- Entry Level Cybersecurity Resume Example

Resume Examples
- Common Tasks & Responsibilities
- Top Hard & Soft Skills
- Action Verbs & Keywords
- Resume FAQs
- Similar Resumes
Common Responsibilities Listed on Entry Level Cybersecurity Resumes:
- Monitor and analyze network traffic for suspicious activity
- Develop and implement security policies and procedures
- Perform vulnerability scans and penetration tests
- Monitor and respond to security incidents
- Perform regular security audits
- Implement security controls to protect systems and data
- Configure and maintain firewalls and other security devices
- Research and recommend security solutions
- Train users on security policies and procedures
- Monitor compliance with security policies
- Develop and maintain security awareness programs
- Investigate security breaches and recommend corrective actions
Speed up your resume creation process with the AI-Powered Resume Builder . Generate tailored achievements in seconds for every role you apply to.
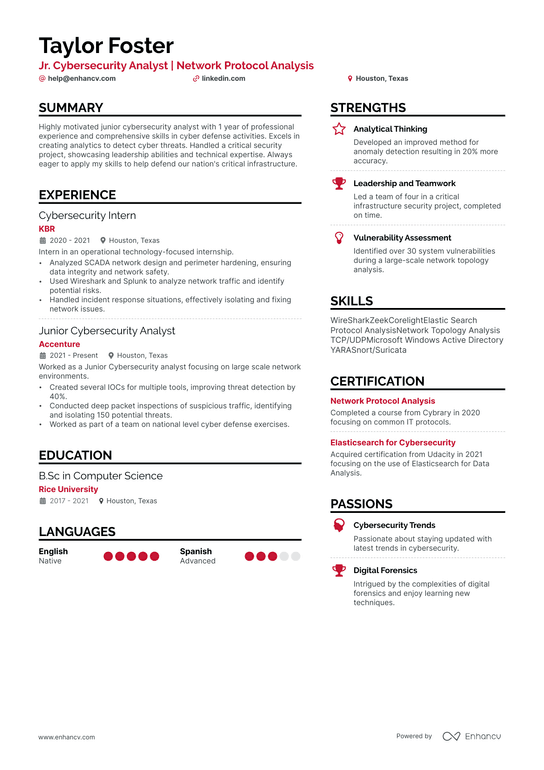
Entry Level Cybersecurity Resume Example:
- Developed and implemented security awareness training program for 100+ employees, resulting in a 25% decrease in security incidents caused by human error.
- Conducted regular security audits and vulnerability scans, identifying and addressing 50+ security vulnerabilities and reducing the risk of cyber attacks by 40%.
- Collaborated with cross-functional teams to implement security controls and configure firewalls, ensuring compliance with industry standards and protecting sensitive data.
- Monitored and analyzed network traffic for suspicious activity, detecting and responding to 20+ security incidents and minimizing the impact of cyber attacks on the organization.
- Researched and recommended security solutions, leading to the implementation of a new endpoint protection system and reducing the risk of malware infections by 50%.
- Performed penetration tests on critical systems, identifying and addressing 10+ vulnerabilities and improving the overall security posture of the organization.
- Investigated security breaches and recommended corrective actions, leading to the implementation of new security controls and reducing the risk of future incidents by 30%.
- Developed and maintained security policies and procedures, ensuring compliance with industry standards and reducing the risk of regulatory fines by 25%.
- Performed regular vulnerability scans and penetration tests, identifying and addressing 30+ security vulnerabilities and improving the overall security posture of the organization.
- Security awareness training
- Security audits
- Vulnerability scanning
- Firewall configuration
- Network traffic monitoring
- Incident detection and response
- Security solution research
- Endpoint protection
- Penetration testing
- Security breach investigation
- Security policy development
- Compliance management
- Risk assessment and mitigation
- Cross-functional collaboration
- Cyber threat intelligence
- Intrusion detection and prevention
- Encryption and data protection
- Access control management
- Security incident management
- Security tool implementation and management
Top Skills & Keywords for Entry Level Cybersecurity Resumes:
Hard skills.
- Network Security
- Vulnerability Assessment
- Penetration Testing
- Incident Response
- Security Information and Event Management (SIEM)
- Firewall Configuration and Management
- Intrusion Detection and Prevention
- Risk Assessment and Management
- Security Auditing and Compliance
- Cryptography
- Identity and Access Management (IAM)
- Security Operations Center (SOC) Operations
Soft Skills
- Attention to Detail
- Analytical Thinking
- Problem Solving
- Communication Skills
- Teamwork and Collaboration
- Adaptability
- Time Management
- Critical Thinking
- Customer Service
- Ethics and Integrity
Resume Action Verbs for Entry Level Cybersecuritys:
- Investigated
- Implemented
- Collaborated
Generate Your Resume Summary
Resume FAQs for Entry Level Cybersecuritys:
How long should i make my entry level cybersecurity resume, what is the best way to format a entry level cybersecurity resume, which keywords are important to highlight in a entry level cybersecurity resume, how should i write my resume if i have no experience as a entry level cybersecurity, compare your entry level cybersecurity resume to a job description:.
- Identify opportunities to further tailor your resume to the Entry Level Cybersecurity job
- Improve your keyword usage to align your experience and skills with the position
- Uncover and address potential gaps in your resume that may be important to the hiring manager
Complete the steps below to generate your free resume analysis.
Related Resumes for Entry Level Cybersecuritys:
Entry level it manager, entry level system administrator, fresher cybersecurity, fresher network engineer, it security analyst, it support specialist, junior system administrator, cybersecurity analyst.
9 Entry Level Cyber Security Resume Examples for 2024
Breaking into cyber security starts with a good entry-level resume. This article lays out clear examples and strategic tips. You'll learn to highlight your skills, education, and any relevant experience. We'll guide you through crafting a resume that speaks to hiring managers directly, in a language that resonates with the cyber security industry. Expect straightforward advice that puts you on the right path to your first cyber security job.

- 26 Apr 2024 - 1 new resume template (Cybersecurity Incident Responder) added
- 18 Apr 2024 - 1 new section (Key skills for cyber security roles) added
- 10 Apr 2024 - 1 new resume template (Information Security Specialist) added
- 02 Apr 2024 - 1 new section (Quantify your achievements) added
- 25 Mar 2024 - 1 new section (Match your skills to the job) added
- 17 Mar 2024 - 1 new section (Beat resume screeners) added
- 09 Mar 2024 - 4 new sections, including 'Placement of education section', added
- 09 Mar 2024 - 5 new resume templates, including Entry Level Cyber Security with Network Security specialization, added
- 07 Mar 2024 - Article published
- 04 Mar 2024 - Resumes approved
- 02 Mar 2024 - First draft complete
Next update scheduled for 04 May 2024
Here's what strong entry-level cyber security resumes share.
Quantifying Impact With Metrics : Good resumes show clear impact with numbers. They include reduced risk percentages , increased system uptime , attack simulations conducted , and security patches applied .
Match Skills With Job Description : You should include skills on your resume that you have and are mentioned in the job description. Some common ones are firewall management , intrusion detection , cryptography , security auditing , and threat analysis .
Up-to-date Industry Certifications : Staying current is crucial. Mention certifications like Certified Ethical Hacker or CompTIA Security+ to show that you're a well-prepared candidate.
use this maybe to have a resume upload button widget 1: yellow Here's a short quick tip / warning for people to include. If your symptoms get worse or do not improve after 1 day, go to a lower altitude if you can. Try to go around 300 to 1,000 metres lower.
widget 2: red / but not serious Here's a short quick tip / warning for people to include. If your symptoms get worse or do not improve after 1 day, go to a lower altitude if you can. Try to go around 300 to 1,000 metres lower.
helpful blue / but not serious Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include. Here's a short quick tip / warning for people to include.
Entry Level Cyber Security Resume Sample
Placement of education section.
Put your education section at the top of your resume if you are new to cyber security. This will show your latest and most relevant learning. If you have cyber security certifications or have studied related topics, highlight these first. It tells employers that you have the knowledge needed for this kind of work.
If you have done internships in cyber security, list them under your education. This way, you link your learning to real work. It helps employers see how you have applied your skills in a work setting.
Emphasize security clearances
If you have any security clearances, put them on your resume. This is more important for cyber security jobs than most other fields. It lets employers know you can handle sensitive information.
Also, if you have been part of any cyber security clubs or groups, list these in an additional section. It shows your interest and dedication to this field beyond just your studies.
Keep your resume brief
Your resume should be one page long. This length works well for entry-level positions. Focus on the last 5 years of your work and studies. If you have done projects or work in the cyber security field, make sure to include it.
When you list your experience and skills, be clear and to the point. This makes your resume easier to read and shows that you can share information in a simple way, which is important in cyber security work.
Junior Cyber Security Analyst Resume Sample
Highlight relevant technical skills.
In your skills section, list technical abilities that match the job you want. For cyber security, skills like knowledge of firewalls, understanding of different operating systems, and basic coding are good to list. Show any hands-on experience with security tools or software.
If you have completed relevant projects, even in school, describe them briefly. Details like these show employers that you can apply your skills in practical tasks, which is key for cyber security roles.
Cyber Security Engineer Resume Sample
Beat resume screeners.
Applicant Tracking Systems (ATS) can be the first hurdle you face when applying for an entry level position in cyber security. Understanding how these systems work will help you get your resume noticed.
Make sure your resume has the right keywords. Look at the job description for the entry level cyber security role and use the same words in your resume. For example, if the job description mentions 'network security', make sure you include 'network security' in your resume.
Use a simple format. ATS can have trouble reading fancy fonts or layouts. Stick with a standard resume format and a clear font like Arial or Times New Roman. Here are some points to keep in mind:
- Include specific skills like 'firewall administration' or 'incident response' to show you have the knowledge needed for the job.
- Highlight any relevant projects or coursework if you lack job experience. This could be class projects or personal projects that show your skills in cyber security.
Cyber Security Consultant Resume Sample
Match your skills to the job.
When you apply for a job in cyber security, show you have the skills they want. Read the job post and use the same words they do to describe your abilities. This makes it clear you are a good fit for the role.
- List any programming languages you know, like Python or Java, to show you can handle the technical parts of the job.
- Talk about any security tools you have used, such as firewalls or antivirus software, to show you understand how to protect against threats.
- If you come from a different job, point out any experience managing sensitive data or following safety rules.
Entry Level Cyber Security with Network Security specialization Resume Sample
Key skills for cyber security roles.
When building your entry-level cyber security resume, focus on the specific skills that show you're prepared for the challenges in the field. You'll want to highlight your technical abilities in a dedicated skills section, which can help you pass through Applicant Tracking Systems (ATS) that scan for relevant keywords.
- Network security
- Firewall administration
- Incident response
- Knowledge of cybersecurity frameworks like NIST
- Vulnerability assessment
- Encryption techniques
- Security Information and Event Management (SIEM) tools
- Understanding of operating systems , both Windows and Linux
- Programming languages , like Python or Java
- Identity and access management (IAM)
Remember, you don't need to have every skill listed, but you should include those most relevant to the job you're aiming for. Tailor your resume to showcase the skills that align with the job description. For example, if the job focuses on network security, ensure skills like firewall administration and vulnerability assessment are prominent.
If you have completed any relevant projects, either through coursework or on your own, mention these under a 'Projects' section, and link the skills you've listed to the work you've done. This gives a practical demonstration of your abilities, making your resume stand out to hiring managers.
Information Security Specialist Resume Sample
Quantify your achievements.
Using numbers to show your impact helps hiring managers see the value you bring. In cyber security, even at an entry level, you can demonstrate how you've made a difference. Think about times you've helped improve security or efficiency.
Here are some ways to reflect your impact:
- Include percentage increases in system security after you implemented new protocols.
- Show number of security breaches you identified and resolved.
Consider any project where you've played a role, even in a learning capacity. Maybe you contributed to reducing the response time to threats or increased the number of secure transactions . If you're unsure of exact numbers, estimate based on your contributions. For example:
- If you worked on a team that improved software security, estimate the percentage of vulnerability patches you were involved in implementing.
- For projects that enhanced data protection, mention the amount of data you helped to secure.
- Did you assist in training? Include the number of people you trained and any feedback scores to show effectiveness.
- If you've been part of a monitoring team, share the frequency of security checks you conducted.
Remember, numbers stand out to hiring managers. They make your experience tangible and show the clear impact of your work.
Cybersecurity Incident Responder Resume Sample
- Security Analyst Resume Examples
- Cyber Security Resume Examples
- Security Engineer Resume Examples
- Security Manager Resume Examples
- Cyber Security Analyst Resume Examples
- Network Security Engineer Resume Examples
- Mechanical Service Engineer Resume Examples
- Software Engineer Resume Examples
Quick links
Entry level cyber security, resume sample #1, resume sample #2, resume sample #3, junior cyber security analyst, resume sample #4, cyber security engineer, resume sample #5, cyber security consultant, resume sample #6, entry level cyber security with network security specialization, resume sample #7, information security specialist, resume sample #8, cybersecurity incident responder, resume sample #9, additional resources, questions get in touch.
Build my resume
- Resume builder
- Build a better resume in minutes
- Resume examples
- 2,000+ examples that work in 2024
- Resume templates
- 184 free templates for all levels
- Cover letters
- Cover letter generator
- It's like magic, we promise
- Cover letter examples
- Free downloads in Word & Docs
5 Cyber Security Resume Examples for the Job in 2024
Cyber Security
Best for senior and mid-level candidates.
There’s plenty of room in our elegant resume template to add your professional experience while impressing recruiters with a sleek design.
Resume Builder
Like this template? Customize this resume and make it your own with the help of our Al-powered suggestions, accent colors, and modern fonts.
Cyber Security Resume
- Cyber Security Resumes by Experience
- Cyber Security Resumes by Role
- Write Your Cyber Security Resume
As a cyber security expert, you’re the shield that guards networks and systems from dangerous threats. Your in-depth knowledge helps you prevent attacks before they’re even a blip on the radar, and thanks to your keen eye for detail, you monitor networks and respond to incidents promptly and effectively.
You’re no stranger to battling malware, DDoS attacks, or zero-day vulnerabilities—but creating a resume and writing an effective cover letter that highlights all of your strengths is a whole different ballgame.
Just like you’re an expert in your field, we know a thing or two about applying for jobs, and we’re here to help. Our cyber security resume examples and resume tips will help you land more interviews and advance your career.
or download as PDF

Why this resume works
- Detail specific threats you’ve addressed or security measures you’ve implemented.
- Make mention of the specific security frameworks and systems you’re familiar with and be clear about how they were used in your previous positions.
- If you hold any cyber security certifications, include these to highlight commitment to staying up-to-date with the latest in the field.
Cyber Security Intern Resume

- Look back to your practical projects that directly relate to the position you are applying for. From there, show what you learned, and you’re ready to use in real-work setting.
Entry-Level Cyber Security Resume

- Talk about the specific projects related to cyber security you’ve been a part of to demonstrate your knowledge and enthusiasm for the field.
- And include certifications. Even entry-level ones can help demonstrate your dedication and commitment to a career in cyber security.
Cyber Security Engineer Resume

- While quantified achievements will do you good here, adding a certification in your area of specialization will get you closer to be hired. See how Ezekiel successfully deploys his certificate in information systems security in his application.
Cyber Security Analyst Resume

- Most of the time, when people include a summary statement, they do so to their own detriment! Unless you’re gonna take the time to be specific to the job you want and speak to your greatest successes without repeating what you’ve already said in your resume, it’s best to just leave it out.
Related resume examples
- Data Engineer
- Network engineer
- Software Engineer
Adjust Your Cyber Security Resume to Match the Job

Organizations depend on your skills to protect them from various threat actors, so you’ll have a lot to talk about in this part of your resume. The key is to be as specific as you can and stay far, far away from generic terms like “hard worker.”
Seeing as your job is entirely based in IT, zone in on those technical skills . List software, cyber security frameworks, and, of course, the programming languages you’ve mastered. Don’t forget to mention your knowledge of networks, malware, and various system vulnerabilities.
Unless you’re in a leadership position such as CISO, soft skills can be reserved for the “work experience” section
Need some ideas?
15 popular cyber security skills
- Security Auditing
- Firewall Administration
- Threat Intelligence
- Crisis Management
Your cyber security work experience bullet points
Between setting up new firewalls, responding to incidents, and carrying out cyber security audits to pinpoint potential vulnerabilities, it’s safe to say you’ve got your hands full. However, in a job like yours, it’s better to focus on the bigger achievements rather than on the daily grind.
Why? It’s simple—as a cyber security expert, your work is why your company can keep running seamlessly, with no risk of data leaks and the monetary losses that come with them. Your effectiveness is directly tied to the success of your organization.
Regardless of the extent of your experience, use this part of your resume to talk about the things you’re proud of, be it improving response readiness or minimizing impact. Rely on data to make your claims stand out as the stellar accomplishments they truly are.
- Highlight instances where your work decreased malware incidents and mitigated risks.
- Show that you know how to act quickly that by talking about cutting down response times.
- Threat modeling and risk assessment are crucial, so don’t forget to include those metrics in your resume: how many threat models have you created? What kind of an increase in threat prevention were you able to achieve?
- Make sure to refer to specific technologies where applicable; for example, say that you upgraded Cisco ASA firewalls and the throughput boost that this brought on.
See what we mean?
- Implemented a comprehensive log monitoring and analysis system, cutting incident response time by 32%
- Developed comprehensive antivirus and anti-malware strategies, decreasing malware incidents by 41%
- Conducted vulnerability assessments using Nessus, reducing risk exposure by 74%
- Spearheaded the implementation of a LogRhythm SIEM platform, enabling a 23% speed boost in detecting potential threats
9 active verbs to start your cyber security work experience bullet points
- Implemented
3 Tips for Writing an Entry-Level Cyber Security Resume
- Even if you’re just starting out, it’s important to fill your resume with relevant skills and work experience bullet points. If this is your first job in cyber security, simply talk about the projects you’ve worked on during your education, such as leading a student group to create a comprehensive incident response plan.
- Don’t list every cyber security-related skill you can think of—pick the things you know you’re good at. Stick to around 10 skills and swap them around based on the job description . For instance, if there’s an emphasis on monitoring traffic, discuss how you used Wireshark to troubleshoot networks in the past.
- Aside from your education, be it in college or at a cyber security bootcamp, you may have obtained some extra certifications—throw them in! Adding certs like the CompTIA Security+, CFR, or CEH can enhance your resume .
3 Tips for Writing a Cyber Security Resume if You’re Experienced
- If you’re a pro in a specific area of cyber security, such as threat analysis, incident response, or penetration testing, make sure to emphasize that in your resume. This is especially helpful if the job you’re applying to is in the same field as your expertise.
- Cyber security is in a constant state of flux, with new threats and methods cropping up all the time. Show that you’re always keeping up by mentioning recent certifications, contributing to open-source security projects, or attending events like the Black Hat USA.
- While you shouldn’t put down “teamwork” as a skill, you should still mention instances of cross-departmental collaboration. Mention times when you worked with other experts, such as colleagues from the IT, legal, or software engineering departments, and highlight any impactful projects that resulted from these partnerships.
You can, but you don’t have to. The only way to benefit from it is to tailor it to the job, mentioning the company and role by name. Highlight your proficiencies, such as network monitoring or malware detection.
Spotlight the skills that are relevant to both careers as well as your education. For instance, if you previously worked as a nurse, you can highlight the attention to detail required when administering medication and compare it to needing to scan complex lines of code when programming in Python.
Take the time to give further explanation of any gaps and why changing careers is in the interest of the company when you write your cyber security cover letter .
The reverse-chronological format is the way to go. Start with your most recent cyber security job and then work your way back. Omit roles that aren’t relevant to the job and instead add a section for your projects to keep things related to the cyber security field.
Land your next job with our AI-powered, user-friendly tool.
Gut the guesswork in your job hunt. Upload your existing resume to check your score and make improvements. Build a resume with one of our eye-catching, recruiter-friendly templates.
• Work in real-time with immediate feedback and tips from our AI-powered experience. • Leverage thousands of pre-written, job-specific bullet points. • Edit your resume in-line like a Google Doc or let us walk you through each section at a time. • Enjoy peace of mind with our money-back guarantee and 5-star customer support.
Resume Checker Resume Builder

- • Developed and implemented a threat detection system that reduced false positives by 60%.
- • Collaborated with a team to enhance security protocols, resulting in a 30% improvement in system resilience.
- • Managed security assessments for 10+ clients, ensuring compliance with industry standards and regulations.
- • Advised 15+ clients on cybersecurity best practices, leading to a 50% reduction in security breaches.
- • Initiated and led a project that enhanced the security infrastructure for a major financial institution.
- • Conducted regular training sessions for clients, enhancing their internal team's cybersecurity knowledge.
- • Designed a multi-layered security protocol that was adopted across 5 major projects.
- • Collaborated with software developers to integrate security measures at the code level, reducing potential vulnerabilities.
- • Played a key role in a team that successfully defended against a major cyber-attack, ensuring data integrity.
7 Cyber Security Analyst Resume Examples & Guide for 2024
Customize this resume with ease using our seamless online resume builder.
All resume examples in this guide

Junior Cyber Security Analyst

Ethical Hacker
Penetration Tester

Security Analyst
Application Security Engineer

Cybersecurity Engineer
Resume guide, how to write a cyber security analyst resume, cyber security analyst header - the first impression, how to write a powerful resume summary, what should you include in your cyber security analyst experience section, does a cyber security analyst resume need an education section.
Are certificates essential for cyber security analyst resumes?"?
Top skills to include on your cyber security analyst resume
Key takeaways.
By Experience
So you have the skills to defend a network (and possibly hack it too).
But do you know how to translate them onto a job-winning resume?
If you don’t, your resume won’t get read, and it’ll be filed alongside the candidates who couldn’t fend off a script kiddie.
Luckily, you’ve found this guide, and you can save your thanks for when you get the job. But watch out for those vengeful blue hat hackers who you beat to the mark…
According to the BLS , Cyber Security Analyst jobs are predicted to increase by 31% from 2020 to 2029, so now’s the perfect time to be on the hunt for a new role.
Get ready to land a job where you’ll hook the worms, quarantine the virus, burn the Trojan, neutralize spyware, unclog the DOS, and build a firewall that Dumbledore would be proud of. You’re a wizard.
Prove it in your resume.
This guide will show you how.
What you’ll learn here
- What a Cyber Security Analyst Resume looks like, with templates and examples.
- Which resume sections you need to include.
- What qualifications and certificates are important, and how to list them.
- How to write clear and impactful sections that align with the job description.
- How to get the hiring manager to visualize what you can do.
Take a piece of A4 paper and fold it into 3 sections. Top, middle, and bottom. The top third is reserved for directly answering the hiring manager’s most pressing questions.
You have 5 seconds to capture their attention. But how?
Take their job listing and write a resume that matches. Take note of the keywords they use, and exactly what they’re looking for in the “Responsibilities” section of the job description.
Do they want an analyst who’s eliminated CVE’s using C++? Created hardware and software upgrades with a programming language? If you have it, flaunt it.
Emphasize all of the skills and qualifications they’re directly looking for.
Applying for your first Cyber Security Analyst role? At a minimum, they need to see some kind of IT-related work. Do you have any experience with Homelab? TryHackMe? Hack The Box? Practical experience is a major asset as an entry-level Cyber Security Analyst
Get recruiters visualizing your abilities using descriptive techniques, like CAR (Challenge, Action, Result). What was the challenge? The actions you took? And the results?
That’s the best way to build their confidence in you – before you ever meet them.
Top resume sections
- Header with your personal information
- A resume summary with an overview of your abilities
- Experience section to dive deep into your achievements and techniques
- Education & certifications sections
- Skills section that highlights the top requirements of the role
What recruiters want to see
- Examples of CAR (Challenge, Action, Results)
- Relevant certifications and proof of how you made use of your knowledge
- Proficiency with technologies and software
- Understanding of the requirements of the role
Resume headers need to look professional and include all necessary information. Miss a step here and it might be game over before it’s even begun.
Don’t worry – simple, but crucial information presented professionally is all you need to do here.
It’s the first section the recruiter will see, so let’s start off on the right foot.
Your resume header should include:
- Your first and last name
- Job title and seniority level
- Email address
- Phone number
- Relevant links (portfolio, Github profile, personal website or LinkedIn )
2 cyber security analyst resume header examples
This header is missing the mark. It has nothing but an email address, a city and a name.
Unfortunately, he also made a mistake in the spelling of his email and now he’s unreachable.
Let’s fix this.
This one leaves a much better first impression.
This candidate has included multiple methods of contact , along with a link to their Github profile.
This shows great attention to detail.
Now that the header is written, let’s move onto writing the resume summary.
Just underneath your header sits your resume summary.
Your job with this section is to impress the recruiter in less than 5 seconds.
How do you do this?
By first reading the job description to see exactly what they’re looking for in their ideal candidate.
Then, mirror the same keywords that they use in your resume summary (as long as you truthfully have those skills).
This could be which technologies you’ve worked with to identify and prevent against threats, how you remediated security breaches, and the years of experience you have in cybersecurity.
Use the CAR (challenge, action, result) approach to write your resume summary.
Let’s take a look at two different examples.
2 Cyber security analyst resume summary examples
This summary leaves important questions unanswered:
- What kind of Cyber Security Analyst experience? How many years?
- What specific skills and technical knowledge does the candidate have?
- Which tools are they proficient with?
- What kind of impact did they make in previous roles?
Let’s take a look at a better example.
Your goal is to grab the attention of the recruiter and have them pick up the phone to call you in for an interview.
Using real figures and quantifiable data is the way to go. You can talk about:
- Years of experience
- Specific technologies used
- Actions taken
- Real results, such as money made or saved
Congrats! The recruiter was impressed by your summary and wants to deep dive further into your experience.
Use the experience section to expand on your previous roles and the processes you used.
It’s all about the challenges you faced, the steps you took to remedy them, and the impactful results you achieved.
Now is not the time to be shy about your achievements – recruiters want to build the confidence that you have what it takes to succeed.
Let’s look at some examples:
Cyber security analyst resume experience examples
- • Helped to engage cyber threats in a timely manner, taking the necessary steps to contain and neutralize the attacks as part of a team
- • Implemented and enhanced company security measures
- • Determined weaknesses in infrastructure security
You can’t be this vague and still expect to land an interview!
Anyone can simply list out responsibilities on their resume. Stand out by weaving in achievements and quantifiable results.
You have to expand and be specific.
Let’s see this in action:
- • Lead repair of OS after detaining and neutralizing DOS, Trojan, and other malware attacks, saving the company an estimated $400,000 over 2 years.
- • Configured and maintained company’s first Devo SIEM antivirus system in the first month after identifying weaknesses in the initial security assessment.
- • Ran development and maintenance of IAM and led the encryption protection of cloud security.
- • Maintained an MTTR of 3.5 hours on average.
This section is much better!
It calls out specific keywords that were likely in the job description, and it makes an impact with real achievements that are backed up with data.
Your resume definitely needs its own education section . Here’s what you should include:
- Your degree
- University/college name
- Graduation year
- Bonus points: Notable projects
Many Cyber Security Analyst jobs require a postgraduate degree or diploma in either Cybersecurity, Information Assurance, or another related field of study.
If you lack formal education, a few years of highly relevant job experience should be enough to make up for it.
Are certificates essential for cyber security analyst resumes?"?
Certificates are worth their weight in gold in the field of Cyber Security Analyst.
There are plenty to choose from and each one is valued slightly differently from company to company.
Write a separate dedicated section for your certifications . List them out in order from the most relevant and recent. Include the name of the certification and the year you completed it.
Want some inspiration on where to start?
Here’s our list of the most popular and valuable Cyber Security Analyst certifications in the industry:
Top 24 cyber security analyst certificates for your resume
- CompTIA Security+
- CompTIA Pentest +
- CompTIA Network+
- CompTIA IT Operations Specialist
- CompTIA Secure Infrastructure Specialist
- GIAC cert. Incident Handler GCIH
Cyber Security Analysts need both technical and soft skills to be listed in your resume skills section . Recruiters are looking out for proof of this in your resume.
Technical skills are the practical knowledge that you learned with your experience, training and education. This can include the programming languages you’re familiar with, your attack tools and techniques, and frameworks that you turn to.
Soft skills are the personality traits that make you a great asset to a team. They can be centered around your attention to detail, ability to communicate, your motivation to learn, or other admirable traits like those.
Just as with the summary and experience sections, your best place to start is by reading the job description . What skills are they listing as requirements and nice-to-have? If you have it, flaunt it.
Here’s a list of both technical and soft skills to get you started on the right track:
Hard / Technical Skills List
- Data analytics
- Risk assessment
- Malware analysis
- Cloud security
- SIEM & vulnerability assessments
- Incident response
- Cryptography
- Information security (authentication, access control, authorization, audit)
- Application architecture
- IT governance
- Risk & compliance
- Industrial frameworks (NIST, MITRE ATT&CK, OWASP,PCI-DSS, ITIL)
- Understanding of ISO standards
- Regulatory Compliance (SOX, FFIEC, 17A5)
Soft skills list
- Make presentations
- Communication skills (written & verbal)
- Work well with a team and individually
- Strong attention to detail
- Ability to meet tight deadlines
- Project management
- Management skills
- Problem solving
- Performs well under pressure
- Read the job description to see what specific qualifications and knowledge is required, and then write your resume to reflect that.
- Don’t just list out the responsibilities of your past roles – expand on your achievements and back it up with real data.
- Use the CAR method (Challenge, Action, Result) to describe your abilities.
- Certifications are essential in a Cyber Security Analyst resume. Read the job descriptions to see which ones are required. List out your certifications in their own section, starting with the most relevant one first.
Cyber Security Analyst resume examples
Explore additional cyber security analyst resume samples and guides and see what works for your level of experience or role.
For Junior Cyber Security Analyst roles, highlight:
- Experience with intrusion detection systems or firewalls. Mention practical examples of operations or improvements you made.
- Any certifications, like Security+ or SSCP, enhance your profile.
Instead of just listing your skills/tools, always tie them to examples of successful prevention of threats, e.g., "used IDS to avert a potential data breach...".

Hacking methodology trends greatly define the role of an Ethical Hacker. Top traits HRs seek in resumes include:
- Experience in penetration testing and tools, firewall intrusion detection systems, and reverse engineering are critical. Emphasize these skills to stand out.
- Talk about relevant certifications, like CEH or CISSP; these demonstrate your professional learning and commitment.
- Beyond technical skills, showcase your understanding of network protocols, threat modeling, or secure coding practices, e.g., "prevented security breach by implementing...".
- Never just list your abilities; always match them with actions and results, e.g., "Identified and patched...".

Driving factors of your application for a Penetration Tester job include:
- Highlight any experience with OWASP, Metasploit, or Kali Linux. These skills indicate sound technical knowledge. Avoid listing them out; instead, mention how you used them to find vulnerabilities, e.g., "used Metasploit to discover XSS vulnerabilities...".
- Present any security certifications like OSCP or CEH; they boost credibility.
- Showcase your knowledge of the latest security threats. Mention how you leveraged that knowledge to thwart an attack or boost system security.

Resumes for Security Analyst roles should contain:
- Demonstrate knowledge of network defense methodologies or security information and event management (SIEM) tools, without just listing them.
- Focus on any certifications you own, like CISSP or CompTIA Security+.
- Reflect the scope of your knowledge of cybersecurity threats and how you used that knowledge to detect and mitigate threats, e.g., "Analyzed patterns and detected..."."

- Demonstrate your experience with Secure SDLC or OWASP best practices. Display how you applied them to specific projects.
- Professional certifications like CSSLP or CEH are highly preferable.
- Emphasize your successful efforts on improving application security, e.g., "lowered application risks by implementing...".

In a Cybersecurity Engineer's resume, provide:
- Evidence of your knowledge of network security architectures and relevant certifications, like CISSP or CISM.
- Show how your technical expertise, in IDS or encryption, helped improve system security.
- Demonstrate results, for instance, "reduced system vulnerabilities by...". This connects your skills with their practical application.

Looking to build your own Cyber Security Analyst resume?

- Resume Examples
The Best Synonyms for "Proficient" on Resume
How to present your informal education to employers, is it better to staple or paperclip a resume, how to ask an employer for feedback on why you didn't get the job, a surprising lesson from maisie williams about career change, what is an unsolicited resume.
- Create Resume
- Terms of Service
- Privacy Policy
- Cookie Preferences
- Resume Templates
- AI Resume Builder
- Resume Summary Generator
- Resume Formats
- Resume Checker
- Resume Skills
- How to Write a Resume
- Modern Resume Templates
- Simple Resume Templates
- Cover Letter Builder
- Cover Letter Examples
- Cover Letter Templates
- Cover Letter Formats
- How to Write a Cover Letter
- Resume Guides
- Cover Letter Guides
- Job Interview Guides
- Job Interview Questions
- Career Resources
- Meet our customers
- Career resources
- English (UK)
- French (FR)
- German (DE)
- Spanish (ES)
- Swedish (SE)
© 2024 . All rights reserved.
Made with love by people who care.
Resume Builder
- Resume Experts
- Search Jobs
- Search for Talent
- Employer Branding
- Outplacement
- Resume Samples
Cyber Security Analyst Resume Samples
The guide to resume tailoring.
Guide the recruiter to the conclusion that you are the best candidate for the cyber security analyst job. It’s actually very simple. Tailor your resume by picking relevant responsibilities from the examples below and then add your accomplishments. This way, you can position yourself in the best way to get hired.
Craft your perfect resume by picking job responsibilities written by professional recruiters
Pick from the thousands of curated job responsibilities used by the leading companies, tailor your resume & cover letter with wording that best fits for each job you apply.
Create a Resume in Minutes with Professional Resume Templates
- Work with developers, system/network administrators, and other associates to ensure secure design, development, and implementation of applications and networks
- Perform network traffic analysis using raw packet data, network flow, Intrusion Detection Systems (IDS), and custom sensor output from communication networks
- Assist the Cyber Security Manager with the development of the IA related Procedures, and Work Instructions
- Tracks performance metrics and provides timely updates to CSOC management
- Develop, improve and help implement best practices for risk reduction across a broad range of enterprise applications, systems, networks and interfaces
- Assists with the development of processes and procedures to improve incident response times, analysis of incidents, and overall SOC functions
- Works with clients to implement system security measures, assists with computer security plans and documentation and provides technical guidance and training
- Provide technical and operational leadership for cyber-security incident response
- Assist with triage, prioritisation and response to cyber-security events and incidents
- Act as technical incident lead during major cyber-security incidents
- Continuously improve maturity and operational efficiency of the team – including methodologies, processes, detection use cases and response playbooks
- Maintain an up-to-date knowledge of cyber threats
- Drive continuous learning and knowledge sharing within the team
- Work in a 'business hours + rostered on-call' environment
- Provide SME level input for APS
- Working in a SIEM environment
- Provide SME level input support for SC Administrators and HBSS Support Admin's
- Provide ATO Certification & Accreditation artifacts for ACAS and CMRS capabilities
- Provides incident remediation and prevention documentation
- Provides performance metrics as necessary
- Provides customer service that exceeds our customers’ expectations
- Ability to compress knowledge to an easily understandable level for organization circulation
- Knowledge of common application frameworks Strong attention to detail
- Proven accountable, dependable and reliable work ethic
- Demonstrable knowledge of application security, risk assessment, validation of security pen test results, and vulnerability resolution
- Demonstrable knowledge of secure coding practices and the ability to conduct security assessments and analysis of applications
- Ability to break down highly complex technical topics into language and diagrams understandable to a wide audience
- Strong attention to detail
- Strong knowledge of network protocols, network analysis tools, and network architecture
- Excellent business analysis skills, including strong communication abilities
- Ability to perform basic malware analysis to develop network based indicators and custom protocol decoders
15 Cyber Security Analyst resume templates
Read our complete resume writing guides
How to tailor your resume, how to make a resume, how to mention achievements, work experience in resume, 50+ skills to put on a resume, how and why put hobbies, top 22 fonts for your resume, 50 best resume tips, 200+ action words to use, internship resume, killer resume summary, write a resume objective, what to put on a resume, how long should a resume be, the best resume format, how to list education, cv vs. resume: the difference, include contact information, resume format pdf vs word, how to write a student resume, csfc core team cyber security analyst resume examples & samples.
- Provide cyber threat analysis to support development and research teams
- Bachelor’s degree plus 3+ years or Master's degree plus 2+ years working in a cyber-security operations or information security space
- 1+ years leading a cyber-threat analysis related function
- Knowledge of three-tier Internet application architecture
- Experience in packet capture analysis using tcpdump or wireshark
- Knowledge of HTTP, IP, TCP/UDP, BGP, MPLS, and OSPF protocols
- Should have an knowledge of the following areas
- Denial of Service attacks
- Malware analysis
- Knowledge of Network Forensic tools and analysis techniques with a proven ability of identifying malicious traffic and infection vectors
- Experience working with SAP BusinessObjects is a plus
- Understanding of the tools such as, Splunk, ArcSight, Map Reduce, and the sources available to conduct cyber security alerting, analysis, and enhanced situational awareness
Csfc Core Team Senior Cyber Security Analyst Resume Examples & Samples
- Work with Security Operation teams to collect data for incident metrics reporting
- Bachelor’s degree or equivalent work experience. Masters is a plus
- 5+ years working in a cyber-security operations or information security space
- 3+ years leading a cyber-threat analysis related function
- Working experience in analyzing Netflow, DNS, Proxy and web access logs
- Extensive experience in packet capture analysis using tcpdump or wireshark
- Should have an extensive knowledge of the following areas Cyber crime
- Computer Forensics
- Network monitoring, IDS/IPS, Firewalls, Proxy servers, load balancers
- Must be a self-starter, self-motivated and able to work independently with little oversight
- Significant experience working with SAP BusinessObjects
- Strong understanding of the tools such as, Splunk, ArcSight, Map Reduce, and the sources available to conduct cyber security alerting, analysis, and enhanced situational awareness
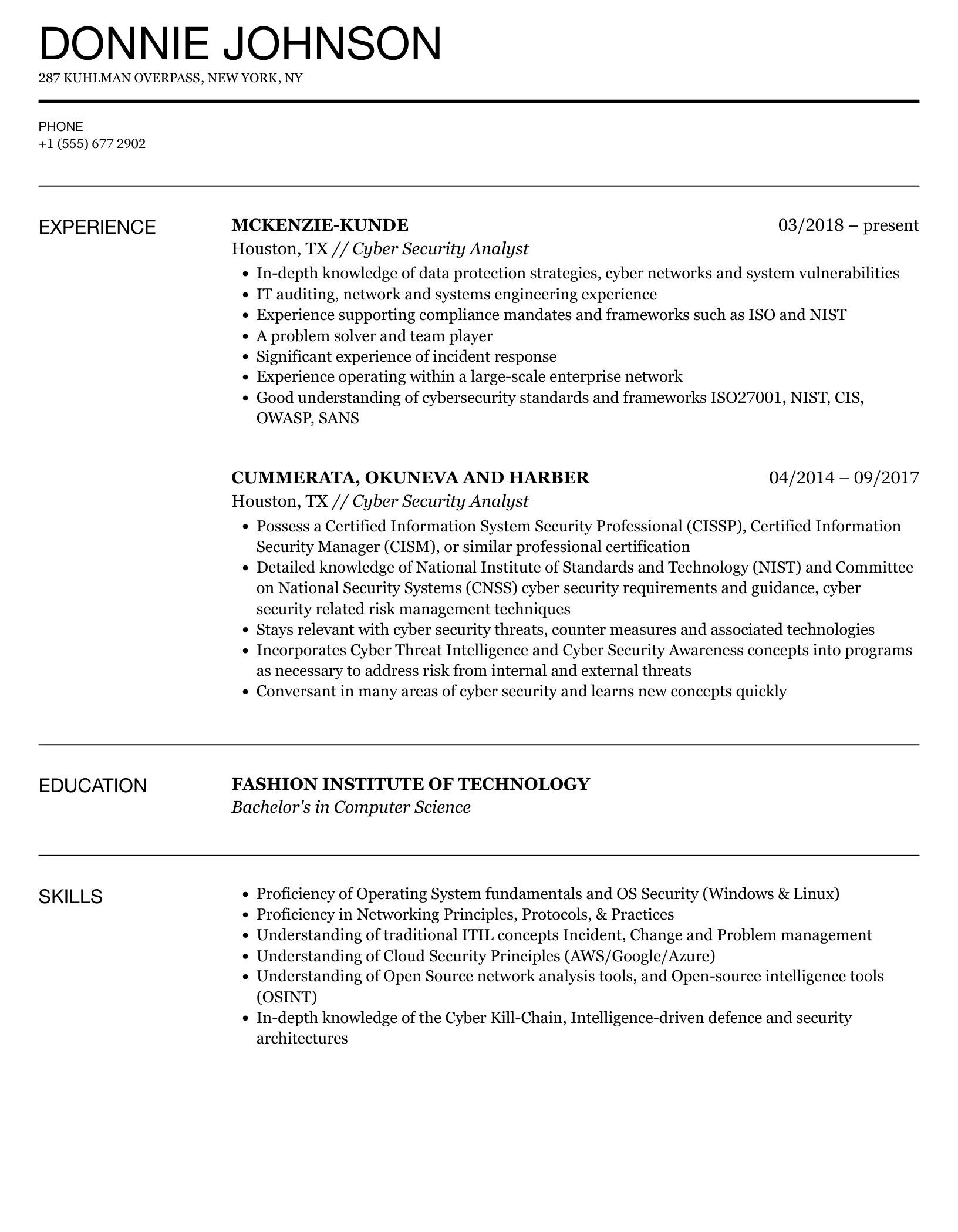
Cyber Security Analyst Resume Examples & Samples
- 3 years of experience as an information assurance analyst on DoD projects or systems of similar scope
- 3 years of experience in working with the DoD IA driving policies, including DoD 8510.01 (DIACAP), DoDI 8500 series (Information Assurance), or CNSSI 1253
- Knowledge of existing USSTRATCOM systems and missions
- Ability to analyze system requirements and develop technical solutions
- Experience with establishing security policies and procedures
- Experience with developing training and instructional documentation
- Knowledge of command and control and communications systems
Cyber Security Analyst, Senior Resume Examples & Samples
- 10 years of experience with information assurance, including information assurance system evaluations, system security penetration testing, security information management, or security event management
- Experience with testing tools, including Nessus, Metasploit, nmap, BurpSuite, Kismet, Nipper, Wireshark, or BackTrack
- Experience with configuring, administering, and troubleshooting operating systems, including UNIX, Linux, Windows, iOS, or Android 6
- Experience with network vulnerability assessments and penetration testing
- Experience with analyzing results, writing assessments, and test reports
- Experience with Cyber forensics a plus
- Experience with the project management framework
- Knowledge of databases, applications, and Web server design and implementation
- Possession of excellent team leadership, development, and client relationship skills
- BS degree in Information Assurance, CS, or Computer Engineering
- Certified Information Systems Security Professional (CISSP), CISM, or other recognized technical Cyber Security Certification preferred
Cyber Security Analyst, Mid Resume Examples & Samples
- Under direct supervision, provides technical support to the organization's internal users of computer applications and client hardware
- Answers routine questions regarding system procedures, online transactions, systems status and downtime procedures
- Assists network services, software systems engineering and/or application development in order to restore service and/or identify problems
- Maintains a troubleshooting tracking log ensuring timely resolution of problems
- Experience with configuration and management of network systems, network design, and integration of security technologies
- Experience with identifying security flaws and misconfiguration from multiple data sources using trend analysis and automated and manual test results
- Experience with analyzing results and writing assessments and test reports
- Ability to communicate in Arabic
- BS degree in Information Assurance, CS, IT, or Computer Engineering
- Experience with Cyber forensics
- Ability to demonstrate industry recognition and publication a plus
- MA or MS degree in Cyber Security, Information Security, or CS
- 5+ years of experience I working with computer network devices and operating systems
- 4+ years of experience with information assurance and security practices
- 3+ years of experience with writing SSPs or other security related policy
- 3+ years of experience with DoD 8500.1, DoD 8500.2, DoD 8510.01, or NIST 800-53
- 1+ years of experience with resolving security findings discovered on network devices and OS
- 1+ year of experience with C&A package review for CA or DAA making risk-based recommendations
- CISSP, CISM, or GSLC Certification, including DoD 8570 IAM Level III
- Experience with FISMA reporting and spreadsheet and DB coding
- Knowledge of DoD acquisition policy
- Knowledge of Service Orientated Architecture (SOA)
- MS degree in a related field
IT Cyber Security Analyst Resume Examples & Samples
- Performing competitive analyses and maintain knowledge of emerging technologies in both the automotive and consumer electronics field
- Actively work with Security Partners, Research, Government, Advanced Engineering for information sharing, joint project development, and reporting
- Scope includes all portions of the connected vehicle ecosystem from vehicle systems, backend cloud infrastructure, to mobile platforms
- Some travel expected to cover critical Cyber Security Conferences or meet with home base in Dearborn
- Monitor global NIDS, Firewall, and log correlation tools for potential threats Initiate escalation procedure to counteract potential threats/vulnerabilities Provide Incident remediation and prevention documentation Document and conform to processes related to security monitoring Provide performance metrics as necessary Provide customer service that exceeds our customers’ expectations
- Research and identify key indicators of malicious activities on the network and end user workstations
- 4 years of hands-on experience in a security operations center (SOC) environment Strong command of Linux systems administration
- Hands on experience with tools such as Wireshark, Hex Rays, IDA Pro or Hex workshop. Experienced in computer security incident response activities Advanced capability to analyze malware, including: worms, viruses, trojans, rootkits and bots Experience with network monitoring and packet analysis tools Strong understanding of TCP/IP An attitude of providing FANATICAL support to the end users! Strong analytical / problem solving skills Strong decision making / risk assessment capability
- GCIH certification/and/or penetration testing experience is highly desired/
- We are offering a competitive hourly rate plus a bonus structure and shift differential for qualfied hours!* **
- Manage & triage daily cases presented in the Brand Protector application tools
- Prepare case studies for internal Under Review and Legal meetings pertaining to infringements that you have researched
- Issue and continuously follow-up on Cease and Desist Notifications to infringers for timely case closure
- Maintain a thorough knowledge of the types of brand infringements and the proper disposition processes available to you as a Brand Protection Analyst for JPMorgan Chase
- Track and monitor the Brand Protection caseload through various reporting methods available to you
- Perform periodic quality assurance checks of Brand Protection databases
- Perform research regarding new technologies used by the firm and brief entire team
- Assist in additional research and executing additional functions within the Cyber Security IT Risk group as required
- B.A. or B.S. preferred
- 2 years of financial services, risk management, technology, digital services or legalfacing experience
- Basic understanding of Cyber Security, Information Security and Risk Management
- Technology experience or technology risk background is a plus
- Strong PC skills, including MS suite are a must (MS Access a plus)
- Web analytics and web design knowledge are a plus
- Attention to detail and strong organizational skills required
- Goal oriented, independent thinker, self-starter
- Excellent interpersonal communication skills (written and verbal) are a must
- Demonstrate an ability to work effectively in a large complex corporate environment
- Demonstrated ability to work independently on projects and produce required results in a time-sensitive environment
Senior Cyber Security Analyst Resume Examples & Samples
- Carry out triage of security events and elevate their priority to incident when required
- Review and remediation of data loss prevention incidents and issues
- Advanced capability to analyse malware, including: worms, viruses, trojans, rootkits and bots
- Provide guidance and mentoring to new and existing members of the team
- Typically a Bachelor’s degree or suitable industry experience
- Strong command of operating systems administration – Windows, LINUX and UNIX
- Good understanding of common protocols and services such as FTP, HTTP, SMB, LDAP and SSH
- Strong time management skills with the ability to multi-task
- Strong decision making and risk assessment capability
- Ability to multitask and be flexible, in an environment of rapid change
- Day-to-day usage of industry standard security tools (SIEM,IDS, IPS, traffic analyst, etc.)
- Research and identify key indicators of malicious activities on the network and end-user workstations
- Initiate the escalation procedure to counteract potential threats/vulnerabilities
- Provide incident remediation and prevention documentation
- Provide performance metrics as necessary
- Provide subject matter expertise on security projects and ensure security controls are implemented according to defined policies
- Participate in business security awareness and training initiatives
- Bachelor’s degree or suitable industry experience
- Strong understanding of TCP/IP
- Experience of vulnerabilities, exploits and network attacks
- Experience of Packet analysis tools
- Hands-on experience in a security operations center (SOC) environment
- Security certifications (as provided by SANS, ISC2, ISACA, E-Council, etc.)
- Lead CSFC EMEA cyber threat analysis, alerting, and reporting based on intelligence and information gathered from both internal and external sources globally
- Drive cyber security research projects using multiple data sources, perform analysis and disseminate findings to both technical and non-technical consumers throughout the Citi enterprise
- Work daily with different Information Security counterparts to gather intelligence and data for analysis and to formulate changes in technology, policy or procedure that may reduce the risk to information security with an emphasis in the EMEA region
- Actively monitor and research cyber threats with a direct or indirect impact to the Citi brand, regional business operations, technology infrastructure and client trust
- Supervise daily interactions with the Cyber Security Fusion Center and collaborate with Cyber Intelligence Center staff to fuse threat intelligence with risk, impact, mitigation and recovery assessments
- Maintain a routine business integration with the CSFC leaders in Warren, NJ, USA and Irving, TX, USA
- Bachelor’s degree and significant equivalent work experience
- Proven ability to review information to determine its significance, validate its accuracy and assess its reliability to technical and non-technical audiences
- Expertise or significant working knowledge several of the following areas
- Perform CSFC EMEA cyber threat analysis, alerting, and reporting based on intelligence and information gathered from both internal and external sources globally
- Conduct research using multiple data sources, perform analysis and disseminate findings to both technical and non-technical consumers throughout the Citi enterprise
- Work daily with different Information Security teams to gather intelligence and data for analysis and to formulate changes in technology, policy or procedure that may reduce the risk to information security with an emphasis in the EMEA region
- Interact daily with the Cyber Security Fusion Center and collaborate with Cyber Intelligence Center staff to fuse threat intelligence with risk, impact, mitigation and recovery assessments
- Maintain a routine business integration with the CSFC teams in Warren, NJ, USA and Irving, TX, USA
- 3+ years working in a cyber-security operations or information security space
- Exceptional written and verbal communication and presentation skills to internal and external customers, ability to speak and write in multiple languages a plus
- Should have expertise or working knowledge in the following areas
Csirt Cyber Security Analyst Resume Examples & Samples
- One or more of the following technical certifications: GIAC Certified Incident Handler (GCIH), GIAC Certified Forensic Analyst, EnCE or equivalent certification in these areas
- Strong technical expertise in
- Ability to document and explain technical details clearly and concisely to both technical peers and senior (non technical) business management
- Ability to manage multiple projects under tight deadlines
- Solid attention to details
- Ability to think “outside the box” and identify opportunities to improve current processes
- Bachelor's Degree with 2-3 years of Information Security experience or an Associate's Degree with equivalent technical certifications
- Strong technical skills across cyber security technologies including; scripting skills and an understanding of network traffic flows, and vulnerability management
- Computer literacy with proficiency in Windows Server, Windows 7, and Microsoft Office Suite
- Ability to effectively interact with customers, support staff, outside vendors and various levels of management
- Demonstrate ability to work in teams in a manner consistent with Company objectives
- Intrusion detection/prevention systems, web application/database firewall systems experience
- Working knowledge of security related technologies and practices, including: authentication and authorization, endpoint protection, encryption, segmentation strategies, vulnerability management, secure remote access, and firewalls
- Holds one of the following certifications: CISSP, CISM, EnCE, GCIH, GCIA, GREM, GCFA, GPEN, SSCP, CCFP, or equivalent
- Experience with regulatory compliance issues such as: FFIEC, OFCC, SEC and Federal Reserve plus: SOX, GLBA and PCI
- Provide training and mentorship to lower-level security analysts
- Malware Detection
- Network Monitoring Tools
- Email Security
- Bachelor’s degree in Computer Science or equivalent combination of education and experience required
- GCIA, GCIH required. GCFE, CISSP, Security +, Network +, CEH, RHCA, RHCE, MSA, MCP, or MCSE preferred
- Experience creating Snort signatures required
RIC Palo Alto IT Cyber Security Analyst Resume Examples & Samples
- Research and develop concepts around related Cyber Security incidents reported in industry and research organizations.Lead technology and feature Security projects delivering to internal customers.Development and maintenance of tools (e.g. Fuzzing) for use in internal vehicle penetration testing.Threat Analysis and Risk Assessment tool/modeling against connected vehicle concepts.Development of security specifications and tools as needed for connected vehicle features and testing
- 5+ years of experience in IT, product development, or research with 1-2 years experience in a security related field
- The ideal candidate will have exceptional planning, research and investigative skills, and the ability to work within the framework of security, privacy, usability, and reliability constraints in the automotive environment
- The candidate will contain a working knowledge of industry IT security and controls efforts as well as embedded security tools and processes (ideally automotive)
- We collaborate extensively within Ford and with external partners, thus we require exceptional communication and collaborative skills
- Strong knowledge of Security and Controls, CPMM, Supplier Relationship and Contracts Management Experience
- Strong ability to work independently, work on all aspects of a project, take follow-up on project deliverables, go above and beyond the task at hand
- Ability to develop and maintain technical documentation as required for projects at hand
- Ability to influence teams towards a desired outcome with varying degree of authority requiring strong facilitation, active listening, and team-building skills
- General understanding of CAN network, firewalls and primary/secondary bootloader architecture within microcontrollers
- Knowledge with cryptographic algorithms and protocols
- Knowledge with PKI management
- Knowledge of industry standard security protocols, tools, processes
- Experience with Secure Coding Techniques
- Experience with embedded hardware and software and coding experience with one or more platforms (see below)
- Knowledge of digital communication and familiarity with communication technologies such as TCP/IP, Ethernet, Bluetooth, WiFi, DSRC and CAN
- Mobile web/in-vehicle application development
- Embedded experience (Windows/QNX/Linux/Microcontroller) is a plus
- Strong programming experience (C/C++/CS/Python/Lua/Qt)
- Azure Cloud Security, general Web services / object oriented development experience are a plus ( C++, CS, Qt, Lua, Perl/Python )
- Knowledge with common programming frameworks such as .NET, Android SDK, and/or iOS SDK
- Familiarity with in-vehicle network architecture, modules, and protocols (CAN etc.) are a plus
- Electrical or System Engineering background will be a plus for module-related work, but not required
- Mobile Phone Application Programming, Bluetooth, Networking familiarity a plus, but not required
- Penetration testing and tools experience is a plus
- PKI experience on medium to large deployments is a plus
- 5 years of Security Analysis (SOC) experience with significant previous Information Technology experience with network technologies, specifically TCP/IP, and related network tools is required
- Knowledge of common network tools (e.g., ping, traceroute, nslookup)
- Knowledge of Windows command line (e.g., ipconfig, netstat, dir, nbtstat)
- Comprehensive knowledge of network design, defense-in-depth principles and network security architecture
- Experience in host forensics
- 3-5 years of IT experience
- 1-3 years of security-related experience
- Ability to analyze raw PCAP data to validate security events, interpret network traffic, and extract indicators
- Knowledge of common attacker tools, malware families, and known attacker group TTPs
- Ability to write tools and automate tasks in scripting languages such as Python
- Experience hunting for unknown threats, as well as tracking existing campaigns and adversaries to see how they evolve over time
- Experience writing snort/suricata/YARA signatures
- Monitor for intrusions and insider threats
- Determine severity and impact of Cyber Threat scenarios
- Perform second-level analysis, remediation and escalations
- Assist engineers in developing cyber defense tools and procedures
- Identify and model new threat scenarios
- Support investigations of wrong doing by internal or contracted staff
- Flexibility for possible after hours escalations from our first tier Cyber Security Operations Center
- Possible participation in the ongoing development and enhancement of our Insider Threat Program and security metrics program
- Collaborate directly with peers outside of security team to resolve urgent matters in a constructive and thoughtful manner
- 3+ years experience within a Security Operations Center (SOC) resolving events related to malicious intrusion, data loss and/or user behavior anomalies
- Knowledge of malware propagation, behavior, and how machines get infected
- Strong technical understanding of
Senior SOC Cyber Security Analyst Resume Examples & Samples
- Comprehensive Knowledge of TCP/IP, IPv6, UNIX, Windows, HTTP
- Ability to conduct packet analysis and decode
- Knowledge of intrusion detection methodologies and techniques for detecting host and network-based intrusions via intrusion detection technologies
- Monitor individual workstations and laptop activity to identify any attacker or event that violates current policy. Document all activity violating policy, assign criticality and escalate to the end user based on the severity of the occurrence
- Identify new vulnerabilities in TCF’s environment using internal assessments defined by TCF policy. Deliver incident reports documenting the new vulnerabilities weekly to the appropriate avenues based on severity
- Update TCF employees’ outdated antivirus versions, and monitor the aging of antivirus definitions on TCF network endpoints
- 2 year college degree or equivalent industry experience
- 1 year of experience either working in IT Security or Information Technology
- Familiarity with network security applications, protocols, and associated hardware
- Monitors global NIDS, Firewall, and log correlation tools for potential threats
- Initiates escalation procedure to counteract potential threats/vulnerabilities
- Highly proficient in intrusion analysis and incident response
- Ability to handle high-pressure situations in a productive and professional manner
- Strong time management, skills with the ability to multitask
- Packet and log analysis
- General knowledge and experience and expertise with ethical hacking, firewall and intrusion detection/prevention technologies, secure coding practices, and threat modeling
- Web Security Gateway
- 1+ year of previous Cyber Security experience
- Working knowledge of Sharepoint
- Investment Bank / Compliance / Regulatory Reporting background
- Evaluating assigned IT areas for cyber security risks
- Identify risk areas and work with team for possible resolutions
- Implement and test safeguards implemented to ensure functioning as designed
- Report to top management findings and new design requirements
- Degree in technical field
- Experience with large data platforms
- Minimum of 3 years experience in network information security coupled with mobile applications
- Certifications in IT Security a major plus
Lead Cyber Security Analyst Resume Examples & Samples
- Assist program sponsor in planning the delivery of the overall program and its supporting strategic projects and run initiatives to achieve program strategic goals and demonstrated success against goals
- Assist in the definition of projects scope and objectives, involving all relevant stakeholders and ensuring technical feasibility
- Providing subject matter expertise to the supporting program team and program sponsor to support the success of project/initiative delivery against established scope
- Report and escalate to executive management by forming supportive relationships to ensure ongoing visibility of project success and progression toward strategic goals
- Facilitate development of new initiatives to support the strategic direction of the program and establish support through the project budget planning cycle
- Provide technical subject matter expertise to support the execution of the program portfolio of projects
- Provide support to Cybersecurity Program Management Office and Strategy team to connect overall Cybersecurity strategy, service management and Program Management while fostering an environment of continuous improvement
- Bachelor’s Degree or equivalent in computer science, management information systems or equivalent discipline from an accredited college or university required
- Minimum 5-7 years’ of overall experience in Information Technology
- Minimum 5-7 years’ experience in IT Risk Management, Information
- Minimum 3 years’ experience with Cyber security SIEM tools
- Security Consulting, Information Security
- Demonstrated experience in understanding of Cyber Analytics in support of Cybersecurity programs such as Insider Threat/Cyber Investigations/Identity & Access Management
- Working knowledge and understanding of project management processes
- Proven success in leading project/programs driving execution based on strategic direction
- Master’s Degree or equivalent in computer science, management information systems or equivalent discipline from an accredited college or university
- Strong process orientation and understanding of technology and financial services
- Proficient use of data analytics tools
- Monitor individual workstations and laptop activity to identify any attacker or event that violates current policy. Document all activity violating policy, and assign criticality based on the severity of the occurrence
- Identify new vulnerabilities in TCF’s environment using internal assessments and industry standards. Deliver incident reports documenting the new vulnerabilities weekly to the appropriate avenues based on severity
- Monitor the TCF enterprise network for malicious activity through the Endpoint Protection tool. Identify any trends in malicious network behavior, such as an increase in attacks or a new virus emerging. Utilize daily automatic reports and create manual reports to send to the appropriate management team
- Complete analysis of reported vulnerability data on a daily basis using internal tools and vendor partner tools. Monitor data for cyber attacks on TCF’s network
- Document and investigate more complex Security incidents as defined by TCF policy. Escalate incident reports to IT management in order to maintain compliance with security related regulatory requirements
- Maintain current knowledge of industry best practices and regulations such as Community Emergency Response Teams (CERT) and SysAdmin, Audit, Network and Security (SANS)
- 4 year college degree or equivalent industry experience
- 2-3 years of experience either working in IT Security or Information Technology
- Experience or knowledge of how to conduct intelligence analysis
- Excellent written and verbal communication skills, with an emphasis on relationship building
- Scoping of penetration tests, use cases, and timing
- Development of ‘rules of engagement’ with partners
- Performing ethical hacking tests within explicit bounds
- Capture test findings, communicate repeatable process steps
- Develop and communicate recommendations on findings remediation
- Creation of testing reports and delivery of results to management
- Continuous improvement of testing processes and methodologies
- Coordinate and function as an SME to third-party penetration testing efforts, as needed
- Bachelor’s Degree in Computer Science or other field of study
- 2+ years of penetration testing experience
- Master's Degree in Computer Science
- 1-5+ years of experience and knowledge of ISO27001
- CEH - Certified Ethical Hacker Certification
- Deep experience in IP based networking
- Strong encryption background
- Broad Operating System knowledge
- Previous Security Experience with Cellular Carriers
- Demonstrable Threat Modeling experience
- This role will span both traditional IP based infrastructure as well as in-vehicle technologies - working knowledge of vehicle-based security protocols is a big plus
- CISSP - Certification
Senior Information & Cyber Security Analyst Resume Examples & Samples
- Establish, implement, monitor, review and improve a suitable set of controls for the prevention of threats to the security of our information assets, ensuring the business objectives of the organization
- Act as security relationship manager to our Digital Technology team. Providing them support, advice and direction related to the security of our digital assets
- Assist with the operation of controls operated by information security
- Ensure all staff are: able to identify and respond to threats, aware of the threats we face and practiced in responding to cyber events
- Oversees one of the BCIS workstreams. The Information and Cyber Security Analyst will be expected to lead one workstream and participate in all facets of the BCIS programme
- Assist with the gathering and dissemination of security intelligence
- Assist with the development and testing of effective IT recovery plans ensuring the availability of critical applications
- Assist with the development and testing of effective business continuity plans
- Assist with the development and testing of crisis management plans
- Participate in and / or lead as required incident response, from discovery through to recovery, lessons learned and remediation
- Analyze IT infrastructure and operations and help to design controls to ensure the security of corporate information assets
- Help business units understand and establish acceptable levels of risk, reducing the potential for incidents that pose security threats
- Help business application teams integrate sound security components into their systems
- Protect data privacy and information integrity in response to business needs and compliance requirements
- University degree (or equivalent). Math, science or computer science preferred
- Proven experience in an information security role
- Excellent, demonstrable, customer service skills
- Excellent communication (spoken and written) and interpersonal skills
- Good influencing skills. Able to deal with all levels of the organization
- Able to take the initiative. Positive ‘can do’ attitude and a determination to succeed
- Diligent, able to work to deadlines while managing multiple priorities
- Inquisitive, able to solve problems and come up with solutions
- Curious, innovative, willing to challenge conventional approaches and test new ones
- Managing and performing on teams that conduct analyses related to forensic investigations, cybercrimes, and/or cyberattacks; and supporting various and dynamic security analysis needs of the team
- Analyzing security logs, monitoring logs, firewall logs, intrusion prevention system logs, and network- and core-related logs
- Analyzing and developing baselines for all related risks from Security Analytics and/or other log management tools, emphasizing security analysis of critical system logs and network protocols
- Managing analyses of logs, traffic flows etc. to identify malicious activity, design rules that trigger response to malicious activity, analyzing the findings on malicious activity and preparing reports; developing response procedures for addressing potential security threats and driving the on-boarding of new logs into Security Analytics
- Utilizing cyber forensics knowledge to analyze and draft findings, articulating this information to various internal and external audiences and levels
- Utilizing Netwitness and security analytics, including Security Information and Event Management (SIEM) products such as Q1Labs, ArcSight, and Nitro
- Conducting analyses of evidence of network penetrations and data theft using firewalls, active directory, Windows operating systems, intrusion detection/prevention systems, proxy servers, breach indicators, and log aggregation technology
- Utilizing creative problem-solving and written and oral communication skills to articulate, explain, and deliver technical concepts and issues to non-technical business leadership; researching pertinent technical matters with an attention to detail, and innovating new solutions and processes, incorporating new technologies, when warranted
- Exhibiting capabilities to multitask, perform and deliver results as both part of a team and independently
- Adapting to ever-changing schedules and work assignments, including the ability and willingness to work extended hours and conduct business travel domestically and/or globally; and,
- Willingness and motivation in taking the initiative for individual and team professional growth and development
- Network Analysis, Host Forensics Analysis, Malware Analysis
- SIEM Experience
- Use of threat intelligence sources
- Experience with Forensics toold (enCase, MIR, CarbonBlack etc.)
- Splunk experience (OR other big data platforms)
- Scripting/software development skills
- Working knowledge of common intrusion analysis models
- Formal incident response efforts - coordinated responses to major intrusions or exploits
- Provide consistent and repeatable methods to resolve security incidents
- Allow management to envision additional threats and incorporate improvement activities
- Daily analysis of multiple data sources (host and network activity) with the ability to determine if a threat applies to Ford or not
- 2+ years’ professional experience in an IT related field
- 3+ years’ experience with infrastructure development or operations
- Experience with reviewing system language log files, data correlation, and analysis (i.e. firewall, network flow, IDS, system logs)
- In depth knowledge of servers, clients, various computer peripherals, network and/or Storage technologies
- Strong deductive reasoning, critical thinking, problem solving, and prioritization skills
- Customer service including the resolution of escalations, incident handling, and response
- Experience in a fast paced, high stress, support environment, able to work with a sense of urgency and pay attention to detail
- Coordinate and perform security testing activities (penetration testing, vulnerability scanning, application security testing), report on results, track metrics & trends, and drive remediation
- Coordinate and perform proactive security monitoring, event analysis, incident response, and trending
- Participate in and respond to internal and 3rd-party security audit & assessment activities
- Engage in security architecture reviews
- Design & implement new security solutions & projects
- Assist with contingency planning and disaster recover processes
- Maintain security policies & procedures
- Assess adherence to security requirements and manage exceptions & mitigations
- Provide on-the-job security education & training for junior security team members
- Create and maintain software security resources for the software engineering team
- Develop and enhance security awareness training for employees and contractors
- Prepare quarterly briefings for the Information Security Steering Committee and track the progress on actions coming out of the meetings
- Develop and maintain IMS strategy & roadmaps to address risk landscape
- Develop and manage portfolio of IM&S projects. Ensure the right strategic investments are made. Drive the execution of IM&S projects through the assigned project managers
- Broad Information Security experience
- Experience developing and implementing security strategies and security patterns
- Depth and breadth across all the core bodies of information security knowledge including threat, vulnerability, risk, and controls
- Excellent English oral and written communication skills
- Experience in working in a global, multinational organisation
- CISSP, ISSAP, or SABSA certification
- Broad foundation of on the job IT technical knowledge
- Having Bachelors degree in any discipline
- Demonstrated manual product penetration testing experience; for example, you must be able to simulate a SQL injection without tools, simulate XSS attack, X-Path Injection, etc
- Knowledge on domain understanding about the HVAC / Fire control systems, controllers, field instruments, cameras, industrial networks, sensors etc
- Having 3+ years of hands-on experience on Data Classification, Encryption & IRM technologies
- Good Understanding of Data Classification Standards & Technology such as Boldon James
- Good knowledge on NIST and other industry standards
- Good knowledge on Networking and Linux, Basic Knowledge on Active directory and LDAP
- Ability to write scripts either in Python or Perl
- Good knowledge on server maintenance activities
- Basic knowledge on Windows, NetApp filer and SharePoint technologies
- Knowledge on Information Security fundamentals is added advantage
- Technical lead for the Behavior Analytics platform for the entire company and accountable for the availability, reliability and performance of the platform
- Collaborate with IT infrastructure/Application teams and business security leaders to define and gather Analytics requirements
- Consolidate and validate business assumptions relevant to the solution strategy, prior to initiating and throughout the analytical process
- Identify and gather the relevant and quality data sources required to fully answer and address the problem for the recommended strategy
- Integrate/transform disparate data sources and determine the appropriate data hygiene techniques to apply
- Understand the company’s IT Infrastructure/Applications, Business model/processes, Security controls and develop Threat Detection Models within the Behavior Analytics platform
- Define the global and business level metrics reporting dashboard
- Having 5+ years of hands-on experience on UEBA Domain ( Securonix)
- Ability to write scripts SQL and good knowledge on DBA administration tasks
- Hands-on experience on Linux or UNIX platform
- Hands-on experience on McAfee or Symantec DLP events analysis
- Strong knowledge on server administrator tasks
- Good knowledge on HR and proxy systems
- Good in troubleshooting data integration issues
- Hands-on experience on Building threat model with various transmission channels like USB, Email etc
- Proven team player, will be working individually and with other staff members, on both long-term projects and rapid response under tight deadlines
- Ability to work with local and remote IT staff/management, vendors and consultants
- Ability to work independently and possess strong project management skills
- Demonstrated proficiency in
- Implementation and maintenance of SIEM (ArcSight, IBM Qradar, McAfee NitroSecurity, etc.)
- Forensic analysis tools (MIR, EnCase, FTK)
- Malware analysis tools (dynamic and static)
- Vulnerability assessment tools (Qualys, ISS Scanner, nmap, etc.)
- Secure Web Gateway (BlueCoat, Microsoft Forefront)
- Network sniffers and packet tracing tools (DSS, NAI SnifferPro, Ethereal and tcpdump)
- Encryption technologies (PGP, PKI and X.509)
- Directory services, LDAP, and their inherent security (Active Directory, CA Directory)
- Proxy and caching services
- Client/server platforms including Sun Solaris, Windows, Linux
- Operating system hardening procedures (Solaris, Linux, Windows, etc.)
- LAN/WAN routing and high availability (OSPF, BGP4/iBGP, EIGRP and NSRP)
- Bachelor’s degree in Computer Science, Engineering, or other related field
- Minimum five years of information security experience, preferably in the financial services industry
- Minimum three years hands-on security operations experience including interdisciplinary experience with four or more of the following: Cyber Threat Analysis, Digital Computer Forensics, Incident Response, Application Security, Operating Systems Security, Cryptographic Controls, Networking, Programming languages
- Technical experience and comprehensive knowledge of threat actor capabilities, intentions, methodologies and motives
- Familiarity with computer network exploitation and network attack methodologies while maintaining an understanding of the relationship these activities have with the financial services industry and critical infrastructure
- Industry knowledge of leading-edge security technologies and methods
- Shift work and working in an on-call response capacity is required including availability for 24 x 7 on-call support responsibilities
- Previous people/project management experience is a plus
- Government Security Clearance is a plus
- Strongly prefer at least one of the following certifications: CISSP, GCIA, GCIH, CHFI, GCFA, CCE, CFE
- Monitor information system activity, collect, review, and retain audit logs to include system logs and records and determine actions to be taken when discrepancies are detected
- Performs analyses to validate established security processes and recommend additional security steps to ensure compliance with applicable DOD IA requirements and baseline IA controls
- Conduct network security vulnerability assessments using DoD provided scanning tools and liaison with network administrators to correct identified problems
- Review Information Assurance Vulnerability Alerts (IAVA) for applicability and impact to the range networks. Ensure that all systems are patched and report compliance
- Evaluate information systems for compliance with Defense Information Security Agency (DISA) Security Technical Implementation Guideline (STIG) and review measures needed to bring systems into compliance
- Conduct vulnerability scanning for new information system deployment or systems temporary connected to support training events or testing
- Verify all Virus Signatures are kept up to date, and Automated and Manual Virus Scans are documented, scheduled and are being completed
- Assist in evaluation of Information Systems for compliance with Government statutes, DoD 8500.2 IA Controls, DoD FISMA directives, policies and regulations
- Information System Security
- Risk Analysts
- Network Security Auditing
- Host Based Security System (HBSS) Administration
- Assured Compliance Assessment Solution (ACAS) Administration
- VMware Administration
- DoD Certification and Accreditation
- Provide administrative support for the DoD Information Assurance Certification and Accreditation Process (DIACAP)
- Maintain system accreditation status in Enterprise Mission Assurance Support Service (eMASS) by performing quarterly updates and updating documentation
- Review DISA Application Security and Development Security Technical Implementation Guide (STIG) checklist items and perform remediation/mitigation activities as required
- Support Cyber Security Inspections three times a year
- Conduct annual contingency plan and disaster recovery reviews for specific systems
- Report activities on a Monthly Status Report
- Bachelor's degree or four (4) years of additional experience in lieu of degree
- Previous experience supporting the Department of Defense is preferred
- Three (3) years of experience with Department of Defense Information Assurance Certification and Accreditation Process (DIACAP) Certification and Accreditation packages, reviewing, interpreting, identifying and resolving (remediation/mitigation) Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIG) checklist items
- Three (3) years of experience with DISA Security Content Automation Protocol (SCAP) Content program and SCAP benchmarks and DISA STIG viewer
- Three (3) years of experience with securing and configuring Windows Server 2008 operating system and related products (SQL Server, Internet Information Services, Active Directory, etc.)
- One (1) year of experience managing packages with the Enterprise Mission Assurance Support Service (eMASS) system
- Experience with Department of Defense Information Assurance Risk Management Framework Assessment and Authorization Process (RMF) packages
- Develop, write, and review certification and accreditation (C&A) documentation per Department of Defense (DoD), Risk Management Framework (RMF) for DoD Information Technology (IT) (formerly DIACAP)
- Perform the duties of Navy Validator for all NNSY accreditation submissions and assist other Naval Shipyards and the corporation on these duties when required
- Evaluate and test information systems and networks to determine compliance with CS requirements
- Conduct evaluation, test, and accredit various Industrial Plant Equipment (IPE) that contain computer technology to ensure full compliance with Navy and DoD requirements
- Assist with office clerical work; assist users with Cyber Security (CS) related issues, and provide other CS support as the need arises (e.g., auditing, contingency planning, CS awareness training,
- Bachelor’s Degree in Cyber Security, Information Technology or related field and a minimum of three (3) years direct experience in the IT field
- Institutional knowledge and a minimum of 3 years’ experience, on the mission critical procedures, systems, and processes, as they pertain to the Public Naval Shipyards’ Information Technology and Cyber Security requirements
- Qualified and registered as a Navy Validator IAW DoN Memorandum 5239, Ser 5.0/1274 dated 18 Mar 10, Subj: QUALIFICATION STANDARDS AND REGISTRATION PROCEDURES FOR NAVY VALIDATORS
- Experience in certifying and accrediting DON information systems and networks, as well as Platform IT
- Expert knowledge of and experience with CS requirements as defined by Public Laws, National, DoD, and DON guidance [e.g., Federal Information Security Management Act (FISMA), DoDD 8500.1, DoDI 8500.2, DoDI 8510.01 (Risk Management Framework (RMF) for DoD Information Technology (IT)), DODINST 8570/01M INFORMATION ASSURANCE WORKFORCE IMPROVEMENT PROGRAM. SECNAVINST 5239.3, OPNAVINST 5239.1, NIST Special Publications Series 800, etc
- Expert knowledge and experience with the requirements outlined in OPNAVINST N9210.3 Safeguarding Naval Nuclear Propulsion Information
- Ability to move and maneuver up to 50 pounds of weight (computer hardware, accessories, support equipment, etc.)
- Serve as an individual on the Cyber Security Team
- Develop Cyber Security documentation validating software quality, security, reliability and maintainability attributes. Identify gaps in Cyber Security/CND posture and assess risks
- Participate in development and review of DIACAP/RMF documentation, Networthiness Documentation, and ensure STIG compliance and validation
- Provide quality assurance specialist support including formulating, coordinating, directing, and executing all quality assurance policies, tools, and training programs; conducting internal controls reviews to ensure product assurance competency and the effectiveness of surveillance activities
- Develop strategies, goals, tasks, roles, responsibilities, and information needs for Cyber Security surveillance and oversight
- Review information systems for compliance with applicable DoDI 8500.01 and DoDI 8510.01
- Provide IS security advice and guidance in accordance with applicable regulations, and directives and guidance to Government and DoD partners for the protection of data at all classification levels including SCI
- Evaluate and recommend approval, disapproval, or waiver(s) for IS processing national security data
- Provide input or consideration in the promulgation of future security policy
- Support and/or conduct site visits and assessments to inspect and verify IS reports and plans at various locations, and provide a written report for review and approval
- Prepare reports and memoranda, to include, but not limited to: Memoranda for the Record (MFR), Memoranda of Agreement (MOA), Authorization To Proceed, and status and technical briefs for review and approval by government Cyber Security
- Update data on Government-provided databases with current information about IS status
- Prepare, review, and record notification and status messages to indicate A&A state of systems to system owner or programs
- Ensure IS security requirements, including applicable RMF directives and guidance, are addressed and applied; appropriate documentation prepared by the system owners or programs inclusive of the Security Assessment Package, Concept of Operations (CONOPS) Plan, System Security Plans, System Requirements Traceability Matrix, Risk Management Matrix, Test Results, interface control documents, requests for changes, test plans, and other related program security documentation
- Track completion of the Security Assessment Package and report status
- Provide preparation of the Security Assessment Report (SAR). The SAR contents include, but not limited to, the Summary of Assessment results and Authorization Recommendation
- Bachelor's degree preferably in a Technical Computer Field (Computer Science, Management Information Systems, Information Technology, Networking). 8 years applicable experience may be considered in lieu of degree
- Experience with XACTA, DIACAP, Risk Management Framework (RMF), NIST, eMASS, SCAP Scanning, IAVA’s methodologies, STIG’s and ACAS
- · - Minimum 5 years data/network/information system assurance and system design, information security assessments, C&A, Plan of Action Milestones (PoAM) remediation, Information Assurance Vulnerability Alerts
- Experience performing Information Assurance functions in a Capability Maturity Model Integration (CMMI) Maturity Level 3 (or better)
- Required Certifications: Currently possess DoD 8570 certification, Security +
- In depth knowledge of Information Assurance auditing, continuous monitoring, and analysis
- Possesses strong analytical skills and good interpersonal and communications skills in dealing with multiple contractor and government organizations
- Must currently possess TS/SCI
- NSA Information Assurance Guidelines
- Certifications: CompTIA Security +, CISSP, CEH, GSEC, GCIH, CISA, GCED, SSCP, and/or CISA
- Familiar with multiple operating systems including Linux and Windows
- Virtualization experience with technologies such as KVM and VMWare VSphere
- Minimum Certification as a DoD 8570 IAM II, must possess or able to obtain from hire date, within 6 months IAT Level II certification related to the Information Assurance field
- Demonstrated exceptional ability to troubleshoot complex systems required
- 5 years IT experience
- 2+ years administrating servers
- 4+ years with vulnerability scanners
- Knowledge and experience in working with ACAS
- Knowledge and experience in working with NESSUS Scanner
- HBSS APS working knowledge
- Support Risk Management Framework
- Upload information, documentation, and artifacts into the eMASS application for Army tracking of RMF compliance
- Coordinate with IASOs, IMOs, and system owners to establish POA&Ms
- Track POA&M progress and coordinate with IASOs for updates
- Develop routine POA&M approval package and brief the Authorizing Official Representative
- Develop and track Privacy Impact Assessments
- Develop and track System Interconnection Agreements
- Routinely Review System Security Plans
- Routinely Review System Standard Operating Procedures
- Maintain FISMA Compliance Reporting
- Perform routine FISMA Technical Control Reviews
- Document findings and coordinate with owners to establish POA&Ms
- Perform routine FISMA Continuity of Operations Reviews
- Perform routine FISMA Security Control Reviews
- Participate in annual Information Technology Continuity Planning
- Per new RMF standards, support more frequent external 3rd party assessments required for Army Assessment and Authorization Official Representative
- Perform physical security inspections Minimum Qualifications
- Must possess at least 5 years of hands on technical experience with a minimum of 4 year of experience in Information Assurance or a Master’s degree and 3 years’ experience
- Must be able to work independently and provide timely status updates, as well as be able to manage multiple tasks
- Must be a highly effective communicator (both verbal and written) and possess excellent analytical and problem-solving skills
Cyber Security Analyst Intern Resume Examples & Samples
- Pursuing bachelor's degree, preferably in Computer Science, Cyber Security, Information Technology, Computer Engineering, or related IT discipline
- Strong technical skills including understanding of software development principles
- Hands-on experience through coursework or internship
- Ability and obtain and maintain a SECRET Security Clearance
- Willing to live and work in the Charleston, SC area
- Computer based training system development
- Ability to quickly adapt to a changing environment
- Ability to quickly learn new concepts and software is necessary
- Candidate should be a self-motivated, independent, detail oriented, responsible
- Ability to multi-task& support multiple priorities
- Ability to handle multiple clients and multiple team members with confidence
- Maintain DIACAP/RMF IA controls so that security posture remains high
- Participate in the Cyber Security Working Integrated Product Team (WIPT) and provide updates
- Conduct verification tests for system upgrades to maintain the high security posture
- Create ATO POA&M entries for items (such as patches) that will take additional time to research to prevent potential negative effects by testing changes to the environment prior to implementation. The IA analysts will work with the System Administrators and Database Administrators (DBAs) to develop a remediation plan, including a schedule, mitigation strategy, and details to enable the IAM and AO to understand the risk
- Support Cyber Security auditing, continuous monitoring and analysis
- Scan the environment with vulnerability assessment tools such as ACAS/Nessus
- Prepare Cyber Threat Analysis, POAMs, and IAVM reports
- Bachelors degree or equivalent experience (4 years) and 5 years or more experience
Information Cyber Security Analyst Resume Examples & Samples
- Performs routine to moderately complex cybersecurity incident analysis including technical investigations, evidence gathering, log events analysis, stakeholders' interviews and threat mitigation
- Monitors systems to identify and respond to anomalous activity such as worms, Trojans, viruses, and malware. Investigates ongoing internal and external vulnerability assessments for the purpose of identifying vulnerability trends and makes recommendations to address issues
- Utilizes ticketing system to ensure that logged incidents and/or requests are resolved in a timely fashion
- Performs research to identify and report on the intentions and capabilities of external threat actors
- Performs cybersecurity-related risk assessments and communicates results Information/Cyber Security Manager
- Keeps current and maintains an understanding of industry threats, vulnerability landscape and applicable exploits
- Conducts research on emerging products, services, protocols, and standards in support of cyber security enhancement and development efforts
- Performs special projects and additional duties and responsibilities as required. Where applicable and when performing the responsibilities of the job, employees are accountable to maintain Sarbanes-Oxley compliance and adhere to internal control policies and procedures
- Thorough knowledge and understanding of information security systems and appliances
- Knowledge and experience supporting, reviewing, or administrating security technologies such as IDS/IPS, log aggregators, Internet and email filters, and next generation threat prevention platforms
- Experience with system vulnerability scanning tools and ability to analyze associated scan results
- Experience with administration of application whitelisting systems is preferred. Working knowledge of current attack methodologies, such as man-in-the middle, sniffing, phishing/vishing, cross site scripting, SQL injection and DDoS; as well as monitoring methods used to identify and respond to anomalous activity such as worms, trojans, virus', and malware
- Strong analytical and troubleshooting skills. Strong written and verbal communication, interpersonal, and organizational skills
- Ability to work both independently with sole responsibility and as part of a team to deliver high quality work product in a fast-paced environment
- Ability to multi-task, prioritize projects, and exercise strong professional judgment. Ability to work well with people from different disciplines with varying degrees of technical experience
- Develop Risk Management asset protection framework and asset classification processes that enable mitigation of risk to HP’s most critical assets & ecosystems. To include issue/gap management framework, including supporting processes and procedures
- Provide consultative advice to internal customers that enables them to make informed risk decisions and develop acceptable risk mitigation strategies
- Generate succinct and actionable reporting to Risk Owners that provides a current status on all open issues, including remediation plans or exception requests
- Conduct periodic touch bases with GRC and Business Unit Sr. Leadership risk owners to ensure accountability and visibility of all open issues and to verify progress is being made towards previously committed remediation plans
- Communicate information security risk and compliance assessments (e.g., vulnerability scans, penetration tests, PCI DSS, risk assessments, etc.) results to management, both verbally and in writing
- Gather documentation and technical information in support of issue remediation efforts and audit requests
- Work with GRC Team to enhance or streamline existing eGRC tool, issue management, & risk register workflows as appropriate
- As the Sr. GRC Analyst & leading be example, must keep abreast of latest security and privacy legislation, regulatory, advisories, alerts, and vulnerabilities
- 5 years of Information Security, Cyber Security, &/or GRC related experience required
- Excellent prioritization and multitasking capabilities
- Experience in developing processes and technology standards Ability to train and mentor staff
- Exceptional attention to detail and strong focus on quality
- High knowledge of or exposure to ANZ teams and systems
- Experience in IT Security tools
- Basic Regex Coding Skillset
- Execute (thru providers) pen-testing on our products
- Understand and prioritize security findings and risks
- Work with upper management, architecture and engineering teams on resolution
- Advanced understanding of access control (Identity, provisioning, authentication, authorization)
- Advanced understanding of security monitoring (logging, error and exception handling as part of application lifecycle)
- Advanced understanding of operational security, e.g., security of hosting environments (firewalls, Intrusion Detection Systems), key management, key revocation, rotation
- Experience in interaction with pen testing providers in order to identify the risk associated to security findings. Basic understanding of pen testing and related frameworks
- Experience with the definition of security policies (e.g., input validation, hosted services configuration) and implementing good security practices
- Basic understanding of automated security testing frameworks (e.g., fuzz testing)
- Lead efforts in intrusion detection, malware analysis, and APT analysis
- Design and execute remediation efforts within the "Response" phase of cyber incident lifecycle across functions, business units and regions
- Continuously engage intelligence team in a two way conversation: Develop, refine, and maintain intelligence requirements to focus intelligence in support of detection operations, and provide feedback on detection indicators and intruder tactics, techniques, and procedures
- Mentor and provide direction to junior analysts, conduct additional triage on escalations from those analysts
- Conduct forensic investigations of internal or external threats based on a working knowledge of IT environments including: Microsoft Windows, Apple MAC, Linux, mobile devices and infrastructure components such as firewall technology, Active Directory, and operational log and event console activity
- Champion use of processes, standards, governance, and disciplined execution
- Evaluate and use advanced IR products and services to improve efficiency and effectiveness of incident response
- Lead projects to enhance CSIRT capabilities up to region or sector level
- Analyze and reverse engineer malware
- High School Diploma or GED from an accredited institution is required
- Minimum 5 years of experience in cyber security incident response, security operations, or a graduate of Eaton's Leadership Development Program is required
- Must reside within a 50 mile radius of work location or work remotely; no relocation benefit offered
- Bachelor’s or Master’s degree in a technical discipline such as: B.E / BTech / MCA / Equivalent (EITC) or B.S. Comp Science / Mathematics / Engineering / Equivalent
- Excellent proficiency with the English language (written and verbal). Additional language capabilities are a plus
- 10 years of IT experience in information technology
- Deep understanding of multiple Information Security disciplines with relevant work experience and/or relevant certifications (e.g. GCIH, CSIH, GREM, etc.)
- Deep understanding of common threats, penetration/intrusion techniques and attack vectors
- 3 years of experience with security technologies (e.g. IPS, IDS, SIEM, DNS, proxies) and detection techniques (e.g. forensics, malware analysis, packet analysis)
- 3 years of experience in correlating events from multiple sources to detect suspicious and/or malicious activity
- 3 years of application development and secure programming techniques
- 3 years of solution design and architecture
- 3 years of experience in internet technology and remote access control systems
- Previous experience as an IT Security Analyst or related field as typically acquired during 6 to 8 years in a similar position
- Three to five (3 to 5) years of healthcare information technology industry experience preferred
- Previous experience providing cyber security support by planning, coordinating, integrating and synchronizing cyber defense and prevention activities
- Proven experience ensuring compliance with all applicable state and federal cyber laws and regulations
- Significant experience creating comprehensive and accurate reports that are used to communicate Sutter Health’s risk profile impact to peers and management
- Thorough knowledge of information systems security concepts and current information security trends and practices including security processes and methods
- General knowledge of Federal and State IS security and privacy-related regulatory requirements and laws
- In depth knowledge regarding NIST, HIPAA, FIPS, and other recognized industry security standards and best practices
- Detailed understanding of DLP and DLP technologies
- Detailed understanding of data movement in a large healthcare system and typical healthcare business processes
- In depth knowledge of cyber security solutions, policies and technologies
- Understanding of the lifecycle of a network threat and network vulnerability exploitation in a healthcare environment
- Minimum of 10 years of work related experience required
- Prior work experience specifically-related to Cybersecurity/IA with demonstrated understanding of applicable DoD Cybersecurity/IA guidelines, instructions, and directives is required
- A Secret Security clearance is required
- Program management experience is required
- Prior supervisory, task management, technical management, or project leadership experience in the areas of Cybersecurity/IA
- A thorough understanding of cyber stakeholders and the process/procedures for integration
- Ability to develop briefings and present them to high level officials
Cyber Security Analyst, FCC Resume Examples & Samples
- Three (3)+ years in the IT field
- Security+, CISSP, GWAPT, GPEN, GCIH, CISM/CISA is a plus! ISO27001 Lead Auditor is also a plus
- Support the development of risk evaluation criteria; prioritize the risk register that identifies trends; communicate common view of the categories of security risk
- Assist in implementation of new security solutions
- Conduct and participate in vulnerability audits and assessments
- Monitor NASA agency sensors and SOC (Security Operations Center) systems for incidents and malicious activity
- Generate high quality reports
- Coordinate with both Tier 1 and Tier 3 teams while providing incident handling and response support for the agency
- BS degree in relevant field/technology or equivalent years of experience
- Experience reviewing and analyzing large amounts of raw log data (firewall, network flows, IDS, system logs),
- Track record of being motivated to learn and thrive on challenges
- Commitment to Excellence; Thirst for Knowledge
- Experience working in a mission critical security operations team, preferably 24x7
- Experience with enterprise level security incident event management tools such as ArcSight or Splunk
- CEH, Security+, GCIA are desired certifications
Cyber Security Analyst, Lead Resume Examples & Samples
- 10+ years of experience with information assurance or Cybersecurity, including 3 of the following areas: systems requirements, operational requirements, test and evaluation, or training
- 3+ years of experience in a technical security role, including network security, operating system security, Internet or Web security, Data Loss Prevention (DLP), anti-malware, IDS/IPS, and penetration and vulnerability testing
- Experience with designing and implementing a Cybersecurity program for a federal agency and documenting and championing technical requirements that result from business processes or organizational change recommendations
- Knowledge of security concepts and security management practices, security architecture, security operations, and security modeling
- Knowledge of Certification and Accreditation (C&A) activities in accordance with the NIST, OMB, and DOE processes
- Ability to analyze the security architecture of IT systems for compliance with federal and agency policies and manage multiple priorities and projects, deliverables, and stakeholders
- Ability to influence peers and management, team cross-functionally, and form relationships to achieve objectives
- 3+ years of experience with the Department of Energy
Senior Cyber Security Analyst CND Tools Data Integration TS Resume Examples & Samples
- 10-15 years of related experience in data security administration
- Must be DoD 8570: IAT III (either CISA; GCIH; GCED; CISSP; CASP) and CND-SP Specialty: CND-IS
- Work location Reston
Weapons & Tactics Cyber Security Analyst Resume Examples & Samples
- IAT Leave II Certification required. Certified Ethical Hacker, Net+, CCNA, and Windows/Linux certifications highly desired
- Must complete self-assessment questionnaire, customer pre-screen, skills assessment lab, and pass the training and certification program(s) as directed by the customer, and remain Mission Ready qualified
- Must have experience working with and in a network systems security environment with a focus on security and information assurance
Intermediate Cyber Security Analyst TS Resume Examples & Samples
- Serves as technical team or task leader
- 10-15 years of directly related experience in network analysis and design
- Requires Relevant Certifications: DoD 8570 IAT III (CASP; CISSP; GCIH; GCED; CISA) and CND-IS (CEH; SSCP)
- Must be willing to obtain & maintain a CI polygraph
Senior Cyber Security Analyst CND Tools Data Integration Lead TS Resume Examples & Samples
- Broad scope of tasks to include O&M and tuning of cyber defense tools, integration of Splunk, Forescout, Fire Eye, Tanium and other tools, security architecture design, implementing new cyber capabilities, implementing regional based IPS, designs and defines system architecture for new or existing computer systems
- Performs functions to include but not limited to systems engineer, audit/inspection, infrastructure support, certification and accreditation, vulnerability management, detection and response support services
- Lead and manage a team of cyber experts
- 10-15 years of related experience in data security administration (5+ years computer network defense and information assurance experience)
- Analyze data communications networks; including planning; designing; evaluating; selecting; and upgrading operating systems and protocol suites and configure Firewalls; IPS/IDS and other defensive capabilities as needed
- Have specialized knowledge in computer network theory and understand IT standards; including but not limited to the OSI model; and the methods of exploiting those standards
- Plan network layouts and configures cyber defense systems to protect the network
- Analyzes network topologies and traffic and capacity requirements
- Serve as Firewall and IPS/IDS engineer
- Have experience with multi-tasking providing on ground support to a critical Security Operations center
- Have excellent oral and written skills creating programmatic documentation; standard operating procedures and granular process checklists
- Conduct special projects by request
- Requires Relevant Certifications: DoD 8570 IAT III (CASP; CISSP; GCIH; GCED; CISA) and CND-IS (CEH; SSCP) 2. Must be willing to obtain & maintain a CI polygraph
AIS / Cyber Security Analyst Resume Examples & Samples
- A.S./A.A or B.A. Degree with ten (10) years of experience in IT disciplines may substitute for the Bachelor's Degree requirement
- Five (5) years of cyber security related experience
- Working level knowledge of DoD cyber security practices/procedure is required
- Three (3) years of specific DIACAP/DIARMF related experience
- Experience in briefing DoD Executive Leadership (0-6/GS-13 and above) a plus
- SME level knowledge current DoN cyber security practices/procedure is highly desirable
- CISSP is highly desirable
- Active TS/SCI
- Bachelor’s degree from an accredited institution and 7 years of direct experience or an additional 4 years of direct relevant technical experience may be substituted for education
- Fully Qualified Navy Validator (FQNV)
- Compliant with DoD 8570.01-M Information Assurance Manager Level III requirements (GSLC, CISA, CISSP)
- Prior experience with NIST 800-53 Controls
- Strong communication, coordination, and collaboration skills
- Hold (or be able to obtain) at least one of the following certifications: Cisco Certified Network Associate (CCNA), Microsoft Certified System Engineer (MCSE), Red Hat Certified Systems Administrator, and/or Oracle Certified Solaris Administrator (OCSA)
- Experience with the Assured Compliance Assessment Solution (ACAS) Solution and Security Compliance Automated Protocol (SCAP) tools
- Experience with Security Technical Implementation Guides (STIG) and associated Checklist
- Experience in completing, submitting, and tracking accreditation packages for Navy Programs of Record (POR), sites, and/or systems
- Prior experience with Risk Management Framework (RMF)
- Incident handling (guiding customers, directing resources through intelligence-based response process)
- Environment monitoring and development of thorough incident reports
- Delivering threat awareness and education briefings
- Maintaining technical proficiency in the use of tools, techniques and countermeasures
- Maintaining professional knowledge of trends in computer and network vulnerabilities and exploits
- Participation in the production of cohesive technical intelligence reports
- Adherence to the highest standards of ethical and professional conduct
- Development of thorough incident reports
- With computer security concepts and best practices
- With networking, system administration and security best practices
- Using Unix/Linux operating systems including command-line tasks and scripting
- Writing formal reports and other technical documentation
- With analyzing and investigating computer network intrusions
- With malware analysis
- With conducting data analysis
- Ability to obtain and maintain appropriate DoD Secret level security clearance
- Current DoD Secret level security clearance
- Experience providing enterprise incident handling support
- Experience researching and tracking Advanced Persistent Threat (APT) campaigns
- Experience performing programming/scripting tasks
- Experience using Digital Forensics techniques and tools (Encase, FTK, File Systems)
- Experience performing forensic analysis tasks (Intrusions and/or Incident response)
- Experience with Cyber Kill Chain and Intelligence Driven Response
- Experience with Reverse Engineering of malware
- SANS GIAC GGCIH/GCFA, or CISSP certification(s)
- Experience mentoring junior level employees
- Effective customer service skills
- Demonstrated experience with networking, system administration, architectures and security elements
- Ability to obtain and maintain appropriate DoD clearance
- Demonstrated excellent customer service and teaming skills
- Malware/ Reverse Engineering experience
- Enterprise incident handling experience
- Forensic analysis experience
- Using the big data toolset Splunk, analyse security incidents for evidence of malicious behaviour . (Training on Splunk provided)
- Carry out analysis to determine the root cause of events, with the support of big data, enterprise wide forensic toolsets and intelligence processes
- Using enterprise wide forensic toolsets, carry out threat hunting activities, looking for trouble. Ingest, analyse and contextualise data and turn that into intelligence for threat assessment and risk management
- Applying scientific and analytical skills, develop big data algorithms for detection and reporting of threats against the organisation and sector
- Reverse engineer malware and malicious code to determine the risk and impact across differing platforms, from enterprise to field equipment, then feed that information back into the architecture for security enhancement
- De-obfuscate code to determine actions of scripts and malware
- Perform protocol analysis for the detection and investigation of command and control traffic
- Analysis packet level data for the detection and analysis of covert exfiltration mechanisms
- Provide advice on configuration of network security devices for service and security enhancement
- Liaise with UK Government agencies for intelligence sharing
- Participate within the Global Thales security community
- Perform vulnerability assessments and penetration tests of systems to determine risk and recommend mitigating actions
- Carry out first responder actions, triaging and containing breaches
- Identify service inadequacies and contribute to the Customer Service Improvement Plan
- Maintain an understanding of current and emerging threats and vulnerabilities and security technology developments
- Candidate will need to become familiar with, adhere to and ensure implementation of all Thales security policies and standards and the change control environment
- Support client facing / end user helpdesk and other IT Support Team’s
- Ensuring support tickets are fully updated with the most current data. Provide proper escalations and hand overs to management and support staff
- Experience or skilled in one or more of the following areas: Cyber security, network security, forensics, vulnerability assessment, data analytics or big data techniques
- A technical degree, PhD or equivalent experience
- Knowledge of myriad of operating systems, from the latest to legacy Windows, Unix and embedded SCADA platforms
Team Lead, Cyber Security Analyst Resume Examples & Samples
- Partners with cyber security researchers on data analysis, prototype implementation, collaboration, and feedback
- As necessary, shares knowledge with external entities including law enforcement, intelligence and other government organizations and agencies
- Must be able to obtain a federal security clearance
- Keen ability to anticipate and recognize cyber security threats
- Clearly communicating technical information in various forms to senior management, peers, and customers
- Develop IT security policies, procedures, standards, and guidance as required by the Federal government and Federal customers
- Provide IT security policy and methodology recommendations to Federal customers
- Ensure information systems are operated, used, maintained, and disposed in accordance with Federal customer security policy, procedures, standards, and guidance
- Support implementation of cybersecurity and risk management frameworks to drive technical solutions for Federal customers
- Conduct oral and written communications on cybersecurity project status and issues with IT Manager and Team Lead to facilitate project planning and control of relevant task orders
- Communicate technical topics to management and non-technical audiences, as well as interface with the Federal customer when required
- Become knowledgeable on the HIPAA policies and procedures for the program and ensure awareness of HIPAA breach process. Understand your role in HIPAA compliance and be able to execute that role in an effective manner
- Bachelor’s degree and 9 years related work experience, Master’s degree and 7 years of experience; or 13 years of experience across multiple IT disciplines including cybersecurity, information security auditing, and information assurance in lieu of a degree
- 3 years’ experience in developing, implementing, or evaluating IT security policies and procedures, system security plans, configuration management plans, security audit plans, and security risk assessment plans
- Must be a US citizen or green card holder
- “Big Four” audit and management consulting experience supporting Federal government contracts
- Experience in FISMA, GAO FISCAM, NIST Cybersecurity Framework, NIST information security standards and guidance including FIPS 199, FIPS 200, NIST SP 800-53, and NIST SP 800-53A
- Solid understanding of Access Control, Audit and Accountability, Configuration Management, and, Identification and Authentication control families in NIST SP 800-53
- Solid understanding of SSA operations
- Strong team player committed to excellence and adherence with Northrop Grumman values, ethics, and standards of conduct
- Strong written, verbal, and interpersonal communication skills
Principal Cyber Security Analyst Resume Examples & Samples
- Responsible for tuning and filtering of events and information, creating custom views and content using all available tools following an approved methodology and with approval and concurrence from management
- Notify the Customer of significant changes in the security threat against the Customer networks in a timely manner and in writing via established reporting methods
- Coordinate with the O&M team to ensure production systems are operational
- Produce daily/weekly/monthly/quarterly reporting as required by management
- Maintain system baselines and configuration management items, including security event monitoring “policies” in a manner determined and agreed to by management. Ensure changes are made using an approval process agreed to in advance
- Coordinate with appropriate organizations regarding possible security incidents. Conduct intra-office research to evaluate events as necessary, maintain the current list of coordination points of contact
- Produce reports identifying significant or suspicious security events to appropriate parties. Include latest security threat information and tie back to specific intrusion sets of nation state actors when possible
- Review and evaluate network modifications and recommend security monitoring policy updates
- Establish procedures for handling each security event detected
- Be able to create and add user defined signatures, or custom signatures, to compensate for the lack of monitoring in threat areas as warranted by threat changes or as directed by the customer. This includes creating content in Arcsight as needed
- Maintain a network diagram depleting the relevant security checkpoints in the network
- Develop and implement a methodology using Arcsight Use Case UML processes that identify procedures for correlating security events. Analysis should all be able to create custom content and develop new use cases to better correlate security event information
- Develop and utilize “Case Management” processes for incident and resolution tracking. The processes should also be used for historic recording of all anomalous or suspicious activity
- Identify misuse, malware, or unauthorized activity on monitored networks. Report the activity appropriately as determined by the customer
- Maintain proficiency and skills through relevant training, conventions, conferences, and on-the-job training
- Science related Bachelor's or Master's degree with a GPA 2:1 or above (UK) or GPA of 3.0 or above (US) or First Class/2nd Upper Honours (Singapore)
- Technical background in cyber security is not mandatory but demonstration of interest and passion for the field will be advantageous
- Ability to deliver under pressure and to tight deadlines
- Excellent organisation and time management
- Conduct platform or operating system vulnerability scans which assess exposure of system to attacks or hacking. Respond to questions regarding viral activity, concerns about spam/phishing etc. Produce reports
- Serve as organization's POC for the third party certification of security procedures and use of cyber security protections. Ensure that system's security controls, policies and procedures examined, measured and validated against third party standards
- Design, plan and implement test strategies to support the core infrastructure in the contingency environment for all critical business applications to ensure business continuity in the event of a major business interruption or disaster
- Lead projects as related to technology refresh/evaluation such as Load Balancing and SSL technology. Research corrective measures (long term solutions) needed for any chronic issues identified that compromise security of particular systems or platforms
- Participate in developing and testing of new methodologies and systems for recovery of the critical core business processes and the enterprise infrastructure
- May serve as technical lead or project lead in projects involving testing defenses against hacking, Denial of service, spam, break-ins, or related attacks. Provide technical guidance to less senior staff or applications developers/systems administrators
- Ability to identify security requirements for applications and services and to effectively communicate requirements to application development teams and application/business owners
- Ability to review application source code for vulnerabilities, using both manual and automated code scanning techniques
- Ability to identify and explain the risks associated with common application vulnerabilities, demonstrate exploitation, and recommend mitigation options
- Ability to initiate and promote activities to foster Information Security awareness and education among application development
- Information security and application security or application development experience
- Ability to coordinate activity among multiple teams, both technical and non-technical
- Strong verbal and written communications skills; comfortable briefing senior management
- Strong interpersonal skills for developing relationships with individuals and teams across the enterprise
- Strong understanding of fundamental Application Security concepts, including common types of attacks and exploitation techniques
- Experience with various application security tools
- Familiarity with emerging applications security exploits and willingness to research them
- Solid understanding of frequently used web application security testing tools
- Solid understanding of common web and systems application vulnerabilities
- Familiarity with key security concepts/frameworks such as OWASP, CVE, and CVSS
- Thorough understanding of application architecture and supporting component
- Perform monitoring, research, assessment and Attack analysis on Intrusion Detection and Prevention tools as well as Anomaly Detection systems, Firewalls, Antivirus systems, proxy devices
- Follow pre-defined actions to handle BAU and High severity issues including escalating to other support groups
- Identifying weaknesses and vulnerabilities within the system
- Execute daily ad hoc tasks as needed
- 5 years of experience with Cyber threat analysis
- DoD 8570 complaint IAT II certification
- GXPN: GIAC Exploit Researcher and Advanced Penetration Tester, GREM: GIAC Reverse Engineering Malware, GCFA: GIAC Certified Forensic Analyst, GWAPT: GIAC Web Application Penetration Tester, GPEN: GIAC Certified Penetration Tester, GCIA: GIAC Certified Intrusion Analyst, or GCIH: GIAC Certified Incident Handler Certification
- Assessing the security impact of security alerts and traffic anomalies on customer networks
- Escalating and explaining severe security incidents to clients verbally
- Responding to technical security questions and concerns from clients
- Possessing a deep understanding of hacker techniques, vulnerabilities, attacks and countermeasures
- Conducting research on emerging security threats and potential customer impact
- Strong knowledge of the TCP/IP protocol suite and related security concerns
- Working knowledge of well-known security tools such as NMAP, Nessus, TCPDump, Wireshark, Netcat, and Backtrack
- Working knowledge of common attacks and vulnerabilities
- Strong understanding of common categories of malware and characteristics of each
- Advanced college coursework in Computer Science or Information Technology, or equivalent experience
- Bachelor's degree in similar field desirable
- Relevant industry standard certifications preferred (SANS, CISSP, C|EH, Etc..)
- Candidate expected to work towards SANS GIAC Certified Intrusion Analyst (GCIA) within 6 months of entry into this position
- ========================================
- Bachelor’s degree in related field with 10+ years of experience in IT with a minimum of 5+ years in IT security. An equivalent combination of education, certification, and experience may be considered
- IAT III Level certification, CISSP preferred
- Knowledge of DIACAP and RMF processes and deliverables
- Ability to understand the impact of cybersecurity on an information system and its organization and how risks may affect goals and objectives
- Ability to meet and communicate effectively with management and technical staff
- Knowledge of DIACAP and RMF processes and necessary forms and artifacts
- Experience with vulnerability scanners, STIG, NIST SP, Retina, SRR, ACAS (Nessus)
- Experience with security hardening, and maintenance
- Knowledge of cybersecurity regulations, and policy, including federal mandates, FISMA, and service-specific regulations
- Knowledge of NIST SP 800-30, 800-37, 800-39, 800-53, 800-53A, 800-60, and DoDI 8500 Series
- Self-motivator with ability to work as part of a team or independently with little supervision or direction
- Professional oral and written presentation skills
- Attention to detail and effective problem-solving skills
- Conduct platform or operating system vulnerability scans which assess exposure of system to attacks or hacking. Respond to questions and issues raised regarding viral activity, spam/phishing etc. Produce reports
- Participate in internal reviews by auditors, operational risk assessment staff, or compliance/reporting staff to prepare assessments or reports of operational risks associated with IT/IS infrastructure, access to systems, exposure to attacks, etc
- Review commercial products available to enhance corporate hardware, platforms, applications and data. May test or evaluate products under consideration for purchase or licensing
- 2 + years’ experience supporting Sail point’s Identity Governance products (IdentityIQ and IdentityNow)
- Extensive experience with Java and J2EE application development and support
- Demonstrate experience supporting Linux Operating System (SUSE and Red hat)
- Demonstrate extensive experience with SQL query development
- Knowledge and support of Oracle database
- Knowledge of SDLC development Life Cycle and Configuration Management
- Able to support JBOSS or Web logic application
- Able to support Apache webserver
- Good understanding of Privileged Account Security Solution with CyberArk PIM (Privileged Identity Management) preferred
- Experience deploying and supporting Microsoft Windows Cluster preferred
- Experience and supporting Microsoft IIS services is preferred
- Experience installing, configuring, and supporting Microsoft Active Directory is preferred
- BS in IT/Cyber Security or related field
- 5-10+ years’ experience in multiple cyber security domains (Access Control, Network Security, Governance / Risk Management, Architecture & Design, Operations)
- Demonstrated Experience with Incident Response
- Demonstrated Experience with Network Reconnaissance
- Demonstrated data mining experience (Data auditing, Aggregation, Validation and Reconciliation; Advanced Modelling Techniques; Testing, Developing, and Presenting outputs in clear and concise reports)
- Familiarity with Defensive Cyber Operations (DCO-Teams) and Computer Protection Teams (CPT)
- Familiarity with basic programming and scripting languages (i.e. Python)
- Demonstrated Experience working in a Client Service environment
- Knowledge of Security Best Practices: NIST, CIS, CISCO, Juniper, Checkpoint, Microsoft, Unix/Linux
- Familiarization with large scale data analytics
- Strong Analytical Skills
- Experience Managing and Prioritizing Multi-Dimensional Technical Requirements
- Military Cyber experiences within DoD preferred
- MS in IT/Cyber Security or related field
- Demonstrated experience with the various phases of digital forensics that involves acquisition, examination, analysis and reporting
- Relevant security knowledge and experience in two or more of the following areas: Digital forensics, Malware analysis, Incident response, network/host intrusion detection or security operations
- Self-motivated and able to work in an independent manner
- Solid working experience with any of the following tools/vendors is desired: Arcsight, Splunk, Wireshark, Riverbed, Sourcefire IDS or Cisco ASA. Certifications with these tools/vendors will be given extra consideration
- Must have at least two (2) certifications in the field of information technology. ** Certified Intrusion Analyst Certification (GIAC) is preferred **
- BA/BS required: Master’s preferred. Focus areas include: Information Assurance, Cyber Security Science, Information Security
- Between 7 - 10 years IA/Cyber Security experience developing and executing IA, CND, Cybersecurity policy and programs within DoD
- Possess working knowledge of DoD policies, directives and instructions (i.e. 8500 series) and technical guidance
- Host Security & Information Security Continuous Monitoring (ISCM), Risk Management Framework Implementation and Governance, DoD IA/CND Compliance Requirements, Federal Information Security Management Act (FISMA), Computer Network Defense Service Provider (CNDSP) Program, cyber security, knowledge of relevant DoD components, IA Portfolio and Governance Management, and Cloud Computing
- Ability to support training and/or facilitation engagements with senior government personnel
- CISSP, ITIL, PMP, CISM
Entry Level Cyber Security Analyst Resume Examples & Samples
- Determine if security events monitored should be escalated to incidents and follow all applicable incident response and reporting processes and procedures
- Ability to problem solve, ask questions, and discover why things are happening
- Correlate data from intrusion detection and prevention systems with data from other sources such as firewall, web server, and DNS logs
- Reporting outputs will be reviewed and approved to ensure quality and metrics are maintained
- 7 years of operational IT experience
- 5+ years’ experience with Network Security Monitoring, SIEM and/or other log aggregation and correlation tools
- 4+ years’ experience with host-centric detection & response skills, as well as process automation
- Excellent communication skills with the ability to drive technical change and constructively influence peers and leadership
- Specific focus on Digital Forensics & Investigative Response (DFIR), cyber security, threat detection, penetration testing (red/blue) and vulnerability management
- Experience leading small to medium-sized teams in focused, matrixed projects
- Experience with Agile Management
Associate Cyber Security Analyst Resume Examples & Samples
- Processing of Requests
- Support of Entitlement Reviews and remediation of exceptions
- Participation in Quality Reviews
- Support the Develop and Maintenance of Internal Procedure Documentation
- Identify security administration deficiencies, recommend improvements, and assist to implement corrective action
- Secondary On-call responsibilities when assigned
- Generally work is self-directed and not prescribed
- Software development lifecycle and JAVA development skills, code analysis
- Security Testing (Functional testing)
- Monitoring and Event Handling (1st, 2nd or 3rd Line)
- Drafting and presenting quality documentation in good written English
- Ability to explain findings in terms of technical and business risk
- Analytical & Systematic Approach
- Integrating COTS products
- Embedded software and processor driven devices
- Shell Scripting
- Conduct platform or operating system vulnerability scans which assess exposure of system to attacks or hacking. Aggregate vulnerabilities discovered during scanning process and produce reports
- Participate in disaster recovery assessments, drills, or redundancy/backup assessments
- Must have proven record of accomplishment in successful problem solving. Proactive learner and creative problem solver who enjoys being in a fast-paced environment, and who enjoys interactions that lead to ultimate customer success and satisfaction
- Must have ability to analyze current business workflow and align new strategy to the large user base across different divisions; influence senior management on project strategy and identify business opportunities, acting as an escalation point and advocate for critical customer issues, collaborating with other departments as needed
- Must have experience engaging and coordinating cross-functional resources both internally and with customer organizations to align on problem solving activity; deriving primary pain points and objectives for stakeholder groups including key data elements used in business processes, unique technical specifications and opportunities for high impact changes
- Must have ability to solve and document solutions for usage of other technicians and customers
- Must have ability to coordinate and communicate to large diverse groups of both technical and non-technical stakeholders leveraging strong command & control skills
- Must have excellent verbal and written communication skills with demonstrated experience communicating with technical and non-technical audiences
- Knowledgeable of Credential management, non-human identity and Privilege access management work stream
- Bachelor’s Degree in Math, Science, Engineering or Computer Science and 8 years previous experience with security configurations of Windows, Linux, and Cisco operating systems in an enclave. 4 additional years of experience can be substituted for the degree
- Candidate must have a DoD Top Secret security clearance
- Experience building, configuring, STIGing, and administering HBSS and ACAS
- Understand principles of information assurance, DOD Risk Management Framework (RMF), NIST 800-53 security controls, and cybersecurity best practice
- Ability to analyze IA test results, identify system weaknesses and develop a risk analysis/evaluation
- Experience documenting RMF artifacts, procedures, processes, and documentation to support system accreditation
- Perform as the team’s cybersecurity operations lead responsible for managing cyber status and reporting of Cyber Task
- Excellent interpersonal skills, selfmotivated, with keen attention to detail
- Must have CISSP or equivalent certification under DoD 8570.01-M in an ISSO/IAM-III role
- Knowledge intrusion detection and firewall system architecture and management; Windows, Linux, and Unix operating systems; IAVM Program; and NIST accreditation process; CAC/PKI technology; security incident handling; software testing and evaluation; Common Criteria requirements; FIPS 140-2 standards
- Specific expertise includes but is not limited to: utilizing
- 3+ years of experience in Cybersecurity policies, processes, and guidance
- Experience with SAP, Citrix, Excel, Business Process Procedures (BPP's), and Change Management
- Knowledge of federal IT security requirements and technical knowledge of the implementation of security controls and practices on an array of technical environments and applications
- Knowledge of SAP security and maintaining user management security roles
- BA or BS degree in IT or CS
- Experience with Heat, Quality Center, QA Tools, UPerform, and Dimensions
- Experience in the area of configuration management and request for change processes
- Possession of excellent oral and written communications skills in the preparation of client-ready, executive-level briefings and reports
- Windows Server 2008 R2 OS Training
- Develop and deliver business specific opportunities to minimise costs
- Be capable of acting as the escalation point for critical issues when required
- Ensure quality outcomes are provided by the team to internal stakeholders
- Provide escalation support to issues encountered in day to day operations
- Mentor staff on internal processes and technology to improve methodologies and up skill resources
- Security Analysts will assist in the creation of processes/procedures, technical documentation, as well as completion of project tasks
- Provides regular monitoring, triage, and response to automated security alerts
- Provide timely detection, identification, and alerts of possible attacks/intrusions, anomalous activities, and misuse activities, and distinguish these incidents and events from benign activities
- Identifies false-positives and false-negatives from alerting
- Provides regular feedback to enhance our security monitoring and controls
- Work with others to resolve computer security incidents and vulnerability compliance
- Examine network topologies to understand data flows through the network
- Provides mentorship to Security Technicians
- Proven Information Technology experience with network technologies, specifically TCP/IP, HTTP and related network tools is required
- In depth understanding of regular expressions
- In depth understanding of network services, vulnerabilities and attacks
- Skill in performing packet-level analysis using appropriate tools (e.g., Wireshark, tcpdump)
- Knowledge of server and client operating systems
- Knowledge of defense-in-depth principles and network security architecture
- Skill in network mapping and recreating network topologies
- Knowledge of the types of Intrusion Detection System (IDS) hardware and software
- Skill in tuning sensors
- Skill in protecting a network against malware
- Knowledge of how traffic flows across the network (TCP/IP, Open System Interconnection model [OSI], Information Technology Infrastructure Library [ITIL])
- Conduct platform or operating system vulnerability scans to assess exposure of system to attacks or hacking. Respond to questions regarding viral activity, concerns about spam/phishing etc. Produce reports
- Serve as technical lead or project lead in projects involving testing defenses against hacking, Denial of service, spam, break-ins, or related attacks. Provide technical guidance to less senior staff or applications developers/systems administrators
- Experience with multiple phases of the intelligence process, including producing and disseminating intelligence products in written and verbal form
- Experience integrating written analysis products with structured threat data
- Ability to apply data science processes to manipulate and analyze cyber threat intelligence
- Familiarity with one or more classes of threat actor, such as nation state, organized crime, or hacktivist entities
- Experience with email and web advanced malware detection technologies such as FireEye and Yara
- Experience with SIEM and/or log aggregation technologies such as ArcSight, Splunk, or ELK
- Experience with netflow analysis and/or deep packet inspection technologies
- Experience developing and tuning new detection signatures
- Familiarity SOC monitoring operations
- 4 years+ of related Information Security experience
- High aptitude for troubleshooting
- A self-starter with a strong work ethic
- Experience in driving change and delivering measureable results
- Experience supporting global customers
- Vulnerability management experience
- Experience with the McAfee suite of endpoint security products
- SIEM experience
- Cloud computing experience
- Must be rising junior in a Bachelors program or above, with a minimum 3.2 GPA – both cumulative and major (will be verified by transcripts)
- Must have strong communication skills and ability to work effectively in a collaborative environment
- Preferred Course of Study: Computer Science / Information Assurance
- 3 years experience with Python, web2py and API Scripting
- 2 years experience with Splunk, vulnerability management and networking skills
- Security certifications a strong plus (CISSP, SANS, etc)
- Support Center management in the risk management process to
- Identify the Center cyber footprint
- Identify and understand the Center’s cyber risks
- Identify how the Center processes and uses unclassified but sensitive information (e.g., OUO, PII, ECI, UCNI)
- Identify how the Center processes and uses classified information
- Maintain knowledge of cyber requirements within the Center and the Center’s mission
- Serve as the Center’s liaison for Corporate Unclassified Information and PII requirements and be able to direct Center personnel to available resources
- Corporate Dictionary for definition of PII
- Corporate, Identify and Protect Unclassified Information, and Control Personally Identifiable Information
- Available Corporate Tools
- Participate in Cyber Security working groups, CSO Senate, and Cyber related training
- Communicate information regarding cyber security to Center management and/or the Center workforce as necessary
- Be cognizant of any foreign national personnel working with, or within, the Center, as well as the rules regarding foreign national access to SNL cyber resources
- CSAA: Coordinate, prepare and maintain the Cyber Security Accreditation Agreement (CSAA) information in NWIS, in accordance with applicable Corporate and Cyber Security policies
- Audits: Assist Cyber Security personnel and auditors with
- Internal corporate inspections, surveys and audits
- External inspections, surveys and audits
- Cyber Security self-assessments and risk assessments
- ISSO: As the Information System Security Officer (ISSO) for classified stand-alone cyber systems within your center, coordinate, prepare and maintain one-page classified cyber security plans. Potential assignment as an AISSO for network security plans
- Refer Center management or line personnel to external organizations when applicable
- Bachelor’s degree or equivalent experience (4 years) and 2+ years of Information Technology experience
- Familiarity DISA STIGs
- Demonstrated ability to exercise good judgment, discretion and tact
- Demonstrated ability to communicate detailed technical information to a non-technical audience
- Demonstrated ability to run vulnerability scan reports, analyze and interpret results
- Demonstrated ability to maintain Windows server and desktop systems
- Familiarity with AD and group policy objects
- Demonstrated ability to understand and manipulate Windows registry entries
- Excellent written, verbal, and decision-making skills
- Demonstrated ability to work independently without day-to-day supervision
- At least 2 years of experience as a desktop or server system administrator
- Familiarity with Linux
- Familiarity with Tenable Security Center
- Security + or SSCP certification
- Familiarity with Windows Server 2012
- Familiarity with VMWare ESXi 6

Cyber Security Analyst, Chennai Resume Examples & Samples
- Good understanding of cyber security principles like; cyber security architecture, defense in depth, default deny, least privilege, compartmentalization, privileged initiation, RBAC, etc
- Good understanding of basic cyber security controls like; IDS/IPS (host and network), hardening, security policies, Malware Protection, Filtering, NGFW, etc
- Basic understanding and knowledge about Industrial Control Systems and SCADA systems
- Good knowledge in industrial communication protocols (eg.,Modbus, CAN, EtherCAT) and standards - IEC 60870-5, IEC 61850
- Experienced software developer in at least C/C++ and C#
- Experienced network developer in Winsock, Berkley, TCP/IPv4 and v6
- Real time Programming skill would be an added advantage
- Advanced degree with experience in a national security related field
- Active federal security clearance - DOD TS or DOE Q
- Foreign language skills desired
- Build real-world situational awareness from cyber technical data
- Intelligence Analysis, Data Fusion Methodologies, and Data Visualization Techniques
- Analytic workflow
- Analysis of network activity logs using Wireshark, Splunk, netflow, etc. to identify root cause, malicious activity, and evidence of post-exploitation
- Analysis of Windows log files for the purpose of finding artifacts related to malicious activity
- Develop and produce reports on all activities and incidents to help maintain day to day status, develop and report on trends, and provide focus and situational awareness on all issues
- Mentor and train cyber security analysts on advanced detection and analysis methods
- Provide support for the A/V hotline and appropriately document each call in an existing tracking database for this purpose
- Coordinate with appropriate organizations regarding possible security incidents
- Conduct intra-office research to evaluate events as necessary, maintain the current list of coordination points of contact
- Produce reports identifying significant or suspicious security events to appropriate parties
- Recommend and/or execute procedures for handling each security event detected
- Be able to create and add user defined signatures, or custom signatures, to compensate for the lack of monitoring in threat areas as warranted by threat changes or as directed by the customer
- Develop appropriate ArcSight Dashboards, Data Monitors, Query Viewers, Trends, and Reports as needed to investigate detection trends and activities
- Develop and implement a methodology using Arcsight Use Case UML processes that identify procedures for correlating security events
- Analyst should all be able to create custom content and develop new use cases to better correlate security event information
- Utilize “Case Management” processes for incident and resolution tracking
- Identify misuse, malware, or unauthorized activity on monitored networks
- Provide analytical support as needed for the overall projects and systems by working with engineers, O&M, and other personnel to ensure effective operations of all capabilities, piloting of new systems, and periodic updates to systems
- Bachelor’s Degree in cyber security, computer engineering, computer science, or other closely related IT discipline
- Minimum of five years of progressively responsible experience in cyber security analysis, incident response, or related experience
- Experience in Incident Handling and/or Digital Forensics, familiarity with advanced cyber threats, experience authoring and reading Snort and/or Yara rules; and advanced knowledge of TCP/IP, OSI model, and pcap analysis
- DoD 8570 IAT Level III compliant
- Prior cyber security experience, ideally in Penetration testing role
- Able demonstrate a passion for cyber security - through written papers, research etc
- Knowledge of a variety of architectures and exploitative tools
- Desire to conduct research
- Review, document, and analyze defensive security tactics and procedures
- Collaborate to analyze attack vectors, gather evidence, and implement preventative controls
- Architect and design cyber security technologies, integration of cyber detection capabilities, and defensive countermeasures
- Provide recommendations on strategies for improving cyber security controls
- Design and implement cyber maturity models to evaluate the effectiveness of an organization’s cyber program
- Prepare and present technical reports and briefings
- Work in a cyber-program focused on collaboration, partnership, and “out of the box” creativity
- 4+ years of cyber operations, engineering, and / or architecture experience
- 3+ years of audit experience
- 2+ years in a leadership role in cyber security
- 2+ years government related cyber security experience
- ) Advanced threat monitoring, threat intelligence experience
- ) Security Information Management, monitoring, platform management
- ) Networking Firewall Experience
- Monitor and analyze security event data
- Use security tools to determine the nature and scope of security events to differentiate between potential intrusion attempts and false alarms
- Use the trouble ticketing system to track security event investigations to resolution
- Document all activities during an incident and provide status updates to leadership
- Stay up to date on current vulnerabilities, attacks and countermeasures
- Conduct proactive threat and compromise research and analysis
- Assist with the development of processes and procedures to improve NOC operations
- Foster and maintain good relationships with colleagues to meet Sponsor’s requirements
- 24x7 shift coverage
- 3+ years' experience in an enterprise security role
- Extensive experience with Web Application Security - able to identify, confirm, and remediate vulnerabilities
- Broad knowledge of security best practices and compliance requirements
- Technical and user experience with Atlassian suite of products, including, but not limited to, JIRA, Confluence, or Bamboo
- Experience with secure coding best practices
- Experience implementing and assessing security controls in appropriate information systems
- Determine agency-level risk to the mission or business case
- Experience with enterprise Identity Management technologies and implementation
- DoD 8570.1M IAM level 2 is required (i.e., CISSP or CASP)
- Resource will act as the IASO for hosted systems, assuming the responsibilities
- Resource will assist hosted customers in obtaining and maintaining RMF for DOD IT, DIACAP, and other certifications as required
- Resource will update and/or assist the hosted system's personnel in updating artifacts of the accreditation package and store the artifacts in organizationally defined repository; i.e., system diagram (logical and physical) Hardware/Software/Firmware Inventory, Interface & Ports, Protocols and Services listing, etc
- Resource will assist in the preparation of network infrastructure specifications or designs incorporating required information security features
- Resource will review and evaluate Information Systems Design Plans, Continuity of Operation Plans, Communication Plans, engineering change proposals and configuration changes for compliance with relevant security regulations, policies, and best industry practice
- Resource will assist in the preparation of required documentation and coordination with Authorizing Official/Designated Approval Authority to obtain hosted system security accreditation to include certification procedures and criteria, certification evaluation reports and reports of findings
- Resource will provide security engineering design and analysis services
- Resource will perform vulnerability scanning of computer systems using authorized security scanning software
- Resource will use results of vulnerability scans to determine vulnerabilities and develop operational plans to remediate or mitigate vulnerabilities as they are discovered
- ) Advanced threat monitoring, threat intelligence, dark web, gathering analysis
- ) Security Information Management, Monitoring, Platform Management - Experience with SIEM tools (i.e., Archsight, Splunk, Snort, Qradar)
- ) Perimeter protection - Networking Firewall
- **NO CORP TO CORP****
- Provides subject matter expertise on enterprise cyber security risks, threats, technologies, and potential impact
- Continually monitors against authorized security control requirements and reports system risks and application configurations or vulnerabilities
- Intercepts and prevents internal and external attacks or attempts against PNNL systems
- Interprets, analyzes, and executes incident response actions for detected intrusion anomalies and events
- Conducts system, network, and software vulnerability assessments and penetration testing
- Prepares and presents technical reports and briefings
- Contributes to design, development and implementation of countermeasures, cyber security systems integration, and leverages tools specific to cyber security operations
- Ability to reverse engineer malware
- Advanced Security Certification (CISSP, CEH, EnCE, etc)
- Weekend or evening “on-call” duties
- Exceptionally strong peer leadership, interpersonal, collaborative, and customer relationship skills are essential
- Use practical knowledge to effectively remediate threats, and modify activities and priorities to anticipate and respond to changing conditions
- Network protocols, uses, and potential exploitation by malicious software
- Applying layered computer network defense techniques and network policy architectures
- Tracking malware infections across a wide enterprise
- Working independently and leading collective team efforts to develop theories, ideas, and concepts around cyber security methodologies
- 1+ years of experience Cyber Security, Information Security and Risk Management
- 1+ years of experience of Domain Name System (DNS), networking topologies and protocols, and internet security concepts
- 1-2 years of financial services, risk management, technology, digital services or legal-facing experience
- Experience leveraging Open Source Intelligence (OSINT) to inform a process a plus
- Experience with Lockheed Martin’s Cyber Kill ChainTM and Intelligence Driven Defense a plus
- Nice to have experience in Brand Protection detection tools
- CISSP, Security+ or equivalent security certification preferred
- Active or ability to obtain SC clearance
- Experience with SIEM and/or log aggregation technologies such as LogRhythm, Netwitness, RSA SA or McAfee ESM
- Develop an overarching security awareness strategy that takes corporate culture and existing relevant policies and technical security standards into account
- Drive the development and publishing of security awareness materials and contents
- Facilitate training sessions for new hires, existing employees and target user groups as required by the business
- Evaluate existing security capabilities to understand needs with a view to translating those needs into additional capabilities verified to meet business requirements
- Serve as an information security advisor to other subject matter experts and key business stakeholders, establishing trust relationships through active engagement and powerful collaboration
- Interpret relevant security policies, standards, guidelines and best practices for the purposes of communicating security requirements and rationales to internal customers in non-technical terms
- Act as an advocate for information security on mergers & acquisition projects
- Own and manage the team’s intranet site to keep contents relevant and updated
- Conduct threat and vulnerability assessments to determine security requirements and controls following assessment of the potential business impact of security breach
- Provide security consultancy and assessment services whilst introducing improvements in technical security standards and security implementation designs/patterns
- Sound decision making skills with exceptional ability to strike the right balance between security requirements and strategic business objectives
- Strong analytical and conceptual skills balanced by broad perspective on how security efforts support realization of business goals
- Demonstrated experience in understanding security risks, identifying control gaps and advising senior management and relevant business stakeholders on the most effective mitigation options
- Working knowledge of security frameworks and industry best practices such as NIST, SANS, ISF, ISO 27001 and COBIT
- Ability to thoroughly review technical design components to ensure alignment with security policies, standards and best practices
- Strong knowledge and understanding of current and emerging cyber security threats, vulnerabilities, trends and mitigations ranging across the technologies required to provide layered defense
- Excellent understanding of key information security terms, tenets and models
- Strong interpersonal skills and positive attitude required to interface with all levels within the organization
- 5 years of experience with SharePoint
- 3 years of experience as a Cyber security analyst as of January 2010
- Experience with Enterprise Mission Assurance Support Service (eMASS)
- Experience in developing change management plans and procedures
- Experience in writing product evaluation papers and senior staff summary documents
- DODI 8570 IAT Level I or higher Certifications, including Net+, Security+, CISSP, and CISM
- Experience with DoD and Air Force Cybersecurity policies and processes, including DODI 8530
- Experience with Air Force or DoD Command and Control capabilities
- Experience with JCIDS Battlespace Awareness requirements
- Experience with developing DoDAF artifacts and using them as input for system validation and verification
- MCSE or MCITP, SQL, SPLUNK, and Oracle Certifications
- Investigate network intrusions and other cyber security breaches to determine the cause and extent of the breach
- Research, develop, and recommend hardware and software needed for Incident Response and develop policies and procedures to analyze malware
- Participate in technical meetings and working groups to address issues related to malware security, vulnerabilities, and issues of cyber security and preparedness
- Collaborate with the Executive Director of Cyber Security & Investigations and INFOSEC to facilitate an effective IR program
- Prepare, write, and present reports and briefings
- Thoroughly investigate instances of malicious code to determine attack vector and payload
- Develop high performance, false positive free, signature based network level, and malware detection schemes
- Participate in special forensic investigations as required, including collection, preservation of electronic evidence
- Preserve and analyze data from electronic data sources, including laptop and desktop computers, servers, and mobile devices
- Preserve, harvest, and process electronic data according to the department's policies and practices on an as necessary basis
- Endpoint and network intrusion detection, investigation, and response
- Information security monitoring and risk management
- Identify areas of weakness and vulnerability and recommend changes to meet security standards
- Attack sensing and warning
- Host and network security auditing
- Insider threat analysis
- Previous experience working in a regulated/compliance based environment (PCI/POS/Gaming)
- Previous experience with ProofPoint
- Bachelors and five (5) years or more experience; or Masters and three (3) years or more experience
- Excellent organizational, attention to detail, multi-tasking, and time management skills
- Ability to interface effectively with all levels within the organization
- A holistic understanding of attack vectors, current threats, and remediation strategies is essential for this role
- Certifications such as CISSP, CEH, etc
- Five (5) years incident response experience
- Three (3) year vulnerability scanning experience
- Apple OSX operating systems (system administration level)
- Penetration testing experience. Working knowledge of security auditing processes
- Coding/Scripting experience e.g. Perl, VB Script, Python etc
- Three (3) years or more experience in lieu of degree
- Ability to occasionally support flexible shifts
- Ability to occasionally support travel
- An understanding of attack vectors, current threats, and remediation strategies
- Three (3) years development / programming / scripting
- Application Development / Programming / Scripting
- Database Administration (i.e. Microsoft SQL, MySQL, Postgre)
- One (1) year vulnerability scanning experience
- Coding/Scripting experience e.g. Perl, VB Script, Python, Bash, Shell etc
- Data Analytics, including mastery with Excel, Filemaker and other tools
- Ability to effectively lead meetings and projects
- Experience with SharePoint administration (basic level)
- Strong written, verbal, interpersonal skills, emotional intelligence, and a positive attitude to interface effectively with all levels within the organization
- Possess excellent analytical and problem-solving skills
- Excellent organizational, detail, multi-tasking, and time management skills
- 3+ years incident response or vulnerability management experience
- Operating Systems: Linux, Apple OSX, Windows (system administration level)
- High level of experience with Splunk for data analysis
- Coding/Scripting experience e.g. Perl, VB Script, Python etc. is a plus
- Collaboration with IT technical teams for issue resolution and mitigation
- Collaboration with IT technical teams to deliver Information Security service improvements through project lifecycle
- Host level forensics
- Experience assisting the development and maintenance of tools, procedures, and documentation for the Computer Security Incident Response Team (CSIRT)
- Subject matter expert (SME) in one or multiple areas such as Windows, Unix, firewalls, intrusion detection, threat detection analysis, or computer forensic
- Outstanding work ethic
- Ability to rapidly find, assimilate and correlate information correctly while under pressure
- One or more of the following SANS GIAC, GCIA or GCIH certification and/or CISSP, CISM
- Working knowledge UNIX/Linux
- Working knowledge of malware forensic technologies
- Working knowledge of malware sandboxing technologies
- Working knowledge Vulnerability Management Products
- Working knowledge of SQL queries
- Bachelor's Degree and 5+ years of experience or H.S. Degree and 9+ years of experience
- Experience with Cisco or Palo Alto firewalls is required
- Experience conducting Threat Analysis
- Experience with Splunk is highly desired
- Experience conducting Vulnerability Assessments running such tools as WebInspect, Burp, Nessus, Appscan and others
- Experience defining and managing tasks with minimal oversight and providing status to senior government managers
- Experience writing and maintaining organizational and project level IT security policies, standards, guidelines and procedures based on Federal IT security requirements and agency policies/practices
- Experience administering and configuring a broad range of operating systems, databases, and server configurations
- Experience applying, tailoring and augmenting 3rd party security baselines for operating systems, databases, mobile devices, laptops, workstations, servers and cyber security defense infrastructure
- Knowledge of Linux and Windows scripting
- Communication skills that include developing and delivering technical papers and presentations to senior management, stakeholders and peers in business (non-technical) terms, if required
- Reporting skills - relating project, task and other work status to senior IT management and stakeholders both informally and formally
- Documentation skills - writing policy, plans, procedures and supporting documentation
- Maintain currency on Federal security recommendations and practices
- Evaluate security tools and develop business cases for investments in technology solutions that deliver improvements in security
- Assist with creating and maintaining policies, standards, guidelines and procedures
- Recommend improvements for the overall security posture of infrastructure, systems and applications
- Monitor NASA agency reports and SOC (Security Operations Center) systems for incidents and malicious activity
- Correlate and discover relationships between events and incidents
- Produce high quality reports
- Perform relevant incident data analysis and correlate with multiple sources for mitigation
- Provide incident handling and response support for the agency
- 4-6 years related work experience
- Process oriented individual excelling in a team environment
- Knowledge of common enterprise applications, e-mail, web, cloud, client/server applications
- Ability to obtain a government clearance (US Citizenship is required)
- Experience with customer service coordinating with team activities
- Experience reviewing and analyzing log data
- Familiarity in a command line environment
- CEH, Security+ are desired certifications
- Review threat data from various sources, and develop custom signatures for open source Intrusion Detection Systems (IDS) or other custom detection capabilities
- Employ advanced forensic tools
- May conduct malware analysis of attacker tools providing indicators for enterprise defensive measures, and reverse engineer attacker encoding protocols
- Interface with remote team members located across the globe
- Bachelor’s degree in a Computer Science/Engineering or Information Technology related field
- 2 to 5+ years of successful work experience in IT technologies including networking, operating systems, or a related field
- Knowledge of networking protocols (such as TCP, UDP, DNS, FTP, SMTP, DHCP, etc.)
- Experience with Windows operating system functionality (file system structure, registry keys, scheduled tasks, processes, services, memory management, data storage, etc.)
- Excellent analytical and critical thinking skills
- Excellent interpersonal and communication skills (verbal & written)
- Required Travel: <10%
- Experience managing an investigation; understanding the methodologies for investigative triage, case/investigation definition, etc
- Understanding of the Windows File System structure, and ability to recover deleted files, search hidden files, and access registry keys
- Knowledge of Operational Security (OpSec) principles for cyber operations with an emerging understanding of the relationships between the cyber domain disciplines
- Ability and experience capturing and analyzing volatile (in-memory) data
Tier Three Cyber Security Analyst Resume Examples & Samples
- Extensive experience analyzing and synthesizing information with other relevant data sources, providing guidance and mentorship to others in cyber threat analysis and operations, evaluating, interpreting, and integrating all sources of information, and fusing computer network attack analyses with counterintelligence and law enforcement investigations
- Email security
- Digital media forensic
- Monitoring and detetion
- Vulnerability assessment and pen test
Tier Two Cyber Security Analyst, DC Metro Resume Examples & Samples
- Extensive experience working with various security methodologies and processes, advanced knowledge of TCP/IP protocols, experience configuring and implementing various of technical security solutions, extensive experience providing analysis and trending of security log data from a large number of heterogeneous security devices
- Expert knowledge in two or more of the following areas: Vulnerability Assessment, Intrusion Prevention and Detection, Access Control and Authorization, Policy Enforcement, Application Security, Protocol Analysis, Firewall Management, Incident Response, Encryption, Web‐filtering, Advanced Threat Protection
- Specialized experience in one of the following areas
Cyber Security Analyst Vulnerability Management TS Resume Examples & Samples
- Broad scope of tasks associated with vulnerability management; system and application scanning; compliance reporting and other cyber security tasks related to identifying and mitigating security vulnerabilities
- Performs VM functions related to audit/inspection; infrastructure support; certification and accreditation; detection and response support services
- Requires DoD 8570: IAT II and CND-SP Specialty: CND Analyst
Senior Principal Cyber Security Analyst CND Tools Data Integration Resume Examples & Samples
- Broad scope of tasks to include O&M and tuning of cyber defense tools; integration of Splunk; Forescout; Fire Eye; Tanium and other tools; security architecture design; implementing new cyber capabilities; implementing regional based IPS; designs and defines system architecture for new or existing computer systems
- Performs functions to include but not limited to systems engineer; audit/inspection; infrastructure support; certification and accreditation; vulnerability management; detection and response support services
- Executes policies and guidance provided by senior functional/technical leads
- Must be willing to obtain and maintain CI polygraph
Intermediate Cyber Security Analyst Data Integration Aggregation TS Resume Examples & Samples
- Communicates alerts to agencies regarding intrusions and compromises to their network infrastructure, applications and operating systems
- Primary responsibility is Maintain; Configure and Troubleshoot Cyber Defense Systems. The candidate will have experience in one of the following areas
- Linux based servers and appliances
- Client\Server technologies and troubleshooting
- May also assist with the following: 80/443 web content filters/proxies; email security capabilities; IDS; IPS;SEIM; DNS security practices; advanced log analysis; network monitoring; network flow analysis; packet capture analysis; network proxies; firewalls; anti-virus capabilities; Linux/UNIX command line; and access control lists
- Ability to write signatures for detection systems; such as SNORT and McAfee Intrushield a plus
- Will have experience with multi-tasking providing on ground support to CNDSP work centers
- Will have excellent oral and written skills creating programmatic documentation; standard operating procedures and granular process checklists
- Requires DoD 8570: IAT III and CND-SP Specialty: CND-IS
- DbProtect vulnerability Assessment & Database Inventory. Assess, identify and remediate vulnerabilities that expose the database. Enforce user access controls and privileges
- SNORT network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Perform traffic analysis and packet logging on Internet Protocol (IP) networks. Carry-out protocol analysis, content searching, and content matching to detect probes or attacks, including operating system fingerprinting attempts, common gateway interface, buffer overflows, server message block probes, and stealth port scans
- Countertack Active Defense to detect malware infections on client systems and collect forensic memory dumps
- Report and disable lost mobile devices to include mobile phones, tablets, and thin clients
- Assist with System Certification / Assessment and Audit response / compliance assurance
- Adhere to Service Level Agreements (SLAs), Key Performance Indicators (KPIs), and operational metrics
- Utilize ITSM (Remedy preferred) ticketing system
- Experience with Remedy service management systems and working in a collaborative service desk environment would be an asset
- Other skills required include possessing strong written & verbal communication skills and inter-personal qualities needed to collaborate closely with Operations and Engineering Staff, Service Desk Support Technicians, Managers and Customers
- Capable of managing multiple tasks while demonstrating flexibility with adjusting priorities depending on operational need and will be able to assimilate new technologies quickly and be willing to maintain industry knowledge
Senior Principal Cyber Security Analyst Resume Examples & Samples
- Linux (Debian, RedHat, CentOS) and Windows experience (system administration level)
- Strong written, verbal, interpersonal skills, emotional intelligence, and a positive attitude
- Seven (7) years cyber security experience
- Strong Splunk skill set. The security analyst will leverage Splunk to analyze logs and other security events to find targeted attacks against network based bank assets
- Strong Intrusion Analysis background. Resource must be able to identify and interpret weblogs from various webservers
- Working knowledge of Linux, Windows, and OS X operating systems
- Comfortable with scripting languages and regular expressions
- Working knowledge of enterprise Client / Server architecture
- We are a front line team that handles active security events and highly current threats. On call and after hours work can be expected although we rotate to approximately one week every 2 months
- The analyst will use new intelligence to update existing controls to detect new threats against the bank. Will be expected to have solid technical skills to operate independently and to support others within the security team
- Understanding of stateful firewalls and able to interpret firewall rules
- Familiarity with web application attacks including SQL injection, cross-site scripting, and remote file inclusion
Csoc Cyber Security Analyst Resume Examples & Samples
- Interface/engage with external customers on a range of topics to include: alerts, system configurations, incident response, calibration of detection tools and similar activities
- Serve as a technical resource during pre-sales, ramp up, deployment and operations for the CSOC business leadership
- Correlate actionable security events from various log sources which either feed or supplement the Security Information and Event Management (SIEM) solution
- HS degree required, Bachelor’s degree in a Computer Science/Engineering or Information Technology related field highly preferred
- 5 to 8 years of successful work experience in IT technologies including networking, operating systems, or a related field
- Capable of learning new concepts and processes quickly, and adapting to a constantly changing environment
- Ability to apply skill set to resolve complex problems
- Required Travel: <10% (International and Domestic)
- Working knowledge of ICS (Industrial Control Systems) systems, protocols, etc
- Application of common Cyber Security concepts including Intrusion Detection Systems, Host Intrusion Prevention Systems, and Anti-Virus Solutions
- Experience with network signature development with tools such as SNORT, NetFLOW, WireShark, tcpdump or related tools
- 1 year of Cyber Security experience
- Ability to manage tools such as Tippingpoint, Splunk, and Forcepoint
- Experience performing risk/vendor assessments or policy development
- Experience with Intrusion detection systems (IDS)
- Experience with in-plane switching (IPS)
New Grad-cyber Security Analyst Resume Examples & Samples
- Develop sound Cybersecurity processes to include implementation of RMF-based policies and procedures
- Conduct assessments of systems and networks within the networking environment or enclave and identify where those systems and networks deviate from acceptable configurations, enclave policy, or local policy
- Execute vulnerability assessments; ensure mitigation of risks and support obtaining certification and accreditation of systems
- Document the results of Certification and Accreditation activities and technical or coordination activity and prepare the system Security Plans and update the Plan of Actions and Milestones POA&M
- Be completing or has completed their degree (Bachelor’s, Master’s, or PhD) from an accredited institution; It must be no more than 1 year if the degree has already been obtained
- Not have professional work experience in their field of study (excluding internships, co-ops, or research studies)
- Be majoring in a STEM degree field such as computer engineering, computer science, engineering, physics, or math
- Have an overall cumulative GPA of 3.25/4.0 or higher (unofficial academic transcripts must be provided at time of application by uploading the documents to your application or profile)
- Be able to obtain a U.S. Government security clearance (U.S. citizenship is a pre-requisite)
- Good presentation and writing/communication skills
- Self-motivated, willing to learn, and interested in working in a team environment
- Have an overall cumulative GPA of 3.70/4.0 or higher
- Top Secret/SCI security clearance
- Working knowledge of Linux Red Hat and Microsoft operating systems
- Working knowledge and understanding of boundary protection devices, including firewalls and IPS devices
- Candidate should have experience supporting CND or related teams; working CND duties; working with DoD / Government Leaders at all levels; and strong communication skills
- Knowledge of hacker tactics, techniques and procedures (TTP)
- Ability to conduct malware analysis - analyze packed and obfuscated code. Understanding of software exploits
- Associates Degree and 4 years experience in IS
- Applicable military experience/training or equivalent training certificate(s) from an accredited training program may substitute for the degree requirement
- A Bachelor’s degree in Electrical Engineering, Information Systems, Computer Science, Physics, Math, or related field that supports the duty requirements may fulfill all the education and experience requirements established for this position
- Candidate must possess a CompTIA Security+ with Continuing Education (CE) certification. Must meet DoD 8570.01-M IAT II certification within six months of hire (CEH certification)
- Candidate will provide C2 support, situational awareness support, and provide leadership & support for all CND applicable activities within Protect, Detect, Respond, and Sustain
- Candidate will support teams within a performance-based environment with pre-determined Acceptable Levels of Performance (ALP’s)
- Candidate is responsible for maintaining the integrity & security of enterprise-wide systems & networks
- Candidate should have at least one other IA certification completed, i.e., SSCP, CSIH, GCIA, GCIH or CEH
- Candidate should have UNIX Administrative skills. -
- Be able to conduct malware analysis
- Demonstrated hands on experience with various static and dynamic malware analysis tools
- Knowledge of advanced threat actor tactics, techniques and procedures (TTP) Understanding of software exploits
- Ability to analyze packed and obfuscated code
- Comprehensive understanding of common Windows APIs and ability to analyze shellcode
- Conducts tests on existing complex data security architecture to determine degree of stability
- Reviews security status reports to oversee system status and potential and actual security violations
- Writes reports and communicates to management/client findings. Understand and provide expertise on the Operational Acceptance process for weapon systems and IT capabilities. Prepare and conduct system implementation readiness reviews on behalf of the 24 AF Commander
- Experience working with company software and hardware products
- Experience working with operating systems
- Experience with networking
- Good communication skills to interact with team members, management, and support personnel
- Defense community experience required
- Data and Network security experience required
- Technical writing experience desired
- Cloud computing experience desired
- Network architecture experience desired
- Required Certifications: Security+, IAT Level II
- Identifies security exposures that currently exist, or are emerging, and that create potential threats to Baker Hughes infrastructure, systems or data. Notifies leadership of potential or existing threats and proposes risk mitigating strategies
- Able to perform computer forensics for Windows and UNIX based operating systems
- Utilizes “Incident Response” and testing procedures during the investigation of security alerts and events
- Capable of understanding network forensics in order to identify lateral movement and threat vectors related to a cyber-event
- Monitors security blogs, articles, and reports and remains current on related laws, regulations, and industry standards to keep up to date on the latest security risks, threats, and technology trends and uses this knowledge. Incorporates information into processes, procedures, and audit preparedness activities
- Ability to assess present cyber security related technical controls and recommend additions or modifications where appropriate to increase defensive posture. Familiarity with the technical security control marketplace and recommend future direction in order to fill existing or emerging gaps as they are known to exist
- Able to engages at all levels of Business and IT Functions as deemed necessary based on the type and severity of a Cyber Incident
- 5-7 years’ experience
- Security audit functions experience
- Security operations experience including the deployment and use of enterprise tools such as firewalls, web proxies, anti-virus and patching solutions
- Proficiency in forensics, forensic investigation/analysis, advanced incident handling, intelligence gathering, forensic research, and formal incident investigation
- Detailed technical experience with a minimum of four years’ experience in one or more of the following: computer network penetration testing and techniques; computer evidence seizure, computer forensic analysis, and data recovery; computer intrusion analysis and incident response, intrusion detection; computer network surveillance/monitoring; network protocols, network devices, multiple operating systems, and secure architectures
- Applicable Certifications: CISSP, GIAC Certified Intrusion Analyst (GCIA), GIAC Certified Incident Handler (CGIH), GIAC Certified Forensic Analyst (GCFA)
- Ensure all pertinent information is obtained to allow the identification, categorization, incident handling and triage actions to occur in a time sensitive environment
- Analyze network traffic and various log data and open source information to determine the threat against the network, recommend appropriate countermeasures, and assess damage
- Act as the point of contact for accepting, collecting, sorting, ordering, and passing on incoming information for the reported cyber events
- Facilitate and expedite the tracking, handling, and reporting of all security events and computer incidents in accordance with organizational procedures
- Evaluate and perform incident escalation in accordance with organizational guidelines
- Solve complex technical issues with limited supervision
- Work with other team members to ensure an effective and efficient cyber incident management system
- Open to future career development opportunities within Textron business unit locations
- Protect and maintain the privacy of employee personnel records including, but not limited to, personal and compensation information about employees
- Bachelor’s Degree in Information Assurance/Security or related field required
- Ability to obtain a secret security clearance required
- Relevant internship experience preferred
- Degree from designated National Centers of Academic Excellence in Information Assurance (CAE/IAE) Education Programs preferred
- MCSE, CCNA, CCNP, ISC, CAP, Associate of (ISC)²/CISSP, CISM, CompTIA, or GIAC certifications preferred
- Knowledge of a scripting language, Python preferred
- Ability to work individually and part of a team with little supervision
- A high level of personal integrity with the ability to handle confidential matters
- Demonstrated knowledge of incident data flow and response, content, and remediation
- Demonstrated understanding of incident response processes, cyber threats, vulnerabilities and network exploits
- Working knowledge of security monitoring, security event and incident management systems, Internet content filtering/reporting, and malware prevention
- Working knowledge of anti-virus, firewall, intrusion detection/prevention, and web security technologies
- Classroom experience or exposure to incident response or malware analysis
- (ISC)², Microsoft, CompTIA, or GIAC certifications preferred
- Knowledge of a scripting language, Python or PowerShell preferred
- Familiar with common server and authentication technologies
Joint Service Provider Cyber Security Analyst Resume Examples & Samples
- BS degree with 2 years experience OR 6 years experience in lieu of degree
- 6+ years of Cyber Security experience
- DoD Experience - 2 or more years
- IAT Level III certification
- Selected candidate will collect and analyze event information and perform threat or target analysis duties
- Provides operations for persistent monitoring on a 24/7 basis of all designated networks, enclaves, and systems
- Reviews incident logs/records mining for patterns and correlate with tools, including Splunk
- Coordinates with external organizations and authorities to collaborate on investigations, collect IOCs, share intelligence, etc
- Coordinates and distributes directives, vulnerability, and threat advisories to identified consumers
- Provides daily summary reports of network events and activities and delivers metric reports
- Recommend counter measures to malware and other malicious type code and applications that exploit customer communication systems
- Monitors various sources for threat intelligence on a regular basis
- Conduct reverse engineering for known and suspected malware files
- Develop policies and procedures to investigate malware incidents for the entire computer network
- Assist in the development and delivery of malware security awareness products and briefings
- Develops models for identifying malicious activity using various tools and statistical analysis
- Works closely with other teams to investigate and remediate incidents
- Active Top Secret or Secret security with the ability to obtain a TS/SCI
- Existing Public Trust
- CEH, MSCE, CGIA, CCNA, or CISSP Certification
- Statistical modeling and analysis experience to infer possible cybersecurity threats
- Experience in analysis in investigations, such as with IT, law enforcement, military intelligence, or business analytics
- Pentesting experience
- Participate in audit review and interview of subject matter experts (SMEs)
- Bachelor’s degree
- 6+ years of relevant experience
- Apply knowledge of cyber best practices, controls, policies, procedure, and standards
- Apply cyber and information privacy approached to systems, networks, services, devices, tools, communications, policies, and business processes
- Document findings for client reporting
- Monitor for and investigate suspicious or malicious activity and alerts
- Review Change Management requests for security relevance and impact
- Daily review of system, application logs, and custom monitoring tools
- Malware and Advanced Persistent Threat (APT) analysis and remediation
- Leading Incident Response and Investigations
- Availability for rotating on-call shift (1 week every 10-12 weeks)
- Bachelor’s degree or 5+ years of related field experience
- Professional Certifications preferred including SANS GIAC, CISSP, Security+
- 5+ years work experience in Information Technology
- 3+ years experience in information security incident response and operations management
- 3+ years of OS, application, and network security weaknesses, vulnerabilities, and remediation
- Experience researching, analyzing, and resolving complex problems with minimal supervision
- Must possess excellent written and verbal communication skills
Cyber Security Analyst / CI Poly / CR Squad Resume Examples & Samples
- Expert knowledge of physical computer components and architectures, including the functions of various components and peripherals, basic programming concepts, assembly codes, TCP/IP, OSI models, underlying networking protocols, security hardware and software
- Proficiency with command line interface for UNIX/Linux and Windows
- Proficiency in writing, editing, executing scripts on Windows, Linux, UNIX systems
- Certifications such as CEH, Security+, SANS GPEN, GIAC, OSCP
- One or more of the following experiences required: Experience with toolsets such as Wireshark, Metasploit, tcpdump, NMap, Nessus, Snort, BRO, EnCase, Forensic Toolkit, Windows Fundamentals, Unix fundamentals, exploitation theory, privilege escalation, evidence removal
- Possess one of the following certifications, or similar certification upon hire or be willing to obtain within 6-months of start date
- Experience with encryption and decryption such as PGP, DES, AES, RSA, PKI
- Experience with Cyber Threats Detection and Mitigation, Behavioral Malware Analysis
- Experience with, Advanced Network Traffic Analysis, Malicious Network Traffic Analysis
- Experience programming in C, C++, C#, Ruby, Perl, Python, SQL
- Certifications such as GXPN, GREM CCNA, CCNP, CCIE, RHCE, CompTIA
- Experience working with correlation environment tools (i.e., ArcSight)
- BS/BA in Computer Science, Information Systems, Software Engineering or other related analytical, scientific or technical discipline or 6 years related experience
- Ability to work independently and also collaborating with others
- Must be motivated and results oriented
- Final DoD TS/SCI clearance with reinvestigation in the last 5 years
- DISA’s HBSS 301 Advanced ePO5.1
- CompTIA Network+
- 1-3 years experience risk managemet framework
- Manage all aspects of Information Systems (IS), data availability, integrity, authentication, confidentiality, and non‐repudiation
- Develop and execute Government approved security policies, plans, and procedures; design and implement data network security measures
- Conduct vulnerability assessments and carries out penetration tests
- Perform social engineering tests and analyzes technical security weaknesses
- Research and maintain proficiency tools, techniques, countermeasures, and trends in computer and network vulnerabilities, data hiding, and encryption
- Develop tools, techniques, training, and countermeasures for computer and network vulnerabilities, data hiding, and encryption
- TS/SCI with active polygraph clearance is required
- Experience working in a cyber-security position
- Experience adapting easily to new and changing technologies
- Experience performing penetration testing and using tools such as Wireshark and Splunk
- Experience supporting the Intelligence Community and expertise with multiple technical applications is required
- Experience working across organizations, managing multiple, high-priority tasks
- Excellent written communication skills are required
Cyber Security Analyst Principal Resume Examples & Samples
- Requires sound understanding of Cyber security systems and process
- Provide systems engineering service support/advisement to the customer on cyber event resolution efforts of suspected and detected cyber network defense (CND) events
- Provide subject matter expertise (SME) support to technical problem resolution capabilities on CNDS components
- Advise customer on performance of the CND systems
- Provide SME support and advise customer on the Indications and Warning functions within the ops center associated with security breaches, intrusions, or illicit activity
- Provide SME support to customer meetings, forums, and crisis action teams
- Bachelors and nine (9) years or more experience; Masters and seven (7) years or more experience ; PhD or JD and four (4) years or more experience
- Bachelor’s degree with 5+ years of Cyber experience or equivalent relevant experience
- Relevant cyber security experience in accordance with the job description mentioned above
- Experience working with IT systems, networks, processes, or requirements
- Proficient with multiple CND tools
- Demonstrated ability to manage multiple tasks and deliverables simultaneously
- Ability to work independently and with a team
- Familiarity with the Customer/Client missions and organizations
- Excellent writing, organization, verbal communication, and presentation skills
- Experience with the Customer/Client Communications Systems Directorate
- Experience working in the Intelligence Community
- Experienced user in Microsoft Office applications (PowerPoint, Word, Excel, etc.)
- Commitment to recognize, understand, respect and operate effectively within various SETA, FFRDC, and Government lines of authority
- Bachelor’s Degree (equivalent experience accepted in lieu of degree) 6 + years of relevant work experience
- Knowledge of Federal and DoD Guidance (DoDD 8500.1, DoDI 8500.2), DIACAP, RMF, NIST, and DoD Certification & Accreditation processes
- Excellent written and organizational skills
- General knowledge of network, server and desktop technologies
- IAT Level III Certification (CISSP or equivalent)
- Acceptable Computing Environment certification
- Bachelors and Five (5) years or more of related experience; or equivalent relevant experience in leiu of a degree
- DoD 8570/8140 IAT II Certification (Security+, GSEC, or SSCP)
- Experience with Cross Domain technologies
- Experience with Information Technology Virtualization o Experience with Cloud IA Technologies
- Experience with Cryptography
- Experience with Public Key Infrastructure
- Experience with Network and Host-Based Intrusion Detection and Prevention Systems
- Experience with Cyber mission Computer Network Defense of space assets o Experience with Cyber Defense Techniques
- Operational Readiness, Verification, and Validation Reviews
- Masters and seven (7) years or more related experience; PhD or JD and four (4) years or more of related experience
- CISSP, or CISM certification o Applies extensive technical expertise and has full knowledge of other related disciplines
- Receives assignments in the form of objectives and establishes goals to meet objectives
- Provides guidance to subordinates to achieve goals in accordance with established policies
- Work is reviewed and measured based on meeting objectives and schedules
- Establishes and recommends changes to policies which affect subordinate organization(s)
Cyber Security Analyst, Expert Resume Examples & Samples
- Applies current Information Assurance technologies to the architecture, design, development, evaluation and integration of systems and networks to maintain system security
- Developing customer technical solutions and enhancement of operational network security that harden networks to protect client's data against cyber attacks
- Providing technical, security, and certification support during the development and testing phases of advance technology equipment
- Developing requirement documents and system design documents
- Participating in technical meetings to gain an understanding of customer requirements and to generate enterprise-wide system-level solutions
- Providing technical support for specific contract tasks, contacts with vendors, and participating in external/commercial technical forums
- Will prepare security documentation, using NIST and VA standards to achieve accreditation of supported systems. Represents program security interests at customer meetings
- Provide support to achieve and maintain full FISMA High Assessment and Authorization (A&A) certification
- Bachelor’s Degree in computer science, electronics engineering or other engineering or technical discipline is required
- Minimum of 10 years experience with information security engineering discipline
- Minimum of 5 years experience with complex security architecture consisting of multiple trust levels
- 5+ years experience provisioning and operation of Security networking equipment, including IDS, Antivirus, AAA, Firewall, Security Gateway, VPN appliances, and SIEM architectures
- Experience with Agiliance Risk Vision tool
- Experience supporting VA Office Information & Technology is desired
- Ability to pass VA Position Sensitivity and Background Investigation
- 82 and DoD 8510.01 Risk Management Framework (RMF) to provide solutions at the programmatic level in the development of complex work products, including analyses, reports, plans, policies, and presentations. This position will require occasional domestic and international travel and will be located in Arlington, VA or Norfolk, VA
- 5+ years of experience with information assurance and security controls
- Experience with building out accreditation packages for MCCAST (USMC) using the Risk Management Framework (RMF) process
- Ability to travel periodically, both internationally and domestically
- Knowledge of Industrial Control Systems (ICS) and IT networking preferred
- 4 year college degree in Computer Science, Management Information Systems, Computer Information Systems, or Computer Engineering
- Industry certifications: Security Plus, Global Information Assurance Certification (GIAC), Global Certified Incident Handler (GCIH), Certified Information Systems Security Professional (CCISP)
- 5 years of experience in IT Security roles or Security Technology
- Familiarity with Symantec Endpoint Protection (SEP) or other Endpoint Protection programs
- Knowledge of Advanced Persistent Threat (APT) activities
- Level IT security policies, processes, and guidance
- Possession of excellent oral and written communications skills in the preparation of client
- Ready, executive
- Level briefings and reports
- Identification of electronic attacks from internal and external sources globally
- Threat assessment of detected attacks and event escalation to the appropriate business area
- Act as 1st line point of contact for detected security events
- Apply decision-making logic and adequately react to security events affecting the business areas of Barclays Group
- Provide CND reports, trends, responses, mitigations, analysis, and information dissemination
- Provide C2 support, situational awareness support, and provide leadership & support for all CND applicable activities
- Support the development, documentation and tracking of measurements & metrics relevant to the ALP’s
- Maintain the integrity & security of enterprise-wide systems & networks
- Support security initiatives through predictive & reactive analysis, and by articulating emerging trends to leadership & staff
- Possess a CompTIA Security+ with Continuing Education (CE) certification
- Experience supporting CND or related teams
- Experience working CND duties
- Strong communication skills (both written and verbal)
- In-depth understanding of TCP/IP protocols, ports, and services
- At least one other IA certification completed, i.e., SSCP, CSIH, GCIA, GCIH or CEH
- UNIX Administrative skills
- Command Line Scripting skills (PERL, python, shell scripting) to automate analysis task
- Performs network traffic analysis utilizing raw packet data, net flow, IDS, and custom sensor output as it pertains to the cyber security of communications networks
- Correlates actionable security events from various sources including Security Information Management System (SIMS) data and develops unique correlation techniques
- Develop analytical products fusing enterprise and all- source intelligence
- Conduct malware analysis of attacker tools providing indicators for enterprise defensive measures, and reverse engineer attacker encoding protocols
- Interface with external entities including law enforcement organizations, intelligence community organizations and other government agencies such as the Department of Defense
- 5 years of professional experience and a Bachelor’s degrees from an accredited college in a related discipline, or equivalent experience/combined education
- CND reports, trends, responses, mitigations, analysis, and information dissemination
- C2 support, situational awareness support, and provide leadership & support for all CND applicable activities
- Supporting teams within a performance-based environment with pre-determined Acceptable Levels of Performance (ALP’s)
- Supporting the development, documentation and tracking of measurements & metrics relevant to the ALP’s
- Maintaining the integrity & security of enterprise-wide systems & networks
- Supporting security initiatives through predictive & reactive analysis, and by articulating emerging trends to leadership & staff
- BS/BA in Computer Science/Engineering (or equivalent)
- 5+ years experience with Network or Information Security support
- Needs to have a keen understanding of threat vectors as well as exfiltration techniques
- Experience hunting proactively for threats within an enterprise
- Experience investigating computer network intrusions in an enterprise
- Security tool integration and process automation via scripting
- Experience investigating intrusions in cloud/hybrid environments is desired
- The ideal candidate will be knowledgeable and passionate about all things cyber
- 5+ year experience with Incident Response
- We prefer someone with 8+ years overall IT Infrastructure experience and 5+ years of recent operational security experience (SOC, Incident Response,
- Malware Analysis, IDS/IPS Analysis, etc
- 3+ years experience with Network and/or Information Security support
- Systems security exposure in at least two Operating Systems (Windows, Linux preferred)
- Strong troubleshooting skills of complex network and security problems
- Strong analytical skills to perform threat, vulnerability, and intrusion detection analysis
- Highly disciplined and motivated, able to work independently, under direction, or as a member of a team
- Must be able to attain a Secret Security Clearance
- Needs to have an understanding of threat vectors as well as exfiltration techniques
- CISSP or other security certifications. CCNA/CCNP or other network certifications
- 1+ year experience with Incident Response
- We prefer someone with 5+ years overall IT Infrastructure experience and 1+ years of recent operational security experience (SOC, Incident Response, Malware Analysis, IDS/IPS Analysis, etc.)
- Responsible for monitoring and auditing ACAS Security Console (SC) and CMRS data feed and report directly to command IAM
- Maintain ACAS date feed, via APS to DISA (Tier I)
- Responsible for assisting SC Administrators with applying patches, ACAS update, STIGS, and plugins
- Provide ATO Certification & Accreditation artifacts for ACAS and CMRS capabilities
- Responsible to ensure SC roll updates as required
- Provide SME level input support for SC Administrators and HBSS Support Admin's
- Must possess at least 5 years of hands on technical experience with a minimum of 5 year of experience in Information Assurance
- 8 years IT experience
- 5+ years administrating servers
- 3+ years with vulnerability scanners
- 2+ years Microsoft SQL server administration
- 1+ years with IIS administration
- NESSUS Scanner experience
- Security Center experience
- Master's degree in Engineering, Computer Science, Business Management, Information Systems Management, or a related discipline, as well as ten (10) years of general experience and six (6) years of relevant experience OR possess a Bachelor's degree in Engineering, Computer Science, Business Management, Information Systems Management, or a related discipline, as well as twelve (12) years of general experience and eight (8) years of relevant experience
- Possess five (5) years of experience providing information technology support services, including information assurance
- Possess, or obtain within the first six months of assignment, the appropriate Risk Management Framework (RMF) training and certification
- Possess, or obtain within the first six months of assignment, an active security-related certification (e.g., CISSP, CAP, or Security+)
- Possess exceptional organizational skills
- Possess excellent interpersonal and communication skills, both oral and written
- Proven ability to participate in the analysis of IT and business issues
- Minimum 2 years' professional experience supporting information assurance or technology delivery to DoD
- Risk Management Framework Training and Certification required within the first six months of employment
- Active security-related certification (CISSP, CAP, or CompTIA Security+)
- Bachelor Degree in Information Technology or related field
- Strong written and verbal communications skills are a must
- B.S. in information systems related major
- MINIMUM OF INTERIM SECRET CLEARANCE REQUIRED
- Provide Level 1 support for Information Security requests; Review security policy clarifications and exception requests; assist in Rubicon Security projects under the direction of a Sr. Security Engineer or a Principal Security Engineer; triage general security questions from other internal teams
- Monitor and analyze network traffic and IDS alerts
- Participate in incident response and triage
- Required Skills, Knowledge and Experience
- Industry Certification such as Security+, SSCP, CEH, etc
- Familiar with; Trend DSM, Splunk, Algosec, Safenet, Vormetric
- 1+ years of experience with different aspects of Information Security including knowledge of network, web and platform technologies and secure application development methods
- Familiarity with TCP/IP protocol
- On-call 24/7 support
- Experience Required: 3+ years relevant experience
- Secret Clearance Required
- Ability to work in a cross-functional team environment
- Ability to work effectively with a broad range of personalities and people
- Flexible, Dependable and Self-motivated
- Willingness to learn new skills from senior peers
- Bachelor’s degree in Computer Science, Cyber Security, Systems Engineering, Information Technology or other related technical discipline, is required
- Knowledge and experience with network infrastructure, modern operating systems, database applications, web applications and other computing technologies is preferred
- At least 3 years of system, network and or applications security experience is required
- At least 3 years of experience as a System Administrator/Information System Engineer is preferred
- Possession of at least two or more of the following Industry Certifications is strongly preferred
- Perform log analysis and monitor and respond to security events
- Respond to security events driving issues to closure engaging all appropriate resources
- Document Security process and procedures
- Support service request in-take process and communicate back to requestors promptly
- Provide enforcement of security policies, standards and procedures
- Staying current on security technologies, trends, standards and best practices
- Continually update skills
- This position will sit in Nike’s 24/7 Cyber Defense Center and will involve shift work including day, evening and weekend roles
- Bachelor’s degree in computer science or related field, or equivalent work experience
- Five years of information technology experience with two years in an information security-related role
- Solid knowledge and understanding of information technology systems and process
- Experience using Splunk for log analysis
- Experience with Unix, Linux
- Computer programming and scripting languages (python, c++, perl, etc.)
- Experience analyzing firewall access control lists
- One or more of the following professional certifications
- Bachelor’s degree and 12+ years of professional IT experience, including Cyber Security. Additional years of experience will be considered in lieu of a Bachelor's degree
- US citizenship required and must possess an active DOD Secret clearance or above (Active Top Secret highly preferred)
- Must have solid knowledge of Security Operation Center (SOC), Computer Incident Response Teams (CIRTs), Network Operations Security Center (NOSC), across Defense, Intel, or other highly regulated environments
- Knowledge in computer forensic methodology and evidence chain of custody
- Demonstrate timely task completion involving solid organizational skills, task tracking, follow-up, and productive peer interaction
- Working knowledge of Defense-in-Depth models traditional and updated
- Analyze, disassemble, and reverse engineer code to discern weaknesses for exploitation; document and transition results in reports, presentations and technical exchanges
- Bachelor Degree or equivalent experience Target of 8 years hands on A&A experience with Navy and/or DoD programs
- Able to work in a highly collaborative and cross-functional team environment
- Highly organized, prepared, and reliable
- Strong analytical skills and can-do problem solving attitude
- Possess and maintain a valid Cyber Security certification for CAP, GSLC, CISM, or CISSP
- Designated as a member of the Cyber Security Workforce at a target IAM Level II in accordance with DoD 8570 and SECNAV Manual 5239.2
- Target of 8 years hands on A&A experience with Navy and/or DoD programs
- Experience with Risk Management Framework (RMF) and/or National Institute of Standards and Technology (NIST) 800- 53 preferred
- Designation as or ability to obtain designation as a Navy Qualified Validator (NQV)
- Potential for teleworking: No
- Work with Cyber Analysts to assist in the remediation of identified vulnerabilities for all IT organizations
- Report on and enhance current metrics surrounding vulnerability management
- Take a lead role in the vulnerability management lifecycle
- Team Leadership experience, taking initiative; providing and following through on solutions
- Proficient with Security related service and process assessments and evaluations based on NIST, COBIT, ISO and ITIL standards
- Knowledge and experience implementing controls based on security regulation. E.g. NIST 800-53
- Effective and excellent oral and written communication, analytical, judgment and consultation skills
Cyber, Security Analyst Resume Examples & Samples
- Configure, implement, manage and maintain security devices as well as provide general knowledge and recommendations for security best practices
- Actioning escalated incidents, problems and service requests in a timely manner
- Owning and managing tickets through to resolution
- Performing audit and analysis functions on client data
- This specialty covers integration, implementation, modification, and coordination of the installation, testing, operation, troubleshooting, and maintenance of hardware and software systems
- Functions may include conducting needs analyses, planning and scheduling the installation of new or modified hardware/software, developing functional and technical requirements and specifications, allocating systems resources, managing accounts, documentation, and access to systems and equipment, monitoring the performance, capacity, availability, service ability, and recoverability of installed systems, implementing security procedures and tools, maintaining systems configuration, managing the installation and integration of system patches updates, and enhancements, and ensuring the rigorous application of information security/information assurance policies, principles, and practices
- Experience / Knowledge of SIEM technology – HP Arcsight ESM
- Very strong working knowledge of security tools such as firewalls, IDS/IPS, A/V, anti-spam, content management, server and network device hardening
- Completion of University or College program in Computer Science; or 5 years of equivalent industry experience in the information systems field
- Proven experience in the design, implementation and troubleshooting of operational security solutions
- Understanding of mitigating controls at the systems, network, and application level (VPN, Firewalls, Intrusion detection and prevention, security information event management systems (SIEM), server hardening and encryption technologies)
Cyber Security Analyst On-call Resume Examples & Samples
- Analyze cyber security requirements, technologies, risks, or issues
- 15+ years of relevant experience
- IT audit experience and CISA certification
- Investigation, escalation, and coordination of information security incidents
- Contribution to cyber threat assessments and ad-hoc security reviews and/or investigations
- Identification of cyber security threads within the Nestlé landscape and workable solutions
- Contribute on the design, development and implementation of new analytic methods for detecting threads
- Review the application design, architecture and implementation, provide the security test recommendations
- Run & Analyze the penetration test (Manual & Automated) and pinpoint the security issues and suggest counter measures for security improvements
- Keep up to date with evolving cyber threats and identify any new and sophisticated methods of detecting vulnerabilities
- Highly customer focused and motivated with willingness to take ownership/responsibility for their work and ability to work both independently and in a team oriented environment
- Demonstrate manual product penetration testing; must be able to simulate a SQL injection without tools, simulate XSS attack, X-Path Injection and etc
- Good understanding of security development lifecycle process
- Knowledge of requirement gathering, planning, and creating test plan
- 6-8 years of hands-on experience in Security Testing
- Understanding of Vulnerability Assessment, Penetration Testing, Application Security Testing, SOC and Managed Security Services
- Should possess relevant university degree and/or professional qualifications (ex
- Intimate knowledge and hands-on experience using various penetration testing tools like Nessus, Web Inspect, Nmap (Slow Scans, Service detection, OS detection, namp Scripts), BurpSuite, Nikto, ZAP & fuzz testing tools like SPIKE, PEACH etc. including manual techniques
- Manual security assessment using browser utilities like developer toolbar, browser plugins
- Knowledge of Wireless networks and Infrastructure Penetration Testing
- In depth knowledge of Networks and Operating Systems
- Knowledge of configuration review of applications, servers, network devices and others
- Knowledge of Web Application Assessment
- Should be able to think "out of the box". Possess ability to implement new attack approaches/vectors
- Knowledge of SAP and/or other non-traditional environment is a plus
- Good understanding of security development lifecycle processes
- Automated Whitebox Fuzz testing using SPIKE, PEACH and/or Other COTS Tools
- Knowledge of open source Ethical hacking tools (Kali)
- Highly motivated with willingness to take ownership/responsibility for their work and ability to work both independently and in a team oriented environment
- Adept at selecting and utilizing appropriate technologies to solve complex problems effectively
- Ability to work within an International team
- Lead security assessments of customer systems, services, and programs, as well as provide oversight to less experienced staff
- Analyze customer processes and configurations to verify that previously identified flaws have been corrected, and document the results
- Develop approaches for industry-specific threat analyses, application-specific penetration tests, and the generation of vulnerability reports
- Develop detailed remediation reports and recommendations for compliance and security improvements across industries based on changing threats
- Develop and update a consistent approach to information security programs and ensure adherence with best practices
- Minimum of 4 years of related experience
- Must possess at least a Secret clearance with the ability to be granted a Top Secret clearance
- Clearly articulates technical requirements and other information in written documentation
- Effectively communicates technical and nontechnical concepts to a variety of audiences
- Communicates well with customer technical staff and management
- Methodically gathers, documents, and presents specific customer requirements
- Follows existing processes and procedures, and propose updates to such. Develop new processes and procedures as necessary
- Works with minimal supervision, set priorities, and give attention to detail and quality
- Demonstrates strong organizational and time-management skills: multitasking, working individually and with a team, having a positive attitude, being self-motivated and reliable, being trustworthy, having strong interpersonal and diplomatic skills, and being able to handle stress in a professional manner
- Demonstrates technical skills in one or more focus areas (i.e. networking, messaging support (Exchange), Active Directory, system administration, etc.)
- Be proficient with Microsoft Office
- Have knowledge and hands on experience with IT architecture and design (e.g., firewalls, intrusion detection systems, virtual private networking, virus protection technologies, LAN/WAN design, and/or general internetworking technologies)
- Understanding of risk management practices and security program development including change management, access control, and physical security
- Understanding of the NIST Special Publications (SP) with emphasis on 800-37, 800-53, 800-53A
- IP network and security engineering experience including a basic understanding of IP routing, quality of service mechanisms, MPLS, and IPsec architectures
- Hands on system administraqtion experience with various operating systems including Windows, AIX, BSD, z/OS, RHEL, SUSE, HPUX, QNX, etc
- Experience with system development lifecycles (SDLCs)
- Experience with change management processes
- Leading large/complex security assessments of customer systems, services, and programs
- Supporting and interacting with customers, at the highest levels, as well as providing oversight to less experienced staff
- Analyzing customer processes and configurations to verify that previously identified flaws have been corrected, and document the results
- Developing approaches for industry-specific threat analyses, application-specific penetration tests, and the generation of vulnerability reports
- Developing detailed remediation reports and recommendations for compliance and security improvements across industries based on changing threats
- Develop and update a consistent approach to information security programs and adherence with best practices
- Bachelor’s degree in a related field, or equivalent
- Minimum of 6+ years related experience
- Experience assessing Federal information systems’ compliance with the Federal Information Security Management Act (FISMA). Specifically, conducting independent security control assessments in accordance with NIST SP 800-53, 800-53A, CNSSI 1253, and the Risk Management Framework (RMF) described in NIST SP 800-37
- Clearly articulate requirements and other information in written documentation and effectively communicate technical and non-technical concepts to a variety of audiences
- Broad understading or knowledge of risk management practices and security program development including change management, access control, and physical security
- Direct experience involving configuration, deployment, and administration of network appliances, operating systems, and databases
- Demonstrated excellent technical skills in one or more focus areas (i.e. networking, messaging support (Exchange), Active Directory, system administration, etc.)
- Demonstrated strong organizational and time-management skills: multitasking, working individually and with a team, having a positive attitude, being self-motivated and reliable, being trustworthy, having strong interpersonal and diplomatic skills, and being able to handle stress in a professional manner
- ISC2 Certified Authorization Professional (CAP)
- Hands-on experience with and knowledge of IT security architecture and design (e.g., firewalls, intrusion detection systems, virtual private networking, virus protection technologies, LAN/WAN design, and/or general internetworking technologies)
- Experience with one or more information security frameworks such as SAS70/SSAE No. 16, PCI, NERC CIP, Nuclear Energy Institute (NEI) 0809, HIPAA, GLBA, SOX, etc
- Broad understanding of risk management practices and security program development including change management, access control, and physical security
- Broad IP network and security engineering experience including a basic understanding of IP routing, quality of service mechanisms, MPLS, and IPsec architectures
- Hands on experience configuring, deploying, and managing mission critical network appliances such as routers, firewalls, IDS/IPS, DPI, etc
- Hands on system administration experience with various operating systems including Windows, AIX, BSD, z/OS, RHEL, SUSE, HPUX, QNX, etc
- Hands on system administration experience with DB2, MS SQL, Oracle, Sybase, etc
- Have a Security+ certification and actively working towards the CISSP
- The qualified candidate will assess network threats such as computer viruses, exploits, and malicious attacks
- Monitor for potential compromise, intrusion, deficiency, significant event or threat to the security posture and security baseline
- Update and maintain standard operating procedures and other technical documentation
- 2-4 years concentration security operations and analysis
- Prior experience working in one of the following
- Computer Incident Response Team (CIRT)
- Experience in the detection, response, mitigation, and/or reporting of cyber threats affecting client networks and one or more of the following
- Experience in computer intrusion analysis and incident response
- Working knowledge of Intrusion detection/protection systems
- Knowledge and understanding of network devices, multiple operating systems, and secure architectures
- System log analysis
- Experience responding to and resolving situations caused by network attacks
- HTTP Headers & Status codes
- FTP Traffic & Status Codes
- At least 1 security certification as stated below
- Or related advanced IT certification
- Speaks English fluently
- Experience with firewalls, routers or antivirus appliances a plus
- Experience working on a 24x7x365 watch desk environment
- Experience with industry standard help desk tools
- Bachelor degree related education or relevant experience
- EDR/Endpoint AV
- TCP-IP and Packet Captures
- Splunk, Kibana, Logstash, Sumo Logic or similar
- Cloud security architectures – particularly AWS and the related tooling
- Operating System internals across Linux & Windows.Security-related professional certification (Crest CRIA/CCNIA/CCMRE/CCHIA, SANS GIAC, GCIH, GPEN, GCFA) is an asset
- Development experience with Python or C++ is an asset
Senior Cyber Security Analyst, Disa Resume Examples & Samples
- Security+ CE, CISSP or equivalent in holding a DoD-8570 IAT Level 2 baseline certification and knowledge of layer 3 router configurations and the ability to troubleshoot/investigate anomalies
- Snort and IDS/IPS monitoring experience
- Ability to obtain a CND-A certification (Certified Network Defense-Architect) within 180 days of start date
- Solid understanding and work experience with TCP/IP, common networking ports and protocols, traffic flow, system administration, OSI model, defense-in-depth and common security elements
- Demonstrated understanding of the life cycle of network threats, attacks, attack vectors, and methods of exploitation with an understanding of intrusion tactics, techniques and procedures (TTPs)
- Familiarity with Lockheed Martin's Intelligence Driven Defense or Cyber Kill Chain methodology desired
- Serve as a Boundary/ACL Operations Engineer supporting our DISA Command Center Network Assurance customer
- Analyze layer 3 router configurations and troubleshoot anomalous activity
- Determine indicators that can mitigate anomalous activity
- Analyze intelligence reports and strategic boundary hardening initiatives and make recommendations based on IAP router tool capabilities
- Perform ACL reviews (Access Control List)
- Strengthen boundary defensive posture and advise on tool capabilities to support ongoing and future operations
- 5 years relevant Cyber Security / Information Assurance experienceExperience with Risk Management Framework (RMF) and eMASSExperience with DoD RMF Assessment and Authorization (formerly Certification and Accreditation) processes
- Experience with development of Cyber Security / IA accreditation documentation
- Experience with vulnerability scanning using ACAS
- CISSP or Security + certificationOperating system certification on Windows or Linux (can be obtained within 1 year)
- BS in Computer Science or other technical field
- 2) Experience working with leading firewall, network scanning and intrusion detection products and authentication technologies. They use - Cisco Sourcefire, but experience with that tool isn't required
- 3) Understanding of Windows/Linux operating systems and command line tools
- *Experience with EnCase Forensic Software is a nice to have***��
- Develop content for enterprise full-packet capture security application, combining big data security information collection, management, and analytics capabilities with full network and log-based visibility and automated threat intelligence from commercial vendor and other government agencies
- Perform daily Intrusion Detection Sensor (IDS) monitoring to ensure that all sensors are active
- Review the Security Information and Event Management (SIEM) tool interface, as the tool correlates and aggregates alert data from multiple IDS sensor types and additional security devices
- Review alerts and packet-level data collected from sensors on a daily basis
- Submit an End-of-shift Report summarizing activities for each shift
- BS or equivalent + 6 Years IT OR 10 Years IT required in lieu of Bachelors
- Must have at least four years experience in full packet capture analysis
- Must have experience conducting analysis at the packet level
- Experience with RSA Security Analytics
- Experience administering UNIX-based systems
- Experience with Python scripting
Junior Cyber Security Analyst Resume Examples & Samples
- Receive, document, and report cyber security events
- Categorize incidents and implement corresponding escalation procedures
- Conduct daily operational update meetings for SOC staff and unscheduled situational update briefings for FAA leaders
- Provide telephone, e-mail and ticket service to customers
- Access, secure and inspect local classified information processing areas
- In addition to required education or equivalent experience; - Minimum four (4) years IT experience
- Experience with intrusion detection systems and threat techniques. (Lateral Movement, Rootkits & Toolkits
- Experience working in a network security environment, such as a Security Operations Center (SOC), Computer Emergency Response Team (CERT), Computer Incident Response Team (CIRT), Computer Incident Response Center (CIRC) or Cyber Security Incident Response Center (CSIRC)
- Experience with business process reengineering, capability maturity model, change management, or process improvement
- Exceptional writing and documentation skills
- You will maintain twenty four (24) hours a day, seven (7) days a week, three hundred sixty five (365) days per year, incident handling capability
- You must be a proven team player with excellent oral and written communications skills
- You must be capable of working on projects independently. Frequent interaction with government client is required
- You must have previous experience working in a network security incident response team, such as a Security Operations Center (SOC), Computer Emergency Response Team (CERT), Computer Incident Response Team (CIRT), Computer Incident Response Center (CIRC) or Cyber Security Incident Response Center (CSIRC). Infrequent (<5%) local travel, infrequent (<5%) long distance travel
- Defines and validates the need for proposed new or improved systems (5%)
- Proactively identify potential security issues in order to advise and consult Exelis on prevention, monitoring and mitigation strategies (5%)
- Maintains and manages corporate DoD 8570 compliance and training/certification program (5%)
- Researches, designs, deploys and manages network-based security protections such as next-generation firewall protections, intrusion prevention, content filtering, web application filtering and malware prevention
- Act as a coach (subject matter expert) to the rest of the team on any network security related issues
- Defines architectural standards to secure corporate and cloud-based data center and application solutions
- Develops policies, procedures and standards relating to the security and protection of corporate data and business functions
- Represents the Information Security team in meetings with customers, business partners and business leadership
- Oversees the work of managed service partners, vendors, and others that perform work on behalf of Williams
- Performs regular network security device configuration audits for compliance with regulations, business needs, and adherence to industry best practices
- Monitors and interprets released indicators of compromise and other cyber threat intelligence, then designs and deploys technical solutions to mitigate them
- Participates in security risk discussions and strategic risk assessment/planning with teammates and peers
- Participates in the development and execution of corporate information security strategies and direction
- Excellent listening and communication skills (verbal and written)
- Creative problem solving and solutions development
- Effective project management including personal time management and ability to multi-task in a fast paced environment
- Demonstrates leadership and ability to work independently
- A Bachelor's degree in IT-related area or 7+ years of associated hands-on IT experience
- Deep technical understanding of core networking technologies (OSI model, TCP/IP and routing protocols, switching, VLANs, network virtualization, etc.)
- Deep technical understanding of operating systems (Unix-based systems, Windows, OSX, IOS, etc.)
- 3+ years’ of recent hands-on technical experience with next-generation firewall platforms such as Palo Alto
- 3+ years’ of recent hands-on technical experience with load balancing, proxying and security technologies such as those provided by F5 Networks products (Local Traffic Manager, Global Traffic Manager, Application Security Manager, and Access Policy Manager, etc.)
- Deep understanding of different cyber security threats, how they propagate through the network and how to configure network devices to protect against them
- Experience with information security incident response and the development of response planning and preparedness policies and procedures
- Experience with deploying and managing remote access technologies (VPN, SSL VPN, etc.)
- Develops reports and other documentation in support of business needs, audit and compliance testing
- Extremely detail oriented
- Experience functioning in a team lead or technical lead role
- Occasional on-call duties
- Disaster Recovery concepts and application
- Experience with virtualization technologies such as VMware and Docker
- Palo Alto certification
- F5 Networks certification
- Cisco certification
- CISSP certification
- GIAC certification
- Understanding of automated threat intelligence feed technologies and protocols, such as STIX and TAXII
- Experience with server and application security tools, such as web application security scanners, vulnerability scanners, etc
- Experience with scripting and/or application development
- Experience with UNIX or Linux management
- Experience with Microsoft Windows Server 2008, 2008 R2, 2012
- Experience with security technologies that are closely related to the networking (IDS/IPS, NAC, WAF) is a plus
- Experience with networking and infrastructure monitoring tools
- Experience with packet capturing, analysis and troubleshooting
- Experience utilizing netflow and other analytics tools
- Experience in SIEM management and tuning
- Experience with threat analytics and the consumption / usage of threat intelligence feeds
- Experience with penetration testing / threat hunting
- Assist in monitoring, incorporation, and analysis of federal security requirements impacting business systems
- Translate federal and organizational cyber security requirements into specifications meaningful to senior management, stakeholders, and Engineering/Operational staff members
- Leverage industry good practice expertise to enhance the maturity of security services offered by the group
- Participate in internal staff meetings and other stakeholder discussions
- Provide process and quality improvement recommendations
- Provide project status updates describing the state of assigned security related deliverables, accomplishments, and significant risk items
- Adhere to local organizational policies, procedures, and practices
- This role requires thought leadership, strong analysis skills, and the ability to interact with varying stakeholder entities
- Ability to lead, advise, and coordinate others
- Strong verbal and written communication skills with the ability to communicate to all levels of the organization
- Security+ or higher level DoD approved 8570 IA baseline certifications. Ability to obtain within 6 months
- Broad understanding of federal security requirements, including
- Knowledge using Microsoft Office products
- Perform A&A activities and monitor status, within eMASS and XACTA for all INSCOM G7/Modernization program office systems and sites
- Provide Confidentiality, Integrity and Availability by identifying appropriate IA controls within accreditation packages and verify implementation is in accordance with DoD and Army IA standards
- 9 years of general IA experience, with a minimum of 5 years of demonstrated experience with program support based on NIST Special Publication 800-37 (Guide for Applying the Risk Management Framework to Federal Information Systems)
- Bachelor's Degree in Computer Science, Information Systems, Engineering, Business, or related scientific or technical discipline
- Risk Management Framework Training
- EMASS Training
- Active TS/SCI based upon an SSBI required
- Bachelor's Degree in Computer Science (or related field) and 3+ years of hands-on working experience in cyber intrusion detection, system administration or network administration
- Cyber intrusion detection, incident response or forensic analysis experience
- Solid understanding of computer network protocols including TCP/IP
- Linux and Windows system administration experience
- Working knowledge of information security issues, trends and leading practices
- Demonstrated analytical skills
- Self-disciplined and self- motivated
- Coding/Scripting experience e.g. Perl, Bash, VB Script, Python, etc
- Experience working with networking and security tools such as Tenable Security Center, McAfee Vulnerability Manager, ELK, Intella and Metasploit
- Certifications such as CISSP, GCIA, CEH, GCIH, GCFA or CSIH
- A self-starter, performing tasks with minimal supervision but working effectively with immediate and cross-functional team members
- Possess excellent analytical and problem- solving skills
- Excellent organizational, detail, multi-tasking and time management skills
- Creating advance queries methods in Splunk or advance Grep skills,
- Firewall ACL review
- Examining Snort based IDS events
- Pcaps, web server log review
- Knowledge of information security programs and processes
- Strong skills and experience in requirements management, especially in the security field
- Work well within a team of professionals in a multi- disciplinary environment
- Strong client engagement and facilitation skills, and the ability to build positive working relationships
- Bachelor's degree (equivalent experience accepted in lieu of degree) in computer science, computer engineering, information systems, cyber security or a related field
- Minimum of five years of directly relevant experience in information systems and information security
- Minimum three years of experience performing Cybersecurity/IA responsibilities including planning, testing, and documenting accreditation packages for Information Technology (IT) systems and networks
- Information Assurance and technical writing skills
- IT experience in System Administration, Linux preferred
- Experience with Android Operating System
- Experience in conducting Application Security scans using HP Fortify
- Tactical networks and information systems
- Server virtualization technologies
- Knowledge of Federal and DoD Guidance (DoDD 8500.1, DoDI 8500.2), RMF, DIACAP, NIACAP, NIST, and DoD Certification & Accreditation processes
- Must meet baseline IA certification requirements for an IAT and/or IAM Level II position per DoD 8570.01-M (CISSP, CISM, CISA, etc). Will consider Security+ as satisfying requirement
- Microsoft Certified IT Professional (MCIPT)/Microsoft Certified Systems Engineer (MCSE)
- VMware Certified Professional (VCP)
- Red Hat Certified Engineer (RHCE), or Red Hat Certified Architect (RHCA), or Red Hat Certified System Administrator (RHCSA)
- US citizenship required and must possess an active DoD Secret clearance or above
- Must be a Certified Computer Forensic Examiner from one of the following
- CCE: Certified Computer Examiner
- EnCe: EnCase Certified Examiner
- CSFA: CyberSecurity Forensic Analyst
- Previous experience with Splunk (Splunk Power User)
- Performs forensic analysis of digital information and gathers and handles evidence
- Identifies network computer intrusion evidence and perpetrators
- Investigates computer fraud or other electronic crimes, crack files and system passwords, detects steganography and recovers deleted, fragmented and corrupted data from digital media of all types
- Ensures chain of custody and control procedures, documents procedures and findings in a manner suitable for courtroom presentation and prepares comprehensive written notes and reports
- May be required to testify in court as expert witnesses
- DoD 8500 Series / NIST SP 800 Series
- Navy Cross Domain Solutions Off
- Knowledge of Cybersecurity aspects of MILSATCOM/GPS
- Knowledge of C41/IT products
- IA Level II certification
DP Ns-cyber Security Analyst Resume Examples & Samples
- Be responsible for the identification of network attacks from internal and external sources
- Act as a member of the team to identify incidents and threats
- Utilise processes and technologies to detect and prevent malicious attacks
- Respond to security events, from detection, analysis to closure
- Ensure availability and security of the network infrastructure due to adequate security systems and mechanisms, pro-active monitoring, resilient technical design and effective capacity planning
- Identify network vulnerabilities
- Specification of change control procedures for networking security systems and work with the ITIL service desk to schedule changes
- Act as technical mentor to other IT staff
- Maintain documentation of proposed & deployed infrastructure
- Manage, monitor and backup of firewalls, security appliances, spam filters IDS etc, remote access solutions, VPN’s, third party suppliers and vendor relationships
- Contribute to Business Continuity Planning
- Ensure IT Disaster recovery is planned and tested for all services
- Actively seeks new or alternative ways to complete project
- Identify key or underlying patterns that could affect present or future service performance
- Networking security experience in an enterprise environment
- A good understanding of network security technologies and processes including and understanding of current and emerging security threats and an awareness of systems and methods to counter them
- Knowledge of TCP/IP including routing protocols, management protocols, IPSEC VPN’s, SSL
- Good communication skills enabling interaction with all levels of the business (including written and oral communication where appropriate)
- Proactive and highly motivated, a robust individual who drives their own success
- Analytical and logical thought processes, ability to relate and coordinate requirements across the business or develop structured solutions
- Customer focussed, service driven
- Strive to make systems, services and processes more efficient
- The ability to work to targets in a flexible manner individually or as part of a team
- Broad understanding of security techniques and technologies including Intrusion Detection, Threat Analysis and Malware & Trojan Research
- An understanding of the current and developing Malware & Trojan landscape
- Knowledge of full packet capture technologies
- Knowledge of correlation tools and SIEM technologies
- Sandbox technologies
- Knowledge of log analysis tools and techniques
- LAN/WAN experience
- Able to demonstrate the Drax values of Honest, Energised, Achieving and Together
- Cisco Security Products
- VPN Remote Access Technologies
- Please note that proof of qualifications will be requested at interview
- Interact with, configure, and troubleshoot network intrusion detection devices and other security systems via proprietary and commercial consoles, both local and remote
- Linux/Unix and Windows operating system navigation and administration, working from the command line (vs using a GUI)
- Packet analysis, and related tools (tcpdump, Wireshark, ngrep, etc.)
- Using and recognizing regular expressions
- Database queries and structures
- Highly professional communication (written and verbal), teamwork and customer service skills -Attention to detail and great organizational skills
- Problem solving, and ability to diagnose and troubleshoot technical issues
- Ability to work both independently and collaboratively with peers, across teams, and with management
- Strong passion for learning new technology and concepts quickly
- Under limited supervision, investigate incidents that are escalated per procedure. Communicates with customers as appropriate, keeping Cyber Security Operations Center (CSOC) management informed per incident severity requirements. Follows applicable processes and procedures while maintaining the flexibility to “think outside the box” during the investigation in order to find all affected systems including “patient zero” performs root cause analysis; determines attribution if appropriate; completes documentation; and participates in lessons learned post mortem. For high severity level incidents function as a team member of the incident team, interfacing with outside incident response personnel as well as both senior and junior cyber associates
- Creates, revises and maintains processes and procedures related to continuous monitoring, triage, incident analysis and incident response activities. Consults with other cyber associates to continuously improve those processes and procedures and ensure that when new tools or external inputs change that the documentation is adjusted accordingly
- Mentors and trains junior cyber associates on proper investigation techniques, documentation requirements and evidence handling. Serves as a technical consultant to those associates. Functions as a technical contact for managed security service provider (MSSP) analysts when technical questions arise, consulting with senior analysts and management for guidance as appropriate
- Performs rule creation, system tuning, rule tuning and threat intelligence integration in order to improve the detection capabilities of the security systems
- Communicates with CSOC management, cyber and information security staff members and customers in written and verbal communication regarding investigations and status updates. Maintains need-to-know discretion for all investigations
- Interfaces regularly with the Cyber Security Engineer to test and improve custom tools, suggesting features and improvements in order to improve efficiency and productivity. During investigations, communicates with the engineer in order to quickly gather the information needed in the most efficient manner possible, giving constructive feedback on custom tools provided in that process
- Performs knowledge sharing with team members through meetings, presentations and written communications. Creates, revises and maintains documentation of incident response processes and procedures in the central knowledge base
- Participates in after-incident lessons learned meetings to give input on recommendations for process or procedure improvements and to provide mitigation recommendations to reduce future incidents or minimize their impact
- Potential on-call support during nights and weekends
- Performs other duties as assigned by management
- Demonstrated experience in threat detection technologies including: intrusion detection and prevention systems (IDS/IPS), security incident and event management (SIEM) technology, and network packet analyzers. Experience with security data analytics, endpoint protection, malware analysis, and forensics tools are highly desired
- Demonstrated SIEM utilization skills, including the ability to review and analyze security events from various monitoring and logging sources to identify or confirm suspicious activity
- Demonstrated experience in incident analysis and response activities, including execution of response and analysis plans, processes and procedures and performing root cause analysis. Experience in a SOC environment is preferred
- Demonstrated ability to analyze large data sets and unstructured data for the purpose of identifying trends and anomalies indicative of malicious activity
- Proven knowledge of current security trends, threats and techniques. Demonstrated self-driven desire to continually learn and grow in knowledge related to the constantly evolving threat landscape
- Proven experience on both Linux-based and MS Windows-based system platforms with a strong IT technical understanding and aptitude for analytical problem-solving
- Demonstrated strong understanding of enterprise, network, system and application level security issues
- Proven understanding of the current vulnerabilities, response, and mitigation strategies used in cyber security
- Demonstrated strong team player – collaborates well with others to solve problems and actively incorporates input from various sources. Proven experience motivating fellow team members toward excellence and project completion
- Demonstrated customer focus – evaluates decisions through the eyes of the customer; builds strong customer relationships and creates processes with customer viewpoint
- Demonstrated analytical skills – continuously defines problems, collects or interprets data, establishes facts, anticipates obstacles,and develops plans to resolve; strong problem solving skills while communicating in a clear and succinct manner effectively evaluating information/data to make decisions
- Demonstrated inherent passion for information security and service excellence
- Proven excellent verbal and written communication skills; frequently expresses, exchanges or prepares accurate information conveying information to internal and external customers in a clear, focused and concise manner. Continuously conforms to proper rules of punctuation, grammar, diction and style
- Demonstrated self-starter with strong internal motivation. Proven ability to work with general supervision or direction
- Proven ability to work under multiple deadlines with general supervision. Cite examples of successfully organizing and effectively completing projects where given minimal direction
- Demonstrated ability to perform an activity such as: preparing and analyzing data and figures; transcribing; viewing a computer terminal; extensive reading
- Linux-based and MS Windows-based system platforms
- Fundamental or greater understanding of encryption technologies
- Basic experience with one or more scripting languages (examples: Python, Perl, Java or Ruby)
- Knowledge of Identity & Access Management practices, systems and controls
- Experience with security tools including but not limited to IDS (snort or suricata preferred), IPS, data analytics software, SIEM solutions (QRadar preferred), web application firewall (WAF), malware analysis, knowledge base platforms and live response/forensics tools
- Experience with privilege identity management processes, solutions and products, plus
- Knowledge and use of CyberArk product, a plus
- Support projects related to Credential management, non-human identity and Privilege access management work stream. Specifically: develop and manage project schedule, dependencies resources; define and manage risks and issues; write and deliver project status; and, coordinate across work streams
- Demonstrated ability to provide subject matter expertise to develop options and recommended solutions
- Ability to coordinate and communicate to large diverse groups of both technical and non-technical stakeholders leveraging strong command & control skills
- Excellent verbal and written communication skills and strong facilitation and influencing skills. Ability to engage with broad range of and enterprise stakeholders across all levels (staff to executive management)
- Coordinate and manage public keys and certificates within the environment, as well as mitigating cyber security vulnerabilities associated with the area of focus
- Provide cyber security support to business and technical teams in the design of standardized products and customized solutions. Must be flexible to continuously changing demands and technologies and have the ability to maintain a library of security tools used as part of this function
- Bachelor’s degree with a concentration in computer science, technology, accounting or business or equivalent combination of education and experience
- Minimum of 5 years experience in I/T including 1 years direct experience in cyber security
- Demonstrated verbal/written communication and presentation skills
- Working knowledge of cryptography, key management and security concepts and solutions
- Experience maintaining and operating public key management and certificate solutions, with specific experience working with PKI discover and management platforms (Venafi preferred)
- Hands on data analysis experience, preferably in the Access Management domain. Perform analysis of risk assessments, governance violations related to privilege access, and other data to identify operational risks and trends
- Ability to absorb information and data from multiple sources, apply strong analytical skills, and provide thoughtful and strategic recommendations to deliver tangible business value
- Good general understanding of the data concepts (Data Quality, Data Modeling, etc.) with emphasis on Metadata
- Demonstrated high proficiency in SQL, MS-Excel and MS-Access
- Utilizes COTS/GOTS and custom tools and processes/procedures in order to scan, identify, contain, mitigate and remediate vulnerabilities, and intrusions
- Candidate will develop, test, and evaluate computer system interoperability and execute detailed computer systems analysis and design. Additional Tasks may include: — Configure and maintain IDS/IPS systems
- Continuously monitor networks for defense and abnormalities
- Periodic and monthly inspection/scans of networks to validate/update network devices and systems
- Support projects during execution events with: 1) installing and operating cybersecurity tools on event networks, 2) scanning and providing residual risk statements for hosted mission systems, and 3) CND support at off-site locations and visitor/device management during on-site events
- Generate and review accreditation package artifacts in accordance with DoD 8510.01 and NIST 800-53R4 Required
- Must meet at least one of the following requirements and the experience must have been obtained within the past three (3) years
- Two (2) years’ experience in classified and unclassified computer hardware and software diagnostic procedures, Windows 7/8/10 including Servers 2008R2, 2012R2, UNIX, and knowledge in LINUX Red Hat or later operating systems and environment
- One (1) year experience in computer diagnostic, file defragmentation, file backup, file recovery, and LAN management procedures used in fault isolation of hardware and software
- One (1) year experience in Virtual Environments
- Manage and maintain CND tools, including scanning systems, IPS and IDS systems. Perform cyber vulnerability management (Windows, Linux, Solaris, etc.)
- Support Cybersecurity team in preparation of accreditation packages
- Track and enter system IAVA compliance in CMRS or EMASS
- Experience analyzing operating systems (Microsoft, Linux, Solaris) for compliance with DISA STIGs
- Experience with CND tools, including commercial scanning tools i.e. Nessus, HBSS, and ACAS
- Effective communication skills and basic technical writing experience
Mceits Cyber Security Analyst Resume Examples & Samples
- Maintain DIACAP/RMF package throughout and provide inputs to the customer
- Use IA scans so that security remains high
- Update DIACAP/RMF packages (NIPR/SIPR) to meet DIACAP and USMC policies
- Produce a report of the weekly scans and detail issues or concerns
- Create ATO POA&M entries for items (such as patches) that will take additional time to research to prevent potential negative effects by testing changes to the environment prior to implementation
- 8570 Information assurance technician (IAT) level II or III
- DIACAP/RMF experience
- DISA Stig Viewer, DISA SCC Tool, SCAP Tools
- Detect threats or anomalous behavior within the network, for users and on hosts
- Assess the risk posed by the threat or anomalous behavior
- Take appropriate actions required to, contain, remediate the threat and reduce risk to the organization
- Identify critical situations that need to be escalated to the special operations group and/or the incident response team
- Experience with vulnerabilities and remediation
- Experience with threat and attack methodologies
- Experience with DLP solutions
- Experience with scripting (Python preferred)
- Experience analyzing OS security event logs
- Experience with malware detection
- Design a matrix of the legislative and policy requirements mapped against security deliverables. Identify audit points that can validate compliancy and work with Compliancy teams to establish ownership and audit points throughout the year
- Where appropriate, attend weekly project, program, and change meetings with the Service Providers (SCPs), the client, and its customers. Provide guidance, coordination, and communications to aid in all aspects of security delivery, process development, and maintain a cohesive security delivery environment
- Integrate the Service Provider's Logical Security Administration process with client's, client's customers, other Service Component Provider's, and Third Party Vendor(Vendors)' Logical Security Administration processes, where the processes interact
- Develop a Client Security Guiding Committee to discuss the Security Program. Establish a formal quarterly meeting schedule for the exchange of current security information between all members
- Integrate SCP Security plans into a single Client plan for maintaining security across the entire support environment. Audit for compliancy and update annually at a minimum. Deliver appropriate Security Plan documentation outlining our high-level activities such as security assessment, security governance, security awareness training, Client assistance, Roles and Responsibilities, auditing, systems and tools, cross-tower relationships and communication paths, and security DB development and reporting
- In conjunction with the Client and its customers, identify KPI's for effective execution of the Security Plan. Develop a dashboard for monitoring KPI's
- Work with the SCPs to provide reporting on management and the execution of the Security Plan
- Provide SCP oversight for the regularly review, capture learning and improve on Security, and the execution of the Security Plan
- Develop a forward-looking schedule for the planned Security testing, assessments, and analysis
- Provide for and facilitate the annual risk assessment. Guiding the SCPs, provide for security evaluations, which include conducting internal audits, supporting external audits, conducting self-assessments, and evaluating security incidents. Create a security risk register for the consolidation and documentation of risk management and assessment activities
- Cooperate and assist with efforts by the Client, Client Customers and/or representatives of the Client for security tests (e.g. audits, Third Party security tests, the annual Control Penetration Test)
- Provide for vulnerability scans for all network assets at least once per year
- Engage Finance, Purchasing, and other towers where required to develop solution alternatives, identification of costs, and vendor negotiations for alternative cost models. Monitor activities being progressed to address shortfalls in Security for Services
- Provide detailed descriptions of the potential benefits and exploitation opportunities that exist for planned technology upgrades and the effort required to realize these benefits
- Document and identify security risks associated with the Services, and in support of Risk Management. Recommend solutions or mitigation for vulnerabilities or weaknesses in services
- Work closely with Change Management and application development and implementation teams for reviews during the technology reviews and SDLC
- Ability to self-manage with little interaction from other management staff
- Flexible and able to adapt to manage a fast-changing environment
- Ability to Multi-Task
- Ability to pull diverse teams
- 5 to 7 years of experience in system / network / product penetration testing
- Having Bachelors in any discipline
- Knowledge of attack frameworks like VASTO, Virtualization Assessment Toolkit to exploit virtualization systems
- Knowledge of Specific virtualization platform attacks and exploits
- Good communication & Negotiation skills
- Knowledge on domain understanding about the HVAC control systems, controllers, sensors etc
- CEH Certification is Mandatory. Additional certifications such as OSCP, CCSP, CCSK will be highly desirable
- Strong software engineering skills
- Ability to manage multiple initiatives simultaneously
Cyber Security Analyst Level Resume Examples & Samples
- Collect, analyze, and disseminate relevant cyber threat intelligence
- Obtain and disseminate threat actor knowledge
- Analyze current cyber events in the media
- Document attacks, work with investigators, and combine with external intelligence
- Provide technical data gathered about intel
- Provide new rule sets to security tools not managed by our team
- Oversee process to manage whitelists and blacklists
- Large scale implementation of McAfee DLP endpoint technology for the entire company and accountable for the availability, reliability and performance of the platform
- Implementation of Discover and file permission solution across the organization and define process to mitigate access control issue
- Collaborate with IT infrastructure/Application teams and business security leaders to define and gather Data protection requirements
- Consolidate and validate business assumptions relevant to the solution strategy, prior to initiating and throughout the process
- Understand the company’s IT Infrastructure/Applications, Business model/processes, Security controls and develop detection models
- Publish global and business level deployment metrics reporting dashboard
- Having 6-8 years of hands-on experience on McAfee DLP, Varonis, Stealth bits
- Hands on experience in configuring and implement DLP rules across venues Data in motion, Data at rest and Data in use
- Hands on experience in implementing Discover solutions like Symantec, McAfee, Kazeon or Stealthbits
- Strong troubleshooting skills in fixing McAfee DLP endpoint issues
- Strong knowledge on Linux or UNIX platform
- Ability to write scripts in Perl or python
- Good knowledge on Office 365 features and security controls
- Provide technical expertise and mentoring to peers
- Strong experience with handling malicious code and management of anti-malicious code technologies
- Strong experience with managing email, Internet and anti-virus security controls
- Understand security requirements for ICS (industrial control systems)
- Strong oral and written communication, and presentation skills
- Ability to work with a cross functional team and handle multiple tasks and priorities
- 5+ years of experience in a hands-on security analysis or security engineering role
- Specific understanding of application and operating system hardening, vulnerability assessments, security auditing, TCP/IP & network fundamentals, intrusion detection systems, firewalls, VPNs, WAFs
- Solid understanding of hybrid-cloud environments and how they present specific challenges to the security field
- Expertise with network firewalls, PKI, vulnerability scanners, zero-day/ATP, anti-virus, forensics, email security technologies, forensics software, SIEM, HIDS/NIDS//IPS, malware analysis and protection, content filtering, identity and access management, data loss prevention, content filtering technologies, application firewalls, security incident response techniques
- Expertise with threat hunting and threat assement
- Knowledge of NIST 800-53 controls
- Background with ITIL/ITSM processes
- CISSP, CEH, CSSLP or equivalent is a plus
- Works well under pressure and can resolve complex problems
- Excellent communication skills, presenting, listening and informing. Can communicate up, down and across the organization
- Adhere to eCPGI Core Values: Accountability, Integrity, Efficient, Effective, Fulfillment, Respect, Positivity, Commitment to Excellence
- Work with subcontractors and commercial vendors in the selection and evaluation of secure operating systems, cybersecurity applications, networks, hardware, databases, etc
- Present information in a positive manner to management and customers
- Works in a collaborative fashion, elevates team results over individual results
- Work on multiple simultaneous tasks
- Apply advanced technical principles, theories, and concepts to solutions
- Work on unusually complex technical problems and provide solutions which are highly innovative
- Experience in Identity and Access Management implementations
- Agile Experience
- Strong communication skills as position will require effective to communication to business stakeholders
- Demand Management experience
- Application on-boarding experience preferred
- 0-2 years of knowledge of common enterprise applications, e-mail, web, cloud, client/server required
- Knowledge of information systems security concepts and current information security trends and practices including security processes and methods
- General knowledge regarding NIST, HIPAA, FIPS, and other recognized industry security standards and best practices
- General understanding of DLP and DLP technologies
- Working understanding of the anatomy of an attack
- General understanding of using Microsoft windows workstation and server, Unix/Linux and network OS’s
- Proven ability to use Internet Technologies including DNS, routing, SMTP, HTTP, DHCP, and FTP etc
- Written/verbal interpersonal communication skills with the ability to interact effectively with a broad and diverse group of peers, users, and executives
- Proven ability to prioritize work while multi-tasking on assigned work
- Ability to perform and conduct Incident Response and participate in security incident and post incident response process
- Implement mitigation measures to ensure that appropriate treatment is applied depending on the nature of the security threat perceived as well as ensure that the customers and management notifications as is appropriate
- Take proactive measures to manage all security perimeter equipments, intrusion detection systems, manage identity and access programs, data correlation tools and or system components as may be required to interrupt or affect the above threats
- Completion of University or College program in Computer Science or three years of equivalent industry experience in the information systems field
- Knowledge of security event/incident management systems
- General comprehension of mitigating system controls, networks and applications (VPN, Firewalls, Intrusion detection, server hardening and encryption technologies)
Internal Cyber Security Analyst Resume Examples & Samples
- A bachelor’s degree in Computer Science, Information Security or a related subject or equivalent industry experience
- Broad knowledge of a wide range of Information Technology systems and a deep understanding of the inherent security risks associated with these technologies
- Ability to present security topics to a non-technical audience and presenting the business value of security
- Excellent interpersonal skills with the ability to build and influence teams; and Self-motivated and able to deal with multiple projects
- Fluent in English, German is a strong plus
- Install, maintain, monitor, troubleshoot, and decommissions sensor devices
- Configured in accordance with DOT and SOC standards
- Maintain configuration control of all signatures and test them before being deployed in the operational environment
- Evaluate and test all upgrades and patches prior to deployment in production
- Identify requirements for additional sensor locations which will enhance the situational awareness capability
- Underlying factors affecting the expansion of sensor deployment will be the results of the ongoing Network Mapping task and the continued installation of Intrusion Detection Sensors
- Coordinate and assist local personnel in the installation of network intrusion detection systems as approved by the COR or SOC management
- In addition to required education or equivalent experience
- Minimum three (3) years IT experience
- Experience with the following
- Analyze reports to understand threat campaign(s) techniques, lateral movements and extract indicators of compromise (IOCs)
- Understand and convey of the lifecycle of the network threats, attack vectors, and network vulnerability exploitation
- Maintain awareness of directives, orders, alerts, and messages
- Maintain situational awareness of cyber activity in the Information Technology (IT) by reviewing open source reporting for new vulnerabilities, malware, or other threats that have the potential to impact the organization
- Familiar with signatures, tactics, techniques and procedures associated with preparation for and execution/implementation of such attacks
- Experience with intelligence briefings
- Experience with intelligence products
- Experience with early indications and warnings
- Experience with Open Source intelligence techniques
- Experience working in a network security incident response team, such as a Security Operations Center (SOC), Computer Emergency Response Team (CERT), Computer Incident Response Team (CIRT), Computer Incident Response Center (CIRC) or Cyber Security Incident Response Center (CSIRC)
- Minimum four (4) years IT experience
- You must have previous experience working in a network security incident response team, such as a Security Operations Center (SOC), Computer Emergency Response Team (CERT), Computer Incident Response Team (CIRT), Computer Incident Response Center (CIRC) or Cyber Security Incident Response Center (CSIRC)
- Infrequent (<5%) local travel, infrequent (<5%) long distance travel
IT Security Analyst / Cyber Security Analyst Resume Examples & Samples
- Acts as the lead ISSO for the IT Operations team
- Liaison between Cyber Security Team and ITO
- Manages Cyber Security compliance roles for the IT Operations team including risk compliance, vulnerability/patching, standard operating procedure & processes, configuration compliance and related roles
- Supports development and upkeep of relevant System Boundaries and including authorization packages, progress reporting, etc
- Manages and maintains POAMs
- Manages technical hardware / software inventory as it relates to security
- Coordinates physical security management and monitoring for department assets
- Coordinates IT Operations team participation in support of security incident response
- Prepares monitoring and management reports, as necessary, in support of relevant responsibilities
- Participates as a fully integrated member of assigned project teams, responsible to the delivery of successful solutions
- Contributes to the team support for ITO event management including investigation, troubleshooting, reporting, resolution, root cause analysis and corrective action management
- Monitors system performance, security and stability – takes action to identify trends and proactively inform management of issues
- Information Security, 4 - 6 Years
- Infrastructure Platforms (PC, Client/Server. Mainframe), 4 - 6 Years
- Server Infrastructure, 4 - 6 Years
- GM-ISP&P-Information Systems Security Policies & Practices, 4 - 6 Years
- IT Security Administration, 4 - 6 Years
- Relevant work experience in the areas of Security Compliance, Vulnerability Management and/or related disciplines
- Demonstrated experience supporting Infrastructure Services in an enterprise environment
- Demonstrated success participating and/or leading complex enterprise-level projects with focus on disciplines related to Servers, Storage, Mainframe, and/or End User Computing
- Experience leading security-focused change initiatives within complex technical teams including process development, compliance monitoring and team coordination
- Results-oriented member of technical support teams; the successful candidate is a self-starter, able to manage complex incidents, proactively identify opportunities for improvement and develop innovative solutions
- Excellent time management skills including ability to multi-task and effectively prioritize work
- Excellent work ethic; willing to extend the extra effort and time required to meet critical deadlines
- Strong oral and written communications skills; able to articulate ideas and listen effectively; professionally communicates with all customers, vendors and technical support staff, including remote customers and team members in foreign countries
- Strong analytical, and problem-solving skills
- Accomplished analyst able to manage complex technical problems through identification, design, solution definition and implementation
- Demonstrated experience managing vendor relationships related to incident management, project coordination, relationship development and SLA maintenance
- On call support required for incident management
- Hands-on team member willing to work in heavy industry/plant environments when required (very limited)
- Demonstrated experience managing, supporting and/or developing Cyber Security compliance for technical project teams with focus in the areas of
- Lean / Six Sigma practice (Green belt or greater preferred)
- Hands on experiences using and/or developing compliance and monitoring process using the RSA Archer toolset
- Experience with Cyber Security framework (NIST)
- Vulnerability scanning and related tools (Nessus)
- Cyber Security or other related professional certifications
- X86 Server Management and Administration
- Symantec Endpoint protection
- Landesk management suite
- Conduct vulnerability/compliance assessments, to include analysis on AF/DoD systems
- Assist team with defining, implementing, and documenting IT and cybersecurity policies and tactics, techniques, and procedures for conducting assessments and resolution
- Demonstrate an ability to methodically and proactively analyze problems and identify solutions
- Candidate must also be able to adequately report how a vulnerability was exploited and quantify the overall impact would be to the particular system
- US citizen with active DoD Top Secret clearance and be SCI eligible
- Possess an active ISC2 CISSP certification or possess a CompTIA Security+ certification and willing to obtain a CISSP certification to meet DoD 8570 IAM Level 3 requirement
- Familiarity with Oracle and My SQL databases
- Well versed in common Cyber Threat terminology, vulnerability and penetration test principles and methodologies, possess basic knowledge of cyber incident and response, and related current events
- Familiarity with DISA STIGs, NIST SP800-53.x requirements, and experience in conducting DoD vulnerability/compliance assessments
- Minimum 5 years working with and in a network systems security environment with a focus on security and information assurance
- Willing to complete pre-screen assessment, comply with contract and customer training and certification requirements
- Possess strong written and verbal communication skills to include the ability to render concise reports, summaries, and formal oral presentations
- Well versed with the Microsoft Office Suite (MS Word, MS Excel, MS PowerPoint)
- Minimum Bachelor’s degree in related field
- Experience with Power Shell, SED, AWK, Perl, Python, bash, etc
- Experience with Networking and storage solutions such as NetApp
- Experience with shell programming and the UNIX environment
- Experience or familiarity with military operations and/or supporting a mission system
- Respond to incident and perform root cause investigations for access service systems and the supporting infrastructure, often in partnership with other teams
- Manage change coordination and validation, including OS, database and middleware patching / upgrades, application releases and other infrastructure changes
- Produce reports and dashboards regarding system health and other operational metrics
- Lead projects as related to technology refresh/evaluation such as Load Balancing and SSL technology. Implement tools, infrastructure and other capabilities to automate / optimize Access systems operations. Research corrective measures (long-term solutions) needed for any chronic issues identified that compromise security of particular systems or platforms
- Advanced installation, administration and maintenance knowledge of UNIX and/or Windows Server operating system; web technologies; communication protocols; security standards; and technical project management
- Excellent knowledge of relational databases (Oracle, SQL Server, Sybase) and SQL
- Solid experience in the administration and performance tuning of application stacks (e.g., Tomcat, JBoss, Apache)
- Solid scripting skills (e.g., shell scripts, Perl, PowerShell, Python)
- Solid networking knowledge (LAN/WAN concepts, OSI network layers, TCP/IP)
- Experience with directories and LDAP protocols
- Desirable hands-on experience with implementing / supporting one or more of these products
- Analyzes problems associated with the mission
- Builds stable working relationships internally and externally
- Professionally applies company policies and procedures to resolve routine to complex issues
- Identifies creative ways to solve problems related to the mission and works with other analysts and the program manager to implements the solutions
- Works with other analysts, managers, customers, and sponsors regularly, and creates a reputation for technical prowess and leadership skills
- Works independently and with project teams easily
- Principles and practices of network security monitoring
- Experience building and managing SIEM platform, use cases, and content
- Escalation point for security services incidents or complex changes
- Training of peers, briefing customers, and other Seattle Genetics organizations outside operations
- Planning and overseeing security patching, signatures, and code upgrades
- Stay abreast of cyber security issues by research of industry trends, viewing watch lists, and by other means to keep Seattle Genetics’ security posture up to date
- Excellent customer services skills, proven technical expertise in Information and Network Security, and well-rounded understanding and command of the fundamentals of network routing, TCP/IP and Network Security
- Monitoring and analyzing logs and alerts from a variety of different technologies (IDS/IPS, Firewall, Proxies, Anti-Virus, etc…), across multiple platforms
- Assessing the security impact of security alerts and traffic anomalies on networks
- Creating comprehensive security write-ups which articulate security issues, analysis and remediation techniques
- Gather, maintain, and analyze cyber-security data and other key performance indicators for regular executive review
- Responding to technical security questions and concerns from the business
- Maintaining a strong awareness and understanding of the current threat landscape
- Occasionally supervise and direct junior analysts during incident triage and investigation
- Use technical dexterity to choose the right tool and how to use it effectively across a range of security scenarios
Senior Cyber Security Analyst / , V-soc Resume Examples & Samples
- This position could be a salary grade 3 or 4 depending on combined level of education and work experience
- Can demonstrate critical thinking and problem solving skills
- Possess good time management and written and oral communications skills
Cyber Security Analyst Hbss Resume Examples & Samples
- Analyze and report HBSS incidents to CERT responders
- Deploy and configure McAfee point products such as VirusScan Enterprise, Rogue System Detection, Policy Auditor, and Data Loss Prevention / Device Control Module
- Performs analyses at all levels of total system product to include: concept, design, fabrication, test, installation, operation, maintenance and disposal
- Assists in ensuring that customer or product requirements are converted into total systems solutions
- Bachelor’s degree in related field or equivalent; advanced degree preferred
- Minimum of 8 years work related experience with at least 4 years of related HBSS technical experience
- Candidates must have a DoD SECRET level security clearance
- Current DoD 8570 IAT level II certification (Security+ or equivalent)
- Experience managing and certification in Windows or Linux OS
- Strong SQL skills and experience
- McAfee / Intel Security Certified Product Specialist Certification
Cyber Security Analyst, Associate Senior Resume Examples & Samples
- Provide subject matter expertise on enterprise cyber security risks, threats, technologies, and potential impact
- Interview customer IT leadership and technical personnel regarding cyber security controls and processes
- Assist in designing and implementation of cyber maturity models to evaluate the effectiveness of an organization’s cyber program
- Translate technical discussions and information into non-technical material for presentation to leadership
- Mentors and supports peers and junior staff in technical growth
- Experience conducting assessments or evaluations using security frameworks
- Knowledge of cyber security technologies across the industry. Experience in evaluation or comparisons of various technology verticals is preferred (such as firewalls, HIDS, IDS/IPS, malware analysis, end point protection)
- Strong skills using Microsoft Office Suite (Word, Excel, Outlook)
- Experience working with SIEM, packet capture solutions, endpoint solutions, API integrations, virtual infrastructure, system hardening, and forensic technologies
- Ability to clearly communicate technical information to a non-technical audience
- Advanced knowledge of Windows, Linux, and Mac infrastructures
- Work effectively as part of a cohesive team or as an individual contributor
- Familiarity with security concepts like risk, vulnerabilities, data management, confidentiality, access controls, etc
- 3+ years of cyber operations, engineering, and / or architecture experience
- 1+ years government related cyber security experience
- Experience working with NIST
- Experience with the Risk Management Framework
- Experience analyzing data
- Experience with security compliance for web applications
- Good communication skills and experience interfacing with technical teams for compliance purposes and non-technical clients
- Needs to be detail oriented, needs to like documentation
- 3+ years of experience with Cybersecurity and vulnerability risk assessments
- Experience with DoD Operational Test Agencies (OTA)
- Experience with Cybersecurity as it relates to DoD acquisition life cycle
- Experience with the principles of IA, including confidentiality, integrity, non–repudiation, availability, and access control and security testing
- Ability to perform in a military environment
- Ability to travel for approximately 25% of the time to stateside and international locations
- Ability to analyze and write technical documents
- Experience with an Air Force or DoD Certification and Accreditation program, developing or analyzing POA&M’s, SIP, DIP, and security test and evaluation reports
- Experience with evaluating IA compliance of a system against current DIACAP, Risk Management Framework, and DoD Cybersecurity policy
- Experience with penetration testing and Blue or Red Teams
- Knowledge of DoD networks and communications
- Knowledge of TCP/IP and networking
- BS degree in a technical field, including Computer Science, Engineering, Math, Science, or a related field
- DoD 8570 Compliant Certification, including Security+ and Certified Ethical Hacker (CEH)
- Offensive Security Certified Professional (OSCP) Certification
- Strong understanding of IT operations: help desk, end-point management, and server management
- Strong understanding of security operations concepts: perimeter defense, BYOD management, data loss protection, insider threat, kill chain analysis, risk assessment, and security metrics
- Strong analytical and Diagnostic skills
- Understand architecture, administration, and management of operating systems, networking, and virtualization
- Enthusiastic and highly adaptable
- Detailed knowledge in two or more of the following
- Conduct Perform vulnerability and risk assessment on Information Systems to ensure they are in compliance with security standards and measures utilizing Assured Compliance Assessment Solution (ACAS) and Nessus Scanner
- Perform risk assessments on systems, applications, and baselines in support of Risk Management Framework (RMF) for DoD Information Technology (IT) Department of Defense Instruction (DoDI) 8510.01 of HQ networks and systems
- Prepare risk assessment report for submission to the Authorizing Official (AO)
- Assist enforcement of Authorization, Assessment, and connection standards for HQ’s and Theater’s networks and systems
- Maintain ACAS SecurityCenter by installing SecurityCenter updates, patches and plugin definition
- Maintain ACAS RedHat Operating System by applying OS patches
- Perform review, analysis, and documentation for the life cycle security requirements of applications, systems, and networks within HQ USCENTCOM
- Review and update ACAS tactics, techniques and procedures (TTPs) and Standard Operating Procedures (SOPs)
- Review current intelligence for relevant threats and develop appropriate actions/response
- Assist with tracking of compliancy reporting for USCENTCOM orders
- Analyze network or system changes/reconfigurations for security impacts
- Coordinate and participate in Cyber Security risk analysis and assessments, as required
- Must meet DoD 8570.01-M minimum of IAT Level II Certification (i.e. Security +) upon hiring
- Must have demonstrated experience with Assured Compliance Assessment Solution (ACAS) and Nessus scanner to include creation of dashboards and providing analysis of vulnerabilities
- The candidate must of have experience with Risk Management Framework (RMF) for DoD Information Technology (IT) Department of Defense Instruction (DoDI) 8510.01
- Candidate must have an understanding of vulnerabilities, exploits, and practical working knowledge of DoD Cyber Security program
- Must be able to read and understand DoD Cyber Security orders, policies and procedures
- Must have experience within the USCENTCOM AOR and must be familiar with its mission
- Candidate must have strong communications skills both verbally and in writing
- Military Experience (Active Duty or Reserves)
- Experience with Cyber Security in a Joint and Coalition Partner environment
Cyber Security Analyst / , Vsoc Resume Examples & Samples
- This position could be a salary grade E01 or E02 depending on combined level of education and work experience
- Demonstrated understanding of computer networking and operating systems
- Demonstrated understanding of current threats, vulnerabilities, and attack trends
- This position could be a salary grade E03 or E04 depending on combined level of education and work experience
- Demonstrated to advanced experience with computer networking and operating systems
- Demonstrated to advanced experience of current threats, vulnerabilities, and attack trends
- Experience with one of the following: Splunk, NetWitness, Arcsight, McAfee NSM, and other related tools
- Analyze and respond to information security events to protect company personnel, assets and data
- Research and provides technical summaries of attack techniques, vulnerabilities and security controls
- Author and maintain operational processes, procedures and standards
- Maintain servers, workstations, networking equipment, mobile devices and infrastructure devices
- Assist in designing security awareness campaigns and outreach
- Bachelor's degree in Computer Science, Computer Engineering, Information Technology or Information Assurance
- CompTIA Security+, CompTIA Network+ or equivalent technical knowledge
- CISSP, CEH, GIAC, CISA, CRISC, MCSE or equivalent certification, a plus
- Strong interest in information security, hacking and secure design principles
- Strong technical skills with Microsoft Office suite
- Capacity to manage multiple engagements and competing priorities
- 1+ years of experience with RMF or DIACAP processes
- 01M Compliant IAM Level II Certification, including CAP, CASP, CISM, CISSP or Associate, or GSLC or IAT Level II Certification, including CCNA-Security, GICSP, GSEC, Security+ CE, or SSCP
- Experience with the implementation of DoD STIGs
- Experience with supporting security control selection and other activity in support of RMF-specific steps
- Knowledge of the Navy's Cybersecurity policies and procedures
- Prior experience working in one of the following: Security Operations Center (SOC), Network Operations Center (NOC) or Computer Incident Response Team (CIRT)
- Experience in the detection, response, mitigation, and/or reporting of cyber threats affecting client networks and one or more of the following: Computer intrusion analysis and incident response or Intrusion detection/protection systems
- Familiarity with packet analysis to include: HTTP Headers & Status codes; SMTP Traffic & Status codes; FTP Traffic & Status Codes
- At least one of the following certifications: CISSP, PMP, CCNP or related advanced IT certification
- Level 2: Minimum 2 years (in excess of degree requirements stated above) of progressively responsible experience in IT security
- Level 3: Minimum 5 years (in excess of degree requirements stated above) of progressively responsible experience in IT security
- Level 4: Minimum 8 years (in excess of degree requirements stated above) of progressively responsible experience in IT security
- Assist with administration of web content filters/proxies, email security, IDS/IPS, SIEM, DNS security, firewalls, network access control, and anti-virus software
- Leads the effort to manage the deployment of security patches and configuration changes to protect UGI information assets
- Coordinate resources to ensure security patches are applied and properly tested in a timely manner
- Assist in security incident response and remediation
- Configure, monitor, and audit security appliances
- Analyze traffic flows, system logs, and packets using security appliances (e.g., QRadar)
- Assist with development, evaluation, and maintenance of IT security policy and procedures
- Contribute to cyber security initiatives to protect systems and information
- Participate in ongoing cyber security training to promote security awareness and improve operational efficiency
- Collaborate with other IT security staff as necessary to identify potential threats, respond to reported violations, and ensure consistent application of IT security policies and procedures
- Three (3) years of IT security related experience
- Proficiency with vulnerability scanning, remediation, and reporting
- Demonstrated proficiency with Windows and Linux operating systems
- Working Knowledge of data security, network security, systems and applications security
- Experience administering firewalls, IDS/IPS, SIEM, and other security technologies
- Experience with NIST and ISO Industry Standards
- General knowledge of Information Security concepts, policies, and procedures
- Excellent verbal, written, analytical, and interpersonal skills
- IT security certifications (Security+, CISA, CISSP, or GIAC)
- Experience with privilege identity management processes required
- Knowledge and use of CyberArk or privilege account management product
- Experience related to credential management, non-human identity, and privilege access management work stream (specifically, developing and managing project schedules and dependencies resources, defining and managing risks and issues, writing and delivering project status, and coordinating across work streams)
- Must have proven record of accomplishment in successful problem solving
- Proactive learner and creative problem solver who enjoys being in a fast-paced environment and providing customer success and satisfaction
- Must have ability to analyze current business workflow and align new strategy to the large user base across different divisions
- Ability to influence senior management on business critical decisions
- Use complex analytics to correlate information from multiple sources to detect advanced threat actions
- Train IT admins and web developers on common industry security best practices
- Run security awareness campaigns
- Perform vulnerability and penetration testing
- Validate information security policy compliance
- Support investigations and perform forensic analysis
- Keep up to date on latest security whitepapers, incidents, tools, and tactics for defending against advanced threats
- Attend Security conferences
- Lead Division Security Operations
- Must demonstrate intimate knowledge and understanding of network protocols, multiple operating systems, web development, and network and domain architectures
- Must demonstrate knowledge of latest cyber threats and tactics, techniques, and procedures used to infiltrate computer networks
- Demonstrated ability to document and report on gathered analytics and risk analysis
- Must be able to demonstrate using shell scripting and tools to query and parse log data
- Degree must be in a relevant field (e.g. IT, Computer Science, Computer Engineering, Information Security, Information Assurance, or related degree)
- Must have one or multiples of the following: OSCP, OSCE, OSEE, OSWE, GSEC, GCIH, GCIA, GPEN, GWAPT, GCWN, GCED, GXPN, CEH, CHFI, ECSA, ECIH, ECSS, CISSP, CSSLP, CCFP or LPT
- Travel up to 15%
- Coordinate with technology subject matter experts to maintain currency of the system’s technical description and control implementation statements
- Perform a security impact analysis for each proposed change to the system’s configuration
- Maintain the GSS system’s security artifacts and security documentation library
- Review work instructions and operational procedures for compliance with security requirements and policy Interpret security principles and requirements for technical teams
- Monitor remediation of system vulnerabilities discovered by scanning tools
- Provide expertise and assistance in the development of the security policies and procedures and also assist ensuring compliance with those policies and procedures
- Active CompTIA Security+ or ISC2 CISSP certification
- Demonstrated experience and knowledge of use of BigFix as well as knowledge of system analytics
- Broad understanding of security protections typical in enterprise environments, including security hardening, firewalls and input filtering, architectures and boundary/endpoint best practices
- Familiarity with Splunk, Symantec Endpoint Protection, Tenable Security Center and IBM Endpoint Manager (IEM) and SourceFire IDS/IPS tools
Intern, Cyber Security Analyst Resume Examples & Samples
- Participate in security tool implementation, integration, and performance evaluation
- Review of security tool outputs, alerts, alarms, and reports
- Security log and event analysis
- Analyze system events, security alerts, and network activity, evaluate detection mechanisms
- Participate in cyber security activities, communication, and coordination across the Sony Enterprise
- Work with the various teams to gather, evaluate, analyze, and report on metrics to ensure performance of security service delivery and identify trends
- Working towards an undergraduate degree in Computer Science, Cyber Security, Information Technology or related subject matter
- Fluency in another language (particularly Japanese) a plus
- Available at least 20 hours per week
- Service delivery of cyber security tools, capabilities, and programs for the global monitoring and detection framework
- Assess performance and maturity of detection and monitoring architecture, tools, and processes, and make recommendations for improvements
- Interface with Sony Operating Companies globally to assess cyber security, monitoring, and reporting requirements and deliver tailored solutions to support the requirements
- Prioritize multiple tasks and formulate responses/recommendations to internal customers and team members in a fast-paced environment
- Apply technical acumen and analytical capabilities to speed and enhance monitoring, detection, and response capabilities
- Interpret, develop, and implement metrics collection to measure performance of security capabilities
- Mentor other team members
- Provide assistance to other security teams as needed
- Support investigation of incidents using SIEM and other data, event graphs, annotations, cases, and reports
- Assist in the development of advanced detection and monitoring content for Sony’s global infrastructure, systems, and applications
- Bachelor’s degree in Computer Science or similar field is preferred, or other equivalent experience
- Minimum of 8 years’ experience in Information Technology with 5 years’ experience in one or more of the following areas: information security, network operations or system administration with a significant security element
- Advanced experience with log management solution Splunk in the following areas
- Remedy Tasks (IA validation using ACAS)
- Perform Audit Reviews
- Perform manual STIG checks
- Setup and Run SCAP/SCC scans
- Perform vulnerability analysis in ACAS
- Download ACAS reports and post to sharepoint site
- Create reports in ACAS
- Monitor and track OPDRs, IAVMs, MCD, and MARADMINs
- Track and create Plan of Action & Milestones (POA&Ms)
- Create work instructions and standard operating procedures
- Review and update security documentation
- Proactive work ethic, can work as an individual or as a team
- Xacta / RSA Archer Experience
- Strong problem solving skills- solutions driven
- Sys Admin and Engineering Background
- Syslog SIEM Update/Integration/Reporting
- Articulate encryption standards, deployment strategies and technologies
- File Server AV Monitoring
- Malware Monitoring
- Metrics reporting
- Log Sources and Management with the SIEM
- AMP for Endpoints Malware Alerts management and escalation
- Certificate management
- Powerbroker understanding and client side software installation reviews
- Helpdesk Tickets
- Security Incident handling
- Scanning/Policy/Compliance
- Change control reviews approvals/rejections
- Version/Maintenance/Release monitoring of various security tools
- Software license tracking
- Alert – Threat Bulletins
- Manage third party risk, specifically IT
- Escalate security related incidents
- Basic SIEM knowledge, preferably LogRhythm
- Basic regulatory understanding covering GDPR and various US regulations
- Demonstrable English proficiency
- Basic Cisco Security product knowledge including ASA’s, ThreatGrid and network fabric
- Basic Intrusion Prevention and Detection technology understanding
- ISO 27001/2:2013 certification
- University degree preferably in Computer Science field
- Be able to work in a pressurized situation and set priorities accordingly
- Ability to build strong relationships with key stakeholders across the organization
- Ability to think logically to analyze, troubleshoot and resolve complex issues
- Must be professional, courteous and enjoy working with people; critical thinking, creativity, and independent judgment are expected
- Strong interpersonal skills and the ability to work within a team
- Ability to work in a fast paced, high pressure work environment
- Bachelor degree or equivalent experience
- 2+ years IT security experience
- Local to Austin or willing to relocate to the area (we do not provide relocation assistance)
- Project Management skill-sets are a requirement
- Bachelor’s degree in Computer Engineering, Computer Science or related field or equivalent work experience, required
- 5 years’ experience in Information Technology Security & Network, or related are, required
- GCIH – Global Certified Incident Handler, required
- OSCP – Offensive Security Certified Professional, required
- Advanced knowledge of Compliance Frameworks: PCI-DSS, ISO 27001/27002, NIST CSF
- Advanced knowledge of Programming Languages: Java, C/C++, Python, Perl, Verilog, VHDL, PHP, Assembly
- Advanced knowledge of Operating Systems: Linux, Solaris, OS X, Windows XP, Windows 7/8/10, Windows Server 2003/ 2008/2012
- Advanced knowledge of malware analysis
- Advanced knowledge of Point of Sale systems payment technologies such as P2PE and Tokenization
- Advanced knowledge of internal and external penetration testing
- Advanced knowledge of application code and platform configuration reviews
- Advanced knowledge of VoIP security assessments, social engineering, and wireless security testing
- Advanced knowledge of global penetration testing designed to meet PCI requirements
- Advanced knowledge of planning and implementing risk management programs
- Advanced knowledge of cyber-crime remediation
- Advanced knowledge of incident response handling, social engineering, and forensic analysis
- Display empathy, understanding and patience with employees and external customers
- Experience with Windows and Linux servers with GPOs, IAVMs and STIGs
- Recent experience creating and updating Python scripts
- Experience with ClearQuest and ClearCase
- Provision/ De Provision User Access Across Multiple platforms: Windows /Unix/AS400/Oracle
- CyberArk PIM Suite including but not limited to provisioning for; Secure Document Vault (Secure repository and sharing infrastructure), Enterprise Password Vault (Privileged Accounts at OS and DB levels), Application Identity Manager (App2App credentials and encryption keys), Privileged Session Manager (Control and monitor privileged accesses)
- Coordinate system and application configuration and management tasks
- Coordinate integration services, product updates, change requests and Tier-3 support
- Provide timely response to address server and client-server application performance and/or availability issues
- Lead, coordinate and participate in process improvements as they relate to IdM infrastructure and system
- In conjunction with business and department priorities and directives, conduct vendor and product research on software and systems products to address business needs
- Tier 3 support for all service desks using NAMCK VPN
- RSA – server / application support / provisioning
- Privileged User Access Review
- CyberArk – Server / Application Support
- Knowledge of core security principles
- Highly skilled in Running/providing services on a Linux/UNIX platform
- Demonstrated knowledge of Windows AD
- Knowledge of AutoIt scripting
- Ability to establish goals, objectives, and work plans
- Ability to understand the business and technical requirements while developing the associated content and documentation
- Proficiency in upgrading various software and hardware platforms
- Detail-oriented, self-motivated and disciplined, with excellent time management skills
- Experience with all of the following platforms: Windows, Unix, AS400, Oracle, Tandem, Mainframe
- Previous Cyberark Administrative support
- A history of workstation support
- A history of call center or relevant customer interfacing roles
- Relevant security certifications (CISSP, CISA, GIAC, Security Plus)
- Monitors system availability and performance
- Reacts to customers escalations
- Determine sophistication, priority, and threat level of identified malware
- Conduct log and system analysis for various system, and network and security devices capabilities to including NexGen Firewalls, WAFs, Database monitoring solutions, Identity Management Solutions, Virtualized platforms, Linux/Unix and Windows operating systems. include routers, Windows, Linux, and UNIX
- BS/BA degree or equivalent combination of related work experience required
- 5 years of SOC experience delivering security solutions to an enterprise or with a security services organization is required
- Prior security analysis experience is required
- Managed Security Services (MSS) experience HIGHLY DESIRED!
- 1 or more certifications include, Security+, CEH, GCIA, GCIH, CISSP or similar
- Experience in analyzing security logs generated by Intrusion Detection/Prevention Systems (IDS/IPS), firewalls, Anti-Virus, and/or other security logging sources
- Experience performing security analysis utilizing SIEM technologies
- Experience performing analysis utilizing IDS consoles
- Strong understanding of general cybersecurity concepts
- Excellent verbal and written communication skills in language to be supported
- Phone and remote support experience. Knowledge and resolution ability
- Ability to mentor new analysts
- Degree/Diploma in Computer Science, Computer Engineering, Electrical Engineering, Management Information Systems or equivalent certifications (MCSE, MCP, Oracle/MCDBA, HP-UX, CCNA, CCNP, SNIA)
- Minimum of 1-2 years’ experience within IT Operations, infrastructure services support (Systems NT, UX, Backups, DB’s, IT Security or Network management), operations monitoring and end user support
- Minimum of 1-2 years’ hands-on technical knowledge of the applicable technology platform that you will be responsible for: Network management, Security and HP Open View Products. Must be able to demonstrate troubleshooting and problem solving skills
- SIEM knowledge will be considered an advantage
- Strong interpersonal and security skills
- Clearly and in a timely manner with all customers, partners and users, internal and external
- Team player. Ability to collaborate and cooperate with members of team and members of other teams
- Understanding of 24x7 mission critical enterprise computing environments and the impact of service disruption on a company’s bottom line
- Ability to pro-actively learn new technology, processes and other skills
- Able to pro-actively search for solutions from knowledge bases, support, documentation and other information
- Keen interest in continual learning and professional development
- Time management skills and ability to multi-task and prioritize assigned tasks, problems and requests in a high pressure environment
- Flexible, self motivated with the ability to work under pressure in an international and culturally diverse organization
- Technical skills (procedures and documents the employee has to be acquainted with)
- Good knowledge of IT Operations, infrastructure services support (Systems NT, UX, Backups, DB’s or Network management), operations monitoring and end user support. Good understanding of ITSM/ITIL processes
- Part in a team that has established itself as a preferred partner for Hi-tech Services & Support throughout EMEA
- Competitive remuneration package
- 4 days additional paid leave (total:24 days)
- Food vouchers
- Reviews security and network events that are populated in a security information and event management (SIEM) system
- Investigates intrusion attempts and performs in-depth analysis of exploits
- Provides network intrusion detection expertise to support timely and effective decision making of when to declare an incident
- Conducts proactive threat research
- Analyzes a variety of network and host-based security appliance logs (Firewalls, NIDS, HIDS, Sys Logs, etc.) to determine the correct remediation actions and escalation paths for each incident
- Independently follows procedures to contain, analyze, and eradicate malicious activity
- Documents all activities during an incident and provides leadership with status updates during the life cycle of the incident
- Creates final incident report detailing the events of the incident
- Provides information regarding intrusion events, security incidents, and other threat indications and warning information
- University Degree (Equivalent to Bachelor degree) in Computer Science, Information Systems Security, or a related disciplines plus generally four years of experience with security operations, computer network defense, or intelligence analysis
- Higher Secondary Education plus two years of experience or training in the accounting field
- Minimum two years of experience in NID monitoring and incident response
- Industry recognized professional certification such as CISSP, GCIH, GCIA, Security+.Past experience with or current understanding of government intelligent processes and systems
- Direct experience with Malware analysis techniques and methodologies.Working knowledge of the Linux Operating system (CentOS, Red Hat, Ubuntu).Scripting Skills (e.g. PERL, Python, shell scripting, VBS)
- Familiarity with network security methodologies, tactics, techniques and procedures.Experience with IPS/IDS, SIEMS, and other computer network defense security tools.Experience reviewing and analyzing network packet captures
- Possess a comprehensive understanding of TCP/IP protocol, security architecture, and remote access security techniques/products
- Demonstrate a deep interest in learning new technology platforms for security testing, and forensics
- Keep abreast on latest security news/trends
- Conduct security tests using automated tools, ad-hoc tools and manual testing
- Conduct penetration testing against different technological domains including, but not limited to, web products, hardware products, wireless products, software, cloud based software, smart device applications
- Assess and calculate risk based on vulnerabilities and exposures discovered during testing
- Create required information security documentation technical reports and formal papers on test findings, and complete requests in accordance with requirements
- Handle and complete customer projects to the defined requirements in the timeframe required by customer with the highest quality and integrity of work
- Meet and exceed customer’s expectations with projects and other related tests and activities
- Ability to grasp information quickly
- Strong analytical and critical thinking skills demonstrated by the ability to make sound decisions independently
- Ability to execute on tasks and lead projects as needed
- Demonstrate excellent communication and collaboration skills in order to effectively work with clients, IT management, and staff
- Demonstrate knowledge of, and ability to communicate about, the information security threat landscape
- Thorough understanding of all layers of the OSI model
- Strong SIEM utilization skills
- Strong programming knowledge in Python and/or C# (.NET). Other languages a plus
- Ability to produce well commented code and clearly articulated documentation
- Analyze, correlate, and data mine network traffic and event logs to identify malicious activity
- Conduct research and development focused on the detection of tools, tactics and procedures leveraged by modern threat actors and malware
- Participate in or lead customer facing meetings and projects, including those that involve technical topics or technical service delivery
- Comprehensively understand networking protocols and infrastructure designs; including routing, firewall functionality, host and network intrusion detection systems, encryption, load balancing, and other network protocols
- Understand strategic objectives and vision, and work towards those goals
- 2-5 years of professional information security experience
- Software development experience involving automation and/or APIs
- Data science, machine learning, and/or statistical modeling experience that can be applied to anomaly detection
- Bachelor’s degree and 2 years of experience in information systems and IT security. An additional 6 years of experience will be considered in lieu of degree
- Currently possess or be able to obtain a public trust clearance
- Experience identifying when threats to the network should be communicated to management, and the ability to formally document and communicate the threat in a report
- Be capable of interpreting task requirements and selecting appropriate methodologies to complete task and carry it through to completion
- Strong interpersonal, organizational and communication skills
- At least one year of experience performing NIST-based Security Assessment and
- Authorization (formerly called Certification and Accreditation) activities in direct support of Federal information systems
- Experience with real time threat awareness/continuous monitoring that includes: operational experience, firewall management, security information and event management (SIEM), and the ability to identify threats to the network
- Relevant professional certifications from recognized industry consortiums including ISC2, ISACA, CompTIA, and GIAC specifically Security+, CAP, CISSP or equivalent
- Experience with Tenable Security Center
Siem Cyber Security Analyst Resume Examples & Samples
- Develop, test and coordinate the implementation of innovative and enhanced security SIEM content solutions
- Develop and analyze SIEM content performance metrics for actionable items
- Investigates incidents using SIEM technology, packet captures, reports, data visualization, and pattern analysis
- Produce and revise documentation of ArcSight developed content
- Understand and maintain the appropriate knowledge of Security Technologies, (AV, HIPS, NIPS, SIEM, WAF/DAM, DLP), security procedures, and services within the SOC
- Minimum of 4 years of direct experience in the analysis of security events from the SIEM platform
- Minimum of 4 years in building content in the SIEM ArcSight technology
- Good knowledge in building flexconnector
- Good knowledge in building ArcSight logger report
- Ability and experience in writing clear and concise technical writing specifically in event analysis and incident handling documentation
- Good understanding of network infrastructure protection systems
- Create technical documentation around the content deployed to the SIEM
- Good understanding of operating systems security measures
- Good understanding of application protection systems. (WEB)
- Experience in Intrusion Detection or Prevention Systems
- Experience with the TCP/IP stacks
- Excellent communications and vulgarization skills
- Takes initiatives, has leadership and organizational skills
Expert Cyber Security Analyst Resume Examples & Samples
- Applies the concept of operations set of disciplines for the planning, analysis, design and construction of information systems across a major sector of the organization
- Develops analytical and computational techniques and methodology for problem solutions
- Performs strategic systems planning and business information planning for specific projects
- Performs process and data modeling in support of the planning and analysis efforts using both manual and automated tools
- Applies reverse engineering and re-engineering disciplines to develop strategic and planning documents
- Applies business process improvement practices to re-engineer methodologies/principles and business process modernization projects
- Applies, as appropriate, activity and data modeling, transaction flow analysis, internal control and risk analysis and modern business methods and performance measurement techniques
- Assists in establishing standards for information systems procedures
- Develops and applies organization-wide information models for use in designing and building integrated, shared software and database management systems
- Constructs sound, logical business improvement opportunities consistent with the CIM guiding principles, cost savings, and open system architecture objectives
- Must have current/active TS/SCI with Polygraph
- Requires at least 11 years of relevant experience. Applicable degrees/certifications will count toward relevant experience as follows
- Demonstrated on-the-job experience with Sponsor or Sponsor partner networks and systems
- At least two years of demonstrated on-the-job experience with vulnerability assessment tools (hands on experience) and cyber security engineering
- Demonstrated on-the-job experience performing in-depth analysis on reports produced from vulnerability assessment tools and the ability to communicate those results effectively to other project stakeholders
- Demonstrated on-the-job experience communicating and collaborating effectively with program leads and Technical SMEs in support of program milestones or projects that require extensive collaboration over long periods of time
- Demonstrated on-the-job experience coordinating program remediation plans for addressing vulnerability findings
- Demonstrated on-the-job experience recommending reciprocity risk management principles that standardize security assessments where possible
- Demonstrated on-the-job experience assessing and guiding the implementation of identified corrections associated with technical vulnerabilities
- Demonstrated on-the-job experience providing guidance and direction on the maintenance of security configuration control of hardware, systems, and application software where needed
- Demonstrated on-the-job experience participating and provide support for program reviews
Senior Cyber Security Analyst Soc-mtl Resume Examples & Samples
- Investigate security events and incidents
- Perform malware analysis and reverse engineering
- Perform Network Security Monitoring
- Review and interpret alerts and provide diagnostics during incident management and analysis to support clients. (as a LVL3)
- Adhere to best practices for security management
- Provide 2nd and 3rth level response to security threats and vulnerabilities and able to analyze event logs, syslogs, and other data sources to determine the root cause of security events and provide a recommendation to resolve the event
- Analyzing security events, incidents and problems to provide recommendations on action
- Maintaining the relationship to keep clients and management informed and throughout the incident, problem and change management cycles
- Proactive monitoring of client environments using specialized security applications
- Ongoing training and certification to maintain your technical skills at the highest level
- Participation in a weekly after hours on-call rotation
- Participate to monthly calls with customers
- Competence in using an internal and external ticketing system for ITIL-based incident, problem and change management
- Methodical and creative approach to problem-solving
- Proven experience in the implementation, daily management and troubleshooting of firewalls of multiple vendors
- Proven experience in the daily management and troubleshooting of the intrusion prevention systems (IPS)
- Knowledge of NIST, ISO 27001, ITIL, SAS70 (or 5970) and/or other compliance frameworks
- Experience in building UseCases within Arcsight
- To demonstrate a deep interest in learning new technology platforms for security testing, and forensics
- To keep abreast on latest security news/trends
- To conduct security tests using automated tools, ad-hoc tools, and manual testing
- To conduct penetration testing against different technological domains including, but not limited to, web products, hardware products, wireless
- To assess and calculate risk based on vulnerabilities and exposures discovered during testing
- To create required information security documentation, technical reports and formal papers on test findings, and complete requests in accordance
- Candidate must be a self-motivated individual that is dedicated to exceeding client expectations, be willing to contribute to team efforts, and possess
- Experience with cybersecurity testing of products and software to identify weaknesses and flaws is a plus
- Experience installing and using various OS distributions and application packages
- Hands-on experience with commercial, open source and free security solutions such as AppScan, Fortify, Maltego. Kali Linux, Nessus, OpenVAS,
- Security related certifications a plus: CISSP, CISA, CEH, GIAC
- Strong expertise in testing in two or more of the following domains: Embedded software, embedded security, industrial control systems / SCADA,
- Experience or training in the IA governance , technical hardening and / or accreditation & certification frameworks and Information Security program Security Plans, STIGS, Center Internet Security baselines for Networking ,OSes, Application and Database components, NIST standards for Risk Management and Cybersecurity frameworks specifically
- Experience in the use of Service Now or service request ticketing systems, and MS Word , Excel, Power Point and SharePoint,
- Experience using eGRC, SEIM, and Vulnerability Scanning tools
- Experience with NIST SPs for SSPs, DFARs, Encryption and other International security and regulatory standards
- Experience in the use of MS Project, MS, Visio, SCCM,FIM/ MIM and other Microsoft products, Archer and SPLUNK eGRC /SEIMs and other MVM / Nexus security tools
Related Job Titles
- Knowledge Base
- Free Resume Templates
- Resume Builder
- Resume Examples
- Free Resume Review
Click here to directly go to the complete cyber security resume sample
“Cyber Security is much more than a matter of IT.” -Stéphane Nappo
Likewise, getting a cybersecurity job is much more than applying for a job with a generic resume.
Unless you write a customized cybersecurity resume, your chances of getting selected for the job is pretty low.
You need to frame the perfect cybersecurity resume that can make you stand out amongst every other average applicant for the recruiters to shortlist you for the targeted job.
And, by the end of this blog, you will be able to write a job-winning cybersecurity resume.
Table of Content:
- What are the roles and responsibilities of a cyber security professional?
- What is the average salary of cyber security professionals?
- How to professionally write a cyber security resume?
- What sections to use in cyber security resume?
- How to frame your experience on cyber security engineer resume in the best manner?
- How to write a perfect cyber-security resume header?
- Why cyber security resume profile title is necessary and how to write it?
- How to provide the correct details in the personal information section of your cyber security resume?
- What is the best way to compose a resume summary or objective to give an overview of your resume and mention the achievements of your career?
- What are the additional information you need to include in the cyber security resume
Here are some of the related profiles you can look into:
- Entry Level Cyber Security Resume
- Security Analyst Resume
- Cyber Security Certifications
- Front End Developer Resume
- Java Developer Resume
Roles & Responsibilities of a Cyber Security Professional
As organizations are going into an online business atmosphere, the requirement of cyber security professionals is more than ever. According to the Bureau of Labor Statistics , we will see a 31% increase in job demand for an information security professional from 2019 - 2029.
The typical cyber security job description is:
- Monitor the cloud environment and look for malicious activities
- Set up user access controls systems and monitor user access for ensuring the security
- Conduct regular security audits for identifying security Vulnerabilities.
- Configure patch management protocols for updating software automatically
- Configure vulnerability management system throughout the cloud system
- Set up and follow disaster management protocols at the time of problems & ensure complete data recovery
Cyber Security Salary

According to Payscale.com , the average salary of a cyber security professional is $76,575 per year.
Glassdoor.com says the average base pay of a cyber security professional is around $1,00,706 in the United States
How to Write a Professional Cyber Security Resume?
You need to follow three stages of resume writing to curate an impeccable cyber security engineer resume religiously.
The three stages of resume writing are given below:
- Stage 1 : Master Cyber Security Resume
- Stage 2 : First Draft of Cyber Security Resume
- Stage 3 : Final Draft of Cyber Security Resume
1. Master Cyber Security Resume
The master resume is your folder wherein you need to list all the details of your professional experience, education, certifications, awards and recognitions, internships, training, contact and personal information, etc.
You need to gather every detail even though you may not need them in your current cyber security resume sample. Always keep in mind that your master folder can be used for the following time frame:
Resume writing in the present : The master folder helps you find all the required information in one place. Thus making sure that you do not miss out on mentioning any important details on your security resume.
Resume update in the future : For any future updates of your cyber security resume sample, you can find the required details in your master folder. This saves you time and avoids looking for scattered pieces of information.
2. First Draft of Cyber Security Resume
In the second stage of resume writing, you need to frame the first draft of your cyber security resume.
You have to compose the following sections as part of your second stage:
- Personal Information
- Profile Title
- Professional Experience
- Certifications (if any)
- Awards & Recognition (if any)
- Additional Information (if any)
Do keep in mind that every standard section must be framed, whereas the optional sections can be framed only when required.
3. Final Draft of Cyber Security Resume
The final stage of writing your cyber security entry level resume requires you to compose the following two sections:
Key Skills : Create this section in the last second step of security resume-writing. All you have to do is create a separate "key skills" section of your resume. Then identify your most significant skills from the professional experience section of your resume and objectively place them out in this section.
Summary/Objective : Create this section in the last step of resume-writing. You need to give an overview of your cyber security resume, and it can be done by composing a resume summary or objective. If you have fewer than 3 years or no work experience, compose a resume objective. Else, compose a resume summary for your resume.
Every stage can help you focus on the important factors that can make your security resume-writing a hassle-free experience.
Follow them religiously, and you can end up creating the perfect junior cyber security analyst resume to make the recruiters give you the required shortlist.
Cyber Security Resume Sections
Every resume consists of various sections that communicate the different aspects of your educational and professional experience, including many other details.
Listed below are the standard and traditional sections of a cyber security resume that you need to frame at all times:
- Summary/Objective
Here is a list of all those sections which are optional and can be framed only when required or needed to enhance your cyber security resume for freshers :
- Awards & Recognitions (if any)
Learn more about resume sections on Hiration's 2023 Guide to sections in a resume .
Cyber Security Resume: Professional Experience
Just as resume writing requires three stages to cover all the aspects of your resume, the professional experience section requires the following factors:
- STAR Format
- Frame Points
- Bucketing & Bolding
1. STAR Format
The STAR format is an important factor that can help you communicate your professional experience to the recruiters in an effective way.
STAR stands for the following points:
- S stands for the Situation : context of your professional contributions to an organization.
- T stands for the actual Task : that was assigned to you as a professional.
- A stands for the Action : that you performed to execute the task assigned for a specific job profile.
- R stands for your action's Result : or outcome in the form of an achievement figure.
2. Framing Points
Let us look at the two cyber security resume examples given below to understand why your points should be framed and how to incorporate them in your cyber security intern resume:
Cyber Security Resume Example 1:
"As a cyber security professional, I assisted the information security infrastructure for 30+ major components in my previous organization. I also Assisted in the weekly technical analysis, consulting, designing, and review of products. Multiple vulnerability scanning technologies while identifying new techniques and tools we conducted by me to ensure up-to-date means of cyber security. The evaluation of the existing technical issues was effectively managed by me. It was done by identifying innovative solutions to broaden any security challenges. I was also responsible for rendering assistance in managing various projects by consulting with various corporate teams. 3 Junior Application was assisted by me with vulnerability remediation governance and requirements. Effectively coordinated with 4 Senior System Engineers and Cyber Operations teams to research attack surfaces. Successfully executed ad hoc for the entire organization and supervised priority tracking enterprise vulnerability scanning activities."
Cyber Security Resume Example 2:
Rendered assistance to the information security infrastructure for 30+ major components Assisted in the weekly technical analysis, consulting, designing, and review of products Conducted multiple vulnerability scanning technologies while identifying new techniques and tools Evaluated existing technical issues by identifying innovative solutions to broad any security challenges Rendered assistance in managing various projects by consulting with various corporate teams Assessed 3 Junior Applications with vulnerability remediation governance and requirements Coordinated with 4 Senior System Engineers & Cyber Operations teams to research attack surface Executed ad hoc for the entire organization and supervised priority tracking enterprise vulnerability scanning activities
In conclusion, with the help of the above two cyber security resume examples, we advise you to always frame your points and avoid writing bulky paragraphs.
Grouping & Highlighting
Let us look at the two cyber security resume examples given below to understand why you should apply bucketing and bolding in your framed points and how to incorporate them in your security resume:
Rendered assistance to the information security infrastructure for 30+ major components Conducted multiple vulnerability scanning technologies while identifying new techniques and tools Evaluated existing technical issues by identifying innovative solutions to broad any security challenges
Consulting & Technical Analysis
Also, use power verbs to start your points to have more impact on your professional experience statements.
In conclusion, you should always list your points under unique buckets and bold the most significant highlights of your career to raise your chances of being shortlisted.
Implement what you have learned from the above cyber security resume example to draft a kick-ass resume for yourself.

Also Read: How to compose the work experience in your resume?
Cyber Security Resume: Header
The header of your entry-level cyber security resume can help you stand out among other applicants and make it easier for the recruiters to keep track of your security resume.
Here are the points that need to be followed to frame the perfect cybersecurity resume header:
- It should be written in the topmost part of your security resume.
- Do not write "CV" or "Resume" as the heading of your resume
- It should be written in the largest font size.
- It should be written in 16-20 font sizes .
- There should be a single space between your first and last names.
- In case you have a middle name, only the initial of your middle name followed by a period should be written between your first and last name.
- Example: Mindy Becky Iglesias should be written as Mindy B. Iglesias.
There is more about this section on Hiration’s 2023 Guide To Writing The Perfect Resume Header to help you frame the perfect header for your cyber security intern resume.
Refer to the snapshot of the perfect header from a cyber security resume sample :

Also Read: How to Write a Perfect Resume Header in 2023?
Cyber Security Resume: Personal Information
An ideal personal information section should contain the details of your:
- Contact Number
- Email Address
- Current Location
- Designation
Hiration Pro Tip : Including details like gender, passport details, date of birth, etc., depending on the country you are targeting. In the Mideast, for instance, these details are required, but not in the US. Scan the hiring norms for the country you are targeting before you include (or don't include) these details.
1. Contact Number
Your contact number can make the recruiters get in touch with you in case of any likely shortlist. Moreover, some recruiters may even want to interview you directly over the phone.
Hence, you need to provide your contact number through which the recruiters can easily get in touch with you.
Below are some tips you need to keep in mind while adding contact number in resume:
- Mention your country’s ISD code as a prefix before your contact number
- Add a plus sign (+) right before the ISD code
- Add a space in the middle of the phone number for increasing readibility
- Eg : +1 27460 17367
Note: If you have 2 or more mobile numbers, only add the active mobile number on which you are available 24x7.
If the recruiter cannot get in touch with you, there is no point in giving out your contact number in your details. Hence, be sure that you are writing it correctly in your cybersecurity resume.
2. Email Address
You need to have an official email ID through which you can email your resume to the recruiters .
Avoid giving out a fancy or made-up email id in the resume. It can make you seem unprofessional.
Example: [email protected] or [email protected]
Your email address should have your real name to maintain a professional approach at all times.
Example : [email protected] or [email protected]
3. Current Location
Providing your current location in your cybersecurity resume is important. It should be farmed by keeping the following points in mind:
- Strictly avoid mentioning your house number, locality name, street number, etc., because the recruiters do not require those pieces of information.
- Mention your current city and state if you are looking for a job in your own country
- If you are applying for a job in another country, then you can mention your city and country of residence.
Also Read: How to compose your contact information in 2023?
Take a look at the sample cybersecurity resume below for a visual understanding of the personal information section:
Have a look at the snapshot below taken from the cyber security resume sample drafted on our resume builder to give you a picture of how you should be writing your personal details in your cybersecurity resume:

4. Designation: Profile Title
The recruiters can recognize your professional identity through your profile title. It ideally communicates the following facts:
- Your current designation.
- Your functional industry.
- Your level of seniority in your line of work.
Frame a professional profile title by following the below-given guidelines:
- Write it as the second-largest text in your cybersecurity resume.
- It should ideally be written in 14-16 font size.
Here is our cyber security resume sample for you to get a better understanding of how an ideal profile title looks like:

Cyber Security Resume: Key & Technical Skills
The recruiters use the ATS to pick only the suitable ones, and you need to rank high on the ATS.
Your key skills section is the perfect section wherein you can use the keywords used by the recruiters in the job description.
- Read the job description carefully and identify the skills that are required for the job.
- Simply scan through your professional experience section and choose the most specific skills that you possess as a professional.
- Tally both and pick matching key skills from both lists.
- Create a separate key skills section on the cybersecurity resume and highlight the key skills in that section.
Also, make sure that every skill you highlight is justified in your professional experience statements.
Here are some common information security analyst skills for a cyber security resume:
CyberSecurity Resume Key Skills
CyberSecurity Technical Skills
Learn how to effectively curate this section by going through Hiration's 2023 Guide on what skills to put on a resume .
Here is another cyber security resume sample showcasing the perfect key skills section:

Cyber Security Resume Summary
A cybersecurity resume summary needs to be framed to give an overview of your junior cyber security analyst resume.
Given below is a list of what you should follow to write a perfect cyber security resume summary:
- Write your summary at the end to easily decide what to put in your cybersecurity resume summary and what points to skip.
- Pick only the highlights of your career from the professional experience section.
- Try and include the keywords used by the recruiter in the job listing.
- Write a cybersecurity resume summary that does not exceed 4 lines. But if you have extensive years of experience, then an exception can be made for 5 lines.
- Compose a cyber security resume summary only if you have work experience of over 3 years.
Given below is a career snapshot from our cyber security resume sample showcasing the ideal cyber security resume summary section:

Also Read: How to write a resume summary in 2023?
Cyber Security Resume Objective
An objective should be composed for your entry-level cyber security resume if:
- you have no work experience.
- you have very limited work experience of fewer than 3 years.
- you are a fresh graduate writing an entry-level resume.
Avoid making the mistake of listing your demands in an objective. Instead, mention what you can do to contribute towards an organization to achieve its targets and goals.
The role of your cyber security resume objective is to make the recruiters recognize your skills as a professional. You need to convince the recruiters that you are the perfect candidate they looking for.
Also Read: How to write a professional resume objective in 2023?
Cyber Security Resume: Education
You need to provide the details of your educational qualification as it can help you communicate the level of your knowledge to the recruiters.
There is a specific requirement of educational qualification for every job profile, so make sure that you provide yours.
The education section of your entry-level cyber security resume should ideally consist of the following factors:
- Name of the school/university you have attended.
- Name of the courses you have pursued.
- The location of your school/university.
- Enrollment and graduation dates in the month & year format.
You can take a look at the below-given cyber security resume sample showcasing the ideal education section for your resume:

Also Read: How to list your education information on resume in 2023?
Cyber Security Resume: Certification
The certification section is also an essential part of the cybersecurity resume, along with the education section.
When including the certification in the cybersecurity resume, here are the elements you need to add:
- Name of the certification
- Name of the accreditation body
- Date of certification & expiry date in the month & year format.
Here's is an ideal format of writing the certification section in a cyber security resume:
{(Certification Name) | (Certification Body) | (Date of Certification - Date of Expiry)}
Here are a couple of entry level cyber security certifications for your reference:
- CompTIA Network+
- CompTIA Security+
- CompTIA CySA+
- CompTIA Linux+
- ISACA CSX Cybersecurity Fundamentals Certificate
- GIAC Information Security Fundamentals (GISF)
Also Read: How to list your certifications on resume in 2023?
Cyber Security Resume: Additional Information
Additional information is related to all those details related to the languages you speak, productive hobbies you keep, or any other information that relates to your field of work.
Below are a list of additional information you can add in your resume:
- Hobbies & Interests
- Volunteer Experience
- Publications & Research
Refer to the cyber security resume sample given-below and frame the perfect additional information section on your resume:

Cyber Security Cover Letter
A cyber security cover letter will help your resume stand out among 100+ resumes in front of the recruiter.
Here are steps to write a perfect cyber security cover letter:
- Ensure to use similar formatting and fonts in the resume and cover letter
- Do not go beyond one page for the resume cover letter. The ideal word count for a resume cover letter is 400-500 words.
- Complete the entire cyber security cover letter within 2-3 paragraphs.
- Start the first paragraph of the cyber security cover letter with your years of experience & certifications.
- Address the cover letter to the recruiter by their name.
- Always ask the recruiter for an interview at the end of your cover letter
Cyber Security Resume Sample
- Consulted and rendered assistance for major components of the information security infrastructure
- Assisted in the technical analysis , designing, consulting and product review of security components
- Aided with multiple vulnerability scanning technologies and packages while identifying new tools and techniques
- Evaluated & assessed existing technical issues by researching & identifying innovative solutions to broad security challenges
- Rendered assistance in managing components of various projects to completion & consulting with various corporate teams
- Assisted 2 Junior Application & System Engineers with vulnerability remediation governance and requirements
- Coordinated with 3 Senior Application & System Engineers and Cyber Operations teams to conduct attack surface research
- Executed ad hoc and priority tracking enterprise vulnerability scanning activities across the organization
- Maintained and monitored the enterprise Data Loss Prevention (DLP) solution while administering DLP environments
- Monitored & responded to alerts generated from tool while working with vendors to render assistance in DLP technology
- Configured policies and gained in-depth knowledge on following the incident response process via event escalations
- Responded to escalations via the Incident Response team and assisted the Cyber Security team in Live VAPT
- Implemented the strategies to perform VAPT activities on networks, web servers, websites and mobile applications
- Informed clients networks and websites about the vulnerabilities while aiding the Security Development team in patching
- Detected intrusion & deployed software technologies like C, C++, PHP, Perl, Java & Shell while performing malware analysis
- Managed and administered operating systems while working on virtualization software and networking
- GPA: 4.0/5.0
- Languages : English and Japanese
Frequently Asked Questions
How do i make a cyber security resume with no experience.
Below are the steps you need to take when creating a cyber security resume with no experience:
- Understand the job description
- Decide a professional and readable resume design
- Write the resume header with all relevant information
- Add a resume objective on top
- Add your education information
- Add any projects, or community activities you have under the education section
- List your relevant skills
- And add some other sections such as language, hobbies & interests.
- Send the resume to the recruiter in PDF format
What are some cyber security resume keywords and skills?
Given below are some cyber security resume keywords you can add in your resume:
Key Takeaways
- Always write your name as the resume header to maintain your resume's unique identity and avoid writing "Resume" or "CV."
- Provide your personal information as per the requirements of the hiring guidelines.
- Compose a resume objective if you are a fresher or someone with less than 3 years of work experience or changing careers.
- A resume summary is to be composed only if you have more than 3 years of professional experience.
- Frame one-liner bullet points to write your work experience and ensure starting each point with a suitable power verb.
- Provide the dates of your professional experience or education in the " date & month " format.
Now that we have reached the end of this blog using all the cyber security resume examples and information security resume samples that we have provided in this blog, it can help you write a great resume.
Go to Hiration resume builder and create a professional resume for yourself. Additionally, reach out to us at [email protected] , and you can get 24/7 professional assistance with all your job & career-related queries.
Share this blog
Subscribe to Free Resume Writing Blog by Hiration
Get the latest posts delivered right to your inbox
Stay up to date! Get all the latest & greatest posts delivered straight to your inbox
Is Your Resume ATS Friendly To Get Shortlisted?
Upload your resume for a free expert review.

Resume Worded | Career Strategy
Cyber security resume summary examples.
Approved by hiring managers, here are proven resume summary examples you can use on your Cyber Security resume. Learn what real hiring managers want to see on your resume, and when to use which.

- Cyber Security
- Cyber Security Analyst
- Cyber Security Architect
- Cyber Security Consultant
- Cyber Security Director
- Cyber Security Intern
- Cyber Security Manager
- Cyber Security Specialist
- Entry-Level Cyber Security Analyst
- Senior Cyber Security Engineer
- Cyber Security resume templates
- Similar summary examples
Cyber Security Resume Summary Example
Showcase your biggest achievements.
By mentioning that you've secured data for Fortune 500 companies, you're emphasizing your ability to handle high-stakes situations and deal with demanding clients. The number of thwarted cyber attacks quantifies your efficiency and effectiveness in your role.
Highlight your technical expertise
Specifically mentioning that you implemented robust security infrastructure using cutting-edge technologies not only indicates your deep technical skills, but also your adaptability and eagerness to stay updated with the latest advancements in the field.
Cyber Security Analyst Resume Summary Example
Explain your compliance expertise.
When you mention conducting regular security audits for HIPAA compliance, you're showing deep knowledge of industry-specific requirements. This speaks volumes about your attention to detail and your commitment to upholding high security standards, which could be a major plus for employers in the healthcare sector.
Highlight your preventive measures
Prevention is better than cure, especially in cybersecurity. By highlighting that you identified and resolved security vulnerabilities before they could be exploited, you're proving your ability to foresee potential threats and act preemptively. Moreover, maintaining a 100% clean security record is a solid testament to your competence and reliability.
Most resumes don't make it past the first round of screening. Our tool analyzes your resume and provides actionable insights to help you get noticed by hiring managers. Get an instant score and find out how to improve your chances of landing an interview.
Cyber Security Architect Resume Summary Example
Show your capacity to meet stringent requirements.
Designing a secure IT architecture for a major financial institution is a complex task, especially given the stringent regulatory requirements in this sector. Mentioning this showcases your ability to perform under pressure and to meet high standards.
Demonstrate your practical impact
By stating that you've implemented a new security software that improved threat detection rates by 75%, you're showing potential employers your capacity to make a quantifiable, practical impact on the company's security posture.
Cyber Security Consultant Resume Summary Example
Demonstrate your advisory role.
When you mention advising businesses across multiple sectors on cyber risk management, it underscores your knowledge in diverse industries and portrays you as an expert who can wade through complex, multi-faceted issues.
Highlight your adaptability
Developing bespoke security frameworks for each client shows your ability to think on your feet, adapt to different situations and devise unique solutions that cater to each client's specific needs and risk profile.
Cyber Security Director Resume Summary Example
Quantify your leadership role.
Managing security operations of a multinational corporation is a big deal. But when you add that you managed a budget of over $5M annually, it takes your leadership skills to another level. You're showing that you can handle major responsibility and financial resources, which can be particularly appealing to large organizations.
Share your strategic success
Reducing security incidents by 80% over five years is a significant achievement. It not only shows that you have a strong strategic mindset, but also that you can execute your strategies effectively. Plus, this kind of result implies a long-term commitment to an organization, which can be a plus in a field where continuity and consistency matter.
Cyber Security Intern Resume Summary Example
Leverage your educational background.
As a student or a recent graduate, your academic achievements and experiences can help bridge the gap between a lack of work experience and the job requirements. Mentioning a successful internship at a cybersecurity firm shows that you have some practical exposure to handling real-world cybersecurity issues.
Emphasize hands-on experience
Hands-on experience with security tools and methodologies can set you apart from other early-stage professionals. By emphasizing this, you're showing that you haven’t just studied cybersecurity, you’ve actually practiced it. It could be the deciding factor that lands you your next job or internship.
Cyber Security Manager Resume Summary Example
Emphasize your managerial skills.
Managing a team of 20 security professionals across three continents doesn't just demonstrate your managerial skills, it also shows your ability to work in a multinational environment, coordinating efforts across different time zones and cultures.
Show your proactive approach
Introducing a security awareness program indicates that you're proactive and focused on prevention rather than just mitigation. It also depicts your ability to devise and implement strategic initiatives with quantifiable success.
Cyber Security Specialist Resume Summary Example
Demonstrate your crisis management skills.
As a cybersecurity professional, responding to a crisis is a critical part of your job. Highlighting a specific incident where you played a significant role not only demonstrates your ability to handle high-pressure situations, but also showcases your problem-solving skills and resilience. So, when you mention you played a key role in an incident response operation, you're essentially showing that you can be trusted during a cybersecurity crisis.
Showcase your proactive approach
Developing a threat intelligence program isn’t a small feat. Emphasizing this shows your ability to stay ahead of the curve and reduce potential risks, a trait highly valued in the cybersecurity field. Plus, tying this action to a quantifiable result—like reducing the time to detect threats—gives a clearer idea of the impact of your work.
Entry-Level Cyber Security Analyst Resume Summary Example
Use relative experience to your advantage.
As an entry-level professional, your experience might not be as extensive as others. But by mentioning a project where you built a secure network for a local non-profit, you're showing potential employers that you've practically applied your academic knowledge.
Demonstrate your training and readiness
As a recent graduate, mentioning your training in the use of advanced security tools and methodologies can compensate for your lack of experience. This shows that you've invested time in developing practical skills and that you're ready to hit the ground running.
Senior Cyber Security Engineer Resume Summary Example
Make your impact known.
By stating that you've designed and implemented security solutions for a global tech firm, you underscore your competence in handling complex, large-scale projects. Adding the result - a 90% reduction in security incidents - underscores your effectiveness.
Show your leadership abilities
Mentioning that you led a team of 10 security professionals not only speaks volumes about your leadership skills but also implies that you're capable of coordinating efforts to manage and mitigate cyber threats.
Cyber Security Resume Templates

Network Engineer

Security Manager
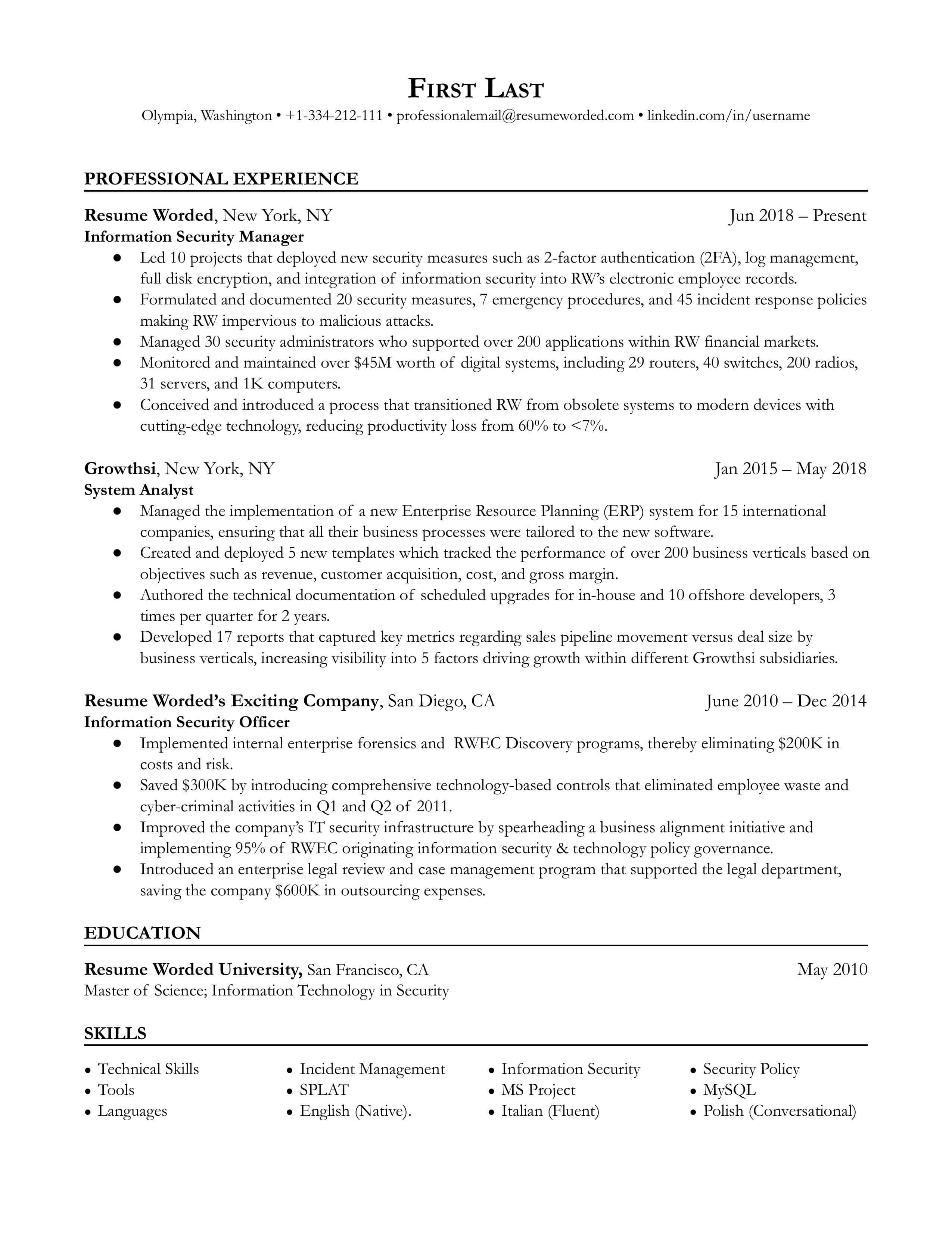
Engineering Resume Summary Examples
- > Civil Engineer Summary Examples
- > Electrical Engineer Summary Examples
- > Front End Developer Summary Examples
- > IT Manager Summary Examples
- > Java Developer Summary Examples
- > Manufacturing Engineer Summary Examples
- > Mechanical Engineer Summary Examples
- > Network Administrator Summary Examples
- > Python Developer Summary Examples
- > Quality Assurance Tester Summary Examples
- > Quality Engineer Summary Examples
- > Scrum Master Summary Examples
- > Software Developer Summary Examples
- > Software Engineer Summary Examples
- > System Administrator Summary Examples
- > Web Developer Summary Examples
Engineering Resume Objective Examples
- > Civil Engineer Objective Examples
- > Electrical Engineer Objective Examples
- > Front End Developer Objective Examples
- > IT Manager Objective Examples
- > Java Developer Objective Examples
- > Manufacturing Engineer Objective Examples
- > Mechanical Engineer Objective Examples
- > Network Administrator Objective Examples
- > Python Developer Objective Examples
- > Quality Assurance Tester Objective Examples
- > Quality Engineer Objective Examples
- > Scrum Master Objective Examples
- > Software Developer Objective Examples
- > Software Engineer Objective Examples
- > System Administrator Objective Examples
- > Web Developer Objective Examples
Engineering Resume Guides
- > Civil Engineer Resume Guides
- > Electrical Engineer Resume Guides
- > Front End Developer Resume Guides
- > IT Manager Resume Guides
- > Java Developer Resume Guides
- > Manufacturing Engineer Resume Guides
- > Mechanical Engineer Resume Guides
- > Network Administrator Resume Guides
- > Python Developer Resume Guides
- > Quality Assurance Tester Resume Guides
- > Quality Engineer Resume Guides
- > Scrum Master Resume Guides
- > Software Developer Resume Guides
- > Software Engineer Resume Guides
- > System Administrator Resume Guides
- > Web Developer Resume Guides
Thank you for the checklist! I realized I was making so many mistakes on my resume that I've now fixed. I'm much more confident in my resume now.


IMAGES
VIDEO
COMMENTS
Here's an example of a recent graduate's resume objective for an entry level cybersecurity specialist role: Data-driven and detail-oriented cybersecurity specialist. Recently graduated from Arizona State University with a bachelor's degree in Computer Science. Highly proficient in vulnerabilities and risks in networks.
Cyber Security Resume Samples: Resume Summary. right; Persistent, detail-oriented cyber security analyst with 3+ years experience with government security software contractor. ... The objective statement on a entry-level cyber security resume tells the agency your career goals. Like the summary, use relevant experience, skills, and achievements ...
A recruiter-approved Entry Level Cyber Security Analyst resume example in Google Docs and Word format, with insights from hiring managers in the industry. Updated for 2024. ... or volunteer work in your summary. Aspiring cyber security analyst with experience conducting security audits and implementing access controls during a summer internship ...
Here are the steps to compose an entry-level cybersecurity resume: 1. Decide on the format. First, decide how you want to arrange and format your resume. For entry-level positions, a chronological format can be best, listing work experience in reverse chronological order from most recent to earliest. As you select a template or design your ...
Summary. Diligent cyber security analyst with 3+ years of experience securing systems and data. Seeking to deliver airtight information security at Cypherdyne Systems. ... Entry-Level Cyber Security Resume Job Description [Sample] Good Example. Network Engineer. Webnominal, Inc. 2014-2019. Monitored and secured 30+ websites with 0 successful ...
Here are some keywords and action verbs you should consider incorporating into your resume: 1. Technical Skills: Mention specific cybersecurity tools, software, and programming languages you are proficient in, such as Python, Java, C++, Wireshark, Metasploit, Nmap, Snort, or Kali Linux. 2.
Top 5 Tips for Your Entry-Level Cyber Security Resume. Tailor your resume to each role. To impress recruiters, only send out resumes that are tailor-made to match each job description. For instance, if a role stresses Kali Linux and Burp Suite, and you're a pro at these tools, place them at the top of your skills list. Highlight your training
Entry Level Cyber Security Resume Example 1. Tested both layer 1 and 2 while implementing services at layers 1, 2, and 3 as required. Administered technical validations while testing and repairing CAT5E/CAT6 copper, including Multimode 62.5.
Step 1: Create a cybersecurity resume template. One of the most important characteristics for any resume to have is readability. Hiring managers want to find the information they need quickly and easily. You can find plenty of free and paid cybersecurity specialist and cybersecurity analyst resume templates online.
Here are some steps you can follow to write a cybersecurity resume: 1. Create a header. The first step is to write a clear header at the top of the page, using an easy-to-read font and white space, that includes your full name and contact information. You might include your full home address or just your city and state.
Tips to help you write your Entry Level Cyber Security Analyst resume in 2024 Focus on relevant technical skills As an entry-level cybersecurity analyst, be sure to highlight your technical skills, such as knowledge in programming languages (Python, C++), operating systems (Windows, Linux), security frameworks (NIST, ISO), and any tools or ...
1. A cyber security resume gives you increased chances of getting an interview: Cyber security is a highly competitive field, so a strong resume is essential for getting your foot in the door. A well-written resume that highlights your skills and experience will make you more likely to be selected for an interview. 2.
Here's a template to help you format your cybersecurity analyst resume: Download Resume Template. To upload the template into Google Docs, go to File > Open > and select the correct downloaded file. Related: Best Resume Templates and Types. Get interview-ready with tips from Indeed.
There are three easy-to-follow steps to resume writing that can help you organize your process of making the perfect resume. Let's tale a look: Stage 1: Master Entry Level Security Analyst Resume. Stage 2: First Draft of Entry Level Security Analyst Resume. Stage 3: Final Draft of Entry Level Security Analyst Resume.
Here's what strong entry-level cyber security resumes share. Quantifying Impact With Metrics: Good resumes show clear impact with numbers.They include reduced risk percentages, increased system uptime, attack simulations conducted, and security patches applied.. Match Skills With Job Description: You should include skills on your resume that you have and are mentioned in the job description.
Here are eight steps you can take to write an effective cyber security resume for an entry-level role: 1. Decide on presentation. First, you can decide how you want to arrange and format your resume. For entry-level positions, highlighting your education before your work experience can be an effective strategy.
Why this resume works. For an entry-level cyber security resume, highlight your education and any relevant projects or internships you've completed. Talk about the specific projects related to cyber security you've been a part of to demonstrate your knowledge and enthusiasm for the field. And include certifications.
How to write a cyber security analyst resume. Take a piece of A4 paper and fold it into 3 sections. Top, middle, and bottom. The top third is reserved for directly answering the hiring manager's most pressing questions. You have 5 seconds to capture their attention.
I event had the privilege to work collectively with the security development team to resolve network vulnerabilities. All in all, I did a fantastic job as a cyber security analyst in company x. Cyber Security Analyst Resume Example 2. Malware Analysis & Security Improvement.
Cyber Security Analyst Resume Examples & Samples. Experience in developing processes and technology standards Ability to train and mentor staff. Exceptional attention to detail and strong focus on quality. High knowledge of or exposure to ANZ teams and systems. Experience in IT Security tools.
Given below is a career snapshot from our cyber security resume sample showcasing the ideal cyber security resume summary section: Also Read: How to write a resume summary in 2023? Cyber Security Resume Objective. An objective should be composed for your entry-level cyber security resume if: you have no work experience.
Secured data for Fortune 500 companies, thwarting 100+ cyber attacks annually.Implemented robust security infrastructure using cutting-edge technologies, reducing system vulnerabilities by 80%.Experienced in overseeing global teams, managing cyber risk, and working closely with C-Suite executives.