluetooth headset and mobile phone electromagnetic fields on the human auditory nerve
Affiliation.
- 1 ENT Department, University of Verona, Verona, Italy; Department of Neurology, University of Verona, Verona, Italy.
- PMID: 23619813
- DOI: 10.1002/lary.24103
Objectives/hypothesis: The possibility that long-term mobile phone use increases the incidence of astrocytoma, glioma and acoustic neuroma has been investigated in several studies. Recently, our group showed that direct exposure (in a surgical setting) to cell phone electromagnetic fields (EMFs) induces deterioration of auditory evoked cochlear nerve compound action potential (CNAP) in humans. To verify whether the use of Bluetooth devices reduces these effects, we conducted the present study with the same experimental protocol.
Study design: Randomized trial.
Methods: Twelve patients underwent retrosigmoid vestibular neurectomy to treat definite unilateral Ménière's disease while being monitored with acoustically evoked CNAPs to assess direct mobile phone exposure or alternatively the EMF effects of Bluetooth headsets.
Results: We found no short-term effects of Bluetooth EMFs on the auditory nervous structures, whereas direct mobile phone EMF exposure confirmed a significant decrease in CNAPs amplitude and an increase in latency in all subjects.
Conclusions: The outcomes of the present study show that, contrary to the finding that the latency and amplitude of CNAPs are very sensitive to EMFs produced by the tested mobile phone, the EMFs produced by a common Bluetooth device do not induce any significant change in cochlear nerve activity. The conditions of exposure, therefore, differ from those of everyday life, in which various biological tissues may reduce the EMF affecting the cochlear nerve. Nevertheless, these novel findings may have important safety implications.
Keywords: Bluetooth headset; cochlear nerve action potentials; electromagnetic field; intraoperative monitoring; mobile phones.
© 2013 The American Laryngological, Rhinological and Otological Society, Inc.
Publication types
- Randomized Controlled Trial
- Cell Phone*
- Cochlear Nerve / physiopathology*
- Electromagnetic Fields / adverse effects*
- Evoked Potentials, Auditory / physiology*
- Middle Aged
Bluetooth Blog
Now available: new bluetooth market research.
- March 26, 2024
- Jason Marcel
- Ambient IoT , Audio Streaming , Auracast , Bluetooth Low Energy , Broadcast , Data Transfer , Device Networks , Electronic Shelf Label , LE Audio , Location Services
The Latest Bluetooth Market Research
For the last few years, the Bluetooth Special Interest Group (SIG) has been working with ABI Research – a global leader in analyzing, tracking, and forecasting the transformation of the smart device and IoT markets – to develop a wide range of market research note that highlight recent and upcoming Bluetooth ® technology trends and forecasts. These reports help global IoT decision makers stay up to date on the role Bluetooth technology can play in their technical roadmaps.
Below is a list of market research reports released within the last year.
2024 Bluetooth ® Market Update
Supported by updated forecasts from ABI Research and insights from several other analyst firms, this annual report features new market insights that help technology leaders and industry experts stay up to date on the latest Bluetooth trends.
The 2024 Bluetooth ® Market Update includes an overview of updated forecasts for LE Audio, Auracast™ deployments, and the transition from Bluetooth Classic Audio to LE Audio. The report also highlights the progression of new, high-volume markets, such as electronic shelf labels (ESL) and Ambient IoT.
Read the report
Auracast™ Broadcast Audio Retrofit Solutions and Opportunities
This report by ABI Research delves into the opportunity for public spaces to offer new Auracast™ augmented audio experiences and enhanced assistive listening to its occupants and visitors by using cost-effective retrofit Auracast™ solutions, accelerating wider adoption of Auracast™ transmitters as well as receiver devices. The report:
- Outlines various hardware options and solutions tailored to specific use cases
- Evaluates market potential across various venue types
- Maps specific use cases to venues that are particularly conducive to retrofit solutions
Download the report
The Ambient IoT – The Emergence of a New Class of Bluetooth ® IoT Devices
Over the past two years, the Ambient IoT has been a growing topic of discussion. This report from ABI Research and the Bluetooth SIG:
- Offers a definition for the Ambient IoT
- Outlines the targeted use cases
- Highlights the next steps needed to capitalize on the Ambient IoT opportunity.
The report also explains the central role of Bluetooth ® technology in addressing Ambient IoT use cases, characterized by its low power consumption, low cost, flexibility, interoperability, and scalability.
How the Bluetooth ® Electronic Shelf Label Standard Will Impact the Smart Retail Market
In this report, ABI Research explores how the recent arrival of the new Bluetooth ® Electronic Shelf Label (ESL) standard will help create an interoperable ESL ecosystem that can address many of the challenges being faced by retail and other environments. The research note:
- Summarizes the primary verticals that benefit from ESLs and the key use cases within each
- Deep dives into the retail market, including the growing pressures and market drivers within it as well as the benefits ESL can bring to retailers
- Outlines the challenges with previous ESL technologies and the reasons behind the demand for standardization
- Examines the benefits of the Bluetooth ESL standard and the impact it will have on ESL market forecasts
LE Audio: The Future of Bluetooth ® Audio
In this market research note, ABI Research outlines how the arrival of LE Audio will help establish new use cases and consumer experiences, open the audio ecosystem to new industry players, and enable the Bluetooth audio market to scale to new heights. This report:
- Maps the multi-strategy transition from Classic Audio solutions to dual-mode solutions to single-mode LE Audio solutions
- Outlines the path towards building a Bluetooth LE Audio ecosystem, including an overview of LE Audio device shipments by market segment
- Introduces new market opportunities enabled by the emergence of Auracast™ broadcast audio, including public and private broadcast use cases for consumer and assistive listening applications, along with early adoption forecasts
Check out more Bluetooth market research .
FEATURED REPORT
The 2024 Bluetooth ® Market Update provides updated forecasts and trends in key Bluetooth solution areas and highlights Bluetooth use cases that will drive future growth.
SEE THE FULL REPORT
- Member Blogs
- Case Studies
- Infographics
- Study Guides
Recently Released: New Trends for Bluetooth Device Networks
Though more commonly associated with audio streaming and wearable devices, Bluetooth ® technology also plays…

New Market Forecasts for Bluetooth Audio
Building on nearly 25 years of audio Bluetooth ® innovation, Bluetooth LE audio and Auracast™…

The 2024 Bluetooth ® Market Update examines the direction and adoption of Bluetooth technology.

The Latest Bluetooth Market Research For the last few years, the Bluetooth Special Interest…
Bluetooth Developer Journey
As a leading player in the semiconductor industry committed to the development of cutting-edge…

Auracast™ Broadcast Audio Continues to Make Headlines With Major Media
Auracast™ broadcast audio is a new Bluetooth ® capability that will deliver life-changing audio experiences.…

Auracast ™ Broadcast Audio Retrofit Solutions and Opportunities
This report by ABI Research delves into the opportunity for public spaces to offer…
Generic Health Sensor Design and Implementation Guide
The Generic Health Sensor (GHS) Design and Implementation Guide guides implementers of health sensor…
- SIG Working Group

Bluetooth Technology Is Pioneering the Hearing Aid Innovations of the Future Bluetooth技術が切りひらく補聴器イノベーションの未来
In an industry where innovation and accessibility intertwine, Panasonic has emerged as a pioneering…
![research articles bluetooth ABI Growth Chart.png 815076338[1]](https://www.bluetooth.com/wp-content/uploads/2024/03/ABI_Growth_Chart.png_8150763381-660x384.png)
How Can Bluetooth® Technology Enable Digital Transformation Across the Industrial IoT?
Internet of Things (IoT) have come to be synonymous with connected devices during this…
![research articles bluetooth shutterstock 1653733096[1]](https://www.bluetooth.com/wp-content/uploads/2024/03/shutterstock_16537330961-660x372.jpg)
How Bluetooth® NLC Standardizes Control for Smart Lighting
Discover how Bluetooth ® NLC is paving a new path for lighting control and making…
![research articles bluetooth packetcraft logo tagline[1]](https://www.bluetooth.com/wp-content/uploads/2024/03/packetcraft_logo_tagline1.png)
Auracast Vision Catches Mainstream Wind at CES 2024 - Bluetooth LE Audio Highlights
At CES 2024 in Las Vegas earlier this year, LE Audio-enabled products were showcased…

ReSound Nexia - Made for Auracast
ReSound Nexia is the industry-first hearing aid to connect to Bluetooth Low Energy Audio…

Developing Auracast ™ Receivers with an Assistant Application for Legacy Smartphones
This guide describes a standards compliant approach to developing Auracast™ receivers that work with…

Revolutionizing Online Order Fulfillment: Managing Mis Shipments
Discover how Wiliot, an ambient Internet of Things (IoT) pioneer, is revolutionizing the online…
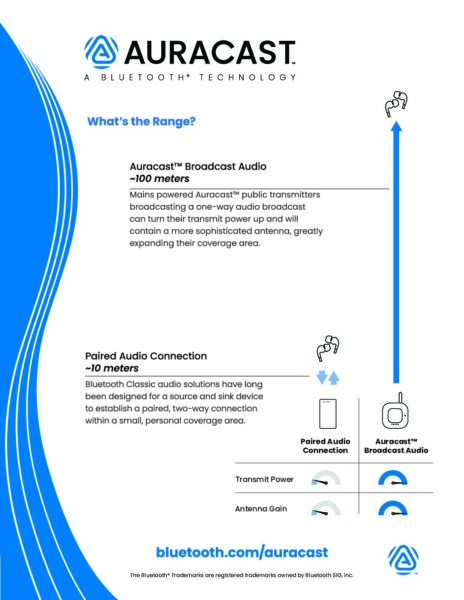
What's the Range of Auracast ™ Broadcast Audio?
Get the answer to the question everyone’s asking. Find out what the coverage area…
![research articles bluetooth 2312 CES Handout Images FINAL existing pdf 464x600[1]](https://www.bluetooth.com/wp-content/uploads/2024/01/2312_CES_Handout-Images_FINAL-existing-pdf-464x6001-1.jpg)
Can You Add Auracast ™ Support to Existing Devices?
Are you waiting for native Auracast™ support? You might not have to. Find out…
![research articles bluetooth 2312 CES Handout Images FINAL unlimited pdf 464x600[1]](https://www.bluetooth.com/wp-content/uploads/2024/01/2312_CES_Handout-Images_FINAL-unlimited-pdf-464x6001-1.jpg)
Is the Number of Auracast ™ Receivers Really Unlimited?
Not convinced? Learn how an unlimited number of Auracast™ receivers can join a single…

The Ambient IoT - The Emergence of a New Class of Bluetooth ® IoT Devices
Over the past two years, the Ambient IoT has been a growing topic of…

ABI Snapshot – Auracast ™ Retrofit Solutions and Opportunities
Auracast™ product momentum is growing, and one emerging category is Auracast™ retrofit transmitters.

Auracast TM Product Momentum Is Building
Bluetooth SIG CMO Ken Kolderup shares some exciting news about Auracast™ product availability, along…

Helping Sony Music Solutions Inc. (SMS) Create Memorable Concert Experiences with the FreFlow LED Light System
When we talk about the things we missed during the shutdowns that were part…

Retail Pharmacy
A leading retailer is collaborating with Wiliot, an ambient Internet of Things (IoT) pioneer,…
The Bluetooth ® Low Energy Primer
Are you new to Bluetooth Low Energy? Learn about its constituent parts, features, and how it works.

Introducing Bluetooth ® LE Audio
Now available for free digital download, get your copy of this in-depth, technical overview of the LE Audio specifications.
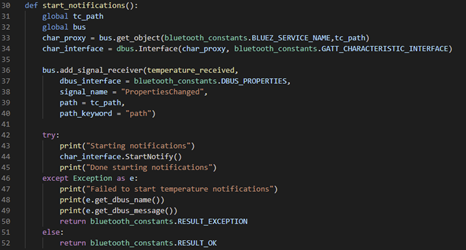

Bluetooth ® Technology for Linux Developers
Learn how to use the interprocess communication system D-Bus and the BlueZ APIs to create Bluetooth applications for Linux computers.
Designing and Developing Bluetooth ® Internet Gateways
Learn about Bluetooth ® internet gateways, how to make them secure and scalable, and design and implement your own...
I need help with...
- Becoming a Bluetooth Member
- Qualifying & Declaring My Product
I’m looking for something else:
- KnowledgeBase and Support Requests
Have a suggestion, question, or feedback?
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- 03 April 2024
The EU’s ominous emphasis on ‘open strategic autonomy’ in research
You have full access to this article via your institution.
South Korean science minister Lee Jong-ho and European commissioner for research Iliana Ivanova celebrate South Korea joining Horizon Europe in March. Viewing research through a security lens makes it harder for other non-EU countries to follow. Credit: HANDOUT/EPA-EFE/Shutterstock
Last month, the European Commission published a ‘course correction’ for its Horizon Europe research fund, which is worth around US$100 billion over seven years, from 2021 to 2027. It’s not easy to make major alterations at the mid-way point of such a large enterprise, whose two predecessors funded 1.5 million collaborations across 150 countries. But the European Union has made substantial changes in the fund’s latest strategic plan that researchers need to be aware of.
One of the most important is a phrase now peppered throughout the document: open strategic autonomy.
This political concept means that the EU will strengthen its self-sufficiency while remaining open to cooperation with other regions. The term is not new — in Horizon Europe’s first strategic plan (for 2021–24), open strategic autonomy was one of four priority areas for funded projects, alongside the green transition, the digital transition and building a more resilient, competitive, inclusive and democratic Europe.

Horizon Europe turmoil changed the lives of these five scientists
The EU has reduced these four priorities to three — and open strategic autonomy has been upgraded. It is now an overarching theme for all research funded by Horizon Europe from 2025 to the end of 2027. Barring a sudden outbreak of world peace, this mode of thinking and action is expected to influence — if not dominate — the next iteration of Horizon Europe, called FP10, which will start in 2028.
This change of priorities is concerning researchers. The European Research Council (ERC), which funds investigator-led research and is part of Horizon Europe, issued a statement at the end of January , saying: “The ERC’s independence and autonomy must be protected under FP10.”
But for now, just as a tanker cannot be turned around at full speed, Horizon Europe retains key elements of the original plan. The EU wants to maintain its climate funding (35% of the total Horizon Europe budget) and increase biodiversity funding to 10% of the budget, which are both welcome decisions. It is also committed to the idea of moonshot-style missions: specific goal-oriented funds to tackle urgent global challenges, such as improving soil health and establishing carbon-neutral cities. It plans to meaningfully integrate social-sciences and humanities researchers into collaborations — not just include them as afterthoughts — and to improve diversity and equity. And it is continuing to reach beyond its borders.

War shattered Ukrainian science — its rebirth is now taking shape
Last week, it was announced that South Korea’s researchers will be able to participate in EU-funded projects related to global challenges. Last November, Canada also joined the programme. And New Zealand before that. The United Kingdom’s researchers are also back, after a gap of nearly four years after Brexit. These are, broadly speaking, all representative democracies with which EU countries have defence- and security-cooperation agreements. The principle of open strategic autonomy will make it more difficult to cooperate with countries for which this is not the case.
The EU is obviously responding to the world-changing events of the past decade. When discussions about the first iteration of Horizon Europe were beginning, wars, pandemics and the election of populist leaders mostly seemed to be twentieth-century concerns. As the EU — and its international partners, too — responded to levels of instability that few were expecting, heavier emphasis on a research agenda to strengthen supply chains, ensure resilience of essential infrastructure and establish more manufacturing at or closer to home is understandable.
But a security mindset cannot be baked into what is fundamentally an open and autonomous research cooperation fund. In addition to sharing research and cooperating in the development of new technologies, Horizon Europe — originally called the Framework Programme — was created to re-establish trust between Europe’s nations in the second half of the twentieth century. It was part of a larger effort to prevent them from going to war with each other .
Strategic plans have to remain flexible. Circumstances change, and it’s important to be able to make adjustments when that happens. But making open strategic autonomy a theme for all EU funding is neither sensible nor desirable.
Nature 628 , 8 (2024)
doi: https://doi.org/10.1038/d41586-024-00962-4
Reprints and permissions
Related Articles

- Climate change
Don’t dismiss carbon credits that aim to avoid future emissions
Correspondence 02 APR 24

A 2023 hurricane caught Mexico off guard: we must work together to prepare better
Comment 02 APR 24

Melting ice solves leap-second problem — for now
News & Views Forum 27 MAR 24

Time to sound the alarm about the hidden epidemic of kidney disease
Editorial 03 APR 24

Sam Bankman-Fried sentencing: crypto-funded researchers grapple with FTX collapse
News 28 MAR 24

Larger or longer grants unlikely to push senior scientists towards high-risk, high-reward work
Nature Index 25 MAR 24
Cuts to postgraduate funding threaten Brazilian science — again
Correspondence 26 MAR 24
Don’t underestimate the rising threat of groundwater to coastal cities

‘Exhausted and insulted’: how harsh visa-application policies are hobbling global research
World View 26 MAR 24
Faculty Positions, Aging and Neurodegeneration, Westlake Laboratory of Life Sciences and Biomedicine
Applicants with expertise in aging and neurodegeneration and related areas are particularly encouraged to apply.
Hangzhou, Zhejiang, China
Westlake Laboratory of Life Sciences and Biomedicine (WLLSB)
Faculty Positions in Chemical Biology, Westlake University
We are seeking outstanding scientists to lead vigorous independent research programs focusing on all aspects of chemical biology including...
School of Life Sciences, Westlake University
Faculty Positions in Neurobiology, Westlake University
We seek exceptional candidates to lead vigorous independent research programs working in any area of neurobiology.
Head of the histopathology and imaging laboratory
GENETHON recruits: Head of the histopathology and imaging laboratory (H/F)
Evry-Sud, Evry (FR)
Seeking Global Talents, the International School of Medicine, Zhejiang University
Welcome to apply for all levels of professors based at the International School of Medicine, Zhejiang University.
Yiwu, Zhejiang, China
International School of Medicine, Zhejiang University
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Experts expanding the reach of engineering research
Between the roles of students learning in labs and the faculty who chart the course of that research, a group of specialists give the research enterprise incredible strength.
- Alex Parrish
- Share on Facebook
- Share on Twitter
- Copy address link to clipboard
Addressing global challenges requires a strong team, and the work that occurs between the formation of an idea and the presentation of a solution demands skilled hands.
Many of the research faculty who direct labs at Virginia Tech have projects in motion with the potential of making a better world, but that research requires extensive trial and error. To best complete the work that happens between the beginning and the end of those projects, the engagement of skilled experts is essential.
Those same skilled experts also bring mastery into the sphere of educating, standing beside students at a lab bench or lending their knowledge to the next generation of engineers and scientists.
A little more than 5 percent of all employees at Virginia Tech are identified as a postdoctoral associate, research associate, research assistant professor, or postdoctoral associate. Some are attached to specific projects; others work broadly with faculty who are managing a large portfolio.
In most cases, the work comes after acquiring a doctorate in the field, so expertise is firmly established. These are critical positions in the Department of Mechanical Engineering , which hosts more than 30 labs that push the boundaries of innovation through funded research from agencies both domestic and international. Two people working in that realm are Amanda Leong and Sibin Kunhi Purayil.

The nuclear option: Amanda Leong
The nuclear engineering program within the mechanical engineering department has several labs in Blacksburg, and two of them house the work of Professor Jinsuo Zhang. To manage multiple projects and students at two sites, Zhang relies on Research Assistant Professor Amanda Leong.
Leong came to Virginia Tech after finishing her bachelor’s degree in mechanical engineering at Ohio State, jumping straight into the doctoral program in the College of Engineering with Zhang. She had started with Zhang’s lab when both were in Ohio, where she first started working in nuclear engineering.
She followed the research to Virginia, completing her Ph.D. and learning her way around Blacksburg labs. Her own research focus is on energy, particularly the area of material corrosion in advanced nuclear reactors and the use of molten salt as a fuel or coolant in energy plants.
In her role as a research assistant professor, Leong mentors two senior design teams with projects in her area of expertise, one in the Department of Mechanical Engineering and one in the Department of Material Science and Engineering . In addition to those teams, she co-supervises the lab’s students’ and postdocs’ research and helps address questions as they arise. She also serves as main advisor to an undergraduate research team.
“Dr. Leong does the work of the lab directly,” said Zhang. “Because of her work, we are able to get solutions more quickly when students have issues or problems or when they develop new ideas and new research directions."
She also has continued her own investigations and an increase in the number of published papers that she has produced has followed.
“When you’re a student, you usually just work on one project,” Leong said. “I oversee several.”
With her background in the field, Leong also helps analyze the data coming from the team’s research, quickly filtering issues that could derail the learning process so that students can more easily interpret what they’re seeing.
“Because I was exposed to research earlier, I pick up some things that newer people might not be able to see,” she said. “I really enjoy teaching students, seeing their light bulbs come on. I love solving problems together.”
Leong is enjoying the work she has found in Zhang’s lab, and her hopeful long-term plan is to find her way to a tenure-track research and teaching position.

Bringing solar energy home: Sibin Kunhi Purayil
Sometimes, a research scientist with specialized skills is needed for a specific project. This is how Sibin Kunhi Purayil came to work for Ranga Pitchumani , the George R. Goodson Professor of Mechanical Engineering, in the Advanced Materials and Technologies Laboratory .
Purayil earned his Ph.D. in India and worked at the National Aerospace Laboratory before being recruited for Pitchumani’s solar energy research at Virginia Tech. Pitchumani is editor-in-chief of the peer-reviewed journal Solar Energy and was chief scientist of the SunShot Initiative , a federal grant challenge aimed at making solar energy more widely instituted.
Pitchumani received funding in 2018 from the U.S. Department of Energy for a new project to develop high efficiency solar absorber coatings viable at high temperatures, and it was a perfect fit for Purayil’s skill set.
The young scientist spent a lot of time during his 2019 postdoctoral work developing nanometer-thick flexible, transparent, and conductive coatings. These could be used for space, flexible electronics, and solar energy applications employing sophisticated thin film deposition techniques, and he was eager for new opportunities.
Purayil sought a position that would allow him to continue making contributions to the greater environmental good: reduce the carbon dioxide emissions that can result from energy production.
“My goal was to, in my way, reduce carbon emission and work toward global carbon neutrality,” Purayil said. “This project has a lot of possibilities, and if we can improve the solar absorber’s efficiency, it could make a significant contribution to that cause.”
Pitchumani’s project – involving harvesting solar thermal energy at high temperatures with high efficiency - was a great match for Purayil’s goal. Purayil used a novel approach utilizing highly textured, high-temperature-stable solar absorber coatings designed to operate at temperatures exceeding 750 degrees celsius in an air atmosphere. The coatings they chose were made through cost-effective and industrially viable deposition techniques, meaning the technology will be more readily transferable from lab to practice.
Purayil’s prior work with coatings and materials had equipped him with the experience Pitchumani needed. Together they have created the most efficient absorber of solar energy for high temperature solar thermal processes, be it power generation, providing industrial process heat, or producing solar fuels, all contributing to a decarbonized future — and to Purayil’s professional goals. Pitchumani and Purayil have filed for a patent on this innovation.
Better results through expert teams
One of the advantages of the research enterprise at Virginia Tech lies in its blend of experts with budding inventors. By employing specialists who both innovate and teach, a full body of knowledge is being passed on to the next generation of engineers.
In the cases of Leong and Purayil, both have had the opportunity to take their proven acumen in academics to the next level, giving back to learning, and building their own body of work. Working beside professors with long histories in their fields provides insights for how that body of work fits into the bigger picture while finding solutions to the world’s most complex problems.
Chelsea Seeber
540-231-2108
- Affordable and Clean Energy
- College of Engineering
- Green energy
- Materials Science and Engineering
- Mechanical Engineering
- Nuclear Engineering
- Sustainability
- Sustainable Cities and Communities
- United States Department of Energy
- Virginia Tech Global Distinction
Related Content

An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Sensors (Basel)

Secure Bluetooth Communication in Smart Healthcare Systems: A Novel Community Dataset and Intrusion Detection System †
Mohammed zubair.
1 Kindi Center for Computing Research, Qatar University, Doha P.O. Box 2713, Qatar
2 Department of Computer Science, Qatar University, Doha P.O. Box 2713, Qatar
Ali Ghubaish
3 Department of Computer Science and Engineering, Washington University in St. Louis, St. Louis, MO 63130, USA
Devrim Unal
Abdulla al-ali, thomas reimann.
4 Copenhagen Emergency Medical Service, 3400 Hillerød, Denmark
5 Department of Emergency Management, Jacksonville State University, Alabama, AL 36265, USA
Guillaume Alinier
6 Hamad Medical Corporation Ambulance Service, Doha P.O. Box 3050, Qatar
7 School of Health and Social Work, University of Hertfordshire, Hatfield AL10 9AB, UK
8 Weil Cornell Medicine, Doha P.O. Box 24144, Qatar
9 Faculty of Health and Life Sciences, Northumbria University, Newcastle upon Tyne NE1 8ST, UK
Mohammad Hammoudeh
10 Information and Computer Science Department, King Fahd University of Petroleum and Minerals, Dhahran 31261, Saudi Arabia
Junaid Qadir
Associated data.
The BlueTack dataset is available at: IEEE Dataport under the title BlueTack , doi: https://dx.doi.org/10.21227/skhs-0b39 .
Smart health presents an ever-expanding attack surface due to the continuous adoption of a broad variety of Internet of Medical Things (IoMT) devices and applications. IoMT is a common approach to smart city solutions that deliver long-term benefits to critical infrastructures, such as smart healthcare. Many of the IoMT devices in smart cities use Bluetooth technology for short-range communication due to its flexibility, low resource consumption, and flexibility. As smart healthcare applications rely on distributed control optimization, artificial intelligence (AI) and deep learning (DL) offer effective approaches to mitigate cyber-attacks. This paper presents a decentralized, predictive, DL-based process to autonomously detect and block malicious traffic and provide an end-to-end defense against network attacks in IoMT devices. Furthermore, we provide the BlueTack dataset for Bluetooth-based attacks against IoMT networks. To the best of our knowledge, this is the first intrusion detection dataset for Bluetooth classic and Bluetooth low energy (BLE). Using the BlueTack dataset, we devised a multi-layer intrusion detection method that uses deep-learning techniques. We propose a decentralized architecture for deploying this intrusion detection system on the edge nodes of a smart healthcare system that may be deployed in a smart city. The presented multi-layer intrusion detection models achieve performances in the range of 97–99.5% based on the F1 scores.
1. Introduction
Cities are being transformed into smart cities via Internet-of-Things (IoT) technology. Smart cities use technologies for sensing, networking, and computation to enhance the quality of life and well-being of inhabitants. Such smart cities also require new service-centric computing paradigms for next-generation networks (5G, 6G, and beyond) [ 1 ]. While there are numerous networking technologies available for long-range communications, the most widely used technology for close-proximity communications is Bluetooth. Bluetooth is well suited for operations on resource-constrained mobile devices due to its low power consumption, low cost, and support for multimedia, such as data and audio streaming. Bluetooth is also widely used in smart healthcare systems to enable untethered wireless communications between smart healthcare devices. Recently, Bluetooth was prominent in its adoption for contact-tracing applications in the fight against the COVID-19 global pandemic [ 2 ].
By the year 2030 [ 3 ], the number of IoT devices is expected to surge by 124 billion. Moreover, the healthcare economy statistics predict that the market for IoT devices will grow from USD 20 billion in 2015 to USD 70 billion in 2025. It was also reported that 30.3 % of the IoT devices in use are in the health sector [ 4 ]. The massive deployment of IoT devices in heterogeneous networks with multiple technologies and protocols (such as Wi-Fi, long-term evolution (LTE), Bluetooth, and ZigBee) makes the task of securing such networks very complex. Research from the Information Systems Audit and Control Association (ISACA) [ 5 ] on smart cities identified the security of IoT devices as important, as numerous smart city critical infrastructure (CI) concepts (e.g., intelligent transport, healthcare system, and energy distribution) rely on the robustness and security of smart technologies and IoT devices [ 6 ].
As the number of Internet of Medical Things (IoMT) devices increases, the network becomes congested, which leads to bandwidth and latency bottlenecks [ 7 ]. For instance, an IoMT device sends data to a medical professional for regular analysis. This transmission of data to the cloud can potentially cause latency and bandwidth congestion in the communication path [ 8 ], which could endanger the life of the patient. To address this challenge, the edge cloud concept has emerged for the IoMT paradigm. An edge cloud improves efficiency and provides more reliability for the smart healthcare system. The quick response time and reduced energy consumption will result in longer battery life for medical devices and reduce the usage of network bandwidth [ 9 , 10 ].
The exponential growth of IoT devices and the massive interconnectivity between such devices greatly opens up the potential attack surface for smart healthcare services that may be exploited by malicious actors. IoT devices are vulnerable to various medium- and high-severity attacks [ 11 ]. Various vulnerabilities allow the intruders to perform a wide range of attacks, such as denial of service (DoS), distributed DoS (DDoS), man-in-the-middle (MITM), data leakage, and spoofing. These attacks result in the unavailability of system resources and can lead to physical harm to the individuals when the patient is ambulance-bound or hospital-bound. According to a report from the Global Connected Industries Cybersecurity, 82 % of healthcare facilities experience cyber-attacks, amongst which, 30 % target IoT devices [ 11 ]. The potential weakness in the network, IoT device, and protocol allows the attackers to access the network completely in an unauthorized way (e.g., Mirai attack) [ 12 ]. Apart from these cyber-attacks, insecure operating systems, and application vulnerabilities are other major threats to the healthcare system. Investigations show that 83 % of IoT devices run on outdated operating systems, and around 51 % of the cyber threats in the health sector concern imaging devices, which lead to the disruption of communication between patients and medical professionals. Moreover, 98 % of IoT device traffic is in plain text that can be intercepted by adversaries.
Traditional security mechanisms cannot be enforced in the IoT network because the network protocol stack itself may have numerous vulnerabilities. Zero-day attacks are very difficult to be detected by traditional security mechanisms due to computational expenses, which do not go well with the resource-constrained nature of typical IoT devices [ 13 ]. Conventional perimeter security controls only defend against external attacks, but they fail to detect internal attacks within the network. An intelligent and faster detection mechanism is required to guarantee the security of the IoT network for countering new threats before the network is compromised.
In this paper, our focus is on the security of Bluetooth communication in smart healthcare systems. After reviewing the significant security problems, we focus on the detection of wireless attacks against IoMT. Wireless attacks are performed when the data are at rest or in transmission from one device to another device in a wireless medium over different channels using various protocols, namely Bluetooth low energy (BLE), Bluetooth basic rate/ enhanced data rate (BR/EDR), Wi-Fi, long-range (LoRA), etc. The openness of the wireless network poses threats to the entire network and can end up compromising the entire system. The attacker may perform various attacks, such as peer-to-peer, denial-of-service, eavesdropping, man-in-the-middle (MITM), and authentication attacks to take over the IoMT device or complete network. The main contributions of this study are as follows:
- We curated a novel first-of-its-kind BlueTack dataset for Bluetooth-based IoT attacks. The BlueTack dataset consists of popular attacks against Bluetooth BR/EDR or Bluetooth classic protocols, namely: Bluesmack, DoS, DDoS, and similar attacks, such as DDoS and MITM attacks on the BLE protocol. To the best of our knowledge, this is the first intrusion detection dataset for the Bluetooth classic protocol and BLE. The BlueTack dataset will be made publicly accessible as described in the Dataset Availability Statement.
- A secure and scalable framework for the deployment of an intrusion detection system(s) (IDS) on the edge nodes of IoT-based healthcare systems in smart cities. The framework guarantees quicker identification of malicious activities to ensure the safety of critically ill patients transported by ambulances.
- A multi-layer intrusion detection model using deep learning (DL) to protect the edge nodes of the smart healthcare IoMT system. Since IoMT is composed of several resource-constrained devices, deploying the DL model on the IoMT device itself for advanced functionality is impractical. Hence, The IDS is divided into two layers: Layer _ 1 (where preprocessing is performed on IoMT devices or the edge node) and Layer _ 2 (a standalone GPU capability device in which the DL model is deployed). The proposed DL-based IDS achieves 99 % accuracy while being deployed in a real-time scenario.
The flow of this paper is structured as follows: Section 2 provides an overview of related work, followed by Section 3 , which illustrates the proposed model, architecture, and dataset in detail. We show the results of the performance evaluation of the proposed model in Section 4 . Finally, the work is concluded with future directions in Section 5 .
2. Related Work
Before we introduce the methodology, we discuss the background and related work available in the literature.
2.1. Security of IoMT
IoMT devices perform diverse tasks in smart healthcare systems, such as recording electrical impulses through electrocardiograms (ECGs) or monitoring blood glucose or blood pressure. For ambulance-bound patients, IoMT devices monitor the patient’s activity, save critical information about the patient’s physiological signals, and trigger alerts to the medical staff inside the ambulance or a remote monitoring device through the cloud. As the complete information of the patient flows in and out through the IoMT gateway [ 14 ], securing the IoMT attack surface assumes critical importance. An attacker may target the IoMT gateway to manipulate information before sending it to the doctor or to launch denial of service attacks to make the information unavailable. Such malevolent activities can put the patient’s life at risk. Rasool et al. [ 15 ] reviewed various security issues of IoMT devices. The authors describe the vulnerabilities that exist in these devices, which can be exploited by attackers easily. In our article, we consider internal and external threats that are targeted against IoMT infrastructure. Since these devices are severely resource-constrained, it is easy to render these devices unavailable by draining their battery with devastating implications [ 16 ]. Thus, our focus in this paper is on attacks that may drain the batteries of these devices or that make the devices unavailable due to multiple ping requests.
2.2. Communication in Smart Healthcare System
The typical architecture of a smart healthcare system is shown in Figure 1 . A typical smart healthcare system comprises three domains: IoT domain, cloud domain, and user domain, which generate data, store data, and make diagnoses, respectively. The IoT domain consists of wireless medical devices, actuators, sensors, gateways, and other devices. Here, the focus is on acquiring patients’ data from IoMT devices and transmitting it to the cloud for storage and subsequent access. The cloud domain is stratified by the edge and core cloud. The edge cloud is placed on the premises of the medical facility to ensure continuous connectivity and low latency, in addition to quicker diagnosis of acute cases. The core cloud provides massive storage and comprehensive analysis of data, and it helps in the diagnosis of current symptoms based on previous related records.

The use of Bluetooth and related protocols (BLE: Bluetooth low energy; BR/EDR: Bluetooth basic rate/enhanced data rate) in a typical smart healthcare system for communication between electronic patient care record device (EPCRD) and other entities over the edge and the cloud.
During IoMT communication, the vital information of a patient is maintained by an electronic patient care record device (EPCRD), which is commonly known as a Toughpad. It has the capability of integrating different communication protocols and it acts as a gateway for Bluetooth, Wi-Fi, and long-term evolution (LTE) communication. Furthermore, the EPCRD acts as an edge device that allows and enables the technologies for computation at the edge of the healthcare network. It accomplishes the tasks of caching, processing storage, computation offloading, request distribution, and delivery of the services from the cloud end to the user end. In our proposed approach, we leverage edge cloud technology and deploy the IDS on the edge nodes of the healthcare system. The user domain delivers the processed data from other domains to the authorized clinical staff. Integration and streaming of vast volumes of data from different sources are visualized in various forms, such as graphics, images, tabular, and other representations.
Medical devices (such as defibrillators and insulin pumps) that are continuously linked with the patient for medical treatment are referred to as active medical device(s) (AMD). On the other hand, medical devices (such as home monitoring devices and medical beds) whose focus is on periodic monitoring of the patient physical condition and report generation are called passive medical device(s) (PMD). Wireless communication technologies are adopted for communication in IoT devices such as near-field communication (NFC), RFID, Wi-Fi, Bluetooth, LTE, and LoRA. Various IoMT devices use different wireless technologies. Most of the AMD and PMD utilize Bluetooth classic, V4.X, and V5. Bluetooth technology provides a generic profile for medical IoT devices to use the 2.4 GHz frequency band, as recommended by the international telecommunication unit (ITU) [ 17 ]. Some of the basic differences between BR/EDR and the BLE are showcased in Table 1 .
Technical details of Bluetooth technology.
Bluetooth-enabled devices have two modes of operation. In the single mode, a BLE device cannot interface with a device that is operating on BR/EDR, and vice versa. Whereas in dual-mode, both BR/EDR and BLE devices can communicate with each other. However, the major concern is about security and privacy in all Bluetooth versions. In this paper, we focus on the detection of attacks against the BR/EDR and BLE, since the medical sensor and data collection devices in the considered testbed utilize this version of Bluetooth.
2.3. Vulnerabilities in the Bluetooth Protocols
The major vulnerability factor in Bluetooth devices is the version that is used for communication. Table A1 in the Appendix A describes the vulnerabilities and security flaws of Bluetooth devices for different versions [ 18 ]. Few of the known vulnerabilities have been identified by researchers, such as MITM, Bluesmack, battery drain attacks, and backdoor attacks [ 19 ]. Recently, researchers identified the “SweynTooth” vulnerability affecting implantable medical devices (e.g., insulin pumps, pacemakers, and blood glucose monitors) and hospital equipment (e.g., patient monitors and ultrasound machines) that work on BLE [ 20 ]. The Bluetooth protocol has problems due to the encryption key length and improper storage of the link keys can be potentially manipulated by the adversary [ 12 ].
2.4. Intrusion Detection Systems
Some prior research studies on intrusion detection system(s) (IDS) dedicated to the cyber-physical system [ 21 ] or smart environments using the Wi-Fi protocol against DoS attack [ 21 ] have adopted various AI techniques, such as ML and DL. One such approach, Ref. [ 22 ], proposed a hybrid model that is based on the principal component analysis (PCA) and information gain (IG) incorporating the support vector machine (SVM), multi-layer perceptron (MLP), and instance-based learning models to identify the intrusions in the network. The model is trained and tested using the NSL-KDD, Kyoto 2006+, and ISCX 2012 datasets, and the optimal features are selected using an ensemble classifier. However, the performance of the model is evaluated with some publicly available datasets, which are not real-time datasets. Sawarna et al. [ 23 ] proposed an efficient IDS based on the deep neural network (DNN) using the principle component analysis–grey wolf optimization (PCA-GWO); it eliminates adversarial activities by providing faster alerts. This research was conducted to address the problem of data dimensionality for publicly available huge datasets. They tested the NSL-KDD dataset on various ML and DNN models to detect anomalies, among which the best accuracy was attained by the DNN. Baburaj et al. [ 24 ] proposed a cloud-based healthcare system using an SVM model to predict the health condition of a patient. The confidential data were accessed only by a legitimate user. This approach focused on data mining techniques using ML models, but not identify the anomalies in the system.
Likewise, a supervised approach for detecting intrusions in IoT devices in a smart home was proposed by Eanthi et al. [ 25 ]. In this approach, a lightweight standalone three-layer IDS framework is built using a decision tree (DT) classifier with promising results. Nevertheless, the evaluation of the proposed model is based on a simulation performed on the open-source Weka tool and the effectiveness of the IDS is not tested against real-time traffic and attacks.
2.5. IDS for Bluetooth Enabled Systems
Very few researchers have focused on the security perspective of Bluetooth technology, especially intrusion detection. Various attacks against Bluetooth devices are discussed below to emphasize the need for effective intrusion detection for Bluetooth-enabled medical IoT devices. Bluetooth technology provides a generic profile for the IoMT devices and it uses the 2.4 GHz frequency. It is identified as an attractive protocol for the healthcare system due to its robustness, lesser power consumption, low cost, suitability for short-distance communication, and support for data and audio streaming. Moreover, it helps in the IoT domain for machine-to-machine (M2M) communication [ 26 ]. Compromising the IoMT devices could lead to sensitive patient information being revealed through the interception and decoding of the data and audio/video streaming packets. An IDS detects malicious activities or policy violations that bypass the security mechanism on a network and is the process of monitoring and detecting unauthorized events intruding on the network. An intruder is one who escalates the privileges of the users to gain access to data or services or to control the entire network. Bluetooth-enabled systems require a different approach and standard IDS developed for other protocols are not effective due to the difference in traffic patterns and the highly constrained nature of Bluetooth devices [ 27 ].
Haataja et al. [ 28 ] proposed a Bluetooth intrusion detection and prevention system based on a set of rules by investigating Bluetooth security to discover malicious communication on the Bluetooth network. Krzysztoń et al. [ 29 ] proposed a detection system to identify the malicious behavior of Bluetooth traffic in a Bluetooth mesh network. Multiple watchdog nodes are used for cooperative decisions in different areas of the mesh network. Malicious activities are detected based on the received signal strength indicator (RSSI). However, this model encountered the problem of modeling the transmission range and RSSI parameters with obstacles, such as furniture and walls. This detection mechanism was not deployed to a variety of attacks and was evaluated in a simulated environment.
Similarly, Satam et al. [ 30 ] built a Bluetooth IDS (BIDS), where the normal behavior of the Bluetooth traffic was defined based on the n-gram approach, and malicious traffic was classified using traditional ML algorithms. This method attained the highest precision of about 99.6 % and recall of 99.6 % against DoS attacks. Yet, the effectiveness of the IDS was not tested against different datasets and other attacks. An anomaly-based intrusion detection system was proposed by Psatam et al. [ 31 ] to detect multiple attacks on the Bluetooth protocol using ML models by following the zero-trust principle. Nevertheless, the model was not tested using different attacks and datasets. Newaz et al. [ 32 ] focused on the detection of the BLE for multiple attacks using ML models to identify the abnormal behavior of the BLE traffic from the normal traffic pattern. The evaluation of the model was done on their own real-time traffic for an ideal dataset but was not tested on other datasets.
From the above literature and Table 2 , it is observed that the existing IDS approaches that are dedicated to healthcare IoT systems are at the initial stage of development. Few of the proposed IDS have validated their models on the data of the network simulation (dataset) or on a small number of IoT devices, but they have not been tested on multiple datasets. Moreover, these proposed IDS models detect malicious activities on the network by identifying the traffic patterns as normal or abnormal. It is also important to identify the various types of attacks on the network. In the below subsection, we describe the healthcare system in use by this paper and the Bluetooth technology (BR/EDR and BLE) deployed.
Various BIDS approaches in comparison to our proposed models. Our Bluetooth intrusion detection covers both Bluetooth classic and Bluetooth low-energy protocols.
3. Methodology
To understand the application of the proposed architecture, we consider a scenario of an IoMT system (i.e., smart healthcare system) that comprises multiple IoMT devices as shown in Figure 2 . Vital information from the IoMT devices is transferred to edge devices and the cloud and is further sent to the medical staff.

Architecture of the proposed security framework. The proposed system involves an edge cloud for reducing request/response delays. The IDS is multi-level and suits the resource restrictions of IoMT devices.
3.1. Scalable Architecture
By considering the significant security mechanisms, we designed a scalable architecture to deliver appropriate patient details to the medical experts from patient care efficiently and without manipulation, i.e., tampering. Our ultimate goal is to provide a security mechanism to detect malicious activities against Bluetooth communication on the edge node. The proposed architecture has enforced security policies, and detection mechanisms at the edge cloud and edge nodes to ensure fast response and secure emergency services. Edge computing helps to process the data efficiently with a quicker response time and assists with the deployment of the IDS. Figure 2 represents the proposed architecture of smart healthcare for detecting malicious behaviors of ambulance-bound, Bluetooth-enabled IoT medical devices in the smart healthcare system.
As the complete information of the patient flows in and out through the medical IoT gateway, it allows for a potential attacking surface to compromise the complete system by (1) targeting the medical IoT gateway to manipulate information before sending it to the medical professional or by (2) launching DoS/DDoS or MITM attacks to make the information manipulated or unavailable. Such malevolent activities can potentially put the patient’s life at risk. To avoid such abrupt manipulation of the information, we enforced a multi-layer intrusion detection model on the edge nodes of the healthcare system. The detection system comprises two layers, namely, Layer _ 1 and Layer _ 2 . Layer _ 1 is responsible for gathering patient information through a gateway and performing the preprocessing, feature engineering, and feature selection techniques using various ML algorithms. Layer _ 2 will detect the abnormal activities of the Bluetooth traffic on the edge node using a DNN classifier. Next, we describe in detail the features of each layer:
3.1.1. Layer _ 1
Layer _ 1 receives data from various medical IoT devices. The data from IoT devices is received at medical IoT gateways to analyze and store on the edge node. The fetched information is deeply analyzed and processed before it is transmitted to the medical professional for diagnosis. On this layer, preprocessing, feature engineering, and feature selection techniques using various ML algorithms are performed. Data preprocessing helps to provide the privacy of the medical information from the IoT devices because the information received from IoT devices is in plain text that can be intercepted by adversaries to perform medium- and high-severity attacks [ 34 ]. Data preprocessing is performed to transform actual data into data compatible with ML/DL models. For this process, we used numericalization (where a string is converted into integer (stoi), and then encoded into tokenized sentences before feeding to any model) and normalization. Data preprocessing helps the model to be trained and tested quickly. It also increases the accuracy of classification. We provide a detailed explanation of these stages below.
Eliminating/Dropping features : While capturing the traffic, we eliminated some information, such as source and destination information, due to two major issues, firstly, in some scenarios, it is difficult for the sniffer to collect this information [ 33 ], while in other cases, the adversary may spoof its address giving wrong information. In both cases, the classifier attempted to misclassify the traffic by replacing the missing values with some random numbers, giving higher false positives and true negatives. Likewise, we eliminated some other unimportant and irrelevant features.
Feature selection : In this process, significant features were selected from the dataset by applying various feature selection techniques [ 35 , 36 ]. Feature selection increases the model performance, decreases computational cost, and also increases storage efficiency. Additionally, using appropriate features reduce the problem of overfitting.
There are various ML approaches for selecting features, such as filter-based methods, wrapper methods, embedded, and statistical methods. In the univariate selection technique, a statistical test is applied to each feature to select the features, which have a strong bond with the output variables. We used Chi square (chi-2) , in Equation ( 1 ), which gives the level of independence between the features x _ t and the label y _ t ; it differentiates the chi-distribution, with the degree of freedom as 1.
where F indicates the frequency of the features and their labels in a dataset; P = frequency of the features emerges without a label; Q = frequency of label emerges without features; Z = frequency of neither features nor label emerges in the given dataset; and M = no. of training samples x t = x 1 , x 2 , … x i and prediction sequence y t = y 1 , y 2 , … y i .
Recursive feature elimination (RFE) is an effective method to find an optimal set of features for both regression and classification tasks. Initially, it creates a model dependent on all the features and estimates the importance of each feature of a given dataset. It priorities the features based on the rank order and eliminates those features that are of the least importance based on the evaluation metrics (in our case, we selected accuracy as a metric to find the optimal features) of the proposed model (DNN), which is depicted in Figure 3 .

Accuracy of the model based on several features. Based on the varying accuracy of the number of features, we chose nine features from the dataset to train and test the model.
We also utilized logistic regression (LR) and random forest (RF) [ 37 ] to determine which features contributed to the output variable [ 38 ]. Table 3 and Table 4 show (“True” value), which indicates that the feature contributed to the output variable, based on each univariate selection algorithm. The final score is given based on the cumulative of the four algorithms used. In the BR/EDR and BLE dataset, they contain four and five non-numerical values, respectively. The non-numerical values are converted to numeric values before they are fed to the model using one-hot encoders, a process called numericalization. Finally, we only selected the features that were important for identifying abnormal activities.
Univariate selection score of the BR/EDR selected feature.
Univariate selection score of BLE selected features.
Normalization : This is a feature engineering technique used to have the data in one range for faster processing and classifier accuracy. There are various normalization techniques available, among which Z-score normalization is highly used due to its simplicity and performance accuracy [ 33 ].
3.1.2. Layer _ 2
Initially, the medical data from IoT devices is collected and pre-processed on the first layer, and the collected events from Layer _ 1 events are sent for detection and identification to the second layer (the edge node). If any manipulation or deviation in the Bluetooth traffic is identified, an alert is triggered. On this layer, the events of the IoT medical device are actively captured and recorded on the events collector and are placed on the EPCRD device. This traffic is fed in the format of a feature vector, which is represented in Equation ( 2 ).
This feature vector is fed to Layer _ 2 to identify the malicious activities on this device based on the DL technique, which is deployed on the second layer of the edge node. The reason for placing two layers of intrusion detection is to protect the IoT system from device-based attacks and to have full coverage of the IoT healthcare network. The classifier model gives 99 % accuracy, which has been placed on Layer _ 2 . As the preprocessing and intrusion detection phases are separated on different devices, the resulting system constitutes a multi-layer IDS. At last, the IDS model triggers an alert for the administrator to take the required course of action against the intrusion.
3.2. Dataset Description
We developed a Bluetooth (BR/EDR and BLE) dataset using realistic traffic generated using the smart healthcare testbed [ 39 ] as described above in Figure 2 , with the following specifications: GPU 128-core Maxwell, CPU Quad-core ARM A57 @1.43 GHz, and memory of 4 GB 64-bit LPDDR4 25.6 GB/s; this device is commonly known as NVIDIA Jetson Nano. The dataset comprises abstract meta-information from the network traffic flow link layer (data link) of the Bluetooth-enabled IoMT network. The generated data do not cover the exact patient vital information but we considered the payload size of the vital during data generation and transmission.
While generating the data, we used three IoMT devices that were easily available in the market (SpO2, heart rate, and ECG), which operated wirelessly. During the data generation process, we considered Bluetooth version.4 and above. We observed some delays in data transmission for DoS attacks. However, in a DDoS attack, the IoMT device stops sending the data transmissions, and the device malfunctions. The generated data are stored in the local drive of the edge node.
We collected 5 GB of BR/EDR and BLE data over about 76 h during normal traffic patterns and while performing the attacks. Therefore, the data collected included benign and malicious traffic. The performed attacks were DDoS, Bluesmack, MITM, and DoS on the L2CAP (link layer control adaption protocol) layer of the Bluetooth protocol stack. The L2CAP protocol was located in the data link layer of the stack, and it provided connectionless and connection-oriented data services to the top layer protocols. It allowed the upper-level protocols and applications to send and receive the data frames.
After analyzing the captured traffic in the preprocessing data, we used a Dell Precision T5820 workstation having the feature of Intel ® Xeon ® W-2245 (16.5 MB cache, 8 cores, 16 threads, 3.90 GHz to 4.70 GHz Turbo, 155 W), NVIDIA ® RTX™ A4000, 16 GB GDDR6, 4 DP. The data preparation process was done using Python libraries. These libraries are most efficient in the domain of data science (e.g., Pandas). Pandas supports various input and output data formats and has strong probabilities in estimating the statics and elementary visualization [ 40 ]. Finally, we selected nine features from each dataset through statistical methods and correlation analysis as presented in Table 3 and Table 4 .
3.3. IDS Classifiers
The entire classification process is divided into two main stages—training and testing. In the training phase, some samples of a dataset are used to train the model. In the testing phase, new samples are fed to the classifier from the test dataset to evaluate the performance. To validate the dataset performance, we used existing supervised and unsupervised ML algorithms in addition to the proposed DL model for training and testing. The reason for using various ML and the proposed DL models is to benchmark it and to show that the dataset is free from abnormal results on different classifier models. Many of the datasets used in the literature are algorithm-dependent [ 41 ]. Our dataset produced acceptable accuracy for supervised and unsupervised ML and DL models. Various experiments with different classifiers helped us build the most efficient DL model to identify malicious activities with more than 99 % accuracy.
3.3.1. Classifier Using Supervised ML Algorithms
Among the existing supervised ML algorithms, we selected the most popular ones, namely: logistic regression (LR), decision tree (DT), support vector machine (SVM), and random forest (RF). We provide short descriptions of the algorithms that we used in experiments.
3.3.2. Classifier Using Unsupervised ML Algorithms
The selected algorithms are naïve Bayes (NB), isolation forest (IF), K-Means (KM), and local outlier factor (LOF). Unsupervised algorithms are trained without using the labels of the features in the dataset. IoMT devices operate on different protocols, and due to this complexity, vulnerabilities may emerge. Furthermore, with classical ML algorithms, many attacks cannot be detected when the attacker does a small manipulation over time. DL techniques can recognize unknown patterns, outliers, and small changes from the training model.
3.3.3. Classifier Using DNN
We used the multilayer perceptron (MLP) model, which is one of the categories of the feed-forward neural network (FNN), with multiple layers: one input layer, one output layer, and three hidden layers. Each layer consists of a set of neurons. The process of assembling the hidden layers is known as a DNN, as depicted in Figure 4 . The DNN-IDS training comprises two phases—forward propagation and backward propagation. In forward propagation, output values are calculated. Whereas, in backward propagation, the weights are updated by passing the residual. The training of the model is implemented using Keras (with TensorFlow backend) and Table 5 provides detailed information on the various functions and parameters used. The combination of all layers is reflected in Figure 4 . The model’s hidden layers are formulated as in the MLP. The vector and the biases are represented as b h and b y .

DNN architecture for the proposed IDS. It has three hidden layers with softmax as the output layer.
DNN architectural hyperparameters.
- Hidden layer: H l ( x ) = H l 1 ( H l 1 − 1 ( H l − 2 ( … ( H l 1 ( x ) ) ) ) ) (4)
- Training samples: x t = x 1 , x 2 , x 3 , x 4 , … , x i − 1 , x i (5)
- Hidden states: h t = h 1 , h 2 , h 3 , h 4 , … , h i − 1 , h i (6)
- Predictions of sequence: y ^ t = y 1 , y 2 , y 3 , y 4 , … y i − 1 , y i (7)
- Input-hidden weighted matrix: W l x · W l h (8)
- Output-hidden weighted matrix: W l y (9)
The objective function of the model, defined as the single pair of the training example ( x t , y t ) is: L is described as the distance calculating the actual y t and y ^ t denote the prediction labels, η denotes the learning rate and k denotes the number of iterations. In DNN, each hidden layer uses a non-linear activation function to model the gradient error. Among various activation functions, ReLU gives faster performance and can train the model with a huge number of hidden layers. For maximizing the efficiency of the DNN, we built the model by considering the binary-cross entropy loss function, ReLU function, and softmax function with non-linear activation to achieve greater accuracy among the most substantial probability value of each class. In addition, we applied dropout techniques, to counter the problem of overfitting, by ignoring the randomly selected neurons. During this process, downstream neurons are ignored in the forward propagation and updated weights are not applied for the backward pass [ 42 ]. The neuron weights are settled within the network and are tuned for specific features. This effect on the network will result in less sensitivity to the definite weights of the neurons, which makes better generalization and is less likely to overfit the training data. In the below subsections, we show the experiments that we performed in the selection of IDS classifiers for the IDS models.
4. Experimental Results
To choose the best classifier for Intrusion detection, we trained and tested the BR/EDR and BLE Bluetooth datasets with supervised and unsupervised ML algorithms and DNN. The experimental results and discussion are provided below.
4.1. Unsupervised ML Algorithms
4.1.1. br/edr dataset.
The BR/EDR dataset is trained and tested on four unsupervised ML algorithms with a balanced ratio of DOS attack and normal traffic pattern. We trained the four algorithms as binary classifiers to identify the DOS attack and normal traffic. The results achieved are shown in Table 6 and Figure 5 . The naïve Bayes algorithm recorded the highest accuracy, precision, F1-score, and other favorable metrics among all the algorithms. The precision and recall scores of Isolation Forest achieved an acceptable level of prediction, while K-means and LOF achieve more than 55 % and 30 % of precision and recall, respectively. This suggests that these two algorithms are not suitable to train the IDS using the created BR/ EDR dataset. Moreover, the reason for lower precision and recall of LOF is a direct indication that the dataset is fully pre-processed. The dataset does not contain a high level of deviations and we performed intensive preprocessing on the dataset to make it normalized and free from outliers (in the Layer _ 1 of the IDS model). Furthermore, the features that have been selected are highly significant for the output class. The other three metrics are the F1 score, area under the ROC curve (AUC), and Cohen’s kappa scores. These metrics provide a homogeneous pattern to the previous three metrics for the Naïve Bayes classifier.

Performance of BR/EDR–Unsupervised ML algorithms. This result shows that the dataset does not show any deviation irrespective of different models (i.e., the dataset is preprocessed intensively).
Performance analysis of the BR/EDR IDS using unsupervised—ML algorithms.
4.1.2. BLE Dataset
Similarly, the BLE dataset was trained and tested on the same unsupervised algorithms, but we modeled those as multiclass classifiers to identify DoS, MITM, and normal traffic from the samples. The performances of the classifiers are shown in Figure 6 . The numeric scores of each class are visible in Table 7 . Among the four unsupervised algorithms, naïve Bayes records the highest accuracy scores of 98 , 78 , and 80 for DoS, MITM, and normal traffic identification, respectively. Recall, precision, and other metrics fall close to the accuracy scores for the naïve Bayes classifier. Isolation forest, K-means, and LOF classifiers show better performances than the BR/EDR dataset with an average accuracy of 80 % for three classes.

Performances of BLE–unsupervised ML algorithms. Multiple attacks were trained on the same models of BR/EDR; we observe that the models are not biased.
Performance analysis of the multiclass classification of the BLE IDS using supervised—ML algorithms.
4.2. Supervised ML Algorithms
4.2.1. br/edr dataset.
Likewise, the dataset BR/EDR was modeled as a binary classifier using four supervised ML algorithms each time, namely LR, DT, SVM, and RF to differentiate the DoS attack and normal traffic. The experimental results depicted in Figure 7 and Table 8 show that accuracy, precision, and recall are satisfactory for all classifiers. However, the RF classifier gave the highest score for all three metrics, followed by DT, SVM, and then LR. This is clear evidence that the classifier model and dataset are efficient in identifying malicious traffic of DoS attacks on Bluetooth medical IoT devices.

Performance of BR/EDR–supervised ML algorithms. The dataset and models are efficient in identifying malicious traffic behavior. (Deployed models are SVM and K-means).
Performance analysis of the BR/EDR IDS using supervised–ML algorithms.
Figure 7 also records the F1-score, AUC score, and Cohen’s Kappa score, substantiating the inference that we deduced from the previous three metrics. Moreover, we can conclude that the dataset gives stable results using any of these supervised ML algorithms, of which RF and DT are the most recommended for general IoT devices and other networks. However, in the case of medical IoT devices, we need to choose a lightweight computationally inexpensive model. Among the tested algorithms, K-means (unsupervised) and SVM (supervised) are lightweight but they are computationally expensive in terms of training a model that is deployable on medical IoT devices. Nevertheless, the performance scores fall short for the real-time IDS model, so we investigated the DNN models using the created datasets.
4.2.2. BLE Dataset
The results of the multi-class model trained using the BLE dataset with four different algorithms are shown in Figure 8 and Table 9 . We observe that, unlike LR, the accuracy scores of the three supervised algorithms, DT, SVM, and RF lie between 95 % and 98 % . Though the average performance of the three algorithms, namely, DoS, MITM, and normal, is satisfactory, it is difficult to choose the best among these three. Moreover, neither one of the single classifiers give better performances for the three identification classes to suit the real-time IDS performance. LR records less than 50 % accuracy and unstable scores for other metrics. Because of these shortcomings, we investigated the use of a DNN model for both of the datasets.

Performances of BLE–supervised ML algorithms. For real-time detection and deployment, neither of the single classifiers gave a better performance.
Performance analysis of the multiclass classification of the BLE IDS using supervised–ML algorithms.
4.3. DNN Model
Two DNNs were modeled as binary and multi-class classifiers using BR/EDR and BLE datasets, respectively. The training accuracies of the two models were between 92 % and 95 % , as depicted in Figure 9 . The testing accuracies were 98 % and above for both models. From these results, we conclude that the classifier model using DNN was the best among all the other algorithms we tested. This deduction was bolstered by considering the training and testing loss scores in Figure 10 . The training loss of the two models started at approximately 0.3 and then reached 0.15 as the learning process went on. Similarly, the lowest Test loss recorded was 0.01 , which is an indication of a stable DNN model.

Training and testing accuracy. The proposed IDS DNN model for the BR/EDR and BLE datasets for 1000 epochs attained an accuracy of 98%.

Training and testing loss–DNN. The recorded test was a loss of 0.01, which indicated that DNN was reliable for the real-time application.
Additionally, to check the uniformity of the dataset, we tested various ratios of abnormal (malicious) and benign traffic patterns. The ratios of benign and abnormal patterns considered were 50–50, 75–25, and 80–20. Each time, the results that we achieved were consistent, which suggests that our dataset does not have any bias in the ratios of the traffic patterns. The accuracy scores of all the tests show that our dataset achieved less accuracy for unsupervised ML algorithms than for the supervised ML algorithms. From Table 10 and Figure 11 , we deduce that the dataset can be considered a standard for training IDS models to identify DoS, DDoS, and Bluesmack attacks against Bluetooth IoMT devices. Moreover, in comparison to other models, our proposed model attained the best accuracy, as shown in Table 11 .

Performance analysis of the binary and multiclass of the proposed model for BR/EDR and BLE, respectively.
Performance analysis of the binary and multi-class classification of the proposed IDS (BR/EDR and BLE).
Comparison of our model with existing IDS models).
5. Conclusions and Future Work
Bluetooth communication is widely adopted in IoMT devices due to its various benefits. Nevertheless, because of its simplicity as a personal wireless communication protocol, Bluetooth lacks security mechanisms, which may result in devastating outcomes for patients treated using wireless medical devices. As discussed, continuous monitoring of network activity is efficient in identifying cyber-attacks in most scenarios. We applied the same concept to Bluetooth-based medical IoT devices in a smart healthcare system. In this paper, we proposed a secure and scalable architecture and deployed the IDS on the edge nodes of the smart healthcare system. we explored the issues and limitations of Bluetooth communication technology in IoMT systems and current IDS for Bluetooth-enabled IoMT devices. The second outcome of this research is a standard Bluetooth dataset and a DNN-based classifier for Bluetooth traffic. To the best of our knowledge, this is the first intrusion detection dataset for the Bluetooth classic and BLE. From the results, we can see that the created dataset can be used to train the IDS model for identifying DoS, DDoS, and Bluesmack attacks on medical IoT devices operated using Bluetooth technology. We also deduce that the proposed IDS classifier using DNN gives more than 99 % accuracy, precision, and recall, which outperforms the existing models for identifying Bluetooth-based attacks.
In the future, we plan to enhance the following critical areas of the proposed model. (1) We look forward to enlarging our dataset with more attack types, other than DoS, DDoS, and MITM. (2) We plan to include the attack data of other protocols, such as Wi-Fi. (3) We will aim to improve the intrusion detection classifier to identify those attacks efficiently on different datasets (by applying data fusion or feature fusion techniques). (4) Furthermore, we plan to develop a mitigation technique for the identified attacks from our model and to detect unknown attacks so that the architecture can be extended to include mitigation mechanisms for the identified attacks.
Acknowledgments
This publication was made possible by an NPRP grant, NPRP 10-0125-170250 from the Qatar National Research Fund (a member of the Qatar Foundation). The statements made herein are solely the responsibility of the authors.
Bluetooth vulnerabilities.
Features candidates for the proposed model.
Funding Statement
This publication was made possible by NPRP grant NPRP 100125-170250 from the Qatar National Research Fund (a member of Qatar Foundation).
Author Contributions
Conceptualization, M.Z., D.U. and A.A.-A.; methodology, M.Z., D.U. and A.A.-A.; software, M.Z.; validation, M.Z.; formal analysis, M.Z.; investigation, M.Z.; resources, M.Z. and D.U.; data curation, M.Z.; writing—original draft preparation, M.Z.; writing—review and editing, M.Z., A.G., D.U., A.A.-A., T.R., G.A., M.H. and J.Q.; visualization, M.Z.; supervision, D.U., A.A.-A. and J.Q.; project administration, D.U.; funding acquisition, D.U. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
Conflicts of interest.
The author declare no conflict of interest.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
- Insider Reviews
- Tech Buying Guides
- Personal Finance
- Insider Explainers
- Sustainability
- United States
- International
- Deutschland & Österreich
- South Africa

- Home ›
- Tech buying Guides ›
Top rated Bluetooth Earphones in India

How we do our research
Our ranking criteria, features comparison:, features to look for while buying bluetooth earphones.

- RIL cash flows
- Charlie Munger
- Feedbank IPO allotment
- Tata IPO allotment
- Most generous retirement plans
- Broadcom lays off
- Cibil Score vs Cibil Report
- Birla and Bajaj in top Richest
- Nestle Sept 2023 report
- India Equity Market
- Best printers for Home
- Best Mixer Grinder
- Best wired Earphones
- Best 43 Inch TV in India
- Best Wi Fi Routers
- Best Vacuum Cleaner
- Best Home Theatre in India
- Smart Watch under 5000
- Best Laptops for Education
- Best Laptop for Students

- Advertising
- Write for Us
- Privacy Policy
- Policy News
- Personal Finance News
- Mobile News
- Business News
- Ecommerce News
- Startups News
- Stock Market News
- Finance News
- Entertainment News
- Economy News
- Careers News
- International News
- Politics News
- Education News
- Advertising News
- Health News
- Science News
- Retail News
- Sports News
- Personalities News
- Corporates News
- Environment News
- Top 10 Richest people
- Top 10 Largest Economies
- Lucky Color for 2023
- How to check pan and Aadhaar
- Deleted Whatsapp Messages
- How to restore deleted messages
- 10 types of Drinks
- Instagram Sad Face Filter
- Unlimited Wifi Plans
- Recover Whatsapp Messages
- Google Meet
- Check Balance in SBI
- How to check Vodafone Balance
- Transfer Whatsapp Message
- NSE Bank Holidays
- Dual Whatsapp on Single phone
- Phone is hacked or Not
- How to Port Airtel to Jio
- Window 10 Screenshot
Copyright © 2024 . Times Internet Limited. All rights reserved.For reprint rights. Times Syndication Service.
- Election 2024
- Entertainment
- Newsletters
- Photography
- Personal Finance
- AP Buyline Personal Finance
- Press Releases
- Israel-Hamas War
- Russia-Ukraine War
- Global elections
- Asia Pacific
- Latin America
- Middle East
- Election Results
- Delegate Tracker
- AP & Elections
- March Madness
- AP Top 25 Poll
- Movie reviews
- Book reviews
- Personal finance
- Financial Markets
- Business Highlights
- Financial wellness
- Artificial Intelligence
- Social Media
South Korean computer chipmaker plans $3.87 billion Indiana semiconductor plant and research center
- Copy Link copied
WEST LAFAYETTE, Ind. (AP) — A major South Korean computer chipmaker said Wednesday it plans to spend more than $3.87 billion in Indiana to build a semiconductor packaging plant and research and development center.
SK Hynix expects the campus to create as many as 800 high-wage jobs in engineering, technical support, administration and maintenance by the end of 2030.
The investment will move Indiana to the forefront of artificial intelligence in America, said Purdue University President Mung Chiang said. The new plant will be built at the Purdue Research Park, an economic development incubator at the university.
The company said the plant will produce high-bandwidth memory chips that will help meet U.S. demand for semiconductors, develop future generations of chips and house an advanced packaging research and development line at the 430,000-square-foot plant (nearly 40,000-square-meter) around 100 miles (160 kilometers) southeast of Chicago.
“We believe this project will lay the foundation for a new Silicon Heartland, a semiconductor ecosystem centered in the Midwest,” company CEO Kwak Noh-Jung said in a news release.
Gov. Eric Holcomb said the project “not only reaffirms the state’s role in the hard tech sector, but is also another tremendous step forward in advancing U.S. innovation and national security.”
The Indiana Economic Development Corp. offered the company of up to $3 million in incentive-based training grants, up to $3 million in manufacturing readiness grants, up to $80 million in performance payments, up to $554.7 million in tax rebates and other incentives. The cities of West Lafayette and Lafayette, Tippecanoe County and Duke Energy offered additional Incentives.

IMAGES
VIDEO
COMMENTS
Nature Electronics 1 , 661 ( 2018) Cite this article. Bluetooth allows electronic devices to communicate over short distances and is used by billions of devices worldwide. Jaap Haartsen recalls ...
In 2019 and 2020 Zhang et al. published their extensive research [47], [48] on the security of secure connection only (SCO) mode introduced with BLE 4.2 (see Section 3.3), which is intended to enforce security mode 1, level 4. The authors note that, according to the Bluetooth specification, SCO mode forces the GATT server (typically the ...
Bluetooth is a method for data communication that uses short-range radio links to replace cables between computers and their connected units. Industry-wide Bluetooth promises very substantial benefits for wireless network operators, end workers, and content developers of exciting new applications. This article delves into the implementation and architecture of Bluetooth. It also describes the ...
Bluetooth is a wireless technology widely used for exchanging data by connecting devices. The name Bluetooth came from a 10th century Danish King, Harald Blatand (in English Harold Bluetooth). He united warring nations of DenmarkNorway. Bluetooth does exactly the same thing; it unites wireless devices ( Bluetooth ).
Bluetooth is one of the popular technology standards for exchanging data over short distances. In this paper, a study of Bluetooth protocol and its applications is presented. We also thoroughly ...
The Bluetooth TM wireless technology is designed as a short-range connectivity solution for personal, portable, and handheld electronic devices. Since May 1998 the Bluetooth SIG has steered the development of the technology through the development of an open industry specification, including both protocols and application scenarios, and a qualification program designed to assure end-user value ...
Bluetooth and 802.11 compliment each other if different ways, but most people will use them for many of the same functions. 5.1. Outlook of technologyMost articles you will come across will tell you Bluetooth is here to stay. The biggest reason Bluetooth is looking so good right now is many more companies are integrating it into their products.
Bluetooth is a pervasive technology for wireless communication. Billions of devices use it in sensitive applications and to exchange private data. The security of Bluetooth depends on the Bluetooth standard and its two security mechanisms: pairing and session establishment. ... research-article; Conference. Acceptance Rates. Overall Acceptance ...
Bluetooth and Microcontrollers. Explore the latest full-text research PDFs, articles, conference papers, preprints and more on BLUETOOTH. Find methods information, sources, references or conduct a ...
Bluetooth low energy (BLE) was first specified in 2010. Since then, its popularity has not ceased to increase. ... Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Application of Bluetooth technology has become ubiquitous in the current age of transportation research. The purpose of this article is to explore advancements of Bluetooth technology, applied to transportation studies, using performance metrics such as match rate, travel time, and segment speed through analyzing collected data from several Bluetooth devices.
1. Introduction. Bluetooth Low Energy (BLE, Bluetooth 4, Bluetooth Smart) is an innovative technology, developed by the Bluetooth Special Interest Group (SIG), which aims to become the best alternative to the huge number of standard wireless technologies already existing and widespread on the market (i.e., IEEE 802.11b (Wi-Fi), ZigBee, ANT+ and Bluetooth Classic (Bluetooth 3.0, Basic Rate ...
Vazquez, Joseph, "A COMPARATIVE ANALYSIS OF DEVICES VIA THE BLUETOOTH PROTOCOL IN A TIME SERIES ANALYSIS" (2022). Electronic Theses, Projects, and Dissertations. 1503. https://scholarworks.lib.csusb.edu/etd/1503. This Project is brought to you for free and open access by the Ofice of Graduate Studies at CSUSB ScholarWorks.
We present results from a 7-day trial of a Bluetooth-enabled card by the New Zealand Ministry of Health to investigate its usefulness in contact tracing. A comparison of the card with traditional contact tracing, which relies on self-reports of contacts to case investigators, demonstrated significantly higher levels of internal consistency in detected contact events by Bluetooth-enabled cards ...
As an integral part of personal communication devices and integrated in many ubiquitous computing systems, Bluetooth (BT) is one of the most prominent technologies for acquiring social proximity traces. The research community has initiated a transition of research methods to reliably represent real-life social connections [9, 43]. Compared with ...
The rise of Bluetooth-equipped devices in personal consumer electronics and in in-car systems has revealed the potential to develop Bluetooth sensor systems for applications in intelligent transportation systems. These applications may include measurements of traffic presence, density, and flow, as well as longitudinal and comparative traffic analysis. A basic Bluetooth sensor system for ...
Ryan used Ubertooth One in his work and exploited the many vulnerabilities of Bluetooth LE version 4.0. In his research, Ryan focused on BLE security, beginning with tracking the devices. He tracked the connections between devices by monitoring the Radio Frequency channels, determining the Bluetooth Access Address and ascertaining the hop ...
The Internet of Things helps to have every individual interconnected with their surroundings and to interact with them through smart devices. In recent years, Bluetooth Low Energy (BLE) technology has become very popular in smart infrastructures, the medical field, the retail industry, and many more areas due to its availability in a plethora of wireless devices. BLE is widely used in IoT ...
ABSTRACT: A Bluetooth ad hoc network can be formed by interconnecting piconets into scatternets. The constraints and properties of Bluetooth scatternets present special challenges in forming an ad hoc network efficiently. This paper, the research contributions in this arena are brought together, to give an overview of the state-of-the-art.
BlueFi works by reversing the signal processing of WiFi hardware and finds special 802.11n packets that are decodable by unmodified Bluetooth devices. With BlueFi, every 802.11n device can be used simultaneously as a Bluetooth device, which instantly increases the coverage of Bluetooth, thanks to the omnipresence of WiFi devices.
Recently, our group showed that direct exposure (in a surgical setting) to cell phone electromagnetic fields (EMFs) induces deterioration of auditory evoked cochlear nerve compound action potential (CNAP) in humans. To verify whether the use of Bluetooth devices reduces these effects, we conducted the present study with the same experimental ...
The Latest Bluetooth Market Research. For the last few years, the Bluetooth Special Interest Group (SIG) has been working with ABI Research - a global leader in analyzing, tracking, and forecasting the transformation of the smart device and IoT markets - to develop a wide range of market research note that highlight recent and upcoming Bluetooth ® technology trends and forecasts.
Research assessments are still not fit for purpose — here's how to change things. A move away from narrow assessment metrics such as high-impact publications is welcome, but a lack of planning ...
Horizon Europe turmoil changed the lives of these five scientists. The EU has reduced these four priorities to three — and open strategic autonomy has been upgraded. It is now an overarching ...
Better results through expert teams. One of the advantages of the research enterprise at Virginia Tech lies in its blend of experts with budding inventors. By employing specialists who both innovate and teach, a full body of knowledge is being passed on to the next generation of engineers. In the cases of Leong and Purayil, both have had the ...
In our article, we consider internal and external threats that are targeted against IoMT infrastructure. Since these devices are severely resource-constrained, ... The second outcome of this research is a standard Bluetooth dataset and a DNN-based classifier for Bluetooth traffic. To the best of our knowledge, this is the first intrusion ...
Wireless. B0B4F54WZW. Our Top Choice: Boult Audio Curve Max Bluetooth Earphones (Blue) T. These earphones offer exceptional sound quality with a powerful bass driver. With a playtime of up to 100 ...
Each state and territory's five-year action and digital equity plans offers a roadmap of what it will take to achieve a more universally connected future for all of their residents. Jake Varn leads education and training efforts for state broadband offices for The Pew Charitable Trusts' broadband access initiative. Article April 3, 2024.
Previous research shows the impact of social media on stock market developments. Some studies show that the effect of social media on stock prices developments is higher than that of conventional media, in particular on the daily basis. Chen et al. (2014) find that the opinions revealed on social media strongly predict future
The new plant will be built at the Purdue Research Park, an economic development incubator at the university. The company said the plant will produce high-bandwidth memory chips that will help meet U.S. demand for semiconductors, develop future generations of chips and house an advanced packaging research and development line at the 430,000 ...