- Frontiers in Artificial Intelligence
- Pattern Recognition
- Research Topics

Deep Learning for Biometrics: Advances and Applications
Total Downloads
Total Views and Downloads
About this Research Topic
Analyzing people’s unique physical and behavioral characteristics is the essence of the science of biometrics. Over the last two decades, we have witnessed an exponential growth of research interests in this domain, through which biometrics has surged from interesting and conventional pattern recognition applications, to deep learning-based mainstream research topics. Three major reasons account for this, first, the technological progress of the sensors that capture biometric signals, second, the significant increase in machines' computing power, and third, the democratization of deep learning paradigms. In this article collection, we are focusing on deep learning and biometric research topics that continue to be challenging, including evaluating new biometric techniques, remarkably improving the performance of existing ones, and ensuring the scalability of biometric systems to handle the ever-increasing amount of biometric data. In fact, biometric systems follow a typical pipeline that is composed of separate acquisition, preprocessing, feature extraction and classification. Deep learning as a data-driven representation learning approach has been shown to be a promising alternative to conventional data-agnostic and handcrafted pre-processing and feature extraction for biometric systems. Combining deep learning models with biological visual perception, many biologically plausible approaches to deep learning have been proposed for review. Including research on a single deep learning model including CNN, RNN, AE, GAN, GNN, and reinforcement learning models, the recent approaches of visual perception computational models oriented deep learning, showing its advantage and its progressive impact on artificial intelligence. Topics include but are not restricted to the following: • AI-Based Biometric Applications • Identity, Expression, Gender and Age Recognition • Vision and Perception • Deep Learning Techniques and Intelligent Systems for analyzing biometric data, such as CNN, RNN, transfer learning with convolutional neural networks, GAN, GNN, and reinforcement learning models for face recognition, gender and ethnicity classification, etc. • Behavioral Analysis and Information Inference • Activity, Action and Posture Recognition • Biometric systems for information assurance • Privacy, Security and Access Control
Keywords : biometrics, deep learning, generative adversarial networks, convolutional neural networks, recurrent neural networks, identity recognition, gender classification, privacy
Important Note : All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements. Frontiers reserves the right to guide an out-of-scope manuscript to a more suitable section or journal at any stage of peer review.
Topic Editors
Topic coordinators, submission deadlines, participating journals.
Manuscripts can be submitted to this Research Topic via the following journals:
total views
- Demographics
No records found
total views article views downloads topic views
Top countries
Top referring sites, about frontiers research topics.
With their unique mixes of varied contributions from Original Research to Review Articles, Research Topics unify the most influential researchers, the latest key findings and historical advances in a hot research area! Find out more on how to host your own Frontiers Research Topic or contribute to one as an author.
A Systematic Review on Physiological-Based Biometric Recognition Systems: Current and Future Trends
- Review article
- Published: 23 February 2021
- Volume 28 , pages 4917–4960, ( 2021 )
Cite this article
- Kashif Shaheed ORCID: orcid.org/0000-0002-7399-6211 1 ,
- Aihua Mao 1 ,
- Imran Qureshi 2 ,
- Munish Kumar 3 ,
- Qaisar Abbas 4 ,
- Inam Ullah 5 &
- Xingming Zhang 1
1810 Accesses
23 Citations
1 Altmetric
Explore all metrics
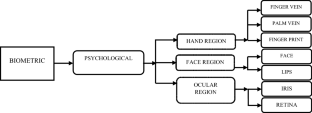
Biometric deals with the verification and identification of a person based on behavioural and physiological traits. This article presents recent advances in physiological-based biometric multimodalities, where we focused on finger vein, palm vein, fingerprint, face, lips, iris, and retina-based processing methods. The authors also evaluated the architecture, operational mode, and performance metrics of biometric technology. In this article, the authors summarize and study various traditional and deep learning-based physiological-based biometric modalities. An extensive review of biometric steps of multiple modalities by using different levels such as preprocessing, feature extraction, and classification, are presented in detail. Challenges and future trends of existing conventional and deep learning approaches are explained in detail to help the researcher. Moreover, traditional and deep learning methods of various physiological-based biometric systems are roughly analyzed to evaluate them. The comparison result and discussion section of this article indicate that there is still a need to develop a robust physiological-based method to advance and improve the performance of the biometric system.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price excludes VAT (USA) Tax calculation will be finalised during checkout.
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others
Role of machine learning and deep learning techniques in EEG-based BCI emotion recognition system: a review
Priyadarsini Samal & Mohammad Farukh Hashmi
Human emotion recognition from EEG-based brain–computer interface using machine learning: a comprehensive review
Essam H. Houssein, Asmaa Hammad & Abdelmgeid A. Ali
Human activity recognition in artificial intelligence framework: a narrative review
Neha Gupta, Suneet K. Gupta, … Jasjit S. Suri
Abbas EI, Mieee MES (2017) Face recognition rate using different classifier methods based on PCA, pp 37–40
Abrishami-Moghaddam H, Farzin H, Moin MS (2008) A novel retinal identification system. Eurasip J Adv Signal Process. https://doi.org/10.1155/2008/280635
Article MATH Google Scholar
Adjimi A, Hacine-Gharbi A, Ravier P, Mostefai M (2017) Extraction and selection of binarised statistical image features for fingerprint recognition. Int J Biometrics 9(1):67–80. https://doi.org/10.1504/IJBM.2017.084133
Article Google Scholar
Aglio-caballero A, Ríos-Sánchez B, Sánchez-Ávila C, Giles MJMD (2017) Analysis of local binary patterns and uniform local binary patterns for palm vein biometric recognition. In: 2017 international carnahan conference on security technology (ICCST). IEEE, pp 1–6
Ahmadi N, Akbarizadeh G (2018) Hybrid robust iris recognition approach using iris image pre-processing, two-dimensional gabor features and multi-layer perceptron neural network/PSO. IET Biometrics 7(2):153–162. https://doi.org/10.1049/iet-bmt.2017.0041
Ahmadi N, Akbarizadeh G (2018) Iris tissue recognition based on GLDM feature extraction and hybrid MLPNN-ICA classifier. Neural Comput Appl. https://doi.org/10.1007/s00521-018-3754-0
Ahmadi N, Nilashi M, Samad S, Rashid TA, Ahmadi H (2019) An intelligent method for iris recognition using supervised machine learning techniques. Opt Laser Technol 120(2018):105701. https://doi.org/10.1016/j.optlastec.2019.105701
Ahmed T, Sarma M (2018) An advanced fingerprint matching using minutiae-based indirect local features. Multimed Tools Appl 77(15):19931–19950. https://doi.org/10.1007/s11042-017-5444-9
Aleem S, Sheng B, Li P, Yang P, Feng DD (2019) Fast and accurate retinal identification system: using retinal blood vasculature landmarks. IEEE Trans Ind Inf 15(7):4099–4110. https://doi.org/10.1109/TII.2018.2881343
Ali YH, Razuqi ZN (2017) Palm vein recognition based on centerline. Iraqi J Sci 58(2):726–734
Google Scholar
Ananth C (2017) Iris recognition using active contours. SSRN Electron J 2(1):27–32. https://doi.org/10.2139/ssrn.3028575
Arsalan M, Hong HG, Naqvi RA, Lee MB, Kim MC, Kim DS et al (2017) Deep learning-based iris segmentation for iris recognition in visible light environment. Symmetry. https://doi.org/10.3390/sym9110263
Barpanda SS, Sa PK, Marques O, Majhi B, Bakshi S (2018) Iris recognition with tunable filter bank based feature. Multimed Tools Appl 77(6):7637–7674. https://doi.org/10.1007/s11042-017-4668-z
Benalcazar DP, Perez CA, Bastias D, Bowyer KW (2019) Iris recognition: comparing visible-light lateral and frontal illumination to NIR frontal illumination. In: Proceedings—2019 IEEE winter conference on applications of computer vision, WACV 2019, pp 867–876. https://doi.org/10.1109/WACV.2019.00097
Bharadwaj S, Vatsa M, Singh R (2014) Biometric quality: a review of fingerprint, iris, and face. Eurasip J Image Video Process 2014(1):1–28. https://doi.org/10.1186/1687-5281-2014-34
Bhardwaj I, Londhe ND, Kopparapu SK (2017) A spoof resistant multibiometric system based on the physiological and behavioral characteristics of fingerprint. Pattern Recognit 62:214–224. https://doi.org/10.1016/j.patcog.2016.09.003
Bhavani M (2013) Human identification using finger images. Int J Comput Trends Technol 4(1):258–263
MathSciNet Google Scholar
Bhukya S (2019) A hybrid biometric identification and authentication system with retinal verification using AWN classifier for enhancing security. https://doi.org/10.1007/978-981-13-1580-0
Borra SR, Reddy GJ, Reddy ES (2016) A broad survey on fingerprint recognition systems. In: Proceedings of the 2016 IEEE international conference on wireless communications, signal processing and networking, WiSPNET 2016, pp 1428–1434. https://doi.org/10.1109/WiSPNET.2016.7566372
Boubchir L, Aberni Y, Daachi B (2018) Competitive coding scheme based on 2D log-gabor filter for palm vein recognition. In: 2018 NASA/ESA conference on adaptive hardware and systems (AHS), vol (i), pp 152–155
Buciu I, Gacsadi A (2016) Biometrics systems and technologies: a survey. Int J Comput Commun Control 11(3):315–330. https://doi.org/10.15837/ijccc.2016.3.2556
Cancian P, Di Donato GW, Rana V, Santambrogio MD, Elettronica D, Bioingegneria I, Milano P (2017) An embedded gabor-based palm vein recognition system, pp 405–408
Cao K, Jain AK (2018) Fingerprint indexing and matching: an integrated approach. In: IEEE international joint conference on biometrics, pp 437–445. https://doi.org/10.1109/BTAS.2017.8272728
Cao K, Jain AK (2019) Automated latent fingerprint recognition. IEEE Trans Pattern Anal Mach Intell 41(4):788–800. https://doi.org/10.1109/TPAMI.2018.2818162
Chauhan S, Arora AS, Kaul A (2010) A survey of emerging biometric modalities. Procedia Comput Sci 2:213–218. https://doi.org/10.1016/j.procs.2010.11.027
Chen Z, Huang W, Lv Z (2015) Towards a face recognition method based on uncorrelated discriminant sparse preserving projection. https://doi.org/10.1007/s11042-015-2882-0
Choraś M (2007) Human lips recognition. Adv Soft Comput 45:838–843. https://doi.org/10.1007/978-3-540-75175-5_104
Choraś M (2010) The lip as a biometric. Pattern Anal Appl 13(1):105–112. https://doi.org/10.1007/s10044-008-0144-8
Article MathSciNet Google Scholar
Chugh T, Cao K, Jain AK (2018) Fingerprint spoof detection using minutiae-based local patches. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 581–589. https://doi.org/10.1109/BTAS.2017.8272745
Czajka A, Bowyer KW (2018) Presentation attack survey. ACM Comput Surv 51(4):1–35. https://doi.org/10.1145/3232849
Czajka A, Bowyer KW (2018) Presentation attack detection for iris recognition: an assessment of the state-of-the-art. ACM Comput Surv 51(4):86
Czajka A, Moreira D, Bowyer KW, Flynn PJ (2019) Domain-specific human-inspired binarized statistical image features for Iris recognition. In: Proceedings of IEEE winter conference on applications of computer vision, WACV 2019, pp 959–967. https://doi.org/10.1109/WACV.2019.00107
Dargan S, Kumar M (2020) A comprehensive survey on the biometric recognition systems based on physiological and behavioral modalities. Expert Syst Appl 143:113114. https://doi.org/10.1016/j.eswa.2019.113114
Darlow LN, Rosman B (2018) Fingerprint minutiae extraction using deep learning. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 22–30. https://doi.org/10.1109/BTAS.2017.8272678
Das S, Muhammad K, Bakshi S, Mukherjee I, Sa PK, Sangaiah AK, Bruno A (2019) Lip biometric template security framework using spatial steganography. Pattern Recognit Lett 126:102–110. https://doi.org/10.1016/j.patrec.2018.06.026
Deljavan Amiri M, Akhlaqian Tab F, Barkhoda W (2009) Retina identification based on the pattern of blood vessels using angular and radial partitioning. In: Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), 5807 LNCS, pp 732–739. https://doi.org/10.1007/978-3-642-04697-1_68
Deng J (2017) Marginal loss for deep face recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition workshops
Deng J (2019) ArcFace: additive angular margin loss for deep face recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, no 1
Deng J, Lu X (2019) Lightweight face recognition challenge. In: Proceedings of the international conference on computer vision workshop. https://doi.org/10.1109/ICCVW.2019.00322
Ding H, Zhou SK, Chellappa R (2017) FaceNet2ExpNet: regularizing a deep face recognition net for expression recognition. In: Proceedings of the12th IEEE international conference on automatic face & gesture recognition (FG 2017), pp 118–126. https://doi.org/10.1109/FG.2017.23
Dongyang DU, Lijun LU, Ruiyang FU, Lisha Y, Wufan C, Yaqin LIU (2019) Palm vein recognition based on end-to-end convolutional neural network 39(2):207–214. https://doi.org/10.12122/j.issn.1673-4254.2019.02.13
Donida Labati R, Genovese A, Muñoz E, Piuri V, Scotti F (2018) A novel pore extraction method for heterogeneous fingerprint images using convolutional neural networks. Pattern Recognit Lett 113:58–66. https://doi.org/10.1016/j.patrec.2017.04.001
Dua M, Gupta R, Khari M, Crespo RG (2019) Biometric iris recognition using radial basis function neural network. Soft Comput 23(22):11801–11815. https://doi.org/10.1007/s00500-018-03731-4
Duan Y, Lu J, Member S, Feng J, Zhou J (2017) Context-aware local binary feature learning for face recognition 8828:1–14. https://doi.org/10.1109/TPAMI.2017.2710183
Engineering C, Gables C (2017) Low resolution face recognition in surveillance systems using discriminant correlation analysis, pp 912–917. https://doi.org/10.1109/FG.2017.130
Fachrurrozi M (2017) Multi-object face recognition using content based image retrieval (CBIR), no x, pp 193–197
Fairuz MS, Habaebi MH, Elsheikh EMA (2019) Pre-trained based CNN model to identify finger vein. Bull Electr Eng Inform 8(3):855–862. https://doi.org/10.11591/eei.v8i3.1505
Fronitasari D, Indonesia U, Gunawan D, Indonesia U (2017) Palm vein recognition by using modified of local binary pattern (LBP) for extraction feature, pp 18–22
Gao Y, Zhao M, Yuille AL (2017). Semi-supervised sparse representation based classification for face recognition with insufficient labeled samples. https://doi.org/10.1109/TIP.2017.2675341
Gomez-barrero M, Kolberg J, Busch C (2018) Towards multi-modal finger presentation attack detection. In: 2018 14th international conference on signal-image technology & internet-based systems (SITIS), pp 547–552. https://doi.org/10.1109/SITIS.2018.00089
Gumede A, Viriri S, Gwetu M (2017) Hybrid component-based face recognition. In: Proceedings of the conference on information communication technology and society, pp 0–5
Guo X, Zhu E, Yin J (2018) A fast and accurate method for detecting fingerprint reference point. Neural Comput Appl 29(1):21–31. https://doi.org/10.1007/s00521-016-2285-9
Hamdan B, Mokhtar K (2016) Face recognition using angular radial transform. J King Saud Univ Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2016.10.006
Harish M, Karthick R, Rajan RM, Vetriselvi V (2019) Iccce 2018. In: Proceedings of the international conference on communications and cyber physical engineering 2018, vol 500. https://doi.org/10.1007/978-981-13-0212-1
Hassner T, Sahin G, Medioni G, Masi I, Tu A (2019) Face-specific data augmentation for unconstrained face recognition. Int J Comput Vis 127:642–667. https://doi.org/10.1007/s11263-019-01178-0
Hatanaka Y, Tajima M, Kawasaki R, Saito K, Ogohara K, Muramatsu C, Fujita H (2017) Retinal biometrics based on iterative closest point algorithm. In: Proceedings of the annual international conference of the IEEE engineering in medicine and biology society, EMBS. https://doi.org/10.1109/EMBC.2017.8036840
Haware S, Barhatte A (2017) Retina based biometric identification using SURF and ORB feature descriptors. In: 2017 international conference on microelectronic devices, circuits and systems, ICMDCS 2017, 2017 January, pp 1–6. https://doi.org/10.1109/ICMDCS.2017.8211697
Heinsohn D, Villalobos E, Prieto L, Mery D (2019) Face recognition in low-quality images using adaptive sparse representations. Image Vis Comput 85:46–58. https://doi.org/10.1016/j.imavis.2019.02.012
Hemanth J (2018) Palm vein recognition based on competitive code, LBP and DCA fusion strategy
Hofbauer H, Jalilian E, Uhl A (2019) Exploiting superior CNN-based iris segmentation for better recognition accuracy. Pattern Recognit Lett 120:17–23. https://doi.org/10.1016/j.patrec.2018.12.021
Hosny KM, Elaziz MA (n.d.) Face recognition using exact Gaussian-hermit moments. https://doi.org/10.1007/978-3-030-03000-1
Hou B, Yan R (2019) Convolutional auto-encoder model for finger-vein verification. IEEE Trans Instrum Meas. https://doi.org/10.1109/tim.2019.2921135
Hsieh SH, Li YH, Wang W, Tien CH (2018) A novel anti-spoofing solution for iris recognition toward cosmetic contact lens attack using spectral ICA analysis. Sensors (Switzerland). https://doi.org/10.3390/s18030795
Hu Y, Sirlantzis K, Howells G (2017) A novel iris weight map method for less constrained iris recognition based on bit stability and discriminability. Image Vis Comput 58:168–180. https://doi.org/10.1016/j.imavis.2016.05.003
Huang J, Zhang Y, Zhang H, Cheng K (2019) Sparse representation face recognition based on gabor and CSLDP feature fusion. In: 2019 Chinese control and decision conference (CCDC), no 1, pp 5697–5701
Hussein ME, Spinoulas L, Xiong F, Abd-Almageed W (2019) Fingerprint presentation attack detection using a novel multi-spectral capture device and patch-based convolutional neural networks. In: 10th IEEE international workshop on information forensics and security. WIFS 2018:1–8. https://doi.org/10.1109/WIFS.2018.8630773
Ito K, Aoki T (2018) Recent advances in biometric recognition. ITE Trans Media Technol Appl 6(1):64–80. https://doi.org/10.3169/mta.6.64
Jacob IJ (2019) Capsule network based biometric recognition system 01(02):83–93
Jain A, East L, Ruud B, Pankanti S, Yorktown H (2002) Introduction to biometrics. Anil Jain Michigan State University. Biometrics: Personal Identification in Networked Society (ii), p 19
Jain AK, Kumar A (2012) Biometric recognition: an overview, pp 49–79. https://doi.org/10.1007/978-94-007-3892-8_3
Jalilian E, Uhl A (2019) Enhanced segmentation-CNN based finger-vein recognition by joint training with automatically generated and manual labels. In: 2019 IEEE 5th international conference on identity, security, and behavior analysis (ISBA), pp 1–8. https://doi.org/10.1109/isba.2019.8778522
Jang HU, Kim D, Mun SM, Choi S, Lee HK (2017) DeepPore: fingerprint pore extraction using deep convolutional neural networks. IEEE Signal Process Lett 24(12):1808–1812. https://doi.org/10.1109/LSP.2017.2761454
Jasim YA, Al-Ani AA, Al-Ani LA (2019) Iris recognition using principal component analysis. In: Proceedings—2018 1st annual international conference on information and sciences, AiCIS 2018, pp 89–95. https://doi.org/10.1109/AiCIS.2018.00028
Jeon WS, Rhee SY (2017) Fingerprint pattern classification using convolution neural network. Int J Fuzzy Logic Intell Syst 17(3):170–176. https://doi.org/10.5391/IJFIS.2017.17.3.170
Ji H, Sun Q, Ji Z, Yuan Y, Zhang G (2017) Collaborative probabilistic labels for face recognition from single sample per person. Pattern Recognit 62:125–134. https://doi.org/10.1016/j.patcog.2016.08.007
Joshi I, Anand A, Vatsa M, Singh R, Roy SD, Kalra PK (2019) Latent fingerprint enhancement using generative adversarial networks. In: Proceedings—2019 IEEE winter conference on applications of computer vision, WACV 2019, pp 895–903. https://doi.org/10.1109/WACV.2019.00100
Kang W, Lu Y, Li D, Jia W (2019) From noise to feature: Exploiting intensity distribution as a novel soft biometric trait for finger vein recognition. IEEE Trans Inf Forens Secur 14(4):858–869
Kaur B, Singh S, Kumar J (2018) Robust iris recognition using moment invariants. Wireless Pers Commun 99(2):799–828. https://doi.org/10.1007/s11277-017-5153-8
Keilbach P, Kolberg J, Gomez-Barrero M, Busch C, Langweg H (2018) Fingerprint presentation attack detection using laser speckle contrast imaging. In: 2018 international conference of the biometrics special interest group, BIOSIG 2018, pp 1–6. https://doi.org/10.23919/BIOSIG.2018.8552931
Kerrigan D, Trokielewicz M, Czajka A, Bowyer K (2019) Iris recognition with image segmentation employing retrained off-the-shelf deep neural networks. http://arxiv.org/abs/1901.01028
Khan T, Donald B, Khan M, Kong Y (1983) Efficient hardware implementation for fingerprint image enhancement using anisotropic gaussian filter. IEEE Trans Image Process 23(1):309–317. https://doi.org/10.1002/qua.560230126
Khan AI, Wani MA (2019) Patch-based segmentation of latent fingerprint images using convolutional neural network. Appl Artif Intell 33(1):87–100. https://doi.org/10.1080/08839514.2018.1526704
Khodadoust J, Khodadoust AM (2017) Fingerprint indexing based on minutiae pairs and convex core point. Pattern Recognit 67:110–126
Kim H, Cui X, Kim MG, Nguyen THB (2019) Fingerprint generation and presentation attack detection using deep neural networks. In: Proceedings—2nd international conference on multimedia information processing and retrieval, MIPR 2019, pp 375–378. https://doi.org/10.1109/MIPR.2019.00074
Kr P, Lenc L (2019) Novel texture descriptor family for face recognition 2:37–47. https://doi.org/10.1007/978-3-030-20915-5
Kr P, Lenc L (2019) Enhanced local binary patterns for automatic face recognition 2:27–36. https://doi.org/10.1007/978-3-030-20915-5
Král P, Lenc L and Vrba A (2019) Enhanced local binary patterns for automatic face recognition. In: International conference on artificial intelligence and soft computing. Springer, Cham, pp 27–36
Krish RP, Fierrez J, Ramos D, Alonso-Fernandez F, Bigun J (2019) Improving automated latent fingerprint identification using extended minutia types. Inf Fusion 50:9–19. https://doi.org/10.1016/j.inffus.2018.10.001
Kumar SVM, Nishanth R, Sani N, Joseph AJ, Martin A (2019) Specular reflection removal using morphological filtering for accurate iris recognition. In: 6th IEEE international conference on smart structures and systems, ICSSS 2019, pp 1–4. https://doi.org/10.1109/ICSSS.2019.8882863
Lee EC, Jung H, Kim D (2011) New finger biometric method using near infrared imaging. Sensors 11(3):2319–2333. https://doi.org/10.3390/s110302319
Li C (2017) Dependence structure of gabor wavelets for face recognition, pp 0–4
Li J, Feng J, Kuo CCJ (2018) Deep convolutional neural network for latent fingerprint enhancement. Signal Process Image Commun 60:52–63. https://doi.org/10.1016/j.image.2017.08.010
Li L, Ge H, Tong Y, Zhang Y (2017). Face recognition using gabor-based feature extraction and feature space transformation fusion method for single image per person problem. https://doi.org/10.1007/s11063-017-9693-4
Li G, Kim J (2016) Author’s accepted manuscript palmprint recognition with local micro-structure tetra pattern reference. Pattern Recognit. https://doi.org/10.1016/j.patcog.2016.06.025
Lin BS, Yao YH, Liu CF, Lien CF, Lin BS (2017) Impact of the lips for biometrics. IEEE Access 5:794–801. https://doi.org/10.1109/ACCESS.2017.2649838
Linsangan NB, Panganiban AG, Flores PR, Poligratis HAT, Victa AS, Torres JL, Villaverde J (2019) Real-time iris recognition system for non-ideal iris images. ACM Int Conf Proc Ser. https://doi.org/10.1145/3313991.3314002
Liu JLC, Chen X, Zhou J, Tan T, Zheng N, Zha H, Hutchison D (2018) Pattern recognition and computer vision
Liu X, Kan M, Wu W, Shan S (2017) VIPLFaceNet : an open source deep face recognition SDK 11(2):208–218
Liu N, Liu J, Sun Z, Tan T (2017) A code-level approach to heterogeneous iris recognition. IEEE Trans Inf Forens Secur 12(10):2373–2386. https://doi.org/10.1109/TIFS.2017.2686013
Liu Y, Member S, Lin C, Guo J, Member S (2012) Impact of the lips in facial biometrics 21(6):3092–3101
Liu H, Yang L, Yang G, Yin Y (2018) Discriminative binary descriptor for finger vein recognition. IEEE Access 6:5795–5804. https://doi.org/10.1109/ACCESS.2017.2787543
Liu H, Yang G, Yang L, Yin Y (2019) Learning personalized binary codes for finger vein recognition. Neurocomputing 365:62–70. https://doi.org/10.1016/j.neucom.2019.07.057
Liu M, Zhou Z, Shang P, Xu D (2019) Fuzzified image enhancement for deep learning in iris recognition. IEEE Trans Fuzzy Syst. https://doi.org/10.1109/tfuzz.2019.2912576
Llano EG, García Vázquez MS, Vargas JMC, Fuentes LMZ, Ramírez Acosta AA (2018) Optimized robust multi-sensor scheme for simultaneous video and image iris recognition. Pattern Recognit Lett 101:44–51. https://doi.org/10.1016/j.patrec.2017.11.012
Lu J, Member S, Liong VE, Member S, Zhou J (2017) Simultaneous local binary feature learning and encoding for homogeneous and heterogeneous face recognition 8828:1–14. https://doi.org/10.1109/TPAMI.2017.2737538
Lu Yu, Xie S, Wu S (2019) Exploring competitive features using deep convolutional neural network for finger vein recognition. IEEE Access 7:35113–35123. https://doi.org/10.1109/ACCESS.2019.2902429
Lu Y, Yan J, Gu K (2018) Review on automatic lip reading techniques. Int J Pattern Recognit Artif Intell 32(7):1–21. https://doi.org/10.1142/S0218001418560074
Lv J (2018) A new discriminative collaborative neighbor representation method for robust face recognition, pp 74713–74727
Lv J-J, Shao X, Huang J, Zhou X, Zhou X, Lv J, Zhou X (2016) Face-specific data augmentation for unconstrained face recognition. Neurocomputing. https://doi.org/10.1016/j.neucom.2016.12.025
Malik F, Azis A, Nasrun M, Setianingsih C, Murti MA (2018) Face recognition in night day using method eigenface, pp 103–108
Manickam A, Devarasan E, Manogaran G, Priyan MK, Varatharajan R, Hsu CH, Krishnamoorthi R (2019) Score level based latent fingerprint enhancement and matching using SIFT feature. Multimed Tools Appl 78(3):3065–3085. https://doi.org/10.1007/s11042-018-5633-1
Mariño C, Penedo MG, Penas M, Carreira MJ, Gonzalez F (2006) Personal authentication using digital retinal images. Pattern Anal Appl 9(1):21–33. https://doi.org/10.1007/s10044-005-0022-6
Marra F, Poggi G, Sansone C, Verdoliva L (2018) A deep learning approach for iris sensor model identification. Pattern Recognit Lett 113:46–53. https://doi.org/10.1016/j.patrec.2017.04.010
Mathematics A (2018) Biometric retinal security system for user identification and authentication in smartphones 119(14):187–202
Mazumdar JB (2018) Retina based biometric authentication system: a review. Int J Adv Res Comput Sci 9(1):711–718. https://doi.org/10.26483/ijarcs.v9i1.5322
Mazumdar JB, Nirmala SR (2018) Retina based biometric authentication system: a review. Int J Adv Res Comp Sci 9(1):711–718
Mazumdar J, Nirmala SR (2019) Person identification using parabolic model-based algorithm in color retinal images. https://doi.org/10.18178/ijeetc.8.6.358-366
Meng XJ, Yin YL, Yang GP, Xi XM (2013) Retinal identification based on an improved circular gabor filter and scale invariant feature transform. Sensors (Switzerland) 13(7):9248–9266. https://doi.org/10.3390/s130709248
Minaee S, Abdolrashidi A (2019) DeepIris: iris recognition using a deep learning approach. http://arxiv.org/abs/1907.09380
Mir SA, Khan S, Bhat MA, Mehraj H (2018) Person identification by lips using SGLDM and support vector machine 4(1):152–157
Miura N, Nagasaka A, Miyatake T (2004) Feature extraction of finger vein patterns based on iterative line tracking and its application to personal identification. Syst Comput Jpn 35(7):61–71. https://doi.org/10.1002/scj.10596
Miura N, Nagasaka A, Miyatake T (2007) Extraction of finger-vein patterns using maximum curvature points in image profiles. IEICE Trans Inf Syst E90-D(8):1185–1194. https://doi.org/10.1093/ietisy/e90-d.8.1185
Moorfield J, Wang S, Yang W, Bedari A, Van Der Kamp P (2020) A Möbius transformation based model for fingerprint minutiae variations. Pattern Recognit 98:107054. https://doi.org/10.1016/j.patcog.2019.107054
Morales S, Naranjo V, Angulo J, Legaz-Aparicio AG, Verdú-Monedero R (2017) Retinal network characterization through fundus image processing: significant point identification on vessel centerline. Signal Process Image Commun 59:50–64. https://doi.org/10.1016/j.image.2017.03.013
Mura V, Orru G, Casula R, Sibiriu A, Loi G, Tuveri P et al. (2018) LivDet 2017 fingerprint liveness detection competition 2017. In: Proceedings—2018 international conference on biometrics, ICB 2018, pp 297–302. https://doi.org/10.1109/ICB2018.2018.00052
Nachar R, Inaty E, Bonnin PJ, Alayli Y (2020) Hybrid minutiae and edge corners feature points for increased fingerprint recognition performance. Pattern Anal Appl 23(1):213–222
Naseem I, Aleem A, Togneri R, Bennamoun M (2017) Iris recognition using class-specific dictionaries. Comput Electr Eng 62:178–193. https://doi.org/10.1016/j.compeleceng.2015.12.017
Nguyen DL, Cao K, Jain AK (2019) Automatic latent fingerprint segmentation. In: 2018 IEEE 9th international conference on biometrics theory, applications and systems, BTAS 2018, pp 1–9. https://doi.org/10.1109/BTAS.2018.8698544
Nguyen DL, Cao K, Jain AK (2018) Robust minutiae extractor: integrating deep networks and fingerprint domain knowledge. In: Proceedings—2018 international conference on biometrics, ICB 2018, pp 9–16. https://doi.org/10.1109/ICB2018.2018.00013
Nguyen K, Fookes C, Jillela R, Sridharan S, Ross A (2017) Long range iris recognition: a survey. Pattern Recognit 72:123–143. https://doi.org/10.1016/j.patcog.2017.05.021
Nguyen K, Fookes C, Ross A, Sridharan S (2017) Iris recognition with off-the-shelf CNN features: a deep learning perspective. IEEE Access 6:18848–18855. https://doi.org/10.1109/ACCESS.2017.2784352
Oliveira A, Pereira S, Silva CA (2018) Retinal vessel segmentation based on fully convolutional neural networks. Expert Syst Appl 112:229–242. https://doi.org/10.1016/j.eswa.2018.06.034
Pandya B, Cosma G, Alani AA, Taherkhani A, Bharadi V, McGinnity TM (2018) Fingerprint classification using a deep convolutional neural network. In: 2018 4th international conference on information management, ICIM 2018, pp 86–91. https://doi.org/10.1109/INFOMAN.2018.8392815
Panetta K, Kamath SKM, Rajeev S, Agaian SS (2019) LQM: localized quality measure for fingerprint image enhancement. IEEE Access 7:104567–104576. https://doi.org/10.1109/access.2019.2931980
Parihar RS, Jain S (2019) A robust method to recognize palm vein using SIFT and SVM classifier 1:1703–1710
Park Y, Jang U, Lee EC (2018) Statistical anti-spoofing method for fingerprint recognition. Soft Comput 22(13):4175–4184. https://doi.org/10.1007/s00500-017-2707-3
Park K, Song M, Youn Kim S (2018) The design of a single-bit CMOS image sensor for iris recognition applications. Sensors (Switzerland). https://doi.org/10.3390/s18020669
Pei T, Zhang L, Wang B (2016) Decision Pyramid Classifier for face recognition under complex variations using single sample per person. Pattern Recognit. https://doi.org/10.1016/j.patcog.2016.11.016
Peng C, Gao X, Wang N, Li J (2018) Face recognition from multiple stylistic sketches: scenarios, datasets, and evaluation. Pattern Recognit 84:262–272. https://doi.org/10.1016/j.patcog.2018.07.014
Peralta D, García S, Benitez JM, Herrera F (2017) Minutiae-based fingerprint matching decomposition: methodology for big data frameworks. Inf Sci 408:198–212. https://doi.org/10.1016/j.ins.2017.05.001
Piciucco E, Maiorana E, Campisi P (2017) Biometric fusion for palm-vein-based recognition systems palm vein biometric recognition: state of the art, pp 18–28. https://doi.org/10.1007/978-3-319-67639-5
Piciucco E, Maiorana E, Campisi P (2018) Palm vein recognition using a high dynamic range approach, pp 1–8. https://doi.org/10.1049/iet-bmt.2017.0192
Qin H, He X, Yao X, Li H (2017) Finger-vein verification based on the curvature in Radon space. Expert Syst Appl 82:151–161. https://doi.org/10.1016/j.eswa.2017.03.068
Qin H, Wang P (2019) Finger-vein verification based on LSTM recurrent neural networks. Appl Sci (Switzerland) 9(8):1–18. https://doi.org/10.3390/app9081687
Qureshi I, Khan MA, Sharif M, Saba T, Ma J (2020) Detection of glaucoma based on cup-to-disc ratio using fundus images 19(1):1–16
Qureshi I, Ma J, Abbas Q (2019) Recent development on detection methods for the diagnosis of diabetic retinopathy. Symmetry 11(6):1–34. https://doi.org/10.3390/sym11060749
Qureshi I, Ma J, Shaheed K (2019) A hybrid proposed fundus image enhancement framework for diabetic retinopathy, pp 1–16. https://doi.org/10.3390/a12010014
Raja KB, Raghavendra R, Venkatesh S, Busch C (2017) Multi-patch deep sparse histograms for iris recognition in visible spectrum using collaborative subspace for robust verification. Pattern Recognit Lett 91:27–36. https://doi.org/10.1016/j.patrec.2016.12.025
Ramachandra R, Raja KB, Venkatesh SK, Busch C (2019) Design and development of low-cost sensor to capture ventral and dorsal finger vein for biometric authentication. IEEE Sens J 19(15):6102–6111. https://doi.org/10.1109/JSEN.2019.2906691
Rana HK (2017) SM Gr up SM journal of iris recognition system using PCA based on DWT. SM J Biometrics Biostat 2:1015. https://doi.org/10.5281/zenodo.2580202
Ranjani R, Priya C (2018) A survey on face recognition techniques: a review. Int J Pure Appl Math 118:253–274
Rathgeb C, Wagner J, Busch C (2019) SIFT-based iris recognition revisited: prerequisites, advantages and improvements. Pattern Anal Appl 22(3):889–906. https://doi.org/10.1007/s10044-018-0719-y
Roy ND, Biswas A (2019) Fast and robust retinal biometric key generation using deep neural nets
Rui Z, Yan Z (2019) A survey on biometric authentication: toward secure and privacy-preserving identification. IEEE Access 7:5994–6009. https://doi.org/10.1109/ACCESS.2018.2889996
Sahu B, Kumar Sa P, Bakshi S, Sangaiah AK (2018) Reducing dense local feature key-points for faster iris recognition. Comput Electr Eng 70:939–949. https://doi.org/10.1016/j.compeleceng.2017.12.048
Sang J, Wang H, Qian Q, Wu H, Chen Y (2018) An efficient fingerprint identification algorithm based on minutiae and invariant moment. Pers Ubiquit Comput 22(1):71–80. https://doi.org/10.1007/s00779-017-1094-1
De Santis M, Agnelli S, Don V, Gnocchi C (2017) 3D ultrasound palm vein recognition through the centroid method for biometric purposes, pp 1–4
Shaheed K, Liu H, Yang G, Qureshi I, Gou J, Yin Y (2018) A systematic review of finger vein recognition techniques. Information (Switzerland). https://doi.org/10.3390/info9090213
Shaheed K, Yang L, Yang G, Qureshi I, Yin Y (2018) Novel image quality assessment and enhancement techniques for finger vein recognition, pp 223–231
Shao L, Zhu R, B QZ (2016) A finger vein identification system based on image quality assessment, vol 3, pp 711–719. https://doi.org/10.1007/978-3-319-46654-5
Sharma RP, Dey S (2019). Quality analysis of fingerprint images using local phase quantization. https://doi.org/10.1007/978-3-030-29888-3_53
Shuyi L, Haigang Z, Jinfeng Y (2019) Finger vein recognition based on local graph structural coding and CNN. May, vol 8. https://doi.org/10.1117/12.2524152
Soh SC, Ibrahim MZ, Abas MF (2019) Image fusion based multi resolution and frequency partition discrete cosine transform for palm vein recognition. In: 2019 IEEE 6th international conference on industrial engineering and applications (ICIEA), pp 367–371
Soh SC, Ibrahim MZ, Yakno MB, Mulvaney DJ (2017) Palm vein recognition using scale invariant feature transform with RANSAC mismatching removal. IT Converg Secur 2017:2. https://doi.org/10.1007/978-981-10-6451-7
Song JM, Kim W, Park KR (2019) Finger-vein recognition based on deep densenet using composite image. IEEE Access 7:66845–66863. https://doi.org/10.1109/ACCESS.2019.2918503
de Souza GB, Santos DFdS, Pires RG, Marana AN, Papa JP (2018) Deep features extraction for robust fingerprint spoofing attack detection. J Artif Intell Soft Comput Res 9(1):41–49. https://doi.org/10.2478/jaiscr-2018-0023
Sun Y, Wang X, Tang X (2013) Deep convolutional network cascade for facial point detection. https://doi.org/10.1109/CVPR.2013.446
Sundararajan K, Woodard DL (2018) Deep learning for biometrics: a survey. ACM Comput Surv. https://doi.org/10.1145/3190618
Sutanty E, Rahayu DA, Rodiah, Susetianingtias DT, Madenda S (2017) Retinal blood vessel segmentation and bifurcation detection using combined filters. In: Proceeding—2017 3rd international conference on science in information technology: theory and application of IT for education, industry and society in big data era, ICSITech 2017, 2018 January, pp 563–567. https://doi.org/10.1109/ICSITech.2017.8257176
Svoboda J, Monti F, Bronstein MM (2018) Generative convolutional networks for latent fingerprint reconstruction. In: IEEE international joint conference on biometrics, IJCB 2017, 2018 January, pp 429–436. https://doi.org/10.1109/BTAS.2017.8272727
Syarif MA, Ong TS, Teoh ABJ, Tee C (2017) Enhanced maximum curvature descriptors for finger vein verification. Multimed Tools Appl 76(5):6859–6887. https://doi.org/10.1007/s11042-016-3315-4
Tams B (2013) Absolute fingerprint pre-alignment in minutiae-based cryptosystems. In: BIOSIG 2013—proceedings of the 12th international conference of the biometrics special interest group, pp 1–12
Tang Z, Wu X, Fu B, Chen W, Feng H (2018) Fast face recognition based on fractal theory. Appl Math Comput 321:721–730. https://doi.org/10.1016/j.amc.2017.11.017
Article MathSciNet MATH Google Scholar
Tann H, Zhao H, Reda S (2019) A resource-efficient embedded iris recognition system using fully convolutional networks. ACM J Emerg Technol Comput Syst 16(1):1–23. https://doi.org/10.1145/3357796
Tertychnyi P, Ozcinar C, Anbarjafari G (2018) Low-quality fingerprint classification using deep neural network. IET Biometrics 7(6):550–556. https://doi.org/10.1049/iet-bmt.2018.5074
Thapar D, Jaswal G, Nigam A (2018) PVSNet: palm vein authentication siamese network trained using triplet loss and adaptive hard mining by learning enforced domain specific features. In: 2019 IEEE 5th international conference on identity, security, and behavior analysis (ISBA), pp 1–8
Thompson J, Flynn P, Boehnen C, Santos-Villalobos H (2019) Assessing the impact of corneal refraction and iris tissue non-planarity on iris recognition. IEEE Trans Inf Forens Secur 14(8):2102–2112. https://doi.org/10.1109/TIFS.2018.2869342
Tran MH, Duong TN, Nguyen DM, Dang QH (2017) A local feature vector for an adaptive hybrid fingerprint matcher. In: Proceedings of KICS-IEEE international conference on information and communications with samsung LTE and 5G special workshop, ICIC 2017, pp 249–253. https://doi.org/10.1109/INFOC.2017.8001668
Travieso CM, Ravelo-García AG, Alonso JB, Canino-Rodríguez JM, Dutta MK (2019) Improving the performance of the lip identification through the use of shape correction. Appl Intell 49(5):1823–1840
Travieso CM, Zhang J, Miller P, Alonso JB (2014) Using a discrete Hidden Markov Model Kernel for lip-based biometric identification. Image Vis Comput 32(12):1080–1089. https://doi.org/10.1016/j.imavis.2014.10.001
Unar JA, Seng WC, Abbasi A (2014) A review of biometric technology along with trends and prospects. Pattern Recognit 47(8):2673–2688. https://doi.org/10.1016/j.patcog.2014.01.016
Wan C, Wang L, Phoha VV (2018) A survey on gait recognition. ACM Comput Surv. https://doi.org/10.1145/3230633
Wang X (2019) Palm vein recognition based on competitive code and, pp 179–183
Wang K, Kumar A (2019) Toward more accurate iris recognition using dilated residual features. IEEE Trans Inf Forens Secur 14(12):3233–3245
Wang Z, Ma S, Han M, Hu G (2017) Long-distance/environment face image enhancement method for recognition, no 1, pp 501–511. https://doi.org/10.1007/978-3-319-71607-7
Wang H, Yang X, Ma L, Liang R (2017) Fingerprint pore extraction using U-Net based fully convolutional network 1:474–483. https://doi.org/10.1007/978-3-319-69923-3
Xi X, Yang L (2017) Learning discriminative binary codes for finger vein recognition. Pattern Recognit 66:26–33. https://doi.org/10.1016/j.patcog.2016.11.002
Xia Z, Lv R, Zhu Y, Ji P, Sun H, Shi YQ (2017) Fingerprint liveness detection using gradient-based texture features. SIViP 11(2):381–388. https://doi.org/10.1007/s11760-016-0936-z
Xin M (2017) Palm vein recognition method based on fusion of local Gabor histograms. J China Univ Posts Telecommun 24(6):55–66. https://doi.org/10.1016/S1005-8885(17)60242-5
Yahaya YH, Shamsuddin SM, Leng WY, Technology D, Pertahanan U (2016) Finger vein feature extraction using discretization. November, pp 28–29
Yang W, Huang X, Zhou F, Liao Q (2014) Comparative competitive coding for personal identification by using finger vein and finger dorsal texture fusion. Inf Sci 268:20–32. https://doi.org/10.1016/j.ins.2013.10.010
Yang W, Ji W, Xue JH, Ren Y, Liao Q (2019) A hybrid finger identification pattern using polarized depth-weighted binary direction coding. Neurocomputing 325:260–268. https://doi.org/10.1016/j.neucom.2018.10.042
Yang W, Ma G, Li W, Liao Q (2013) Finger vein verification based on neighbor pattern coding. IEICE Trans Inf Syst E96-D(5):1227–1229. https://doi.org/10.1587/transinf.E96.D.1227
Yang J, Shi Y, Jia G (2017) Finger-vein image matching based on adaptive curve transformation. Pattern Recognit 66:34–43. https://doi.org/10.1016/j.patcog.2017.01.008
Yang W, Wang S, Hu J, Zheng G, Valli C (2019) Security and accuracy of fingerprint-based biometrics: a review. Symmetry. https://doi.org/10.3390/sym11020141
Yang W, Wang S, Hu J, Zheng G, Yang J, Valli C (2019) Securing deep learning based edge finger vein biometrics with binary decision diagram. IEEE Trans Ind Inf 15(7):4244–4253. https://doi.org/10.1109/TII.2019.2900665
Yang M, Wang X, Zeng G, Shen L (2017) Joint and collaborative representation with local adaptive convolution feature for face recognition with single sample per person. Pattern Recognit 66:117–128. https://doi.org/10.1016/j.patcog.2016.12.028
Yang J, Wei J, Shi Y (2019) Accurate ROI localization and hierarchical hyper-sphere model for finger-vein recognition. Neurocomputing 328:171–181. https://doi.org/10.1016/j.neucom.2018.02.098
Yang L, Yang G, Wang K, Liu H, Xi X, Yin Y (2019) Point grouping method for finger vein recognition. IEEE Access 7:28185–28195. https://doi.org/10.1109/ACCESS.2019.2901017
Yang L, Yang G, Xi X, Meng X, Zhang C, Yin Y (2017) Tri-branch vein structure assisted finger vein recognition. IEEE Access 5:21020–21028. https://doi.org/10.1109/ACCESS.2017.2728797
Yang L, Yang G, Yin Y, Xi X (2018) Finger vein recognition with anatomy structure analysis. IEEE Trans Circuits Syst Video Technol 28(8):1892–1905. https://doi.org/10.1109/TCSVT.2017.2684833
Ye L, Wang H, Du M, He Y, Tao L (2019) Weber local descriptor with edge detection and double Gabor orientations for finger vein recognition. In: Tenth international conference on graphics and image processing (ICGIP 2018), vol 11069. International Society for Optics and Photonics, p 110693J
Yin B, Tran L, Li H, Shen X, Liu X (2018) Towards interpretable face recognition, pp 9348–9357
You W, Zhou W, Huang J, Yang F, Liu Y, Chen Z (2019) A bilayer image restoration for finger vein recognition. Neurocomputing 348:54–65. https://doi.org/10.1016/j.neucom.2018.06.085
Yuan X, Gu L, Chen T, Elhoseny M, Wang W (2018) A fast and accurate retina image verification method based on structure similarity. In: Proceedings—IEEE 4th international conference on big data computing service and applications, BigDataService 2018, pp 181–185. https://doi.org/10.1109/BigDataService.2018.00034
Yuan C, Li X, Wu QMJ, Li J, Sun X (2017) Fingerprint liveness detection from different fingerprint materials using convolutional neural network and principal component analysis. Comput Mater Continua 53(4):357–371
Yuan C, Sun X, Wu QMJ (2019) Difference co-occurrence matrix using BP neural network for fingerprint liveness detection. Soft Comput 23(13):5157–5169. https://doi.org/10.1007/s00500-018-3182-1
Zafar U, Ghafoor M, Zia T, Ahmed G, Latif A, Malik KR, Sharif AM (2019) Face recognition with Bayesian convolutional networks for robust surveillance systems
Zhang M, He Z, Zhang H, Tan T, Sun Z (2019) Toward practical remote iris recognition: a boosting based framework. Neurocomputing 330:238–252. https://doi.org/10.1016/j.neucom.2017.12.053
Zhang Y, Li W, Zhang L, Lu Y (2019) Adaptive gabor convolutional neural networks for finger-vein recognition. In: 2019 International Conference on High Performance Big Data and Intelligent systems, HPBD and IS 2019, (61572458), pp 219–222. https://doi.org/10.1109/HPBDIS.2019.8735471
Zhang Y, Shi D, Zhan X, Cao D, Zhu K, Li Z (2019) Slim-ResCNN: a deep residual convolutional neural network for fingerprint liveness detection. IEEE Access 7:91476–91487. https://doi.org/10.1109/access.2019.2927357
Zhao Z, Kumar A (2017) Towards more accurate iris recognition using deeply learned spatially corresponding features. In: Proceedings of the IEEE international conference on computer vision, 2017 October, pp 3829–3838. https://doi.org/10.1109/ICCV.2017.411
Zhao T, Liu Y, Huo G, Zhu X (2019) A deep learning iris recognition method based on capsule network architecture. IEEE Access 7:49691–49701. https://doi.org/10.1109/ACCESS.2019.2911056
Download references
Acknowledgements
The work of this paper is financially supported by NSF of Guangdong Province (No. 2019A1515010833) and fundamental Research Funds for the Central Universities (No. 2020ZYGXZR089).
Author information
Authors and affiliations.
School of Computer Science and Engineering, South China University of Technology, Guangzhou, 510006, China
Kashif Shaheed, Aihua Mao & Xingming Zhang
Key Laboratory of Space Photoelectric Detection and Perception, Ministry of Industry and Information Technology and College of Astronautics, Nanjing University of Aeronautics and Astronautics, Nanjing, 211106, Jiangsu, China
Imran Qureshi
Department of Computational Sciences, Maharaja Ranjit Singh Punjab Technical University, Bathinda, Punjab, 151001, India
Munish Kumar
College of Computer and Information Sciences, Imam Muhammad Ibn Saud Islamic University (IMSIU), Riyadh, 11432, Saudi Arabia
Qaisar Abbas
School of Software Engineering, Shandong University, Jinan, 250100, China
You can also search for this author in PubMed Google Scholar
Corresponding authors
Correspondence to Kashif Shaheed or Aihua Mao .
Ethics declarations
Conflict of interest.
The authors declare that they have no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Shaheed, K., Mao, A., Qureshi, I. et al. A Systematic Review on Physiological-Based Biometric Recognition Systems: Current and Future Trends. Arch Computat Methods Eng 28 , 4917–4960 (2021). https://doi.org/10.1007/s11831-021-09560-3
Download citation
Received : 12 August 2020
Accepted : 28 January 2021
Published : 23 February 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s11831-021-09560-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Find a journal
- Publish with us
- Track your research
biometric security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Two-Level Biometric Security System For Voting
Optimized content adaptive approach for image detailed enhancement to reduce color distortion.
Digital imaging has significantly influenced the outcome of research in various disciplines. For example, artificial intelligence and robotics, biometric security, multimedia and image processing, etc. Technically, image processing and the Human Visual System (HVS) relies heavily on image enhancement to improve the content of the image. One of the biggest challenges in image processing is detail enhancement due to halo artefacts and gradient inversion artefacts at edges. It has been used to enhance the visual quality of an image. Most algorithms that used to enhance the detail of an image essentially depend on edge-preserving decomposition techniques. in general, the image consist of two major elements are a base layer and a detail layer, which extracted by edge-preserving decomposition algorithms. The detail layer is enhanced to improve the details of the generated image. we propose in this paper, a new model to preserve the sharp edges and achieve better visual quality than the existing norm-based algorithm to enhance the details of the image. Experiments show that the proposed method reduces the distortion at the edges. It improves the details of the generated image significantly.
Cancelable biometric security system based on advanced chaotic maps
Biometric security: a review to future.
This paper presents the different biometric with their limitations and introduces their alternative in form of brain biometric, Breath biometrics, and Tongue biometrics. Brain biometric uses brain wave while breath biometric uses one’s breath and tongue biometric uses a tongue’s shape and variation to distinguish them and present a good alternative for the presently used biometric like fingerprint, iris recognition, face recognition.
Biometric security management based on Internet of Things
Model of the "biometry-code" converter based on artificial neural networks for analysis of facial thermograms.
Existing asymmetric encryption algorithms involve the storage of a secret private key, authorized access to which, as a rule, is carried out upon presentation of a password. Passwords are vulnerable to social engineering and human factors. Combining biometric security techniques with cryptography is seen as a possible solution to this problem, but any biometric cryptosystem should be able to overcome the small differences that exist between two different implementations of the same biometric parameter. This is especially true for dynamic biometrics, when differences can be caused by a change in the psychophysiological state of the subject. The solution to the problems is the use of a system based on the "biometrics-code" converter, which is configured to issue a user key after presentation of his/her biometric image. In this case, the key is generated in advance in accordance with accepted standards without the use of biometric images. The work presents results on using thermal images of a user for reliable biometric authentication based on a neural network "biometrics-code" converter. Thermal images have recently been used as a new approach in biometric identification systems and are a special type of biometric images that allow us to solve the problem of both the authentication of the subject and the identification of his psychophysiological state. The advantages of thermal imaging are that this technology is now becoming available and mobile, allowing the user to be identified and authenticated in a non-contact and continuous manner. In this paper, an experiment was conducted to verify the images of thermograms of 84 subjects and the following indicators of erroneous decisions were obtained: EER = 0.85 % for users in the "normal"state.
Behavioral Biometric Data Analysis for Gender Classification Using Feature Fusion and Machine Learning
Biometric security applications have been employed for providing a higher security in several access control systems during the past few years. The handwritten signature is the most widely accepted behavioral biometric trait for authenticating the documents like letters, contracts, wills, MOU’s, etc. for validation in day to day life. In this paper, a novel algorithm to detect gender of individuals based on the image of their handwritten signatures is proposed. The proposed work is based on the fusion of textural and statistical features extracted from the signature images. The LBP and HOG features represent the texture. The writer’s gender classification is carried out using machine learning techniques. The proposed technique is evaluated on own dataset of 4,790 signatures and realized an encouraging accuracy of 96.17, 98.72 and 100% for k-NN, decision tree and Support Vector Machine classifiers, respectively. The proposed method is expected to be useful in design of efficient computer vision tools for authentication and forensic investigation of documents with handwritten signatures.
Enhanced Palmprint Identification Using Score Level Fusion
Palm print identification has been used in various applications in several years. Various methods have been proposed for providing biometric security through palm print authentication. One such a method was feature level fusion which used multiple feature extraction and gives higher accuracy. But it needed to design a new matcher and acquired many training samples. However, it cannot adapt to scenarios like multimodal biometric, regional fusion, contactless and complete direction representation. This problem will be overcome by score level fusion method. In this article, we propose a salient and discriminative descriptor learning method (SDDLM) and gray-level co-occurrence matrix (GLCM).The score values of SDDLM and GLCM are integrated using score level fusion to provide enhanced score. Experiments were conducted on IITD palm print V1 database. The combination of SDDLM AND GLCM methods will be useful in achieving higher performance. It provides good recognition rate and reduces computation burden.
AI and Deep Learning in Biometric Security
Challenges and opportunities in biometric security: a survey, export citation format, share document.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Sensors (Basel)

Biometric Recognition: A Systematic Review on Electrocardiogram Data Acquisition Methods
Teresa m. c. pereira.
1 IEETA, DETI, LASI, Universidade de Aveiro, 3810-193 Aveiro, Portugal
Raquel C. Conceição
2 Instituto de Biofísica e Engenharia Biomédica, Faculdade de Ciências da Universidade de Lisboa, Campo Grande, 1749-016 Lisboa, Portugal
Vitor Sencadas
3 Instituto de Materiais (CICECO), Departamento de Materiais e Cerâmica, Universidade de Aveiro, 3810-193 Aveiro, Portugal
Raquel Sebastião
Associated data.
Not applicable.
In the last decades, researchers have shown the potential of using Electrocardiogram (ECG) as a biometric trait due to its uniqueness and hidden nature. However, despite the great number of approaches found in the literature, no agreement exists on the most appropriate methodology. This paper presents a systematic review of data acquisition methods, aiming to understand the impact of some variables from the data acquisition protocol of an ECG signal in the biometric identification process. We searched for papers on the subject using Scopus, defining several keywords and restrictions, and found a total of 121 papers. Data acquisition hardware and methods vary widely throughout the literature. We reviewed the intrusiveness of acquisitions, the number of leads used, and the duration of acquisitions. Moreover, by analyzing the literature, we can conclude that the preferable solutions include: (1) the use of off-the-person acquisitions as they bring ECG biometrics closer to viable, unconstrained applications; (2) the use of a one-lead setup; and (3) short-term acquisitions as they required fewer numbers of contact points, making the data acquisition of benefit to user acceptance and allow faster acquisitions, resulting in a user-friendly biometric system. Thus, this paper reviews data acquisition methods, summarizes multiple perspectives, and highlights existing challenges and problems. In contrast, most reviews on ECG-based biometrics focus on feature extraction and classification methods.
1. Introduction
Nowadays, recognition systems are used in a variety of real-world applications to protect ourselves and our information. While some of these systems still depend on conventional technologies, such as cards, keys, or passwords, these mechanisms often have usability and security issues.
As a result, there has been a recent interest in the biometric field. Biometric recognition uses distinctive physiological and behavioral characteristics to automatically identify individuals. The former characteristics can include the face, fingerprint, iris, and hand geometry, whereas the latter can be gait signature and keystroke [ 1 ].
In recent years, researchers have been exploring the use of electrocardiogram (ECG) signals as a biometric recognition trait due to their unique properties: (1) liveness detection: Since the ECG is a recording of the electrical activity of the heart, ECG signals can only be acquired from living individuals [ 2 ]; (2) high security: ECG signals are extremely difficult to counterfeit and consequently, a technology to artificially produce them has not been developed yet [ 3 ]; (3) combined information: the analysis of ECG signals can give us information regarding the identity of a person, as well as heart conditions and emotional and physical status [ 4 ]. The most important advantage of ECG signals is their uniqueness among individuals, which is mainly due to changes in ionic potential, the levels of electrolytes in the plasma, and physiological differences caused by chest geometry, size, and position of the heart [ 2 ]. A typical ECG wave, such as the one presented in Figure 1 , consists of a P wave, a QRS complex, and a T wave.

The sequence of depolarization and repolarization events in the heart and their relationship with the different heartbeat waveforms in an ECG signal (adapted from [ 5 ], original figure kindly provided by the authors).
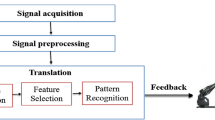
A biometric system is a technology that identifies or authenticates a person through their unique biometric traits. It consists of three main components: an acquisition module, which consists of a sensor that measures the biometric trait; a storage module, where personal data of enrolled subjects is stored); and a biometric algorithm. The biometric algorithm processes the data from the acquisition and storage modules, following two steps: feature extraction and pattern recognition [ 5 ]. Concerning a biometric system using ECG, signals can be acquired through different formats. The standard 12-lead ECG provides information on cardiac activity from 12 different leads over a short period of time, while Holter ECGs record electrical activity from five to seven leads over longer periods of time. Although 12-lead ECGs provide more information, they are not practical for real-world use. Instead, off-the-person methods that acquire ECG signals through skin or finger contact have become more common, making the process more convenient for users [ 6 ].
The advancement of sensing technology has made it possible to explore the use of ECG as a non-invasive biometric, similar to a fingerprint. This has made society’s acceptance of ECG as a biometric very promising [ 2 ]. In addition to traditional off-the-person methods, small wireless ECG body sensors are being developed for long-term monitoring. These sensors use a single lead to measure the electrical potential difference between electrodes placed near the heart. These sensors allow ECG analysis and monitoring to be used for a wider range of applications beyond diagnosing cardiovascular disorders [ 6 ]. However, when compared to medical devices such as Holter devices, wearable sensors produce noisier signals due to various factors, such as the type of electrodes and the number and location of leads. While medical ECG recorders use 12 or 6 wet electrodes, wearable devices typically use between one and three dry electrodes, with only the first lead being used due to its easy implementation in mobile devices. Medical ECG recorders generally provide more reliable data than wearable devices due to their longer and more detailed recording periods and the higher complexity of the setup [ 7 ].
In the next stage of the biometric process, features are extracted from the ECG data. These features are specific attributes of the ECG that allow for the recognition of a particular individual based on inter-subject variability. Feature extraction is a crucial step in pattern recognition. Approaches for feature extraction can be divided into three categories: fiducial, non-fiducial, and hybrid (or partially fiducial). Fiducial-based techniques rely on the accurate detection of reference points, such as the P wave, QRS complex, and T wave. These techniques can also use interval, amplitude, angle, and area measurements of these points as biometric features. However, these approaches require a lot of feature engineering, which can be time-consuming [ 8 , 9 ]. Non-fiducial-based ECG biometric detection methods do not require the detection of fiducial points. Instead, non-fiducial features are derived from segmented windows of ECG signals and may include autocorrelation coefficients and wavelet coefficients. Non-fiducial approaches often have a large number of redundant feature sets that need to be reduced [ 10 ]. Hybrid methods combine both fiducial and non-fiducial techniques by locating only the R-peaks. These are used to segment the ECG signal into single heartbeat waveforms, from which time or frequency domain information is extracted as features [ 8 ].
The final stage of the ECG recognition process consists of classification or pattern recognition. In this stage, the selected features of ECG signals are used as inputs for a classifier. The accuracy of the selection of the features will determine whether the classifier makes a correct or incorrect decision. There are many classification methods that have been proposed in recent years, including Bayesian Network, Linear Discriminant Analysis, Decision Trees, k-Nearest-Neighbors, Support Vector Machines, and Artificial Neural Networks. Each approach has its own advantages and disadvantages [ 10 ].
The success of identifying an individual through their ECG depends on the conditions they are exposed to during the acquisition process, the features that are extracted, and the classifiers used for identification or authentication. It is, therefore, important to evaluate the impact that certain changes have on biometric identification results [ 11 ]. This systematic review aims to discuss past research on the impact of variables in the data acquisition methods of an ECG signal on the biometric recognition process.
The paper is organized as follows: Section 2 presents the review methodology. Section 3 provides an overview of ECG acquisition and databases, which are discussed in Section 4 . Finally, the conclusions drawn are presented in Section 5 .
2. Review Methodology
In this section, the search strategy, which includes the identification, screening, and inclusion phases, is described, and the research questions we aim to answer are presented.
2.1. Search Strategy
This systematic review is structured according to Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) guidelines [ 12 ]. Our literature research was performed from 5 June to 7 October 2022 in the Scopus database. The process of literature search for this literature review is illustrated in Figure 2 , and it is a three-stage process consisting of identification, screening, and inclusion.

Flow diagram of the literature research process (adapted from Prisma Guidelines [ 12 ]).
2.1.1. Identification
For the identification stage, the following general search terms were compiled for the Scopus research on the title, abstract, and keywords fields: (biometric* OR biometry AND ecg* OR electrocardiogram* OR electrocardiography* OR electrocardiographic* OR heart* AND authentication OR identification OR verification OR recognition AND “data collection” OR “signal collection” OR acquisition* OR collection OR signal* OR “body sensors” OR “body sensor” OR sensor* OR biosensor* OR database* OR electrode*). This search resulted in 958 papers. Six of those were duplicates and were consequently removed. Thus, the identification stage resulted in a total of 952 papers.
2.1.2. Screening
Before moving to the manual process of screening, we applied some exclusion criteria in our research. The first criterion concerned the year of publication of the article; only the ones published between 2000 and 2022 were considered. The second criterion was related to the subject area and the following areas were included: computer science, engineering, mathematics, materials science, and decision science. All remaining areas were excluded from our search. The document type was also an exclusion criteria: only conference papers, articles, and reviews the types of paper were considered. Lastly, only papers in English were included. A total of 137 articles were excluded based on the inclusion and exclusion criteria. A total of 815 papers were retrieved from the exclusion criteria process. The second part of the screening stage was a manual process of document exclusion. The purpose of this step was to filter the articles based on their abstract, methodology, results, or findings section to ensure that the articles match the goal of this systematic review. The screening process involved two rounds. In the first round, filtering, and screening were performed to exclude studies based on their respective title and abstract. Studies that did not focus on ECG-based biometric recognition were eliminated in this stage, and a total of 542 articles continued to the following round. The second round performed filtering by an accurate full-text reading of the examined articles from the first round based on an accurate full-text reading. Studies were eliminated based on the following exclusion criteria: (1) not focusing on the data collection process; (2) using ECG for non-biometric purposes; (3) not developing a biometric system algorithm; (4) not available online; and (5) using ECG combined with other biometric traits in a multimodal system. A total of 285 papers were eliminated due to reason (1), seventeen (17) due to reason (2), twenty-eight (28) due to reason (3), thirty-eight (38) due to reason (4), and fifty-three (53) due to reason (5).
2.1.3. Inclusion
After the screening process, 99 studies were integrated into our search. However, we also added some other reports from citation searching (7), resulting in a total of 106 studies included in this systematic review. The majority of papers included were from the journals/conferences presented in Figure 3 (top). The bottom of this figure presents the temporal increase of research on ECG-based biometric systems.

Main journals of publications of the papers included in this systematic review ( top ), and temporal increase of the research on ECG-based biometric systems ( bottom ).
2.2. Research Questions
This work mainly aims to provide some answers to the following questions about the ECG data for biometric systems:
Question 1: How are the ECG signals collected for biometric systems? What is the acquisition hardware information? This review compares the various aspects of the acquisition hardware, such as the intrusiveness of the acquisition (on-the-person vs. off-the-person acquisitions), the number of leads used, and the duration of the acquisition. We also present the most used commercially available and the self-developed acquisition devices and compare them in Table 1 .
Overview of the commercially available and self-developed devices.
Question 2: What should the acquisition protocol look like for a biometric system? Which conditions of acquisition should be considered? The aim of the present systematic review is to evaluate and compare the acquisition protocol of different research concerning the number of subjects and the assessment of the stability of the ECG signal over time. Moreover, since the health status of the subjects is also considered by many researchers, this systematic review presents literature findings regarding the impact of physical conditions, posture, emotions, and cardiac conditions on a biometric system.
Question 3: Which ECG datasets are used for biometric purposes? What are the main differences between them? These questions are addressed in Section 3.3 by presenting a description of the most used ECG databases in the literature and by providing a comparison between them in Table 2 .
Overview of the most used databases in the literature.
Question 4: Which factors of the data acquisition influence the intra- and inter-subject variability? What impact can these two variables have on the performance of a biometric system? The answers to these questions are discussed in Section 4 , in which the sources of intra and inter-subject variability are described.
3. ECG Acquisition and Databases
Regarding ECG acquisition, we covered the characteristics of the systems and protocols, as well as commercially available and self-developed devices. Finally, this section presents an overview of the databases used for biometric purposes.
3.1. Data Acquisition
Data acquisition can be organized according to criteria, such as the acquisition hardware information and acquisition protocol.
3.1.1. Acquisition Hardware Information
To analyze the characteristics of the acquisition systems, we should consider the intrusiveness of the acquisition and the types of electrodes, the number of leads used, and the duration of the acquisition.
Intrusiveness
Since the early research on ECG-based biometrics, the configurations used for data acquisition have significantly evolved. Researchers have mostly focused on addressing the main disadvantage of ECG as a biometric trait: its intrusiveness during data acquisition [ 5 ]. This has led to the development of off-the-person data acquisition methods which are less intrusive than traditional medical settings that use multiple wet electrodes. Data acquisition methods can be broadly divided into two categories based on their level of intrusiveness:
Acquisition methods that require attachment to the body, such as wet Ag/AgCl electrodes applied to the skin with a conductive electrolyte gel, are known as on-the-person methods. This approach relies on half-cell potential, double-layer capacitance, and parallel and series resistances to function. Despite providing good signal quality, wet electrodes can irritate the skin and restrict the user’s movement and may also cause interference between neighboring electrodes. These factors must be considered when using on-the-person data acquisition methods [ 43 ].
This type of acquisition can either be medical or unrestricted by movement, such as through Holter systems. According to medical standards and guidelines, the standard 12-lead configuration allows for the acquisition of an ECG signal in 12 leads (or channels) using three bipolar limb leads, three monopolar limb leads, and six monopolar precordial leads. The orthogonal configuration, also called Frank leads, allows the acquisition of ECG signals using seven electrodes. In early ECG biometric research, recordings from standard 12-lead and Frank leads were used in the development and evaluation of algorithms [ 44 , 45 , 46 , 47 , 48 , 49 , 50 ]. Some researchers chose acquisitions without movement restrictions, with longer duration, and with fewer electrodes, such as Holter systems, which can acquire ECG signals for several hours while subjects perform their daily activities [ 7 , 51 ].
The off-the-person acquisition method refers to devices that are integrated in objects or surfaces with which the subjects interact (e.g., a computer keyboard) and do not require any special preparation of the subject [ 52 ]. Wet electrodes characteristic of medical acquisitions were replaced by dry metallic electrodes, which increase the long-term performance and cause low skin irritation. However, they have high impedance between the electrode and skin, and are susceptible to motion artifacts [ 43 ]. Off-the-person acquisitions reduce the number of leads to two or three, and their placements are confined to the upper limbs, especially on the wrists, hands, or fingers [ 5 , 15 , 16 , 20 , 24 , 53 , 54 , 55 ]. Recently, a few initiatives have been conducted to improve off-the-person configurations and approach unconstrained settings in ECG biometrics. These efforts seek to close the gap to real, commercial applications by developing wearable technologies for ECG acquisition or embedding the sensors into common objects [ 7 , 11 , 13 , 18 , 28 ].
Table 3 presents a comparison of on-the-person and off-the-person acquisitions. Some researchers also compared different types of data acquisition and their influence on the performance of the biometric system. Jyotishi et al. [ 56 ] evaluated their model using three on-the-person ECG databases and two-off-the-person ECG databases. The results showed that the model performs well for both off-the-person and on-the-person ECG data. Srivastva et al. [ 2 ] used two databases, one on-the-person and the other off-the-person, and even mixed them together in a large database. The identification accuracies achieved for both the on-the-person and the off-the-person databases were individually about 99%, whereas an accuracy of approximately 98.5% was obtained for the mixed database. Thus, the authors proved the robustness of their ECG biometric method from signal acquisition methods. Biçakci et al. [ 7 ] used data from two different acquisition devices—the wearable-based chest bands and the medical-based Holter—to investigate whether the models are consistent and not biased by device specifications, providing reliable biometric verification with wearable devices. The results achieved for both datasets presented an equal error rate (EER) of around 5% for an enrollment time of 150 s, proving the reliability of using wearable devices for ECG acquisition for biometric purposes. It is also important to note that off-the-person methods have been gaining popularity in recent years for various applications beyond biometric recognition, such as disease detection. For example, in [ 57 ], the authors presented a method for recognizing diseases related to ECG and EEG data using sensors available in off-the-shelf mobile devices as well as sensors connected to a BITalino device. This suggests that these types of practical and convenient signal acquisition methods can be useful for a wide range of applications beyond biometric recognition.
Comparison of on-the-person and off-the-person acquisitions (adapted from [ 58 ]).
Number of Leads
A standard 12 lead ECG (or even 15-lead ECG) system can record more abnormalities than a single-lead ECG (similar to lead I in a 12 lead ECG). Figure 4 shows a representation of the standard 12-lead and the orthogonal-lead configurations. Due to the practical difficulty of collecting 12-lead ECG, biometric systems with a reduced number of leads have been evaluated.

Electrode placement and leads on the standard 12-lead configurations ( left ) and Frank leads ( right ), with the anterior electrodes depicted in red and the posterior electrodes depicted in a lighter red (adapted from [ 5 ], original figure kindly provided by the authors).
Dong et al. [ 44 ] proposed an identity recognition system and investigated their behavior on the different ECG leads. The experiments based on one-lead ECG showed that the best classification performance was obtained based on lead III and lead V1 and the worst classification performance was obtained based on lead V6. Moreover, experiments based on two-lead ECG outperformed experiments with one-lead ECG. Jekova et al. [ 59 ] used 12-lead resting ECG and evaluated the influence of the different leads on a biometric system. The capability of single limb leads was the lowest in III and aVR, and the highest in I and II. The identification capability of single chest leads was the lowest in V3 and the highest in V1. Multi-lead identification models yield considerably higher accuracy (about 20%) compared to the best single-leads. Porée et al. [ 47 ] proposed a method testing n = 1, 3, 6, and 12 leads, with all possible n-combinations of 12 leads tested. The best performances were obtained with 12 leads and then decreased with the decrease of the number of leads. With n = 3 and 6, the identification rate (IR) was still greater than 90%, whereas for n = 1, the IR was always lower than 90%. Fang et al. [ 60 ] tested their identification system with one- and three-lead ECGs, achieving optimal accuracies of 93% and 99%, respectively. Zhang et al. [ 9 ] suggested to place all the ECG electrodes on the left upper-arm or behind the ears in order to achieve excellent wearability. For the acquisition on the arm, the electrodes were integrated into an arm band, whereas for the acquisition behind the ears, electrodes were integrated into headsets or glasses. The signal strength of the single-arm ECG proved to be around 10% of the signal strength of the chest-ECG. However, arm-ECG heartbeats can still be distinguished. Moreover, the ear-ECG was found to be much weaker (5% of chest-ECG), but also shows a great potential for user identification purpose leveraging distinguishable morphologies. The mean accuracy obtained was as high as 98.8% and 91.1% for the single-arm and ear datasets, respectively.
Duration of Acquisition
Some researchers also assessed the impact of the duration of the ECG segment on the biometric identification’s performance. In the literature, it is predicted that the shorter the duration of the ECG segment used, the lower the performance obtained by the system. Ramos et al. [ 11 ] observed this behavior. However, when increasing the acquisition duration, this conclusion was not valid from a certain point onwards, as more data might introduce redundancy to the system. Results showed that around 10 s of signal are enough to test the identity of an individual. Biçakci et al. [ 7 ] evaluated the performance of their proposed method by varying the sample length. They used 5, 50, 150, 250, and 500 s of samples, achieving an EER of around 7% with only 5 s of enrollment. Ibtehaz et al. [ 61 ] studied the influence of the number of beats on the performance of the system, and results showed that increasing the number of beats significantly improved the performance. They achieved the perfect 100% accuracy using only three (ECG-ID [ 32 ], PTB [ 36 ] databases) and six (MIT-BIH Arrhythmia [ 34 ] and Normal Sinus Rhythm [ 35 ] databases) beats. Bernal-Romero et al. [ 62 ] tested their authentication method on different ECG signal duration: 10, 5, and 3 s. The EER rates for the authentication system with ECG signals had average values of 5.99%, 7.12%, and 9.66% for signal lengths of 10 s, 5 s, and 3 s, respectively. Pinto et al. [ 63 ] varied the number of enrollment templates between 5, 10, 15, and 30 s, achieving equal error rates of 13.70%, 10.92%, 9.52%, and 7.56%, respectively. Djelouat et al. [ 64 ] used testing times from 2 s to 5 s, and results showed an increasing identification rate from 84.44% to 98.88%. Carvalho et al. [ 23 ] aimed to measure the minimal number of heartbeats in which it was possible to identify subjects, even in situations where they were under the effect of fear or disgust, using from just one heartbeat up to twenty heartbeats. The results showed an optimal accuracy of around 75–80% when using 5–12 heartbeats.
3.1.2. Acquisition Protocol
Time stability.
The temporal separation between biometric evaluations may influence the system’s performance. Chee et al. [ 65 ] investigated the influence of different time separations between enrollment and testing data, using PTB [ 36 ] and ECG-ID [ 32 ] databases, with 83.9 days and 5.5 days between acquisitions, respectively. The model achieved accuracies of 64.16% and 92.70%, for long- and short-time separation, respectively, meaning that the model performance drops significantly when the time separation between the enrollment and classification increases. Ramos et al. [ 11 ] studied this influence by evaluating ECG segments from the same/different sessions. The results show that there is a decrease in performance when the sessions are different, except when the signal is collected on the fingers. Thus, the signal acquired on the fingers shows greater stability in the long term. Conversely, the point of acquisition that presents the greatest decrease in performance over time is the chest. Ibtehaz et al. [ 61 ] analyzed the cross-session accuracy using two databases, concluding that identification accuracy sharply falls when tested on data from a different session. Nevertheless, an accuracy above 90% was obtained for the ECG-ID database [ 32 ] and, for the CYBHi database [ 30 ], the accuracy dropped below 80%. Sun et al. [ 66 ] proposed a method for biometric identification, reaching a recognition accuracy of about 95%. However, they found that the accuracy degraded dramatically to 40% when considering a significant time interval between the acquisition of the training and testing templates. Porée et al. [ 47 ] proposed tests concerning the evaluation of the performances with time, concluding that there may exist a degradation of the ECG stability over time, with performances still acceptable after 16 months.
Number of Subjects
The impact of the database size on the accuracy of a biometric system is also a topic of research. Choi et al. [ 67 ] used 20, 40, 60, 80, and 100 subjects, reaching an accuracy of 100% for 20 subjects and an accuracy of 96% for 100 subjects, showing that the drop in accuracy when increasing the number of subjects is minimal. Jekova et al. [ 59 ] presented consistent validation of their identification models on an independent dataset by increasing its size from 10 to 230 subjects. Their validation results confirmed the expected trend for accuracy drop with the increase in the number of subjects. Chen et al. [ 53 ] evaluated their algorithm on 5, 10, 20, 30, 40, and 50 subjects. They noticed that the performance decreases slightly with the number of users increasing (false acceptance rate—FAR—increases from 0.00% to 8.00% and false reject rate—FRR—increases from 0.00% to 10.00% when increasing the number of subjects from 5 to 50). Carreiras et al. [ 17 ] tested the recognition system on an ECG signal database with 618 subjects. However, they also tested the system with subsets of this population, assessing the behavior of the recognition system with a varying number of subjects. For the entire database, results showed an EER of 9.01% and an Identification Error (IE) of 15.64%. The results of the population subsets highlight the fact that the EER does not seem to be affected by the population size, while, conversely, the IE increases with the number of subjects.
Physical Condition
Some researchers investigated the influence of exercise and body movement on the performance of a biometric system. Ramos et al. [ 11 ] studied the impact of the variability caused exclusively by moving the hands, feet, and chest. The results demonstrated that movement of the wrists causes the largest error in biometric identification, followed by movement of the fingers, while movement of the chest has almost no impact on the performance of the method. Huang et al. [ 68 ] showed that the ECG signal undergoes small noise interferences while the subject is walking and large noise when the subject is running or jumping. Nobunaga et al. [ 22 ] aimed to evaluate the effectiveness of their proposed identification method on exercising humans. They measured ECG during rest for one minute, with the subject lying down, and used these acquisitions to train the model. The exercise ECG used to test the model was measured for each subject after raising their foot so that their heart rate increased to over 100 bpm. The study reached an accuracy of 100% during rest and 99.8% during exercise, indicating that their method is accurate at identifying individuals doing exercise. Komeili et al. [ 54 ] also considered the case in which enrollment and testing are in different body conditions: rest and exercise. A feature selection was conducted to select features that are less affected by exercise; these were, then, used for enrolling and testing the biometric system’s users. Experimental results showed an EER of 11%. Moreover, Lee et al. [ 69 ] showed that the ECG cycle became shorter after 10 min of physical exercises, running, and holding breath for a certain period.
Most of the studies only consider supine rest conditions, which represent an important limitation regarding the use of ECG-based biometric systems in real-life contexts. Tirado-Martin et al. [ 21 ] acquired signals in different posture positions: sitting down at rest, standing at rest, and after exercise. They proved that different heart rates between the enrollment and recognition data result in lower performances. However, the best performance was achieved with the enrollment data acquired in a sitting position at rest. Iqbal et al. [ 70 ] achieved an accuracy of 100% when identifying 9 subjects at normal and resting conditions and an accuracy of 96.4% when identifying 39 subjects in 6 different physiological states (working, going up stairs, going down stairs, natural gait, lying with changed position and resting while watching TV). Wahabi et al. [ 71 ] considered an enrollment protocol in which each user’s ECG signal is collected under sit, stand, supine, and tripod postures. The accuracies achieved were 98.04% for sit, stand, and supine and 94.12% for tripod. Raj et al. [ 16 ] used ECG collected in three postures: a sitting posture at rest, a standing posture at rest, and a sitting posture after 20 s of exercise. They achieved an EER of 4.34% for the “standing” case, whereas the “sitting” and “after-exercise” cases worsened to 11.07% and 12.06%, respectively. Moreover, Wahabi et al. [ 72 ] also investigated the effect of body posture on ECG biometric accuracy, demonstrating that the performance of all the methods degraded when the train and testing data were not from the same body position. However, Porée et al. [ 47 ] showed that it is still possible to obtain good results even if the position in which the testing data was recorded is not present in the enrolment database.
An individual’s emotional state is continually changing. These changes occur naturally as a result of body chemistry, levels of stress, and even time of the day. The changes in emotional state are expressed in the ECG trace as changes in heart rate, noise in trace due to muscle flexor action, and variations in electrical potential gain. Thereby, some researchers have investigated the impact of emotions on the identification of individuals [ 73 ]. Zhou et al. [ 74 ] proposed a method of ECG biometrics using signals acquired under different stress levels, achieving an average recognition rate of 95%. Li et al. [ 18 ] used the public database DREAMER, in which the ECG signals acquired from wearable devices are disturbed by the physiological noises from emotional fluctuations induced by different stimuli. The accuracy obtained was of 91.30%, meaning that their method was capable of handling different kinds of emotional disturbances and identifying individuals accurately. Zheng et al. [ 75 ] investigated whether ECG based identification was affected by the status of ECG signal collecting, considering four status pairs: emotional status (calm, high pressure), eating (starve, satiation), sleeping (full, lack), and health (healthy, tired/cold). From the obtained results, the authors concluded that negative emotions (high pressure) and lack of sleep reduced the True Positive Rate (TPR) slightly (around 2–3%), but there was no effect on both eating and health pair status. When using ECG data mixed with all four statuses, the overall TPR of identification reached approximately 85%. Zheng et al. [ 76 ] self-collected calm and high-pressure ECG datasets to investigate the influence of different emotional statuses. They achieved accuracies of 98.10% and 95.67% for calm and high-pressure data, respectively, showing that the ECG signals under different emotion statuses can be used in reliable and accurate biometric systems. Israel et al. [ 73 ] used ECG data collected during seven different tasks performed to stimulate different states of anxiety. The low stress tasks were the subject’s baseline state, mediative, and recovery tasks. The high stress tasks were reading aloud, mathematical manipulation, and driving in virtual reality. Results showed that both within and between anxiety states, nearly all the individuals were correctly classified, as the accuracies obtained were around 97–98%.
Cardiac Conditions
The behavior of a biometric system under heart conditions has also been assessed. Chen et al. [ 77 ] focused on the comparative performance analysis of human identification with ECG signals collected from subjects in different health conditions. Data used consisted of ECG signals from 38 elderly subjects with a variety of chronic diseases and 30 young healthy students. Experimental results indicated that a better recognition accuracy is achieved for healthy subjects (98.14%) when compared to elderly unhealthy subjects (95.62%). Becerra et al. [ 78 ] used a database comprising 20 healthy subjects and 20 pathological subjects (diagnosed with different types of cardiac murmurs). The accuracies obtained were 91.19% and 97.74% for patients with cardiac murmurs and healthy patients, respectively. Singh et al. [ 79 ] used the QT database for patients with cardiac diseases and a second database for healthy patients. The proposed ECG biometric method achieved EER of 0.76% and 0.71% in recognizing people suffering from cardiac arrhythmia and people of good health, respectively. Regarding mixed health status, the method achieved an EER of 1.31%, confirming a very good performance and robustness of the proposal. Singh et al. [ 48 ] proposed a method to identify arrhythmic and normal subjects, reaching an accuracy of 87.37% for the subjects of MIT-BIH Arrhythmia database [ 34 ] and 92.88% for the IIT (BHU) database. Sidek et al. [ 80 ] also used three different databases containing various irregular heart states: MIT-BIH Arrhythmia database [ 34 ], MIT-BIH supraventricular arrhythmia, and Charles Sturt diabetes complication screening initiative, achieving accuracies of 96.7%, 96.4%, and 99.3% for each, respectively. Loong et al. [ 81 ] showed that diseased ECG only reduced the recognition rate by less than 1% and, thus, the system is robust towards diseased ECG. Contrarily, Chiu et al. [ 82 ] registered a drop of 19% between identifying normal subjects and subjects with arrhythmia (100% and 81%, respectively). Moreover, Ghazarian et al. [ 83 ] assessed the accuracy of ECG-based identification for distinct heart condition groups. They discovered that, in contrast to the initial expectation that identification accuracy for healthy normal sinus rhythm should be the highest, the identification accuracy is higher for patients with sinus tachycardia or patients who are diagnosed with both ST changes and supraventricular tachycardia. Conversely, they observed that patients with premature ventricular contractions have an identification accuracy as low as 78.54% and patients with a pacemaker presented an accuracy of 80.2%.
The conditions under which ECG data are acquired can have a major impact not only on the performance of a biometric system but also on the ability to accurately and reliably detect heart conditions. As such, several studies have been investigating the influence of several factors, such as electrode placement, lead configuration, physical exercise, and the intrusiveness of acquisition, on the detection of heart diseases [ 84 , 85 , 86 ].
3.2. Acquisition Devices
3.2.1. commercially available devices.
During the last years, the market of medical-grade wearable ECG devices has expanded, and these have increasingly been used for biometric purposes since they can be easily integrated in biometric systems, reducing costs, power consumption, and time of acquisition. However, researchers still use non-wearable devices for data acquisition since they allow records with higher quality. In this section, some of the most used commercially available acquisition devices are presented, as well as some self-developed sensors for ECG acquisitions. Figure 5 shows the commercially available devices described in this section.

Commercially available devices.
The VitalJacket [ 87 ], presented in Figure 5 a, is a wearable device developed by researchers from the IEETA research unit at the University of Aveiro and commercialized by Biodevices SA [ 88 ]. It is designed to continuously record high-quality ECG and other vital signals in various clinical and everyday settings. The collected data can be stored on an SD card for offline analysis or transmitted via Bluetooth to mobile devices for real-time monitoring and online processing. Ye et al. [ 13 ] investigated the applicability of ECG signals from such wearable device in human identification. In the five-subject study, their proposed method exhibited near 100% recognition rates based on single heartbeats, even with a six-month interval between the training and testing data. Ramos et al. [ 11 ] used VitalJacket to collect ECG signals from twenty healthy participants in two sessions separated by 2 weeks. They investigated the impact of movement, the influence of using different ECG acquisition placement, the impact of temporal separation between sessions, and the impact of the acquisition time. The authors reached an accuracy of 99% for signals collected on the fingers in two different sessions. For the various experiments, the results suggested that the ECG signals acquired using VitalJacket can be used as robust biometrics.
The RespiBAN Professional, which is presented in Figure 5 b, is a wearable system made by PLUX, which includes a PLUX accelerometer biosensor and biosignal acquisition hardware, as well as a respiration biometric sensor embedded in the chest strap fabric. This device can measure various biosignals, including ECG, electrodermal activity (EDA), electromyogram (EMG), and skin temperature. The collected data can be transmitted to mobile devices via Bluetooth. Biçakci et al. [ 7 ] used the WESAD dataset, which consists of ECG recordings collected from a RespiBAN device. The EER obtained was 7.07%, meaning that ECG biometrics will be a valid verification option (or could be in the future) using wearable devices for data acquisition.
The Nymi Band [ 89 ], shown in Figure 5 c, is a wearable device that uses the wearer’s unique cardiac signal to unlock Bluetooth-enabled devices such as computers, smartphones, and cards. To authenticate the user, the Nymi Band is placed on the wrists and the top of the device is touched with a finger. As long as the device is worn, the user remains authenticated. The Nymi Band is equipped with a heart rate monitor, accelerometer, gyroscope, and biometric authenticator, and is powered by a rechargeable battery. Chun et al. [ 14 ] used ECG data from 15 subjects collected using the Nymi Band, achieving an EER of 0.9%, which proves the reliability of this wearable device.
ReadMyHeart [ 90 ], shown in Figure 5 d, is a handheld, non-invasive heart monitoring device made by DailyCare BioMedical Inc. It allows users to record electrical signals from their hearts by placing their thumbs on the device’s conducting plates, without the need for wires or conducting gel. The device takes 30 s to record each measurement and displays the average heart rate, ST segment, and QRS interval. These readings are based on a “modified Lead I-ECG”, rather than traditional standard ECG readings. Islam et al. [ 15 ] captured ECG signals from 112 individuals using the handheld ECG device ReadMyHeart, achieving a minimum EER of 10.52%.
The Vernier ECG Sensor [ 91 ], presented in Figure 5 e, is a device used to measure the electrical potential waveforms produced during the contraction of the heart. It can be used to record standard three-lead ECG tracings or surface EMG recordings of muscle contractions in various parts of the body. The device is usually associated with the Vernier Go!Link interface, which is a low-cost USB sensor interface that connects Vernier sensors to a computer. Raj et al. [ 16 ] used the Vernier sensor for ECG acquisitions on the arm with different body postures, achieving an Optimal performance with an EER of 4.34%.
The PageWriter Trim III [ 92 ] is a compact and cost-effective cardiograph made by Philips, shown in Figure 5 f. It is an interpretative ECG system designed for fast-paced clinical environments, with features such as a high-resolution full-color display and the ability to report, store, and transmit 12-lead ECG data using industry-standard XML. Carreiras et al. [ 17 ] used Philips PageWriter Trim III for ECG acquisitions of 618 subjects, achieving an EER and an IE of 9.01% and 15.64%, respectively.
The Shimmer ECG unit [ 93 ] is a device designed for the measurement of physiological signals for ECG, and it is presented in Figure 5 g. It includes a configurable digital front-end and an ECG sensor that can record the pathway of electrical impulses through the heart muscle. The sensor can be used to record ECG data on resting and ambulatory subjects, or during exercise to provide information on the heart’s response to physical exertion. Li et al. [ 18 ] used a public database, DREAMER, in which data were acquired using the Shimmer ECG Sensor, and an accuracy of 97.2% was obtained.
The BioPLUX [ 94 ] low-noise ECG local differential triode configuration enables fast application and unobtrusive single-lead ECG data acquisition. This sensor can be used to extract heart rate data and other ECG features, enabling its application in research fields such as biomedical, biofeedback, psychophysiology, and sports, among many others. Silva et al. [ 19 ] used the BioPlux Electrocardiography Sensor presented in Figure 5 h integrated on a steering wheel for in-vehicle driver recognition, achieving an IE of 2.40%.
Maxim 86150 Evaluation Kit [ 95 ], presented in Figure 5 i, is a device designed to evaluate the photoplethysmogram (PPG) and ECG bio-sensor module. The device includes a Microcontroller Board and a Sensor Board. The Microcontroller Board houses a microcontroller unit (MCU) with preloaded firmware, Bluetooth connectivity, and power management. The Sensor Board includes the MAX86150 Bio-Sensor Module and two stainless steel dry electrodes for ECG measurement. The Evaluation Kit is powered by an included lithium polymer battery, which is charged with a micro-USB cable. When monitoring is active, the module uses IR Proximity Mode to detect each user’s fingers, and a red LED will turn on when a finger is near the module. Sorvillo et al. [ 20 ] used the Maxim 86150 Evaluation Kit to collect ECG for human identification under rest and mental and physical stress, reaching accuracies of 88% and 68%, respectively.
The BioRadio [ 96 ] is a wireless biomedical monitor, shown in Figure 5 j, with programmable channels for recording and transmitting various combinations of human physiological signals. It is easy to set up and operate, and the wearable device captures data in a flexible file format compatible with a variety of software suites and proprietary tools. Huang et al. [ 68 ] used the BioRadio device with the positions of the electrodes following the Einthoven’s configuration. Abdelazez et al. [ 97 ] also used this device, but the electrodes were positioned under the right and left thumbs instead. Their system achieved a precision of 0.68, being able to identify 98.7% of the false positives while retaining the true positives rate.
The BIOPAC MP160 [ 98 ] is a 16-channel system designed for the acquisition of various physiological signals, including Heart Rate Variability (HRV), Electroencephalogram (EEG), EMG, EGG, and many more. The device, represented in Figure 5 k, offers multiple configurations to suit different research and teaching needs, and records multiple channels with different sample rates up to 400 kHz. Used in conjunction with AcqKnowledge software and BIOPAC electrodes, amplifiers, transducers, and other system components, the MP160 is part of a complete data acquisition and analysis system. Many researchers used the BIOPAC system for data acquisition of their proposed biometric system [ 21 , 22 , 23 ].
Kardia [ 99 ] is a wireless device that allows users to record a medical-grade single-lead ECG in 30 s and receive instant analysis on their phones. It is clinically validated, CE marked, and FDA-cleared, making it a reliable option for checking one’s heart from home. Kardia, in Figure 5 l, is compatible with most popular phones and tablets and, to use it, one only needs to download the Kardia app. Arteaga-Falconi et al. [ 24 ] used the Kardia device along with a mobile phone for ECG acquisitions at different times and conditions, proving the reliability of this mobile device, since the results revealed 1.41% of FAR and 81.82% of true acceptance rate.
3.2.2. Self-Developed Acquisition Devices
As mentioned above, there are also some researchers who developed their own ECG sensors.
Rashkovska et al. [ 25 ] developed a wireless ECG sensor for long-term monitoring and tested it in various applications, including biometric authentication. The initial prototype of the wireless body sensor (WBS) was powered by a coin-sized battery and included a low power microcontroller and a 2.4 GHz radio transceiver. The design was later improved to include a rechargeable battery and a Bluetooth Low Power (BLE) radio transceiver for communication. The WBS is attached to the skin by using self-adhesive electrodes and has evolved into a more flexible and lightweight design that allows for unobtrusive long-term health monitoring and low-cost implementation. It is now commercially available as the SavvyTM sensor. The proposed methodology for biometric authentication using this device achieved an EER from 6% to 13%, depending on the subject.
Blasco et al. [ 26 ] developed a wearable sensor capable of measuring photoplethysmography (PPG), ECG, Galvanic Skin Response (GSR), and Acceleration (ACC) signals from the wrists. The ECG sensor is from Bitalino [ 100 ] and the two electrodes were placed on the inner side of the wristband and on top of the wristband, respectively. The viability of the use of the sensor on a biometric system was tested in three different acquisition conditions: sitting, walking, and sitting after exercise, and the results were promising.
Guven et al. [ 3 ] also developed a fingertip ECG data acquisition device for biometric purposes. The device consists of two dry-contact sensors, produced by Plessey Semiconductors, an instrumentation amplifier, an anti-aliasing filter, an optocoupler, a digital signals controller (DSC), and a USB connection unit. The authors conducted an experiment to evaluate the performance of the proposed device by comparing it to the use of lead-I ECG signal, recorded using Biopac MP36 with three conventional Ag/AgCl electrodes and gel. The results achieved were around 100% for the IE, showing that this portable, inexpensive, and user-friendly device is very promising for biometric applications.
Wieclaw et al. [ 10 ] developed a sensor using an Arduino Uno and e-Health Sensor Platform V2.0 for data acquisition. Arduino Uno is a microcontroller board with 16 MHz quartz crystal and a USB port for programming, debugging, and data transfer. The e-Health Sensor Platform V2.0 extends the Arduino Uno and enables the implementation of biometric and medical applications. Data acquisition was performed using differential OpAmp schema followed by 8-bit ADC operating at 277 Hz sampling rate. ADC data were transferred to a PC via the COM-port using the PySerial Library. Modified schema required the user to touch the electrodes with two fingers from the left hand and one finger from the right.
Peter et al. [ 27 ] used a low-cost sensor and designed a sensor processing board. They used conventional wet cloth electrodes with repositionable conductive adhesive hydrogel to measure the electrical activity from the skin surface. Then, a sensor board that amplifies and filters the signals was designed. They applied a standard difference amplifier approach, which is a suitable solution since the basic ECG data is obtained as an output of the difference of two leads placed on the body. The circuit build consists of three parts: the differential amplifier, a filter, and a post amplifier. Afterwards, the signal follows to an embedded target platform, called Raspberry Pi (RPi), which is a low-power single-board computer. One advantage of the RPi is that it is supported by MATLAB Simulink and a range of design tools, which facilitates easy and fast prototyping.
Ramli et al. [ 28 ] developed a portable ECG detection kit integrated into a wearable bracelet that is responsible for detecting the heartbeat signal of the user and sending out the ECG signals to be processed via Bluetooth. The sensor is equipped with three electrodes and by placing a finger on the topside electrode while the user’s wrists are in contact with the other two electrodes, an electrical circuit is completed; ECG signals are able to be detected by the device. The heartbeat detection kit is formed by six main parts: instrumentation amplifier (IA), high-pass filter (HPF), 60 Hz notch filter, low-pass filter (LPF), analog-to-digital converter (ADC), and signal transmitter. They also developed an Android platform application that acts as a secure login system. This application receives the serial data from the heartbeat detection kit through a Bluetooth connection. Then, when the sign-in or sign-up function of the application is triggered, the incoming data is saved to the database. The database will trigger the back-end system which is the Intel platform board to perform the embedding, features extraction, and pattern-matching processes. Once the processes are done, the verification result will be sent to the android application GUI.
Lourenço et al. [ 29 ] proposed a method and device for ECG acquisition, using a single lead setup at the fingers, with Ag/AgCl electrodes without gel. This setup aims to increase the usability and acceptability of ECG-based biometric systems to the level of other biometric traits in terms of signal acquisition. The rigid base integrates three leads which, due to the underlying sensor design, correspond to the ground, positive, and negative poles. The right-hand thumb is used as a negative electrode and the left-hand index finger acts simultaneously as the positive and ground electrodes. The base sensor is an ecgPLUX active ECG triode and the transmission was done via a Bluetooth wireless bioPLUX research biosignal acquisition unit.
Table 1 show an overview of the commercially available and self-developed sensors described in Section 3.2.1 and Section 3.2.2 .
3.3. Databases
Currently, there are several collections publicly available for ECG biometrics research. Below, the most relevant of the currently available ECG collection are characterized. Table 2 summarizes the characteristics of each. Some are publicly available and can be found on physionet [ 101 ].
3.3.1. On-the-Person
The MIT-BIH Arrhythmia database [ 34 ] is a widely used resource for ECG-based biometrics research and is available at the Physionet repository. It consists of 48 half-hour ECG recordings from 47 subjects that were collected in the laboratories at Boston’s Beth Israel Hospital. Out of 27 subjects, 23 recordings were selected from a mixed population of inpatients (about 60%) and outpatients (about 40%), and the remaining 25 recordings were selected from the same set to include less common but clinically significant arrhythmias. The recordings were digitized at 360 samples per second per channel with an 11-bit resolution over a 10 mV range [ 49 ].
This database is composed of excerpts from 18 subjects from the MIT-BIH Arrhythmia database presented above, which are deemed to be free from arrhythmias or other diseases. Subjects included in this database were found to have had no significant arrhythmias, and they include 5 men, aged 26 to 45 and 13 women, aged 20 to 50 [ 35 ].
This database contains 25 long-term ECG recordings of human subjects with atrial fibrillation (mostly paroxysmal). The individual recordings are each 10 h in duration and include two ECG signals. The original analog recordings were made at Boston’s Beth Israel Hospital using ambulatory ECG recorders with a typical recording bandwidth of approximately 0.1 Hz to 40 Hz [ 40 ].
This database is obtained by the Physikalisch-Technische Bundesanstalt (PTB), National Metrology Institute of Germany [ 36 ]. The database contains 549 records with diverse profile information and various lengths of ECG from 290 subjects. Of the 290 subjects, 148 had suffered from myocardial infarction, 18 had cardiomyopathy or heart failure, and 52 were healthy subjects. Acquisitions were performed both through the standard 12-leads and the three Frank leads [ 49 ].
The ECG identification database was recorded for biometric identification purposes [ 32 ]. Each raw ECG record was acquired for about 20 s with a sampling rate of 500 Hz and a 12-bit resolution. The first two records acquired on the same day were used for each subject. The database consists of 310 one-lead ECG recording sessions obtained from 90 volunteers during a resting state. The number of sessions for each volunteer varied from 2 to 20, with a time span of 1 day to 6 months between the initial and last recordings [ 49 ].
This is an ECG database from the University of Rochester that is focused on biometrics. The study population consists of 202 healthy subjects from the Intercity Digital Electrocardiogram Alliance (IDEAL) database. The database includes 24 Holter recordings that were acquired using the SpaceLab-Burdick digital Holter recorder. The equipment provides 200 Hz sampling frequency signals with 16-bit amplitude resolution. The ECG was acquired using a pseudo-orthogonal lead configuration (X, Y, and Z), obtained through four electrodes placed on the chest. There is an initial resting supine period with a duration of 20 min before starting the ambulatory recording [ 33 ].
The QT database is a collection of ECGs that have been selected to showcase a wide range of QRS and ST-T shapes, with the goal of testing QT detection algorithms with real-world variability. These records were largely drawn from various ECG databases, including the MIT-BIH Arrhythmia Database [ 34 ], as well as additional recordings gathered at Boston’s Beth Israel Deaconess Medical Center. The additional recordings were chosen to represent extreme examples of cardiac (patho)physiology, including data from Holter recordings of patients who experienced sudden cardiac death during the recordings, as well as age- and gender-matched patients without diagnosed cardiac disease. The QT database includes a total of 105 fifteen-minute excerpts of two-channel ECGs [ 37 ].
This database contains data collected from a real-world driving task designed to measure a driver’s stress level. The driving protocol involved following a predetermined route for 20 min on open roads in the Boston area while following a set of instructions. Four types of physiological sensors were used during the experiment: ECG, electromyogram (EMG), skin conductivity (EDA and GSR), and respiration. These sensors were connected to a FlexComp analog-to-digital converter, which isolated the subject from the power supply. The ECG electrodes were positioned in a modified lead II configuration to minimize motion artifacts and maximize the amplitude of the R-waves, and the ECG was sampled at 496 Hz. In total, 27 collections were recorded, 6 from drivers who completed the course only once, and 7 from 3 drivers who repeated the course on multiple days [ 31 ].
The Fantasia Database is a collection of 120 min of continuous ECG recordings taken while subjects were lying down. Two groups of healthy human subjects, ten young and ten elderly participated in this acquisition. Only healthy, nonsmoking subjects with normal exercise tolerance tests, no medical problems, and taking no medication, were admitted to the study. The subjects laids supine for 120 min while continuous ECG signals were collected. All subjects remained in a relaxed state with a normal sinus rhythm while watching the movie “Fantasia” from Disney to help maintain wakefulness [ 39 ].
3.3.2. Off-the-Person
In this work, Silva et al. [ 30 ] presented the CYBHI database which consists of 128 ECG recordings acquired using the off-the-person approach. The ECG signals (2 min long) were recorded simultaneously from both wrists and fingers using dry Ag/AgCl electrodes and electrolycra strips, respectively. These sensors were placed on custom hand-shaped support, and data synchronization was ensured using the syncPLUX synchronization kit. The electrodermal activity data was also collected to provide information about the arousal state of the subject, as the acquisition protocol included both neutral and emotional elicitation tasks. The acquisition protocol consisted of short-term and long-term sessions. Short-term sessions were conducted over 2 days with 65 participants. The participants completed an experimental procedure that was 5 min long, during which they watched a low-arousal video and a high-arousal video (a horror movie trailer). Long-term sessions consisted of 2 data acquisition moments separated by a 3-month period with 63 participants. In both phases, only ECG signals from the fingers were recorded, and in each of the sessions, the subjects were seated for 2 min in a resting position with two fingers on the dry Ag/AgCl electrodes [ 52 ].
Pouryayevali et al. [ 38 ] collected a large database with 1012 ECG recordings from different people. The acquisition hardware consisted of a pad with dry Ag/AgCl electrodes, positioned so that the left thumb was placed on the positive electrode, whereas the right thumb and right forefinger were placed on the negative and reference electrodes, respectively. According to the acquisition protocol, the ECG recordings were performed in the following conditions: supine, tripod, sit, physical exercise, and stand. The ECG signals were recorded for all the subjects while sitting, but they were collected in supine, tripod, physical exercise, and standing conditions only for 63, 63, 71, and 81 participants, respectively. Regarding the time interval, 72, 65, 54, 47, and 43 out of 1012 subjects participated in 2, 3, 4, 5, and 6 acquisition sessions, respectively. The length of each recording ranged from 2 min to 5 min [ 52 ].
This database contains two-lead ECG recordings taken during affect elicitation using audio-visual stimuli. The data was collected using eight film clips containing scenes from different films that were designed to elicit a range of emotions. Of these eighteen film clips, two were intended to evoke the following nine emotions: amusement, excitement, happiness, calmness, anger, disgust, fear, sadness, and surprise. The film clips were between 65 and 393 s long. ECG was recorded using a SHIMMER wireless sensor. A total of 25 healthy volunteers aged between 22 and 33 years old participated in the study [ 41 ].
This dataset consists of ECG recordings, along with several other physiological signals, collected from 15 subjects using a RespiBan device. The device was placed around the subject’s chest and recorded ECG using a standard three-lead configuration. After the subjects were equipped with the sensors, a 20-min baseline was recorded (baseline condition), while sitting/standing at a table. Neutral reading material (magazines) was provided. During the amusement condition, the subjects watched a set of eleven funny video clips. The following phase was a stress condition, in which the subjects were exposed to the Trier Social Stress Test (TSST), which consists of a public speaking and mental arithmetic task. The subjects had to deliver a five-minute speech on their personal traits in front of a panel of three people, focusing on strengths and weaknesses. After the speech, the panel asked to subjects to count down from 2023 to 0, in steps of 17, and asked to start over if they made a mistake. Both tasks lasted about 5 min, resulting in a total of ten minutes for the stress condition. The amusement and stress conditions were followed by a meditation, in which subjects followed instructions with their eyes closed while sitting in a comfortable position for seven minutes [ 42 ].
4. Discussion
Based on the data reported so far, the following issues are discussed: (i) the comparison of the acquisition hardware, (ii) the comparison of the acquisition protocol, (iii) inter-subject variability, and (iv) intra-subjects variability.
4.1. Acquisition Hardware
4.1.1. acquisition devices.
Most databases were collected from medical devices that often have more leads, which makes them more informative. However, the large number of electrodes required, their uncomfortable placement, the limited movement allowed, and the duration of recordings, make it difficult to develop robust biometric systems. Some researchers have attempted to address these issues by using acquisition methods that allow more movement and longer durations using fewer electrodes. One of the most prominent examples was the use of Holter systems, which are designed to continuously acquire ECG signals for several hours while the subjects move and perform daily activities. The Holter monitors are smaller devices compared to standard 12-lead ECG devices, but they still use many wires to connect the electrodes to the recording machine. While these monitors have become more advanced and capable of recording high-quality single or multi-lead ECG, they can still be uncomfortable for patients to wear and can affect the ECG signal’s strength as a biometric trait [ 25 , 102 ].
Despite the potential of off-the-person systems in a practical setting, there are still some challenges that need to be overcome. Off-the-person systems still require the user to hold the electrode or deliberately place the fingers or palms over them. This prevents us to designate them as unconstrained systems, which puts the ECG at a disadvantage over other biometric traits that can already be used for unconstrained recognition. In addition, the use of dry electrodes in farther placement makes the acquisition more vulnerable to interferences, thus affecting the quality of the signal. The efforts on wearable devices have brought ECG biometrics closer to viable, unconstrained applications.
However, the adoption of wearables for biometrics also introduces new challenges [ 26 ]. First, wearable devices tend to use cheaper sensors and hardware than traditional biometric systems. Consequently, sensor readings have more noise, and combined with natural variability in the subject’s state, accuracy is more of an issue. Furthermore, wearable devices have limited computational capabilities and must optimize the usage of their resources to maximize battery life, while providing a quick response to biometric challenges. Hence, these issues must be addressed and adequately solved in order to obtain viable commercial ECG biometric systems [ 3 ].
4.1.2. Number of Leads
It is known that each ECG lead contains discriminative information regarding the electrical activity of the heart. However, the use of 12-lead ECG is a very unpractical solution for biometric purposes, as it requires the placement of many electrodes. Hence, biometric systems have been evaluated with a reduced number of leads, since it represents interest from a technological point of view. Some researchers, such as Porée et al. [ 47 ], tested the use of different combinations of leads (n = 1, 3, 6, and 12 leads) to evaluate the behavior of the system. As expected, they achieved optimal performances with 12 leads and then the performance decreased with the number of leads. However, with only one lead, the performance was still close to 90%. Concerning the use of single-lead ECG, researchers like Jekova et al. [ 59 ] used all 12 leads individually as single-lead configurations in order to assess the influence of each lead. They stated that the capability of single limb leads is highest in lead I (and lead II), which justifies the use of lead I in almost all studies in the literature. Moreover, Zhang et al. [ 9 ] tried to reach high wearability by placing the electrodes on the upper arm or behind the ears, using an armband and headsets, respectively, proving that, although the strength of the ECG is much lower than the chest-ECG, it still has a great potential for user identification purposes. Thus, more efforts should continue to be made to improve performance while using a single-lead ECG, gathered with minimal intrusiveness, as it is a much more user-friendly approach.
4.1.3. Duration of Acquisition
Short-term ECG data (less than several minutes) and long-term ECG data can complement each other. Short-term ECG data is cheaper and easier to collect. Many cardiac diseases can be detected based on short-term ECG, so such data represent the primary diagnostic tool in outpatient departments. However, long-term ECG can help to detect diseases with intermittent symptoms such as paroxysmal ventricular fibrillation (VF) and atrial fibrillation (AF) [ 103 ]. Data acquisition should be a relatively fast process for biometric scenarios. Nevertheless, it is predicted that the shorter the duration of the ECG segment used, the lower the performance obtained by the recognition system. Thereby, many studies assessed the impact of the duration of the ECG segment on the performance of the biometric system, as mentioned above. In general, this behavior was observed in most studies. However, Ramos et al. [ 11 ] showed that this pattern may not always be valid from a certain point onwards, as more data can introduce redundancy to the system. While optimal performances were achieved with ECG segments of 10 s in [ 11 ] and [ 62 ], Djelouat et al. [ 64 ] reached an accuracy of 96.66% with only 5 s of acquisition. Thus, it can be suggested that the optimal duration of acquisition may depend on the conditions of acquisition. Taking into account that the duration of the acquisition for a biometric system should be short, the optimally short acquisition time that does not compromise the performance of the system should be investigated.
4.1.4. Sampling Frequency of Acquisition
In general, to ensure that ECG signals are recorded with sufficient detail and resolution, a sampling frequency of at least 500 Hz is commonly used, since it will allow capturing fast changes in ECG signals [ 104 ]. When the sampling rate is lower, more information can be lost in the recording and there is a greater change of high-frequency noise being misinterpreted [ 5 ]. According to [ 105 ], due to the lack of points available in ECG signals, signals with low sampling frequency are usually inefficient for ECG matching purposes when methods such as cross-correlation, percentage root-mean-square deviation, and wavelet distance measurement are used. As such, the low sampling frequencies used in old commercial systems (e.g., 128 Hz) usually need a reinterpolation of data [ 106 ]. There are already some studies that developed enhancement techniques to increase the number of samples of a given ECG data from low sampling frequency recordings [ 107 ]. Nevertheless, the frequency at which the ECG should be recorded depends on the specific application and the equipment used for recording [ 104 ].
In the past, waves with smaller amplitudes were usually ignored since these were almost always caused by noise. However, with the advent of high-resolution ECG technology, it became possible to detect signals as small as 1 μ V through the use of signal averaging techniques. This advancement has provided new insights and has shown that techniques to reduce noise are effective in clinical settings. In [ 106 ], the authors investigated the effects of the amplitude resolution of ECG acquisition systems on the P-wave analysis. Results proved that at lower bit resolutions, the percentage error is higher than 40%, meaning that almost half of the results are different from the ones obtained with the highest resolution. They concluded that the high resolution used in modern electrocardiographs was suitable for ECG analysis.
There is no standard regarding data acquisition hardware information. Different studies have used various sources, number of leads, and durations of acquisition, making it difficult to compare results between different datasets. However, by analyzing the literature, it can be concluded that the preferable solutions for the acquisition hardware of a biometric system are the following: (1) an off-the-person approach, which is more realistic to a biometric scenario and easily integrated into a biometric system; (2) a one-lead setup, as it is the most practical solution due to the reduction of the number of contact points, making the data acquisition of benefit to user acceptance; (3) a short-term ECG data, since such data would be faster to acquire and to process, resulting in a user-friendly biometric system.

4.2. Acquisition Protocol
4.2.1. number of subjects.
There is an expected trend for a performance drop with an increase in the number of subjects; several studies have confirmed this expectation by testing the system with a different number of subjects and registering a decrease in performance when increasing the number of subjects [ 53 , 59 ]. However, a biometric system should be able to accurately identify and authenticate many subjects. Although the vast majority of studies have tested their models with small databases, Carreiras et al. [ 52 ], for example, used a database with 618 subjects, achieving promising results both on authentication and identification (EER of 9.01% and EI of 15.4%). Thus, larger databases, as well as subsets of those databases, should be used in biometric systems to assess their behavior according to the number of subjects considered.
4.2.2. Time Stability
Multi-session ECG authentication, with enrollment and authentication signals captured across two or more different sessions, has become a more relevant problem of late, primarily because of its similarity to real-world use cases. Error rates calculated using multi-session datasets have been reported to be significantly worse than those using single sessions. Two acquisition sessions in a dataset may differ in several different ways, e.g., signals may be captured under different postures or heart-rate, different hydration levels, or may be captured on different days [ 108 ]. Performance degradation might arise from the morphological changes in the heartbeats from one session to another due to variations in physical or physiological states of these subjects [ 45 ]. Ramos et al. [ 11 ] found a decrease in the performance over time, except when the signal is collected on the fingers, with the chest-ECG being the one that obtained the greatest decrease in performance over time. Thus, off-the-person approaches, which are the most user-friendly, may not suffer significant degradation over time.
4.3. Sources of Variability
The ECG signals could be affected by three major sources of variability, namely inter-subject and intra-subject variability and artefact and noise, which will be individually described.
4.3.1. Inter-Subject Variability
Inter-subject variability is the variability between ECGs from different individuals. The ECG signal uniqueness can be assumed to be acquired mainly from the uniqueness of DNA, besides other physical factors such as age, ethnicity, and gender, which contribute to the different ECG variations. Since the ECG signal is universal, stable, and unique, the inter-subject variability can be affected by the orientation of heart mass and the conductivity of cardiac muscle. Despite this inter-subject variability, the ECG signal should remain sufficiently stable over time to enable ECG-based biometric authentication. The main reasons for inter-subject variability of ECG morphology are the heart geometry and the individual attributes.
- Heart Geometry: Heart size, cardiac muscle thickness, and the overall shape of the heart dictate the paths the electrical current follows inside the heart, the number of muscle cells that depolarize, and the time it takes to depolarize the whole heart. Athletes, due to their high levels of physical training, commonly have larger hearts with thicker myocardia, which affects the ECG with higher voltages in the QRS complex and results in lower basal heart rates [ 109 , 110 ].
- Individual Attributes: Age, weight, and pregnancy are some of the individual attributes that can cause shifts in the heart position and/or orientation. These shifts will change the orientation of the electrical current conduction vectors along the heart, meaning the electrodes will detect the signal from a different perspective, thus altering the ECG waveform. For instance, the QRS complex amplitude tends to increase from birth to adolescence and then gradually begins to decrease afterward [ 8 ]. The authors in [ 111 ] also find that the PR interval increases slightly with increasing age. Studies have shown that the amplitude of the S wave in ECG signals is lower in women than in men between the age interval of 18–40 [ 112 ]. While gender differences in ECG signal parameters are more evident in young adulthood, they are known to decrease their effect afterward.
4.3.2. Intra-Subject Variability
The intra-subject variability refers to the differences in ECG signals from the same individual or within a single ECG signal. It is important for a biometric modality to have low intra-subject variability, as well as high inter-subject variability and stability over time. There are several sources of intra-individual variability such as chest electrode position and respiration. While the former induces variation between ECGs of the same individual, the latter induces variability within a particular ECG. Moreover, besides these two factors, intra-subject variability may also be induced by many other factors [ 8 ]:
- Physical Exercise: The duration of and the intervals between the different deflections of the heartbeats in an ECG signal vary with the heart rate. These changes are especially visible in the interval between the QRS complex and the T wave in situations of tachycardia (higher heart rates) or brachycardia (lower heart rates). Changes in the heart rate caused by physical exercise or meditation can, effectively, affect the electrocardiogram. While Lee at al. [ 69 ] showed that the ECG cycle became shorter after 10 min of physical exercise, running, and holding the breath for a certain period on different dates, Komeili et al. [ 54 ] also demonstrated that if, during feature selection, one investigates the features that are less affected by physical exercise, one can still achieve great biometric performance while exercising. Lee et al. [ 69 ] also investigated the ECG patterns of smokers, finding that there was also a minimal change in the ECG signal before and after smoking.
- Cardiac Conditions: Medical conditions of the heart can also interfere with the dynamics of the electrical pulse conduction and generate variability. In the scope of biometrics, many databases consisting of ECG signals from patients with cardiac conditions have been used. One of the most studied conditions is arrhythmia, which causes wide variations in the heart rate across time. Chiu et al. [ 82 ] mentioned that the low accuracies can be justified by unstable QRS-complexes, causing extracted features to change. However, Becerra et al. [ 78 ] stated that even though cardiac conditions affect the performance of the system, accuracies can be higher for some classifiers. Moreover, Ghazarian et al. [ 83 ] achieved different accuracies for different heart conditions, meaning that feature selection and classification optimization should be performed considering different cardiac conditions.
- Posture: Postures like standing or lying down differ widely on the position and shape of internal organs. The heart is also affected by this, and changes its position in the thorax, and thus its position in reference with the electrode placement, which causes variations in the collected ECG signal. The vast majority of the ECG acquisitions are performed with the subject lying down at rest. However, Porée et al. [ 47 ] stated that there is no requirement or advantage to compare only ECG shapes in supine resting conditions. Moreover, Raj et al. [ 16 ] presented more accurate performances while standing (which is a more realistic biometric scenario) than while sitting. Furthermore, Wahabi et al. [ 72 ] proved that the performance degrades if the training and testing signals are not from the same position, meaning that the enrollment task should be performed in different positions.
- Emotions: The sympathetic and parasympathetic systems of the autonomous nervous system work to increase or reduce the heart rate, respectively. These systems are under the direct influence of psychological states and thus, under stress, fear, and other strong emotions, fatigue, or drowsiness, the heart rate and the ECG signal can be affected. Even though some researchers still achieved good performances with different levels of stress and anxiety (91% and 97% for [ 18 , 73 ], respectively), some others proved a slightly negative impact of emotions on the performance of a biometric system. As mentioned above, Zhang et al. [ 75 ] found a reduction of the true positive rate with ECG signals acquired during high pressure and lack of sleeping situations, whereas the eating and health status did not affect the system. Thus, since there is still no consensus on whether emotions (stress, anxiety, levels of sleeping, levels of thirst and eating, etc.) negatively impact the performance of a biometric system or not, researchers should further investigate these conditions within their systems. However, we must note that it is difficult to design an experimental setup that can induce the same emotion in every subject, as different characters, varying moods, and the inability to accurately self-report an emotional experience may significantly affect the outcome of such a study.
4.3.3. Artefacts and Noise
- Electrode Material: The most used electrodes are silver/silver–chloride coated electrodes with well known frequency-band characteristics and temperature stability. However, different materials can have different characteristics affecting the recording: temperature drift can cause variation of the baseline (low frequency oscillations) while frequency-band modifications can cause attenuation of high frequencies [ 52 ].
- hlSensor Location: In the biometric scenario, it is common to use single ECG recording with only two electrodes placed in non-standard locations which can lead to different morphology of the ECG recording with respect to the standard recordings [ 73 ].
- Power-line Interference: Capacitive coupling with power lines can induce a superimposed (distorted) harmonic signal whose amplitude can obscure the morphological characteristics of ECG: notch filtering is usually used to remove this interference [ 52 ].
- Baseline Drift: Respiration causes changes in thorax volume/electrical impedance, therefore causing the isoelectric level to change slowly (in low frequencies ranges): this artefact is usually removed via low pass filtering [ 52 ].
- Movement Artefacts: The contact interface between skin/electrode is subjected to electrochemical reactions of ionic chemical species under the electrode inducing half-cell potentials of the order of 1V or less. However, patient movements can change the electrode position and the chemical concentrations of these species can vary leading to different half-cell potentials and therefore different iso-electrical (baseline) levels [ 52 ].
5. Conclusions
There are several challenges that must be addressed in order to effectively use ECG as a biometric trait. While many studies have been conducted in reviewing the most popular ECG feature sets and in highlighting similarities and differences among features and classification techniques, there is a lack of research on the data acquisition protocol [ 113 ], which is the focus of this work. Regarding the population size, the majority of the studies have been conducted on a small population (a few tens of subjects). Therefore, the applicability of ECG biometric recognition on a large scale was not yet proven. Moreover, almost all studies ignored the variability of the ECG during life span (i.e., variability induced by work, ageing, sport activity, etc.); besides, only a few studies considered the applicability of these techniques when subjects suffer from pathological conditions. ECG recognition in pathological subjects is another aspect worth additional investigation. Finally, it must be emphasized that, while guidelines are available for ECG acquisition in the clinical scenario, there is still a lack of standardization on ECG acquisition (number of leads and their positioning, sampling frequency, number of bits, filtering, type of electrodes, etc.) for biometric applications. However, ECG databases for biometric recognition should, ideally, include recordings at a given sampling frequency and condition from the same subjects in different circumstances (e.g., relaxed, during and after physical training) and for a period of several years [ 114 ].
Despite the potential of the ECG to be used as one of the main biometric traits, there are still some challenges that need to be solved, especially regarding the acquisition. Quality research is key to addressing the open issues, taking the advantage of current opportunities and proposing increasingly competitive and applicable ECG biometric systems. Furthermore, this research presents a valuable contribution to the field, emphasizing the importance of ECG data acquisition conditions, not only for biometric recognition, but also for other research topics such as disease detection.
Funding Statement
This work was funded by national funds through FCT—Fundação para a Ciência e a Tecnologia, I.P., under the Scientific Employment Stimulus—Individual Call—CEECIND/03986/2018 (R.S.) and the PhD grant UI/BD/153605/2022 (T.M.C.P.), and is also supported by the FCT through national funds, within IEETA/UA R&D unit UIDB/00127/2020, IBEB Strategic Program UIDB/00645/2020, and CICECO-Aveiro Institute of Materials, UIDB/50011/2020, UIDP/50011/2020 and LA/P/0006/2020 (PIDDAC). This work was co-funded by the European Regional Development Fund (FEDER), through Portugal 2020, under the Operational Competitiveness and Internationalization (COMPETE 2020) and Lisboa 2020 programs (grants no. 069918 LISBOA-01-0247-FEDER-069918 POCI-01-0247-FEDER-069918, “CardioLeather”), and CENTRO 2020 program CENTRO-01-0247-FEDER-113480 - “ELIPFOOTSENSE”.
Author Contributions
Author Contributions: Conceptualization, T.M.C.P., R.C.C., V.S. and R.S.; Investigation, T.M.C.P.; Formal analysis, T.M.C.P.; Methodology, T.M.C.P. and R.S.; Supervision, R.C.C., V.S. and R.S.; Writing—original draft, T.M.C.P.; Writing—review & editing, R.C.C., V.S. and R.S. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Informed consent statement, data availability statement, conflicts of interest.
The authors declare no conflict of interest.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
Method of Biometric Authentication with Digital Watermarks
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Help | Advanced Search
Computer Science > Computer Vision and Pattern Recognition
Title: \textit{sweet} -- an open source modular platform for contactless hand vascular biometric experiments.
Abstract: Current finger-vein or palm-vein recognition systems usually require direct contact of the subject with the apparatus. This can be problematic in environments where hygiene is of primary importance. In this work we present a contactless vascular biometrics sensor platform named \sweet which can be used for hand vascular biometrics studies (wrist-, palm- and finger-vein) and surface features such as palmprint. It supports several acquisition modalities such as multi-spectral Near-Infrared (NIR), RGB-color, Stereo Vision (SV) and Photometric Stereo (PS). Using this platform we collect a dataset consisting of the fingers, palm and wrist vascular data of 120 subjects and develop a powerful 3D pipeline for the pre-processing of this data. We then present biometric experimental results, focusing on Finger-Vein Recognition (FVR). Finally, we discuss fusion of multiple modalities, such palm-vein combined with palm-print biometrics. The acquisition software, parts of the hardware design, the new FV dataset, as well as source-code for our experiments are publicly available for research purposes.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
- Nigeria’s NIMC introducing one multi-purpose digital ID card, not three

The National Identity Management Commission of Nigeria (NIMC) has clarified that only one new digital ID card with multiple functions will be introduced in the coming days.
This information is contained in a factsheet posted by the ID authority to its X platform on April 12. This comes after it announced the introduction of the card in a statement early this month, which sparked some confusion .
The announcement had led to various interpretations, including that the agency was planning to introduce three different cards, prompting scathing criticisms in the country’s conventional and social media spaces.
Many Nigerians complained that introducing new cards is a duplicative effort given that many other government-issued or backed IDs are already in existence.
Now, the NIMC has re-assured Nigerians that “the new National ID Card is a single, convenient, and General multipurpose card (GMPC) eliminating the need for multiple cards—not three.”
Reiterating some information about the imminent card which it released in its April 5 statement, the NIMC said the ID will have use cases in different sectors such as payments and the broader financial industry, government intervention and social services, and travels, among others.
“The card will be powered by the AFRIGO card scheme, an indigenous scheme powered by NIBSS. Applicants for the cards will have to request with their NIN through the self-service online portal, NIMC offices or their respective banks,” the NIMC notes. NIBSS is the Nigerian Interbank Settlement System with which the government has partnered over the years to issue Bank Verification Numbers (BVN) as a layer of security for bank account holders.
After the application process for the new multi-purpose card, it will be issued through the applicants’ respective banks in line with existing protocols with the issuance of debit/credit cards, the ID authority explains, adding that it “can be picked up by holders at the designated center or delivered to the applicants at the requested location at an extra cost to be borne by the applicants.”
Related Posts

Article Topics
Africa | biometrics | digital ID | multi-purpose national ID card | national ID | National Identity Management Commission (NIMC) | National Identity Number (NIN) | Nigeria
Latest Biometrics News
U.s. academic institutions get biometric upgrades with new partnerships.
A press release says ROC (formerly Rank One Computing), which provides U.S.-made biometrics and computer vision for military, law enforcement…
- Smart Bangladesh 2041: Balancing ambition with reality
Bangladesh aims to be a “Smart” nation by 2041 as the country goes through a drastic transformation founded on digital identity…
Age assurance tech is ready now, and international standards are on their way
The Global Age Assurance Standards Summit has wrapped up, culminating in a set of assertions, a seven-point call-to-action and four…
NIST finds biometric age estimation effective in first benchmark, coming soon
The U.S. National Institute of Standards and Technology presented a preview of its assessment of facial age estimation with selfie…
Maryland bill on police use of facial recognition is ‘strongest law in the nation’
Maryland has passed one of the more stringent laws governing the use of facial recognition technology by law enforcement in…
Immigrant and civil rights groups urge govt to ban own use of FRT, limit private use
Rights groups continue to call on the U.S. government to limit governmental use of facial recognition technology. Digital rights group…
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Continue Reading

DIGITAL ID for ALL NEWS
- Kenya raises issuance targets for digital IDs and passports
- Cameroon telcos get ultimatum to ID all SIM holders in regions plagued by security crisis
- Sierra Leone putting digital ID at the center of its digital transformation agenda
- DPI gets cloud service launch, UN working groups and a definition of ‘public’
- Idemia upgrading Nigeria’s national biometric system to handle 250M IDs
- Ethiopia announces procurement process for digital ID support hardware
- Confusion as Nigeria national ID cards multiply
- World Bank officials discuss using Korea’s national digital ID as a model
- Daily Biometrics News
Featured Company
- More Biometrics Companies
ID for ALL FEATURE REPORTS
- The rise of digital public infrastructure boosts India towards an $8T GDP by 2030
- Simprints plans to make its biometric ID open source for greater social impact
- AI for secure digital identity revolutionizing banking in Pakistan
- More Features and Interviews
BIOMETRICS WHITE PAPERS
- Decentralized identity for secure user authentication
- Protect your business and customers from threat of account fraud
- Generative AI: How to protect your business in the golden age of fraud and disinformation
- The role of electronic travel authorizations
- Metrics that matter – How to evaluate identity verification technology
- More White Papers
BIOMETRICS EVENTS
- Cyber Revolution Summit India
- Cyber Security & Cloud Expo Europe
- West Africa Border Security Week
- GITEX Africa
- 10th Edition Connected Banking Summit Innovation & Excellence Awards Manila Philippines 2024
- More Biometrics Events
EXPLAINING BIOMETRICS
- Public-private partnerships pose opportunity for DPI and national digital ID initiatives
- How KYC goes beyond identity verification
- What is emotion recognition, and how can biometrics be used to perform it?
- 5 ways to protect your digital life
- Four steps to building a passwordless enterprise
- More Biometrics Explainers
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
A new way to detect radiation involving cheap ceramics
Press contact :.

Previous image Next image
The radiation detectors used today for applications like inspecting cargo ships for smuggled nuclear materials are expensive and cannot operate in harsh environments, among other disadvantages. Now, in work funded largely by the U.S. Department of Homeland Security with early support from the U.S. Department of Energy, MIT engineers have demonstrated a fundamentally new way to detect radiation that could allow much cheaper detectors and a plethora of new applications.
They are working with Radiation Monitoring Devices , a company in Watertown, Massachusetts, to transfer the research as quickly as possible into detector products.
In a 2022 paper in Nature Materials , many of the same engineers reported for the first time how ultraviolet light can significantly improve the performance of fuel cells and other devices based on the movement of charged atoms, rather than those atoms’ constituent electrons.
In the current work, published recently in Advanced Materials , the team shows that the same concept can be extended to a new application: the detection of gamma rays emitted by the radioactive decay of nuclear materials.
“Our approach involves materials and mechanisms very different than those in presently used detectors, with potentially enormous benefits in terms of reduced cost, ability to operate under harsh conditions, and simplified processing,” says Harry L. Tuller, the R.P. Simmons Professor of Ceramics and Electronic Materials in MIT’s Department of Materials Science and Engineering (DMSE).
Tuller leads the work with key collaborators Jennifer L. M. Rupp, a former associate professor of materials science and engineering at MIT who is now a professor of electrochemical materials at Technical University Munich in Germany, and Ju Li, the Battelle Energy Alliance Professor in Nuclear Engineering and a professor of materials science and engineering. All are also affiliated with MIT’s Materials Research Laboratory
“After learning the Nature Materials work, I realized the same underlying principle should work for gamma-ray detection — in fact, may work even better than [UV] light because gamma rays are more penetrating — and proposed some experiments to Harry and Jennifer,” says Li.
Says Rupp, “Employing shorter-range gamma rays enable [us] to extend the opto-ionic to a radio-ionic effect by modulating ionic carriers and defects at material interfaces by photogenerated electronic ones.”
Other authors of the Advanced Materials paper are first author Thomas Defferriere, a DMSE postdoc, and Ahmed Sami Helal, a postdoc in MIT’s Department of Nuclear Science and Engineering.
Modifying barriers
Charge can be carried through a material in different ways. We are most familiar with the charge that is carried by the electrons that help make up an atom. Common applications include solar cells. But there are many devices — like fuel cells and lithium batteries — that depend on the motion of the charged atoms, or ions, themselves rather than just their electrons.
The materials behind applications based on the movement of ions, known as solid electrolytes, are ceramics. Ceramics, in turn, are composed of tiny crystallite grains that are compacted and fired at high temperatures to form a dense structure. The problem is that ions traveling through the material are often stymied at the boundaries between the grains.
In their 2022 paper, the MIT team showed that ultraviolet (UV) light shone on a solid electrolyte essentially causes electronic perturbations at the grain boundaries that ultimately lower the barrier that ions encounter at those boundaries. The result: “We were able to enhance the flow of the ions by a factor of three,” says Tuller, making for a much more efficient system.
Vast potential
At the time, the team was excited about the potential of applying what they’d found to different systems. In the 2022 work, the team used UV light, which is quickly absorbed very near the surface of a material. As a result, that specific technique is only effective in thin films of materials. (Fortunately, many applications of solid electrolytes involve thin films.)
Light can be thought of as particles — photons — with different wavelengths and energies. These range from very low-energy radio waves to the very high-energy gamma rays emitted by the radioactive decay of nuclear materials. Visible light — and UV light — are of intermediate energies, and fit between the two extremes.
The MIT technique reported in 2022 worked with UV light. Would it work with other wavelengths of light, potentially opening up new applications? Yes, the team found. In the current paper they show that gamma rays also modify the grain boundaries resulting in a faster flow of ions that, in turn, can be easily detected. And because the high-energy gamma rays penetrate much more deeply than UV light, “this extends the work to inexpensive bulk ceramics in addition to thin films,” says Tuller. It also allows a new application: an alternative approach to detecting nuclear materials.
Today’s state-of-the-art radiation detectors depend on a completely different mechanism than the one identified in the MIT work. They rely on signals derived from electrons and their counterparts, holes, rather than ions. But these electronic charge carriers must move comparatively great distances to the electrodes that “capture” them to create a signal. And along the way, they can be easily lost as they, for example, hit imperfections in a material. That’s why today’s detectors are made with extremely pure single crystals of material that allow an unimpeded path. They can be made with only certain materials and are difficult to process, making them expensive and hard to scale into large devices.
Using imperfections
In contrast, the new technique works because of the imperfections — grains — in the material. “The difference is that we rely on ionic currents being modulated at grain boundaries versus the state-of-the-art that relies on collecting electronic carriers from long distances,” Defferriere says.
Says Rupp, “It is remarkable that the bulk ‘grains’ of the ceramic materials tested revealed high stabilities of the chemistry and structure towards gamma rays, and solely the grain boundary regions reacted in charge redistribution of majority and minority carriers and defects.”
Comments Li, “This radiation-ionic effect is distinct from the conventional mechanisms for radiation detection where electrons or photons are collected. Here, the ionic current is being collected.”
Igor Lubomirsky, a professor in the Department of Materials and Interfaces at the Weizmann Institute of Science, Israel, who was not involved in the current work, says, “I found the approach followed by the MIT group in utilizing polycrystalline oxygen ion conductors very fruitful given the [materials’] promise for providing reliable operation under irradiation under the harsh conditions expected in nuclear reactors where such detectors often suffer from fatigue and aging. [They also] benefit from much-reduced fabrication costs.”
As a result, the MIT engineers are hopeful that their work could result in new, less expensive detectors. For example, they envision trucks loaded with cargo from container ships driving through a structure that has detectors on both sides as they leave a port. “Ideally, you’d have either an array of detectors or a very large detector, and that’s where [today’s detectors] really don’t scale very well,” Tuller says.
Another potential application involves accessing geothermal energy, or the extreme heat below our feet that is being explored as a carbon-free alternative to fossil fuels. Ceramic sensors at the ends of drill bits could detect pockets of heat — radiation — to drill toward. Ceramics can easily withstand extreme temperatures of more than 800 degrees Fahrenheit and the extreme pressures found deep below the Earth’s surface.
The team is excited about additional applications for their work. “This was a demonstration of principle with just one material,” says Tuller, “but there are thousands of other materials good at conducting ions.”
Concludes Defferriere: “It’s the start of a journey on the development of the technology, so there’s a lot to do and a lot to discover.”
This work is currently supported by the U.S. Department of Homeland Security, Countering Weapons of Mass Destruction Office. This support does not constitute an express or implied endorsement on the part of the government. It was also funded by the U.S. Defense Threat Reduction Agency.
Share this news article on:
Related links.
- Harry Tuller
- Tuller Research Group
- Materials Research Laboratory
Related Topics
- Nuclear security and policy
- Materials science and engineering
- Nuclear science and engineering
- Department of Energy (DoE)
Related Articles

A simple way to significantly increase lifetimes of fuel cells and other devices

Harry Tuller honored for career advancing solid-state chemistry and electrochemistry

Light could boost performance of fuel cells, lithium batteries, and other devices
Previous item Next item
More MIT News

From neurons to learning and memory
Read full story →

A biomedical engineer pivots from human movement to women’s health

MIT tops among single-campus universities in US patents granted

A crossroads for computing at MIT

Growing our donated organ supply

New AI method captures uncertainty in medical images
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
Read our research on: Gun Policy | International Conflict | Election 2024
Regions & Countries
About 1 in 4 u.s. teachers say their school went into a gun-related lockdown in the last school year.
Twenty-five years after the mass shooting at Columbine High School in Colorado , a majority of public K-12 teachers (59%) say they are at least somewhat worried about the possibility of a shooting ever happening at their school. This includes 18% who say they’re extremely or very worried, according to a new Pew Research Center survey.
Pew Research Center conducted this analysis to better understand public K-12 teachers’ views on school shootings, how prepared they feel for a potential active shooter, and how they feel about policies that could help prevent future shootings.
To do this, we surveyed 2,531 U.S. public K-12 teachers from Oct. 17 to Nov. 14, 2023. The teachers are members of RAND’s American Teacher Panel, a nationally representative panel of public school K-12 teachers recruited through MDR Education. Survey data is weighted to state and national teacher characteristics to account for differences in sampling and response to ensure they are representative of the target population.
We also used data from our 2022 survey of U.S. parents. For that project, we surveyed 3,757 U.S. parents with at least one child younger than 18 from Sept. 20 to Oct. 2, 2022. Find more details about the survey of parents here .
Here are the questions used for this analysis , along with responses, and the survey methodology .
Another 31% of teachers say they are not too worried about a shooting occurring at their school. Only 7% of teachers say they are not at all worried.
This survey comes at a time when school shootings are at a record high (82 in 2023) and gun safety continues to be a topic in 2024 election campaigns .
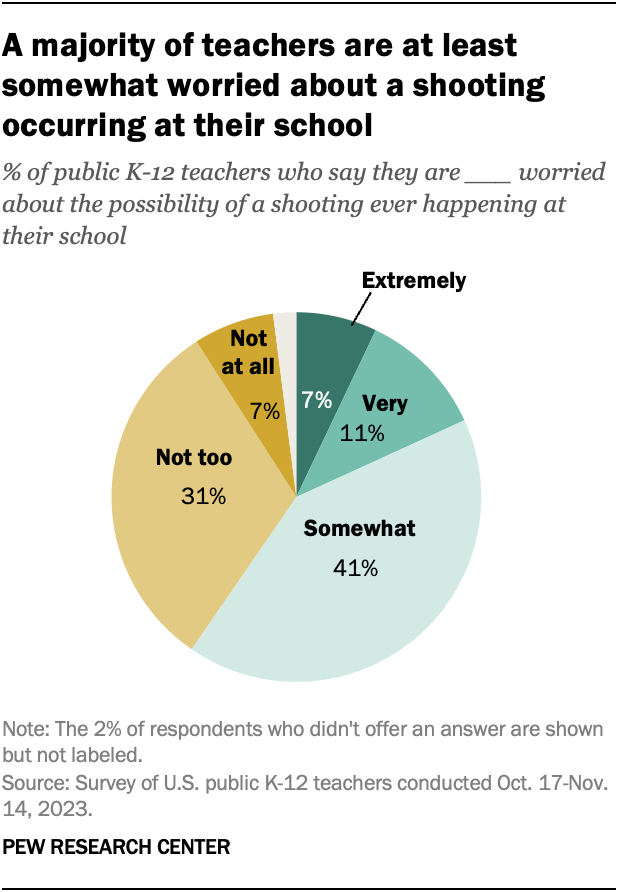
Teachers’ experiences with lockdowns
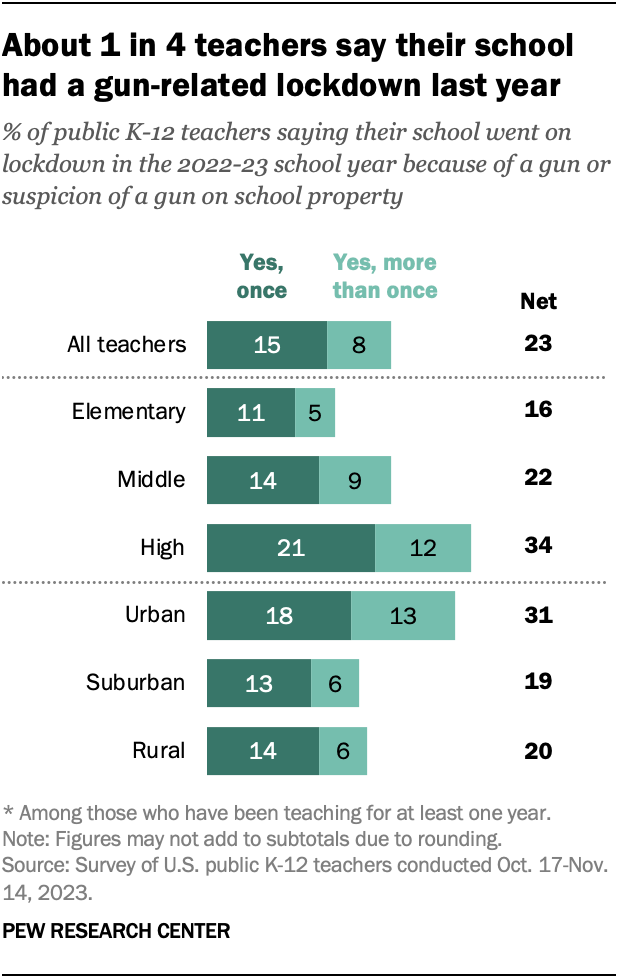
About a quarter of teachers (23%) say they experienced a lockdown in the 2022-23 school year because of a gun or suspicion of a gun at their school. Some 15% say this happened once during the year, and 8% say this happened more than once.
High school teachers are most likely to report experiencing these lockdowns: 34% say their school went on at least one gun-related lockdown in the last school year. This compares with 22% of middle school teachers and 16% of elementary school teachers.
Teachers in urban schools are also more likely to say that their school had a gun-related lockdown. About a third of these teachers (31%) say this, compared with 19% of teachers in suburban schools and 20% in rural schools.
Do teachers feel their school has prepared them for an active shooter?
About four-in-ten teachers (39%) say their school has done a fair or poor job providing them with the training and resources they need to deal with a potential active shooter.
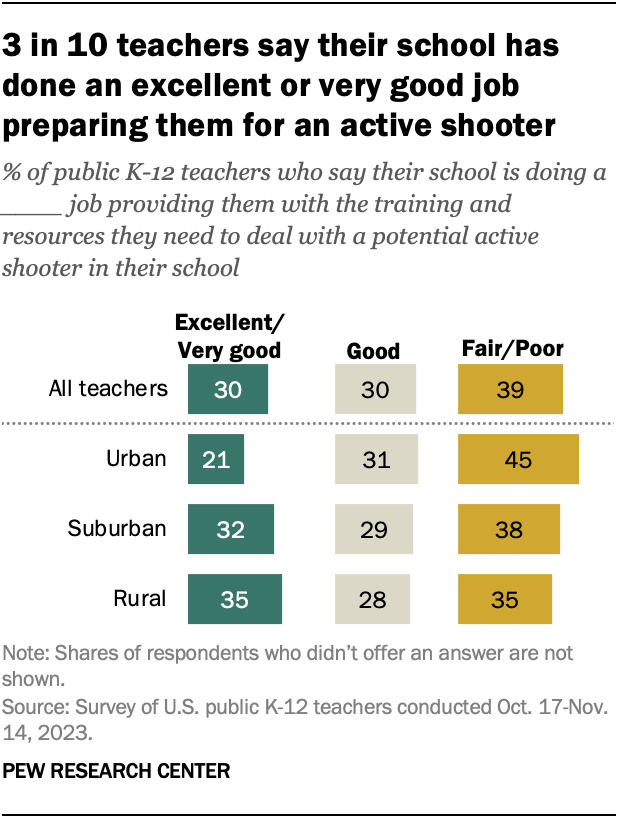
A smaller share (30%) give their school an excellent or very good rating, and another 30% say their school has done a good job preparing them.
Teachers in urban schools are the least likely to say their school has done an excellent or very good job preparing them for a potential active shooter. About one-in-five (21%) say this, compared with 32% of teachers in suburban schools and 35% in rural schools.
Teachers who have police officers or armed security stationed in their school are more likely than those who don’t to say their school has done an excellent or very good job preparing them for a potential active shooter (36% vs. 22%).
Overall, 56% of teachers say they have police officers or armed security stationed at their school. Majorities in rural schools (64%) and suburban schools (56%) say this, compared with 48% in urban schools.
Only 3% of teachers say teachers and administrators at their school are allowed to carry guns in school. This is slightly more common in school districts where a majority of voters cast ballots for Donald Trump in 2020 than in school districts where a majority of voters cast ballots for Joe Biden (5% vs. 1%).
What strategies do teachers think could help prevent school shootings?
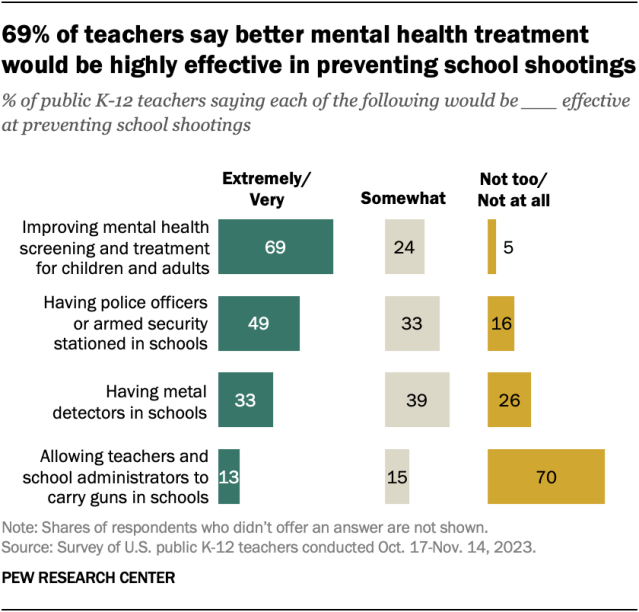
The survey also asked teachers how effective some measures would be at preventing school shootings.
Most teachers (69%) say improving mental health screening and treatment for children and adults would be extremely or very effective.
About half (49%) say having police officers or armed security in schools would be highly effective, while 33% say the same about metal detectors in schools.
Just 13% say allowing teachers and school administrators to carry guns in schools would be extremely or very effective at preventing school shootings. Seven-in-ten teachers say this would be not too or not at all effective.
How teachers’ views differ by party
Republican and Republican-leaning teachers are more likely than Democratic and Democratic-leaning teachers to say each of the following would be highly effective:
- Having police officers or armed security in schools (69% vs. 37%)
- Having metal detectors in schools (43% vs. 27%)
- Allowing teachers and school administrators to carry guns in schools (28% vs. 3%)
And while majorities in both parties say improving mental health screening and treatment would be highly effective at preventing school shootings, Democratic teachers are more likely than Republican teachers to say this (73% vs. 66%).
Parents’ views on school shootings and prevention strategies
In fall 2022, we asked parents a similar set of questions about school shootings.
Roughly a third of parents with K-12 students (32%) said they were extremely or very worried about a shooting ever happening at their child’s school. An additional 37% said they were somewhat worried.
As is the case among teachers, improving mental health screening and treatment was the only strategy most parents (63%) said would be extremely or very effective at preventing school shootings. And allowing teachers and school administrators to carry guns in schools was seen as the least effective – in fact, half of parents said this would be not too or not at all effective. This question was asked of all parents with a child younger than 18, regardless of whether they have a child in K-12 schools.
Like teachers, parents’ views on strategies for preventing school shootings differed by party.
Note: Here are the questions used for this analysis , along with responses, and the survey methodology .

Sign up for our weekly newsletter
Fresh data delivered Saturday mornings
‘Back to school’ means anytime from late July to after Labor Day, depending on where in the U.S. you live
Among many u.s. children, reading for fun has become less common, federal data shows, most european students learn english in school, for u.s. teens today, summer means more schooling and less leisure time than in the past, about one-in-six u.s. teachers work second jobs – and not just in the summer, most popular.
About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .

IMAGES
VIDEO
COMMENTS
Therefore, we have developed a research agenda on these topics with biometric tracking including biometric pricing technology to stimulate the debate in the scientific field and in society in general. ... The aim of this paper is to present a research agenda that focuses on, and directs future considerations towards, intended and unintended ...
However, biometrics offer wider opportunities and their application as enabling technology for modern identity management systems, having a more user-centred approach, will be more important in the near future. In this paper we give an overview of the most important research topics for Biometrics and Identity Management for the near future ...
In this paper we give an overview of the most important research topics for Biometrics and Identity Management for the near future. Discover the world's research 25+ million members
Abstract—Authentication plays a significant part in dealing with security in public and private sectors such as healthcare systems, banking system, transportation system and law and security. Biometric technology has grown quickly recently, especially in the areas of artificial intelligence and identity. Formerly, authentication process has ...
Biometric systems are increasingly replacing traditional password- and token-based authentication systems. Security and recognition accuracy are the two most important aspects to consider in designing a biometric system. In this paper, a comprehensive review is presented to shed light on the latest developments in the study of fingerprint-based biometrics covering these two aspects with a view ...
With an insight into the state-of-the-art research in biometrics for IoT security, this review paper helps advance the study in the field and assists researchers in gaining a good understanding of forward-looking issues and future research directions. Keywords: biometrics, IoT, security, access control, authentication, encryption.
Office of Graduate Studies and Research, San José State University, San Jose, CA 95192-0025 USA ... We accept for the purposes of this paper the definition of biometrics from ISO/IEC JTC1 N3385, 16 Sept., 2009, as ... Eisenhart's publication record on these topics while at NBS was truly
Analyzing people's unique physical and behavioral characteristics is the essence of the science of biometrics. Over the last two decades, we have witnessed an exponential growth of research interests in this domain, through which biometrics has surged from interesting and conventional pattern recognition applications, to deep learning-based mainstream research topics.
Submitted papers should be extended to the size of regular research or review articles, with at least a 50% extension of new results. There are no page limitations for this journal. Topics of interest include, but are not limited to, the following: Biometrics based authentication and identification;
I noticed some biometric research papers of biometric have explored and improved the corpo-ration of machine learning and biometric. Machine learning can greatly improve efficiency and reduce the cost of data collection. Because of the importance of data collection, some papers are directly dedicated to improving data acquisition
In this paper, we present a comprehensive review of the recent advances in biometric recognition using deep learning frameworks. For each work, we provide an overview of the key contributions, network architecture, and loss functions, developed to push state-of-the-art performance in biometric recognition. We have gathered more than 150 papers ...
The first four chapters of this report explain much about biometric systems and applications and describe many of the technical, engineering, scientific, and social challenges facing the field. This chapter covers some of the unsolved fundamental problems and research opportunities related to biometric systems, without, however, suggesting that existing systems are not useful or effective. In ...
Various biometric systems used to measure the unique biological and physiological characteristics of individuals to establish their identity. This paper reviews and scrutinizes the current biometrics systems used in the field of security in terms of usability, techniques, accuracy, advantages, and disadvantages. However, due to the diverse ...
PDF | On Jan 1, 2019, Sunil Swamilingappa Harakannanavar and others published Comprehensive Study of Biometric Authentication Systems, Challenges and Future Trends | Find, read and cite all the ...
Biometric deals with the verification and identification of a person based on behavioural and physiological traits. This article presents recent advances in physiological-based biometric multimodalities, where we focused on finger vein, palm vein, fingerprint, face, lips, iris, and retina-based processing methods. The authors also evaluated the architecture, operational mode, and performance ...
Advanced Topics in Biometrics. Biometrics is the study of methods for uniquely recognizing humans based on one or more intrinsic physical or behavioral traits. After decades of research activities, biometrics, as a recognized scientific discipline, has advanced considerably both in practical technology and theoretical discovery to meet the ...
This paper presents an overview of the main topics related to biometric security technology, with the central purpose to provide a primer on this subject. Biometrics can offer greater security and ...
The purpose of this review is to provide a comprehensive survey on the current biometrics research in IoT security, especially focusing on two important aspects, authentication and encryption. ... the topics such as biometric data protection and biometric-cryptography in the IoT are not covered. To fill this gap, this paper presents an in-depth ...
Tushar Sharma . Upinder Kaur. Keyword (s): Face Recognition . Iris Recognition . Good Alternative . Brain Wave . Biometric Security. This paper presents the different biometric with their limitations and introduces their alternative in form of brain biometric, Breath biometrics, and Tongue biometrics.
This systematic review aims to discuss past research on the impact of variables in the data acquisition methods of an ECG signal on the biometric recognition process. The paper is organized as follows: Section 2 presents the review methodology. Section 3 provides an overview of ECG acquisition and databases, which are discussed in Section 4.
This paper considers methods of fingerprint protection in biometric authentication systems. Including methods of protecting fingerprint templates using zero digital watermarks and cryptography techniques. The paper considers a secure authentication model using cryptography and digital watermarks.
PDF | On Jun 18, 2021, Mr Vinayak Pujari and others published Research Paper on Biometrics Security | Find, read and cite all the research you need on ResearchGate
Current finger-vein or palm-vein recognition systems usually require direct contact of the subject with the apparatus. This can be problematic in environments where hygiene is of primary importance. In this work we present a contactless vascular biometrics sensor platform named \\sweet which can be used for hand vascular biometrics studies (wrist-, palm- and finger-vein) and surface features ...
Now, the NIMC has re-assured Nigerians that "the new National ID Card is a single, convenient, and General multipurpose card (GMPC) eliminating the need for multiple cards—not three.". Reiterating some information about the imminent card which it released in its April 5 statement, the NIMC said the ID will have use cases in different ...
In the current paper they show that gamma rays also modify the grain boundaries resulting in a faster flow of ions that, in turn, can be easily detected. And because the high-energy gamma rays penetrate much more deeply than UV light, "this extends the work to inexpensive bulk ceramics in addition to thin films," says Tuller.
Fingerprint system is a keenly researched area in biometric technologies [9]. It is one of the most well-known biometrics across the globe for personal recognition and identification of ...
Research Topics . Topics. ... (82 in 2023) and gun safety continues to be a topic in 2024 election campaigns. Teachers' experiences with lockdowns. About a quarter of teachers (23%) say they experienced a lockdown in the 2022-23 school year because of a gun or suspicion of a gun at their school. Some 15% say this happened once during the year ...