Core Research and Innovation Areas in Cyber-Physical Systems of Systems
Initial Findings of the CPSoS Project
- Conference paper
- First Online: 01 November 2015
- Cite this conference paper

- S. Engell 15 ,
- R. Paulen 15 ,
- M. A. Reniers 16 ,
- C. Sonntag 17 &
- H. Thompson 18
Part of the book series: Lecture Notes in Computer Science ((LNISA,volume 9361))
Included in the following conference series:
- International Workshop on Design, Modeling, and Evaluation of Cyber Physical Systems
1529 Accesses
26 Citations
The CPSoS project is developing a roadmap for future research and innovation in cyber-physical systems of systems. This paper presents preliminary findings and proposals that are put forward as a result of broad consultations with experts from industry and academia, and through analysis of the state of the art in cyber-physical systems of systems.
- Emergent Behaviour
- Dynamic Reconfiguration
- Full Life Cycle
- Engineering Framework
- Engineer Support
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
This project has received funding from the European Union’s Seventh Programme for research, technological development and demonstration under grant agreement No 611115.
This is a preview of subscription content, log in via an institution to check access.

Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Böse, C., Hoffmann, C., Kern, C., M., M.: New principles of operating electrical distribution networks with a high degree of decentralized generation. In: 20th International Conference on Electricity Distribution, Prague (2009)
Google Scholar
Broy, M., Cengarle, M.V., Geisberger, E.: Cyber-physical systems: imminent challenges. In: Calinescu, R., Garlan, D. (eds.) Monterey Workshop 2012. LNCS, vol. 7539, pp. 1–28. Springer, Heidelberg (2012)
CPSoS Consortium: Cyber-Physical Systems of Systems – definition and core research and innovation areas (2014). http://www.cpsos.eu/wp-content/uploads/2015/07/CPSoS-Scope-paper-vOct-26-2014.pdf
CPSoS Consortium: Cyber-Physical Systems of Systems: Research and innovation priorities (2015). http://www.cpsos.eu/roadmap
CPSoS Consortium: D2.4 Analysis of the state-of-the-art and future challenges in Cyber-physical Systems of Systems (2015). http://www.cpsos.eu/state-of-the-art
DANSE project: Deliverable D4.4 DANSE methodology V03 (2015)
Jamshidi, M. (ed.): Systems of Systems Engineering: Principles and Applications. CRC Press, Boca Raton (2008)
van de Laar, P., Tretmans, J., Birth, M. (eds.): Situation Awareness with Systems of Systems. Springer, Heidelberg (2013)
Maier, M.W.: Architecting principles for system of systems. Syst. Eng. 1 (4), 267–284 (1998)
Article Google Scholar
Reniers, M.A., Engell, S.: A European roadmap on cyber-physical systems of systems. ERCIM News 2014 (97), 21–22 (2014)
Reniers, M.A., Engell, S., Thompson, H.: Core research and innovation areas in cyber-physical systems of systems. ERCIM News 2015(102) (2015)
Download references
Author information
Authors and affiliations.
Process Dynamics and Operations, TU Dortmund, Dortmund, Germany
S. Engell & R. Paulen
Control Systems Technology, Eindhoven University of Technology (TU/e), Eindhoven, The Netherlands
M. A. Reniers
euTeXoo GmbH, Dortmund, Germany
Haydn Consulting Ltd, Sheffield, UK
H. Thompson
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to M. A. Reniers .
Editor information
Editors and affiliations.
Halmstad University, Halmstad, Sweden
Mohammad Reza Mousavi
University of Gothenburg, Gothenburg, Sweden
Christian Berger
Rights and permissions
Reprints and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper.
Engell, S., Paulen, R., Reniers, M.A., Sonntag, C., Thompson, H. (2015). Core Research and Innovation Areas in Cyber-Physical Systems of Systems. In: Mousavi, M., Berger, C. (eds) Cyber Physical Systems. Design, Modeling, and Evaluation. CyPhy 2015. Lecture Notes in Computer Science(), vol 9361. Springer, Cham. https://doi.org/10.1007/978-3-319-25141-7_4
Download citation
DOI : https://doi.org/10.1007/978-3-319-25141-7_4
Published : 01 November 2015
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-25140-0
Online ISBN : 978-3-319-25141-7
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

Cyber-Physical Systems Research Center
The mission of the Cyber-Physical Systems Research Center (CPSRC) is to promote and facilitate collaborative research activities within UCSC as well as with its academic and industrial partners on key cyber-physical systems topics. CPSRC will foster novel foundational and applied research to support applications such as smart cities and buildings, power grids, agriculture, manufacturing, transportation, and connected health.
What are Cyber-Physical Systems?
Cyber-physical systems (CPSs) are built from, and depend upon, the seamless integration of computational algorithms and physical components. These systems combine digital and analog devices, interfaces, sensors, networks, actuators, and computers with the natural environment and with human-made objects and structures. Just as the Internet has transformed the way people interact with information, cyber-physical systems are transforming the way people interact with the physical world. At the same time, the scale and inherent heterogeneity of these systems pose tremendous engineering challenges. New technological approaches are needed to formalize their design, manage and control them in a scalable, efficient, and secure way, and ensure their usability.
CPSRC Reseach Areas
Autonomous systems.

Human sensing

Interconnected Things

Copyright © 2024,
Designed by Zymphonies
- Publications
- News and Events
- Education and Outreach
Software Engineering Institute
Cite this post.
AMS Citation
Hugues, J., 2023: Assuring Cyber-Physical Systems in an Age of Rising Autonomy. Carnegie Mellon University, Software Engineering Institute's Insights (blog), Accessed April 2, 2024, https://doi.org/10.58012/2zra-yv50.
APA Citation
Hugues, J. (2023, October 16). Assuring Cyber-Physical Systems in an Age of Rising Autonomy. Retrieved April 2, 2024, from https://doi.org/10.58012/2zra-yv50.
Chicago Citation
Hugues, Jerome. "Assuring Cyber-Physical Systems in an Age of Rising Autonomy." Carnegie Mellon University, Software Engineering Institute's Insights (blog) . Carnegie Mellon's Software Engineering Institute, October 16, 2023. https://doi.org/10.58012/2zra-yv50.
IEEE Citation
J. Hugues, "Assuring Cyber-Physical Systems in an Age of Rising Autonomy," Carnegie Mellon University, Software Engineering Institute's Insights (blog) . Carnegie Mellon's Software Engineering Institute, 16-Oct-2023 [Online]. Available: https://doi.org/10.58012/2zra-yv50. [Accessed: 2-Apr-2024].
BibTeX Code
@misc{hugues_2023, author={Hugues, Jerome}, title={Assuring Cyber-Physical Systems in an Age of Rising Autonomy}, month={Oct}, year={2023}, howpublished={Carnegie Mellon University, Software Engineering Institute's Insights (blog)}, url={https://doi.org/10.58012/2zra-yv50}, note={Accessed: 2024-Apr-2} }
Assuring Cyber-Physical Systems in an Age of Rising Autonomy

Jerome Hugues
October 16, 2023, published in.
Cyber-Physical Systems
As developers continue to build greater autonomy into cyber-physical systems (CPSs), such as unmanned aerial vehicles (UAVs) and automobiles, these systems aggregate data from an increasing number of sensors. The systems use this data for control and for otherwise acting in their operational environments. However, more sensors not only create more data and more precise data, but they require a complex architecture to correctly transfer and process multiple data streams. This increase in complexity comes with additional challenges for functional verification and validation (V&V) a greater potential for faults (errors and failures), and a larger attack surface. What’s more, CPSs often cannot distinguish faults from attacks.
To address these challenges, researchers from the SEI and Georgia Tech collaborated on an effort to map the problem space and develop proposals for solving the challenges of increasing sensor data in CPSs. This SEI Blog post provides a summary our work, which comprised research threads addressing four subcomponents of the problem:
- addressing error propagation induced by learning components
- mapping fault and attack scenarios to the corresponding detection mechanisms
- defining a security index of the ability to detect tampering based on the monitoring of specific physical parameters
- determining the impact of clock offset on the precision of reinforcement learning (RL)
Later I will describe these research threads, which are part of a larger body of research we call Safety Analysis and Fault Detection Isolation and Recovery (SAFIR) Synthesis for Time-Sensitive Cyber-Physical Systems. First, let’s take a closer look at the problem space and the challenges we are working to overcome.
More Data, More Problems
CPS developers want more and better data so their systems can make better decisions and more precise evaluations of their operational environments. To achieve those goals, developers add more sensors to their systems and improve the ability of these sensors to gather more data. However, feeding the system more data has several implications: more data means the system must execute more, and more complex , computations. Consequently, these data-enhanced systems need more powerful central processing units (CPUs).
More powerful CPUs introduce various concerns, such as energy management and system reliability. Larger CPUs also raise questions about electrical demand and electromagnetic compatibility (i.e., the ability of the system to withstand electromagnetic disturbances, such as storms or adversarial interference).
The addition of new sensors means systems need to aggregate more data streams. This need drives greater architectural complexity. Moreover, the data streams must be synchronized. For instance, the information obtained from the left side of an autonomous automobile must arrive at the same time as information coming from the right side.
More sensors, more data, and a more complex architecture also raise challenges concerning the safety, security, and performance of these systems, whose interaction with the physical world raises the stakes. CPS developers face heightened pressure to ensure that the data on which their systems rely is accurate, that it arrives on schedule, and that an external actor has not tampered with it.
A Question of Trust
As developers strive to imbue CPSs with greater autonomy, one of the biggest hurdles is gaining the trust of users who depend on these systems to operate safely and securely. For example, consider something as simple as the air pressure sensor in your car’s tires. In the past, we had to check the tires physically, with an air pressure gauge, often miles after we’d been driving on tires dangerously underinflated. The sensors we have today let us know in real time when we need to add air. Over time, we have come to depend on these sensors. However, the moment we get a false alert telling us our front driver’s side tire is underinflated, we lose trust in the ability of the sensors to do their job.
Now, consider a similar system in which the sensors pass their information wirelessly, and a flat-tire warning triggers a safety operation that prevents the car from starting. A malicious actor learns how to generate a false alert from a spot across the parking lot or merely jams your system. Your tires are fine, your car is fine, but your car’s sensors, either detecting a simulated problem or entirely incapacitated, will not let you start the car. Extend this scenario to autonomous systems operating in airplanes, public transportation systems, or large manufacturing facilities, and trust in autonomous CPSs becomes even more critical.
As these examples demonstrate, CPSs are susceptible to both internal faults and external attacks from malicious adversaries. Examples of the latter include the Maroochy Shire incident involving sewage services in Australia in 2000, the Stuxnet attacks targeting power plants in 2010, and the Keylogger virus against a U.S. drone fleet in 2011.
Trust is critical, and it lies at the heart of the work we have been doing with Georgia Tech. It is a multidisciplinary problem. Ultimately, what developers seek to deliver is not just a piece of hardware or software, but a cyber-physical system comprising both hardware and software. Developers need an assurance case , a convincing argument that can be understood by an external party. The assurance case must demonstrate that the way the system was engineered and tested is consistent with the underlying theories used to gather evidence supporting the safety and security of the system. Making such an assurance case possible was a key part of the work described in the following sections.
Addressing Error Propagation Induced by Learning Components
As I noted above, autonomous CPSs are complex platforms that operate in both the physical and cyber domains. They employ a mix of different learning components that inform specific artificial intelligence (AI) functions. Learning components gather data about the environment and the system to help the system make corrections and improve its performance.
To achieve the level of autonomy needed by CPSs when operating in uncertain or adversarial environments, CPSs make use of learning algorithms . These algorithms use data collected by the system—before or during runtime—to enable decision making without a human in the loop. The learning process itself, however, is not without problems, and errors can be introduced by stochastic faults, malicious activity, or human error.
Many groups are working on the problem of verifying learning components. In most cases, they are interested in the correctness of the learning component itself. This line of research aims to produce an integration-ready component that has been verified with some stochastic properties, such as a probabilistic property. However, the work we conducted in this research thread examines the problem of integrating a learning-enabled component within a system.
For example, we ask, How can we define the architecture of the system so that we can fence off any learning-enabled component and assess that the data it is receiving is correct and arriving at the right time? Furthermore, Can we assess that the system outputs can be controlled for some notion of correctness? For instance, Is the acceleration of my car within the speed limit? This kind of fencing is necessary to determine whether we can trust that the system itself is correct (or, at least, not that wrong) compared to the verification of a running component, which today is not possible.
To address these questions, we described the various errors that can appear in CPS components and affect the learning process. We also provided theoretical tools that can be used to verify the presence of such errors. Our aim was to create a framework that operators of CPSs can use to assess their operation when using data-driven learning components. To do so, we adopted a divide-and-conquer approach that used the Architecture Analysis & Design Language (AADL) to create a representation of the system’s components, and their interconnections, to construct a modular environment that allowed for the inclusion of different detection and learning mechanisms. This approach supports a full model-based development, including system specification, analysis, system tuning, integration, and upgrade over the lifecycle.
We used a UAV system to illustrate how errors propagate throughout system components when adversaries attack the learning processes and obtain safety tolerance thresholds. We focused only on specific learning algorithms and detection mechanisms. We then investigated their properties of convergence, as well as the errors that can disrupt those properties.
The results of this investigation provide the starting point for a CPS designer’s guide to utilizing AADL for system-level analysis, tuning, and upgrade in a modular fashion. This guide could comprehensively describe the different errors in the learning processes during system operation. With these descriptions, the designer can automatically verify the proper operation of the CPS by quantifying marginal errors and integrating the system into AADL to evaluate critical properties in all lifecycle phases. To learn more about our approach, I encourage you to read the paper A Modular Approach to Verification of Learning Components in Cyber-Physical Systems .
Mapping Fault and Attack Scenarios to Corresponding Detection Mechanisms
UAVs have become more susceptible to both stochastic faults (stemming from faults occurring on the different components comprising the system) and malicious attacks that compromise either the physical components (sensors, actuators, airframe, etc.) or the software coordinating their operation. Different research communities, using an assortment of tools that are often incompatible with each other, have been investigating the causes and effects of faults that occur in UAVs. In this research thread, we sought to identify the core properties and elements of these approaches to decompose them and thereby enable designers of UAV systems to consider all the different results on faults and the associated detection techniques via an integrated algorithmic approach. In other words, if your system is under attack, how do you select the best mechanism for detecting that attack?
The issue of faults and attacks on UAVs has been widely studied, and a number of taxonomies have been proposed to help engineers design mitigation strategies for various attacks. In our view, however, these taxonomies were insufficient. We proposed a decision process made of two elements: first, a mapping from fault or attack scenarios to abstract error types, and second, a survey of detection mechanisms based on the abstract error types they help detect. Using this approach, designers could use both elements to select a detection mechanism to protect the system.
To classify the attacks on UAVs, we created a list of component compromises, focusing on those that reside at the intersection of the physical and the digital realms. The list is far from comprehensive, but it is adequate for representing the major qualities that describe the effects of those attacks to the system. We contextualized the list in terms of attacks and faults on sensing, actuating, and communication components, and more complex attacks targeting multiple elements to cause system-wide errors:
Using this list of attacks on UAVs and those on UAV platforms, we next identified their properties in terms of the taxonomy criteria introduced by the SEI’s Sam Procter and Peter Feiler in The AADL Error Library: An Operationalized Taxonomy of System Errors . Their taxonomy provides a set of guide words to describe errors based on their class: value, timing, quantity, etc. Table 1 presents a subset of those classes as they apply to UAV faults and attacks.
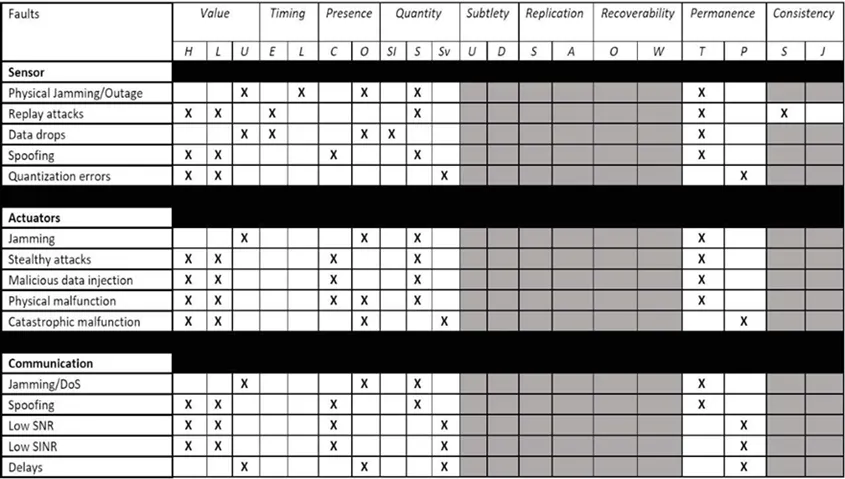
We then created a taxonomy of detection mechanisms that included statistics-based, sample-based, and Bellman-based intrusion detection systems. We related these mechanisms to the attacks and faults taxonomy. Using these examples, we developed a decision-making process and illustrated it with a scenario involving a UAV system. In this scenario, the vehicle undertook a mission in which it faced a high probability of being subject to an acoustic injection attack .
In such an attack, an analyst would refer to the table containing the properties of the attack and choose the abstract attack class of the acoustic injection from the attack taxonomy. Given the nature of the attack, the appropriate choice would be the spoofing sensor attack. Based on the properties given by the attack taxonomy table, the analyst would be able to identify the key characteristics of the attack. Cross-referencing the properties of the attack with the span of detectable characteristics of the different intrusion detection mechanisms will determine the subset of mechanisms that will be successful in environments with those types of attacks.
In this research thread, we created a tool that can help UAV operators select the appropriate detection mechanisms for their system. Future work will focus on implementing the proposed taxonomy on a specific UAV platform, where the exact sources of the attacks and faults can be explicitly identified on a low architectural level. To learn more about our work on this research thread, I encourage you to read the paper Towards Intelligent Security for Unmanned Aerial Vehicles: A Taxonomy of Attacks, Faults, and Detection Mechanisms .
Defining a Security Index of the Ability to Detect Tampering by Monitoring Specific Physical Parameters
CPSs have gradually become large scale and decentralized in recent years, and they rely more and more on communication networks. This high-dimensional and decentralized structure increases the exposure to malicious attacks that can cause faults, failures, and even significant damage. Research efforts have been made on the cost-efficient placement or allocation of actuators and sensors. However, most of these developed methods mainly consider controllability or observability properties and do not take into account the security aspect.
Motivated by this gap, we considered in this research thread the dependence of CPS security on the potentially compromised actuators and sensors, in particular, on deriving a security measure under both actuator and sensor attacks. The topic of CPS security has received increasing attention recently, and different security indices have been developed. The first kind of security measure is based on reachability analysis, which quantifies the size of reachable sets (i.e., the sets of all states reachable by dynamical systems with admissible inputs). To date, however, little work has quantified reachable sets under malicious attacks and used the developed security metrics to guide actuator and sensor selection. The second kind of security index is defined as the minimal number of actuators and/or sensors that attackers need to compromise without being detected.
In this research thread, we developed a generic actuator security index. We also proposed graph-theoretic conditions for computing the index with the help of maximum linking and the generic normal rank of the corresponding structured transfer function matrix. Our contribution here was twofold. We provided conditions for the existence of dynamical and perfect undetectability. In terms of perfect undetectability, we proposed a security index for discrete-time linear-time invariant (LTI) systems under actuator and sensor attacks. Then, we developed a graph-theoretic approach for structured systems that is used to compute the security index by solving a min-cut/max-flow problem. For a detailed presentation of this work, I encourage you to read the paper A Graph-Theoretic Security Index Based on Undetectability for Cyber-Physical Systems .
Determining the Impact of Clock Offset on the Precision of Reinforcement Learning
A major challenge in autonomous CPSs is integrating more sensors and data without reducing the speed of performance. CPSs, such as cars, ships, and planes, all have timing constraints that can be catastrophic if missed. Complicating matters, timing acts in two directions: timing to react to external events and timing to engage with humans to ensure their protection. These conditions raise a number of challenges because timing, accuracy, and precision are characteristics key to ensuring trust in a system.
Methods for the development of safe-by-design systems have been mostly focused on the quality of the information in the network (i.e., in the mitigation of corrupted signals either due to stochastic faults or malicious manipulation by adversaries). However, the decentralized nature of a CPS requires the development of methods that address timing discrepancies among its components. Issues of timing have been addressed in control systems to assess their robustness against such faults, yet the effects of timing issues on learning mechanisms are rarely considered.
Motivated by this fact, our work on this research thread investigated the behavior of a system with reinforcement learning (RL) capabilities under clock offsets. We focused on the derivation of guarantees of convergence for the corresponding learning algorithm, given that the CPS suffers from discrepancies in the control and measurement timestamps. In particular, we investigated the effect of sensor-actuator clock offsets on RL-enabled CPSs. We considered an off-policy RL algorithm that receives data from the system’s sensors and actuators and uses them to approximate a desired optimal control policy.
Nevertheless, owing to timing mismatches, the control-state data obtained from these system components were inconsistent and raised questions about RL robustness. After an extensive analysis, we showed that RL does retain its robustness in an epsilon-delta sense. Given that the sensor–actuator clock offsets are not arbitrarily large and that the behavioral control input satisfies a Lipschitz continuity condition, RL converges epsilon-close to the desired optimal control policy. We conducted a two-link manipulator, which clarified and verified our theoretical findings. For a complete discussion of this work, I encourage you to read the paper Impact of Sensor and Actuator Clock Offsets on Reinforcement Learning .
Building a Chain of Trust in CPS Architecture
In conducting this research, the SEI has made some contributions in the field of CPS architecture. First, we extended AADL to make a formal semantics we can use not only to simulate a model in a very precise way, but also to verify properties on AADL models. That work enables us to reason about the architecture of CPSs. One outcome of this reasoning relevant to assuring autonomous CPSs was the idea of establishing a “fence” around vulnerable components. However, we still needed to perform fault detection to make sure inputs are not incorrect or tampered with or the outputs invalid.
Fault detection is where our collaborators from Georgia Tech made key contributions. They have done great work on statistics-based techniques for detecting faults and developed strategies that use reinforcement learning to build fault detection mechanisms. These mechanisms look for specific patterns that represent either a cyber attack or a fault in the system. They have also addressed the question of recursion in situations in which a learning component learns from another learning component (which may itself be wrong). Kyriakos Vamvoudakis of Georgia Tech’s Daniel Guggenheim School of Aerospace Engineering worked out how to use architecture patterns to address those questions by expanding the fence around those components. This work helped us implement and test fault detection, isolation, and recording mechanism on use-case missions that we implemented on a UAV platform.
We have learned that if you do not have a good CPS architecture—one that is modular, meets desired properties, and isolates fault tolerance—you must have a big fence. You have to do more processing to verify the system and gain trust. On the other hand, if you have an architecture that you can verify is amenable to these fault tolerance techniques, then you can add in the fault isolation tolerances without degrading performance. It is a tradeoff.
One of the things we have been working on in this project is a collection of design patterns that are known in the safety community for detecting and mitigating faults using a simplex architecture to switch from one version of a component to another. We need to define the aforementioned tradeoff for each of those patterns. For instance, patterns will differ in the number of redundant components, and, as we know, more redundancy is more costly because we need more CPU, more wires, more energy. Some patterns will take more time to make a decision or switch from nominal mode to degraded mode . We are evaluating all those patterns, taking into consideration the cost to implement them in terms of resources—mostly hardware resources—and the timing aspect (the time between detecting an event to reconfiguring the system). These practical considerations are what we want to address—not just a formal semantics of AADL, which is nice for computer scientists, but also this tradeoff analysis made possible by providing a careful evaluation of every pattern that has been documented in the literature.
In future work, we want to address these larger questions:
- What can we do with models when we do model-based software engineering?
- How far can we go to build a toolbox so that designing a system can be supported by evidence during every phase?
- You want to build the architecture of a system, but can you make sense of a diagram?
- What can you say about the safety of the timing of the system?
The work is grounded on the vision of rigorous model-based systems engineering progressing from requirements to a model. Developers also need supporting evidence they can use to build a trust package for an external auditor, to demonstrate that the system they designed works. Ultimately, our goal is to build a chain of trust across all of a CPS’s engineering artifacts.
Additional Resources
- Read the paper A Modular Approach to Verification of Learning Components in Cyber-Physical Systems by L. Zhai, A. Kanellopoulos, F. Fotiadis, K.G. Vamvoudakis, and J. Hugues.
- Read the paper Towards Intelligent Security for Unmanned Aerial Vehicles: A Taxonomy of Attacks, Faults, and Detection Mechanisms by L. Zhai, A. Kanellopoulos, F. Fotiadis, K.G. Vamvoudakis, and J. Hugues.
- Read the paper A Graph-Theoretic Security Index Based on Undetectability for Cyber-Physical Systems by L. Zhai, K.G. Vamvoudakis, and J. Hugues.
- Read the paper Impact of Sensor and Actuator Clock Offsets on Reinforcement Learning by F. Fotiadis, A. Kanellopoulos, K.G. Vamvoudakis, and J. Hugues.

Author Page
Digital library publications, send a message, more by the author, don’t wait for roi on model-based analysis for embedded computing resources, november 27, 2023 • by alfred schenker , jerome hugues, from model-based systems and software engineering to moddevops, november 22, 2021 • by jerome hugues , joe yankel, more in cyber-physical systems, systems engineering and software engineering: collaborating for the smart systems of the future, september 20, 2021 • by paul nielsen, safety assurance does not provide software assurance, august 2, 2021 • by mark sherman, accelerating safety assurance, june 7, 2021 • by dionisio de niz, get updates on our latest work..
Sign up to have the latest post sent to your inbox weekly.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection

Smart City Healthcare Cyber Physical System: Characteristics, Technologies and Challenges
Rupali verma.
Computer Science and Engineering, Punjab Engineering College, Chandigarh, India
The recent pandemic has demanded a strong and smart healthcare system which can monitor the patients efficiently and handle the situation that arises from the outbreak of the disease. Smart healthcare cyber physical systems are the future systems as they integrate the physical and cyber world for efficient functioning of medical processes and treatment through external monitoring and control of patients, medical devices and equipment for continuous communication and information exchange of physiological data. Technologies like Internet of Things, Machine learning and Artificial Intelligence have given birth to smart cyber physical systems like Smart Healthcare Systems, Smart Homes, Smart Vehicular Systems and Smart Grid. Such systems are interdisciplinary in nature with multitude of technologies contributing to its effective working. This paper presents a case study on healthcare cyber physical systems presenting its characteristics, role of various technologies in its growth and major challenges in successful implementation of cyber physical medication systems.
Introduction
In the current pandemic, a strong healthcare system is a backbone for any smart city. Effective and efficient monitoring of patients together with regular supply of necessary medicines and treatment with aid of medical devices is possible when a system can meet the demand and supply situation. Such a scenario is possible with a predictive mechanism which forecasts the healthcare situation and works smartly for handling the medical emergency.
Smart Healthcare Cyber Physical Systems (SHCPS) are the future systems capable of supporting the medical fraternity in handling the pandemic situation effectively. Such systems comprise of physical world of patients, medical devices and equipment; externally controlled and monitored medical treatment, connected with cyber world through communication networks for data transfer and information exchange of physiological data which are analysed for feedback and control signals. Such systems improve the quality of medical care by providing efficient and smart services [ 1 ].
The design and development of healthcare cyber physical systems have brought some open issues for discussion like autonomy level, security and reliability which are vital for healthcare cyber physical systems.
Autonomy Level
Cyber physical systems can be classified from low to high level of autonomy based on the tasks performed by the humans in the loop. Technologies like machine learning and artificial intelligence play a major role in shifting the control from human to machine and artificial distributed networks [ 2 ].
Various factors that are crucial in defining the autonomy level in healthcare cyber physical systems (HCPS) are broadly categorized into two domains.
- Equipment based Factors like the medical device type, interaction type and duration with the patient are deciding factors for autonomy level. Medical robots for serving food and medicines to coronavirus patients can work autonomously for assisting the Medicare systems. The team of researchers from Hong Kong have created a humanoid robot called ‘Grace’ for interacting with isolated coronavirus patients and provides services like temperature recording and responsiveness through the thermal camera fitted in the chest. The robot will also socially interact with the coronavirus patients in order to prevent the stress arising from isolation [ 3 ].
- Patient related Patient related factors include the disease type and patient risk level. Communicable diseases like coronavirus necessitate high level of autonomous Medicare cyber physical systems whereas high patient risk level require continuous medical expert support along with the autonomous Medicare systems.
Security Mechanisms
A number of technologies play a vital role in the cyber physical system which can be classified into distinctive areas ranging from data collection with sensor technology and IOT; handling big data and its storage with Cloud computing; data analytics and decision making using artificial intelligence; control and coordination signals to smart machines and actuators thus leading to the commencement of new era termed by Industry 4.0 [ 4 ] and specifically Healthcare 4 for medical applications. A comprehensive security mechanism for authenticated, confidential and secure communication between cyber and physical world forms an integral part of framework during the design and development of cyber physical systems. The criticality of healthcare applications with high levels of autonomy demands a preventive approach for defence against cyber-attacks [ 5 ] and thus the Healthcare Cyber physical systems must incorporate the following in their security mechanism:
- Identification of cyber-attacks on sensors.
- Lightweight cryptography for transmitting physiological data.
- Encryption mechanisms and Blockchain technology for secure storage on cloud-based systems.
- Encrypted feedback signals to actuators.
The data transmitted from patients to medical expert is vulnerable to attacks and hence requires encryption techniques at the client end. Many cryptographic techniques exist in literature, the broad classification is symmetric cryptography and asymmetric cryptography. Biological cryptographic approach based on amino acid codes [ 6 ] is used for transmitting the data from patients to healthcare experts in telemonitoring healthcare system.
Reliability
Reliability is an important metric for cyber physical systems and of utmost significance to healthcare industry. Figure 1 shows the reliability of healthcare cyber physical systems (HCPS) which is dependent on hardware units like health sensors and actuators, software reliability on software systems computing patient’s health status, and network reliability determined by communication networks for transfer of patient data.

Reliability of HCPS
The commencement of cyber physical systems requires optimization of resources and self-adaptive behaviour for efficient, reliable and improved services [ 7 ]. The autonomous systems must be able to identify the failure of different components in the closed loop system and take corrective measures in terms of handling the tasks. Self-adaptive components of cyber physical systems learn from the past data and behave in the current scenario. Smart machines like healthcare robots can self-organize to dynamic environment to meet the challenge of service quality.
This paper highlights the following:
- (i) Characteristics of healthcare cyber physical systems
- (ii) Amalgamation of technologies that have contributed to the growth and implementation of healthcare cyber physical systems.
- (iii) Real time challenges which prompt the researchers, healthcare and manufacturing sector to retrospect and consider during design and effective execution of healthcare cyber physical systems.
Cyber Physical Systems
The need for continuous communication, control and collaboration for efficient and effective systems for quality of service has brought a new era called Industry 4.0 that introduces cyber physical systems. The term cyber physical system was first coined by Helen Gill at NSF in US in the year 2006. A cyber physical system integrates cyber and physical world with sensors, which act like data collectors to gather information like temperature, pressure or speed/activity time for transmission to cyber world for storage in servers. This data is further processed and analysed to act as stimuli for control and coordination signals to actuators thus forming a closed loop system as shown in Fig. 2 .

Cyber physical world with closed loop
The systematic design and modelling of cyber physical systems play a key role in defining the architecture of the system with various software and hardware components, the functional roles of each component; and the communication and control mechanism between cyber and physical space. Thereafter, the simulation of the design with well tested and validation strategies are applied for final adoption of the model in the real time setup [ 8 ]. Unlike the conventional approach to design and deployment, the authors in [ 9 ] suggest a shift from design to runtime and implementation phase for critical decisions, which depend on real time inputs and environment. Table Table1 1 presents the various CPS simulation software and their characteristics, which can be used to test various concepts of modularity, scalability and complexity of cyber physical systems in the application domain.
Simulators for modelling cyber physical systems
Some systems have a symbiotic relationship between physical world and virtual world giving rise to a new term “symbiotic cyber physical systems” [ 14 ]. The term symbiotic relationship has arisen from biology where two organisms benefit from each other and such a relationship is symbiotic in nature. Smart Grid is a perfect example of symbiotic cyber physical system where technology drives to generate energy smartly and the energy is the source of power for the technology elements in the cyber physical system. The smart healthcare cyber physical systems are symbiotic to various autonomous systems as shown in Fig. 3 . Smart grid, smart home, smart vehicular systems, smart hospitals and smart manufacturing units provide services for a smart city healthcare system. In turn, the smart city healthcare system provides healthcare to its inhabitants. These inhabitants or humans are working in various organizations and manufacturing units, thus providing their service or role in various autonomous units. To define the precise role of humans in the autonomous CPS systems is a big and challenging task. An effective approach in this direction is to identify the control strategies and interactions of humans in the closed loop CPS at early stages of software development and thereafter, validate through fast prototyping techniques [ 15 ].

Smart city healthcare cyber physical system
The cyber physical systems differ in terms of their characteristics like autonomy level which determine the tasks controlled and operated by humans, scale which depends on the number of devices connected and risk management which depends on the critical environment of the system. Table Table2 2 presents the various applications areas, characteristic features, technologies and services provided by the CPS in different domains in face of the various security risks and challenges.
Cyber physical systems
Characteristics of Smart City Healthcare Cyber Physical System
Healthcare Cyber Physical Systems can be divided into various levels:
- Unit level HCPS
- Integration level HCPS
- System level HCPS
- Acceptance level HCPS
- Evolutionary level HCPS
Unit level HCPS are basic or the first level of healthcare cyber physical systems which provide monitoring and control of patients in intensive care units or at the hospital level. At this level it continuously monitors the physiological parameters like temperature, pressure, heart rate etc. of the patients and feed the data to the intelligent systems which analyse and control the health actuators connected to the patient. Also, the health staff is in the HCPS loop for support and information to health experts for immediate healthcare aid to the patients.
Integration level HCPS are the second stage of HCPS where the hospitals integrate with smart homes to provide remote monitoring and remote healthcare service to the patients. In case of transfer of high-risk patients in ambulances to hospitals, the latter can integrate with smart ambulances to continuously monitor the patient’s health status and make necessary emergency services in hospital like availability of bed, ventilator support etc.
System level HCPS are the third stage of HCPS where different autonomous systems support the HCPS to form a Smart City Healthcare Cyber Physical System. The smart grid, the powerhouse of energy and backbone for various cyber physical system together with smart home, smart ambulances, smart hospital manufacturing units and smart hospitals form a healthcare ecosystem providing quality of healthcare service to the patients.
Acceptance level HCPS is the level of HCPS where the researchers, technologists, engineers, health experts, academicians coordinate to make the healthcare system effective with policies and standards oriented towards successful implementation of the healthcare ecosystem.
Evolutionary level HCPS is the ideal future HCPS systems which have properties of self-adaptability and self-management. Self-adaptive components of cyber physical systems learn from the past data and behave in the current scenario. Hence, the role of evolutionary behaviour is critical and of significance for the dynamic environment of cyber physical systems.
The Cyber Physical System has physical components and processes which can be represented by a state diagram and different states : healthy, unhealthy, critical and non-working state as shown in Fig. 4 . The overall health of the CPS depends on the working conditions of different components in the closed loop system [ 25 ].

State diagram of cyber physical system
The nature of devices in CPS is heterogeneous which range from sensors, actuators to physical machines controlled by external inputs like mobile devices at dew layer and systems at cyber level. The input and output of data of various devices differ in the data formats, which may be structured/unstructured in nature, which necessitate the conversion of formats through interfaces [ 16 ]. The healthcare cyber physical systems are application domain where time is a critical factor in determining the performance and reliability of the system. A delay in seconds or microseconds in medication to patients can reduce the effectiveness and dependability of the system.
Cyber physical systems are monitored and controlled continuously for effective operation and hence this gives rise to a new term called health-monitoring system (HMS) for CPS [ 25 ]. HMS can perform dual function: to check the status of each physical component in CPS and to apply pre-emptive approach in determining probabilistic health of CPS. Study of behavioural models of physical components is a passive monitoring approach where as a stimulus-based response is an active strategy to determine for anomaly detection [ 25 ].
Based on the above characteristics, the unit and the integration level of HCPS are analysed in terms of characteristics of CPS in Table Table3 3 .
Characteristics of unit and integrated level of HCPS
Section 4 , presents the role of various technologies in seamless monitoring the time critical domain with heterogeneous devices in cyber physical systems where each state is defined by a set of variables. The technologies play a crucial role in defining the health of the system.
Technologies in Healthcare Cyber Physical Systems
The recent pandemic has put an unprecedented pressure on the healthcare system of any city in the world and long working hours of medical experts and health workers. Hence, the future healthcare systems demand Smart City Healthcare Cyber Physical Systems where technology plays a significant role in its successful implementation. Cyber Physical Systems is an application domain where there is integration of plethora of technologies for smart and efficient working of interconnected devices. Internet is the backbone for communication in cyber physical systems and is primarily the most crucial technology and enabler for other technologies like IOT, cloud computing and blockchain [ 4 ]. This section presents the role of various technologies like digital twin, IOT, big data, cloud computing, blockchain, artificial intelligence, machine learning and robotics in the field of healthcare cyber physical systems as shown in Fig. 5 .

Technologies in healthcare cyber physical systems
Digital Twin
Digital twin as shown in Fig. Fig.6 6 is a virtual twin for a physical object or a process. In smart healthcare systems, the digital twin creates virtual assets in cyberspace so that the digital information of resources can be used for planning, control and coordination [ 27 ]. Digital twin for SHCPS is basically a simulation model for medical devices and equipment, and for behavioural analysis of patient treatment process to assist the health care experts to study, analyse and predict the health status of patients.

Digital twin-virtualization in cyber space
The digital twin maintains a resource graph for various medical equipment which is stored as a three-tuple vector represented by {resource id, allocation status, patient id}. The allocation status be busy or idle and expected reallocation may depend upon the patient health. The patient treatment process can be represented by a graph where the nodes represent the health status at different intervals of time and the edges represent the transition based on change in physiological parameters. These graphs can be used for machine learning for computation and classification of patient’s health status.
Internet of Things (IOT)
The Internet of Things brought a new era of machine-to-machine communication [ 4 ] which can be through wireless networks, Bluetooth and other technologies like Near Field Communication, radio communication etc. The IOT enables in integration level smart healthcare cyber physical systems where the sensor networks generate high volumes of data which are then transmitted to remote servers for analysis and control operations. Since some devices in Medical IOT are resource constrained in terms of processing power and memory therefore lightweight authentication and lightweight cryptographic schemes are essential for integrity and confidentiality of data and information exchange. The Medical IOT has helped in recent pandemic in remote monitoring of patients [ 28 , 29 ] through smart wearables like smart watch and smart band to collect patients heart rate and blood pressure; and smart thermometers to measure body temperature. These devices are connected to smart phones, which ultimately send the data to the cloud servers for health analytics.
Big Data Analytics
In healthcare cyber physical systems with IOT of Medical devices, machine to machine communication among heterogeneous nodes and sensors capturing data continuously lead to large data sets which may be structured, unstructured or semi structured and hence require storage, processing and analysis for medical advice. The big challenge is to deal with unstructured data, complexity and veracity issues. The new computing paradigms with high processing power and big data technologies enable to extract hidden patterns and relationships in large amount of data which are gathered from various sources in healthcare cyber physical systems.
The pandemic has led to regular check-up of physiological parameters like temperature, pressure, heart rate so that the symptoms could be easily predicted. The different type of data generated related to coronavirus are the human physiological parameters like temperature, pressure, heart rate; the hospital data which include current corona patient intake, patient health status, facilities available like number of beds, ventilators; the city data like the number of residents currently corona infected, number of patients healthy, number of corona deaths, number of residents vaccinated. The researchers and analysts are interested in survey of spread and predictive analysis for future effect. High end computing devices and deep learning models enable to work on large datasets and identify these hidden patterns. These hidden patterns can be unlocked using statistical, machine learning and deep learning techniques.
The complexity and uncertainty of real world data generated in real time systems like healthcare CPS can also be dealt by methodology based on computational intelligence which includes fuzzy logic approach based on approximation techniques and fuzzy rules for decision making and inferences; evolutionary algorithms like genetic programming and swarm intelligence for natural selection; and artificial neural networks which have many hidden layers with neurons, mimic human brain and trained on large data sets to set the learning parameters for pattern recognition, prediction and classification of data sets [ 30 ].
Cloud Computing
Healthcare data silos are medical information of patients at discrete locations which may be redundant or non-coherent based on data management strategies. Cloud computing is a computing paradigm that provides infrastructure, resources and services to end users on pay per use basis where the cloud servers provide data storage and computing power to users. In healthcare cyber physical systems, the Electronic Health Records can be digitally stored in encrypted format at the cloud server so that it can be shared and accessed by the different entities like patients, hospital management, insurance companies and banks [ 31 ]. The challenging issue is to ensure safety of patient records which depends on the security framework adopted for safeguarding the key generation centre that maintains private keys of all authentic users [ 31 ].
Besides the storage of encrypted data in cloud servers, industry 4.0 standards have defined new service models for cloud manufacturing like control as a service, machinery as a service and industry automation as a service [ 4 ]. These new cloud-based models can be applied for hard real tasks with fog computing resulting in service closed to end users with efficient real time communication in information transfer and control between the healthcare level and controllers.
Dew Computing
The cloud architecture provides services which can be enhanced by edge/fog computing paradigm, a distributed service architecture which improves the efficiency of cyber physical systems by reducing the transmission delay of services provided by cloud model. Dew computing further reduces the delay and provides energy efficiency by introducing another level with smart interfaces or smart devices closer in network to IOT devices as compared to edge devices. These smart systems provide processing capabilities, work on data from physical components, control the actuators and have additional technology benefits of scalability and resilience [ 32 ]. The Dew computing layer is very useful for providing services in healthcare domain [ 33 ] where the patients can be monitored more effectively by providing processing and analytic services close to monitored area. A dew computing architecture with IOT devices; sensors and actuators in first layer; smart devices like smart phones and tablets in second layer called the dew computing layer; storage systems and network equipment in edge device layer; cloudlets and servers at fourth layer called edge server layer which represents the edge or fog computing distributed service and finally the fifth layer with cloud servers providing various infrastructure and software based services[ 32 ]; can be very time efficient for healthcare domains. The lightweight applications on tablets and smart phones in Dew computing paradigms can share patient information and are interoperable which helps in collaboration with other systems to be a part of healthcare cyber physical system of systems.
Blockchain technology provides a decentralised and distributed database for secure and authentic access to electronic health records maintained by cloud servers [ 31 ]. It provides a decentralised platform for maintaining untampered records of events [ 4 ] for various medical transactions that may be at device level or vaccines; and events at patient level. The blockchain is defined by a chain of blocks, each with a number of transactions or communications which are hashed and structured by a Merkle tree. Each block is identified by a hash value and contains the hash of previous block with the exception that the first block is called genesis and has no parent hash value stored in it. Such a link with parent block gives an immutable structure which cannot be tampered.
Such immutable structures can store the transactions of different medical devices and vaccines; and information related to patients. Hence, this technology can have different blockchains for healthcare: Blockchain of medical devices, Blockchain of coronavirus infected patients, Blockchain of vaccines in a hospital. The IBM blockchain [ 34 ] helps in transparent distribution of coronavirus vaccine, by maintaining the transactions safe and traceable. QuillTrace [ 35 ] is a blockchain based technology that helps in tracking medicines in supply chain and identification of fake medicines with help of QR code on medicines.
Artificial Intelligence and Machine Learning
AI and machine learning can be applied at various aspects of healthcare which include medicines, medical equipment, patient and disease. The researchers, academicians and healthcare experts are working together to extract useful information, the hidden patterns from large databases of patient data. These large databases are also used to train machine learning models which are used to classify the patients and help in automatic disease detection and thus support medical experts. The recent pandemic has seen the urgent need of study of drug discovery for coronavirus, the high demand of ventilators which have become the life saving device for the high-risk coronavirus patients, the study of patients with high risk levels and the effect of disease on other organs of the body.
Based on the risk level, the coronavirus patients can be divided into low risk level and highrisk level. At the first stage the patients can be isolated in their homes and the various physiological parameters like their temperature, pressure and heart rate at discrete time points can be sent to medical experts for predicting symptoms based on machine learning techniques and healthcare can be provided through telemonitoring. The next stage demands hospitalization of patients with continuous medical support, care and monitoring. AI and machine learning algorithms have been used to predict the mortality rate of high-risk patients [ 36 ] by training the model with balanced dataset; and features are chosen based on wrapper and filter-based approaches. These features include symptoms, pre-health status and demographic factors which significantly contribute to the disease status of the patient.
Robots are autonomous machines which are programmed to perform a particular task with precision and accuracy. They are cognitive models based on artificial intelligence with capabilities to continuously capture the environment data with sensors to work in complex environments and perform pre-defined actions with high frequency. Robots have a vast role to play in cyber physical systems like medical robots to assist in surgery and patient care, industrial robots to perform manufacturing tasks and surveillance robots for security and safety.
The recent pandemic has seen rising number of coronavirus cases which resulted in patient overload in hospitals. The healthcare robots have found a key role in patient care providing services from patient testing to patient service by delivering regular medicines, food etc. Robots like Moxi perform various services like delivering PPE kits, covid 19 tests and provides pick/drop service to patients [ 37 ]. The robot Mitra assists health staff by taking temperature readings of patients and helps patients in connecting with their relatives through video conferencing [ 38 ].
Industrial robots help in manufacturing products like covid testing kits and ventilators with high frequency and precision; and short development life cycle. Industrial cyber physical working environments with human robot collaboration aim for agile product development and demand for context awareness in robots which identify human working zones and adjust their area and speed [ 39 ]. Unlike machines, human behaviour is flexible and requires constant reminders in the form of audio-visual messages for maintaining a safe distance during collaborative work with high-speed autonomous machines. Therefore, high precision algorithms are required for depth estimation to send control signals to robots and other autonomous machines to avoid accidents due to erroneous computations and movements.
Security robots can help in detecting adherence to covid protocols like wearing of masks, social distancing etc. They capture images, identify objects, generates reports and communicate using multimodal technologies through audio, video and textual data.
Figure Figure7 7 presents the various technologies at various domains and the benefits which helps in automation, resource control and intelligence-based decision making based on big data analytics. Though, various technologies have contributed to the growth of modern cyber physical systems which have led to an evolutionary process resulting in smart, self-aware and self-healing systems but still the present day cyber physical systems face many challenges which have an adverse impact on the health of cyber physical systems affecting its devices, their communication and collaboration resulting in human intervention for reinstating the working state of system.

Technological benefits for cyber physical systems
Section 5 , presents some challenges for a smart city healthcare cyber physical system like energy flow in CPS, integration of diverse devices/levels, the delay or latency which can affect the closed loop system and the cyber-attacks which have surfaced for information theft and disruption of devices.
Challenges in Smart City Healthcare Cyber Physical System
There are numerous challenges for a successful implementation of HCPS like energy flow, integration of heterogeneous devices and at various levels of HCPS, minimum acceptable delay for time critical operations and security risks in healthcare cyber physical systems as shown in Fig. 8 .

Challenges in HCPS

Energy Flow in Cyber Physical Components
The autonomy of cyber physical systems and their applications in critical domain like healthcare demand a continuous flow of energy either from high-powered batteries or from direct power supply. During the system design and modelling of HCPS it becomes imperative to estimate the various components and their energy requirement so that a continuous flow of energy is maintained for smooth functioning of the healthcare cyber physical system. Resource constraint devices with limited battery power is a challenging issue and various energy saving mechanisms exist to manage energy efficiently like the smart sensors [ 20 ] within these devices adapt to the need of environment and change the working mode accordingly but gives a ripple effect on energy quality trade-off. The successful implementation of CPS and its integration to form a smart city healthcare CPS depends primarily on the Smart Grid which is a backbone of energy to the cyber physical systems. The smart home, smart hospitals and smart manufacturing units can aid the Smart grid by installing solar panels and contribute as energy production units in order to meet the energy requirements which have increased exponentially in cyber physical systems.
Integration of Heterogeneous Devices/Levels of HCPS
The smart city healthcare ecosystem requires the integration of cyber physical systems which depends on third party service providers for communication service and third-party cloud service providers for safe data storage which can be accessed by medical experts, insurance companies, patients and researchers. At the internal level, each cyber physical system has heterogeneous nature of devices with different data formats which requires integration and encapsulation of the devices for efficient and effective environment. The major challenge in a heterogeneous environment will be the need of interfaces to communicating devices with different technology level in terms of hardware and software resources. The integration and higher levels of HCPS require data sharing and collaborative functionality which demands system level planning, design and prototype testing [ 26 ].
Delay/Latency
Low latency is a critical requirement for real time applications like healthcare. The delays above a threshold value in transmission of patient data are unacceptable and lead to disrupting the telemonitoring cycle of cyber physical systems affecting timely medication and care to the patients. Also, it is significant in real time applications like healthcare that the fault latency which is a measure of time delay between the occurrence of fault and its recognition must be a small value so that its timely management could enhance the reliability of the system [ 23 ].
Security of healthcare cyber physical systems is a critical issue and needs to be addressed in view of the different types of attacks like denial of service, replay, false data injection and deception attacks. The authors in [ 40 ] have proposed a tree-based attack model for cyber physical systems where the branches categorise the attacks in various sub domains like fault signal injection and hardware tampering of sensors, packet replay attack and information theft in communication channels of closed loop with sensors, controllers and actuators; equipment failure and software malfunctioning in computing resources. Critical infrastructures like smart healthcare systems require cyber security systems, which monitor continuously for identifying fault injections in system that lead to incorrect working of equipment and faulty readings [ 24 ].
Smart healthcare cyber physical systems are future digital systems which must be forensic ready to deal and counter with cyber security attacks [ 19 , 41 ]. Artificial intelligence or machine intelligence have wide role in autonomous systems performing tasks like abnormal behaviour detection due to faults or cyber-attacks [ 42 ]. Malware detection is an important task for smooth and efficient working of cyber physical systems. Many machine learning approaches based on system calls, operation codes and energy consumption patterns are used to identify the malwares [ 43 ].
Along with challenges related to digital world, the healthcare systems are facing the major physical challenge of smart waste management. The hospitals are generating the waste at an alarming rate which needs effective management strategies including its collection at generation sites, transportation and handling techniques for maintaining the health of city environment. The recent pandemic has seen the rise of PPE kits and use of disposable masks which needs smart waste management plan.
The Healthcare Cyber Physical systems are currently working at unit or integration level, with continuous growth of technologies they will evolve into higher level CPS. Smart manufacturing systems that produce vaccines or medical equipment are advanced level CPS with subsystems having characteristics of self-awareness and self-management, and can set to self-configuration mode to optimize the various real time production processes [ 20 ].
The pandemic has taught us that healthcare systems are the lungs of every society and a smart healthcare cyber physical system provides an ecosystem which merges the two wheels cyber world and the physical world connected by a closed loop and steered by various technologies like digital twin, IOT, cloud computing, artificial intelligence, machine learning and big data analytics which play a major role in its effective functioning. The working and implementation in physical world controlled by cyber space face many challenges like heterogeneous nature of physical components, incompatible data formats exchanged between components, resource constraint devices and vulnerability of devices to attacks. Apart from the digital challenges, the physical challenge of waste management still holds its critical place. Though, the birth of new technologies contributes to smart interconnected systems but the challenges of physical and virtual world must be addressed for its growth, efficiency and effectiveness.
received B. Tech in Computer Science from Panjab Technical University, India in 2001; ME in Computer Science (IT) from Panjab University in 2005, and PhD in Computer Science from Panjab University in 2016. She is currently working as Assistant Professor in Computer Science and Engineering, Punjab Engineering College, Chandigarh, India. Her research interests are Cryptography, Algorithms and Data Analytics.

Authors' Contributions
Conceptualization, organization, writing, analysis and editing.
Declarations
The author declares that they have no conflict of interest.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Research on Security Estimation and Control of Cyber-Physical System
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Cyber-Physical Systems
The term Cyber-Physical System (CPS) is used to describe dynamic systems which combine components characterized by a physical state (e.g., the location, power level, and temperature of a mobile robot) with components (mostly digital devices empowered by software) characterized by an operational state or mode (e.g., on/off, transmitting/receiving). From a modeling point of view, physical states evolve according to time-driven dynamics commonly described through differential (or difference) equations, while operational states have event-driven dynamics where events may be controllable (e.g., a turn on command) or uncontrollable (e.g., a random failure). Imparting intelligence to a CPS implies the presence of multiple additional events that correspond to actions such as “start moving” for a mobile robot or “change sampling rate” for a sensor. These physical and operational states generally interact to give rise to a hybrid dynamic system. For example, a sensor with autonomous control capabilities may switch to a data transmitting mode as a result of a particular physical state change (e.g., its residual energy drops below a certain threshold). Examples of CPS include smart grid, autonomous vehicle systems, medical monitoring, industrial control systems, and robotics systems, and among others.
Collaborative Research: CPS: Medium: An Online Learning Framework for Socially Emerging Mixed Mobility
Emerging mobility systems, e.g., connected and automated vehicles and shared mobility, provide the most intriguing opportunity for enabling users to better monitor transportation network conditions and make better decisions for improving safety and transportation efficiency. However, different levels of vehicle automation in the transportation network can significantly alter transportation efficiency metrics (travel times, energy, environmental […]
CNS Core: Small: Collaborative Research: HEECMA: A Hybrid Elastic Edge-Cloud Application Management Architecture
Application software is becoming increasingly abundant in functionality and increasingly demanding of resources, e.g., memory and compute power. This project examines how application software, e.g., a Virtual Reality (VR) based drone control application, can be partitioned and deployed over different parts of a distributed computing infrastructure, i.e., resources are managed by a hybrid of service […]
Decentralized Optimal Control of Cooperating Networked Multi-agent Systems
Multi-agent systems encompass a broad spectrum of applications, ranging from connected autonomous vehicles and the emerging internet of cars, where the spatial domain may be hundreds of miles with time horizons over hours of days, to micro-air vehicles which operate over meter length and minute time scales, and down to nano-manipulation with nanometer spatial microsecond […]
CPS: Breakthrough: Collaborative Research: A Framework for Extensibility-Driven Design of Cyber-Physical Systems
A longstanding problem in the design of cyber-physical systems is the inability and ineffectiveness in coping with software and hardware evolutions over the lifetime of a design or across multiple versions in the same product family. The objective of this project is to develop a systematic framework for designing extensible cyber-physical systems that can enable […]
Workshop on Smart Cities, Arlington, Virginia, December 3-4, 2015
This Workshop will bring together researchers and technical leaders from academia, industry, and municipal government in order to set a short and long-term research agenda for Smart Cities aiming to integrate the three broad fields of Engineering, Computer Science, and Social Science. The Workshop topics cover a variety of fields and specialized disciplines including: transportation, […]
CPS: FRONTIER: COLLABORATIVE RESEARCH: BIOCPS FOR ENGINEERING LIVING CELLS
Recent developments in nanotechnology and synthetic biology have enabled a new direction in biological engineering: synthesis of collective behaviors and spatio-temporal patterns in multi-cellular bacterial and mammalian systems. This will have a dramatic impact in such areas as amorphous computing, nano-fabrication, and, in particular, tissue engineering, where patterns can be used to differentiate stem cells […]
PFI:BIC A Smart-city Cloud-based Open Platform and Ecosystem (SCOPE)
This NSF Partnerships for Innovation: Building Innovation Capacity (PFI:BIC) project from Boston University will research, prototype, and evaluate novel “smart-city” services for the city of Boston and for the Commonwealth of Massachusetts. The centerpiece of the project is a Smart-city Cloud-based Open Platform and Ecosystem (SCOPE), which creates a multisided marketplace for smart-city services based […]
Sensor Research Wins $1M NSF Award
Enhancing the functionality of cyber-physical systems—those that integrate physical processes with networked computing—could significantly improve our quality of life, from reducing car collisions to upgrading robotic surgeries to mounting more effective search and rescue missions. Recognizing Boston University as a key contributor to this effort, the National Science Foundation has awarded Professors Venkatesh Saligrama (ECE, SE) […]
CPS: Synergy: Collaborative Research: A Cyber-Physical Infrastructure for the “Smart City”
The project aims at making cities “smarter” by engineering processes such as traffic control, efficient parking services, and new urban activities such as recharging electric vehicles. To that end, the research will study the components needed to establish a Cyber-Physical Infrastructure for urban environments and address fundamental problems that involve data collection, resource allocation, real-time […]
Topics in Cyber-Physical Systems
Columbia university elen e6908 spring 2019.
- Reading List
Instructor: Prof. Xiaofan Jiang Time: Thursdays 1:50PM-3:40PM Location: 1127 Mudd Class ID: ELEN 6908 E sec. 001
Description:
As computers and communication bandwidth become ever-faster and ever-cheaper, computing and communication capabilities will be embedded in all types of objects and structures in the physical environment. Applications with enormous societal impact and economic benefit will be created by harnessing these capabilities in time and across space. We refer to systems that bridge the cyber-world of computing and communications with the physical world as cyber-physical systems (CPS). This topic course covers important topics and papers from the research literature on CPS. Several application domains are emphasized: smart cities and the built environment, fitness and health care, air quality and environment, and industrial CPS. Several key cross-cutting topics, independent of the application domain, are also covered, including time-series data analytics, energy and power, scalability, time synchronization, and wireless networking.
Objectives:
One objective is to learn the current state of art in Cyber-Physical Systems research, including its various application domains. A second objective is to learn details regarding several necessary principles required for future CPS. A third objective is improving critical reading, presentation, and research skills. Finally, this course aims to foster new ideas and help students develop new projects that lead to publications in CPS related conferences and startups.
Prerequisites:
PhD and MS students with interest in systems research and data science.
Performance assessment:
Performance is assessed based on one or more oral presentations and project ideas development. Students’ attendance to most sessions as well as active participation in the discussions is expected and will be considered for the final grading.
Acknowledgement:
Special thanks to Prof. John A. Stankovic, Prof. Tamer Nadeem, and Prof. Wen Hu for course materials
Course Website:
https://edblogs.columbia.edu/elence6908-001-2019-1/
Prof. Xiaofan (Fred) Jiang < [email protected] >
Participants
Recent Posts
- Hello world!
Recent Comments
- January 2019
- Uncategorized
Subscribe to Email Updates on New Posts
Submit your preferred email in the field below.
Please, insert a valid email.
Thank you, your email will be added to the mailing list once you click on the link in the confirmation email.
Spam protection has stopped this request. Please contact site owner for help.
This form is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
© 2024 Topics in Cyber-Physical Systems
Theme by Anders Noren — Up ↑
This website uses cookies to identify users, improve the user experience and requires cookies to work. By continuing to use this website, you consent to Columbia University's use of cookies and similar technologies, in accordance with the Columbia University Website Cookie Notice .
- Frontiers in Physics
- Social Physics
- Research Topics
Security, Governance, and Challenges of the New Generation of Cyber-Physical-Social Systems
Total Downloads
Total Views and Downloads
About this Research Topic
In recent years, the transformation of devices and systems into intelligent, interconnected entities has given rise to concepts widely recognized as the Internet of Things (IoT) and cyber-physical systems (CPSs). The integration of social networks with CPSs leads to an innovative paradigm known as ...
Important Note : All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements. Frontiers reserves the right to guide an out-of-scope manuscript to a more suitable section or journal at any stage of peer review.
Topic Editors
Topic coordinators, recent articles, submission deadlines, participating journals.
Manuscripts can be submitted to this Research Topic via the following journals:
total views
- Demographics
No records found
total views article views downloads topic views
Top countries
Top referring sites, about frontiers research topics.
With their unique mixes of varied contributions from Original Research to Review Articles, Research Topics unify the most influential researchers, the latest key findings and historical advances in a hot research area! Find out more on how to host your own Frontiers Research Topic or contribute to one as an author.
- News & Media
- Chemical Biology
- Computational Biology
- Ecosystem Science
- Cancer Biology
- Exposure Science & Pathogen Biology
- Metabolic Inflammatory Diseases
- Advanced Metabolomics
- Mass Spectrometry-Based Measurement Technologies
- Spatial and Single-Cell Proteomics
- Structural Biology
- Biofuels & Bioproducts
- Human Microbiome
- Soil Microbiome
- Synthetic Biology
- Computational Chemistry
- Chemical Separations
- Chemical Physics
- Atmospheric Aerosols
- Human-Earth System Interactions
- Modeling Earth Systems
- Coastal Science
- Plant Science
- Subsurface Science
- Terrestrial Aquatics
- Materials in Extreme Environments
- Precision Materials by Design
- Science of Interfaces
- Friction Stir Welding & Processing
- Dark Matter
- Flavor Physics
- Fusion Energy Science
- Neutrino Physics
- Quantum Information Sciences
- Emergency Response
- AGM Program
- Tools and Capabilities
- Grid Architecture
- Grid Cybersecurity
- Grid Energy Storage
- Earth System Modeling
- Energy System Modeling
- Transmission
- Distribution
- Appliance and Equipment Standards
- Building Energy Codes
- Advanced Building Controls
- Advanced Lighting
- Building-Grid Integration
- Building and Grid Modeling
- Commercial Buildings
- Federal Performance Optimization
- Resilience and Security
- Grid Resilience and Decarbonization
- Building America Solution Center
- Energy Efficient Technology Integration
- Home Energy Score
- Electrochemical Energy Storage
- Flexible Loads and Generation
- Grid Integration, Controls, and Architecture
- Regulation, Policy, and Valuation
- Science Supporting Energy Storage
- Chemical Energy Storage
- Waste Processing
- Radiation Measurement
- Environmental Remediation
- Subsurface Energy Systems
- Carbon Capture
- Carbon Storage
- Carbon Utilization
- Advanced Hydrocarbon Conversion
- Fuel Cycle Research
- Advanced Reactors
- Reactor Operations
- Reactor Licensing
- Solar Energy
- Wind Resource Characterization
- Wildlife and Wind
- Community Values and Ocean Co-Use
- Wind Systems Integration
- Wind Data Management
- Distributed Wind
- Energy Equity & Health
- Environmental Monitoring for Marine Energy
- Marine Biofouling and Corrosion
- Marine Energy Resource Characterization
- Testing for Marine Energy
- The Blue Economy
- Environmental Performance of Hydropower
- Hydropower Cybersecurity and Digitalization
- Hydropower and the Electric Grid
- Materials Science for Hydropower
- Pumped Storage Hydropower
- Water + Hydropower Planning
- Grid Integration of Renewable Energy
- Geothermal Energy
- Algal Biofuels
- Aviation Biofuels
- Waste-to-Energy and Products
- Hydrogen & Fuel Cells
- Emission Control
- Energy-Efficient Mobility Systems
- Lightweight Materials
- Vehicle Electrification
- Vehicle Grid Integration
- Contraband Detection
- Pathogen Science & Detection
- Explosives Detection
- Threat-Agnostic Biodefense
- Discovery and Insight
- Proactive Defense
- Trusted Systems
- Nuclear Material Science
- Radiological & Nuclear Detection
- Nuclear Forensics
- Ultra-Sensitive Nuclear Measurements
- Nuclear Explosion Monitoring
- Global Nuclear & Radiological Security
- Disaster Recovery
- Global Collaborations
- Legislative and Regulatory Analysis
- Technical Training
- Additive Manufacturing
- Deployed Technologies
- Rapid Prototyping
- Systems Engineering
- 5G Security
- RF Signal Detection & Exploitation
- Climate Security
- Internet of Things
- Maritime Security
- Artificial Intelligence
- Graph and Data Analytics
- Software Engineering
- Computational Mathematics & Statistics
- High-Performance Computing
- Visual Analytics
- Lab Objectives
- Publications & Reports
- Featured Research
- Diversity, Equity, Inclusion & Accessibility
- Lab Leadership
- Lab Fellows
- Staff Accomplishments
- Undergraduate Students
- Graduate Students
- Post-graduate Students
- University Faculty
- University Partnerships
- K-12 Educators and Students
- STEM Workforce Development
- STEM Outreach
- Meet the Team
- Internships
- Regional Impact
- Philanthropy
- Volunteering
- Available Technologies
- Industry Partnerships
- Licensing & Technology Transfer
- Entrepreneurial Leave
- Atmospheric Radiation Measurement User Facility
- Electricity Infrastructure Operations Center
- Energy Sciences Center
- Environmental Molecular Sciences Laboratory
- Grid Storage Launchpad
- Institute for Integrated Catalysis
- Interdiction Technology and Integration Laboratory
- PNNL Portland Research Center
- PNNL Seattle Research Center
- PNNL-Sequim (Marine and Coastal Research)
- Radiochemical Processing Laboratory
- Shallow Underground Laboratory
Cyber-Physical Research
Our nation’s critical infrastructure—from the electric grid to water distribution systems—forms the backbone of our society. And while new technology advances at a staggering pace, much of this infrastructure—both digital and physical—continues to age. The gap between new technology and aging systems presents daunting challenges for system operators working to maintain safe operations of these resources.
At PNNL, researchers are examining ways to protect critical infrastructure in the face of rapid change and ever-increasing threats to cyber-physical systems. The research involves partnering with system owners and operators to share actionable threat, vulnerability, and mitigation information, and works with vendors to produce secure systems.
Increasing threats require novel solutions
Today’s control systems are under increasing scrutiny and threat, while critical infrastructures require continual functionality upgrades for newer software and hardware. These stressors create a pressing need for security solutions.
PNNL’s cyberNET and powerNET testbeds offer experimental alternatives to improve and enhance cyber-physical research. These testbeds, combined with PNNL’s underlying research infrastructure, provide access to models, datasets, methodologies, and expertise to help understand vulnerabilities and overcome threats to cyber-physical systems.
CyberNET is a unique PNNL capability that provides the ability to emulate enterprise network environments to enable controlled experimentation that wouldn’t be possible in operational environments. It offers a dynamic, easily configurable, and customizable space where researchers can build, test, and evaluate their solutions in an enterprise-like environment.
PowerNET is another PNNL tool designed to assist and accelerate research and development for industrial cyber-physical systems while providing a shared resource to reduce the up-front cost for equipment. The testbed offers a means for non-power system engineers to experiment with power system equipment.
These community-based resources aim to optimize the development of cyber-based systems, tools, and approaches to monitor, detect, delay, and respond to attacks on our nation’s critical infrastructure.
Research topics
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

MODEL OF CYBER PHYSICAL SYSTEM IN THE CUSTOMER SATISFACTION OF AUTOMOBILE INDUSTRY IN INDIA

2019, India sold more 3.99 million units of automobiles. The sales of passenger vehicles were also improved. And the statistics tending to improve by the end of 2021. The most important thing to improve the customer service and customer satisfaction is to identify the demands to the customer. Automobile industries need to find the significant factors, which will meet the demands of the customer to a greater extent. The demands of the customer totally vary from time to time, so it is always necessary for the car industries to be updated with the same. We know that the digitalization plays a prominent role in introducing new technological innovations which in turn meets the demands of the customer. Hence, we can say that digitalization is very important factor for the automobile industries. The paper aims to create a model of Cyber physical systems in the customer satisfaction of automobile industry. The data sample for the research is collected from two Indian states mainly Gujarat and Kerala. The main reason to select India for the study are the increasing use of digitalization methods in India, increasing demands of customer satisfaction and competition in India.
Related Papers
IAEME PUBLICATION
IAEME Publication
Digital transformation and its relationship & impact of front end (Customer), especially on customer experience and customer satisfaction has been a focus of study for last three decades. What has started purely as a “After sales service” initially changed to service dominant logic, Customer relationship management and customer experience with evolution in thoughts accompanied by deep leaps in digital technology from computers of 1960’s to totally digital world of today. The changes in digital technology helped the “Front end -Customer side” to be in sync with the demands of the customers and paradigm shift in the customer service thoughts, knowledge, and practice. This review of literature is based on relationship between digital transformation and customer experience from 2006 to 2020 period, which saw a further dramatic change. Going hand in glove with each other digital transformation and customer experience has contributed to paradigm shift both internally & externally for business and end customers. While period of 1990 to 2000 can be called as initiation period ,2000 to 2005 is attributed to “Growth and adoption “of digital platforms into the customer facing processes. Era from 2006 to 2010 can be termed as a “stabilization era” while 2011 to 2020 with new technology started “Explosion era” in customer experience space with technologies like virtual and augmented reality.
Digital transformation and its relationship & impact of front end (Customer), especially on customer experience and customer satisfaction has been a focus of study for last three decades. What has started purely as a “After sales service” initially changed to service dominant logic, Customer relationship management and customer experience with evolution in thoughts accompanied by deep leaps in digital technology from computers of 1ob960’s to totally digital world of today. The changes in digital technology helped the “Front end -Customer side” to be in sink with the demands of the customers and paradigm shift in the customer service thoughts, knowledge and practice. This review of literature is based on relationship between digital transformation and customer experience from 1990 to 2005 period , which saw a dramatic change in both these areas. Going hand in glove with each other digital transformation and customer experience has contributed to paradigm shift both internally & externally for business and end customers
Vilakshan - XIMB Journal of Management
Purpose Automobile industry has been the backbone of manufacturing sector in any country. During the past decade, passenger car industry has emerged as the one of the growing sectors in the Indian economy. Technological features in the passenger cars industry has been evolving in the global market, and customers have been the most important stakeholders to judge the requirement of these features. Therefore, the purpose of this paper is to analyze the customers’ need for these emerging technologies using Kano model of customer satisfaction. Design/methodology/approach This paper has used the Kano model to assess the customer satisfaction for Indian passenger car companies. Overall, 250 customers of passenger cars from Northern India have been surveyed using well-structured questionnaire designed as per the Kano model. On the basis of responses, this study has categorized the technological attributes of passenger cars as attractive, must be, one-dimensional and indifferent. Findings “...
S. amarathunga
Sahan Amarathunga
Sustainability
José-Luis Montes
Technology has impacted businesses in different areas, and, consequently, many companies have found it necessary to make changes in their structures and business models to improve customer satisfaction. The objective was to quantify the effect of dynamic capabilities on customer satisfaction, through digital transformation within the automotive sector. A random sample of 42 questionnaires on 127 surveyed industries was collected during the period 2019–2020 in a pre-COVID-19 context. A structural equation model (SEM) in two stages was applied. In the first stage, two reflective models were built. In a second stage, a structural equation model was evaluated. The results obtained in this study showed that the capabilities of sensing, seizing and innovation were suitably grouped in a construct called “Dynamic Capabilities”. A positive influence of Dynamic Capabilities on customer satisfaction was found. Therefore, the companies in this industry should focus on developing dynamic capabil...
Hielke Ytsma
This Master Thesis will assess the question; how much digitalization, and connected technology is of importance to sustain as an automotive OEM in the long run. Our research focuses on the 3 leading German premium OEMs namely Audi, BMW and Mercedes, a Daimler brand, as we believe they provide a representative picture of the overall OEM's status quo when it comes to applying connected technology and digitization in their vehicles. In addition, we will study whether digitalization and connected technologies are vital prerequisites to be understood and embraced in full by automotive OEMs in order to sustain as a brand, or even as an entire industry. In order to study this and find supporting evidence to confirm our hypothesis, we created a model allowing us to combine the behavior of the customer, the (mega)trends within society, the business structure of the automotive industry as well as the (smart)phone industry and the offerings of the chosen 3 German OEMs. The inputs for this ...
CONFERENCE ON ELECTRICITY POWER SUPPLY INDUSTRY (CEPSI) 2021: THE ENERGY DIGICON OF ASIA-PACIFIC
Lanka R Perera
Electricity Distribution Utilities worldwide work relentlessly to maintain high levels of customer service to safely guard customer loyalty and their competitive edge in electricity markets. Even in monopolistic markets like that of Sri Lanka, ensuring high standards of customer service is considered paramount both in organizational perspective and in regulatory perspective. The ever-growing customer demands have further fuelled this process. Moreover, within the last decade, this focus has moved from physical service delivery to digital service delivery. In this light, a digital utility solution developed in-house was deployed by Ceylon Electricity Board, to cater to the ever-growing customer demands as well as the requirements of CEB's internal stakeholders. This system identified as "CEBAssist Solutions" is an innovative state-of-art utility solution that aims at improving customer engagement, internal business operations, field operations, workplace efficiency, and service quality by leveraging modern digital technologies. A holistic approach to customer service delivery has been adopted in developing the CEBAssist Solution which comprises multiple systems, modules, and mobile apps. Prospects for business process re-engineering and automation of business operations of CEB's different functional areas and digitizing business processes, which were manually accomplished previously, have been explored in developing the CEBAssist Solutions. At present, the CEBAssist Solutions is being implemented and utilized in all distribution divisions of Ceylon Electricity Board covering the whole of Sri Lanka and its customer mobile app 'CEB Care' has reached a user count of 300,000. This solution has disrupted the local utility market through the rapid delivery of digital products and services to customers combined with advanced features and full access to information. This paper discusses the implementation journey of the digital solution, CEBAssist, its present state of operation and the prospects for growth. In addition, the improvement perceived in customer engagement and the level of customer service delivery, and the lessons learnt via the journey are further discussed.
Dragan Cockalo
The paper presents research results obtained during the process of modeling a system (processes) for providing satisfaction of a company’s customer needs. The cybernetic model assumes a process approach and appropriate marketing research at the beginning and corresponding evaluation at the end; it is also harmonised with the conditions in which Serbian companies (production and services) work and it is
People become stronger as a result of digitalization, which allows them to save both time and money. The digital world blurs the lines between countries and brings individuals closer together. There is no need to go to a store to purchase a product or service; all it takes is a single click. Organizations are developing strategies to reach out to potential customers using digital platforms, which make it simple for them to reach out to the largest number of people. Buyers may now simply compare products on the basis of quality and pricing. Customers' purchasing decisions are also influenced by product availability. This study show that how digitalization influence customer buying behaviour, this study focus on some factors (reliability of digital information, easy access of websites, online digital communication source) which play important role for influencing the customers for buying product through digital platform. This study was conducted in Haridwar (Jwalapur, Kankhal, Sidkul) and sample size was 50. A questionnaire was prepared and based on some factors which influence customer buying behaviour.
Madhya Bharti, UGC CARE Group I Journal
Imthiyaz Ahmed Muhammad , Ayub Khan Dawood
In the twenty-first century, the traditional vehicle's high energy consumption and exhaust outflow issues have been widely concerned around the world. In the last decade, India has been growing at a faster rate on the motorization curve. Over the years, the exploitation and contaminating of natural resources have created the need for renewable and environment-friendly products. The electric vehicle is one of the most practicable alternative solutions to overcome the crises. They are one of the emerging technologies as well as eco-friendly and feasible. The replacement of internal ignition engines with electric engines will reduce pollution to a great extent and be profitable to consumers. Many countries around the globe have implemented this technology and are contributing towards betterment of the environment. The present study aims on influence of service quality on Customer satisfaction of electric vehicles in Chennai. 94 consumers using electric vehicles in Chennai were selected for the study as the samples. This is a descriptive study and questionnaire is used as the study instrument of the study to collect the data. Judgmental sampling, A non-probability sampling method is used to select the consumers. Multiple regression analysis and One-way ANOVA are the statistical tools used. SPSS v23 is used to perform the data analysis. The reliability of the study is observed as 82.8% (Chronbach's alpha = 0.828). It is noted that features, enactment and sales after service significantly impacts Customer satisfaction of e-vehicles, further enactment followed by features predicts Customer satisfaction of e-vehicles more. It is observed that age, monthly income and experience in electric vehicles driving are having significant influence on Customer satisfaction towards electric vehicles.
RELATED PAPERS
Mieneke Luijendijk
Lendvai Gábor
Parasitology Today
Celia Holland
Journal of Clinical Investigation
James Ferrara
mona semalty
Daniela Manzano Bonilla
Juan Luis Cueto Morelo
Bioscience Journal
Rosana Romero
Alex Sandro
Rui Barbosa de Souza
Gazi Medical Journal
petra mezek
Rap, Hip Hop e identidad en las producciones musicales andaluzas
Noelia Sánchez
Rita Frenedozo
Lietuvos istorijos metraštis [Yearbook of Lithuanian History]. 2011, 2010/1, p. 23-38. ISSN 0202-3342; 2538-6549
Agnė Railaitė-Bardė
The European Journal of the History of Economic Thought
ACM SIGART Bulletin
Deepak Kumar
International Journal of Computer Applications
ahmed nasser
African statistical journal = Journal statistique africain
Alexis Naho
Revista de Gastroenterología del Perú
SIVAS II. INTERNATIONAL CONFERENCE ON SCIENTIFIC AND INNOVATION RESEARCH 15-17 SEPTEMBER - SİVAS / TÜRKİYE
abdulhafeez A B U B A K A R ochepa
MINU BAJPAI
Yeshes Vodgsal Atshogs
Gabriel M U Ñ O Z Leal
Prace Instytutu Elektrotechniki
Roman Ostrowski
See More Documents Like This
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

IMAGES
VIDEO
COMMENTS
Open issues in medical cyber physical system (MCPS) During our research, we have found a few things that need to be done in the field of Medical Cyber Physical System (MCPS). These issues can be called: 8.1.1. Security and privacy. Security and privacy issues are being talked about in MCPS, which is when medical devices can talk to each other.
Such that their multi-scale interconnection and interaction is better captured by the notion of Cyber-Physical System of Systems (CPSoS), defining a large and distributed complex system of CPSs. ... To get an overview on the open research topics, the general topics are split into following categories. They only address several general topics as ...
Cyber-physical system (CPS) is an interdisciplinary research field that features systematic integrations of computation, communication, and control of physical processes. It is characterized by the deep complex intertwining process among the embedded cyber components and the dynamic physical components that involve mechanical components, human ...
Journal overview. Cyber-Physical Systems is an international interdisciplinary journal dedicated to publishing the highest quality research in the rapidly-growing field of cyber-physical systems / Internet-of-Things. Publications cover theory, algorithms, simulations, architectures, implementations, services and applications of state-of-the-art ...
This Section lays the groundwork for this research; the theoretical foundations of CPS are presented in 2.1 and additional related work is introduced that also seeks to structure industrial CPS in 2.2.. 2.1 Foundations of Cyber-Physical Systems. The term CPS was introduced by E. A. Lee in 2006; since then, the topic has been further analyzed and developed in several scientific and practical ...
Abstract. The CPSoS project is developing a roadmap for future research and innovation in cyber-physical systems of systems. This paper presents preliminary findings and proposals that are put forward as a result of broad consultations with experts from industry and academia, and through analysis of the state of the art in cyber-physical ...
The purpose of this Research Topic is to promote outstanding research concerning human-in-the-loop cyber-physical systems, focusing on state-of-the-art progress, developments, and new trends. Cyber-physical systems (CPS) are connecting our physical world and cyberspace through real-time sensing, situational awareness, and intelligent control.
A. Cyber-physical systems The term cyber-physical systems (CPS) emerged around 2006, when it was coined at the National Science Foundation (NSF) in the United States [1], with the "cyber" part of the name resulting from the term "cybernetics", introduced as metaphor apt for control systems [11]. (a) The three main functional components ...
In this section, som e open research topics of . interest are identified precisely. ... Human-Cyber-Physical System HCPS to achieve system safety and efficiency for connected vehicles, is proposed ...
A cyber-physical system (CPS) aims at integrating the cyberspace (e.g., Web, Clouds, IoT) with vital physical operational systems (e.g., power grids, water systems, vehicles, UXVs, rail, intelligent transportation systems, etc.). ... All contributions to this Research Topic must be within the scope of the section and journal to which they are ...
Keywords: collective systems, cyber-physical systems, digital twins, systems-of-systems, nature-inspired approaches, verification & validation, swarm robotics . Important Note: All contributions to this Research Topic must be within the scope of the section and journal to which they are submitted, as defined in their mission statements.
The mission of the Cyber-Physical Systems Research Center (CPSRC) is to promote and facilitate collaborative research activities within UCSC as well as with its academic and industrial partners on key cyber-physical systems topics. CPSRC will foster novel foundational and applied research to support applications such as smart cities and ...
Later I will describe these research threads, which are part of a larger body of research we call Safety Analysis and Fault Detection Isolation and Recovery (SAFIR) Synthesis for Time-Sensitive Cyber-Physical Systems. First, let's take a closer look at the problem space and the challenges we are working to overcome.
A Cyber-Physical-Social System (CPSS) is an evolving subset of Cyber-Physical Systems (CPS), which involve the interlinking of the cyber, physical, and social domains within a system-of-systems mindset. ... The oldest research topics were located in the center, with newer research extending to either side, as shown in Figure 6. The oldest ...
The smart healthcare cyber physical systems are symbiotic to various autonomous systems as shown in Fig. 3. Smart grid, smart home, smart vehicular systems, smart hospitals and smart manufacturing units provide services for a smart city healthcare system. In turn, the smart city healthcare system provides healthcare to its inhabitants.
Cyber-Physical Systems (CPS) is a multidimensional complex system that integrates computing, network, and physical environments. Due to the existence of network communications and embedded computers, CPS is vulnerable to attacks, so its security has become an important issue. The paper studies the main types of network attacks and the methods of detection, including the security estimation and ...
The aim of this paper is to explore what CPS research topics are related to the emerging IT trends and to investigate how industries have implemented CPS technologies. Recently, there has been an explosive growth in the development and implementation of various Cyber-Physical Systems (CPS). Accordingly, CPS-related research and advancements in CPS technologies have increasingly been part of ...
Cyber-Physical Systems. The term Cyber-Physical System (CPS) is used to describe dynamic systems which combine components characterized by a physical state (e.g., the location, power level, and temperature of a mobile robot) with components (mostly digital devices empowered by software) characterized by an operational state or mode (e.g., on ...
Topics in Cyber-Physical Systems. Instructor: Prof. Xiaofan Jiang Time: Thursdays 1:50PM-3:40PM Location: 1127 Mudd Class ID: ELEN 6908 E sec. 001. ... One objective is to learn the current state of art in Cyber-Physical Systems research, including its various application domains. A second objective is to learn details regarding several ...
This Research Topic is devoted to the presentation of original research and insightful reviews, emphasizing innovations and enhancements within the domains of advanced attacks, system security, privacy, and trust technology in Cyber-Physical Social Systems (CPSS).
PowerNET is another PNNL tool designed to assist and accelerate research and development for industrial cyber-physical systems while providing a shared resource to reduce the up-front cost for equipment. The testbed offers a means for non-power system engineers to experiment with power system equipment. These community-based resources aim to ...
The present research includes identification of important cyber physical system factors from the factorial analysis. Descriptive analysis used for the data analysis of the survey results. The relations between the important factors were evaluated and model of the cyber physical system factors in the customer satisfaction of automobile industry ...