Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.

OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
Presentation Layer: Protocols, Examples, Services | Functions of Presentation Layer
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts. Now, we will explain about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. At the end of this article, you will completely educate about What is Presentation Layer in OSI Model without any hassle.
- What is Presentation Layer?
Definition : Presentation layer is 6th layer in the OSI model , and its main objective is to present all messages to upper layer as a standardized format. It is also known as the “ Translation layer “. This layer takes care of syntax and semantics of messages exchanged in between two communication systems. Presentation layer has responsible that receiver can understand all data, and it will be to implement all data languages can be dissimilar of two communication system.

Presentation layer is capable to handle abstract data structures, and further it helps to defined and exchange of higher-level data structures.
Presentation Layer Tutorial Headlines:
In this section, we will show you all headlines about this entire article; you can check them as your choice; below shown all:
- Functions of Presentation Layer
Protocols of Presentation Layer
- Example of Presentation Layer Protocols
Presentation Layer Services
Design issues with presentation layer, faqs (frequently asked questions), what is meant by presentation layer in osi model, what protocols are used in the presentation layer, can you explain some presentation layer examples, what are the main functions of the presentation layer, what are services of presentation layer in osi, let’s get started, functions of presentation layer.
Presentation layer performs various functions in the OSI model ; below explain each one –
- Presentation layer helps to translate from American standard code for information interchange (ASCII) to the extended binary code decimal interchange code (EBCDIC).
- It deals with user interface as well as supporting for several services such as email and file transfer.
- It provides encoding mechanism for translating all messages from user dependent format with common format and vice – versa.
- It’s main goal for data encryption and decryption of entire data before they are getting transmission over all common platforms.
- It provides data compression mechanism for source point to decrease the all bits which are transmitted. Due to this data compression system, user are able to transmit enlarge multimedia file at fastest file transfer rate.
- Due to use of Data Encryption and Decryption algorithm, presentation layer provides more network protection and confidentiality while transmission data over the entire network.
- This layer offers best flexibility for data translation for making connections with various kinds of servers , computers, and mainframes over the similar network.
- Presentation layer has responsible to fix all translations in between all network systems .
Presentation layer is used various protocols; below list is available –
- Multipurpose Internet Mail Extensions
- File Transfer Protocol
- Network News Transfer Protocol
- Apple Filing Protocol (AFP)
- Independent Computing Architecture (ICA), the Citrix system core protocol
- Lightweight Presentation Protocol (LPP)
- NetWare Core Protocol (NCP)
- Network Data Representation (NDR)
- Telnet (a remote terminal access protocol)
- Tox Protocol
- eXternal Data Representation (XDR)
- 25 Packet Assembler/Disassembler Protocol (PAD)
Example of Presentation Layer Protocols:
Here, we will discuss all examples of presentation layer protocols; below explain each one –
Multipurpose Internet Mail Extensions (MIME) : MIME protocol was introduced by Bell Communications in 1991, and it is an internet standard that provides scalable capable of email for attaching of images, sounds and text in a message.
File Transfer Protocol (FTP) : FTP is a internet protocol, and its main goal is to transmit all files in between one host to other hosts over the internet on TCP/IP connections.
Network News Transfer Protocol (NNTP) : This protocol is used to make connection with Usenet server and transmit all newsgroup articles in between system over internet.
Apple Filing Protocol (AFP ) : AFP protocol is designed by Apple company for sharing all files over the entire network .
Lightweight Presentation Protocol (LPP) : This protocol is used to offer ISO presentation services on top of TCP/IP based protocol stacks.
NetWare Core Protocol (NCP) : NCP is a Novell client server model protocol that is designed especially for Local Area Network (LAN). It is capable to perform several functions like as file/print-sharing, clock synchronization, remote processing and messaging.
Network Data Representation (NDR) : NDR is an data encoding standard, and it is implement in the Distributed Computing Environment (DCE).
Telnet (Telecommunication Network) : Telnet protocol was introduced in 1969, and it offers the command line interface for making communication along with remote device or server .
Tox : The Tox protocol is sometimes regarded as part of both the presentation and application layer , and it is used for sending peer-to-peer instant-messaging as well as video calling.
eXternal Data Representation (XDR) : This protocol provides the description and encoding of entire data, and it’s main goal is to transfer data in between dissimilar computer architecture.
25 Packet Assembler/Disassembler Protocol (PAD) : Main objective of this protocol is to obtain all data from group of terminal and allots the data into X. 25 packets.
Presentation layer provides several services like as –
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
- It helps to handle and maintain Syntax and Semantics of the message transmitted.
- Encoding data can be done as standard agreed like as String, double, date, and more.
- Standard Encoding can be done on wire.
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model that is the lowest layer, where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts.
Presentation layer is used various protocols like as:
Yes! In this article, already we have been explained many examples of presentation layer; you can check them.
Presentation layer has a responsibility for formatting, translation, and delivery of the information for getting to process otherwise display .
Now, i hope that you have completely learnt about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. If this post is useful for you, then please share it along with your friends, family members or relatives over social media platforms like as Facebook, Instagram, Linked In, Twitter, and more.
Also Read: Data Link Layer: Protocols, Examples | Functions of Data Link Layer
If you have any experience, tips, tricks, or query regarding this issue? You can drop a comment!
Related Posts


OSI Model Layers and Protocols in Computer Network
What is OSI Model?
The OSI Model is a logical and conceptual model that defines network communication used by systems open to interconnection and communication with other systems. The Open System Interconnection (OSI Model) also defines a logical network and effectively describes computer packet transfer by using various layers of protocols.
Characteristics of OSI Model
Here are some important characteristics of the OSI model:
- A layer should only be created where the definite levels of abstraction are needed.
- The function of each layer should be selected as per the internationally standardized protocols.
- The number of layers should be large so that separate functions should not be put in the same layer. At the same time, it should be small enough so that architecture doesn’t become very complicated.
- In the OSI model, each layer relies on the next lower layer to perform primitive functions. Every level should able to provide services to the next higher layer
- Changes made in one layer should not need changes in other lavers.
Why of OSI Model?
- Helps you to understand communication over a network
- Troubleshooting is easier by separating functions into different network layers.
- Helps you to understand new technologies as they are developed.
- Allows you to compare primary functional relationships on various network layers.
History of OSI Model
Here are essential landmarks from the history of OSI model:
- In the late 1970s, the ISO conducted a program to develop general standards and methods of networking.
- In 1973, an Experimental Packet Switched System in the UK identified the requirement for defining the higher-level protocols.
- In the year 1983, OSI model was initially intended to be a detailed specification of actual interfaces.
- In 1984, the OSI architecture was formally adopted by ISO as an international standard
7 Layers of the OSI Model
OSI model is a layered server architecture system in which each layer is defined according to a specific function to perform. All these seven layers work collaboratively to transmit the data from one layer to another.
- The Upper Layers : It deals with application issues and mostly implemented only in software. The highest is closest to the end system user. In this layer, communication from one end-user to another begins by using the interaction between the application layer. It will process all the way to end-user.
- The Lower Layers : These layers handle activities related to data transport. The physical layer and datalink layers also implemented in software and hardware.
Upper and Lower layers further divide network architecture into seven different layers as below
- Application
- Presentation
- Network, Data-link
- Physical layers
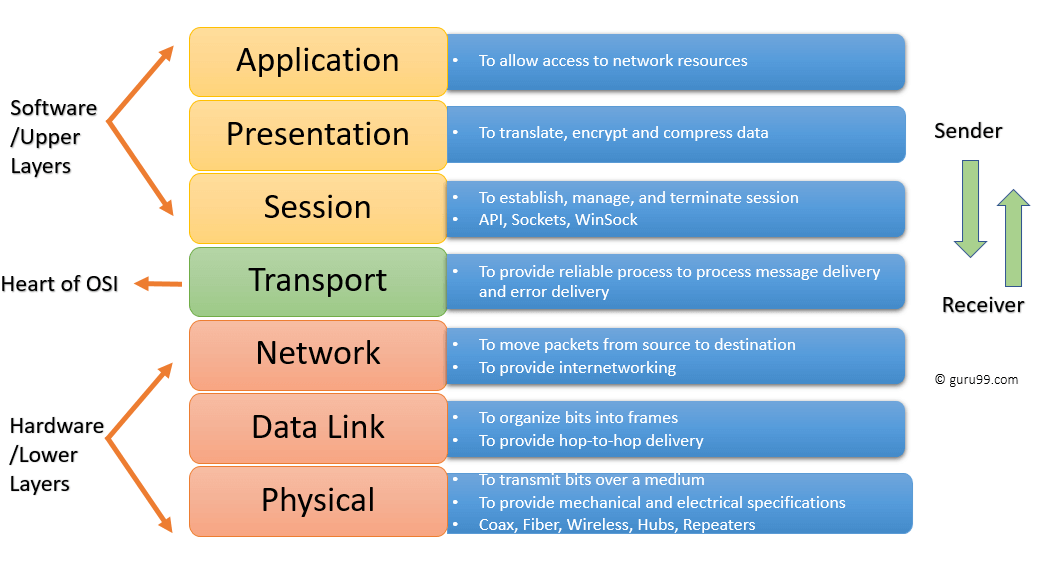
Let’s Study each layer in detail:
Physical Layer
The physical layer helps you to define the electrical and physical specifications of the data connection. This level establishes the relationship between a device and a physical transmission medium. The physical layer is not concerned with protocols or other such higher-layer items. One example of a technology that operates at the physical layer in telecommunications is PRI (Primary Rate Interface). To learn more about PRI and how it works , you can visit this informative article.
Examples of hardware in the physical layer are network adapters, ethernet, repeaters, networking hubs, etc.
Data Link Layer
Data link layer corrects errors which can occur at the physical layer. The layer allows you to define the protocol to establish and terminates a connection between two connected network devices.
It is IP address understandable layer, which helps you to define logical addressing so that any endpoint should be identified.
The layer also helps you implement routing of packets through a network. It helps you to define the best path, which allows you to take data from the source to the destination.
The data link layer is subdivided into two types of sublayers:
- Media Access Control (MAC) layer- It is responsible for controlling how device in a network gain access to medium and permits to transmit data.
- Logical link control layer- This layer is responsible for identity and encapsulating network-layer protocols and allows you to find the error.
Important Functions of Datalink Layer
- Framing which divides the data from Network layer into frames.
- Allows you to add header to the frame to define the physical address of the source and the destination machine
- Adds Logical addresses of the sender and receivers
- It is also responsible for the sourcing process to the destination process delivery of the entire message.
- It also offers a system for error control in which it detects retransmits damage or lost frames.
- Datalink layer also provides a mechanism to transmit data over independent networks which are linked together.
Transport Layer
The transport layer builds on the network layer to provide data transport from a process on a source machine to a process on a destination machine. It is hosted using single or multiple networks, and also maintains the quality of service functions.
It determines how much data should be sent where and at what rate. This layer builds on the message which are received from the application layer. It helps ensure that data units are delivered error-free and in sequence.
Transport layer helps you to control the reliability of a link through flow control, error control, and segmentation or desegmentation.
The transport layer also offers an acknowledgment of the successful data transmission and sends the next data in case no errors occurred. TCP is the best-known example of the transport layer.
Important functions of Transport Layers
- It divides the message received from the session layer into segments and numbers them to make a sequence.
- Transport layer makes sure that the message is delivered to the correct process on the destination machine.
- It also makes sure that the entire message arrives without any error else it should be retransmitted.
Network Layer
The network layer provides the functional and procedural means of transferring variable length data sequences from one node to another connected in “different networks”.
Message delivery at the network layer does not give any guaranteed to be reliable network layer protocol.
Layer-management protocols that belong to the network layer are:
- routing protocols
- multicast group management
- network-layer address assignment.
Session Layer
Session Layer controls the dialogues between computers. It helps you to establish starting and terminating the connections between the local and remote application.
This layer request for a logical connection which should be established on end user’s requirement. This layer handles all the important log-on or password validation.
Session layer offers services like dialog discipline, which can be duplex or half-duplex. It is mostly implemented in application environments that use remote procedure calls.
Important function of Session Layer
- It establishes, maintains, and ends a session.
- Session layer enables two systems to enter into a dialog
- It also allows a process to add a checkpoint to steam of data.
Presentation Layer
Presentation layer allows you to define the form in which the data is to exchange between the two communicating entities. It also helps you to handles data compression and data encryption.
This layer transforms data into the form which is accepted by the application. It also formats and encrypts data which should be sent across all the networks. This layer is also known as a syntax layer .
The function of Presentation Layers
- Character code translation from ASCII to EBCDIC.
- Data compression: Allows to reduce the number of bits that needs to be transmitted on the network.
- Data encryption: Helps you to encrypt data for security purposes — for example, password encryption.
- It provides a user interface and support for services like email and file transfer.
Application Layer
Application layer interacts with an application program, which is the highest level of OSI model. The application layer is the OSI layer, which is closest to the end-user. It means OSI application layer allows users to interact with other software application.
Application layer interacts with software applications to implement a communicating component. The interpretation of data by the application program is always outside the scope of the OSI model.
Example of the application layer is an application such as file transfer, email, remote login, etc.
The function of the Application Layers are
- Application-layer helps you to identify communication partners, determining resource availability, and synchronizing communication.
- It allows users to log on to a remote host
- This layer provides various e-mail services
- This application offers distributed database sources and access for global information about various objects and services.
Interaction Between OSI Model Layers
Information sent from a one computer application to another needs to pass through each of the OSI layers.
This is explained in the below-given example:
- Every layer within an OSI model communicates with the other two layers which are below it and its peer layer in some another networked computing system.
- In the below-given diagram, you can see that the data link layer of the first system communicates with two layers, the network layer and the physical layer of the system. It also helps you to communicate with the data link layer of, the second system.

Protocols supported at various levels
Differences between osi & tcp/ip.

Here, are some important differences between the OSI & TCP/IP model:
Advantages of the OSI Model
Here, are major benefits/pros of using the OSI model :
- It helps you to standardize router, switch, motherboard, and other hardware
- Reduces complexity and standardizes interfaces
- Facilitates modular engineering
- Helps you to ensure interoperable technology
- Helps you to accelerate the evolution
- Protocols can be replaced by new protocols when technology changes.
- Provide support for connection-oriented services as well as connectionless service.
- It is a standard model in computer networking.
- Supports connectionless and connection-oriented services.
- Offers flexibility to adapt to various types of protocols
Disadvantages of the OSI Model
Here are some cons/ drawbacks of using OSI Model:
- Fitting of protocols is a tedious task.
- You can only use it as a reference model.
- Doesn’t define any specific protocol.
- In the OSI network layer model, some services are duplicated in many layers such as the transport and data link layers
- Layers can’t work in parallel as each layer need to wait to obtain data from the previous layer.
- The OSI Model is a logical and conceptual model that defines network communication which is used by systems open to interconnection and communication with other systems
- In OSI model, layer should only be created where the definite levels of abstraction are needed.
- OSI layer helps you to understand communication over a network
- Straight Through Cables vs Crossover Cables
- Address Resolution Protocol: What is ARP Header in Networking
- VLAN Trunking Protocol: What is VTP in Networking & Benefits
- STP – Spanning Tree Protocol Explained
- What is IP Routing? Types, Routing Table, Protocols, Commands
- Layer 2 Switch vs Layer 3 Switch
- Subnetting: What is Subnet Mask?
- What is Wildcard Mask? How to Calculate Wildcard Mask
The OSI Model – The 7 Layers of Networking Explained in Plain English

This article explains the Open Systems Interconnection (OSI) model and the 7 layers of networking, in plain English.
The OSI model is a conceptual framework that is used to describe how a network functions. In plain English, the OSI model helped standardize the way computer systems send information to each other.
Learning networking is a bit like learning a language - there are lots of standards and then some exceptions. Therefore, it’s important to really understand that the OSI model is not a set of rules. It is a tool for understanding how networks function.
Once you learn the OSI model, you will be able to further understand and appreciate this glorious entity we call the Internet, as well as be able to troubleshoot networking issues with greater fluency and ease.
All hail the Internet!
Prerequisites
You don’t need any prior programming or networking experience to understand this article. However, you will need:
- Basic familiarity with common networking terms (explained below)
- A curiosity about how things work :)
Learning Objectives
Over the course of this article, you will learn:
- What the OSI model is
- The purpose of each of the 7 layers
- The problems that can happen at each of the 7 layers
- The difference between TCP/IP model and the OSI model
Common Networking Terms
Here are some common networking terms that you should be familiar with to get the most out of this article. I’ll use these terms when I talk about OSI layers next.
A node is a physical electronic device hooked up to a network, for example a computer, printer, router, and so on. If set up properly, a node is capable of sending and/or receiving information over a network.
Nodes may be set up adjacent to one other, wherein Node A can connect directly to Node B, or there may be an intermediate node, like a switch or a router, set up between Node A and Node B.
Typically, routers connect networks to the Internet and switches operate within a network to facilitate intra-network communication. Learn more about hub vs. switch vs. router.
Here's an example:
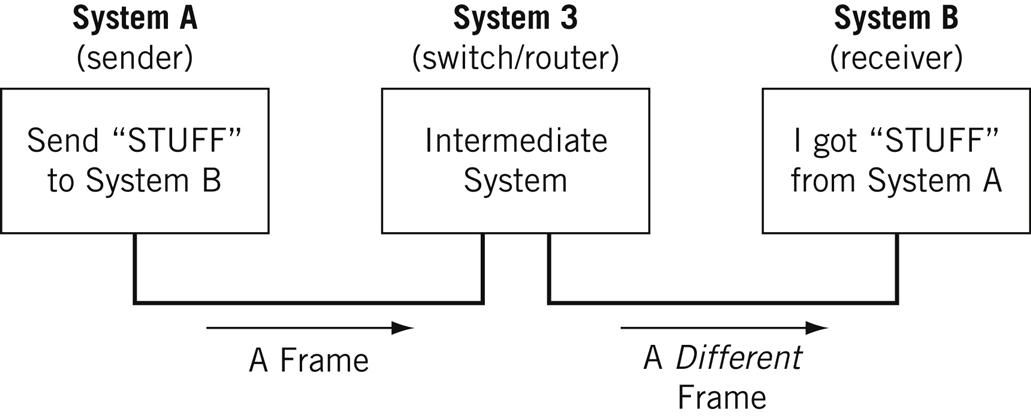
For the nitpicky among us (yep, I see you), host is another term that you will encounter in networking. I will define a host as a type of node that requires an IP address. All hosts are nodes, but not all nodes are hosts. Please Tweet angrily at me if you disagree.
Links connect nodes on a network. Links can be wired, like Ethernet, or cable-free, like WiFi.
Links to can either be point-to-point, where Node A is connected to Node B, or multipoint, where Node A is connected to Node B and Node C.
When we’re talking about information being transmitted, this may also be described as a one-to-one vs. a one-to-many relationship.
A protocol is a mutually agreed upon set of rules that allows two nodes on a network to exchange data.
“A protocol defines the rules governing the syntax (what can be communicated), semantics (how it can be communicated), and synchronization (when and at what speed it can be communicated) of the communications procedure. Protocols can be implemented on hardware, software, or a combination of both. Protocols can be created by anyone, but the most widely adopted protocols are based on standards.” - The Illustrated Network.
Both wired and cable-free links can have protocols.
While anyone can create a protocol, the most widely adopted protocols are often based on standards published by Internet organizations such as the Internet Engineering Task Force (IETF).
A network is a general term for a group of computers, printers, or any other device that wants to share data.
Network types include LAN, HAN, CAN, MAN, WAN, BAN, or VPN. Think I’m just randomly rhyming things with the word can ? I can ’t say I am - these are all real network types. Learn more here .
Topology describes how nodes and links fit together in a network configuration, often depicted in a diagram. Here are some common network topology types:
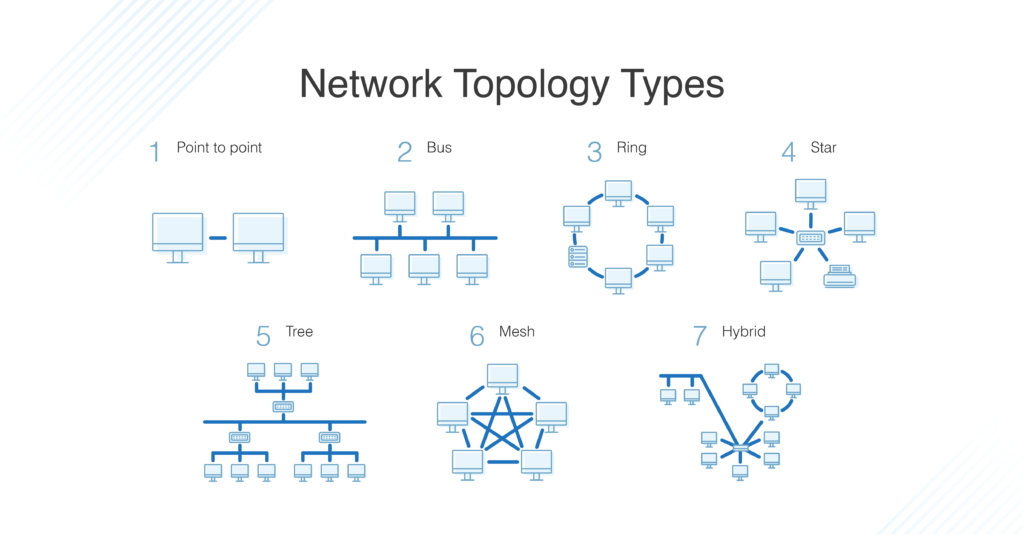
A network consists of nodes, links between nodes, and protocols that govern data transmission between nodes.
At whatever scale and complexity networks get to, you will understand what’s happening in all computer networks by learning the OSI model and 7 layers of networking.
What is the OSI Model?
The OSI model consists of 7 layers of networking.
First, what’s a layer?

No, a layer - not a lair . Here there are no dragons.
A layer is a way of categorizing and grouping functionality and behavior on and of a network.
In the OSI model, layers are organized from the most tangible and most physical, to less tangible and less physical but closer to the end user.
Each layer abstracts lower level functionality away until by the time you get to the highest layer. All the details and inner workings of all the other layers are hidden from the end user.
How to remember all the names of the layers? Easy.
- Please | Physical Layer
- Do | Data Link Layer
- Not | Network Layer
- Tell (the) | Transport Layer
- Secret | Session Layer
- Password (to) | Presentation Layer
- Anyone | Application Layer
Keep in mind that while certain technologies, like protocols, may logically “belong to” one layer more than another, not all technologies fit neatly into a single layer in the OSI model. For example, Ethernet, 802.11 (Wifi) and the Address Resolution Protocol (ARP) procedure operate on >1 layer.
The OSI is a model and a tool, not a set of rules.
OSI Layer 1
Layer 1 is the physical layer . There’s a lot of technology in Layer 1 - everything from physical network devices, cabling, to how the cables hook up to the devices. Plus if we don’t need cables, what the signal type and transmission methods are (for example, wireless broadband).
Instead of listing every type of technology in Layer 1, I’ve created broader categories for these technologies. I encourage readers to learn more about each of these categories:
- Nodes (devices) and networking hardware components. Devices include hubs, repeaters, routers, computers, printers, and so on. Hardware components that live inside of these devices include antennas, amplifiers, Network Interface Cards (NICs), and more.
- Device interface mechanics. How and where does a cable connect to a device (cable connector and device socket)? What is the size and shape of the connector, and how many pins does it have? What dictates when a pin is active or inactive?
- Functional and procedural logic. What is the function of each pin in the connector - send or receive? What procedural logic dictates the sequence of events so a node can start to communicate with another node on Layer 2?
- Cabling protocols and specifications. Ethernet (CAT), USB, Digital Subscriber Line (DSL) , and more. Specifications include maximum cable length, modulation techniques, radio specifications, line coding, and bits synchronization (more on that below).
- Cable types. Options include shielded or unshielded twisted pair, untwisted pair, coaxial and so on. Learn more about cable types here .
- Signal type. Baseband is a single bit stream at a time, like a railway track - one-way only. Broadband consists of multiple bit streams at the same time, like a bi-directional highway.
- Signal transmission method (may be wired or cable-free). Options include electrical (Ethernet), light (optical networks, fiber optics), radio waves (802.11 WiFi, a/b/g/n/ac/ax variants or Bluetooth). If cable-free, then also consider frequency: 2.5 GHz vs. 5 GHz. If it’s cabled, consider voltage. If cabled and Ethernet, also consider networking standards like 100BASE-T and related standards.
The data unit on Layer 1 is the bit.
A bit the smallest unit of transmittable digital information. Bits are binary, so either a 0 or a 1. Bytes, consisting of 8 bits, are used to represent single characters, like a letter, numeral, or symbol.
Bits are sent to and from hardware devices in accordance with the supported data rate (transmission rate, in number of bits per second or millisecond) and are synchronized so the number of bits sent and received per unit of time remains consistent (this is called bit synchronization). The way bits are transmitted depends on the signal transmission method.
Nodes can send, receive, or send and receive bits. If they can only do one, then the node uses a simplex mode. If they can do both, then the node uses a duplex mode. If a node can send and receive at the same time, it’s full-duplex – if not, it’s just half-duplex.
The original Ethernet was half-duplex. Full-duplex Ethernet is an option now, given the right equipment.
How to Troubleshoot OSI Layer 1 Problems
Here are some Layer 1 problems to watch out for:
- Defunct cables, for example damaged wires or broken connectors
- Broken hardware network devices, for example damaged circuits
- Stuff being unplugged (...we’ve all been there)
If there are issues in Layer 1, anything beyond Layer 1 will not function properly.
Layer 1 contains the infrastructure that makes communication on networks possible.
It defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating physical links between network devices. - Source
Fun fact: deep-sea communications cables transmit data around the world. This map will blow your mind: https://www.submarinecablemap.com/
And because you made it this far, here’s a koala:

OSI Layer 2
Layer 2 is the data link layer . Layer 2 defines how data is formatted for transmission, how much data can flow between nodes, for how long, and what to do when errors are detected in this flow.
In more official tech terms:
- Line discipline. Who should talk for how long? How long should nodes be able to transit information for?
- Flow control. How much data should be transmitted?
- Error control - detection and correction . All data transmission methods have potential for errors, from electrical spikes to dirty connectors. Once Layer 2 technologies tell network administrators about an issue on Layer 2 or Layer 1, the system administrator can correct for those errors on subsequent layers. Layer 2 is mostly concerned with error detection, not error correction. ( Source )
There are two distinct sublayers within Layer 2:
- Media Access Control (MAC): the MAC sublayer handles the assignment of a hardware identification number, called a MAC address, that uniquely identifies each device on a network. No two devices should have the same MAC address. The MAC address is assigned at the point of manufacturing. It is automatically recognized by most networks. MAC addresses live on Network Interface Cards (NICs). Switches keep track of all MAC addresses on a network. Learn more about MAC addresses on PC Mag and in this article . Learn more about network switches here .
- Logical Link Control (LLC): the LLC sublayer handles framing addressing and flow control. The speed depends on the link between nodes, for example Ethernet or Wifi.
The data unit on Layer 2 is a frame .
Each frame contains a frame header, body, and a frame trailer:
- Header: typically includes MAC addresses for the source and destination nodes.
- Body: consists of the bits being transmitted.
- Trailer: includes error detection information. When errors are detected, and depending on the implementation or configuration of a network or protocol, frames may be discarded or the error may be reported up to higher layers for further error correction. Examples of error detection mechanisms: Cyclic Redundancy Check (CRC) and Frame Check Sequence (FCS). Learn more about error detection techniques here .
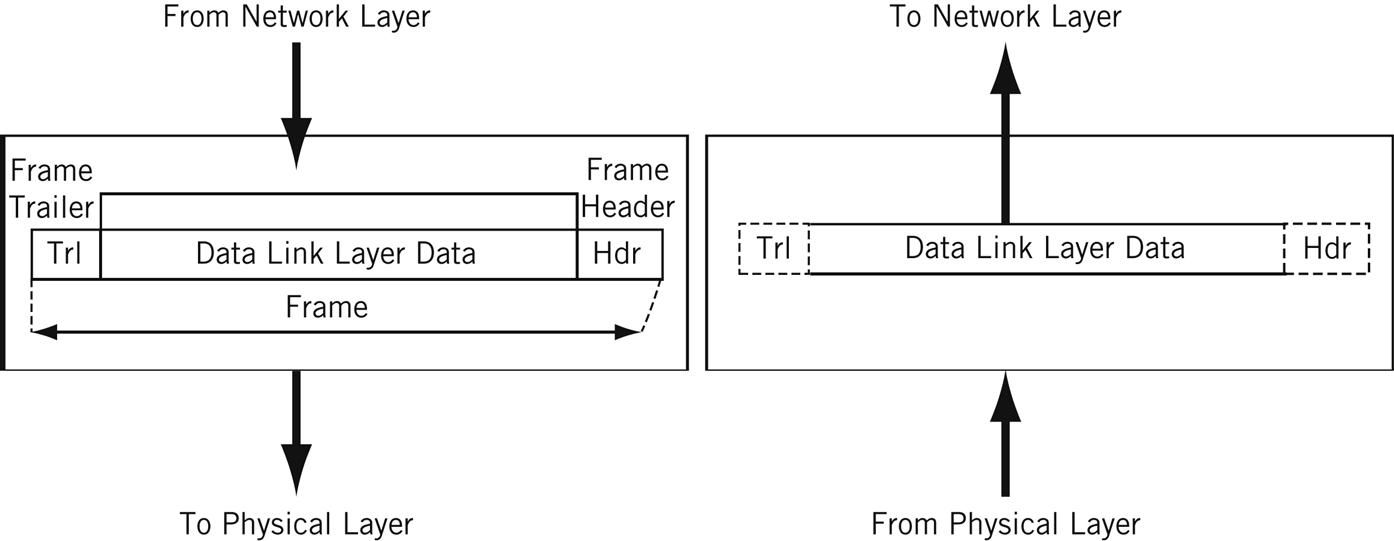
Typically there is a maximum frame size limit, called an Maximum Transmission Unit, MTU. Jumbo frames exceed the standard MTU, learn more about jumbo frames here .
How to Troubleshoot OSI Layer 2 Problems
Here are some Layer 2 problems to watch out for:
- All the problems that can occur on Layer 1
- Unsuccessful connections (sessions) between two nodes
- Sessions that are successfully established but intermittently fail
- Frame collisions
The Data Link Layer allows nodes to communicate with each other within a local area network. The foundations of line discipline, flow control, and error control are established in this layer.
OSI Layer 3
Layer 3 is the network layer . This is where we send information between and across networks through the use of routers. Instead of just node-to-node communication, we can now do network-to-network communication.
Routers are the workhorse of Layer 3 - we couldn’t have Layer 3 without them. They move data packets across multiple networks.
Not only do they connect to Internet Service Providers (ISPs) to provide access to the Internet, they also keep track of what’s on its network (remember that switches keep track of all MAC addresses on a network), what other networks it’s connected to, and the different paths for routing data packets across these networks.
Routers store all of this addressing and routing information in routing tables.
Here’s a simple example of a routing table:
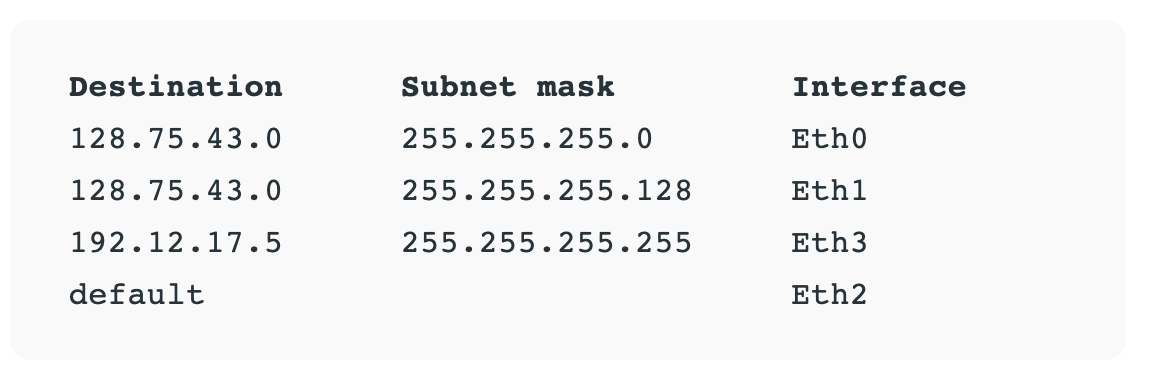
The data unit on Layer 3 is the data packet . Typically, each data packet contains a frame plus an IP address information wrapper. In other words, frames are encapsulated by Layer 3 addressing information.
The data being transmitted in a packet is also sometimes called the payload . While each packet has everything it needs to get to its destination, whether or not it makes it there is another story.
Layer 3 transmissions are connectionless, or best effort - they don't do anything but send the traffic where it’s supposed to go. More on data transport protocols on Layer 4.
Once a node is connected to the Internet, it is assigned an Internet Protocol (IP) address, which looks either like 172.16. 254.1 (IPv4 address convention) or like 2001:0db8:85a3:0000:0000:8a2e:0370:7334 (IPv6 address convention). Routers use IP addresses in their routing tables.
IP addresses are associated with the physical node’s MAC address via the Address Resolution Protocol (ARP), which resolves MAC addresses with the node’s corresponding IP address.
ARP is conventionally considered part of Layer 2, but since IP addresses don’t exist until Layer 3, it’s also part of Layer 3.
How to Troubleshoot OSI Layer 3 Problems
Here are some Layer 3 problems to watch out for:
- All the problems that can crop up on previous layers :)
- Faulty or non-functional router or other node
- IP address is incorrectly configured
Many answers to Layer 3 questions will require the use of command-line tools like ping , trace , show ip route , or show ip protocols . Learn more about troubleshooting on layer 1-3 here .
The Network Layer allows nodes to connect to the Internet and send information across different networks.
OSI Layer 4
Layer 4 is the transport layer . This where we dive into the nitty gritty specifics of the connection between two nodes and how information is transmitted between them. It builds on the functions of Layer 2 - line discipline, flow control, and error control.
This layer is also responsible for data packet segmentation, or how data packets are broken up and sent over the network.
Unlike the previous layer, Layer 4 also has an understanding of the whole message, not just the contents of each individual data packet. With this understanding, Layer 4 is able to manage network congestion by not sending all the packets at once.
The data units of Layer 4 go by a few names. For TCP, the data unit is a packet. For UDP, a packet is referred to as a datagram. I’ll just use the term data packet here for the sake of simplicity.
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two of the most well-known protocols in Layer 4.
TCP, a connection-oriented protocol, prioritizes data quality over speed.
TCP explicitly establishes a connection with the destination node and requires a handshake between the source and destination nodes when data is transmitted. The handshake confirms that data was received. If the destination node does not receive all of the data, TCP will ask for a retry.
TCP also ensures that packets are delivered or reassembled in the correct order. Learn more about TCP here .
UDP, a connectionless protocol, prioritizes speed over data quality. UDP does not require a handshake, which is why it’s called connectionless.
Because UDP doesn’t have to wait for this acknowledgement, it can send data at a faster rate, but not all of the data may be successfully transmitted and we’d never know.
If information is split up into multiple datagrams, unless those datagrams contain a sequence number, UDP does not ensure that packets are reassembled in the correct order. Learn more about UDP here .
TCP and UDP both send data to specific ports on a network device, which has an IP address. The combination of the IP address and the port number is called a socket.
Learn more about sockets here .
Learn more about the differences and similarities between these two protocols here .
How to Troubleshoot OSI Layer 4 Problems
Here are some Layer 4 problems to watch out for:
- Blocked ports - check your Access Control Lists (ACL) & firewalls
- Quality of Service (QoS) settings. QoS is a feature of routers/switches that can prioritize traffic, and they can really muck things up. Learn more about QoS here .
The Transport Layer provides end-to-end transmission of a message by segmenting a message into multiple data packets; the layer supports connection-oriented and connectionless communication.
OSI Layer 5
Layer 5 is the session layer . This layer establishes, maintains, and terminates sessions.
A session is a mutually agreed upon connection that is established between two network applications. Not two nodes! Nope, we’ve moved on from nodes. They were so Layer 4.
Just kidding, we still have nodes, but Layer 5 doesn’t need to retain the concept of a node because that’s been abstracted out (taken care of) by previous layers.
So a session is a connection that is established between two specific end-user applications. There are two important concepts to consider here:
- Client and server model: the application requesting the information is called the client, and the application that has the requested information is called the server.
- Request and response model: while a session is being established and during a session, there is a constant back-and-forth of requests for information and responses containing that information or “hey, I don’t have what you’re requesting.”
Sessions may be open for a very short amount of time or a long amount of time. They may fail sometimes, too.
Depending on the protocol in question, various failure resolution processes may kick in. Depending on the applications/protocols/hardware in use, sessions may support simplex, half-duplex, or full-duplex modes.
Examples of protocols on Layer 5 include Network Basic Input Output System (NetBIOS) and Remote Procedure Call Protocol (RPC), and many others.
From here on out (layer 5 and up), networks are focused on ways of making connections to end-user applications and displaying data to the user.
How to Troubleshoot OSI Layer 5 Problems
Here are some Layer 5 problems to watch out for:
- Servers are unavailable
- Servers are incorrectly configured, for example Apache or PHP configs
- Session failure - disconnect, timeout, and so on.
The Session Layer initiates, maintains, and terminates connections between two end-user applications. It responds to requests from the presentation layer and issues requests to the transport layer.
OSI Layer 6
Layer 6 is the presentation layer . This layer is responsible for data formatting, such as character encoding and conversions, and data encryption.
The operating system that hosts the end-user application is typically involved in Layer 6 processes. This functionality is not always implemented in a network protocol.
Layer 6 makes sure that end-user applications operating on Layer 7 can successfully consume data and, of course, eventually display it.
There are three data formatting methods to be aware of:
- American Standard Code for Information Interchange (ASCII): this 7-bit encoding technique is the most widely used standard for character encoding. One superset is ISO-8859-1, which provides most of the characters necessary for languages spoken in Western Europe.
- Extended Binary-Coded Decimal Interchange Code (EBDCIC): designed by IBM for mainframe usage. This encoding is incompatible with other character encoding methods.
- Unicode: character encodings can be done with 32-, 16-, or 8-bit characters and attempts to accommodate every known, written alphabet.
Learn more about character encoding methods in this article , and also here .
Encryption: SSL or TLS encryption protocols live on Layer 6. These encryption protocols help ensure that transmitted data is less vulnerable to malicious actors by providing authentication and data encryption for nodes operating on a network. TLS is the successor to SSL.
How to Troubleshoot OSI Layer 6 Problems
Here are some Layer 6 problems to watch out for:
- Non-existent or corrupted drivers
- Incorrect OS user access level
The Presentation Layer formats and encrypts data.
OSI Layer 7
Layer 7 is the application layer .
True to its name, this is the layer that is ultimately responsible for supporting services used by end-user applications. Applications include software programs that are installed on the operating system, like Internet browsers (for example, Firefox) or word processing programs (for example, Microsoft Word).
Applications can perform specialized network functions under the hood and require specialized services that fall under the umbrella of Layer 7.
Electronic mail programs, for example, are specifically created to run over a network and utilize networking functionality, such as email protocols, which fall under Layer 7.
Applications will also control end-user interaction, such as security checks (for example, MFA), identification of two participants, initiation of an exchange of information, and so on.
Protocols that operate on this level include File Transfer Protocol (FTP), Secure Shell (SSH), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), Domain Name Service (DNS), and Hypertext Transfer Protocol (HTTP).
While each of these protocols serve different functions and operate differently, on a high level they all facilitate the communication of information. ( Source )
How to Troubleshoot OSI Layer 7 Problems
Here are some Layer 7 problems to watch out for:
- All issues on previous layers
- Incorrectly configured software applications
- User error (... we’ve all been there)
The Application Layer owns the services and functions that end-user applications need to work. It does not include the applications themselves.
Our Layer 1 koala is all grown up.

Learning check - can you apply makeup to a koala?
Don’t have a koala?
Well - answer these questions instead. It’s the next best thing, I promise.
- What is the OSI model?
- What are each of the layers?
- How could I use this information to troubleshoot networking issues?
Congratulations - you’ve taken one step farther to understanding the glorious entity we call the Internet.
Learning Resources
Many, very smart people have written entire books about the OSI model or entire books about specific layers. I encourage readers to check out any O’Reilly-published books about the subject or about network engineering in general.
Here are some resources I used when writing this article:
- The Illustrated Network, 2nd Edition
- Protocol Data Unit (PDU): https://www.geeksforgeeks.org/difference-between-segments-packets-and-frames/
- Troubleshooting Along the OSI Model: https://www.pearsonitcertification.com/articles/article.aspx?p=1730891
- The OSI Model Demystified: https://www.youtube.com/watch?v=HEEnLZV2wGI
- OSI Model for Dummies: https://www.dummies.com/programming/networking/layers-in-the-osi-model-of-a-computer-network/
Chloe Tucker is an artist and computer science enthusiast based in Portland, Oregon. As a former educator, she's continuously searching for the intersection of learning and teaching, or technology and art. Reach out to her on Twitter @_chloetucker and check out her website at chloe.dev .
Read more posts .
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
How-To Geek
The 7 osi networking layers explained.
The Open Systems Interconnection (OSI) networking model defines a conceptual framework for communications between computer systems.
Quick Links
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
The Open Systems Interconnection (OSI) networking model defines a conceptual framework for communications between computer systems. The model is an ISO standard which identifies seven fundamental networking layers, from the physical hardware up to high-level software applications.
Each layer in the model handles a specific networking function. The standard helps administrators to visualize networks, isolate problems, and understand the use cases for new technologies. Many network equipment vendors advertise the OSI layer that their products are designed to slot into.
OSI was adopted as an international standard in 1984. It remains relevant today despite the changes to network implementation that have occurred since first publication. Cloud, edge, and IoT can all be accommodated within the model.
In this article, we'll explain each of the seven OSI layers in turn. We'll start from the lowest level, labelled as Layer 1.
1. Physical Layer
All networking begins with physical equipment. This layer encapsulates the hardware involved in the communications, such as switches and cables. Data is transferred as a stream of binary digits - 0 or 1 - that the hardware prepares from input it's been fed. The physical layer specifies the electrical signals that are used to encode the data over the wire, such as a 5-volt pulse to indicate a binary "1."
Errors in the physical layer tend to result in data not being transferred at all. There could be a break in the connection due to a missing plug or incorrect power supply. Problems can also arise when two components disagree on the physical encoding of data values. In the case of wireless connections, a weak signal can lead to bit loss during transmission.
2. Data Link Layer
The model's second layer concerns communication between two devices that are directly connected to each other in the same network. It's responsible for establishing a link that allows data to be exchanged using an agreed protocol. Many network switches operate at Layer 2.
The data link layer will eventually pass bits to the physical layer. As it sits above the hardware, the data link layer can perform basic error detection and correction in response to physical transfer issues. There are two sub-layers that define these responsibilities: Logical Link Control (LLC) that handles frame synchronization and error detection, and Media Access Control (MAC) which uses MAC addresses to constrain how devices acquire permission to transfer data.
3. Network Layer
The network layer is the first level to support data transfer between two separately maintained networks. It's redundant in situations where all your devices exist on the same network.
Data that comes to the network layer from higher levels is first broken up into packets suitable for transmission. Packets received from the remote network in response are reassembled into usable data.
The network layer is where several important protocols are first encountered. These include IP (for determining the path to a destination), ICMP, routing, and virtual LAN. Together these mechanisms facilitate inter-network communications with a familiar degree of usability. However operations at this level aren't necessarily reliable: messages aren't required to succeed and may not necessarily be retried.
4. Transport Layer
The transport layer provides higher-level abstractions for coordinating data transfers between devices. Transport controllers determine where data will be sent and the rate it should be transferred at.
Layer 4 is where TCP and UDP are implemented, providing the port numbers that allow devices to expose multiple communication channels. Load balancing is often situated at Layer 4 as a result, allowing traffic to be routed between ports on a target device.
Transport mechanisms are expected to guarantee successful communication. Stringent error controls are applied to recover from packet loss and retry failed transfers. Flow control is enforced so the sender doesn't overwhelm the remote device by sending data more quickly than the available bandwidth permits.
5. Session Layer
Layer 5 creates ongoing communication sessions between two devices. Sessions are used to negotiate new connections, agree on their duration, and gracefully close down the connection once the data exchange is complete. This layer ensures that sessions remain open long enough to transfer all the data that's being sent.
Checkpoint control is another responsibility that's held by Layer 5. Sessions can define checkpoints to facilitate progress updates and resumable transmissions. A new checkpoint could be set every few megabytes for a file upload, allowing the sender to continue from a particular point if the transfer gets interrupted.
Many significant protocols operate at Layer 5 including authentication and logon technologies such as LDAP and NetBIOS. These establish semi-permanent communication channels for managing an end user session on a specific device.
6. Presentation Layer
The presentation layer handles preparation of data for the application layer that comes next in the model. After data has made it up from the hardware, through the data link, and across the transport, it's almost ready to be consumed by high-level components. The presentation layer completes the process by performing any formatting tasks that may be required.
Decryption, decoding, and decompression are three common operations found at this level. The presentation layer processes received data into formats that can be eventually utilized by a client application. Similarly, outward-bound data is reformatted into compressed and encrypted structures that are suitable for network transmission.
TLS is one major technology that's part of the presentation layer. Certificate verification and data decryption is handled before requests reach the network client, allowing information to be consumed with confidence that it's authentic.
7. Application Layer
The application layer is the top of the stack. It represents the functionality that's perceived by network end users. Applications in the OSI model provide a convenient end-to-end interface to facilitate complete data transfers, without making you think about hardware, data links, sessions, and compression.
Despite its name, this layer doesn't relate to client-side software such as your web browser or email client. An application in OSI terms is a protocol that caters for the complete communication of complex data through layers 1-6.
HTTP, FTP, DHCP, DNS, and SSH all exist at the application layer. These are high-level mechanisms which permit direct transfers of user data between an origin device and a remote server. You only need minimal knowledge of the workings of the other layers.
The seven OSI layers describe the transfer of data through computer networks. Understanding the functions and responsibilities of each layer can help you identify the source of problems and assess the intended use case for new components.
OSI is an abstract model that doesn't directly map to the specific networking implementations commonly used today. As an example, the TCP/IP protocol works on its own simpler system of four layers: Network Access, Internet, Transport, and Application. These abstract and absorb the equivalent OSI layers: the application layer spans OSI L5 to L7, while L1 and L2 are combined in TCP/IP's concept of Network Access.
OSI remains applicable despite its lack of direct real-world application. It's been around so long that it's widely understood among administrators from all backgrounds. Its relatively high level of abstraction has also ensured it's remained relevant in the face of new networking paradigms, many of which have targeted Layer 3 and above. An awareness of the seven layers and their responsibilities can still help you appreciate the flow of data through a network while uncovering integration opportunities for new components.
Presentation layer and Session layer of the OSI model
There are two popular networking models: the OSI layers model and the TCP/IP layers model. The presentation layer and session layer exist only in the OSI layers models. The TCP/IP layers model merges them into the application layer.
The Presentation Layer
The presentation layer is the sixth layer of the OSI Reference model. It defines how data and information is transmitted and presented to the user. It translates data and format code in such a way that it is correctly used by the application layer.
It identifies the syntaxes that different applications use and formats data using those syntaxes. For example, a web browser receives a web page from a web server in the HTML language. HTML language includes many tags and markup that have no meaning for the end user but they have special meaning for the web browser. the web browser uses the presentation layer's logic to read those syntaxes and format data in such a way the web server wants it to be present to the user.

On the sender device, it encapsulates and compresses data before sending it to the network to increase the speed and security of the network. On the receiver device, it de-encapsulates and decompresses data before presenting it to the user.
Examples of the presentation layer
Example standards for representing graphical information: JPEG, GIF, JPEG, and TIFF.
Example standards for representing audio information: WAV, MIDI, MP3.
Example standards for representing video information: WMV, MOV, MP4, MPEG.
Example standards for representing text information: doc, xls, txt, pdf.
Functions of the presentation layer
- It formats and presents data and information.
- It encrypts and compresses data before giving it to the session layer.
- It de-encrypts and decompresses the encrypted and compressed data it receives from the session layer.
Session layer
The session layer is the fifth layer of the OSI layers model. It is responsible for initiating, establishing, managing, and terminating sessions between the local application and the remote applications.
It defines standards for three modes of communication: full duplex, half-duplex, and simplex.

In the full duplex mode, both devices can send and receive data simultaneously. The internet connection is an example of the full duplex mode.
In the half duplex mode, only one device can send data at a time. A telephone conversation is an example of the half-duplex mode.
In the simplex mode, only one device can send data. A radio broadcast is an example of the simplex mode.
Functions of the session layer
- It is responsible for terminating sessions, creating checkpoints, and recovering data when sessions are interrupted.
- It opens and maintains logical communication channels between network applications running on the local host and network applications running on the remote host.
- If a network application uses an authentication mechanism before it opens a logical communication channel (session) with the remote host, it handles the authentication process.
Examples of the session layer
Structure Query Language (SQL), Remote Procedure Call (RPC), and Network File System (NFS) are examples of the session layer.
By ComputerNetworkingNotes Updated on 2023-10-30 05:30:01 IST
ComputerNetworkingNotes CCNA Study Guide Presentation layer and Session layer of the OSI model
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial
Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
- Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
- Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer

What is OSI Model? – Layers of OSI Model
OSI stands for Open Systems Interconnection . It is a 7-layer architecture with each layer having specific functionality to perform. All these 7 layers work collaboratively to transmit the data from one person to another across the globe. OSI model was developed by ISO – ‘International Organization for Standardization ‘, in the year 1984.
Prerequisite: Basics of Computer Networking
Table of Content
What is OSI Model?
What are the 7 layers of the osi model, physical layer – layer 1, data link layer (dll) – layer 2, network layer – layer 3, transport layer – layer 4, session layer – layer 5, presentation layer – layer 6, application layer – layer 7, what is the flow of data in osi model, advantages of osi model, osi model in a nutshell, osi vs tcp/ip model.
The OSI model, created in 1984 by ISO, is a reference framework that explains the process of transmitting data between computers. It is divided into seven layers that work together to carry out specialised network functions, allowing for a more systematic approach to networking.
The OSI model consists of seven abstraction layers arranged in a top-down order:
- Physical Layer
- Session Layer
- Presentation Layer
The lowest layer of the OSI reference model is the physical layer. It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits. It is responsible for transmitting individual bits from one node to the next. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the Data Link layer, which will put the frame back together.

Functions of the Physical Layer
- Bit synchronization: The physical layer provides the synchronization of the bits by providing a clock. This clock controls both sender and receiver thus providing synchronization at the bit level.
- Bit rate control: The Physical layer also defines the transmission rate i.e. the number of bits sent per second.
- Physical topologies: Physical layer specifies how the different, devices/nodes are arranged in a network i.e. bus, star, or mesh topology.
- Transmission mode: Physical layer also defines how the data flows between the two connected devices. The various transmission modes possible are Simplex, half-duplex and full-duplex.
Note: Hub, Repeater, Modem, and Cables are Physical Layer devices. Network Layer, Data Link Layer, and Physical Layer are also known as Lower Layers or Hardware Layers .
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the DLL to transmit it to the Host using its MAC address. The Data Link Layer is divided into two sublayers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet received from the Network layer is further divided into frames depending on the frame size of the NIC(Network Interface Card). DLL also encapsulates Sender and Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
Functions of the Data Link Layer
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit a set of bits that are meaningful to the receiver. This can be accomplished by attaching special bit patterns to the beginning and end of the frame.
- Physical addressing: After creating frames, the Data link layer adds physical addresses (MAC addresses) of the sender and/or receiver in the header of each frame.
- Error control: The data link layer provides the mechanism of error control in which it detects and retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both sides else the data may get corrupted thus, flow control coordinates the amount of data that can be sent before receiving an acknowledgment.
- Access control: When a single communication channel is shared by multiple devices, the MAC sub-layer of the data link layer helps to determine which device has control over the channel at a given time.

Note: Packet in the Data Link layer is referred to as Frame. Data Link layer is handled by the NIC (Network Interface Card) and device drivers of host machines. Switch & Bridge are Data Link Layer devices.
The network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e. selection of the shortest path to transmit the packet, from the number of routes available. The sender & receiver’s IP addresses are placed in the header by the network layer.
Functions of the Network Layer
- Routing: The network layer protocols determine which route is suitable from source to destination. This function of the network layer is known as routing.
- Logical Addressing: To identify each device on Internetwork uniquely, the network layer defines an addressing scheme. The sender & receiver’s IP addresses are placed in the header by the network layer. Such an address distinguishes each device uniquely and universally.
Note: Segment in the Network layer is referred to as Packet . Network layer is implemented by networking devices such as routers and switches.
The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments . It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found.
At the sender’s side: The transport layer receives the formatted data from the upper layers, performs Segmentation , and also implements Flow and error control to ensure proper data transmission. It also adds Source and Destination port numbers in its header and forwards the segmented data to the Network Layer.
Note: The sender needs to know the port number associated with the receiver’s application. Generally, this destination port number is configured, either by default or manually. For example, when a web application requests a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default ports assigned. At the receiver’s side: Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
Functions of the Transport Layer
- Segmentation and Reassembly: This layer accepts the message from the (session) layer, and breaks the message into smaller units. Each of the segments produced has a header associated with it. The transport layer at the destination station reassembles the message.
- Service Point Addressing: To deliver the message to the correct process, the transport layer header includes a type of address called service point address or port address. Thus by specifying this address, the transport layer makes sure that the message is delivered to the correct process.
Services Provided by Transport Layer
- Connection-Oriented Service
- Connectionless Service
1. Connection-Oriented Service: It is a three-phase process that includes
- Connection Establishment
- Data Transfer
- Termination/disconnection
In this type of transmission, the receiving device sends an acknowledgment, back to the source after a packet or group of packets is received. This type of transmission is reliable and secure.
2. Connectionless service: It is a one-phase process and includes Data Transfer. In this type of transmission, the receiver does not acknowledge receipt of a packet. This approach allows for much faster communication between devices. Connection-oriented service is more reliable than connectionless Service.
Note: Data in the Transport Layer is called Segments . Transport layer is operated by the Operating System. It is a part of the OS and communicates with the Application Layer by making system calls. The transport layer is called as Heart of the OSI model. Device or Protocol Use : TCP, UDP NetBIOS, PPTP
This layer is responsible for the establishment of connection, maintenance of sessions, and authentication, and also ensures security.
Functions of the Session Layer
- Session establishment, maintenance, and termination: The layer allows the two processes to establish, use, and terminate a connection.
- Synchronization: This layer allows a process to add checkpoints that are considered synchronization points in the data. These synchronization points help to identify the error so that the data is re-synchronized properly, and ends of the messages are not cut prematurely and data loss is avoided.
- Dialog Controller: The session layer allows two systems to start communication with each other in half-duplex or full-duplex.
Note: All the below 3 layers(including Session Layer) are integrated as a single layer in the TCP/IP model as the ????pplication Layer”. Implementation of these 3 layers is done by the network application itself. These are also known as Upper Layers or Software Layers. Device or Protocol Use : NetBIOS, PPTP.
For example:-
Let us consider a scenario where a user wants to send a message through some Messenger application running in his browser. The “Messenger” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, encrypted (if any secure data), and converted into bits (0’s and 1’s) so that it can be transmitted.

Communication in Session Layer
The presentation layer is also called the Translation layer . The data from the application layer is extracted here and manipulated as per the required format to transmit over the network.
Functions of the Presentation Layer
- Translation: For example, ASCII to EBCDIC.
- Encryption/ Decryption: Data encryption translates the data into another form or code. The encrypted data is known as the ciphertext and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data.
- Compression: Reduces the number of bits that need to be transmitted on the network.
Note: Device or Protocol Use: JPEG, MPEG, GIF
At the very top of the OSI Reference Model stack of layers, we find the Application layer which is implemented by the network applications. These applications produce the data, which has to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user.
Example : Application – Browsers, Skype Messenger, etc.
Note: 1. The application Layer is also called Desktop Layer. 2. Device or Protocol Use : SMTP
Functions of the Application Layer
The main functions of the application layer are given below.
- Network Virtual Terminal: It allows a user to log on to a remote host.
- FTAM- File transfer access and management: This application allows a user to access files in a remote host, retrieve files in a remote host, and manage or control files from a remote computer.
- Mail Services: Provide email service.
- Directory Services: This application provides distributed database sources and access for global information about various objects and services.
Note: OSI model acts as a reference model and is not implemented on the Internet because of its late invention. The current model being used is the TCP/IP model.
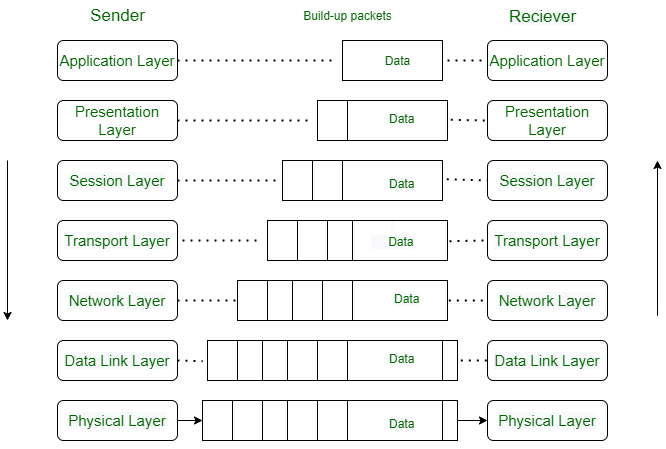
When we transfer information from one device to another, it travels through 7 layers of OSI model. First data travels down through 7 layers from the sender’s end and then climbs back 7 layers on the receiver’s end.
Let’s look at it with an Example:
Luffy sends an e-mail to his friend Zoro.
Step 1: Luffy interacts with e-mail application like Gmail, outlook, etc. Writes his email to send. (This happens in Layer 7: Application layer )
Step 2: Mail application prepares for data transmission like encrypting data and formatting it for transmission. (This happens in Layer 6: Presentation Layer )
Step 3: There is a connection established between the sender and receiver on the internet. (This happens in Layer 5: Session Layer )
Step 4: Email data is broken into smaller segments. It adds sequence number and error-checking information to maintain the reliability of the information. (This happens in Layer 4: Transport Layer )
Step 5: Addressing of packets is done in order to find the best route for transfer. (This happens in Layer 3: Network Layer )
Step 6: Data packets are encapsulated into frames, then MAC address is added for local devices and then it checks for error using error detection. (This happens in Layer 2: Data Link Layer )
Step 7: Lastly Frames are transmitted in the form of electrical/ optical signals over a physical network medium like ethernet cable or WiFi.
After the email reaches the receiver i.e. Zoro, the process will reverse and decrypt the e-mail content. At last, the email will be shown on Zoro’s email client.
OSI Model defines the communication of a computing system into 7 different layers. Advantages of OSI Model include:
- It divides network communication into 7 layers which makes it easier to understand and troubleshoot.
- It standardizes network communications, as each layer has fixed functions and protocols.
- Diagnosing network problems is easier with the OSI model.
- It is easier to improve with advancements as each layer can get updates separately.
Some key differences between the OSI model and the TCP/IP Model are:
- TCP/IP model consists of 4 layers but OSI model has 7 layers. Layers 5,6,7 of the OSI model are combined into the Application Layer of TCP/IP model and OSI layers 1 and 2 are combined into Network Access Layers of TCP/IP protocol.
- The TCP/IP model is older than the OSI model, hence it is a foundational protocol that defines how should data be transferred online.
- Compared to the OSI model, the TCP/IP model has less strict layer boundaries.
- All layers of the TCP/IP model are needed for data transmission but in the OSI model, some applications can skip certain layers. Only layers 1,2 and 3 of the OSI model are necessary for data transmission.
Did you Know? TCP/IP protocol ( Transfer Control Protocol/Internet Protocol ) was created by U.S. Department of Defense’s Advanced Research Projects Agency (ARPA) in 1970s.
We have discussed about What is OSI model?, What are layers of OSI model, How data flows in the 7 layers of OSI model, and the differences between TCP/IP protocol and OSI protocol.
OSI Model – FAQs
Is osi layer still used.
Yes, the OSI model is still used by networking professionals to understand data abstraction paths and processes better.
What is the highest layer of the OSI model?
Layer 7 or Application layer is highest layer of OSI model.
Please Login to comment...
- WhatsApp To Launch New App Lock Feature
- Node.js 21 is here: What’s new
- Zoom: World’s Most Innovative Companies of 2024
- 10 Best Skillshare Alternatives in 2024
- 30 OOPs Interview Questions and Answers (2024)
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
The OSI Model’s 7 Layers, Explained

The Open Systems Interconnection (OSI) model is a framework in network communication that simplifies complex network interactions into a structured format.
What Is the OSI Model?
The Open Systems Interconnection model is a framework in network communication designed to simplify complex network interactions into a structured format. This architecture has seven layers, each of which serves a specific function. All seven layers work together to create a robust and efficient network communication system.
Each of its seven layers has a distinct role, ensuring efficient data transfer from one device to another . The OSI model is essential for understanding how data is transmitted in a network and is also a practical guide for network protocol design and problem solving.
learn more about cybersecurity An Introduction to Microsegmentation in Network Security
The OSI model, developed by the International Organization for Standardization , outlines the essential functions of networking and telecommunications systems for practical application. It plays a crucial role in telecommunications, where vendors use it to define the features and capabilities of their products and services.
This approach allows for a detailed explanation of different aspects of network communication, including transport protocols, addressing schemes and data packaging methods. As a result, the OSI model resolves the complexities of network communication and fosters a more integrated and coherent digital world .
The 7 Layers of the OSI Model
Each layer of the OSI model serves a specific function, yet they work in harmony to create a robust and efficient network communication system. Understanding these layers provides valuable insights into the complexities of network design and operation, showcasing the intricate nature of modern digital communication.
Layer 7: Application Layer
Functionality: The Application Layer is the closest to the end user. It facilitates user interaction with networked systems, providing interfaces and protocols for web browsers, email clients and other applications.
Key protocols: Protocols like HTTP, FTP and SMTP operate at this layer, enabling services such as web browsing, file transfers and email communications.
Layer 6: Presentation Layer
Role: The Presentation Layer acts as a translator, converting data formats from the application layer into a network-compatible format and vice versa. It ensures that data sent from one system is readable by another.
Data formatting: This layer is responsible for data encryption and compression, playing a significant role in maintaining data privacy and efficient transmission.
Layer 5: Session Layer
Managing sessions: It establishes, manages and terminates sessions between applications. This layer ensures that sessions are maintained for the duration of the communication.
Coordination: The Session Layer coordinates communication between systems, managing dialogues and synchronizing data exchange.
Layer 4: Transport Layer
Data segmentation and control: The Transport Layer is crucial for segmenting data into smaller packets. It ensures end-to-end data integrity and delivery, managing flow control, error correction and sequencing.
Protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are key protocols in this layer, differing in their approach to data transmission.
Layer 3: Network Layer
Routing and addressing: This layer is responsible for logical addressing and routing data packets across different networks. It determines the best path for data to travel from source to destination.
Internet protocol: The Internet Protocol (IP), fundamental for internet data exchange, operates at this layer.
Layer 2: Data Link Layer
Framing and MAC addressing: The Data Link Layer frames data into packets. It handles physical addressing through MAC addresses, ensuring that data is directed to the correct hardware.
Error detection: This layer is also involved in error detection and handling, improving overall data transmission reliability.
Layer 1: Physical Layer
Physical transmission: The Physical Layer deals with the physical aspects of data transmission, including cable types, electrical signals and data rates.
Hardware components: It involves hardware components like cables, switches and network interface cards, forming the foundation of network communication.
How Data Flows in the OSI Model
Understanding this data flow process is crucial for professionals, as it aids in diagnosing and troubleshooting network issues, designing efficient network solutions and ensuring robust data security and management.
Encapsulation Process
When data is sent, it begins at the Application Layer and moves down through the layers. At each stage, it is encapsulated with the necessary headers, trailers, and other control information relevant to that layer. For instance, at the Transport Layer, data is segmented and encapsulated with port numbers, while at the Network Layer, IP addresses are added.
Each layer plays a role in preparing the data for transmission. The Presentation Layer may encrypt the data for security, while the Data Link Layer ensures it is formatted into frames suitable for physical transmission.
Data Transmission Across the Network
The Physical Layer transmits the raw bits over a physical medium, such as a cable or wireless network. This transmission is the actual movement of data across the network. In cases where data must move across different networks, the Network Layer’s routing functionalities become crucial. It ensures that data packets find the most efficient path to their destination.
Decapsulation Process
Upon reaching the destination, the data moves up the OSI model, with each layer removing its respective encapsulation. The Data Link Layer, for instance, removes framing, and the Transport Layer checks for transmission errors and reassembles the data segments. Once the data reaches the Application Layer, it is in its original format and ready to be used by the receiving application, whether it’s an email client, a web browser or any other networked software.
Seamless Data Flow
The OSI model ensures that each layer only communicates with its immediate upper and lower layers, creating a seamless flow. This layered approach means changes in one layer’s protocols or functionalities can occur without disrupting the entire network.
OSI Model Advantages
The OSI model is a cornerstone in network architecture for several reasons:
Simplification of network design
The OSI model’s layered approach breaks down complex network processes, making design and operation more manageable. Each layer focuses on a specific aspect of communication, allowing for independent development and easier troubleshooting.
Standardization and interoperability
It establishes universal standards for network communication, enabling different technologies to interact seamlessly. This interoperability is crucial for the efficient functioning of diverse network devices and applications.
Flexibility and Scalability
Adaptable to technological advancements, the OSI model allows individual layers to evolve without overhauling the entire system. This scalability makes it suitable for various network sizes and types.
Enhanced Security
Security measures are integrated at multiple layers, providing a robust defense against threats. Each layer can address specific security concerns, leading to comprehensive network protection.
Real-World Applications of the OSI Model
The OSI model’s influence extends well beyond theoretical concepts, playing a crucial role in various practical aspects of networking:
Network Design and Protocol Development
Network professionals use the OSI model as a blueprint for structuring and developing robust networks. It guides the creation of new protocols, ensuring seamless integration and functionality across different network layers.
Efficient Troubleshooting and Management
In troubleshooting, the OSI model provides a systematic approach for identifying issues, from physical connectivity to application-level errors. It also aids in network maintenance and performance optimization, addressing each layer to enhance overall efficiency.
Cybersecurity Strategy
The model is foundational in crafting layered security strategies . By implementing security measures at different layers, it offers comprehensive protection against various cyber threats. Understanding the OSI layers is key in detecting and mitigating attacks targeting specific network segments.
Educational and Training Tool
It serves as an essential framework in networking education, helping students and professionals alike understand complex network operations. The OSI model is a cornerstone in training programs , emphasizing the intricacies of network architecture and security.
safety first When and How to Run a Phishing Simulation
OSI Model vs. TCP/IP Model
While the OSI model offers a detailed conceptual framework, the TCP/IP model is recognized for its practical application in today’s internet-driven world.
Structural Differences
OSI model : Introduced as a comprehensive, protocol-independent framework, the OSI model details seven distinct layers, offering a more granular approach to network communication.
TCP/IP model : Developed earlier by the U.S. Department of Defense, the TCP/IP model consists of four layers (Application, Transport, Internet and Network Access), combining certain OSI layers.
Theoretical vs. Practical Approach
OSI model : Developed as a theoretical and universal networking model, it’s used more for educational purposes to explain how networks operate.
TCP/IP model : This model is designed around specific standard protocols, focusing on solving practical communication issues. It leaves sequencing and acknowledgment functions to the transport layer, differing from the OSI approach.
Adoption and Use
OSI model: While not widely implemented in its entirety, the OSI model’s clear layer separation is influential in protocol design and network education; simpler applications in the OSI framework may not utilize all seven layers, with only the first three layers (Physical, Data Link, and Network) being mandatory for basic data communication.
TCP/IP model : The dominant model used in most network architectures today, especially in internet-related communications. In TCP/IP, most applications engage all layers for communication.
Frequently Asked Questions
Why is the osi model important.
The OSI model is crucial for standardizing network communication and ensuring interoperability between various devices and systems. It simplifies network design and troubleshooting and serves as a fundamental educational tool in networking.
What are the 7 layers of the OSI model?
Layer 1: Physical Layer — Transmits raw data.
Layer 2: Data Link Layer — Manages direct links and framing.
Layer 3: Network Layer — Handles addressing and routing.
Layer 4: Transport Layer — Ensures reliable data transfer.
Layer 5: Session Layer — Manages connections.
Layer 6: Presentation Layer — Translates data formats.
Layer 7: Application Layer — Interfaces with applications.

HyperSense Software
Built In’s expert contributor network publishes thoughtful, solutions-oriented stories written by innovative tech professionals. It is the tech industry’s definitive destination for sharing compelling, first-person accounts of problem-solving on the road to innovation.
Great Companies Need Great People. That's Where We Come In.
- Domain Names
- Domain Name Search
- Free Domain Transfer
- .com Domain
- 1 Dollar Domain
- Cheap Domain
- Free Domain
- Buy SSL Certificate
- Website Builder
- Website Platforms
- Website Templates
- Web Design Services
- eCommerce Website Builder
- Local Business Listing
- Web Hosting
- WordPress Hosting
- 1 Dollar Hosting
- Windows Hosting
- Free Website Hosting
- Create Business Email
- HiDrive Cloud Storage
- Microsoft 365 Business
- Cloud Server
- VPS Hosting
- Dedicated Servers
- Rent a Server
- IONOS Cloud
- Business Name Generator
- Logo Creator
- Favicon Generator
- Whois Lookup
- Website Checker
- SSL Checker
- IP Address Check
What is the presentation layer in the OSI model?
The presentation layer is the sixth layer in the OSI model and is responsible for converting different file formats. This allows two systems to communicate. Other tasks carried out by the sixth layer include data compression and encryption.
What is the presentation layer?
What does the presentation layer do, which format does the presentation layer use, presentation layer protocols, skipping the presentation layer.
The presentation layer is the sixth layer of the OSI model. It is primarily used to convert different file formats between the sender and the receiver . The OSI model is a reference model that is used to define communication standards between two devices within a network . The development of this standard began in the 1970s and it was first published at the beginning of the following decade. This standard enables seamless interaction between different technical systems.
The model is made up of a total of seven different layers, all having their own clearly defined tasks. While there are clear boundaries between the layers, the layers interact with each other, with each layer building off the one below it. The different layers are as follows:
- Physical layer
- Data link layer
- Network layer
- Transport layer
- Session layer
- Presentation layer
- Application layer
The presentation layer interacts closely with the application layer, which is located directly above it. The presentation layer’s main task is to present data in such a way that it can be understood and interpreted from both the system sending the data and the system receiving it. After this has been accomplished, the application layer then determines how the data should be structured and what sort of data and values are permissible.
Using these entries, a command set, or an abstract transfer syntax, is then automatically created. The presentation layer now has the task of transferring the data in such a way that it is readable without changing the information contained within it.
The presentation layer is often also responsible for the encryption and decryption of data . The information is first encrypted on the sender’s side and then sent to the receiver in an encrypted state. Keys and encryption methods are then exchanged in the presentation layer. The recipient is then able to decrypt the unreadable data and convert it into a format that can be understood and interpreted.
If data is shown during a transfer, we often use the term transfer syntax. These are separated into the abstract transfer syntax , in which the transferred values are written, and the concrete syntax, which contains a definition of the value coding.
The receiver can only process and understand the data they receive if they receive all of the information from the presentation layer. The most common definition language is Abstract Syntax Notation One (ASN.1) , which is also recommended by the ISO. The ISO is an organization that is responsible for developing international standards in technology, management and manufacturing.
The presentation layer has many different formats. The most common text formats are the ASCII (American Standard Code for Information Interchange) and EBCDIC (Extended Binary-Coded Decimal Interchange Code). The most common image formats are GIF, JPEG and TIFF. Widely used video formats include MIDI, MPEG and QuickTime.
There are many different presentation layer protocols as well as transfer and encryption technologies in the presentation layer. These include:
The tasks which are carried out by the presentation layer are not always necessary for communication between two systems. In instances where both systems use the same formats, data conversion is not necessary. Additionally, encryption and compression are not required for every interaction and can also be carried out in another layer of the OSI model. If this is the case, the presentation layer can be skipped and the application layer (7) can communicate directly with the session layer (5) instead .
- Encyclopedia
Build or host a website, launch a server, or store your data and more with our most popular products for less.

What is the OSI Model?
The Open Systems Interconnection (OSI) model is a conceptual framework that divides network communications functions into seven layers. Sending data over a network is complex because various hardware and software technologies must work cohesively across geographical and political boundaries. The OSI data model provides a universal language for computer networking, so diverse technologies can communicate using standard protocols or rules of communication. Every technology in a specific layer must provide certain capabilities and perform specific functions to be useful in networking. Technologies in the higher layers benefit from abstraction as they can use lower-level technologies without having to worry about underlying implementation details.
Why is the OSI model important?
The layers of the Open Systems Interconnection (OSI) model encapsulate every type of network communication across both software and hardware components. The model was designed to allow two standalone systems to communicate via standardised interfaces or protocols based on the current layer of operation.
The benefits of the OSI model are given next.
Shared understanding of complex systems
Engineers can use the OSI model to organize and model complex networked system architectures. They can separate the operating layer of each system component according to its main functionality. The ability to decompose a system into smaller, manageable parts via abstraction makes it easier for people to conceptualize it as a whole.
Faster research and development
With the OSI reference model, engineers can understand their work better. They know which technological layer (or layers) they’re developing for when they create new, networked systems that need to communicate with each other. Engineers can develop networked systems and take advantage of a series of repeatable processes and protocols.
Flexible standardization
The OSI model does not specify the protocols to use between levels, but rather the tasks that protocols perform. It standardizes network communication development so people can rapidly understand, build, and decompose highly complex systems—all without prior knowledge of the system. It also abstracts details, so engineers don’t require the understanding of every aspect of the model. In modern applications, the lower levels of networking and protocols are abstracted away to simplify system design and development. The following image shows how the OSI model is used in modern application development.

What are the seven layers of the OSI model?
The Open Systems Interconnection (OSI) model was developed by the International Organization for Standardization and others in the late 1970s. It was published in its first form in 1984 as ISO 7498, with the current version being ISO/IEC 7498-1:1994. The seven layers of the model are given next.
Physical layer
The physical layer refers to the physical communication medium and the technologies to transmit data across that medium. At its core, data communication is the transfer of digital and electronic signals through various physical channels like fiber-optic cables, copper cabling, and air. The physical layer includes standards for technologies and metrics closely related with the channels, such as Bluetooth, NFC, and data transmission speeds.
Data link layer
The data link layer refers to the technologies used to connect two machines across a network where the physical layer already exists. It manages data frames, which are digital signals encapsulated into data packets. Flow control and error control of data are often key focuses of the data link layer. Ethernet is an example of a standard at this level. The data link layer is often split into two sub-layers: the Media Access Control (MAC) layer and Logical Link Control (LLC) layer.
Network layer
The network layer is concerned with concepts such as routing, forwarding, and addressing across a dispersed network or multiple connected networks of nodes or machines. The network layer may also manage flow control. Across the internet, the Internet Protocol v4 (IPv4) and IPv6 are used as the main network layer protocols.
Transport layer
The primary focus of the transport layer is to ensure that data packets arrive in the right order, without losses or errors, or can be seamlessly recovered if required. Flow control, along with error control, is often a focus at the transport layer. At this layer, commonly used protocols include the Transmission Control Protocol (TCP), a near-lossless connection-based protocol, and the User Datagram Protocol (UDP), a lossy connectionless protocol. TCP is commonly used where all data must be intact (e.g. file share), whereas UDP is used when retaining all packets is less critical (e.g. video streaming).
Session layer
The session layer is responsible for network coordination between two separate applications in a session. A session manages the beginning and ending of a one-to-one application connection and synchronization conflicts. Network File System (NFS) and Server Message Block (SMB) are commonly used protocols at the session layer.
Presentation layer
The presentation layer is primarily concerned with the syntax of the data itself for applications to send and consume. For example, Hypertext Markup Language (HTML) , JavaScipt Object Notation (JSON) , and Comma Separated Values (CSV) are all modeling languages to describe the structure of data at the presentation layer.
Application layer
The application layer is concerned with the specific type of application itself and its standardized communication methods. For example, browsers can communicate using HyperText Transfer Protocol Secure (HTTPS), and HTTP and email clients can communicate using POP3 (Post Office Protocol version 3) and SMTP (Simple Mail Transfer Protocol).
Not all systems that use the OSI model implement every layer.
How does communication happen in the OSI model?
The layers in the Open Systems Interconnection (OSI) model are designed so that an application can communicate over a network with another application on a different device, no matter the complexity of the application and underlying systems. To do this, various standards and protocols are used to communicate with the layer above or below. Each of the layers is independent and only aware of the interfaces to communicate with the layer above and below it.
By chaining together all these layers and protocols, complex data communications can be sent from one high-level application to another. The process works as follows:
- The sender’s application layer passes data communication down to the next lower layer.
- Each layer adds its own headers and addressing to the data before passing it on.
- Data communication moves down the layers until it is eventually transmitted through the physical medium.
- At the other end of the medium, each layer processes the data according to the relevant headers at that level.
- At the receiver end, data moves up the layer and is gradually unpacked until the application at the other end receives it.
What are alternatives to the OSI model?
Various networking models were used in the past, such as Sequenced Packet Exchange/Internet Packet Exchange (SPX/IPX) and Network Basic Input Output System (NetBIOS). Today, the main alternative to the Open Systems Interconnection (OSI) model is the TCP/IP model.
The TCP/IP model
The TCP/IP model is comprised of five different layers:
- The physical layer
- The data link layer
- The network layer
- The transport layer
- They application layer
While layers like the physical layer, network layer, and application layer appear to map directly to the OSI model, this isn’t quite the case. Instead, the TCP/IP model most accurately maps to the structure and protocols of the internet.
The OSI model remains a popular networking model to describe how networking operates from a holistic perspective for educational purposes. However, the TCP/IP model is now more commonly used in practice.
A note on proprietary protocols and models
It’s important to note that not all internet-based systems and applications follow the TCP/IP model or the OSI model. Similarly, not all offline-based networked systems and applications use the OSI model or any other model.
Both the OSI and TCP/IP models are open standards. They’re designed so that anyone can use them, or further build them out to meet specific requirements.
Organizations also design their own internal, proprietary standards, including protocols and models, that are closed-source and only for use within their systems. Sometimes, they may subsequently release them to the public for interoperability and further community development. An example is s2n-tls, a TLS protocol that was originally a proprietary Amazon Web Services (AWS) protocol but is now open source.
How can AWS meet your computer networking requirements?
AWS helps organizations design, deploy, and scale networked systems and applications with less friction.
We have a robust suite of AWS Networking and Content Delivery offerings. They’re designed to complement and integrate with your internal applications and services, across all levels of network operations. Here are some examples:
- AWS App Mesh provides secure, application-level networking for all your services, with built-in communications monitoring and control
- Amazon CloudFront is a content delivery network (CDN) service built for high performance, security, and developer convenience
- AWS Direct Connect offers a direct connection, which doesn’t touch the internet, from your organization to your AWS resources
- Elastic Load Balancing (ELB) distributes incoming network traffic across AWS targets to improve application scalability
Get started with networked systems and applications on AWS by creating an account today.
Next Steps on AWS
Ending Support for Internet Explorer

Computer Network
- Operating Systems
- Computer Fundamentals
- Interview Q
Physical Layer
Data link layer, network layer, routing algorithm, transport layer, application layer, application protocols, network security.
Interview Questions
- Send your Feedback to [email protected]
Help Others, Please Share

Learn Latest Tutorials
Transact-SQL
Reinforcement Learning
R Programming
React Native
Python Design Patterns
Python Pillow
Python Turtle
Preparation

Verbal Ability

Company Questions
Trending Technologies
Artificial Intelligence
Cloud Computing
Data Science
Machine Learning
B.Tech / MCA
Data Structures
Operating System
Compiler Design
Computer Organization
Discrete Mathematics
Ethical Hacking
Computer Graphics
Software Engineering
Web Technology
Cyber Security
C Programming
Control System
Data Mining
Data Warehouse


IMAGES
VIDEO
COMMENTS
Prerequisite : OSI Model. Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required ...
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
What is Presentation Layer? Definition: Presentation layer is 6th layer in the OSI model, and its main objective is to present all messages to upper layer as a standardized format.It is also known as the "Translation layer". This layer takes care of syntax and semantics of messages exchanged in between two communication systems. Presentation layer has responsible that receiver can ...
The presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. On the sending system it is responsible for conversion to standard, transmittable formats. [7] On the receiving system it is responsible for the translation, formatting, and delivery of ...
OSI model, the transport layer is only connection-oriented. A layer of the TCP/IP model is both connection-oriented and connectionless. In OSI model, data link layer and physical are separate layers. In TCP data link layer and physical layer are combined as a single host-to-network layer. The minimum size of the OSI header is 5 bytes.
The presentation layer in the OSI model has five main functions within the frame of presentation layer protocols. Character Code Translation A character code is a representation of text using a ...
Chloe Tucker. This article explains the Open Systems Interconnection (OSI) model and the 7 layers of networking, in plain English. The OSI model is a conceptual framework that is used to describe how a network functions. In plain English, the OSI model helped standardize the way computer systems send information to each other.
Some common Layer 6 protocols are ASCII, JPEG, GIF, MPEG, and PNG. Another main function of the presentation layer is the encryption and decryption of data sent across a network. Most encryption communication protocols straddle multiple layers of the OSI model, but the actual encryption function is Layer 6.
OSI model Layer Protocol data unit (PDU) Function; Host layers 7 Application: Data: High-level protocols such as for resource sharing or remote file access, e.g. HTTP. 6 ... The presentation layer handles protocol conversion, data encryption, data decryption, data compression, data decompression, incompatibility of data representation between ...
The presentation layer is the sixth layer in the OSI model. Known as a translator, the presentation layer converts data into an accurate, well-defined, standard format after it receives it from the application layer. The converted format varies, however, based on the type of data received. Some formats include:
Data Link Layer. Network Layer. Transport Layer. Session Layer. Presentation Layer. Application Layer. Summary. The Open Systems Interconnection (OSI) networking model defines a conceptual framework for communications between computer systems. The model is an ISO standard which identifies seven fundamental networking layers, from the physical ...
The 7 layers of the OSI model. The layers are: Layer 1—Physical; Layer 2—Data Link; Layer 3—Network; Layer 4—Transport; Layer 5—Session; Layer 6—Presentation; Layer 7—Application. It ...
Web browsers and other internet-connected apps, such as Outlook and Skype, use Layer 7 application protocols. Layer 6. The presentation layer. ... Multiprotocol Label Switching , which operates at an OSI model layer that lies between the Layer 2 data-link layer and the Layer 3 network layer -- MPLS can carry a variety of traffic, ...
The presentation layer is the sixth layer of the OSI Reference model. It defines how data and information is transmitted and presented to the user. It translates data and format code in such a way that it is correctly used by the application layer. It identifies the syntaxes that different applications use and formats data using those syntaxes.
TCP/IP model consists of 4 layers but OSI model has 7 layers. Layers 5,6,7 of the OSI model are combined into the Application Layer of TCP/IP model and OSI layers 1 and 2 are combined into Network Access Layers of TCP/IP protocol. The TCP/IP model is older than the OSI model, hence it is a foundational protocol that defines how should data be ...
The OSI model ensures that each layer only communicates with its immediate upper and lower layers, creating a seamless flow. This layered approach means changes in one layer's protocols or functionalities can occur without disrupting the entire network. OSI Model Advantages. The OSI model is a cornerstone in network architecture for several ...
The presentation layer is the sixth layer of the OSI model. It is primarily used to convert different file formats between the sender and the receiver.The OSI model is a reference model that is used to define communication standards between two devices within a network.The development of this standard began in the 1970s and it was first published at the beginning of the following decade.
The lowest layer in the OSI model, the physical layer, is responsible for the transmission and reception of raw data between the network devices and the transmission medium. It stores the information or data in the form of bits and transit bits from one node to another: The physical layer plays a vital role in controlling the transmission rate. ...
The OSI model does not specify the protocols to use between levels, but rather the tasks that protocols perform. It standardizes network communication development so people can rapidly understand, build, and decompose highly complex systems—all without prior knowledge of the system. ... Presentation layer. The presentation layer is primarily ...
The Open Systems Interconnection protocols are a family of information exchange standards developed jointly by the ISO and the ITU-T.The standardization process began in 1977. While the seven-layer OSI model is often used as a reference for teaching and documentation, the protocols originally conceived for the model did not gain popularity, and only X.400, X.500, and IS-IS have achieved ...
The presentation layer is the 6 th layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine. It converts one format of data to another format of data if both sender and receiver understand different formats; hence this layer is also called the ...
The Presentation Layer, situated at Layer 6 of the OSI model, acts as an intermediary between the Application Layer (Layer 7) and the Session Layer (Layer 5). Its primary function is to ensure ...
18. The session layer is meant to store states between two connections, like what we use cookies for when working with web programming. The presentation layer is meant to convert between different formats. This was simpler when the only format that was worried about was character encoding, ie ASCII and EBCDIC.
OSPF, EIGRP, RIP, and BGP run on top of IP 1. That does not make IS-IS a layer-2 protocol. If anything, you could call it a layer-3 protocol, OSPF a layer-4 protocol, and BGP a layer-5 protocol. But seriously, whatever. OSPF and EIGRP use their own transport layers to implement reliable packet delivery. RIP uses UDP and hopes for the best, and ...